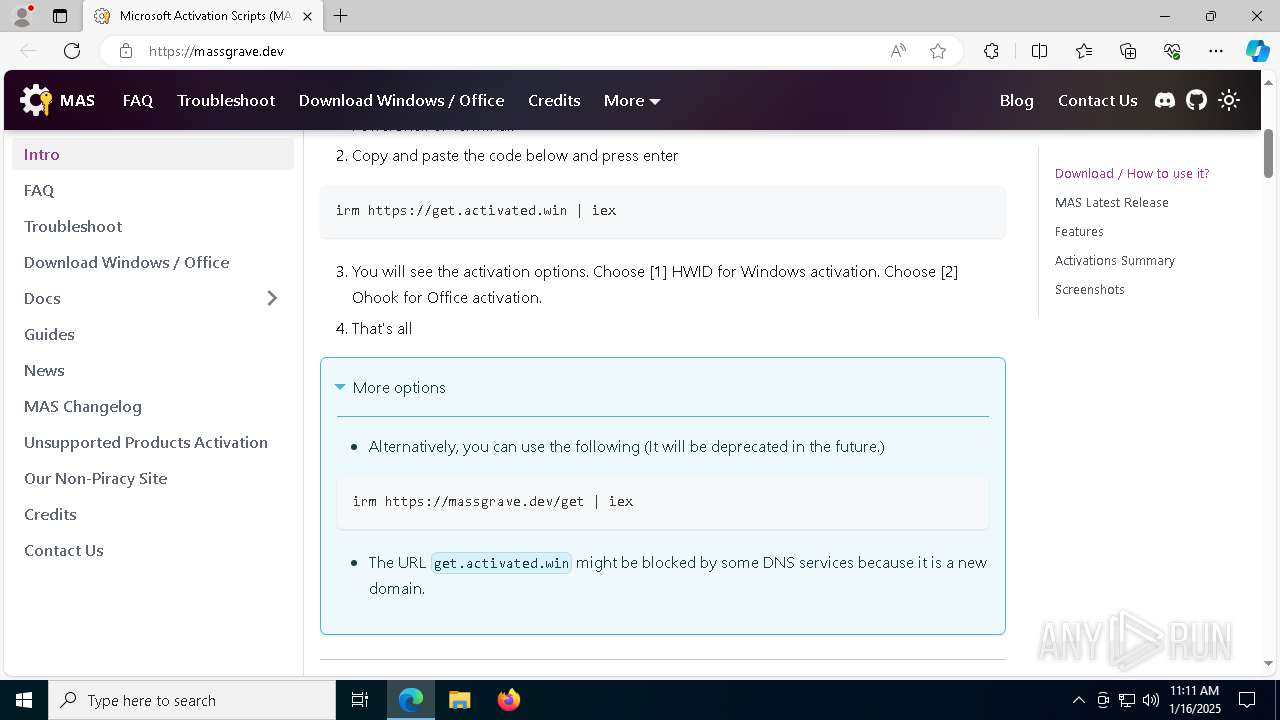
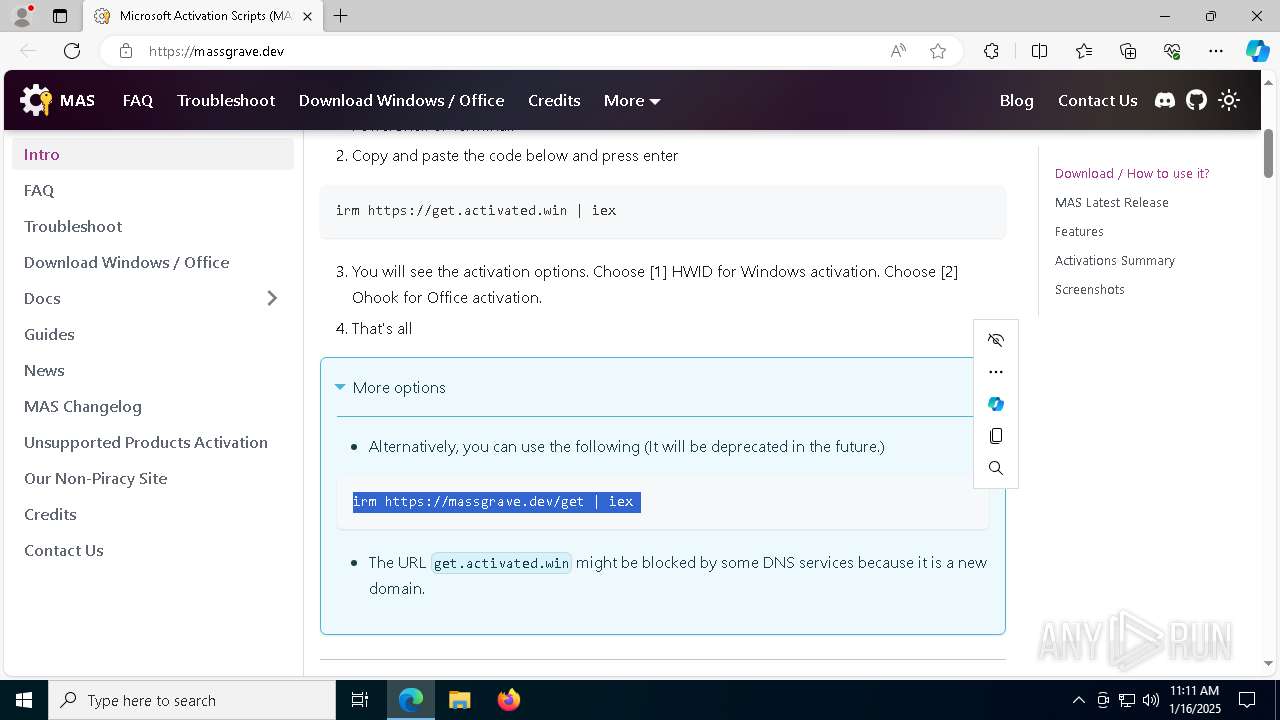
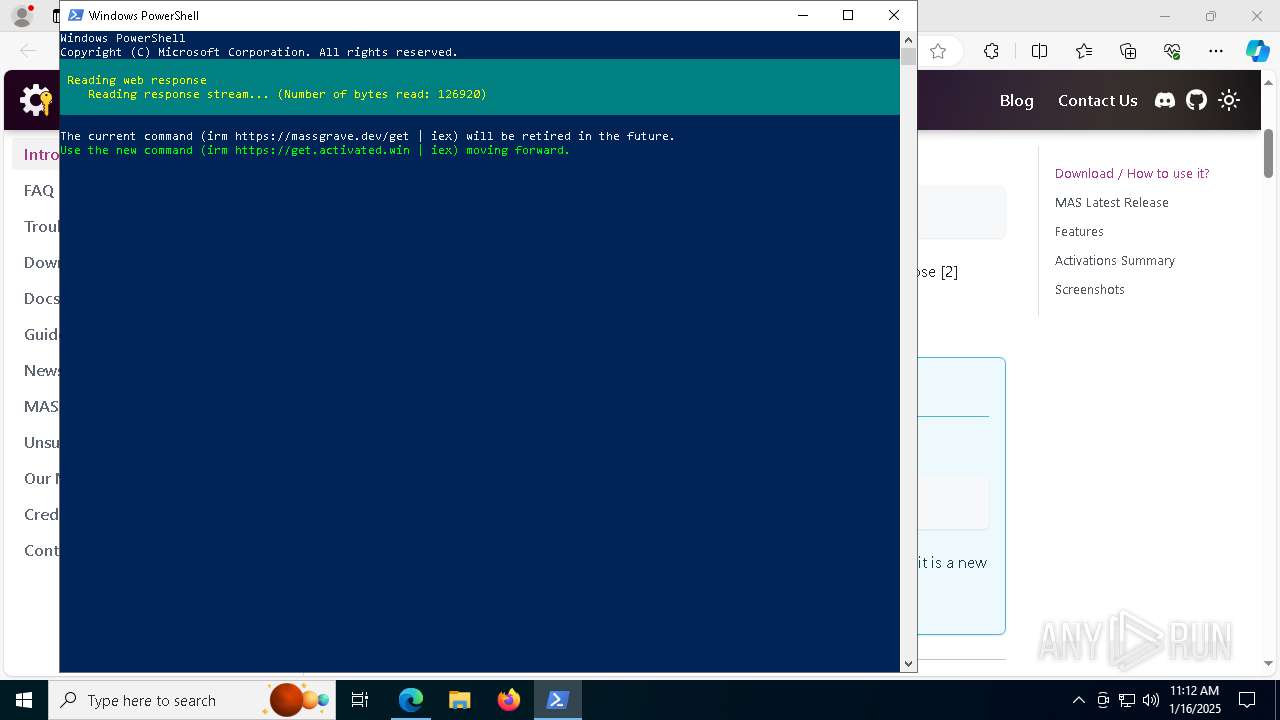
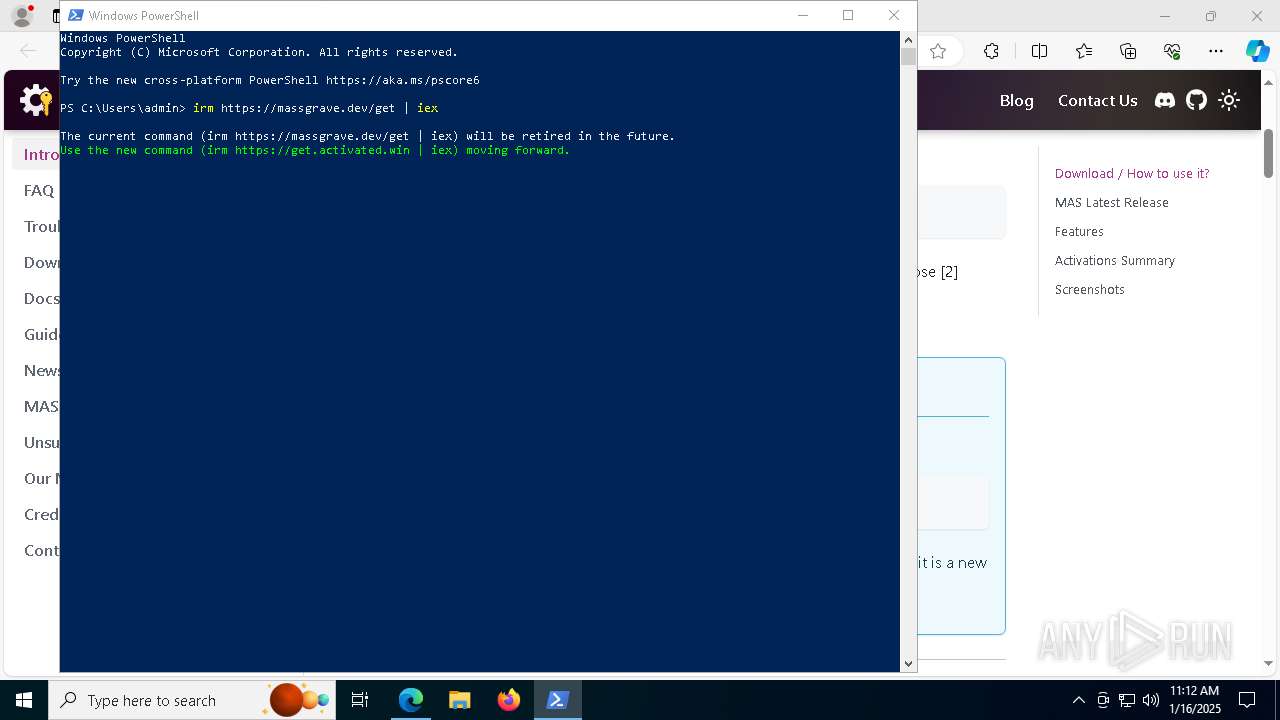
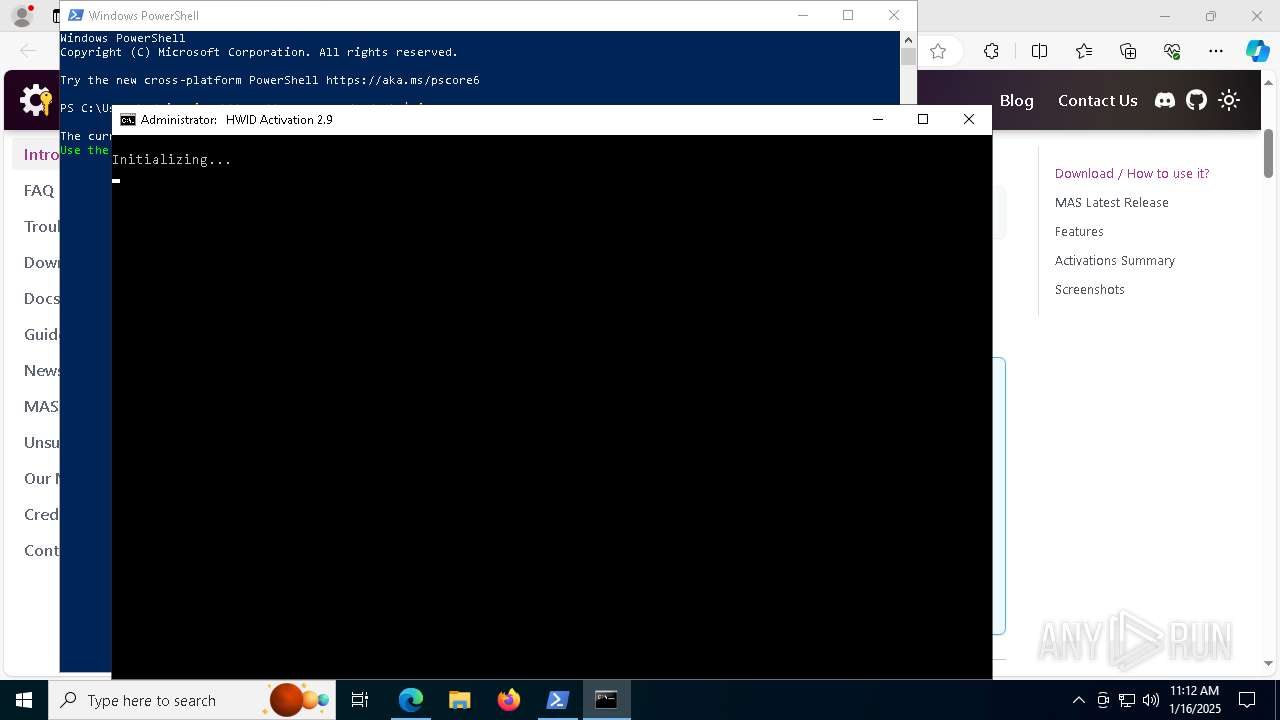
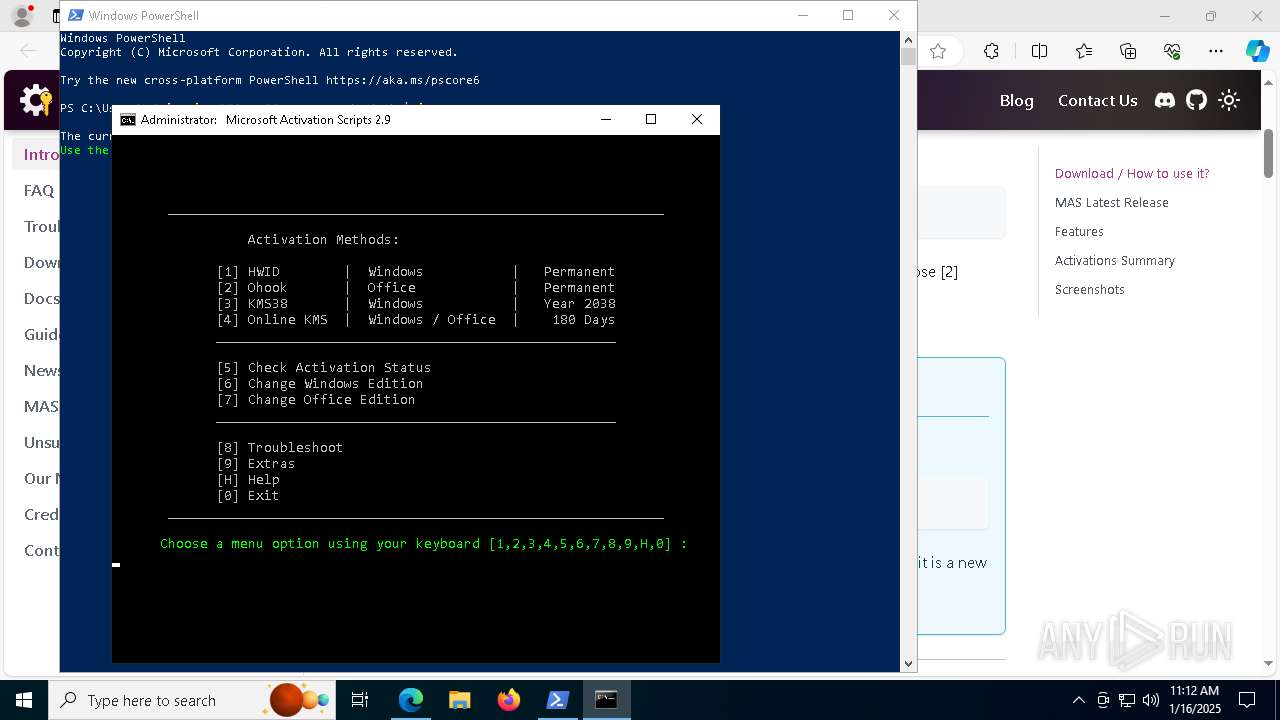
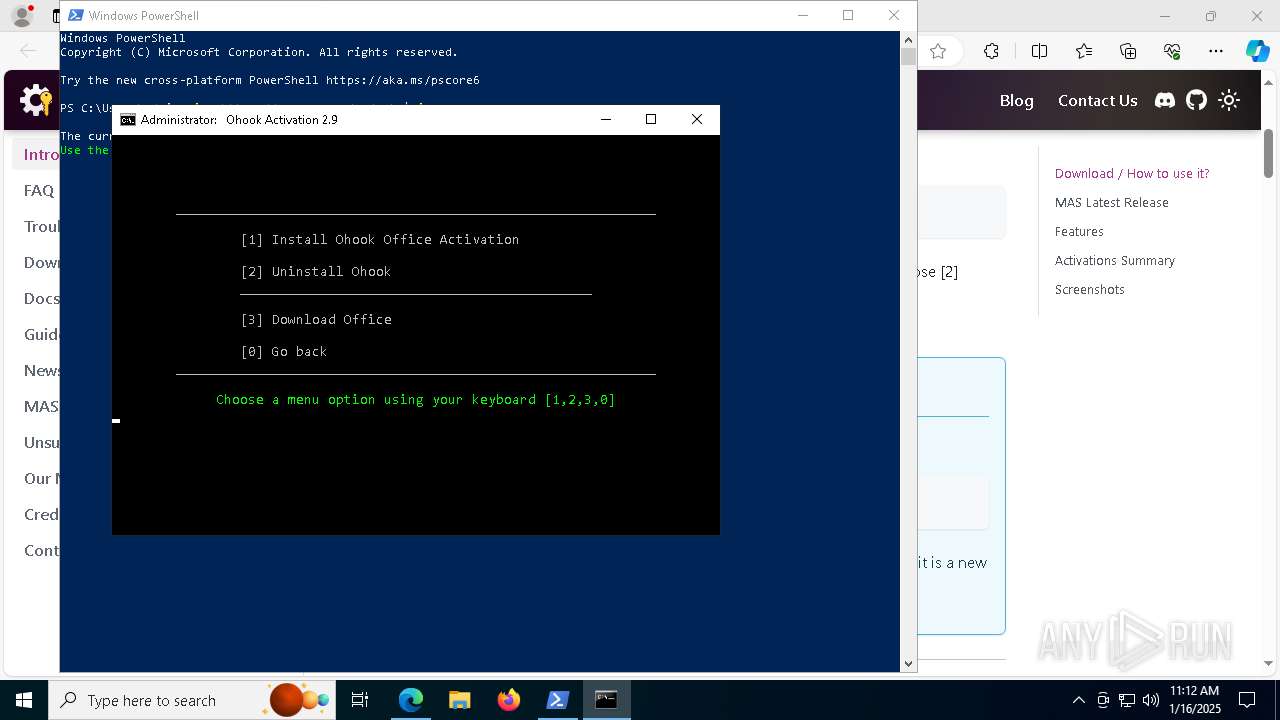
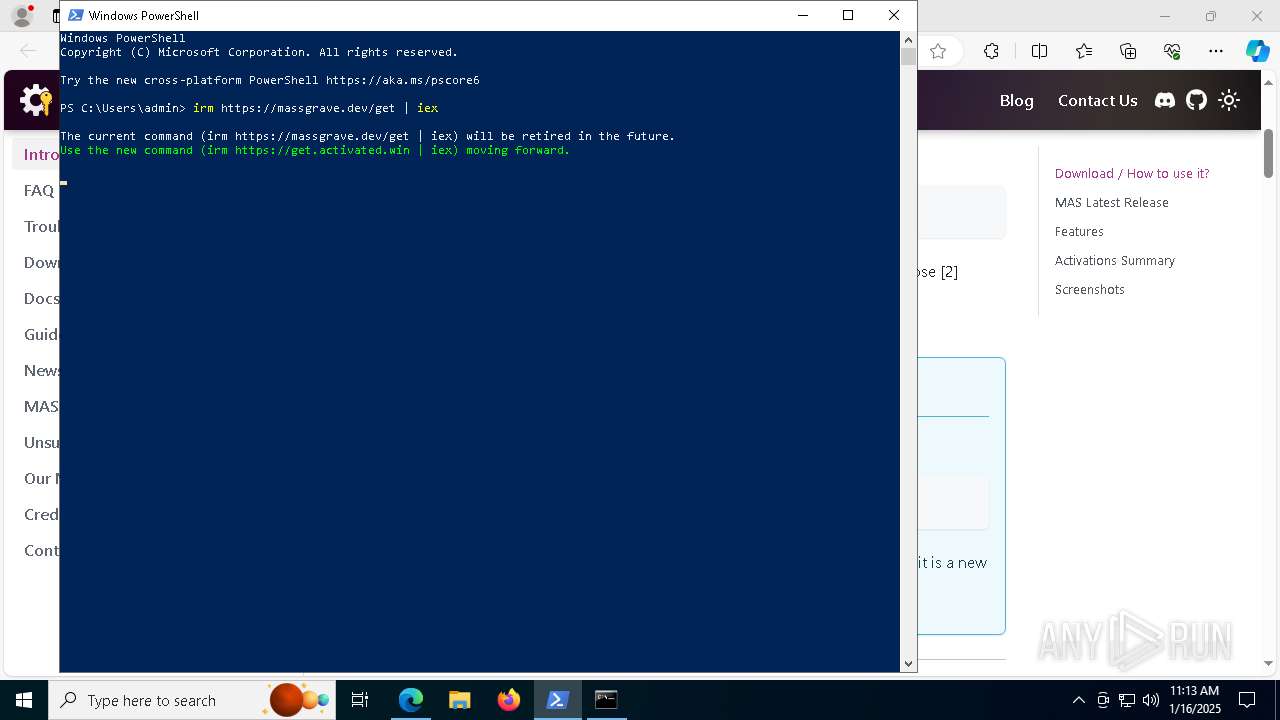
| URL: | https://massgrave.dev/ |
| Full analysis: | https://app.any.run/tasks/1c0d29f7-96ca-4715-87ec-14d25be23142 |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | January 16, 2025, 11:11:33 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 5C95876F594CFFB1178B8861F8C741E0 |
| SHA1: | 4F3DD1555BACB0851AD877F9B40BD8DCC884A71D |
| SHA256: | 6019AF861964CFB41AE5A5FE576ACA4521AFBA41255E5C636B1F53DFA0B6BE7F |
| SSDEEP: | 3:N8a0Kn:2a0K |
MALICIOUS
No malicious indicators.SUSPICIOUS
Windows service management via SC.EXE
- sc.exe (PID: 7364)
- sc.exe (PID: 4528)
- sc.exe (PID: 3508)
- sc.exe (PID: 6972)
- sc.exe (PID: 4804)
- sc.exe (PID: 7368)
- sc.exe (PID: 8000)
- sc.exe (PID: 4076)
- sc.exe (PID: 5532)
- sc.exe (PID: 7544)
- sc.exe (PID: 7484)
- sc.exe (PID: 4824)
- sc.exe (PID: 7704)
- sc.exe (PID: 6972)
- sc.exe (PID: 7088)
- sc.exe (PID: 2992)
- sc.exe (PID: 2136)
- sc.exe (PID: 7736)
- sc.exe (PID: 7104)
- sc.exe (PID: 3896)
- sc.exe (PID: 8068)
- sc.exe (PID: 7720)
- sc.exe (PID: 3888)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 6012)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 6012)
- powershell.exe (PID: 4708)
- powershell.exe (PID: 8000)
- powershell.exe (PID: 4076)
- powershell.exe (PID: 8056)
- powershell.exe (PID: 7296)
- powershell.exe (PID: 5028)
- powershell.exe (PID: 3832)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 6012)
- powershell.exe (PID: 4708)
- powershell.exe (PID: 7296)
- powershell.exe (PID: 8000)
- powershell.exe (PID: 4076)
- powershell.exe (PID: 8056)
- powershell.exe (PID: 5028)
- powershell.exe (PID: 3832)
Starts SC.EXE for service management
- cmd.exe (PID: 7204)
- cmd.exe (PID: 3848)
- cmd.exe (PID: 7516)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 6012)
- cmd.exe (PID: 5092)
- cmd.exe (PID: 7204)
- powershell.exe (PID: 6076)
- cmd.exe (PID: 1796)
- cmd.exe (PID: 3848)
- powershell.exe (PID: 5628)
- cmd.exe (PID: 7332)
- cmd.exe (PID: 7516)
Executing commands from ".cmd" file
- cmd.exe (PID: 7204)
- powershell.exe (PID: 6076)
- cmd.exe (PID: 3848)
- powershell.exe (PID: 5628)
- cmd.exe (PID: 7516)
- powershell.exe (PID: 6012)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 8060)
- cmd.exe (PID: 3208)
- cmd.exe (PID: 5200)
- cmd.exe (PID: 7516)
- cmd.exe (PID: 5592)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 8060)
- cmd.exe (PID: 7204)
- cmd.exe (PID: 3208)
- cmd.exe (PID: 3848)
- cmd.exe (PID: 5200)
- cmd.exe (PID: 7516)
- cmd.exe (PID: 7948)
- powershell.exe (PID: 7316)
- cmd.exe (PID: 4716)
- powershell.exe (PID: 7144)
- cmd.exe (PID: 5592)
- cmd.exe (PID: 7436)
- cmd.exe (PID: 5192)
- cmd.exe (PID: 8060)
- cmd.exe (PID: 5268)
- cmd.exe (PID: 7332)
- cmd.exe (PID: 7136)
- powershell.exe (PID: 7932)
- cmd.exe (PID: 4076)
- cmd.exe (PID: 2756)
- cmd.exe (PID: 6372)
- cmd.exe (PID: 7552)
- cmd.exe (PID: 5848)
- cmd.exe (PID: 7116)
- cmd.exe (PID: 5964)
- cmd.exe (PID: 1616)
- cmd.exe (PID: 4628)
- cmd.exe (PID: 1620)
- cmd.exe (PID: 624)
- cmd.exe (PID: 7840)
- cmd.exe (PID: 7892)
- cmd.exe (PID: 5080)
- cmd.exe (PID: 3080)
- powershell.exe (PID: 1016)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 8060)
- cmd.exe (PID: 3208)
- cmd.exe (PID: 5200)
- cmd.exe (PID: 7516)
- cmd.exe (PID: 5592)
- cmd.exe (PID: 7332)
Application launched itself
- cmd.exe (PID: 5092)
- cmd.exe (PID: 1796)
- cmd.exe (PID: 3848)
- cmd.exe (PID: 7204)
- cmd.exe (PID: 7332)
- powershell.exe (PID: 7316)
- powershell.exe (PID: 7144)
- cmd.exe (PID: 7516)
- powershell.exe (PID: 7932)
- powershell.exe (PID: 1016)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 3848)
- cmd.exe (PID: 7516)
- cmd.exe (PID: 7204)
- cmd.exe (PID: 3060)
- cmd.exe (PID: 7568)
- cmd.exe (PID: 6216)
- cmd.exe (PID: 1448)
- cmd.exe (PID: 4716)
- cmd.exe (PID: 836)
Creates new GUID (POWERSHELL)
- powershell.exe (PID: 6012)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7516)
- cmd.exe (PID: 7568)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 3560)
- cmd.exe (PID: 4308)
- cmd.exe (PID: 7516)
- cmd.exe (PID: 6252)
- cmd.exe (PID: 7612)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 5696)
Hides command output
- cmd.exe (PID: 1760)
- cmd.exe (PID: 5696)
- cmd.exe (PID: 3060)
- cmd.exe (PID: 5592)
- cmd.exe (PID: 5028)
- cmd.exe (PID: 4128)
- cmd.exe (PID: 2408)
- cmd.exe (PID: 7436)
- cmd.exe (PID: 2232)
- cmd.exe (PID: 3816)
- cmd.exe (PID: 5192)
- cmd.exe (PID: 3688)
- cmd.exe (PID: 8168)
- cmd.exe (PID: 6776)
- cmd.exe (PID: 5092)
- cmd.exe (PID: 7528)
- cmd.exe (PID: 3656)
- cmd.exe (PID: 8060)
- cmd.exe (PID: 1616)
- cmd.exe (PID: 8072)
- cmd.exe (PID: 4624)
- cmd.exe (PID: 8180)
- cmd.exe (PID: 7032)
- cmd.exe (PID: 7148)
- cmd.exe (PID: 1876)
- cmd.exe (PID: 7408)
- cmd.exe (PID: 7568)
- cmd.exe (PID: 7032)
- cmd.exe (PID: 7332)
- cmd.exe (PID: 3552)
- cmd.exe (PID: 1356)
- cmd.exe (PID: 4392)
- cmd.exe (PID: 7716)
- cmd.exe (PID: 7792)
- cmd.exe (PID: 3816)
- cmd.exe (PID: 6216)
- cmd.exe (PID: 7472)
- cmd.exe (PID: 3832)
- cmd.exe (PID: 7136)
- cmd.exe (PID: 1228)
- cmd.exe (PID: 4264)
- cmd.exe (PID: 5684)
- cmd.exe (PID: 6056)
- cmd.exe (PID: 7648)
- cmd.exe (PID: 5544)
- cmd.exe (PID: 5588)
- cmd.exe (PID: 1348)
- cmd.exe (PID: 1192)
- cmd.exe (PID: 904)
- cmd.exe (PID: 6256)
- cmd.exe (PID: 5004)
- cmd.exe (PID: 3544)
- cmd.exe (PID: 2356)
- cmd.exe (PID: 4640)
- cmd.exe (PID: 1328)
- cmd.exe (PID: 4156)
- cmd.exe (PID: 7748)
- cmd.exe (PID: 7876)
- cmd.exe (PID: 7932)
- cmd.exe (PID: 5788)
- cmd.exe (PID: 7520)
- cmd.exe (PID: 3060)
- cmd.exe (PID: 4716)
- cmd.exe (PID: 836)
- cmd.exe (PID: 7488)
- cmd.exe (PID: 7308)
- cmd.exe (PID: 6056)
Detects reflection assembly loader (YARA)
- powershell.exe (PID: 5628)
The process bypasses the loading of PowerShell profile settings
- powershell.exe (PID: 7316)
- powershell.exe (PID: 7144)
- powershell.exe (PID: 7932)
- powershell.exe (PID: 1016)
The process hides Powershell's copyright startup banner
- powershell.exe (PID: 7316)
- powershell.exe (PID: 7144)
- powershell.exe (PID: 7932)
- powershell.exe (PID: 1016)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 7516)
- cmd.exe (PID: 8168)
- cmd.exe (PID: 2408)
- cmd.exe (PID: 1616)
- cmd.exe (PID: 3832)
- cmd.exe (PID: 1228)
- cmd.exe (PID: 7648)
- cmd.exe (PID: 5544)
Get information on the list of running processes
- cmd.exe (PID: 3060)
- cmd.exe (PID: 7516)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 7516)
Executable content was dropped or overwritten
- powershell.exe (PID: 5028)
- Dism.exe (PID: 3208)
- Dism.exe (PID: 3640)
Writes data into a file (POWERSHELL)
- powershell.exe (PID: 5028)
Returns all items found within a container (POWERSHELL)
- powershell.exe (PID: 7468)
Starts a Microsoft application from unusual location
- DismHost.exe (PID: 8108)
- DismHost.exe (PID: 7560)
INFO
Checks supported languages
- identity_helper.exe (PID: 7948)
- mode.com (PID: 8108)
- mode.com (PID: 5028)
- mode.com (PID: 8044)
Checks operating system version
- cmd.exe (PID: 7204)
- cmd.exe (PID: 3848)
- cmd.exe (PID: 7516)
Checks current location (POWERSHELL)
- powershell.exe (PID: 6012)
Manual execution by a user
- powershell.exe (PID: 6012)
Reads Environment values
- identity_helper.exe (PID: 7948)
Gets a random number, or selects objects randomly from a collection (POWERSHELL)
- powershell.exe (PID: 6012)
- powershell.exe (PID: 4708)
- powershell.exe (PID: 7296)
- powershell.exe (PID: 8000)
- powershell.exe (PID: 4076)
- powershell.exe (PID: 8056)
- powershell.exe (PID: 5028)
- powershell.exe (PID: 3832)
Reads the computer name
- identity_helper.exe (PID: 7948)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 6012)
- powershell.exe (PID: 4708)
- powershell.exe (PID: 7296)
- powershell.exe (PID: 8000)
- powershell.exe (PID: 4076)
- powershell.exe (PID: 8056)
- powershell.exe (PID: 5028)
- powershell.exe (PID: 3832)
Application launched itself
- msedge.exe (PID: 5464)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 4708)
- powershell.exe (PID: 7296)
- powershell.exe (PID: 6012)
- powershell.exe (PID: 8000)
- powershell.exe (PID: 4076)
- powershell.exe (PID: 5028)
- powershell.exe (PID: 8056)
- powershell.exe (PID: 3832)
Starts MODE.COM to configure console settings
- mode.com (PID: 7028)
- mode.com (PID: 8108)
- mode.com (PID: 5028)
- mode.com (PID: 7776)
- mode.com (PID: 8044)
- mode.com (PID: 4120)
- mode.com (PID: 7976)
- mode.com (PID: 4120)
- mode.com (PID: 7488)
- mode.com (PID: 7808)
- mode.com (PID: 2804)
- mode.com (PID: 5916)
- mode.com (PID: 1796)
- mode.com (PID: 1792)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 8036)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 5880)
The sample compiled with english language support
- powershell.exe (PID: 5028)
- Dism.exe (PID: 3208)
- msedge.exe (PID: 3724)
- Dism.exe (PID: 3640)
Executable content was dropped or overwritten
- msedge.exe (PID: 3724)
Returns hidden items found within a container (POWERSHELL)
- conhost.exe (PID: 7780)
- conhost.exe (PID: 8068)
Sends debugging messages
- DismHost.exe (PID: 8108)
- Dism.exe (PID: 3640)
- DismHost.exe (PID: 7560)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7216)
- powershell.exe (PID: 1916)
- powershell.exe (PID: 5404)
- powershell.exe (PID: 7148)
- powershell.exe (PID: 3680)
- powershell.exe (PID: 3152)
- powershell.exe (PID: 648)
- powershell.exe (PID: 8020)
- powershell.exe (PID: 4708)
- powershell.exe (PID: 4128)
- powershell.exe (PID: 7404)
- powershell.exe (PID: 7720)
- powershell.exe (PID: 8140)
- powershell.exe (PID: 7684)
- powershell.exe (PID: 8120)
Converts byte array into Unicode string (POWERSHELL)
- powershell.exe (PID: 8020)
- powershell.exe (PID: 7148)
- powershell.exe (PID: 3152)
- powershell.exe (PID: 1916)
- powershell.exe (PID: 4128)
- powershell.exe (PID: 8140)
- powershell.exe (PID: 7720)
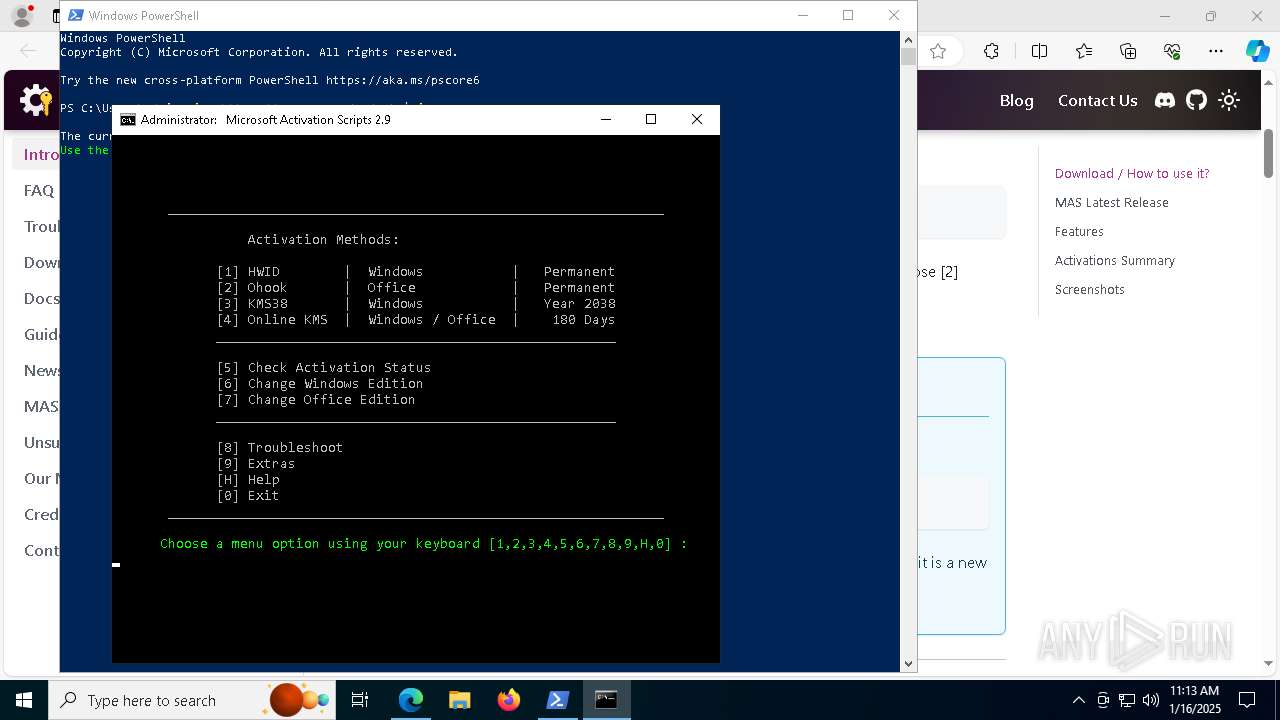
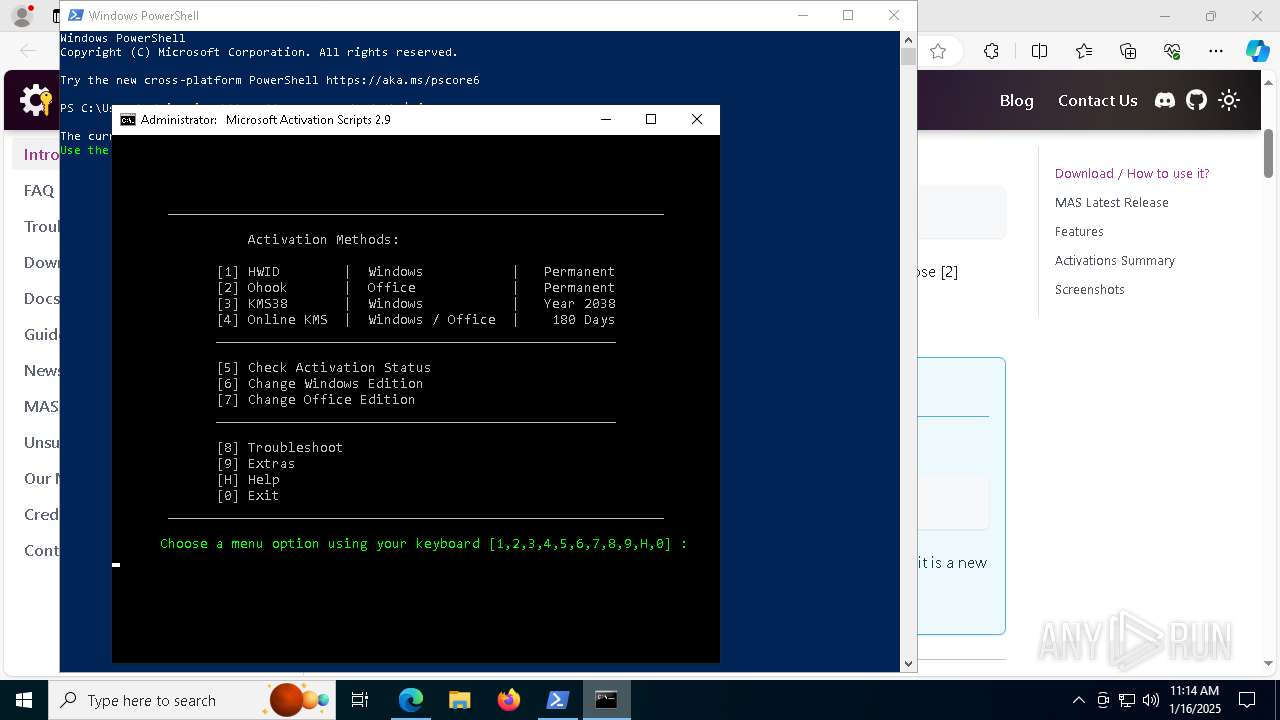
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
1 129
Monitored processes
982
Malicious processes
6
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
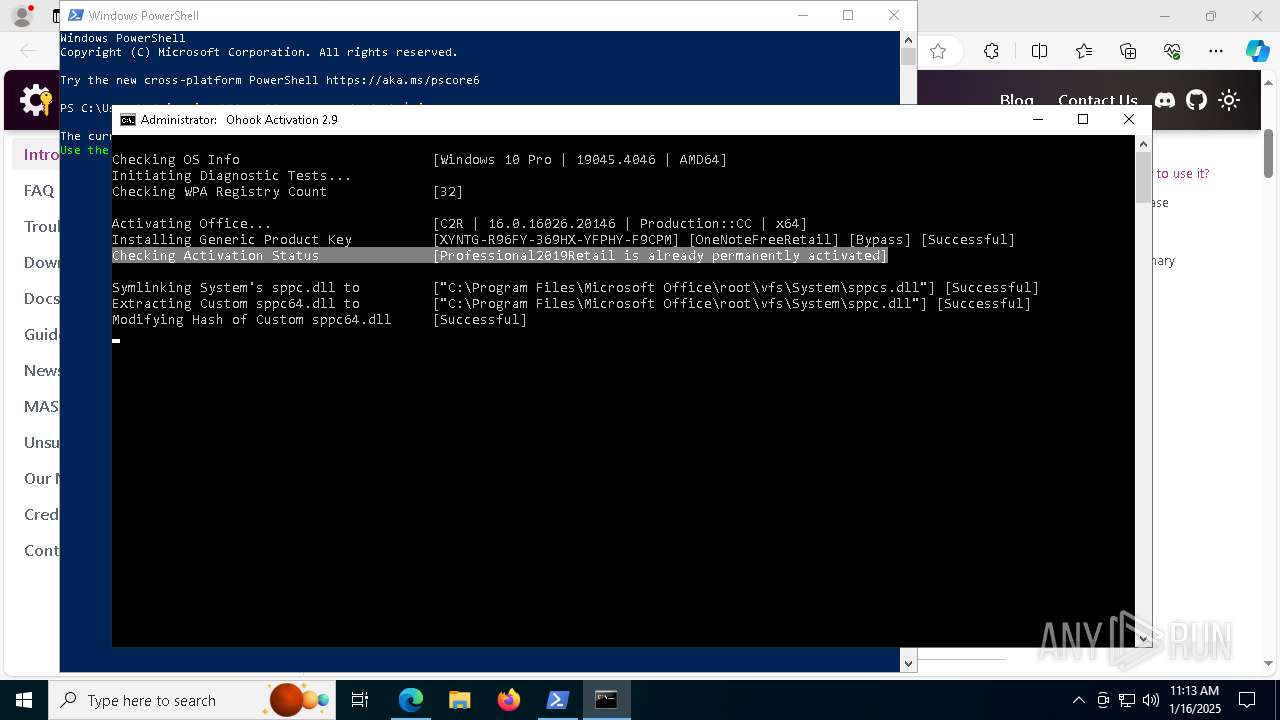
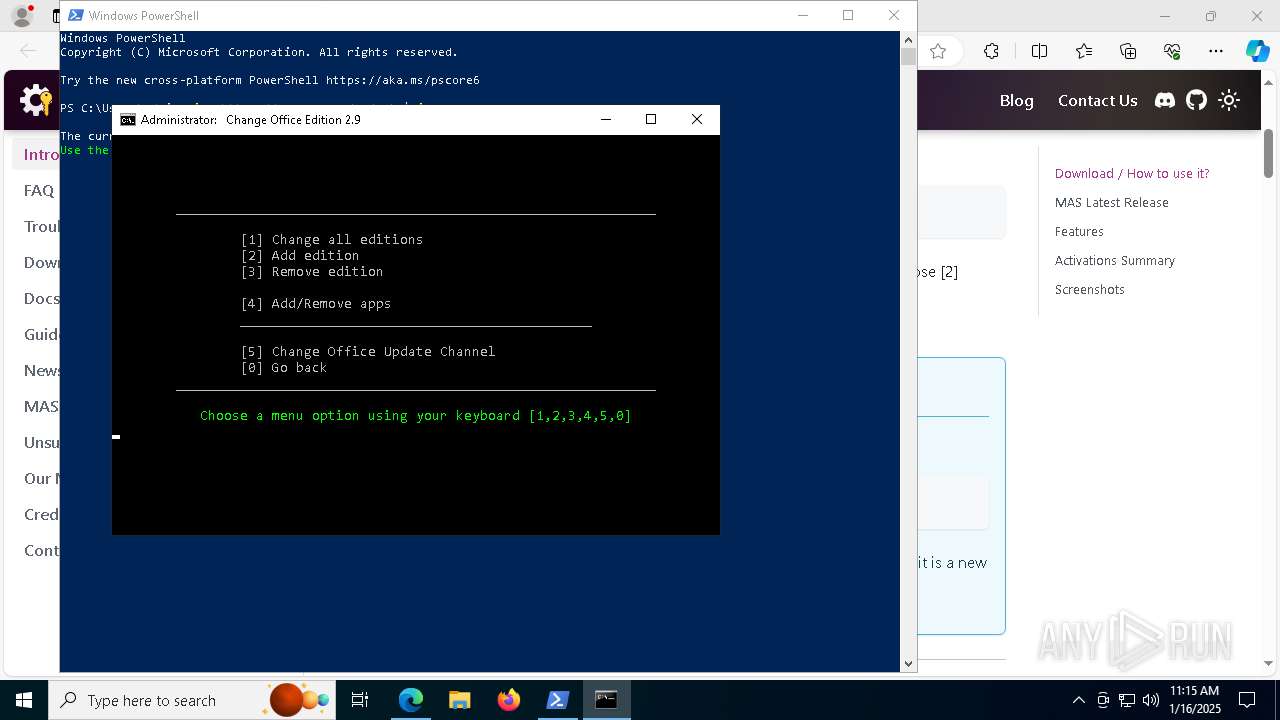
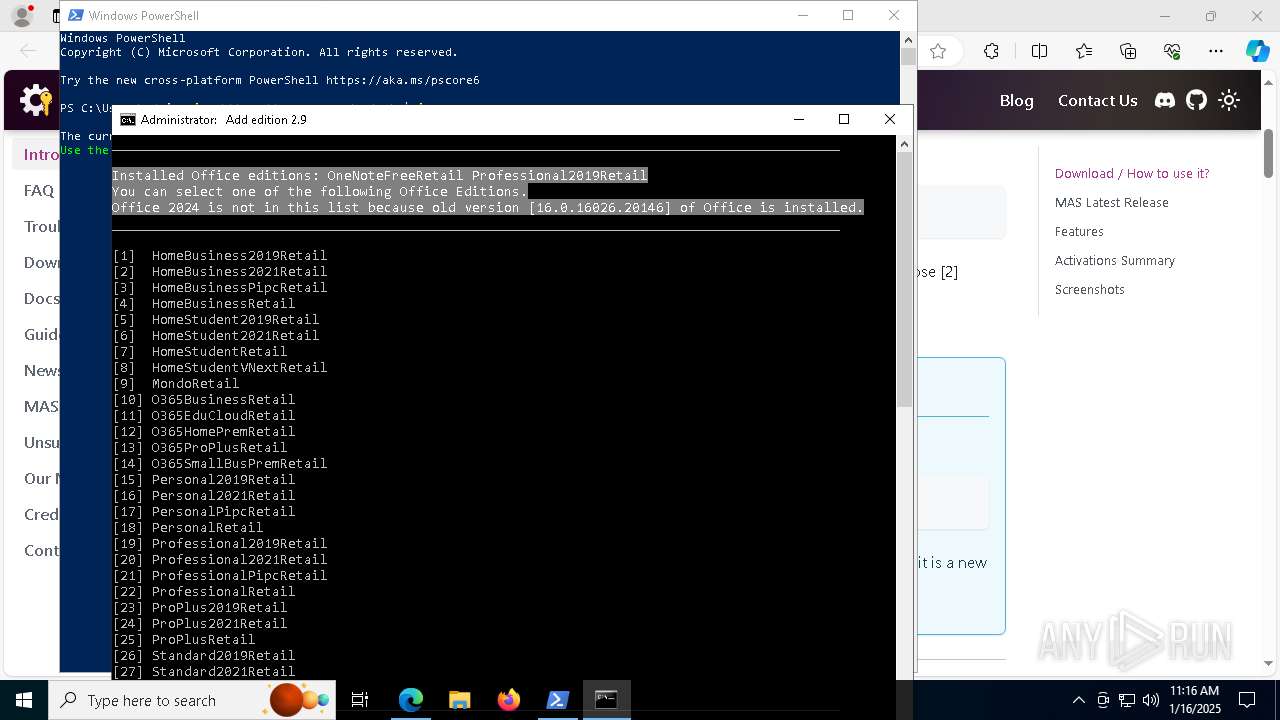
| 68 | C:\WINDOWS\System32\cmd.exe /S /D /c" echo "-Professional2019Retail- " " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | find /i "-PersonalPipcRetail-" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 236 | C:\WINDOWS\System32\cmd.exe /S /D /c" echo "-Professional2019Retail- " " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 308 | cmd /c exit /b 0 | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 308 | find /i "436366de-5579-4f24-96db-3893e4400030" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 440 | C:\WINDOWS\System32\cmd.exe /S /D /c" echo "0" " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 520 | C:\WINDOWS\System32\cmd.exe /S /D /c" echo "-Professional2019Retail- " " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 520 | C:\WINDOWS\System32\cmd.exe /S /D /c" echo " ProfessionalEducation ProfessionalWorkstation Education ProfessionalCountrySpecific ProfessionalSingleLanguage ServerRdsh IoTEnterprise Enterprise " " | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 520 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5656 --field-trial-handle=2364,i,6719803875575739907,14745645754763322564,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 524 | find /i "-ProPlus2021Volume-" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
253 527
Read events
253 495
Write events
23
Delete events
9
Modification events
| (PID) Process: | (5464) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (5464) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (5464) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (5464) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (5464) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 03561B24678A2F00 | |||
| (PID) Process: | (5464) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: A6B02324678A2F00 | |||
| (PID) Process: | (5464) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\262916 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {D688B358-B4A0-495D-9DBD-20141D2C6464} | |||
| (PID) Process: | (5464) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\262916 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {6434148F-1120-4704-9D73-BA7AD6757D2D} | |||
| (PID) Process: | (5464) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\262916 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {6DDD882A-7B8C-42FD-8900-B94775D60E39} | |||
| (PID) Process: | (5464) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\262916 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {9BE948A4-2712-446A-8DE9-958ED7296240} | |||
Executable files
112
Suspicious files
525
Text files
213
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF135084.TMP | — | |
MD5:— | SHA256:— | |||
| 5464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF135094.TMP | — | |
MD5:— | SHA256:— | |||
| 5464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF135084.TMP | — | |
MD5:— | SHA256:— | |||
| 5464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF1350a4.TMP | — | |
MD5:— | SHA256:— | |||
| 5464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF1350a4.TMP | — | |
MD5:— | SHA256:— | |||
| 5464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 5464 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
48
TCP/UDP connections
82
DNS requests
85
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5892 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2496 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7900 | svchost.exe | GET | 206 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1737475196&P2=404&P3=2&P4=BaUhM1iys0GHIFUt8vjA%2bNDhoASehIVlfjqmA3%2frWR9LSPO%2ftCx2pBtuLcYPdFhn8KrG6gy1sD%2fzjhcfk8MT%2bQ%3d%3d | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5536 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5536 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7900 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9b9f8fb4-8a65-41e4-bda3-5416858f0aeb?P1=1737475196&P2=404&P3=2&P4=BaUhM1iys0GHIFUt8vjA%2bNDhoASehIVlfjqmA3%2frWR9LSPO%2ftCx2pBtuLcYPdFhn8KrG6gy1sD%2fzjhcfk8MT%2bQ%3d%3d | unknown | — | — | whitelisted |
7900 | svchost.exe | HEAD | 200 | 199.232.214.172:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/2ed1297e-f6c9-4355-aec4-433ea371b116?P1=1737475196&P2=404&P3=2&P4=kREUmpgsLdbnvtphc3nyy6P9XhzwHalwOYCbhNgc7jeMpYqiQELX3nhFq%2b4LFr%2bU8ns0IJU%2fcrgeEjkWpUF1iw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5892 | svchost.exe | 23.48.23.177:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5892 | svchost.exe | 2.23.246.101:80 | www.microsoft.com | Ooredoo Q.S.C. | QA | whitelisted |
5064 | SearchApp.exe | 2.23.227.215:443 | www.bing.com | Ooredoo Q.S.C. | QA | whitelisted |
5064 | SearchApp.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5464 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6468 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
massgrave.dev |
| unknown |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
Threats
Process | Message |
|---|---|
Dism.exe | PID=3208 TID=7300 Initializing a provider store for the LOCAL session type. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=3208 TID=7300 Instantiating the Provider Store. - CDISMImageSession::get_ProviderStore |
Dism.exe | PID=3208 TID=7300 Provider has not previously been encountered. Attempting to initialize the provider. - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=3208 TID=7300 Loading Provider from location C:\Windows\System32\Dism\LogProvider.dll - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=3208 TID=7300 Attempting to initialize the logger from the Image Session. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=3208 TID=7300 Connecting to the provider located at C:\Windows\System32\Dism\LogProvider.dll. - CDISMProviderStore::Internal_LoadProvider |
DismHost.exe | PID=8108 TID=536 Encountered a loaded provider DISMLogger. - CDISMProviderStore::Internal_DisconnectProvider |
DismHost.exe | PID=8108 TID=536 Disconnecting Provider: DISMLogger - CDISMProviderStore::Internal_DisconnectProvider |
DismHost.exe | PID=8108 TID=536 Disconnecting the provider store - CDISMImageSession::Final_OnDisconnect |
Dism.exe | PID=3208 TID=7300 Encountered a loaded provider DISMLogger. - CDISMProviderStore::Internal_DisconnectProvider |