| download: | /Daksh17440/VIRUS-1.0/raw/refs/heads/main/VIRUS.exe |
| Full analysis: | https://app.any.run/tasks/dd4cb44d-30a4-40bc-9500-1ae33a934da4 |
| Verdict: | Malicious activity |
| Analysis date: | May 28, 2025, 16:32:36 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 7 sections |
| MD5: | CA968D3A6DEA5E46716281CEB6CD575C |
| SHA1: | 792EF05B2262577E39B0C91D57874C2326EF0DC5 |
| SHA256: | 6023EA55D3FF78B3642367375C276BBDE744636C1D485B5BF7CF3D4609936BEF |
| SSDEEP: | 98304:tc6QP+mdQDwh5w53NkVSWLCpiUKUZpk3PkRpl49YjW/gZH/DmC2powOmeSN07NEQ:6UIx6mDg67E4s |
MALICIOUS
No malicious indicators.SUSPICIOUS
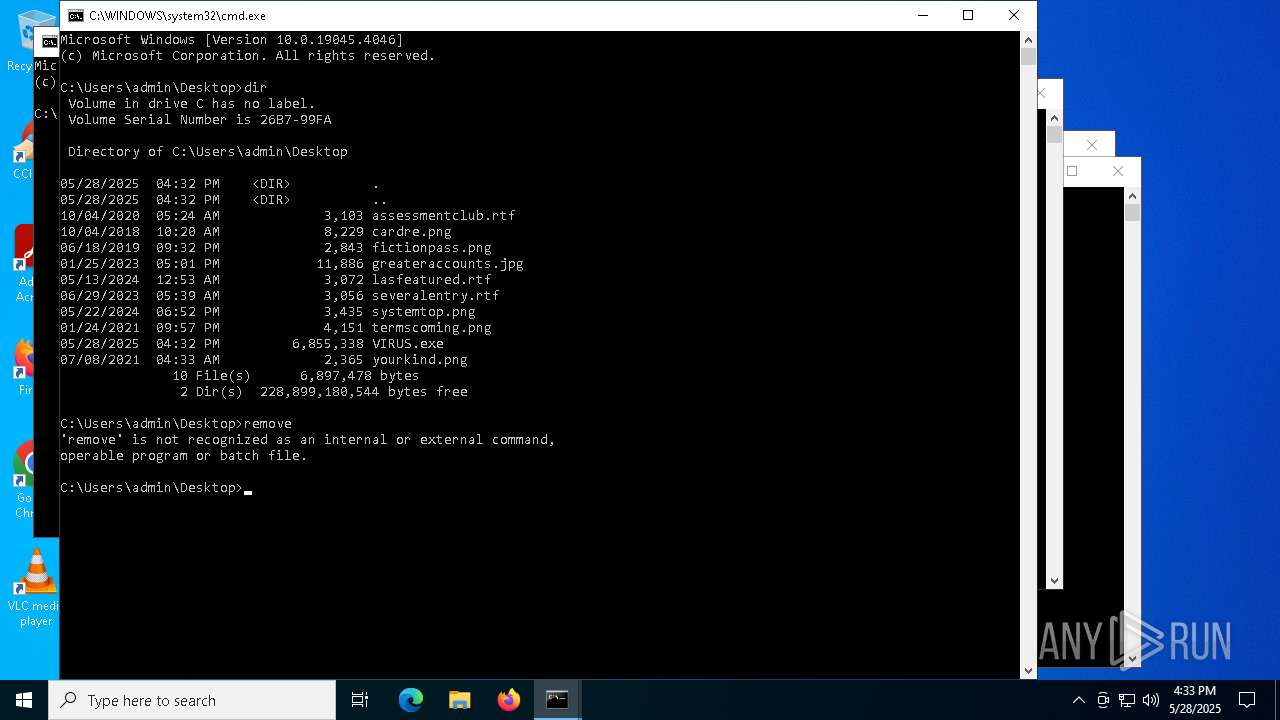
Executable content was dropped or overwritten
- VIRUS.exe (PID: 7512)
Application launched itself
- VIRUS.exe (PID: 7512)
- cmd.exe (PID: 7604)
- cmd.exe (PID: 7648)
- cmd.exe (PID: 7700)
- cmd.exe (PID: 7776)
- cmd.exe (PID: 7928)
- cmd.exe (PID: 7860)
- cmd.exe (PID: 7984)
- cmd.exe (PID: 8064)
- cmd.exe (PID: 8128)
- cmd.exe (PID: 7216)
- cmd.exe (PID: 7176)
- cmd.exe (PID: 5556)
- cmd.exe (PID: 4040)
- cmd.exe (PID: 1228)
- cmd.exe (PID: 5640)
- cmd.exe (PID: 7616)
- cmd.exe (PID: 7196)
- cmd.exe (PID: 5072)
- cmd.exe (PID: 7272)
- cmd.exe (PID: 6944)
- cmd.exe (PID: 8040)
- cmd.exe (PID: 8132)
- cmd.exe (PID: 7252)
- cmd.exe (PID: 616)
- cmd.exe (PID: 5056)
- cmd.exe (PID: 5508)
- cmd.exe (PID: 7736)
- cmd.exe (PID: 8064)
- cmd.exe (PID: 7704)
- cmd.exe (PID: 7376)
- cmd.exe (PID: 7328)
- cmd.exe (PID: 7908)
- cmd.exe (PID: 7756)
- cmd.exe (PID: 8320)
- cmd.exe (PID: 8388)
- cmd.exe (PID: 8460)
- cmd.exe (PID: 8528)
- cmd.exe (PID: 8668)
- cmd.exe (PID: 8604)
- cmd.exe (PID: 8236)
- cmd.exe (PID: 8756)
- cmd.exe (PID: 8824)
- cmd.exe (PID: 8912)
- cmd.exe (PID: 8960)
- cmd.exe (PID: 9092)
- cmd.exe (PID: 9028)
- cmd.exe (PID: 8260)
- cmd.exe (PID: 9176)
- cmd.exe (PID: 8416)
- cmd.exe (PID: 8628)
- cmd.exe (PID: 8760)
- cmd.exe (PID: 8980)
- cmd.exe (PID: 9096)
- cmd.exe (PID: 8448)
- cmd.exe (PID: 9012)
- cmd.exe (PID: 9224)
- cmd.exe (PID: 9500)
- cmd.exe (PID: 9292)
- cmd.exe (PID: 9388)
- cmd.exe (PID: 9440)
- cmd.exe (PID: 9572)
- cmd.exe (PID: 9660)
- cmd.exe (PID: 9948)
- cmd.exe (PID: 10092)
- cmd.exe (PID: 10044)
- cmd.exe (PID: 10172)
- cmd.exe (PID: 8760)
- cmd.exe (PID: 9304)
- cmd.exe (PID: 9736)
- cmd.exe (PID: 9828)
- cmd.exe (PID: 9896)
- cmd.exe (PID: 10080)
- cmd.exe (PID: 9836)
- cmd.exe (PID: 9304)
- cmd.exe (PID: 10060)
- cmd.exe (PID: 9512)
- cmd.exe (PID: 10280)
- cmd.exe (PID: 10348)
- cmd.exe (PID: 9512)
- cmd.exe (PID: 9688)
- cmd.exe (PID: 9220)
- cmd.exe (PID: 10424)
- cmd.exe (PID: 10476)
- cmd.exe (PID: 10584)
- cmd.exe (PID: 10644)
- cmd.exe (PID: 10784)
- cmd.exe (PID: 10740)
- cmd.exe (PID: 10940)
- cmd.exe (PID: 10876)
- cmd.exe (PID: 11228)
- cmd.exe (PID: 10584)
- cmd.exe (PID: 10992)
- cmd.exe (PID: 11096)
- cmd.exe (PID: 11136)
- cmd.exe (PID: 10028)
- cmd.exe (PID: 10348)
- cmd.exe (PID: 10596)
- cmd.exe (PID: 10944)
- cmd.exe (PID: 11148)
- cmd.exe (PID: 10672)
Process drops legitimate windows executable
- VIRUS.exe (PID: 7512)
The process drops C-runtime libraries
- VIRUS.exe (PID: 7512)
Process drops python dynamic module
- VIRUS.exe (PID: 7512)
Loads Python modules
- VIRUS.exe (PID: 7580)
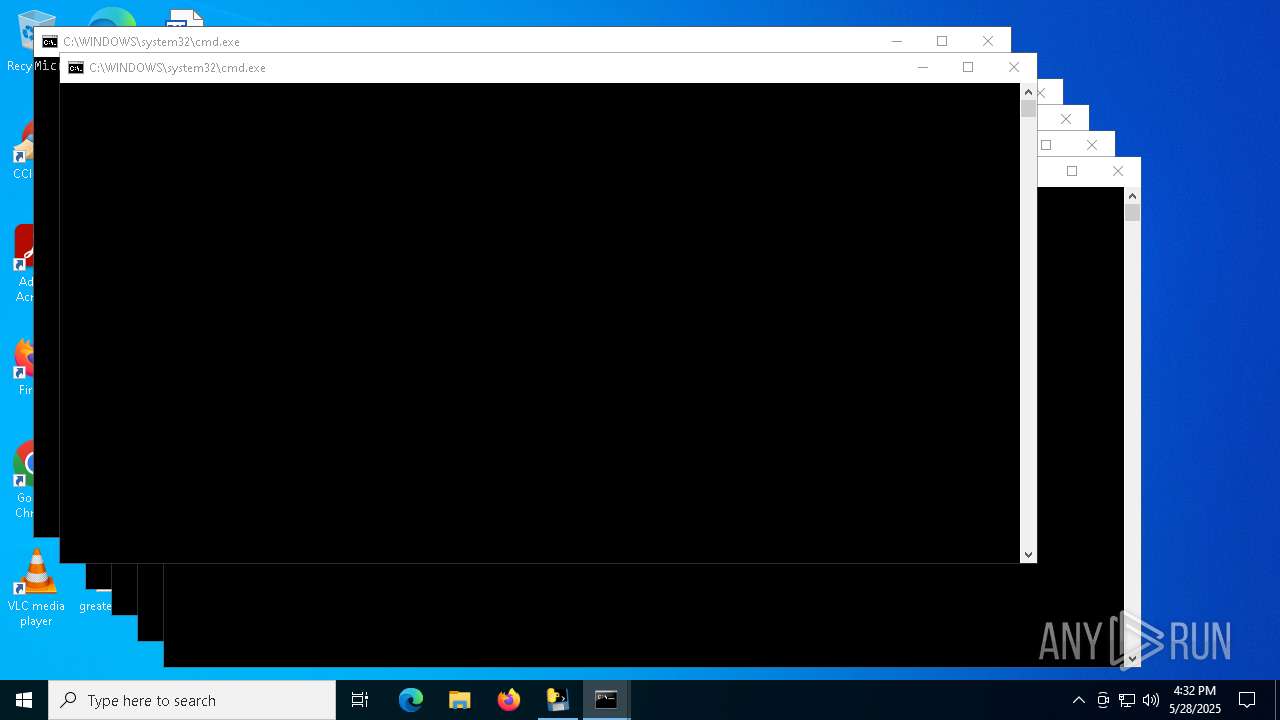
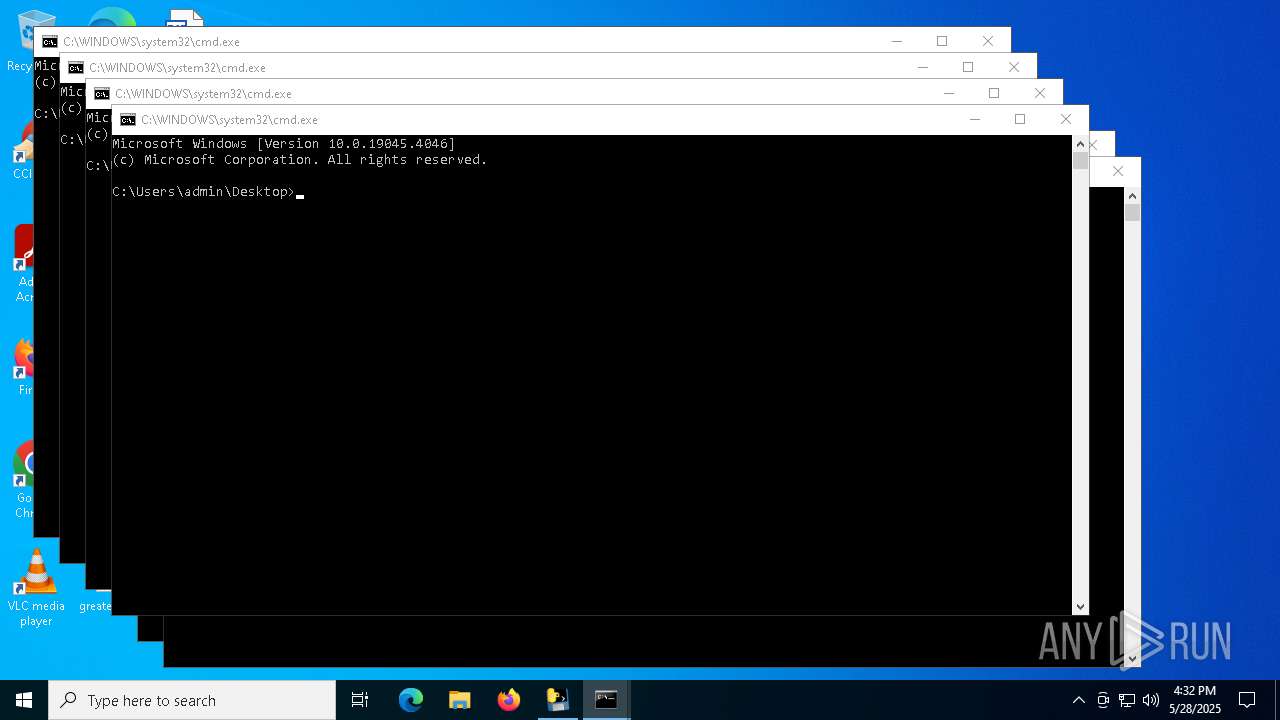
Starts CMD.EXE for commands execution
- VIRUS.exe (PID: 7580)
- cmd.exe (PID: 7604)
- cmd.exe (PID: 7648)
- cmd.exe (PID: 7700)
- cmd.exe (PID: 7776)
- cmd.exe (PID: 7860)
- cmd.exe (PID: 7928)
- cmd.exe (PID: 8064)
- cmd.exe (PID: 7984)
- cmd.exe (PID: 7196)
- cmd.exe (PID: 8128)
- cmd.exe (PID: 7216)
- cmd.exe (PID: 6944)
- cmd.exe (PID: 5556)
- cmd.exe (PID: 4040)
- cmd.exe (PID: 1228)
- cmd.exe (PID: 5640)
- cmd.exe (PID: 7176)
- cmd.exe (PID: 5072)
- cmd.exe (PID: 7272)
- cmd.exe (PID: 5056)
- cmd.exe (PID: 8040)
- cmd.exe (PID: 8132)
- cmd.exe (PID: 7252)
- cmd.exe (PID: 616)
- cmd.exe (PID: 5508)
- cmd.exe (PID: 7736)
- cmd.exe (PID: 7616)
- cmd.exe (PID: 7704)
- cmd.exe (PID: 7376)
- cmd.exe (PID: 8064)
- cmd.exe (PID: 7328)
- cmd.exe (PID: 7908)
- cmd.exe (PID: 7756)
- cmd.exe (PID: 8320)
- cmd.exe (PID: 8388)
- cmd.exe (PID: 8604)
- cmd.exe (PID: 8460)
- cmd.exe (PID: 8528)
- cmd.exe (PID: 8236)
- cmd.exe (PID: 8756)
- cmd.exe (PID: 8824)
- cmd.exe (PID: 8960)
- cmd.exe (PID: 8668)
- cmd.exe (PID: 8912)
- cmd.exe (PID: 9028)
- cmd.exe (PID: 9092)
- cmd.exe (PID: 9176)
- cmd.exe (PID: 8260)
- cmd.exe (PID: 8416)
- cmd.exe (PID: 8628)
- cmd.exe (PID: 8760)
- cmd.exe (PID: 8980)
- cmd.exe (PID: 9096)
- cmd.exe (PID: 8448)
- cmd.exe (PID: 9012)
- cmd.exe (PID: 9292)
- cmd.exe (PID: 9388)
- cmd.exe (PID: 9440)
- cmd.exe (PID: 9500)
- cmd.exe (PID: 9660)
- cmd.exe (PID: 9224)
- cmd.exe (PID: 9572)
- cmd.exe (PID: 9896)
- cmd.exe (PID: 9948)
- cmd.exe (PID: 10044)
- cmd.exe (PID: 10092)
- cmd.exe (PID: 10172)
- cmd.exe (PID: 9304)
- cmd.exe (PID: 8760)
- cmd.exe (PID: 9736)
- cmd.exe (PID: 9828)
- cmd.exe (PID: 9688)
- cmd.exe (PID: 9836)
- cmd.exe (PID: 10080)
- cmd.exe (PID: 10060)
- cmd.exe (PID: 9220)
- cmd.exe (PID: 9304)
- cmd.exe (PID: 10280)
- cmd.exe (PID: 9512)
- cmd.exe (PID: 10348)
- cmd.exe (PID: 9512)
- cmd.exe (PID: 10476)
- cmd.exe (PID: 10644)
- cmd.exe (PID: 10584)
- cmd.exe (PID: 10740)
- cmd.exe (PID: 10784)
- cmd.exe (PID: 10876)
- cmd.exe (PID: 10940)
- cmd.exe (PID: 10424)
- cmd.exe (PID: 11136)
- cmd.exe (PID: 10028)
- cmd.exe (PID: 10348)
- cmd.exe (PID: 10672)
- cmd.exe (PID: 10584)
- cmd.exe (PID: 10992)
- cmd.exe (PID: 11096)
- cmd.exe (PID: 11228)
- cmd.exe (PID: 10596)
- cmd.exe (PID: 10944)
- cmd.exe (PID: 11148)
INFO
The sample compiled with english language support
- VIRUS.exe (PID: 7512)
Reads the computer name
- VIRUS.exe (PID: 7512)
Checks supported languages
- VIRUS.exe (PID: 7512)
- VIRUS.exe (PID: 7580)
Create files in a temporary directory
- VIRUS.exe (PID: 7512)
Reads the machine GUID from the registry
- VIRUS.exe (PID: 7580)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2021:01:13 09:45:06+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14 |
| CodeSize: | 135168 |
| InitializedDataSize: | 139264 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x8914 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows command line |
Total processes
431
Monitored processes
303
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | C:\WINDOWS\system32\cmd.exe /c start | C:\Windows\System32\cmd.exe | — | VIRUS.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 660 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 672 | cmd.exe | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 960 | cmd.exe | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1056 | cmd.exe | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1228 | C:\WINDOWS\system32\cmd.exe /c start | C:\Windows\System32\cmd.exe | — | VIRUS.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2140 | cmd.exe | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2616 | cmd.exe | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4040 | C:\WINDOWS\system32\cmd.exe /c start | C:\Windows\System32\cmd.exe | — | VIRUS.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 012
Read events
6 012
Write events
0
Delete events
0
Modification events
Executable files
19
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7512 | VIRUS.exe | C:\Users\admin\AppData\Local\Temp\_MEI75122\_asyncio.pyd | executable | |
MD5:7493F806ACD8A867D90375362F8EED87 | SHA256:D1F458227ECF60D389145175FA0B61656ECAC2FB80D9BB89E04CDF273E67C543 | |||
| 7512 | VIRUS.exe | C:\Users\admin\AppData\Local\Temp\_MEI75122\_socket.pyd | executable | |
MD5:0DF2287791C20A764E6641029A882F09 | SHA256:09AB789238120DF329956278F68A683210692C9BCCCB8CD548C771E7F9711869 | |||
| 7512 | VIRUS.exe | C:\Users\admin\AppData\Local\Temp\_MEI75122\GIFT!.exe.manifest | xml | |
MD5:55C6004CE35D117C9B3EA0FECB8FC6CC | SHA256:B4CE06E42230B38E683CE736BE6B441E0A534849E6DF4F75EC93A3E8D6F6C5C8 | |||
| 7512 | VIRUS.exe | C:\Users\admin\AppData\Local\Temp\_MEI75122\_ssl.pyd | executable | |
MD5:66172F2E3A46D2A0F04204D8F83C2B1E | SHA256:2B16154826A417C41CDA72190B0CBCF0C05C6E6FE44BF06E680A407138402C01 | |||
| 7512 | VIRUS.exe | C:\Users\admin\AppData\Local\Temp\_MEI75122\VCRUNTIME140.dll | executable | |
MD5:7942BE5474A095F673582997AE3054F1 | SHA256:8EE6B49830436FF3BEC9BA89213395427B5535813930489F118721FD3D2D942C | |||
| 7512 | VIRUS.exe | C:\Users\admin\AppData\Local\Temp\_MEI75122\_bz2.pyd | executable | |
MD5:499462206034B6AB7D18CC208A5B67E3 | SHA256:6C2BBED242C399C4BC9B33268AFE538CF1DEA494C75C8D0DB786030A0DCC4B7E | |||
| 7512 | VIRUS.exe | C:\Users\admin\AppData\Local\Temp\_MEI75122\_ctypes.pyd | executable | |
MD5:B74F6285A790FFD7E9EC26E3AB4CA8DF | SHA256:C1E3E9548243CA523F1941990477723F57A1052965FCCC8F10C2CFAE414A6B8A | |||
| 7512 | VIRUS.exe | C:\Users\admin\AppData\Local\Temp\_MEI75122\_hashlib.pyd | executable | |
MD5:60F420A9A606E2C95168D25D2C1AC12E | SHA256:8AA7ABE0A92A89ADF821E4EB783AD254A19858E62D99F80EB5872D81E8B3541C | |||
| 7512 | VIRUS.exe | C:\Users\admin\AppData\Local\Temp\_MEI75122\_decimal.pyd | executable | |
MD5:56302E90BC4FB799E094987F4556FC0F | SHA256:17F43BF9552FCF8194F4B32909BEFFA4238B76866F7DD50F4B70DE799362F66C | |||
| 7512 | VIRUS.exe | C:\Users\admin\AppData\Local\Temp\_MEI75122\_queue.pyd | executable | |
MD5:34537F5B9DA004C623A61911E19CBEE5 | SHA256:A7CDEDAA58C7BA9ABA98193FCE599598D2CD35ED9C80D1AD7FC9E6182C9A25D5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
19
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.63.118.230:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
11616 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
11616 | SIHClient.exe | GET | 200 | 2.23.181.156:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.23.181.156:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5364 | RUXIMICS.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.132:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 23.63.118.230:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |