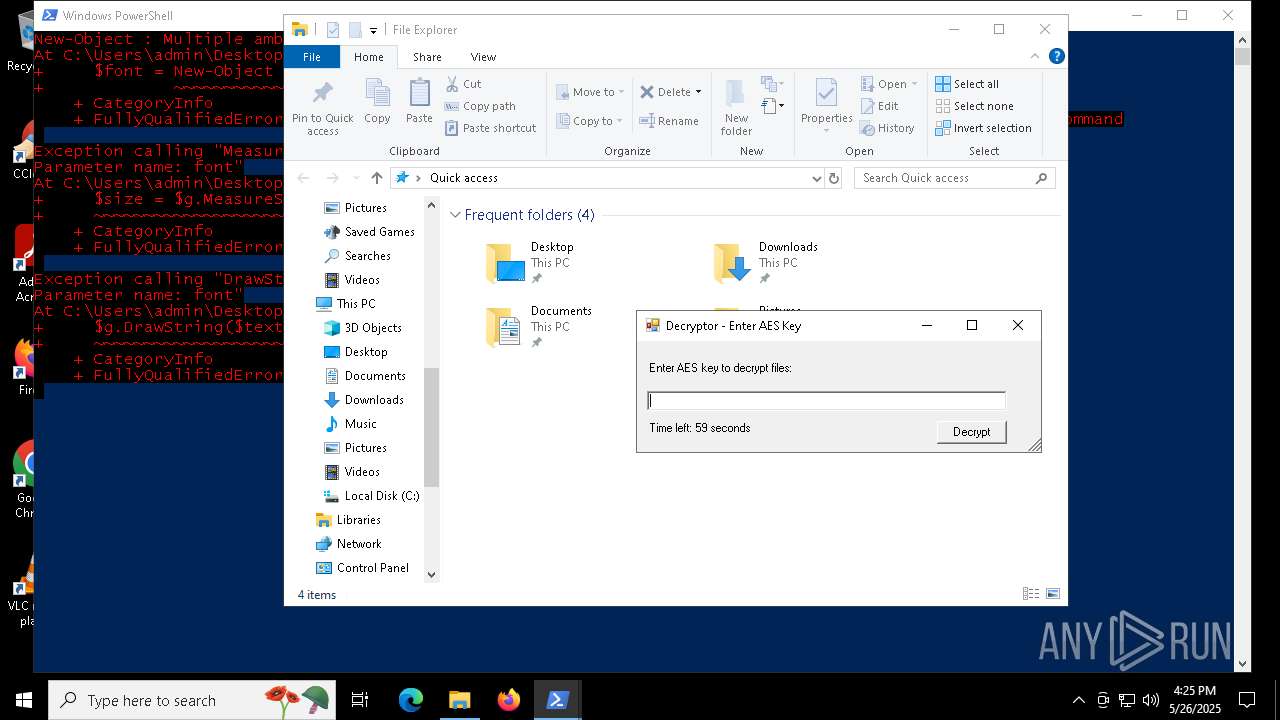
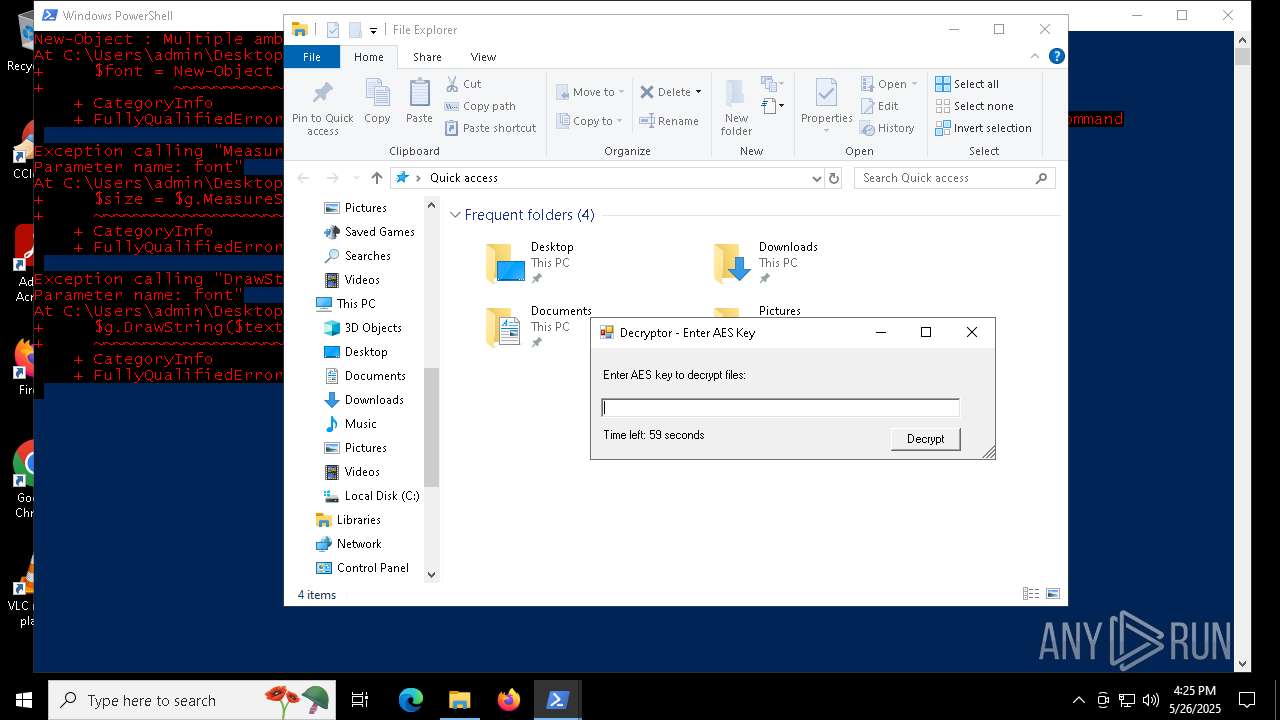
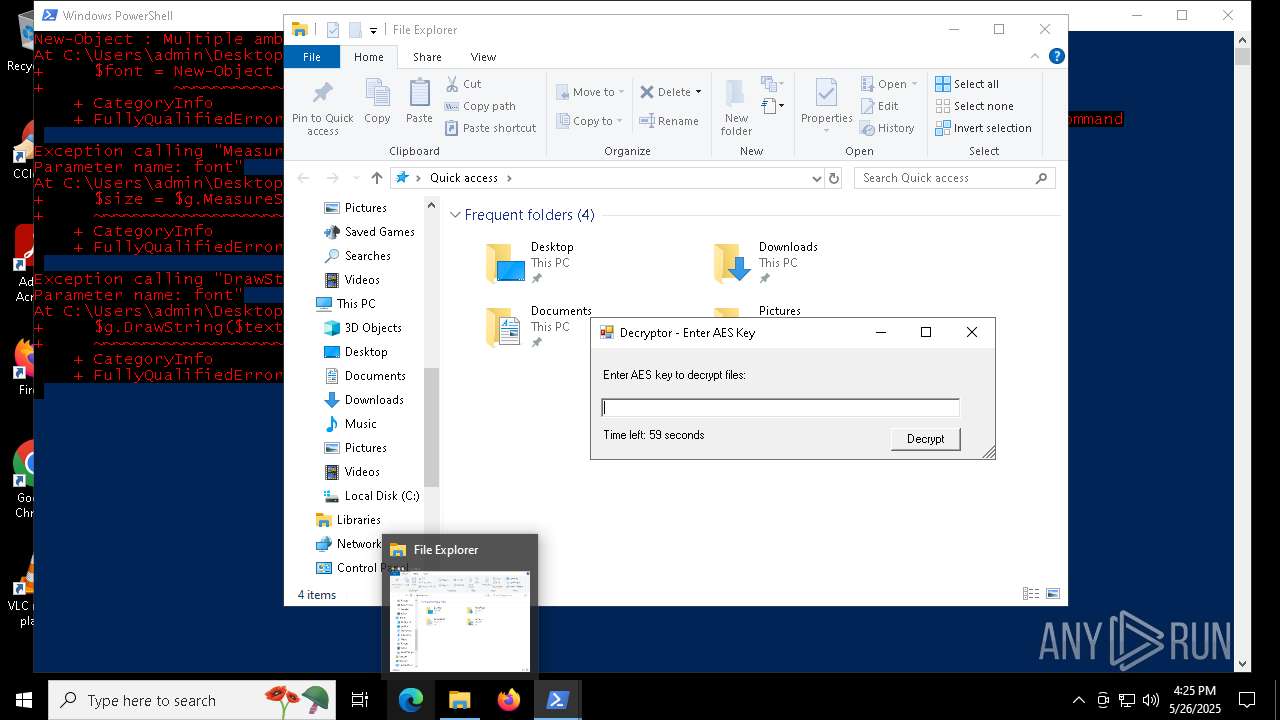
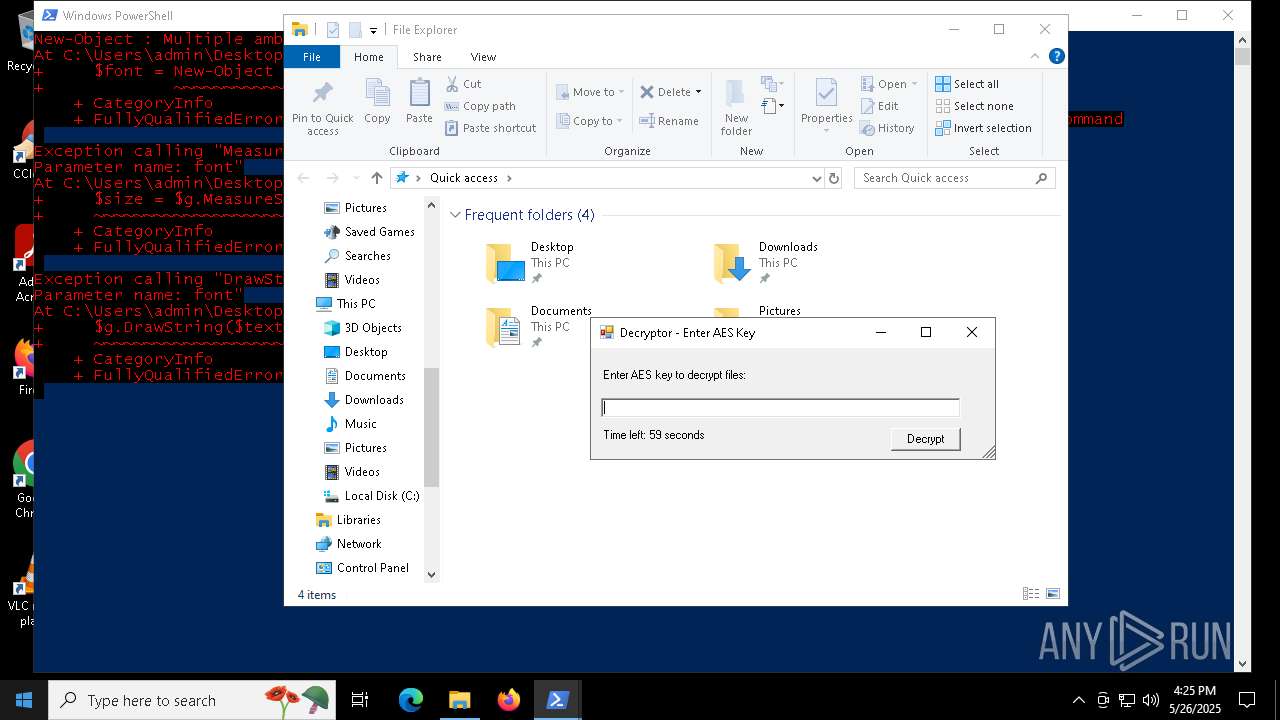
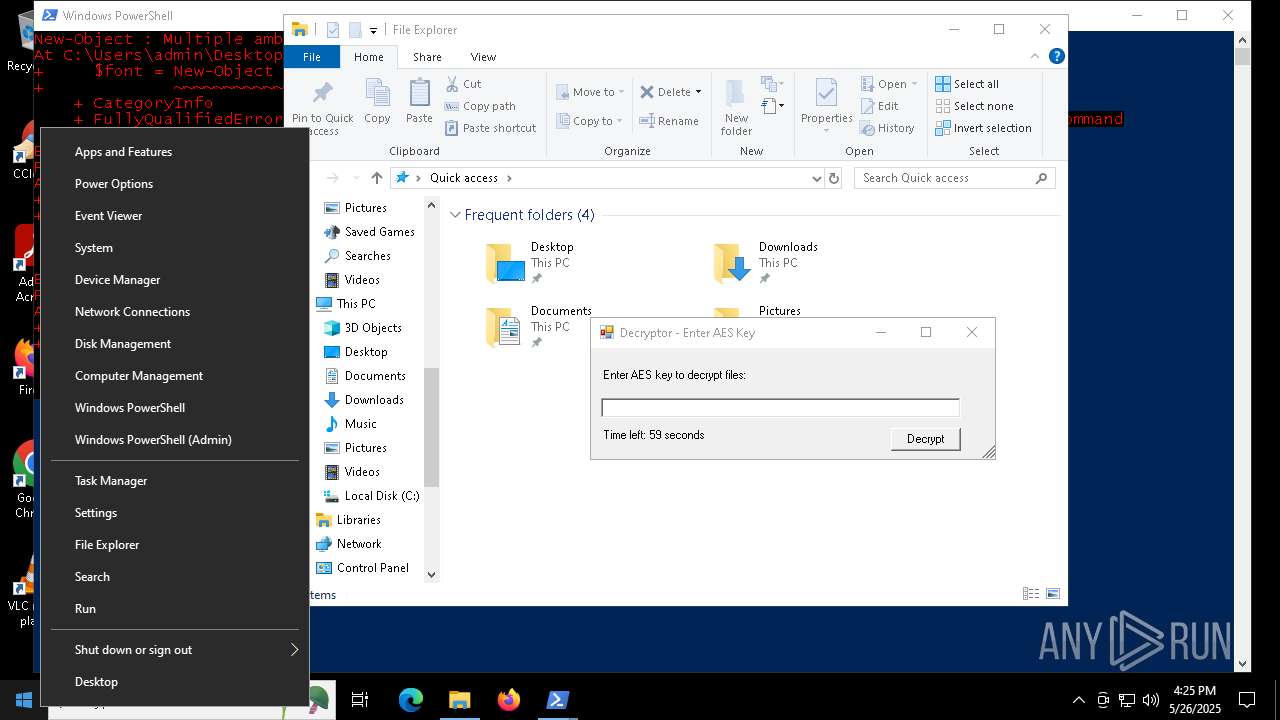
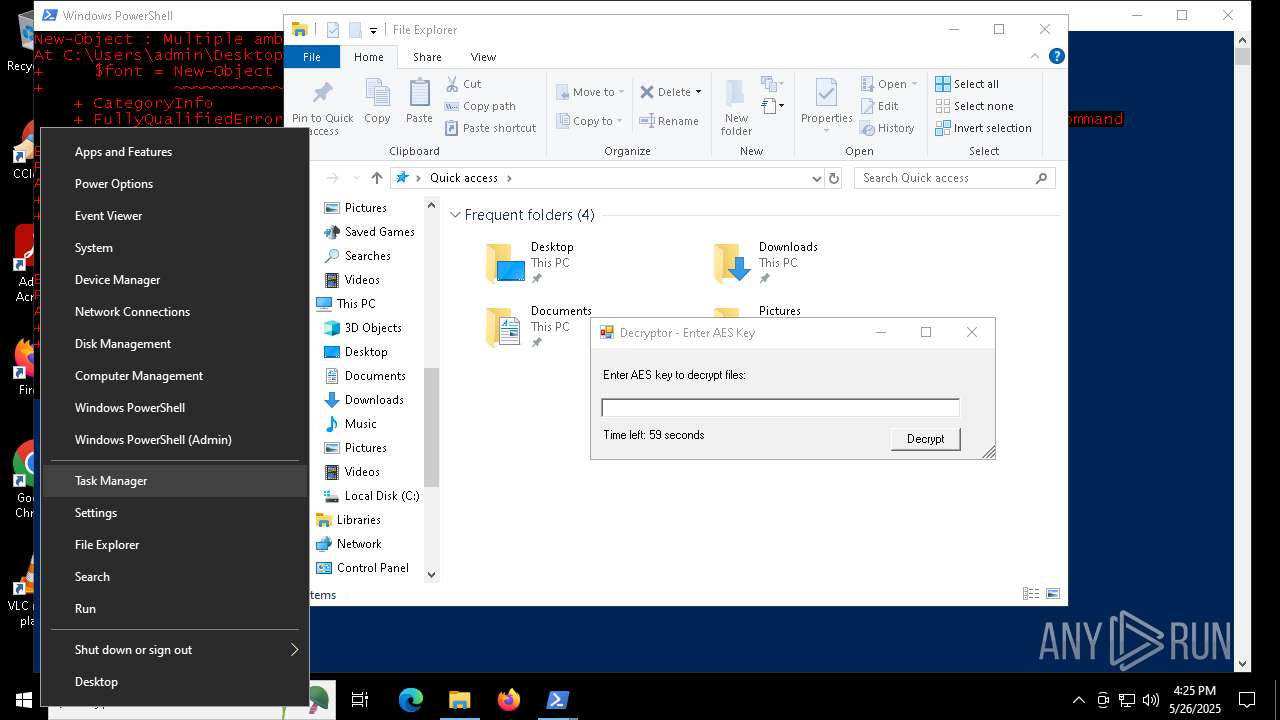
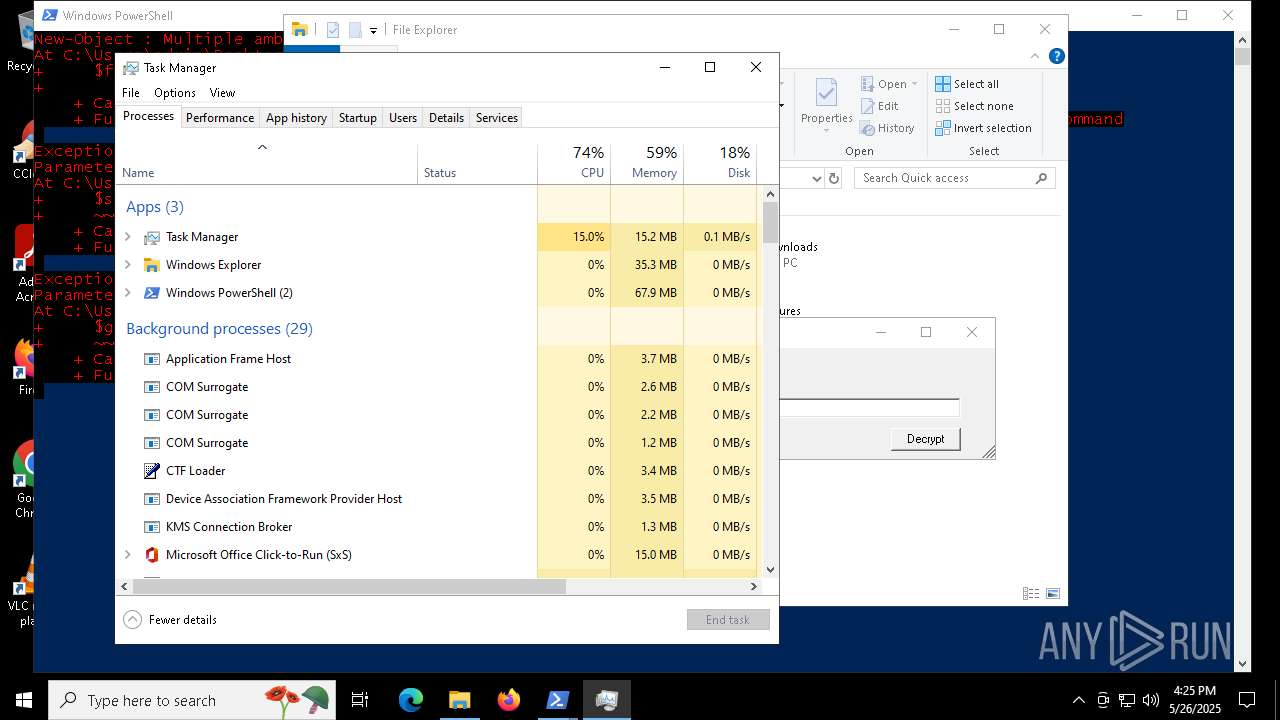
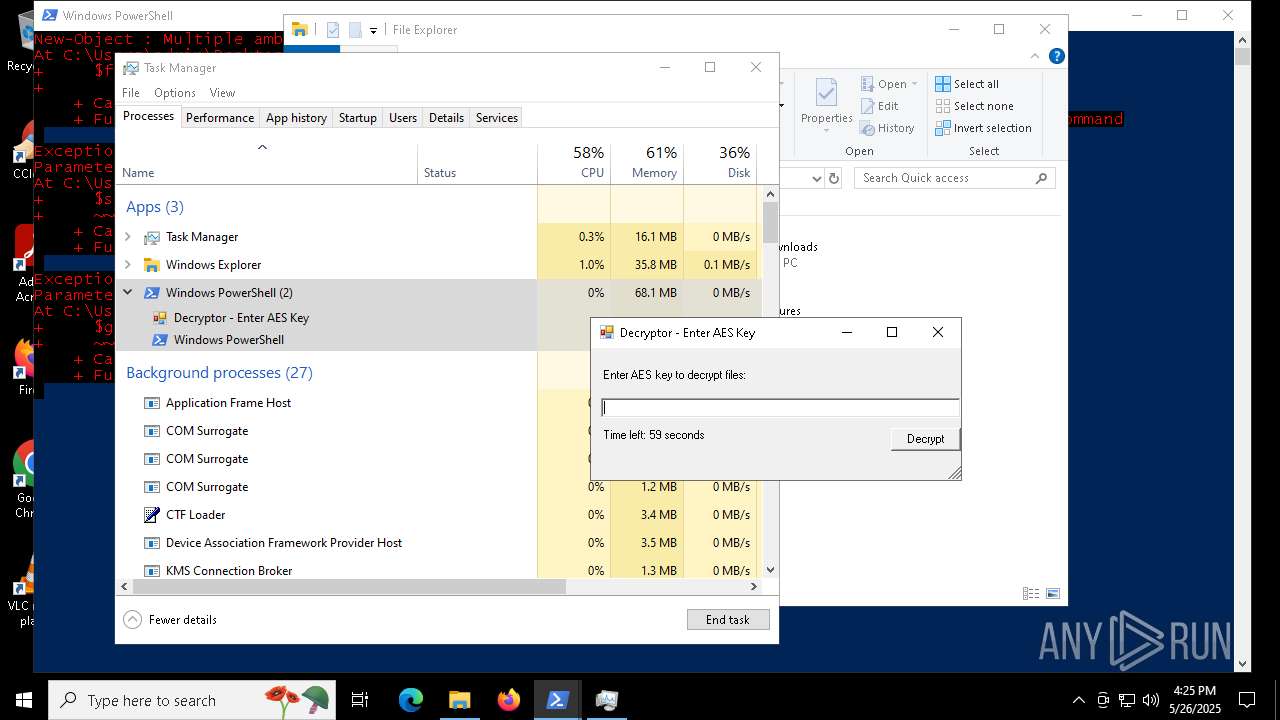
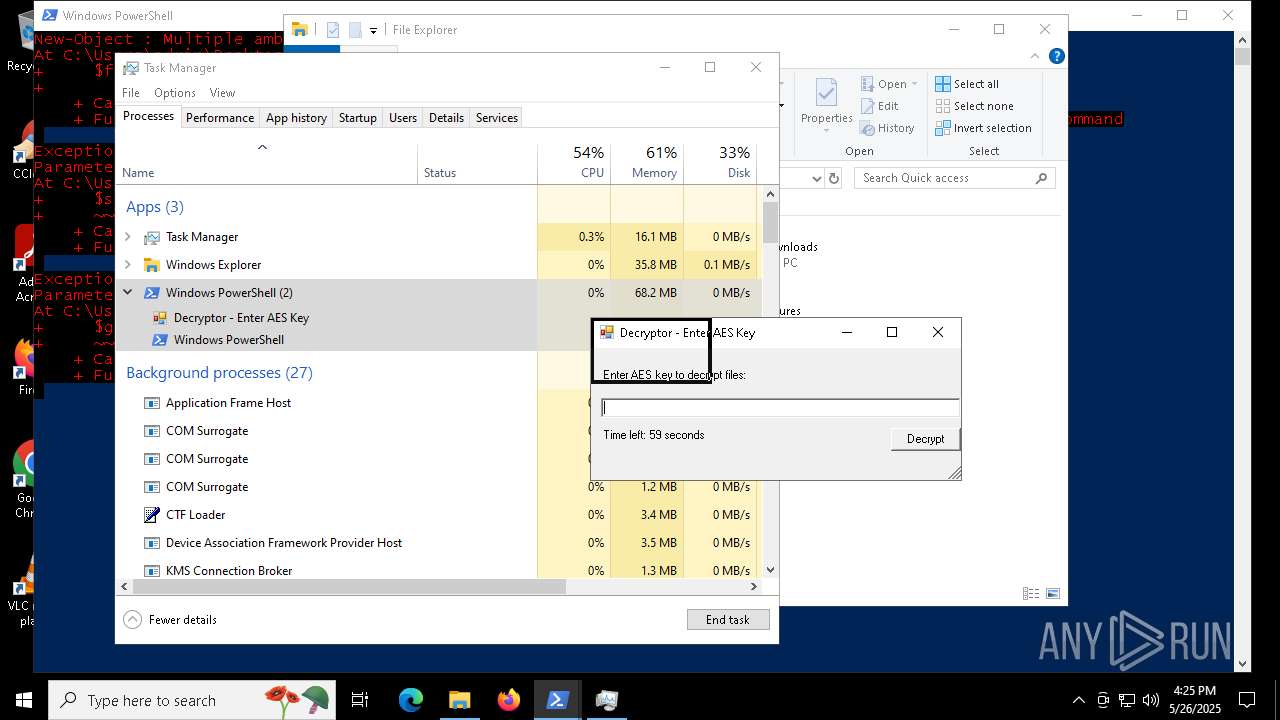
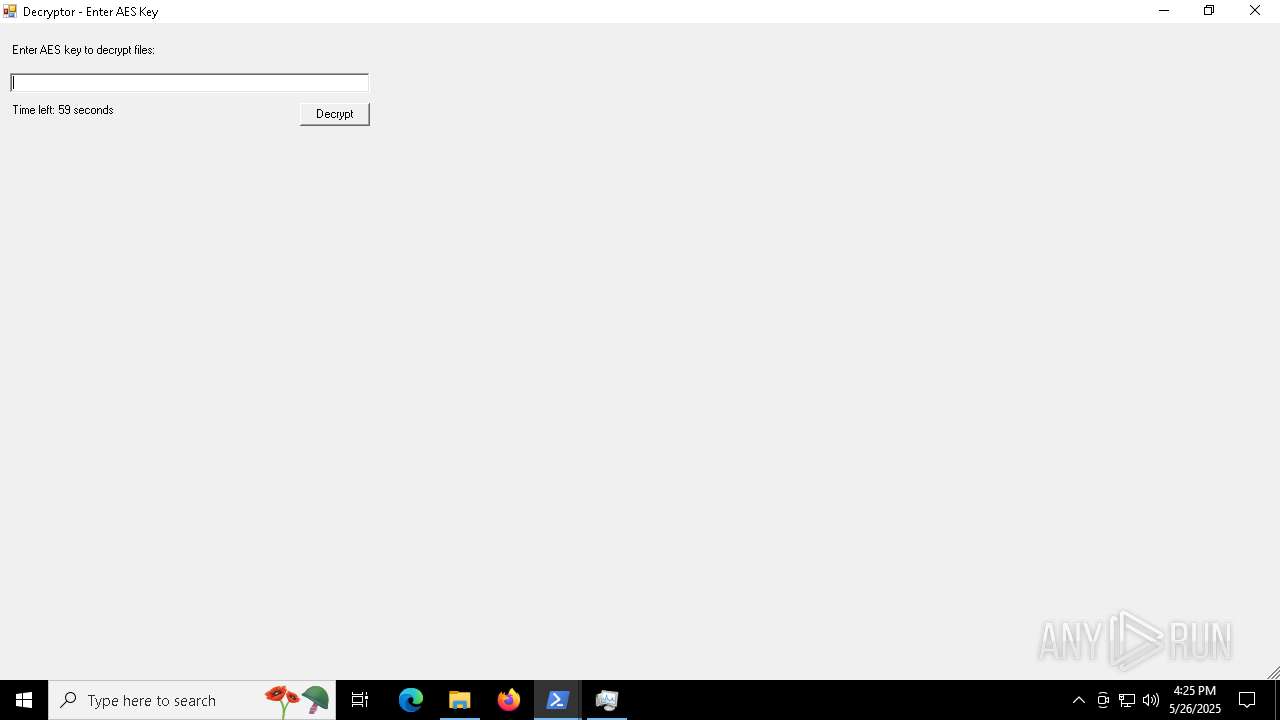
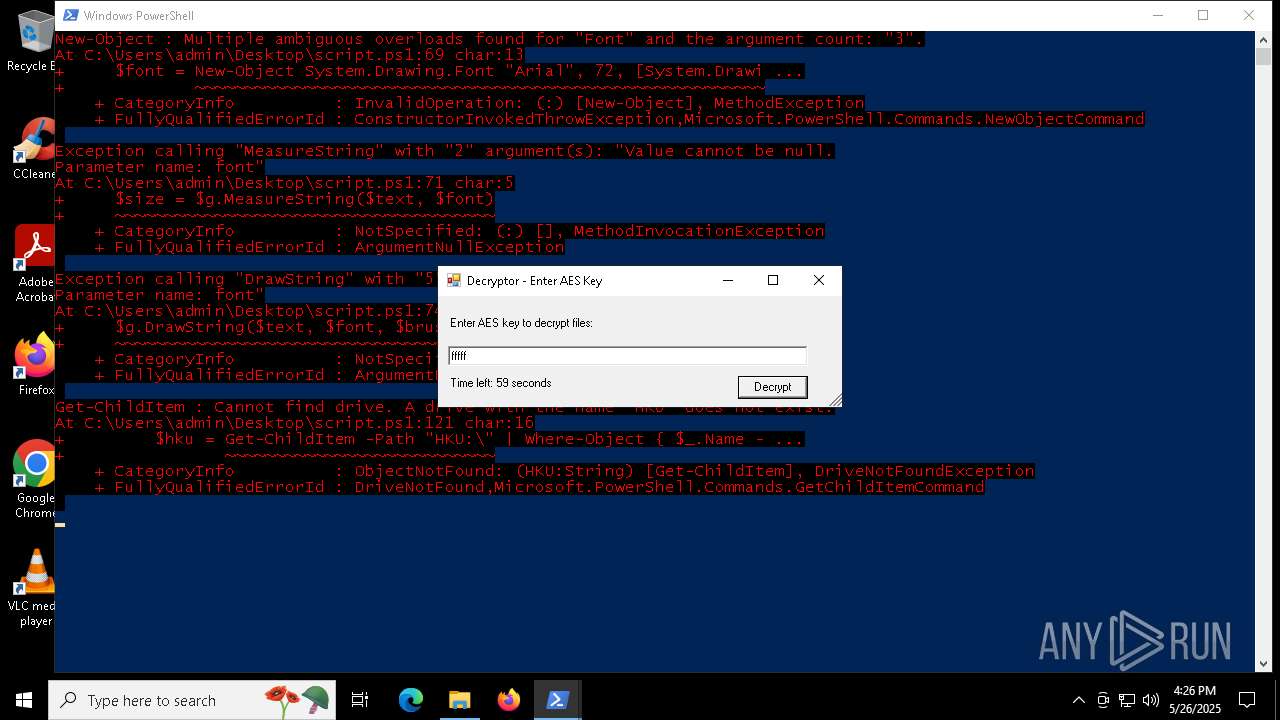
| File name: | script.ps1 |
| Full analysis: | https://app.any.run/tasks/83731c66-b47c-4eba-ae4d-512c86defc7a |
| Verdict: | Malicious activity |
| Analysis date: | May 26, 2025, 16:24:54 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with CRLF line terminators |
| MD5: | 56137D4E01C81C96FA573BF8F317498A |
| SHA1: | 59DA7E21C13CCA0469355F2B9926B8DCC6EAFCD1 |
| SHA256: | 6023118AD8D0A4EB84088003613056DACB1622D75C0E9ADB46742532B662C919 |
| SSDEEP: | 192:lzkRBZoGoNun4ZdT6+GM3C47iTrZjZFrZjV4XBXLUX2yk0ZrXIurZjZLiHXCKQ/J:lwn4Zl6ZAC47e9QR7U/DZxbiy9aU |
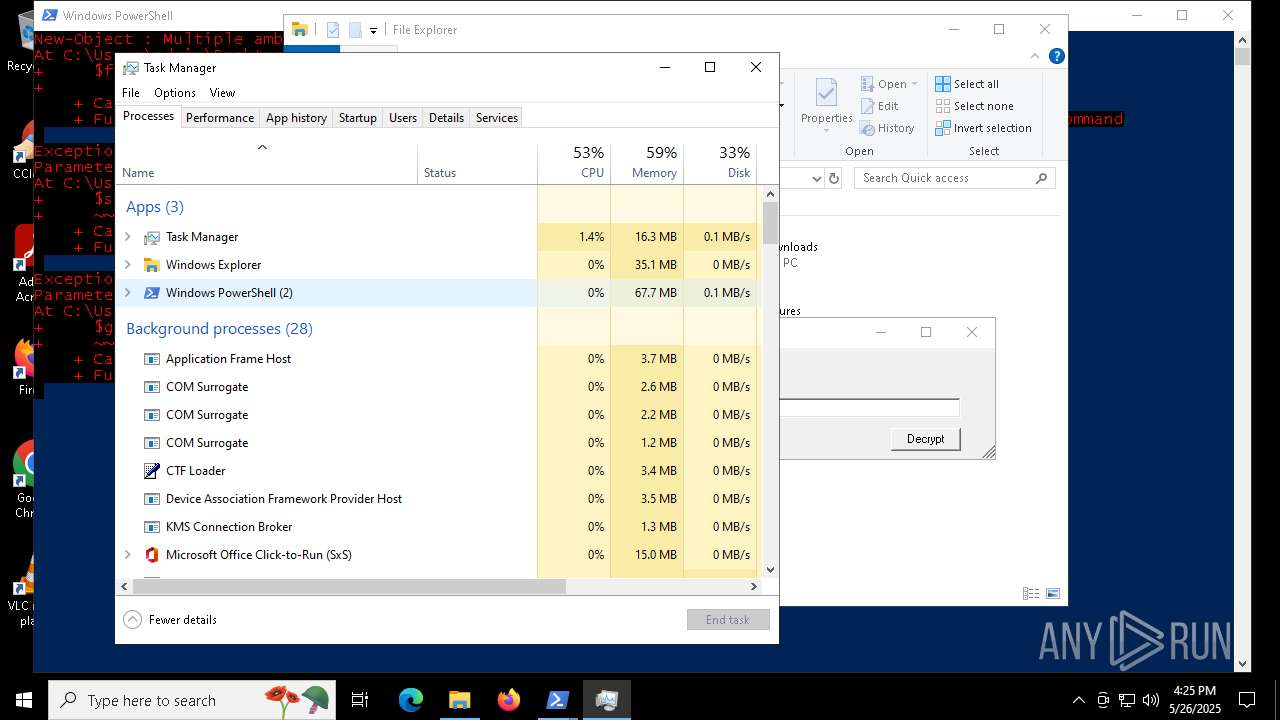
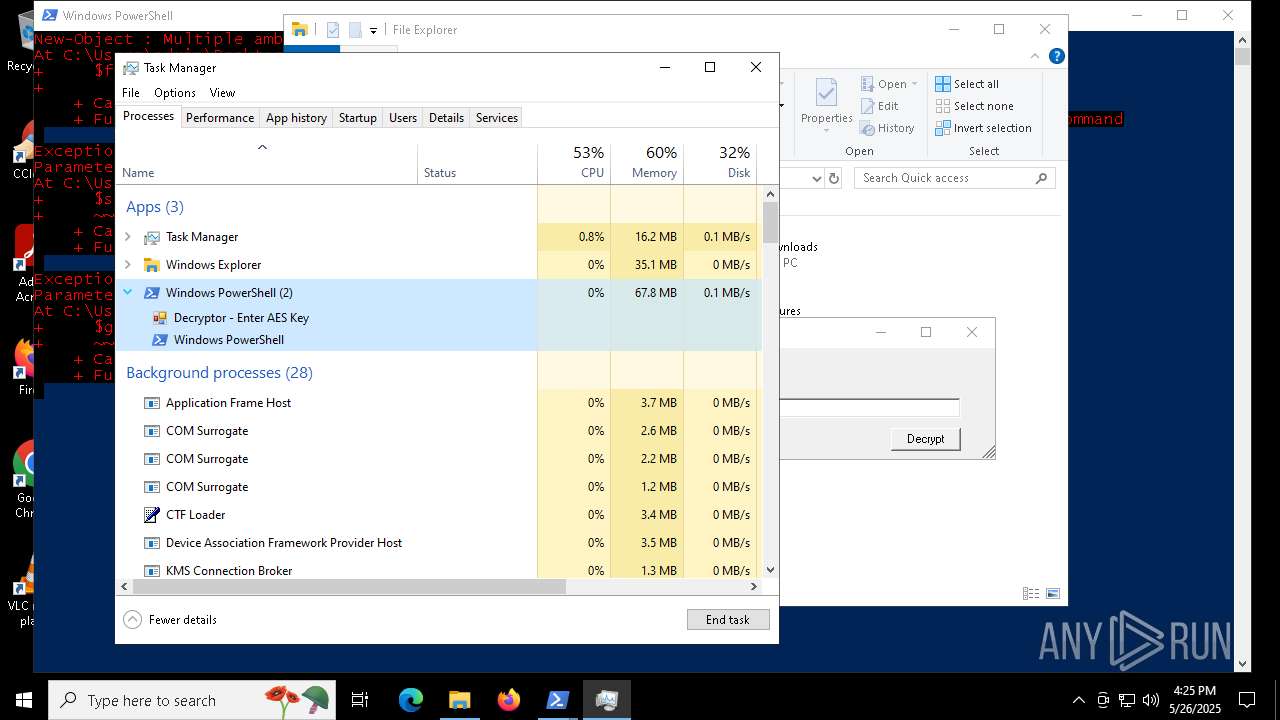
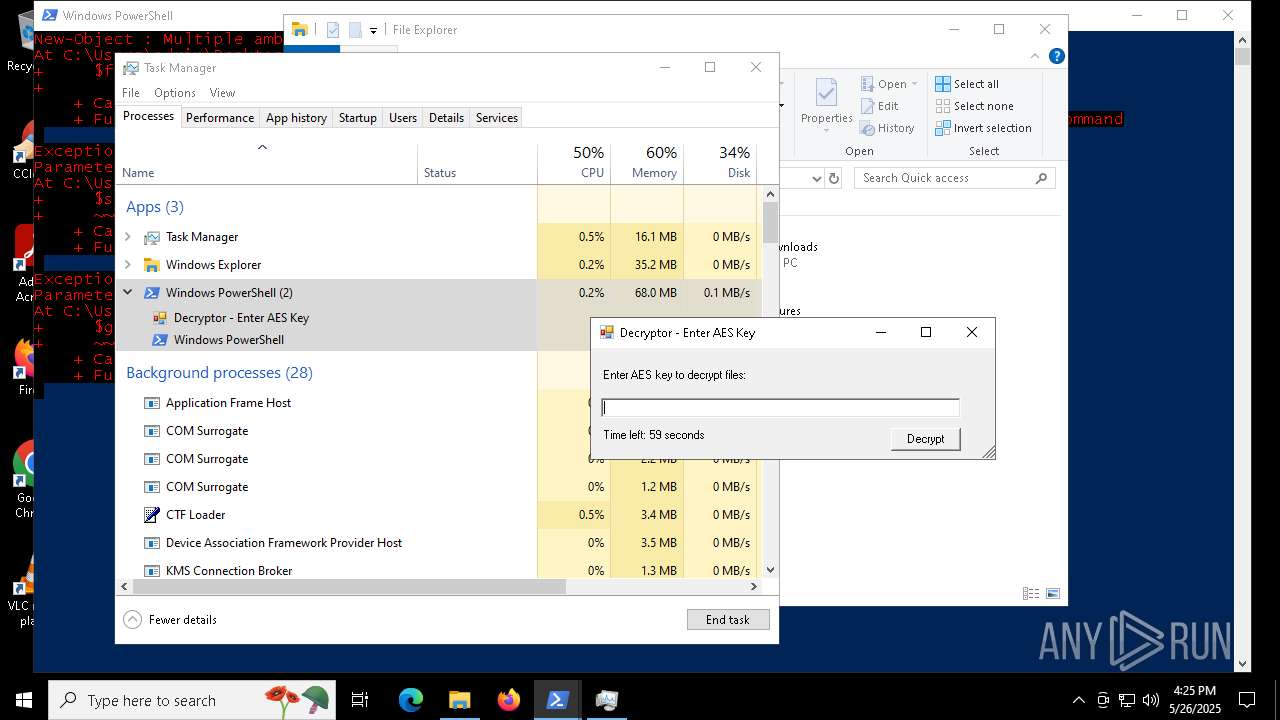
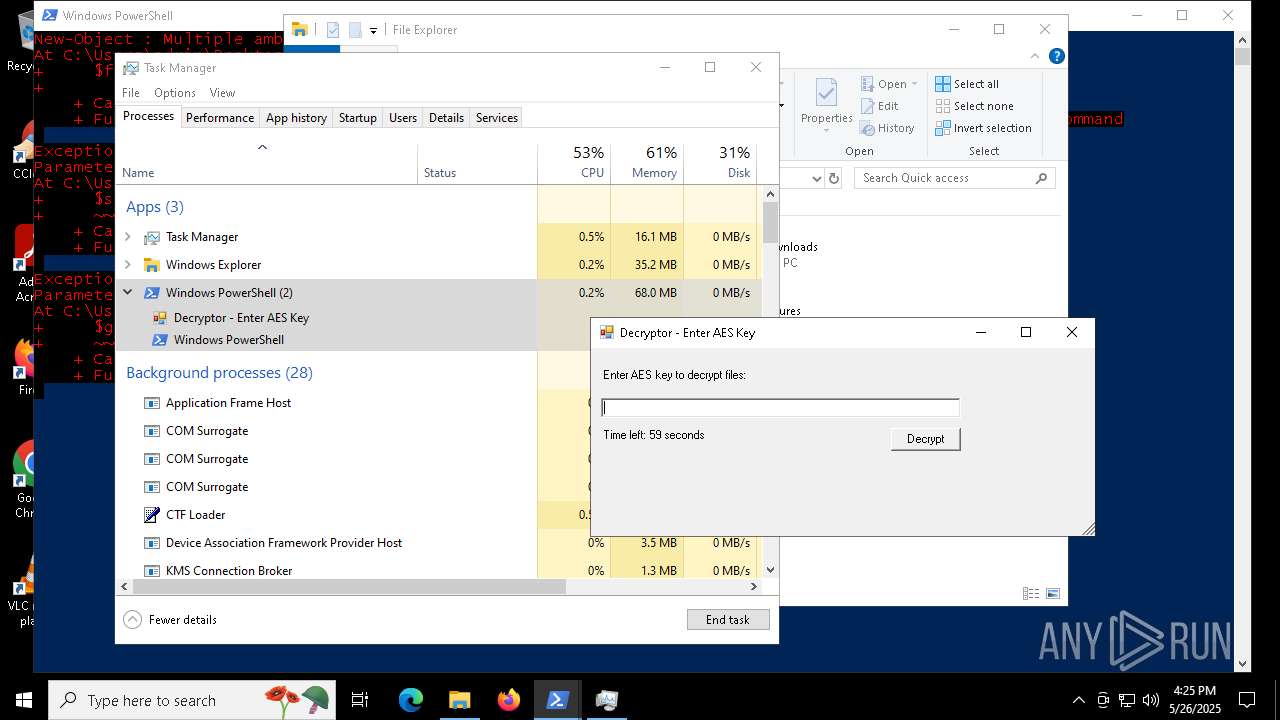
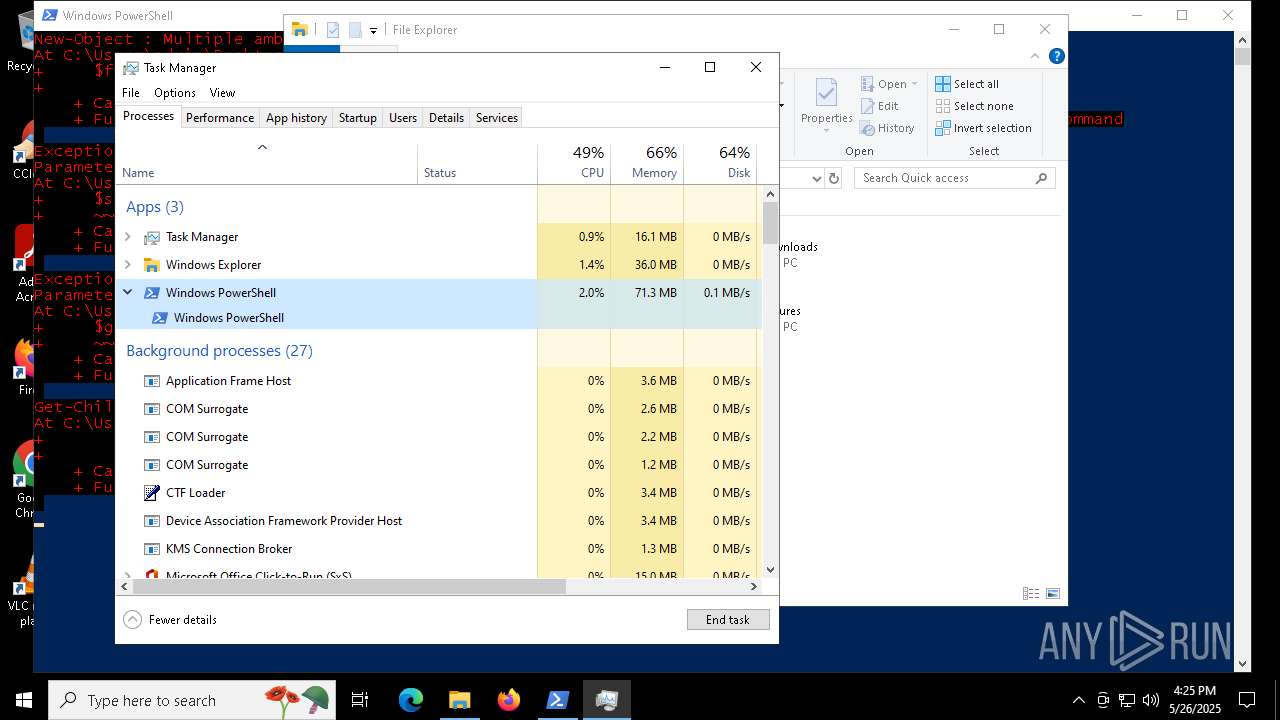
MALICIOUS
Bypass execution policy to execute commands
- powershell.exe (PID: 7352)
SUSPICIOUS
CSC.EXE is used to compile C# code
- csc.exe (PID: 7700)
Executable content was dropped or overwritten
- csc.exe (PID: 7700)
The process bypasses the loading of PowerShell profile settings
- powershell.exe (PID: 7352)
Application launched itself
- powershell.exe (PID: 7352)
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 7352)
The process hides Powershell's copyright startup banner
- powershell.exe (PID: 7352)
Reads security settings of Internet Explorer
- StartMenuExperienceHost.exe (PID: 5212)
Reads the date of Windows installation
- StartMenuExperienceHost.exe (PID: 5212)
The system shut down or reboot
- powershell.exe (PID: 7352)
INFO
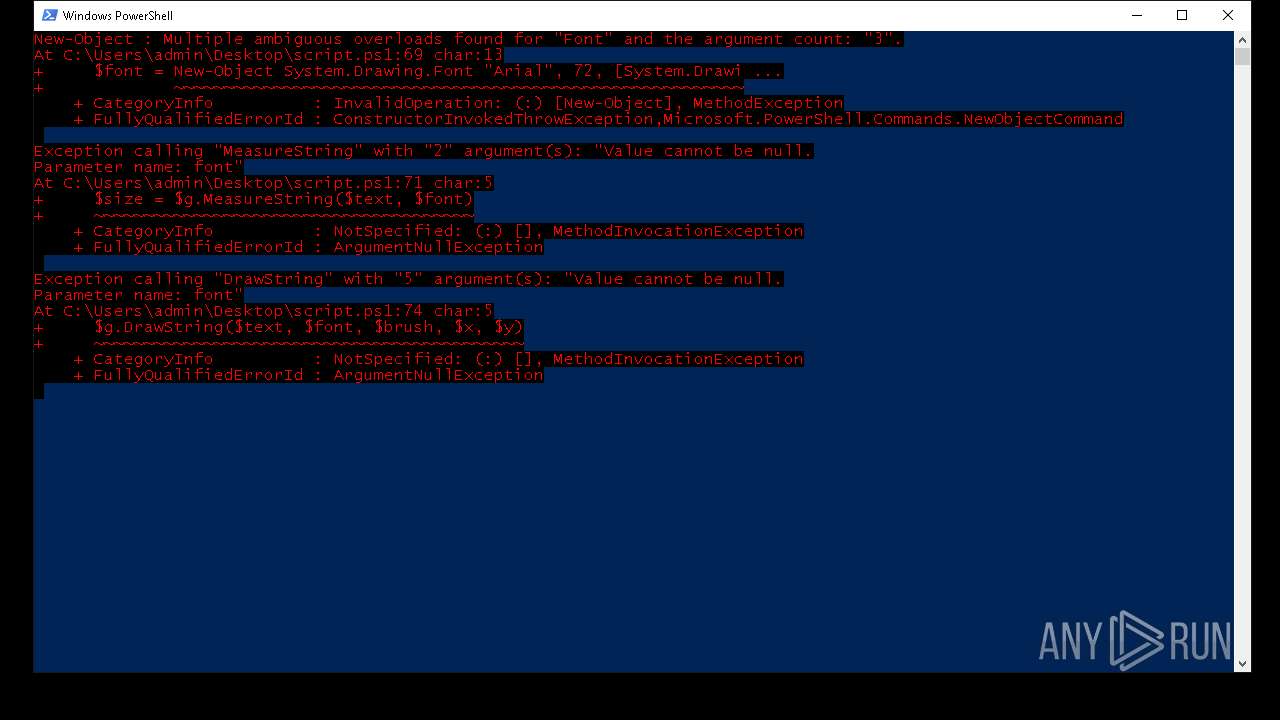
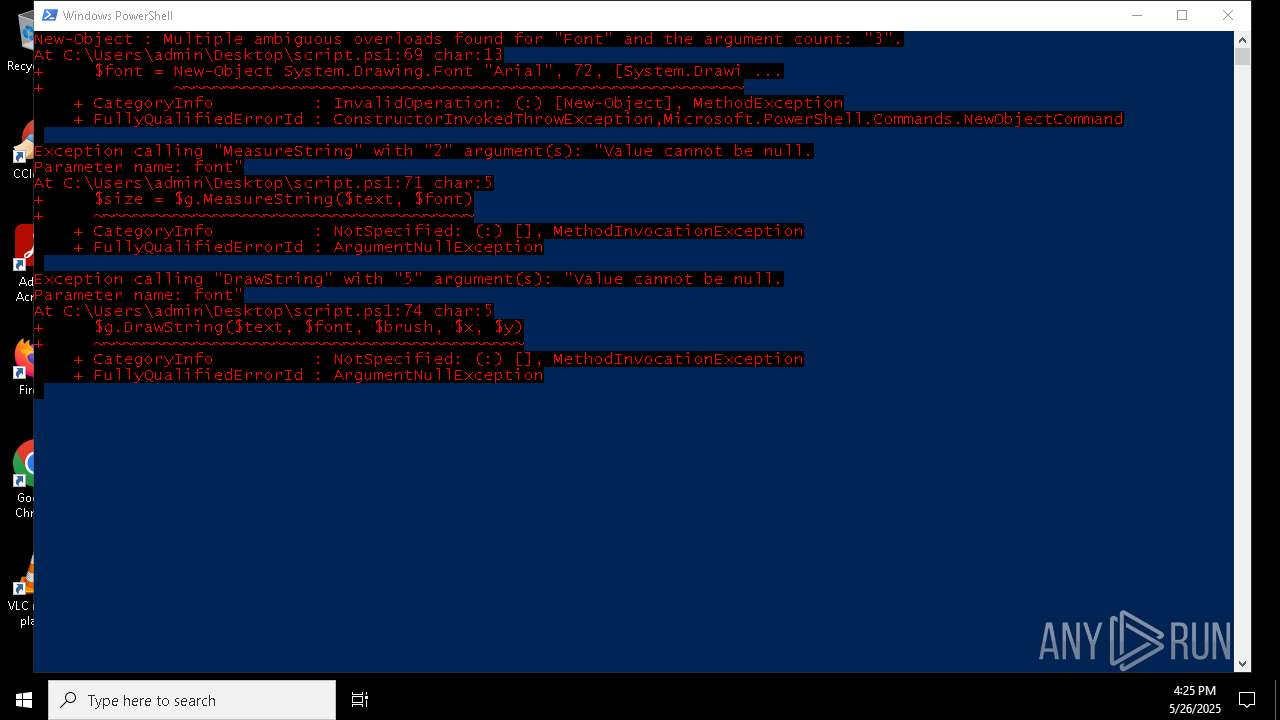
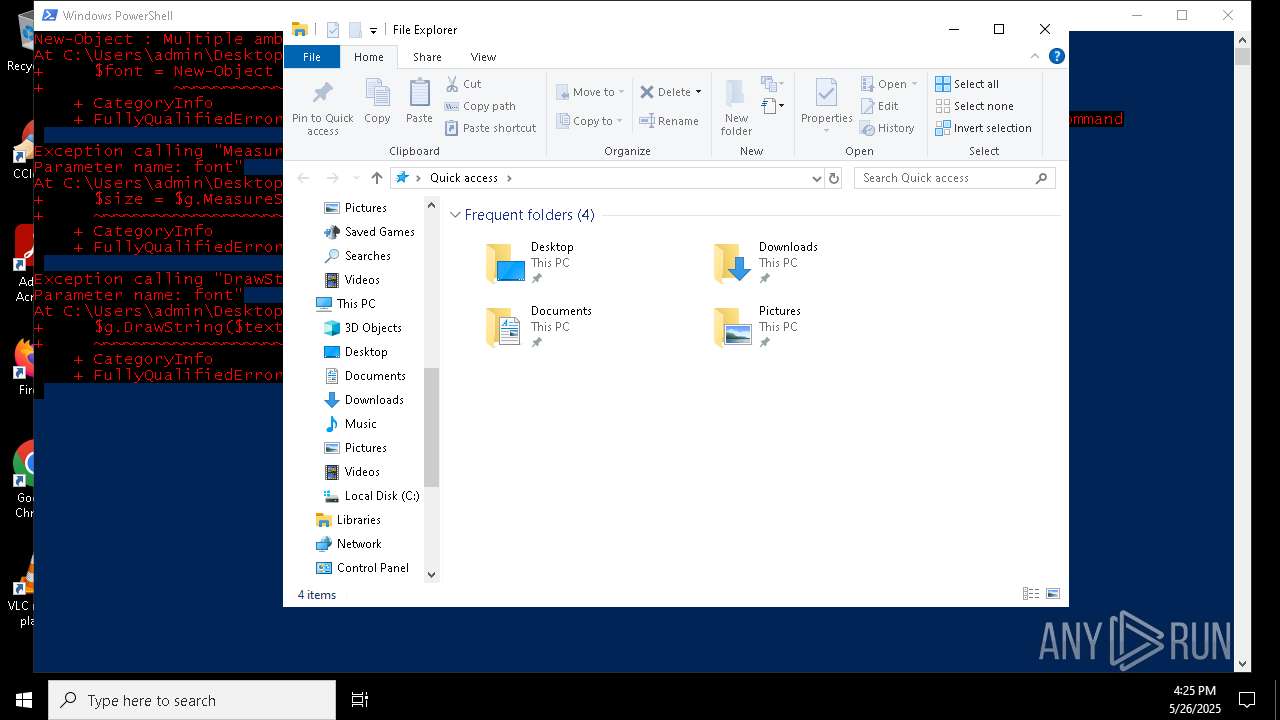
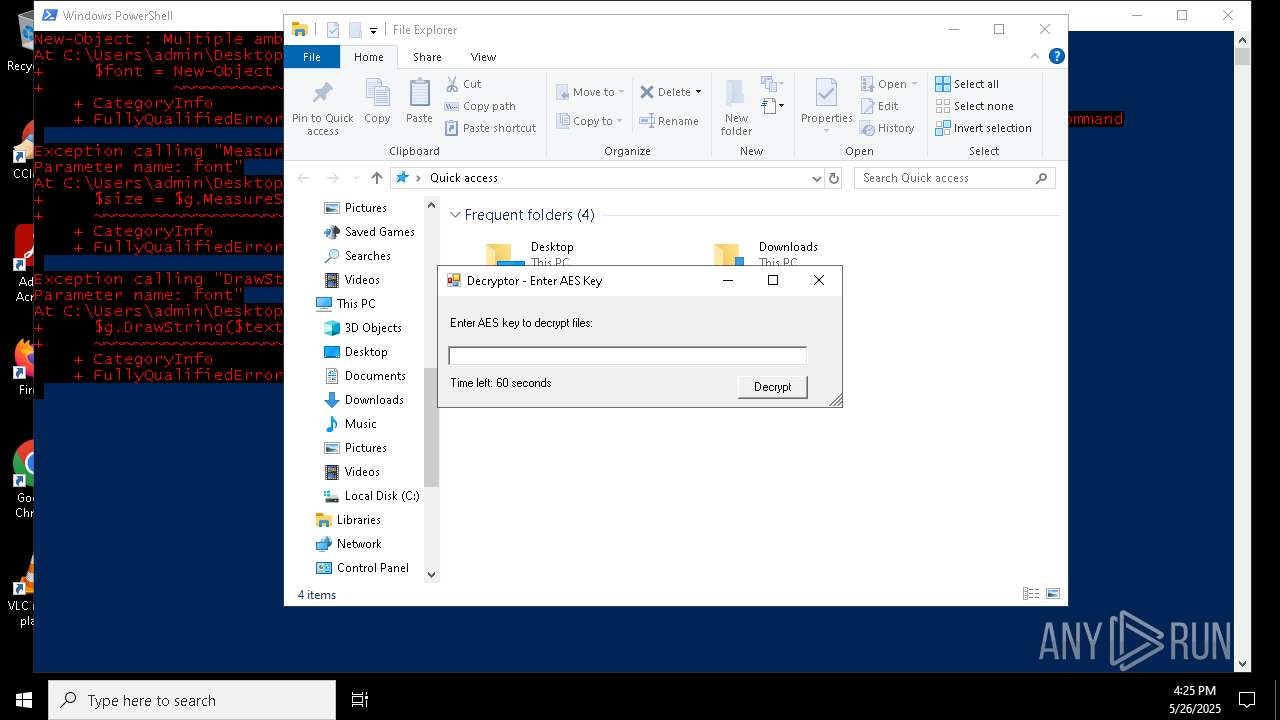
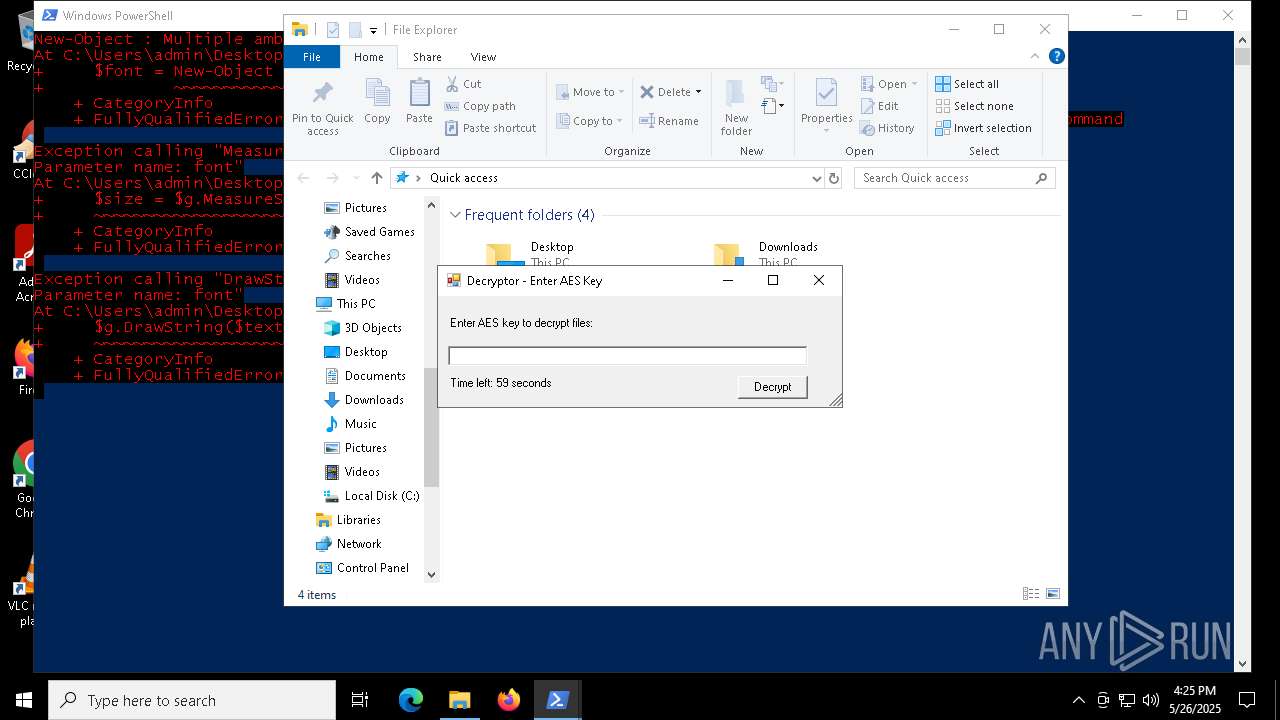
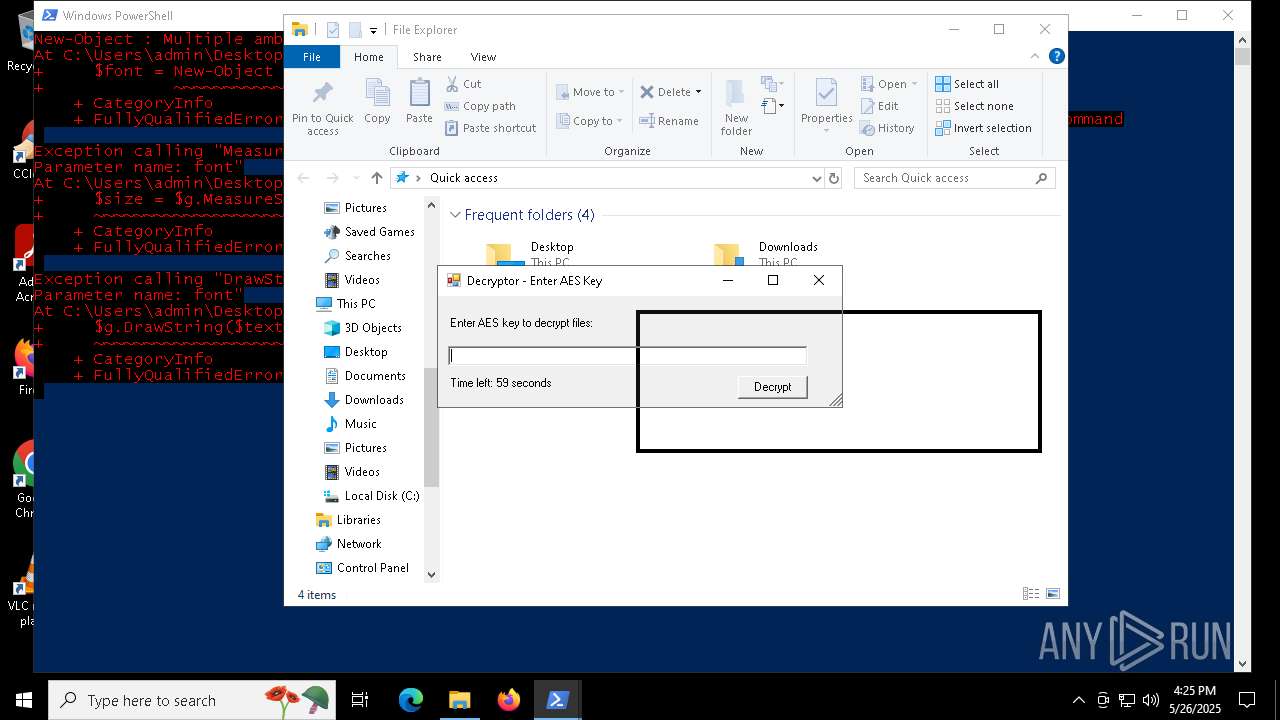
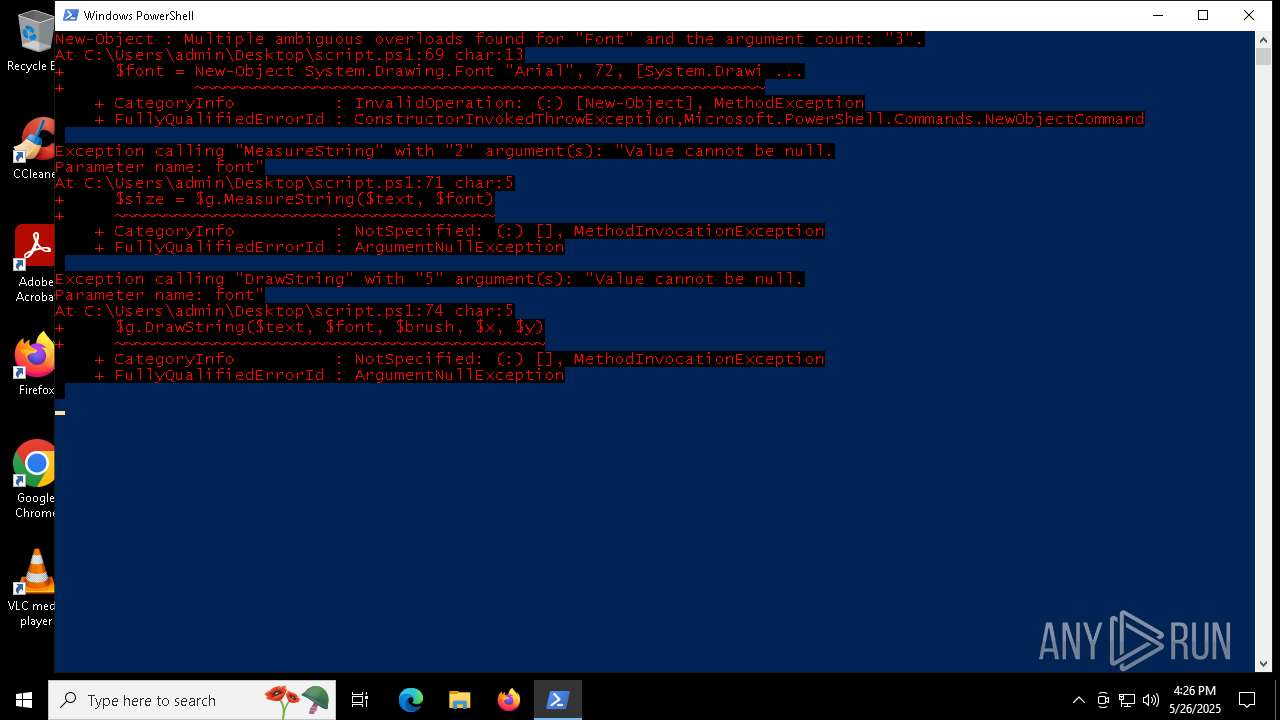
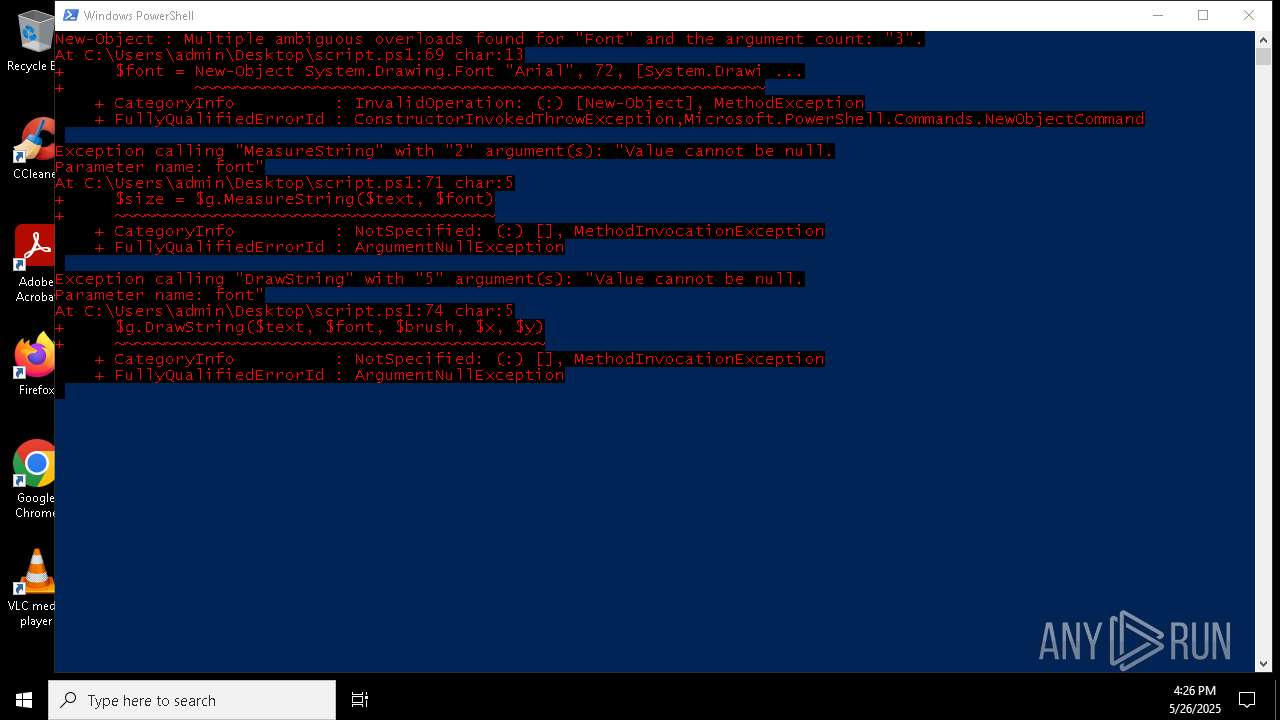
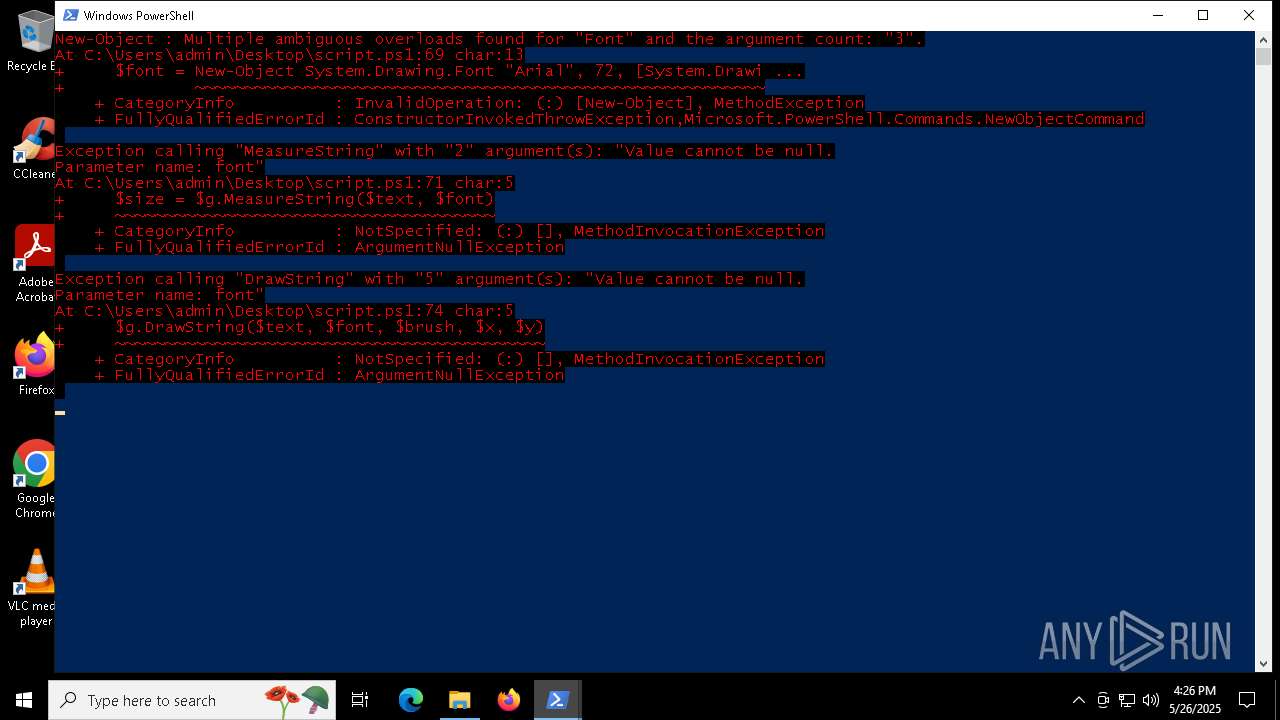
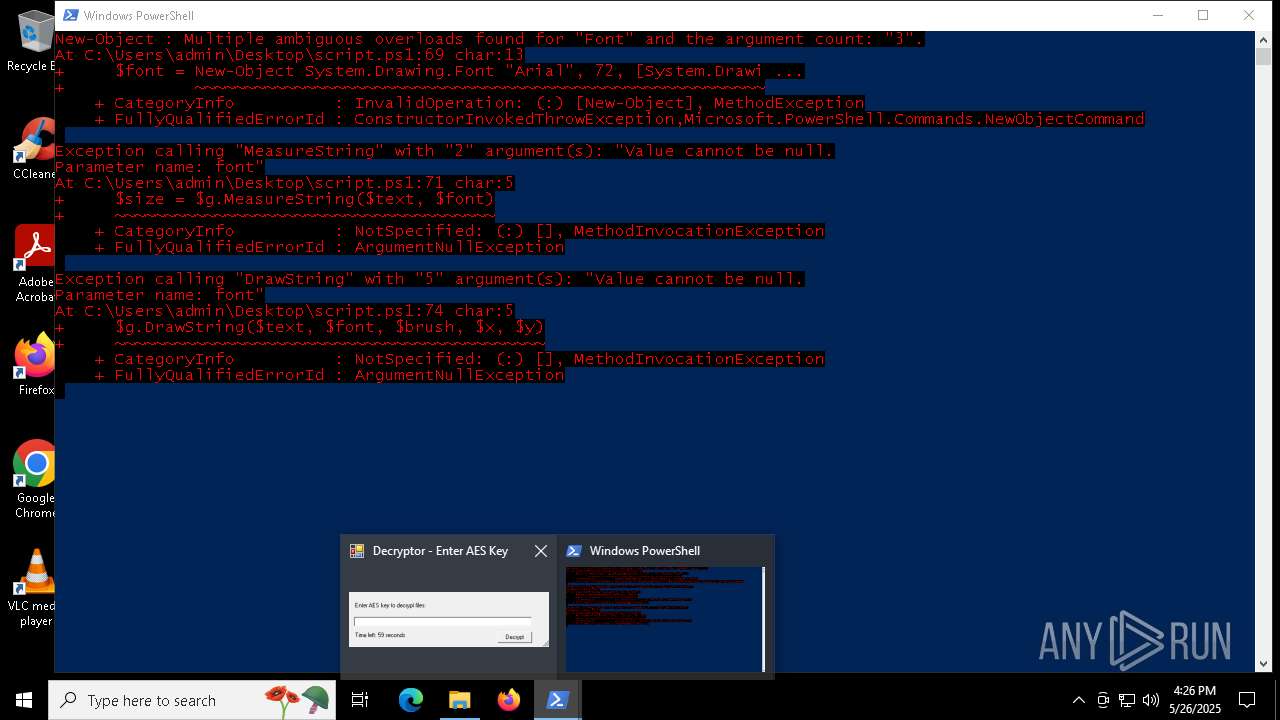
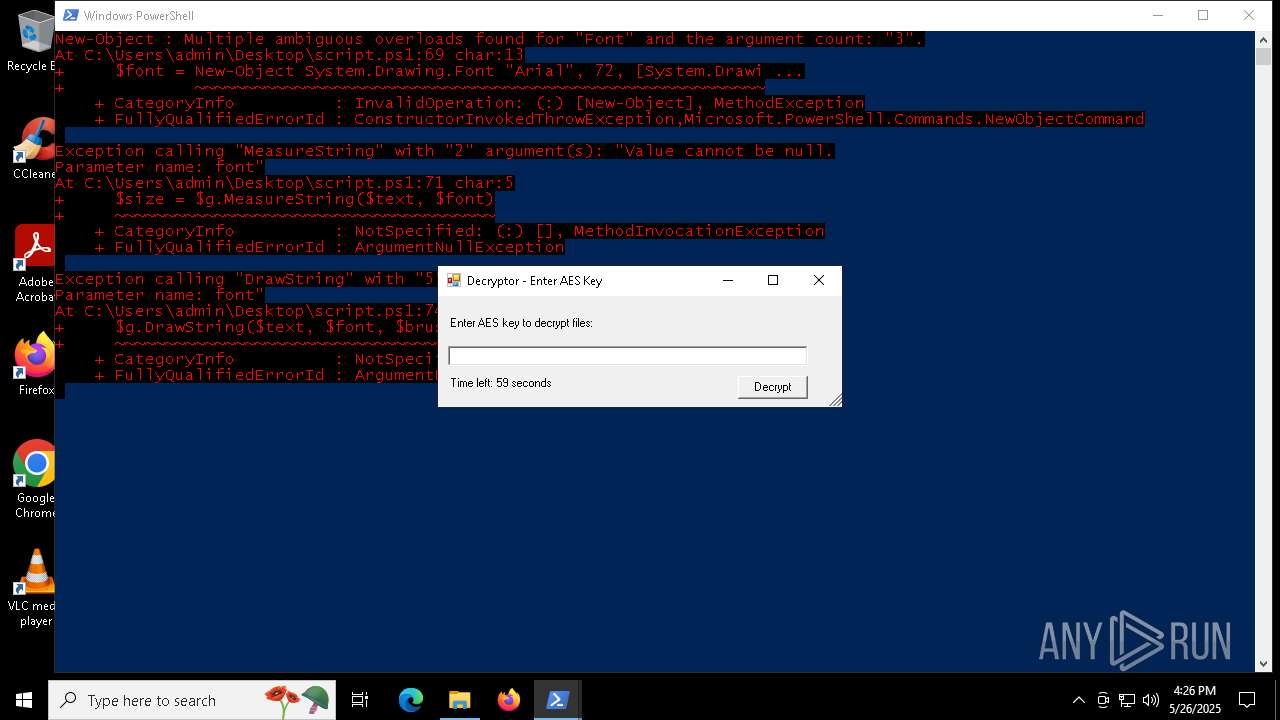
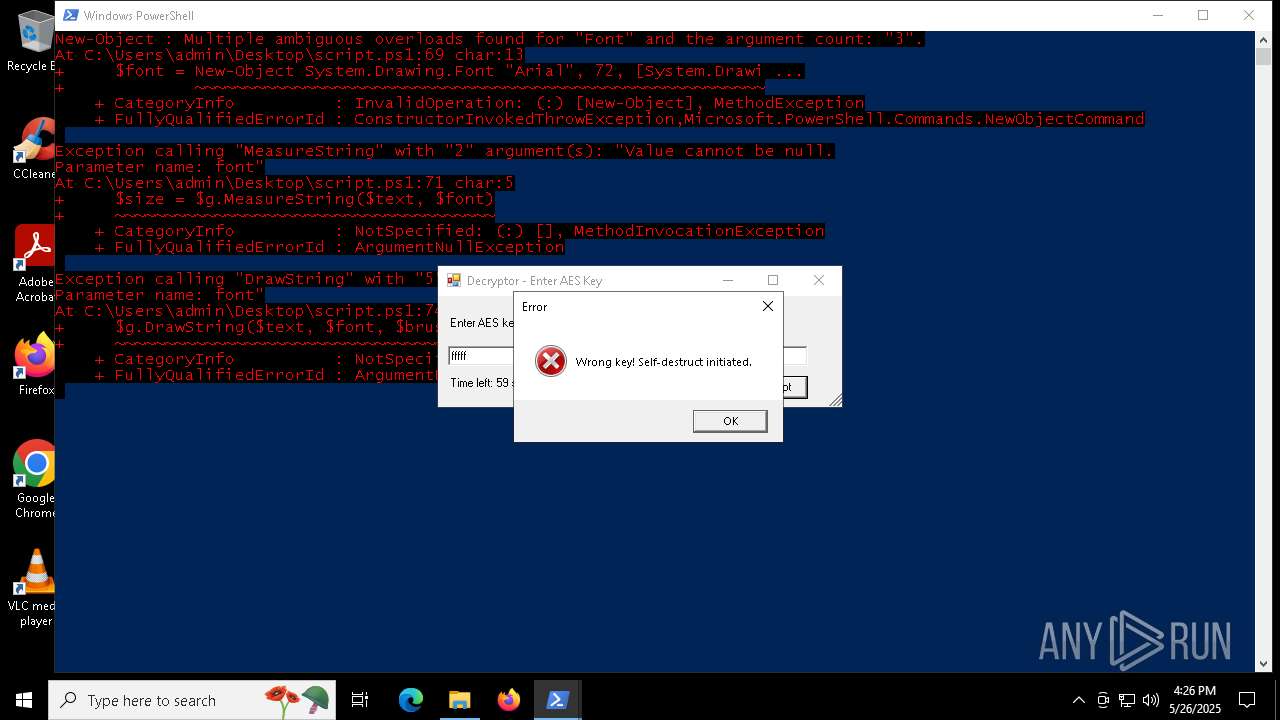
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7352)
Create files in a temporary directory
- cvtres.exe (PID: 7720)
- csc.exe (PID: 7700)
Checks supported languages
- csc.exe (PID: 7700)
- cvtres.exe (PID: 7720)
- StartMenuExperienceHost.exe (PID: 5212)
- TextInputHost.exe (PID: 5960)
- SearchApp.exe (PID: 6564)
Gets data length (POWERSHELL)
- powershell.exe (PID: 7352)
Reads the machine GUID from the registry
- csc.exe (PID: 7700)
- SearchApp.exe (PID: 6564)
Reads security settings of Internet Explorer
- explorer.exe (PID: 7784)
Creates files or folders in the user directory
- explorer.exe (PID: 7784)
Reads the computer name
- StartMenuExperienceHost.exe (PID: 5212)
- TextInputHost.exe (PID: 5960)
- SearchApp.exe (PID: 6564)
Process checks computer location settings
- StartMenuExperienceHost.exe (PID: 5212)
- SearchApp.exe (PID: 6564)
Checks proxy server information
- SearchApp.exe (PID: 6564)
- explorer.exe (PID: 7784)
Found Base64 encoded text manipulation via PowerShell (YARA)
- powershell.exe (PID: 7352)
Found Base64 encoded encryption-related PowerShell classes (YARA)
- powershell.exe (PID: 7352)
Found Base64 encoded file access via PowerShell (YARA)
- powershell.exe (PID: 7352)
Reads the software policy settings
- SearchApp.exe (PID: 6564)
Reads Environment values
- SearchApp.exe (PID: 6564)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
151
Monitored processes
18
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 544 | "C:\WINDOWS\system32\taskmgr.exe" /0 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4556 | C:\WINDOWS\System32\mobsync.exe -Embedding | C:\Windows\System32\mobsync.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Sync Center Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4628 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5212 | "C:\WINDOWS\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe" -ServerName:App.AppXywbrabmsek0gm3tkwpr5kwzbs55tkqay.mca | C:\Windows\SystemApps\Microsoft.Windows.StartMenuExperienceHost_cw5n1h2txyewy\StartMenuExperienceHost.exe | — | svchost.exe | |||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 5960 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 6376 | "C:\WINDOWS\system32\taskmgr.exe" /0 | C:\Windows\System32\Taskmgr.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Manager Exit code: 3221226540 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6564 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7056 | "C:\WINDOWS\system32\shutdown.exe" /l /f | C:\Windows\System32\shutdown.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Shutdown and Annotation Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7352 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" -ep bypass C:\Users\admin\Desktop\script.ps1 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7360 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
41 762
Read events
41 534
Write events
212
Delete events
16
Modification events
| (PID) Process: | (7784) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | delete value | Name: | UpgradeOrPBRAttempts |
Value: | |||
| (PID) Process: | (7784) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | delete value | Name: | DefaultStartLayout_UseWin7UpgradeBehavior |
Value: | |||
| (PID) Process: | (7784) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | delete value | Name: | DefaultStartLayout_UseWin8UpgradeBehavior |
Value: | |||
| (PID) Process: | (7784) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | delete value | Name: | LogonWork |
Value: | |||
| (PID) Process: | (7784) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\Shutdown |
| Operation: | write | Name: | CleanShutdown |
Value: 0 | |||
| (PID) Process: | (7784) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Feeds\DSB |
| Operation: | write | Name: | IsDynamicContentAvailable |
Value: 1 | |||
| (PID) Process: | (7784) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search |
| Operation: | delete value | Name: | SearchboxTaskbarModeForceGlyph |
Value: | |||
| (PID) Process: | (7784) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search |
| Operation: | write | Name: | SearchGlyphType |
Value: 2 | |||
| (PID) Process: | (7784) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search |
| Operation: | write | Name: | TraySearchBoxVisible |
Value: 1 | |||
| (PID) Process: | (7784) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Search |
| Operation: | write | Name: | TraySearchBoxVisibleOnAnyMonitor |
Value: 1 | |||
Executable files
3
Suspicious files
51
Text files
98
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7352 | powershell.exe | C:\Users\admin\AppData\Local\Temp\wallpaper.bmp | — | |
MD5:— | SHA256:— | |||
| 7352 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_irs1jlgq.hqh.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7352 | powershell.exe | C:\Users\admin\AppData\Local\Temp\azlpqbqe.0.cs | text | |
MD5:30904225CFFD70B824BFFF72F1E0400A | SHA256:0A91D83379D7D1F541043AF0C2BB59FF812B354072B55F451C7582B449E33EA1 | |||
| 7352 | powershell.exe | C:\Users\admin\AppData\Local\Temp\azlpqbqe.cmdline | text | |
MD5:7571B44B185B3E185D5649FBED313393 | SHA256:CB1E015F47F1E4E65FC3762F2A4F2C731D98B235B8BB4196A8220894F517F02A | |||
| 8012 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_jt5npcpj.xm3.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7352 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_tdeeroil.ccs.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7700 | csc.exe | C:\Users\admin\AppData\Local\Temp\CSCCF1DE729A41E429E9D2F7A9791D7CFA6.TMP | binary | |
MD5:AD5B1FA6F077796C8F758E7582BD8ED0 | SHA256:63ACBB845A8C7E572399A774BF3D51557B4DC91B0322563A3E4D92B5E083FD8E | |||
| 4628 | TiWorker.exe | C:\Windows\Logs\CBS\CBS.log | text | |
MD5:21174F43D65849A6F06D9F30B00556A8 | SHA256:DF7AFC0C452B15448F278B280F5EA7AFCB45E7E7D448E75AED5F2F4FA8B44207 | |||
| 7700 | csc.exe | C:\Users\admin\AppData\Local\Temp\azlpqbqe.dll | executable | |
MD5:AF52BF3F3CE43837FF37A9E362F1D39B | SHA256:5B6DFB7305ABBF357E4D5BF157E5238830A14D402F44F5BBA945175B4616D222 | |||
| 7700 | csc.exe | C:\Users\admin\AppData\Local\Temp\azlpqbqe.out | text | |
MD5:0F150AF9033443EBB530D944B03DD205 | SHA256:00475452191CC91241DFE962411673EB7D0AC1807E3294BDF6D2FC2AD44B39C4 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
39
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6564 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2244 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2244 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5796 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6392 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
2112 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6544 | svchost.exe | 40.126.31.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
www.bing.com |
| whitelisted |
th.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |