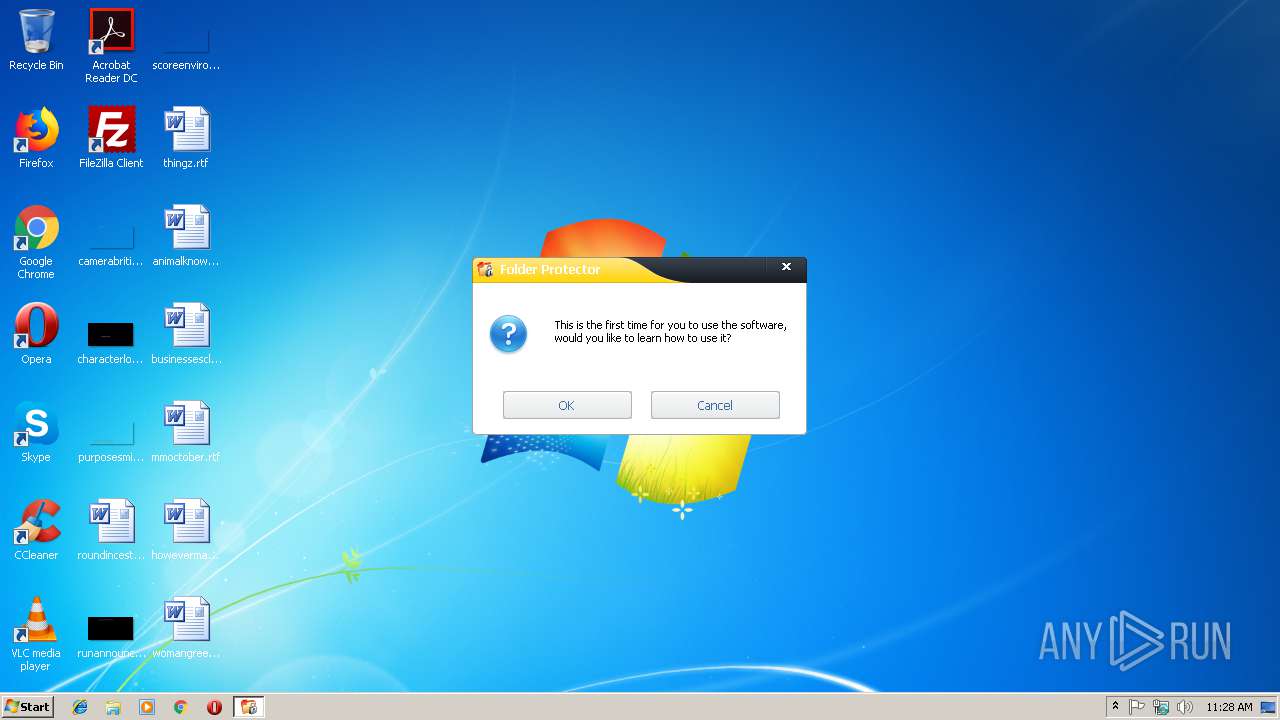
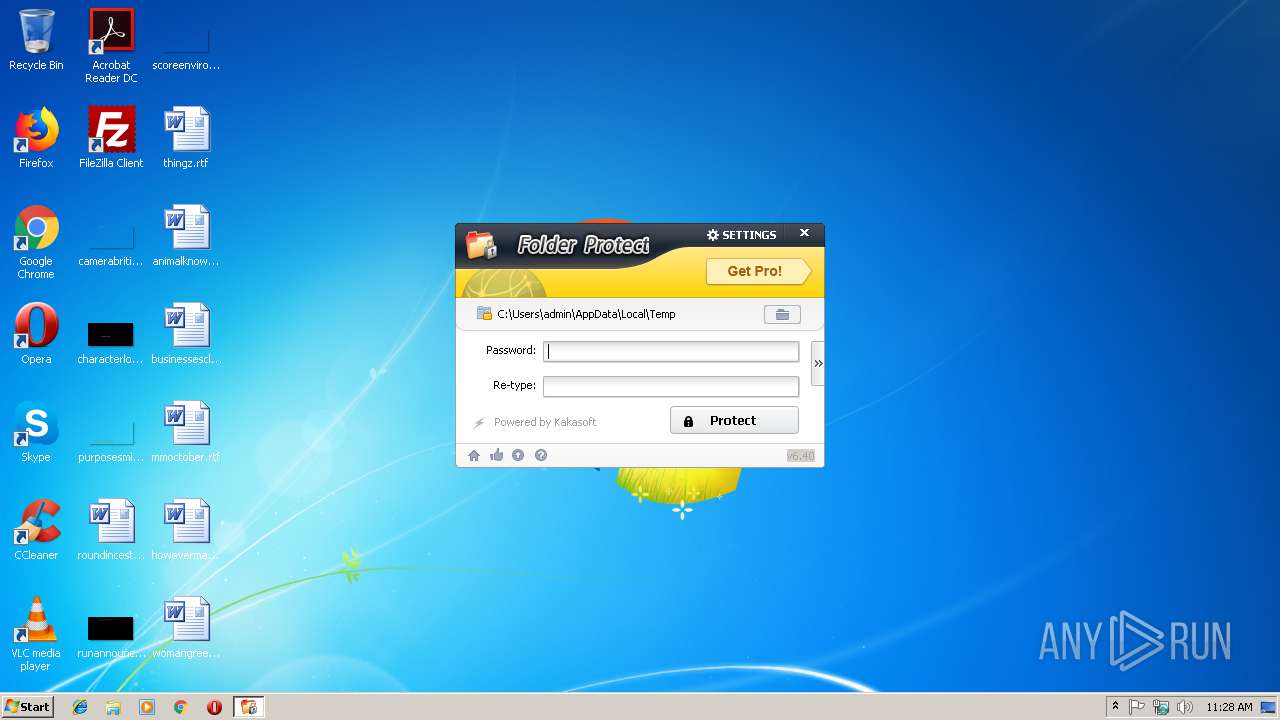
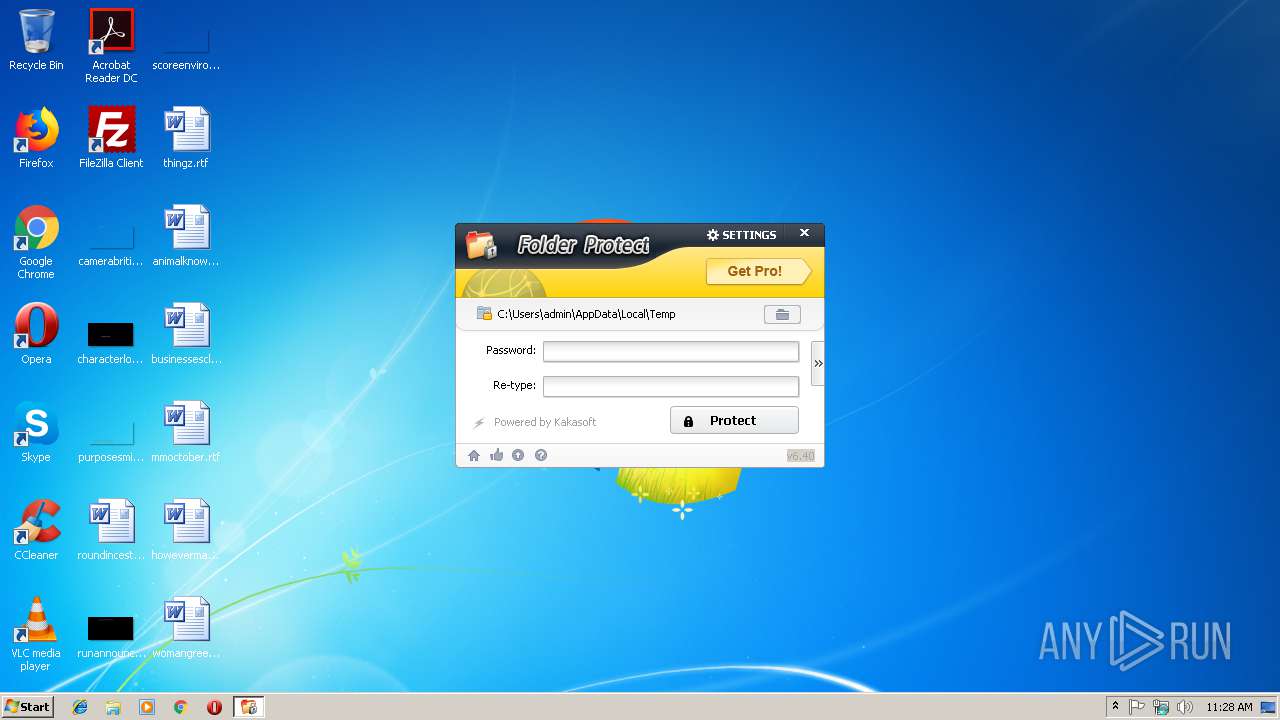
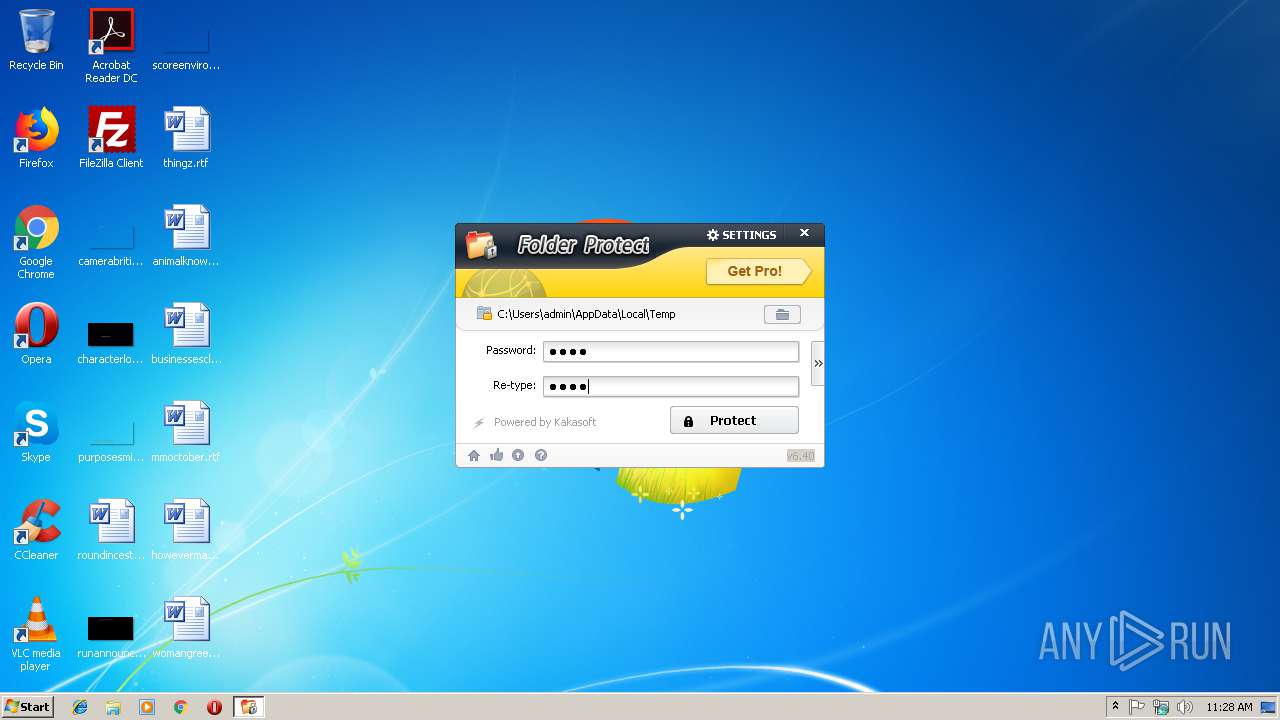
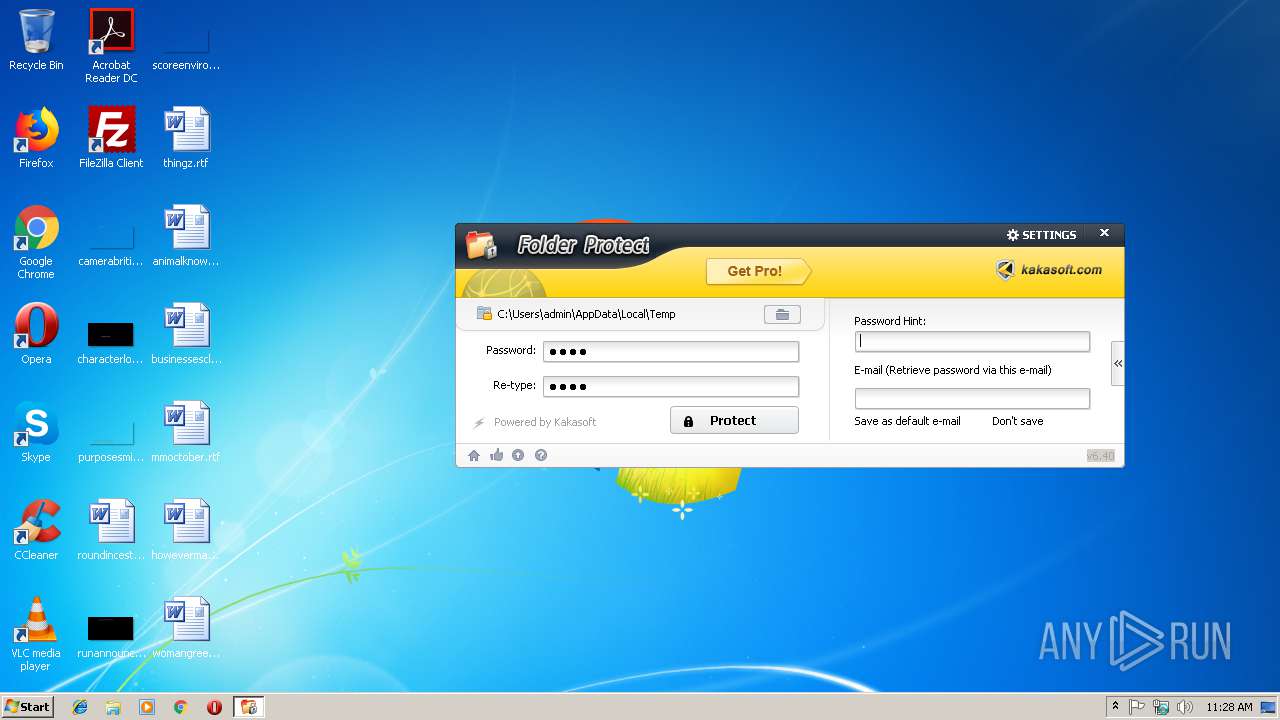
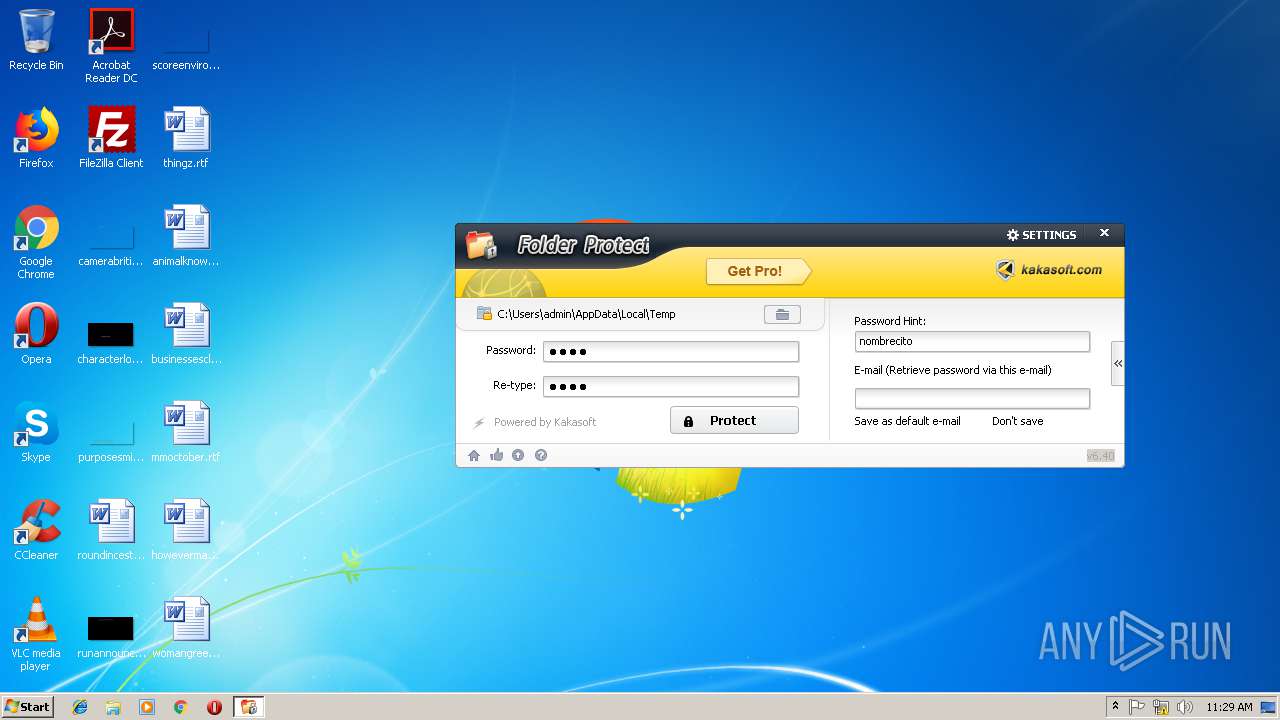
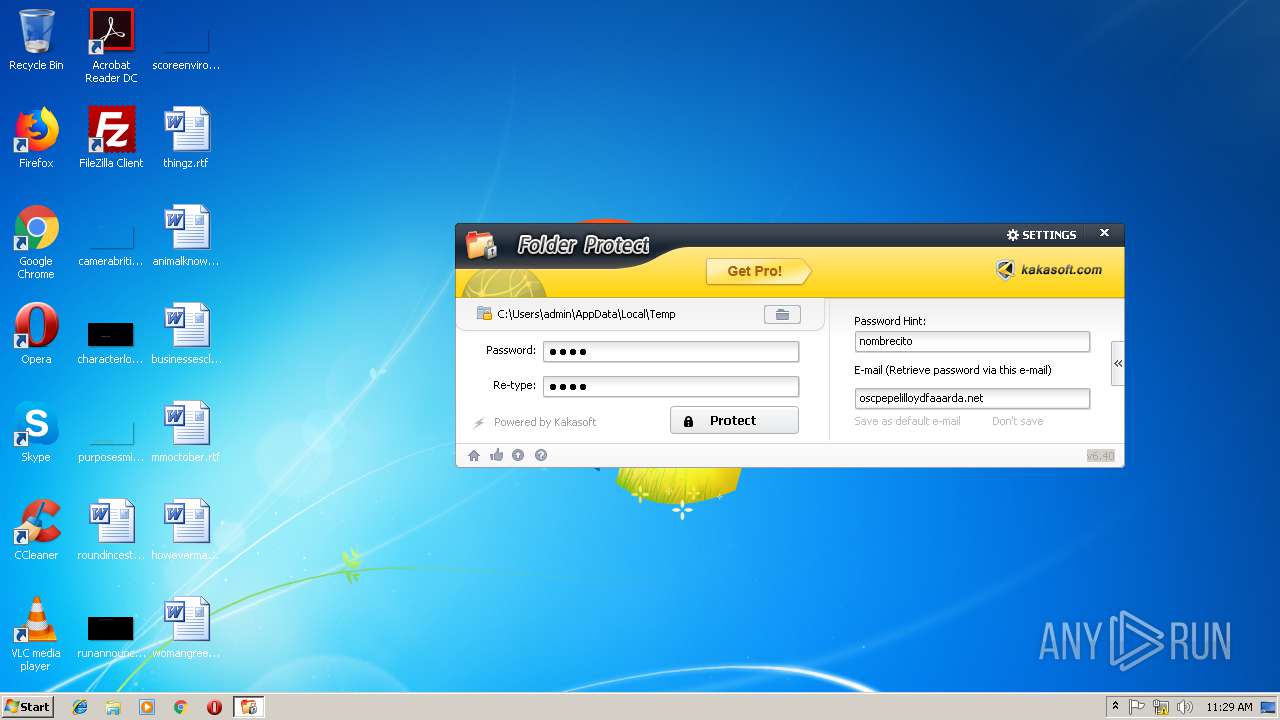
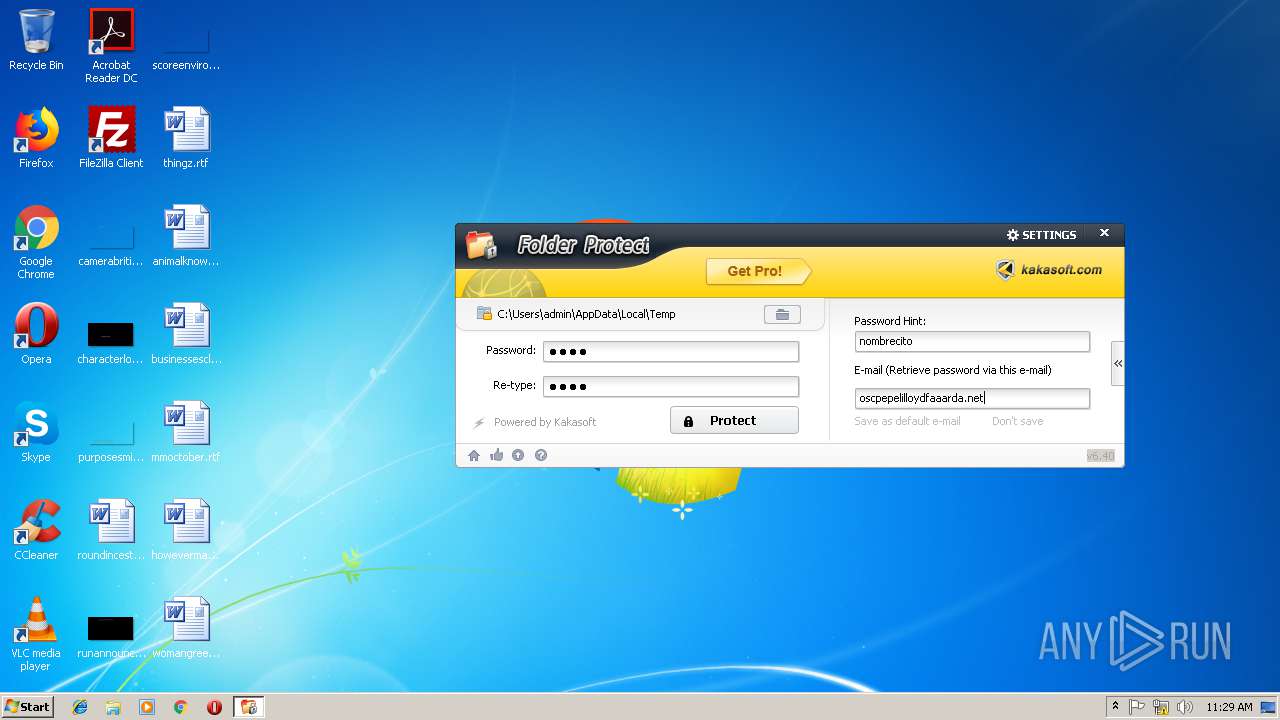
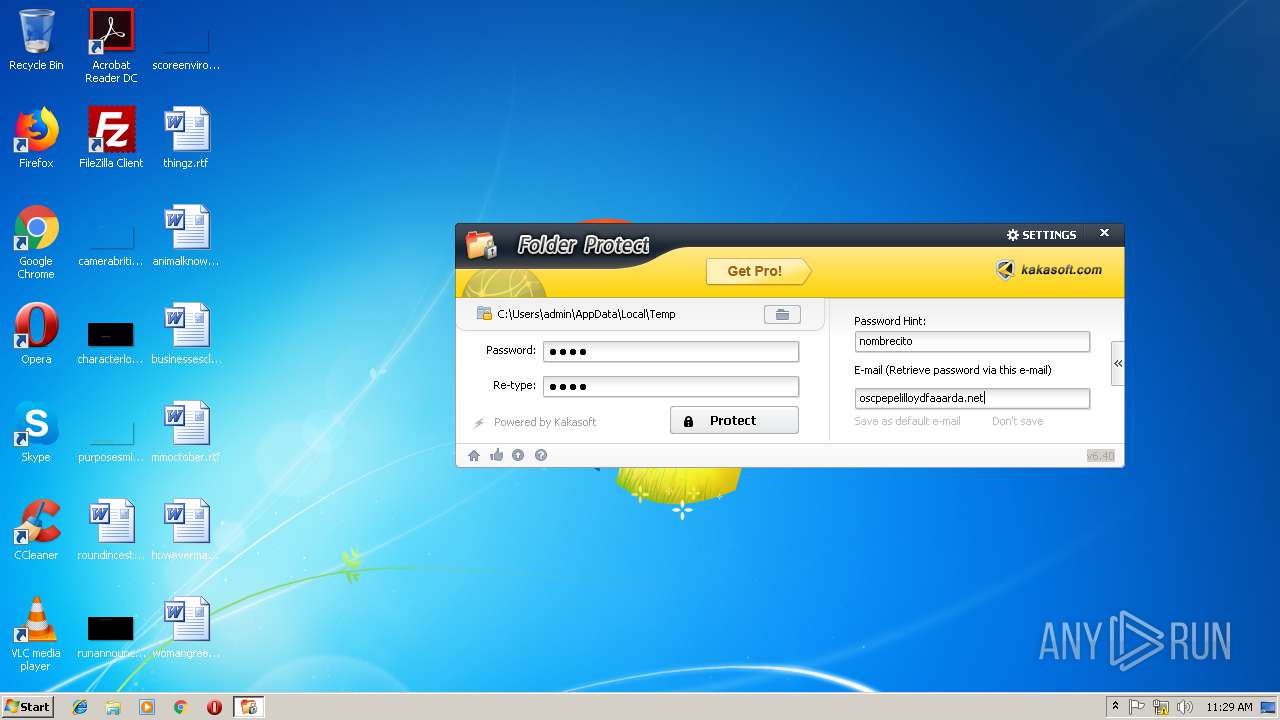
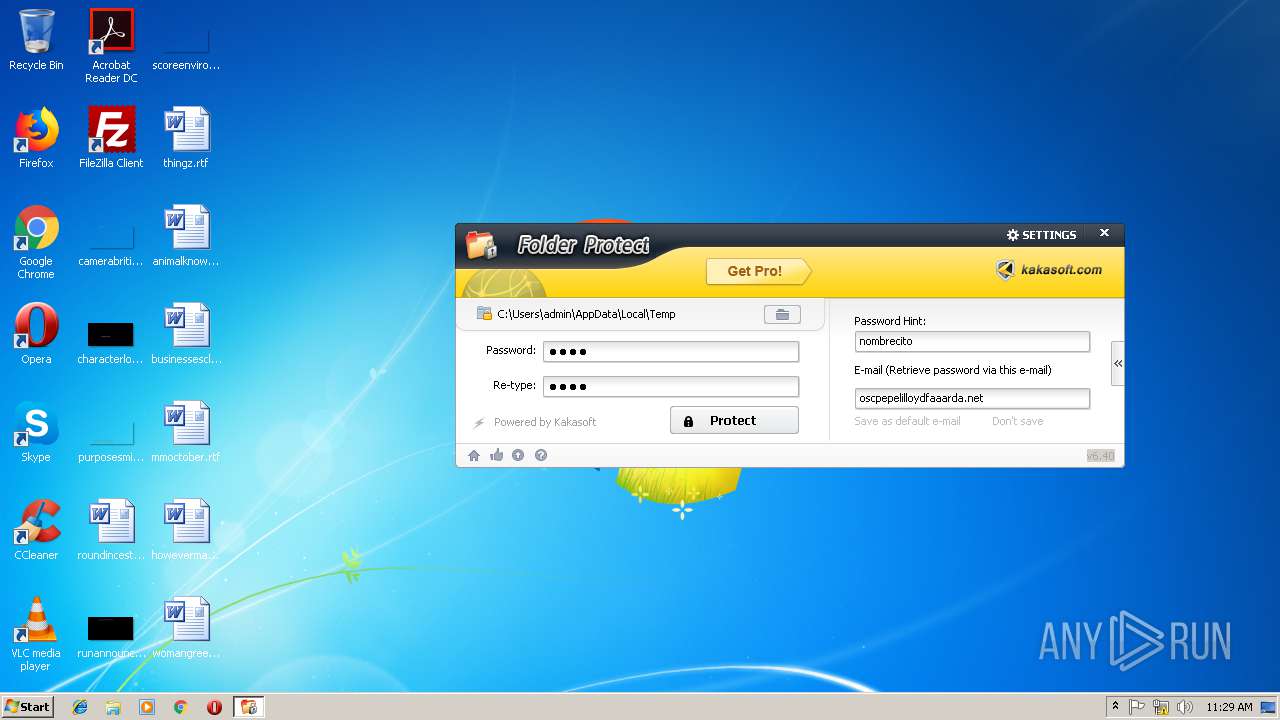
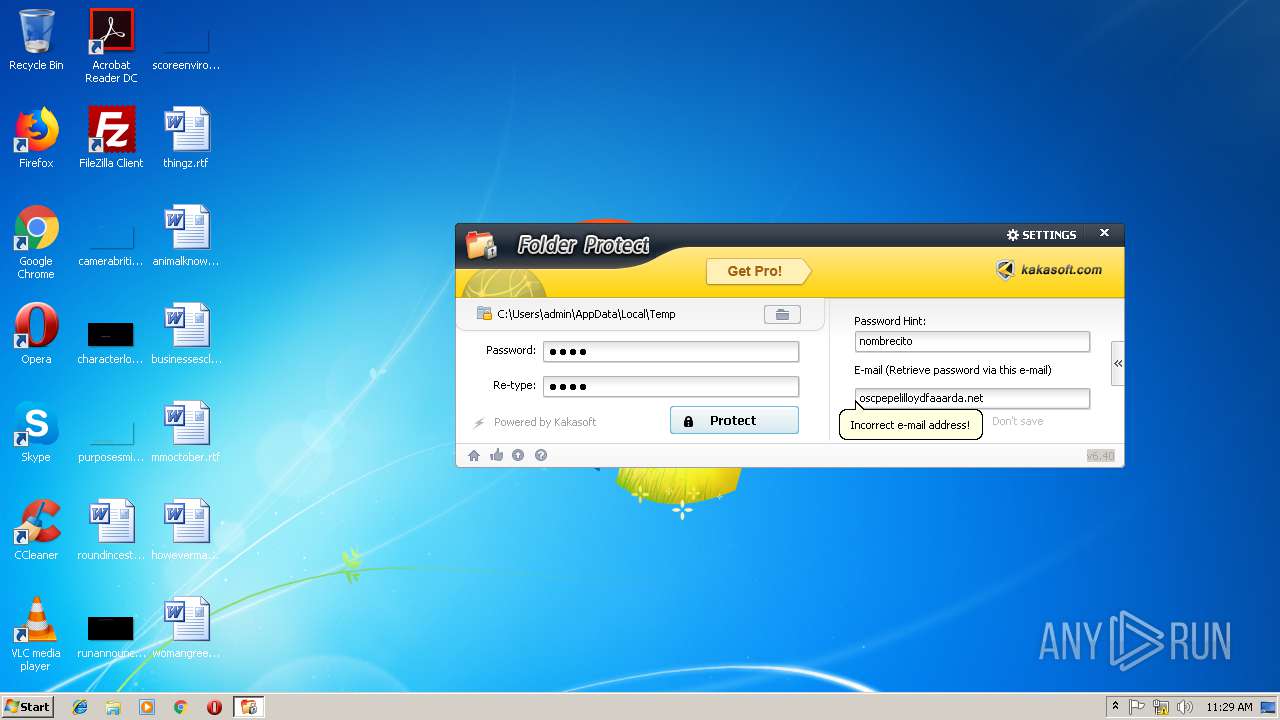
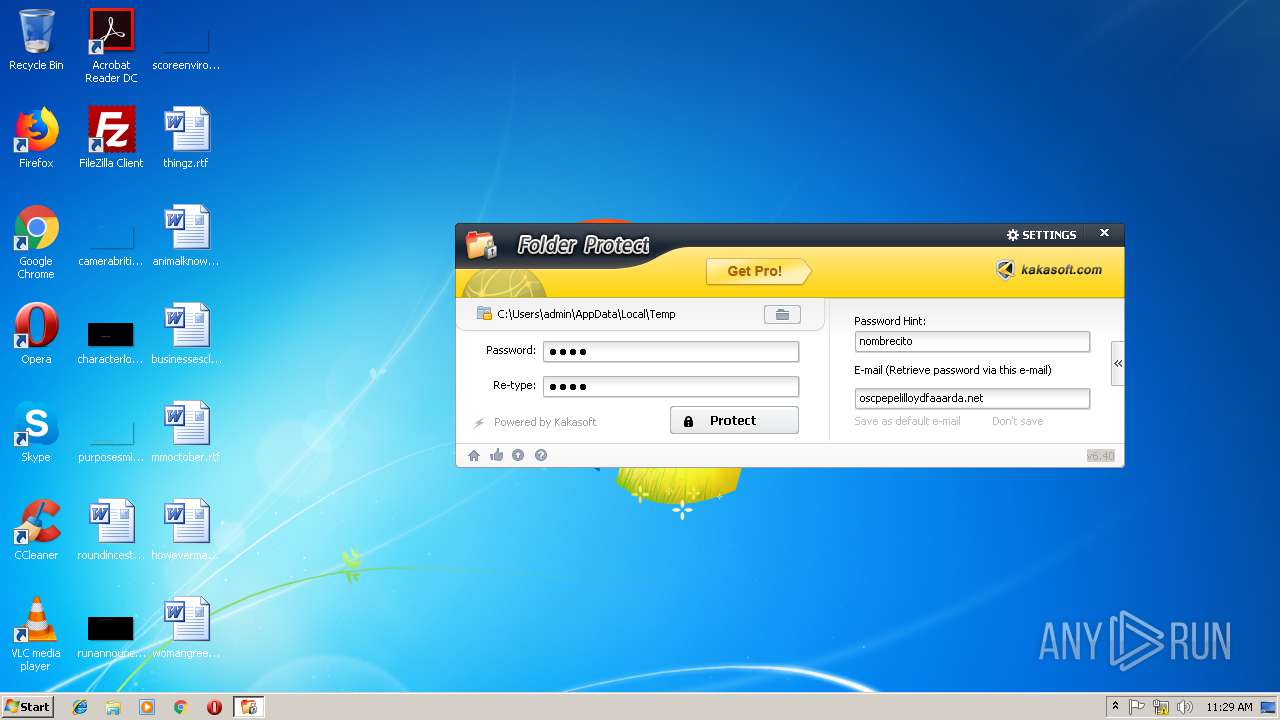
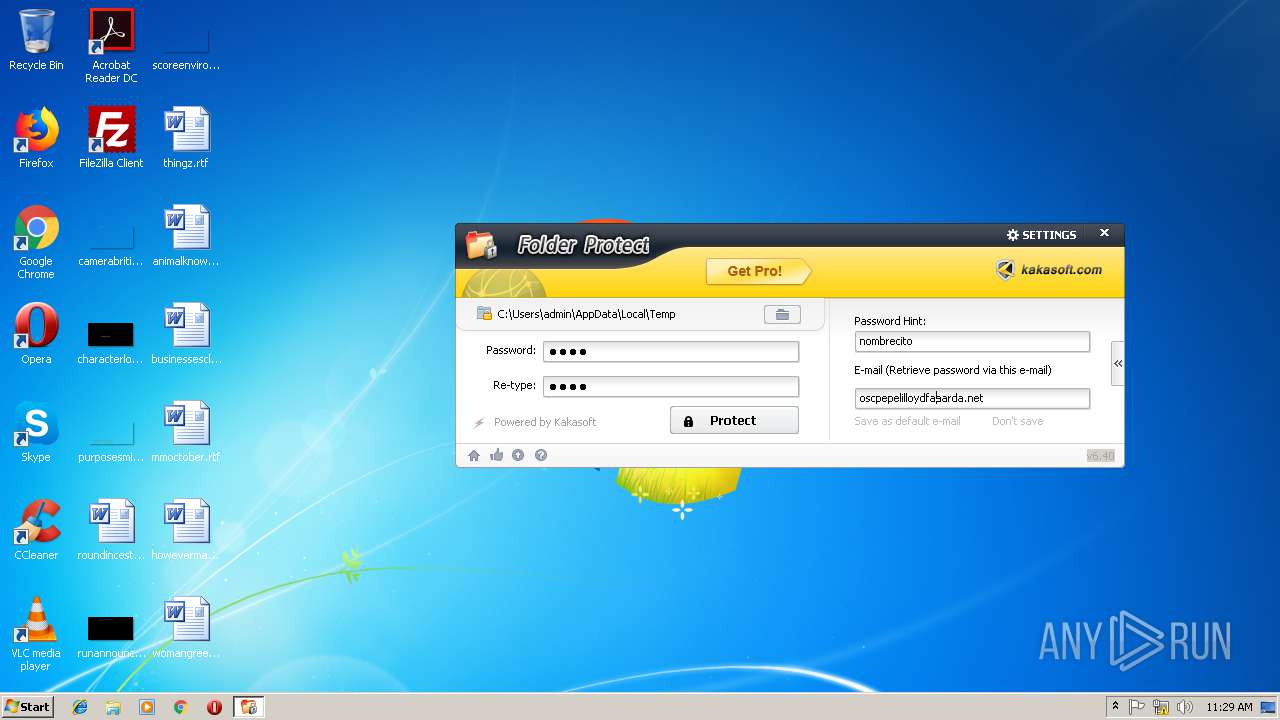
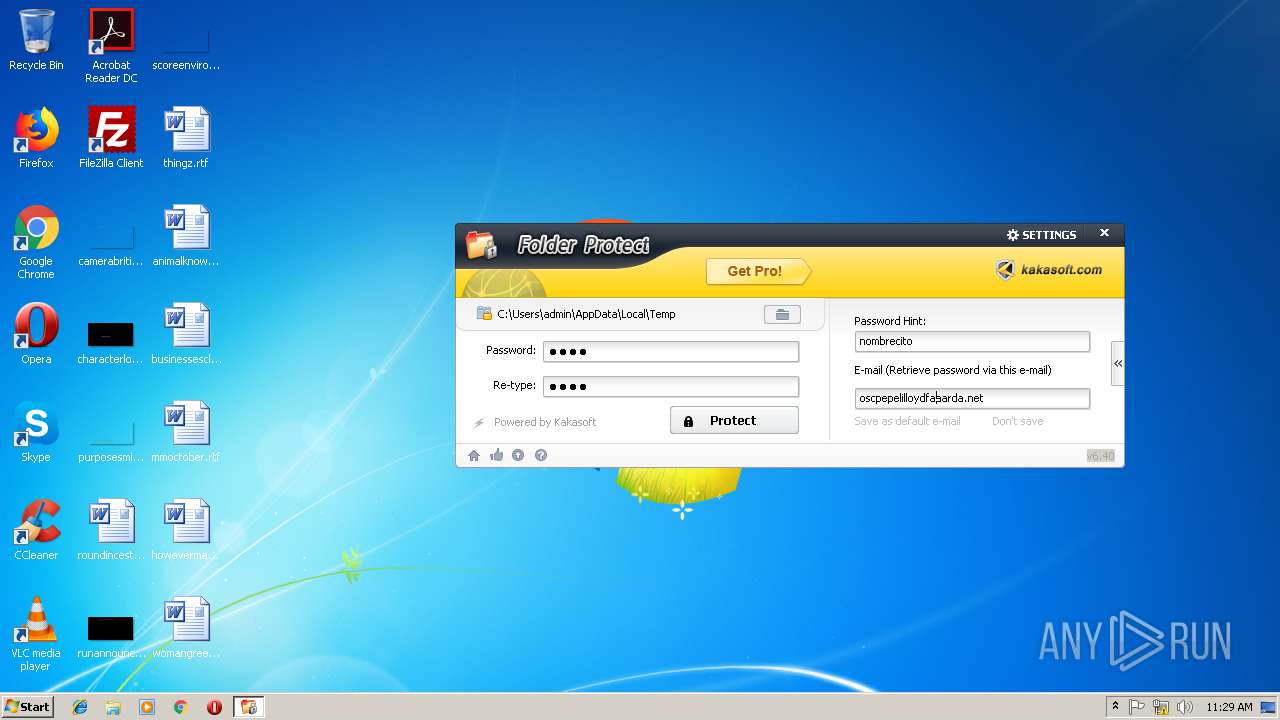
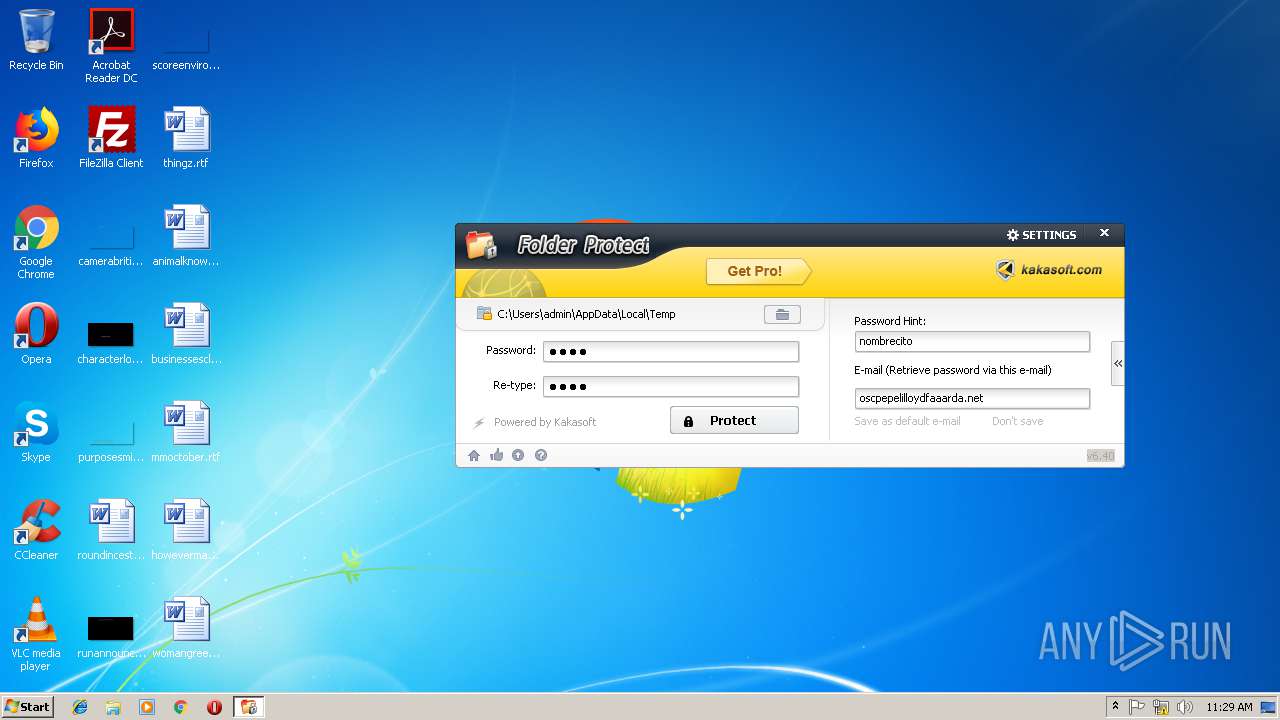
| File name: | lockdir.exe |
| Full analysis: | https://app.any.run/tasks/25e89705-3829-493d-bf64-b9bc8f2b8fd0 |
| Verdict: | Malicious activity |
| Analysis date: | December 17, 2018, 11:27:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed |
| MD5: | F5128D0DEA6942FED4E793DD912C7AE3 |
| SHA1: | 0C2C1D58DC7FBABA5DF6BC8A542E805CAA02C1EC |
| SHA256: | 6025C4D0EF73FB1B12FA07E1A59E001E14E5A5BB25A3435E6B6DFDB61D2365BD |
| SSDEEP: | 24576:7WvoCJLiF4W1Dd5vtaeOBWpklxekZ7Mq+zvUiVbsMHyA1UyKycV:7WvoCJLibd5lMWpkDekFM7zv/Vbs8yAc |
MALICIOUS
Connects to CnC server
- lockdir.exe (PID: 3116)
SUSPICIOUS
Writes to a desktop.ini file (may be used to cloak folders)
- lockdir.exe (PID: 3116)
INFO
Creates files in the user directory
- opera.exe (PID: 3672)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (42.1) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (41.3) |
| .exe | | | Win32 Executable (generic) (7) |
| .exe | | | Win16/32 Executable Delphi generic (3.2) |
| .exe | | | Generic Win/DOS Executable (3.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:07:12 11:59:50+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 1232896 |
| InitializedDataSize: | 155648 |
| UninitializedDataSize: | 7925760 |
| EntryPoint: | 0x8bbbf0 |
| OSVersion: | 5 |
| ImageVersion: | - |
| SubsystemVersion: | 5 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 6.4.0.95 |
| ProductVersionNumber: | 6.4.0.95 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Kakasoft |
| FileDescription: | A useful tool to Lock/Encrypt folders, flash disk and Hard drive |
| FileVersion: | 6.4.0.95 |
| InternalName: | Folder Protector |
| LegalCopyright: | Copyright 2008-2016 KakaSoft.All rights reserved |
| LegalTrademarks: | - |
| OriginalFileName: | - |
| ProductName: | Folder Protector |
| ProductVersion: | 6.4 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 12-Jul-2016 09:59:50 |
| Detected languages: |
|
| CompanyName: | Kakasoft |
| FileDescription: | A useful tool to Lock/Encrypt folders, flash disk and Hard drive |
| FileVersion: | 6.4.0.95 |
| InternalName: | Folder Protector |
| LegalCopyright: | Copyright 2008-2016 KakaSoft.All rights reserved |
| LegalTrademarks: | - |
| OriginalFilename: | - |
| ProductName: | Folder Protector |
| ProductVersion: | 6.40 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0050 |
| Pages in file: | 0x0002 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x000F |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x001A |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 12-Jul-2016 09:59:50 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
UPX0 | 0x00001000 | 0x0078F000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
UPX1 | 0x00790000 | 0x0012D000 | 0x0012CA00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.99971 |
.rsrc | 0x008BD000 | 0x00026000 | 0x00025200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.75353 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.91814 | 850 | UNKNOWN | Chinese - PRC | RT_MANIFEST |
2 | 6.13046 | 4264 | UNKNOWN | Chinese - PRC | RT_ICON |
3 | 5.57219 | 1128 | UNKNOWN | Chinese - PRC | RT_ICON |
4 | 5.19009 | 9640 | UNKNOWN | Chinese - PRC | RT_ICON |
5 | 5.45078 | 4264 | UNKNOWN | Chinese - PRC | RT_ICON |
6 | 5.50517 | 1128 | UNKNOWN | Chinese - PRC | RT_ICON |
7 | 5.54005 | 9640 | UNKNOWN | Chinese - PRC | RT_ICON |
8 | 5.63374 | 4264 | UNKNOWN | Chinese - PRC | RT_ICON |
9 | 5.43935 | 1128 | UNKNOWN | Chinese - PRC | RT_ICON |
10 | 4.22283 | 9640 | UNKNOWN | Chinese - PRC | RT_ICON |
Imports
KERNEL32.DLL |
advapi32.dll |
comctl32.dll |
gdi32.dll |
mpr.dll |
msimg32.dll |
msvcrt.dll |
ole32.dll |
oleaut32.dll |
shell32.dll |
Total processes
31
Monitored processes
2
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3116 | "C:\Users\admin\AppData\Local\Temp\lockdir.exe" | C:\Users\admin\AppData\Local\Temp\lockdir.exe | explorer.exe | ||||||||||||
User: admin Company: Kakasoft Integrity Level: MEDIUM Description: A useful tool to Lock/Encrypt folders, flash disk and Hard drive Exit code: 0 Version: 6.4.0.95 Modules
| |||||||||||||||
| 3672 | "C:\Program Files\Opera\opera.exe" | C:\Program Files\Opera\opera.exe | explorer.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Exit code: 0 Version: 1748 Modules
| |||||||||||||||
Total events
281
Read events
169
Write events
112
Delete events
0
Modification events
| (PID) Process: | (3672) opera.exe | Key: | HKEY_CURRENT_USER\Software\Opera Software |
| Operation: | write | Name: | Last CommandLine v2 |
Value: C:\Program Files\Opera\opera.exe | |||
| (PID) Process: | (3672) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
0
Suspicious files
44
Text files
30
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3116 | lockdir.exe | C:\Users\admin\AppData\Local\Temp\Thumbs.ms\com1.{d3e34b21-9d75-101a-8c3d-00aa001a1652}\ã..\LastF\acrord32_sbx | — | |
MD5:— | SHA256:— | |||
| 3116 | lockdir.exe | C:\Users\admin\AppData\Local\Temp\Thumbs.ms\com1.{d3e34b21-9d75-101a-8c3d-00aa001a1652}\ã..\LastF\CVR3573.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3116 | lockdir.exe | C:\Users\admin\AppData\Local\Temp\Thumbs.ms\com1.{d3e34b21-9d75-101a-8c3d-00aa001a1652}\ã..\LastF\CVR499D.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3116 | lockdir.exe | C:\Users\admin\AppData\Local\Temp\Thumbs.ms\com1.{d3e34b21-9d75-101a-8c3d-00aa001a1652}\ã..\LastF\CVR7ED0.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3116 | lockdir.exe | C:\Users\admin\AppData\Local\Temp\Thumbs.ms\com1.{d3e34b21-9d75-101a-8c3d-00aa001a1652}\ã..\LastF\DbTemp | — | |
MD5:— | SHA256:— | |||
| 3116 | lockdir.exe | C:\Users\admin\AppData\Local\Temp\Thumbs.ms\com1.{d3e34b21-9d75-101a-8c3d-00aa001a1652}\ã..\LastF\1iowsmwn.cz4 | binary | |
MD5:— | SHA256:— | |||
| 3116 | lockdir.exe | C:\Users\admin\AppData\Local\Temp\Thumbs.ms\com1.{d3e34b21-9d75-101a-8c3d-00aa001a1652}\ã..\LastF\1wd05xlf.yzm | binary | |
MD5:— | SHA256:— | |||
| 3116 | lockdir.exe | C:\Users\admin\AppData\Local\Temp\Thumbs.ms\com1.{d3e34b21-9d75-101a-8c3d-00aa001a1652}\ã..\LastF\5sdrmmwf.5rd | binary | |
MD5:— | SHA256:— | |||
| 3116 | lockdir.exe | C:\Users\admin\AppData\Local\Lockdir6 | text | |
MD5:— | SHA256:— | |||
| 3116 | lockdir.exe | C:\Users\admin\AppData\Local\Temp\Thumbs.ms\com1.{d3e34b21-9d75-101a-8c3d-00aa001a1652}\ã..\LastF\Low | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
8
DNS requests
4
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3116 | lockdir.exe | GET | 200 | 50.93.203.14:80 | http://info.kakasoft.com/regmgr/checkupdate.php?name=lockdir_brd&builtdate=151127&cracked=0 | US | text | 121 b | malicious |
3672 | opera.exe | GET | 200 | 66.225.197.197:80 | http://crl4.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 543 b | whitelisted |
3116 | lockdir.exe | GET | 200 | 50.93.203.14:80 | http://info.kakasoft.com/regmgr/custom.php?name=lockdir_brd&ver=6.40&action=2&IsRegUser=0&remark1=28837C09FA_L_316754A3A8&win=7_x86&rt=0 | US | html | 159 b | malicious |
3116 | lockdir.exe | GET | 200 | 50.93.203.14:80 | http://info.kakasoft.com/regmgr/custom.php?name=lockdir_brd&ver=6.40&action=0&IsRegUser=0&remark1=28837C09FA_L_316754A3A8 | US | html | 121 b | malicious |
3116 | lockdir.exe | GET | 200 | 50.93.203.14:80 | http://info.kakasoft.com/regmgr/ad.php?name=lockdir_brd&ver=6.40&builtdate=151127&remark1=28837C09FA_L_316754A3A8 | US | text | 25 b | malicious |
3672 | opera.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPJvUY%2Bsl%2Bj4yzQuAcL2oQno5fCgQUUWj%2FkK8CB3U8zNllZGKiErhZcjsCEAOXQPQlVpLtFek%2BmcpabOk%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3116 | lockdir.exe | 50.93.203.14:80 | info.kakasoft.com | Jazz Network Inc. | US | malicious |
3672 | opera.exe | 82.145.215.40:443 | certs.opera.com | Opera Software AS | — | whitelisted |
3672 | opera.exe | 66.225.197.197:80 | crl4.digicert.com | CacheNetworks, Inc. | US | whitelisted |
3672 | opera.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
info.kakasoft.com |
| malicious |
certs.opera.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3116 | lockdir.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.FolderLock Check-in |
3116 | lockdir.exe | A Network Trojan was detected | MALWARE [PTsecurity] Trojan.FolderLock Check-in |