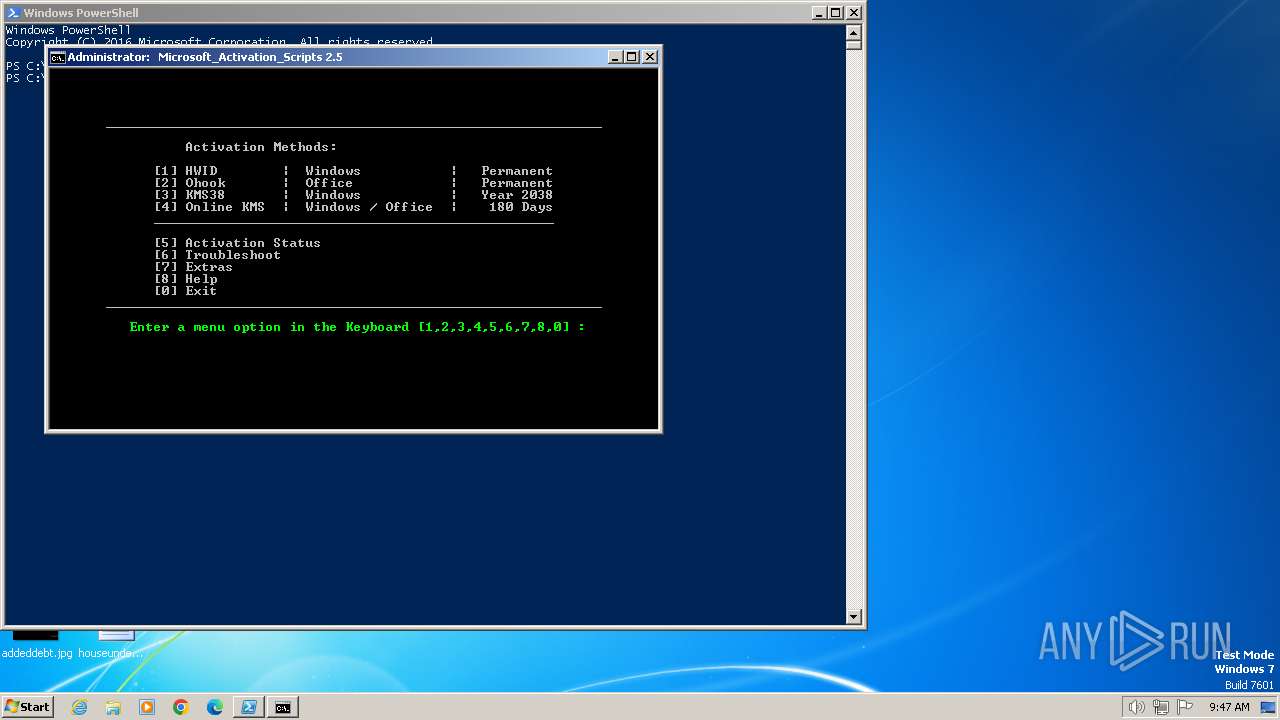
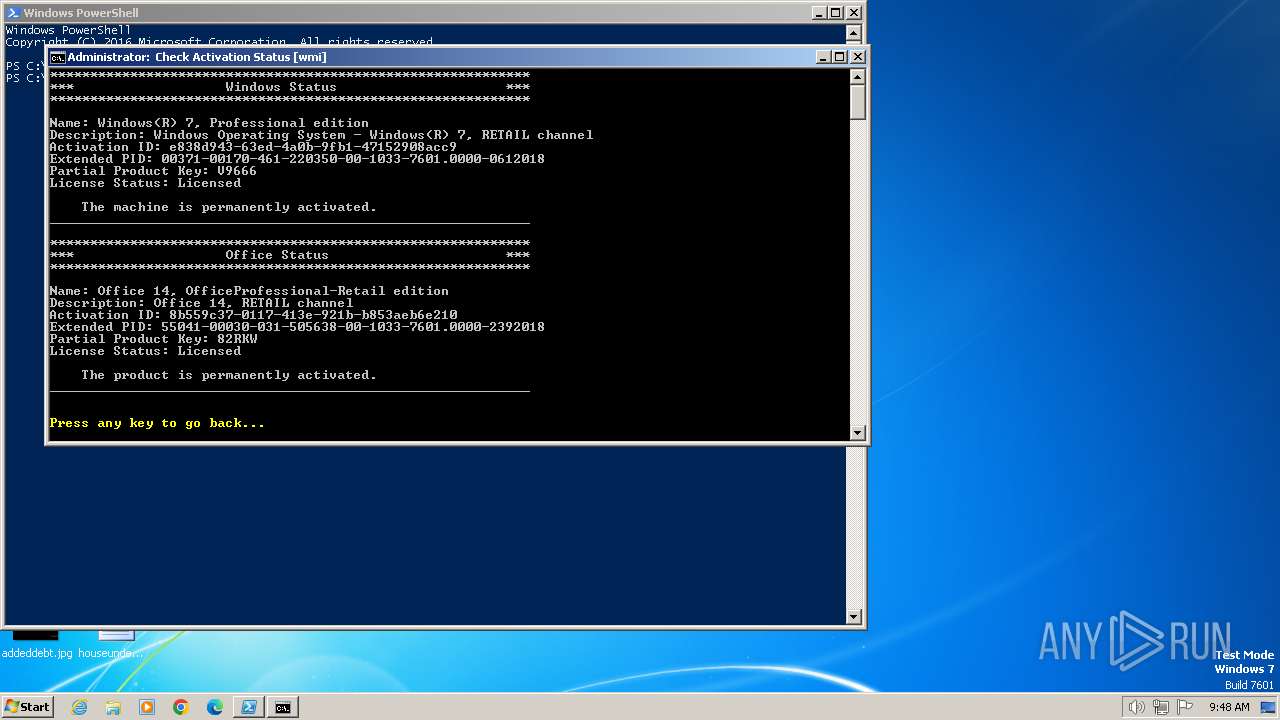
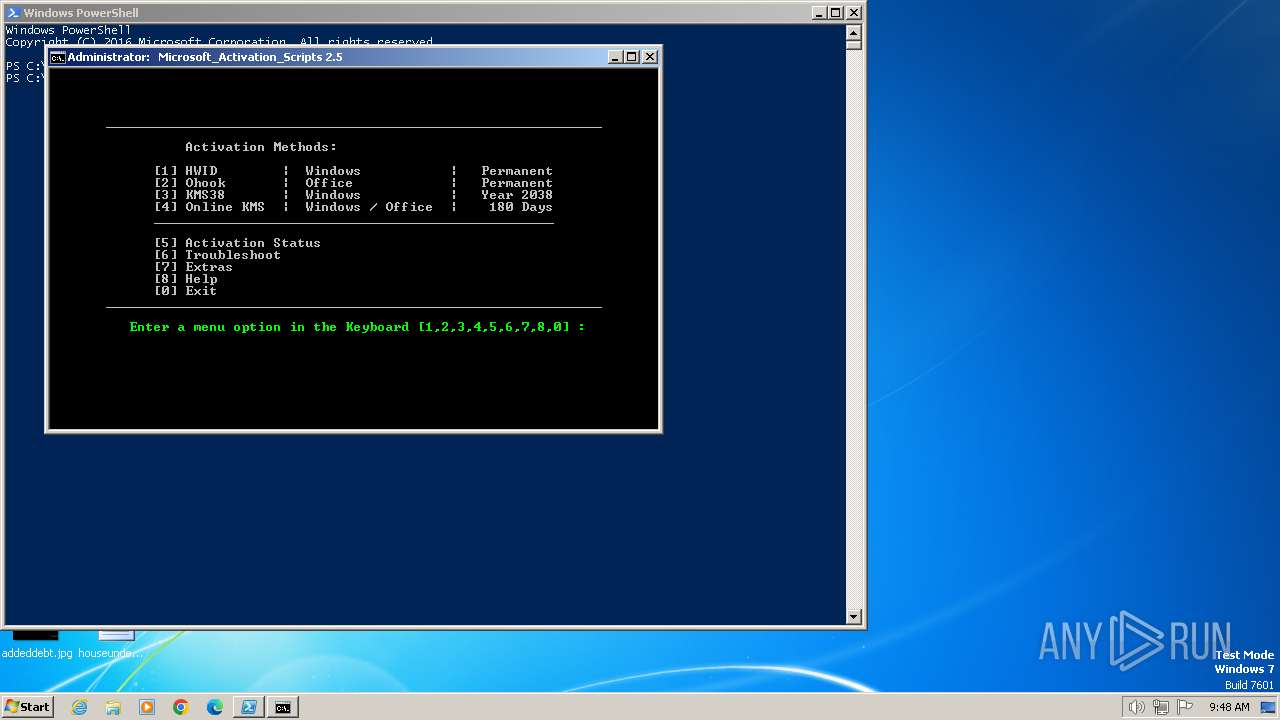
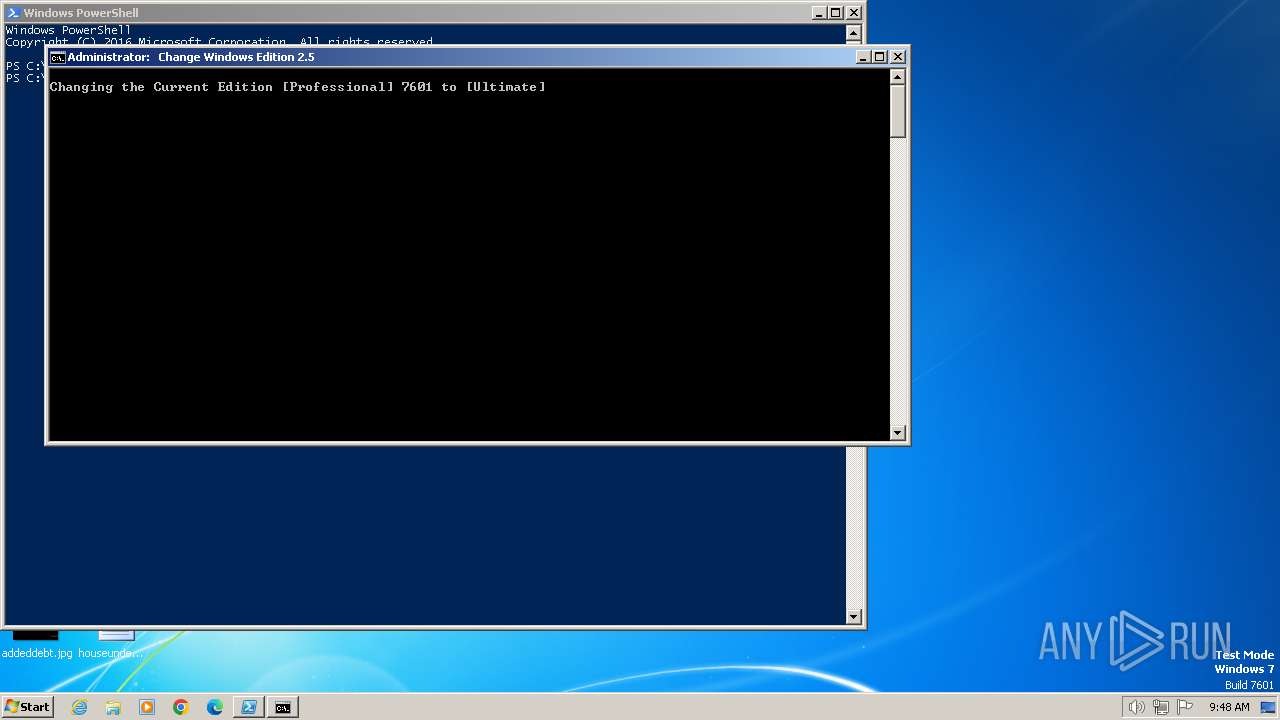
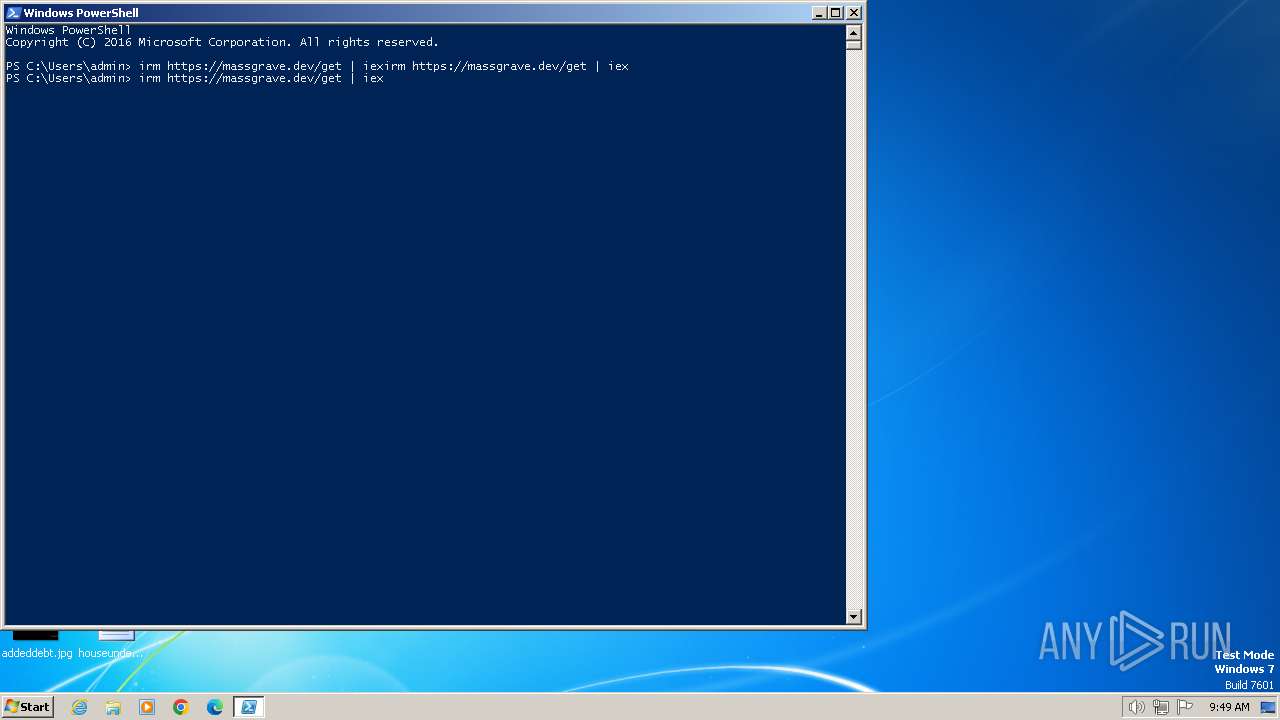
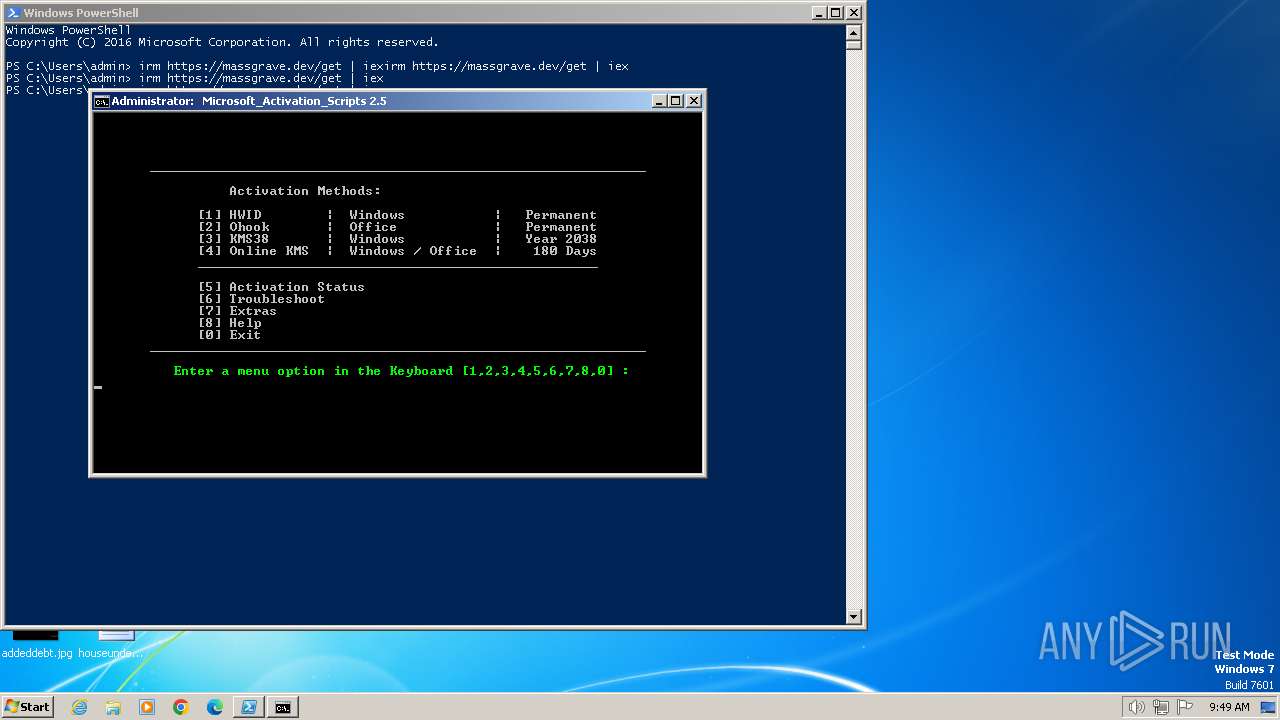
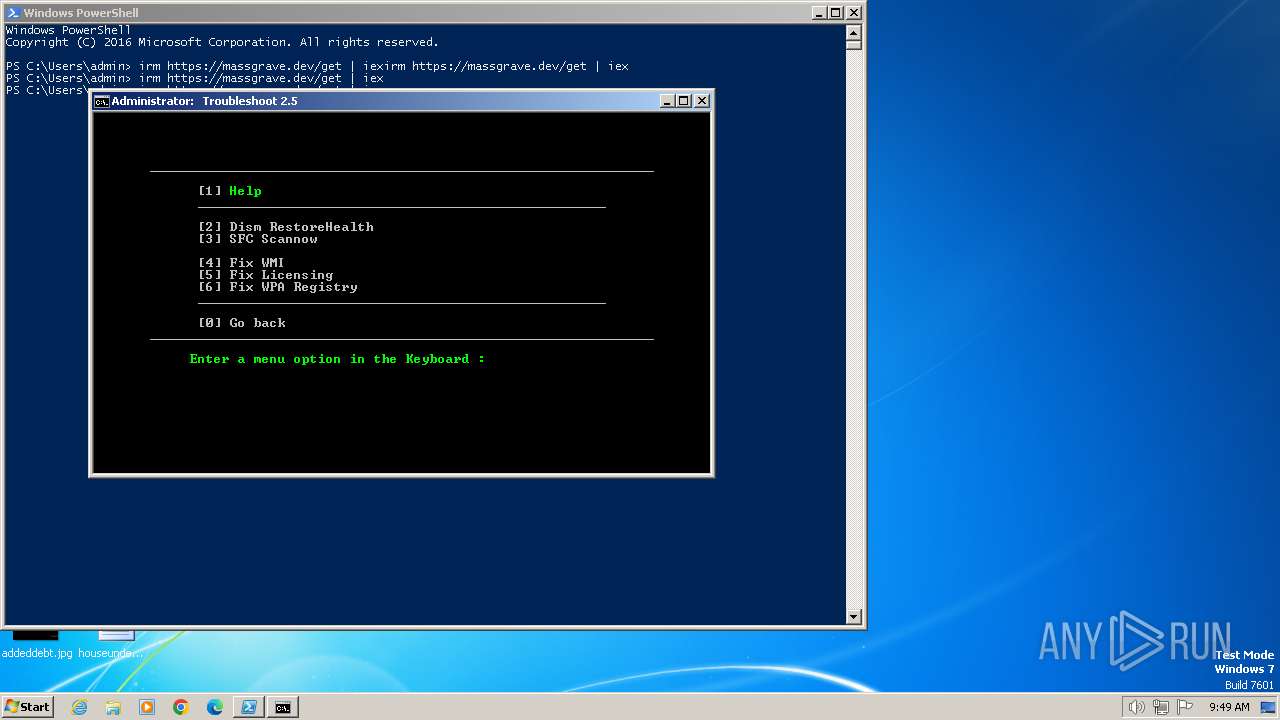
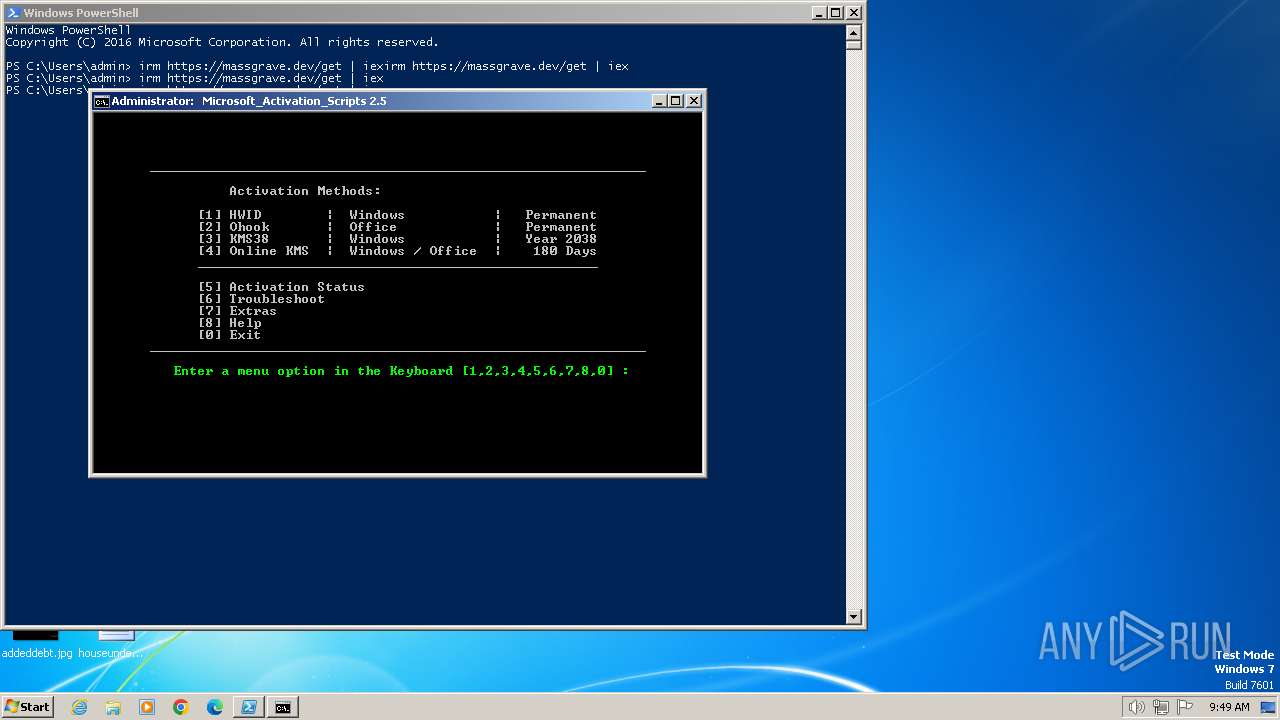
| URL: | https://massgrave.dev/ |
| Full analysis: | https://app.any.run/tasks/f1fbe288-0b94-48e8-80ca-0bec5237ee58 |
| Verdict: | Malicious activity |
| Analysis date: | March 11, 2024, 09:47:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 5C95876F594CFFB1178B8861F8C741E0 |
| SHA1: | 4F3DD1555BACB0851AD877F9B40BD8DCC884A71D |
| SHA256: | 6019AF861964CFB41AE5A5FE576ACA4521AFBA41255E5C636B1F53DFA0B6BE7F |
| SSDEEP: | 3:N8a0Kn:2a0K |
MALICIOUS
Starts NET.EXE for service management
- net.exe (PID: 3104)
- cmd.exe (PID: 2108)
- net.exe (PID: 2152)
- net.exe (PID: 2616)
- cmd.exe (PID: 896)
- net.exe (PID: 3484)
- net.exe (PID: 1768)
- net.exe (PID: 1852)
- net.exe (PID: 1020)
SUSPICIOUS
Executing commands from ".cmd" file
- powershell.exe (PID: 2260)
- cmd.exe (PID: 3984)
- powershell.exe (PID: 3556)
- cmd.exe (PID: 2108)
- powershell.exe (PID: 784)
- cmd.exe (PID: 1796)
- cmd.exe (PID: 896)
The Powershell connects to the Internet
- powershell.exe (PID: 2260)
Starts SC.EXE for service management
- cmd.exe (PID: 3984)
- cmd.exe (PID: 2108)
- cmd.exe (PID: 1796)
- cmd.exe (PID: 896)
Reads the Internet Settings
- powershell.exe (PID: 2260)
- powershell.exe (PID: 3556)
- WMIC.exe (PID: 3420)
- WMIC.exe (PID: 1388)
- WMIC.exe (PID: 1348)
- WMIC.exe (PID: 2572)
- WMIC.exe (PID: 1692)
- WMIC.exe (PID: 3692)
- WMIC.exe (PID: 3720)
- WMIC.exe (PID: 784)
- WMIC.exe (PID: 3272)
- WMIC.exe (PID: 3956)
- WMIC.exe (PID: 2028)
- powershell.exe (PID: 784)
- WMIC.exe (PID: 2580)
- WMIC.exe (PID: 3508)
- WMIC.exe (PID: 3420)
- WMIC.exe (PID: 2192)
- WMIC.exe (PID: 1740)
- WMIC.exe (PID: 2856)
- WMIC.exe (PID: 3324)
- WMIC.exe (PID: 2496)
- WMIC.exe (PID: 3708)
- WMIC.exe (PID: 1976)
- WMIC.exe (PID: 2100)
- WMIC.exe (PID: 1348)
- WMIC.exe (PID: 1836)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 3984)
- cmd.exe (PID: 2108)
- cmd.exe (PID: 2036)
- cmd.exe (PID: 3932)
- cmd.exe (PID: 1796)
- cmd.exe (PID: 3608)
- cmd.exe (PID: 896)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 2260)
- cmd.exe (PID: 3984)
- powershell.exe (PID: 3556)
- cmd.exe (PID: 2108)
- powershell.exe (PID: 784)
- cmd.exe (PID: 896)
- cmd.exe (PID: 1796)
Unusual connection from system programs
- powershell.exe (PID: 2260)
Application launched itself
- cmd.exe (PID: 3984)
- cmd.exe (PID: 2108)
- cmd.exe (PID: 896)
- cmd.exe (PID: 1796)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 3984)
- cmd.exe (PID: 2108)
- cmd.exe (PID: 2588)
- cmd.exe (PID: 2656)
- cmd.exe (PID: 3608)
- cmd.exe (PID: 1796)
- cmd.exe (PID: 896)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 2108)
- cmd.exe (PID: 896)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 2108)
- cmd.exe (PID: 3992)
- cmd.exe (PID: 2036)
- cmd.exe (PID: 1124)
- cmd.exe (PID: 3932)
- cmd.exe (PID: 3072)
- cmd.exe (PID: 896)
- cmd.exe (PID: 1880)
- cmd.exe (PID: 2648)
Hides command output
- cmd.exe (PID: 1124)
- cmd.exe (PID: 2736)
- cmd.exe (PID: 3744)
- cmd.exe (PID: 2080)
- cmd.exe (PID: 3048)
- cmd.exe (PID: 3564)
- cmd.exe (PID: 2588)
- cmd.exe (PID: 3400)
- cmd.exe (PID: 3472)
- cmd.exe (PID: 3024)
- cmd.exe (PID: 2796)
- cmd.exe (PID: 3056)
- cmd.exe (PID: 3364)
- cmd.exe (PID: 3020)
- cmd.exe (PID: 2808)
The process creates files with name similar to system file names
- Dism.exe (PID: 2740)
- Dism.exe (PID: 1888)
Starts a Microsoft application from unusual location
- DismHost.exe (PID: 668)
- DismHost.exe (PID: 2728)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 3608)
- cmd.exe (PID: 2108)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 3564)
Process drops legitimate windows executable
- Dism.exe (PID: 2740)
- Dism.exe (PID: 1888)
Executable content was dropped or overwritten
- Dism.exe (PID: 2740)
- Dism.exe (PID: 1888)
Executes as Windows Service
- VSSVC.exe (PID: 3724)
Starts NET.EXE to map network drives
- cmd.exe (PID: 896)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 896)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 2932)
INFO
Application launched itself
- chrome.exe (PID: 3672)
Manual execution by a user
- powershell.exe (PID: 2260)
- wmpnscfg.exe (PID: 2172)
Checks operating system version
- cmd.exe (PID: 3984)
- cmd.exe (PID: 2108)
- cmd.exe (PID: 1796)
- cmd.exe (PID: 896)
Checks supported languages
- mode.com (PID: 3248)
- mode.com (PID: 3024)
- mode.com (PID: 2864)
- mode.com (PID: 840)
- mode.com (PID: 924)
- DismHost.exe (PID: 668)
- mode.com (PID: 2124)
- DismHost.exe (PID: 2728)
- mode.com (PID: 1548)
- mode.com (PID: 2756)
- mode.com (PID: 1288)
- mode.com (PID: 1548)
- mode.com (PID: 2936)
- mode.com (PID: 3488)
- wmpnscfg.exe (PID: 2172)
Drops the executable file immediately after the start
- Dism.exe (PID: 2740)
- Dism.exe (PID: 1888)
Create files in a temporary directory
- Dism.exe (PID: 2740)
- Dism.exe (PID: 1888)
Reads the computer name
- DismHost.exe (PID: 668)
- DismHost.exe (PID: 2728)
- wmpnscfg.exe (PID: 2172)
Reads the machine GUID from the registry
- DismHost.exe (PID: 668)
- DismHost.exe (PID: 2728)
Reads Environment values
- DismHost.exe (PID: 668)
Reads Microsoft Office registry keys
- reg.exe (PID: 664)
- reg.exe (PID: 1072)
- reg.exe (PID: 3000)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
407
Monitored processes
348
Malicious processes
11
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 240 | findstr /i VOLUME_KMSCLIENT | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 240 | find /i "ComputerSystem" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 296 | findstr /v "f7f81a39-5f63-5b42-9efd-1f13b5431005quot; "MAS_80066066.cmd" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 324 | C:\Windows\system32\cmd.exe /c "prompt $H&for %B in (1) do rem" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 392 | choice /C:123456780 /N | C:\Windows\System32\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Offers the user a choice Exit code: 5 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 392 | findstr /i Windows | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 532 | sc query sppsvc | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 532 | reg delete "HKLM\SOFTWARE\Microsoft\OfficeSoftwareProtectionPlatform" /f /v KeyManagementServicePort | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 548 | C:\Windows\system32\cmd.exe /S /D /c" echo "-el" " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 568 | find /i "STOPPED" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
43 339
Read events
43 075
Write events
245
Delete events
19
Modification events
| (PID) Process: | (3672) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (3672) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (3672) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (3672) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (3672) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3672) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (3672) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (3672) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (3672) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3672) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
62
Suspicious files
50
Text files
52
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3672 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF17f6c4.TMP | — | |
MD5:— | SHA256:— | |||
| 3672 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3672 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
| 3672 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Platform Notifications\LOG.old~RF17f80c.TMP | text | |
MD5:F5B58F0B08202C8D6DE12514994A84BF | SHA256:F5BA8809B6A3920A11CF31E7F6A1DEC46EF4F4339D6158967CCB1405409D1241 | |||
| 3672 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Session Storage\LOG.old | text | |
MD5:E53573A93829681410D5E7DBB1B61C78 | SHA256:A82D28F2C1E22A2AE0ABC5F5AF0CC8EE7AD913BAB3A0BF84CE6D8D23F67E06A3 | |||
| 3672 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\LOG.old~RF17f82b.TMP | text | |
MD5:8593E82FF8753DC10267243C51E8A91B | SHA256:FE9EE2D77D9EB5CBA707EDBCB7F1ABAA83418CDB66D66835B4B9A1B6CC5CC34F | |||
| 3672 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF17fd8a.TMP | — | |
MD5:— | SHA256:— | |||
| 3672 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 3672 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\metadata\LOG.old~RF17f81b.TMP | text | |
MD5:B36B68CE4A71A5BFAF89A4D1CC07893F | SHA256:6422CC04455EF100D67FD9F299AACFEF3BA4F77D0FA1D2440D89E7D1CF65EBBC | |||
| 3672 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\AutofillStrikeDatabase\LOG.old~RF180903.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
13
DNS requests
13
Threats
1
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3672 | chrome.exe | 239.255.255.250:1900 | — | — | — | unknown |
3228 | chrome.exe | 142.250.110.84:443 | accounts.google.com | GOOGLE | US | unknown |
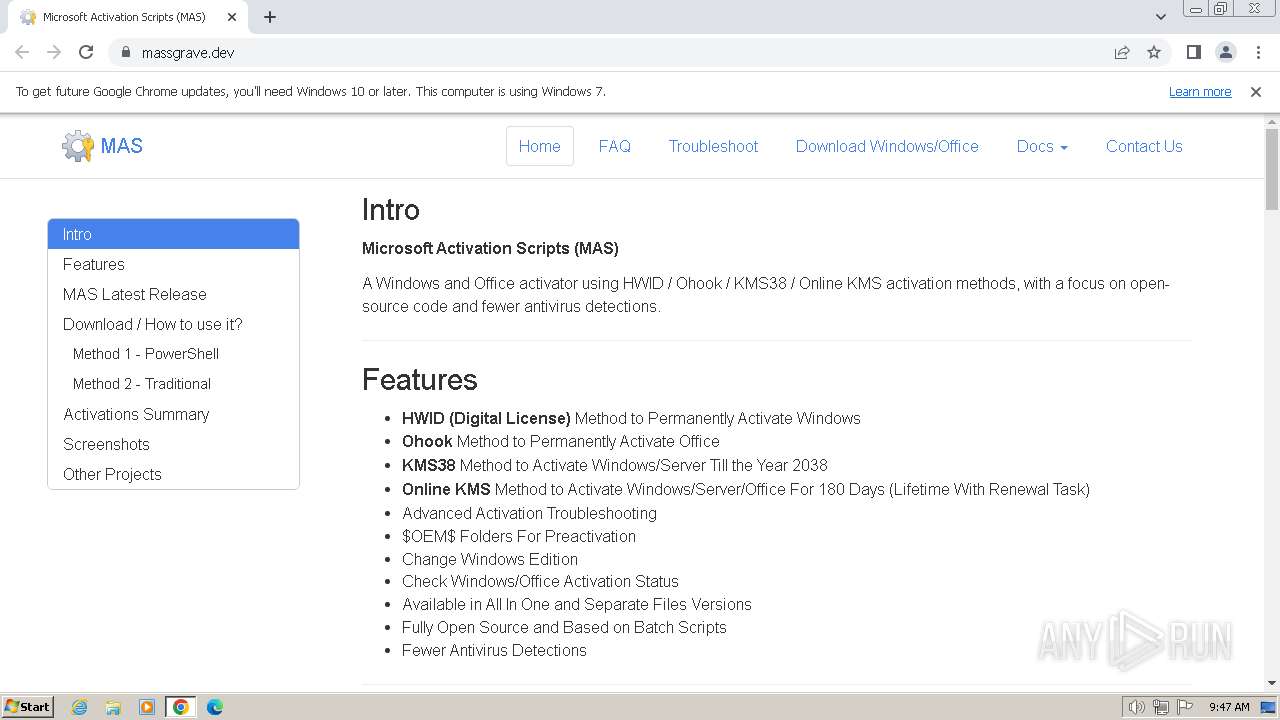
3228 | chrome.exe | 5.45.97.157:443 | massgrave.dev | netcup GmbH | DE | unknown |
3228 | chrome.exe | 18.245.86.38:443 | mathjax.rstudio.com | — | US | unknown |
3672 | chrome.exe | 224.0.0.251:5353 | — | — | — | unknown |
3228 | chrome.exe | 216.58.206.36:443 | www.google.com | GOOGLE | US | whitelisted |
2260 | powershell.exe | 5.45.97.157:443 | massgrave.dev | netcup GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
accounts.google.com |
| shared |
massgrave.dev |
| unknown |
mathjax.rstudio.com |
| whitelisted |
www.google.com |
| whitelisted |
raw.githubusercontent.com |
| shared |
updatecheck.massgrave.dev |
| unknown |
kms.zhuxiaole.org |
| unknown |
kms.moeyuuko.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2260 | powershell.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
Process | Message |
|---|---|
Dism.exe | PID=2740 Instantiating the Provider Store. - CDISMImageSession::get_ProviderStore |
Dism.exe | PID=2740 Initializing a provider store for the LOCAL session type. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=2740 Attempting to initialize the logger from the Image Session. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=2740 Provider has not previously been encountered. Attempting to initialize the provider. - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=2740 Loading Provider from location C:\Windows\System32\Dism\LogProvider.dll - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=2740 Connecting to the provider located at C:\Windows\System32\Dism\LogProvider.dll. - CDISMProviderStore::Internal_LoadProvider |
Dism.exe | PID=2740 Getting Provider OSServices - CDISMProviderStore::GetProvider |
Dism.exe | PID=2740 The requested provider was not found in the Provider Store. - CDISMProviderStore::Internal_GetProvider(hr:0x80004005) |
Dism.exe | PID=2740 Failed to get an OSServices provider. Must be running in local store. Falling back to checking alongside the log provider for wdscore.dll. - CDISMLogger::FindWdsCore(hr:0x80004005) |
DismHost.exe | PID=668 Encountered a loaded provider DISMLogger. - CDISMProviderStore::Internal_DisconnectProvider |