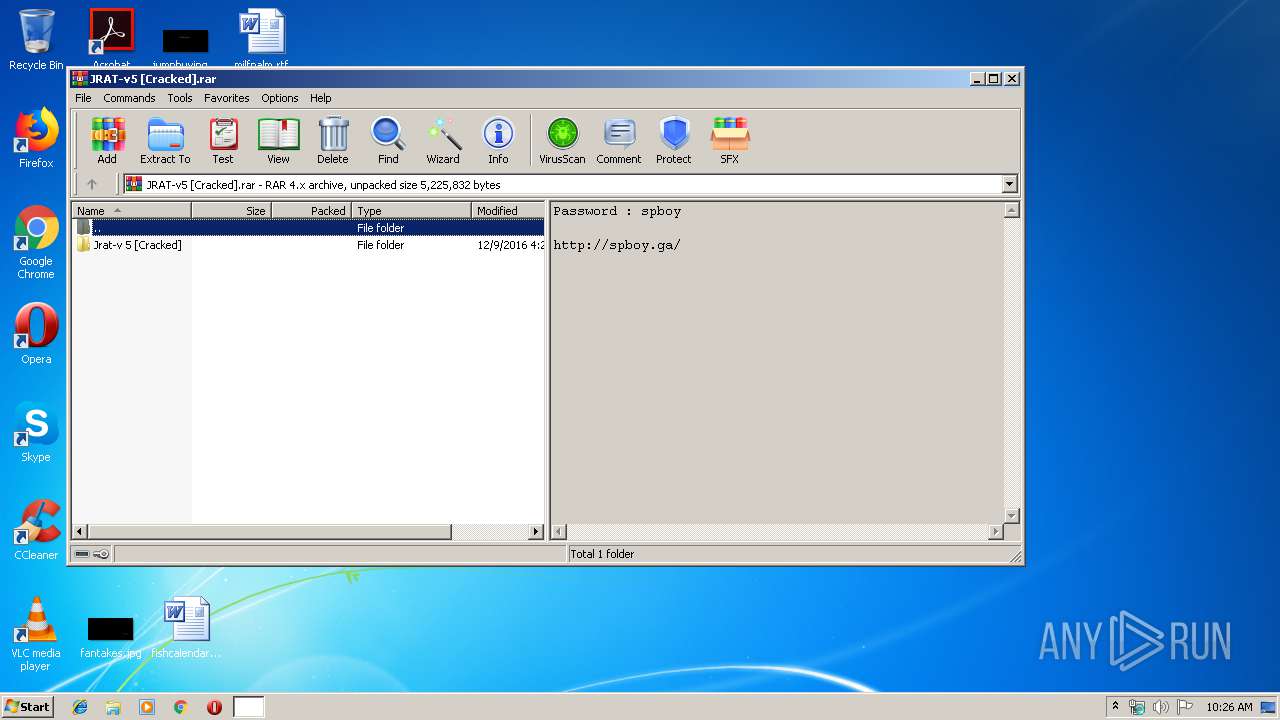
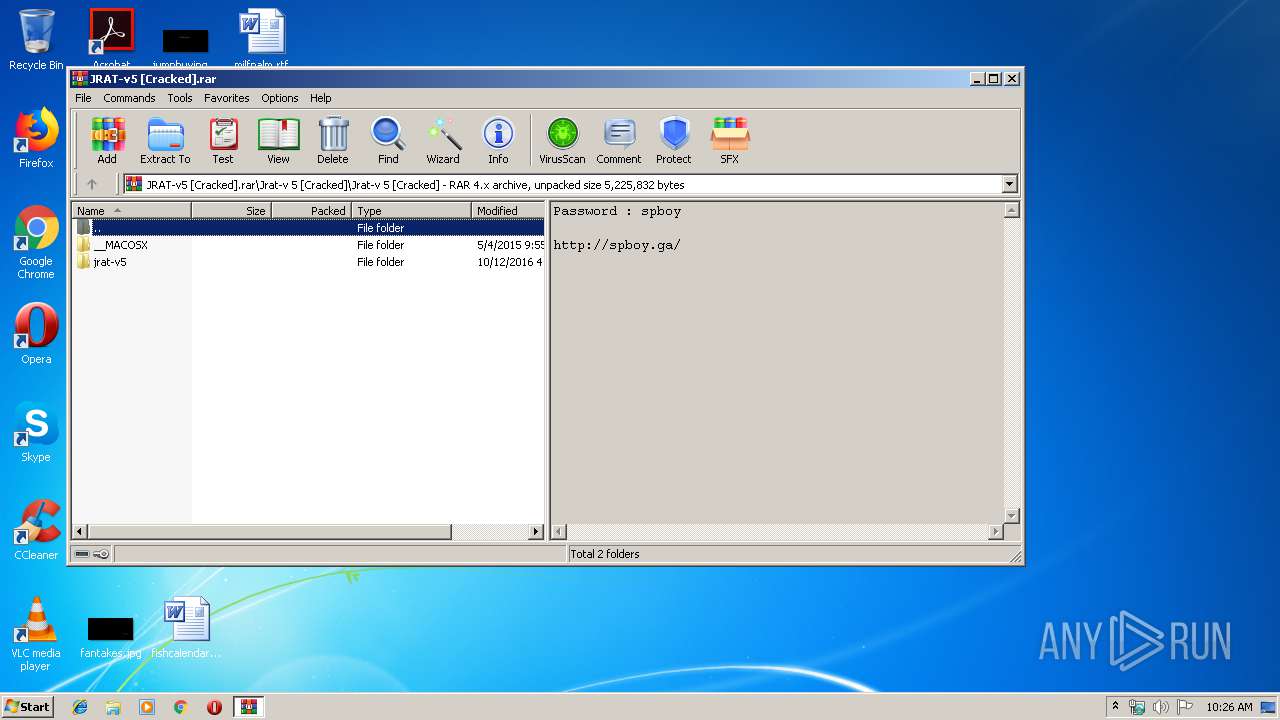
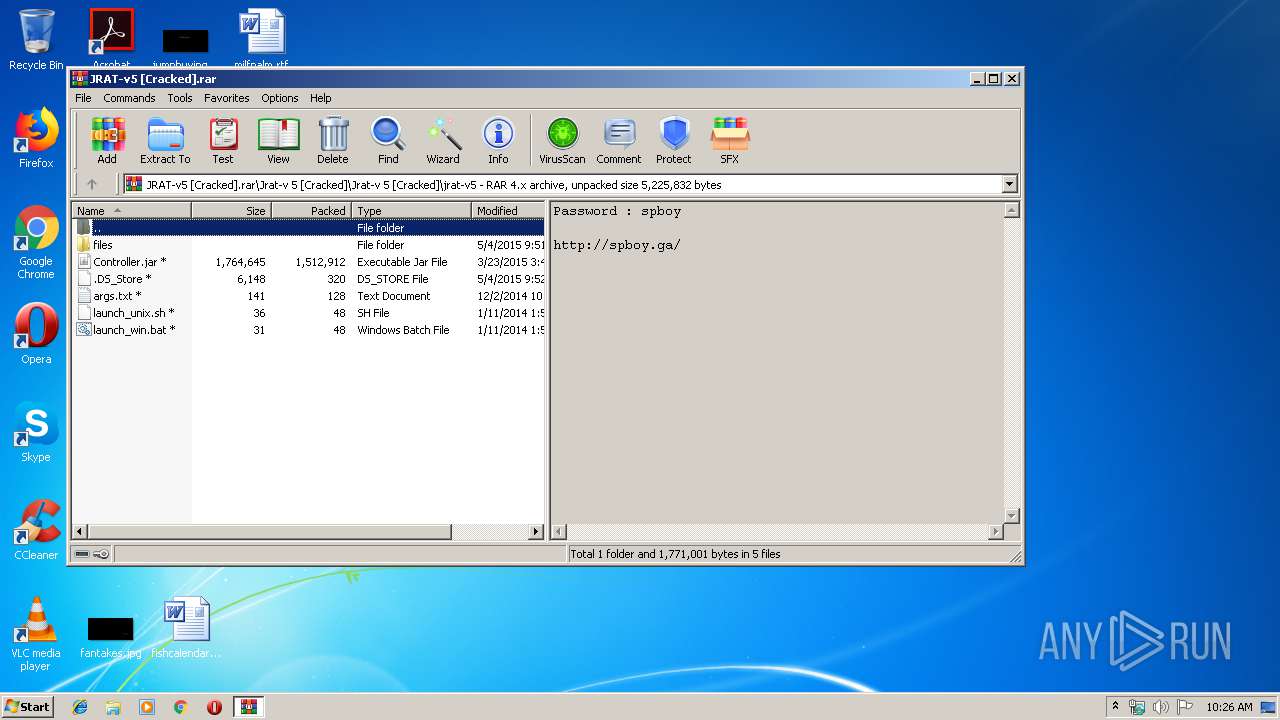
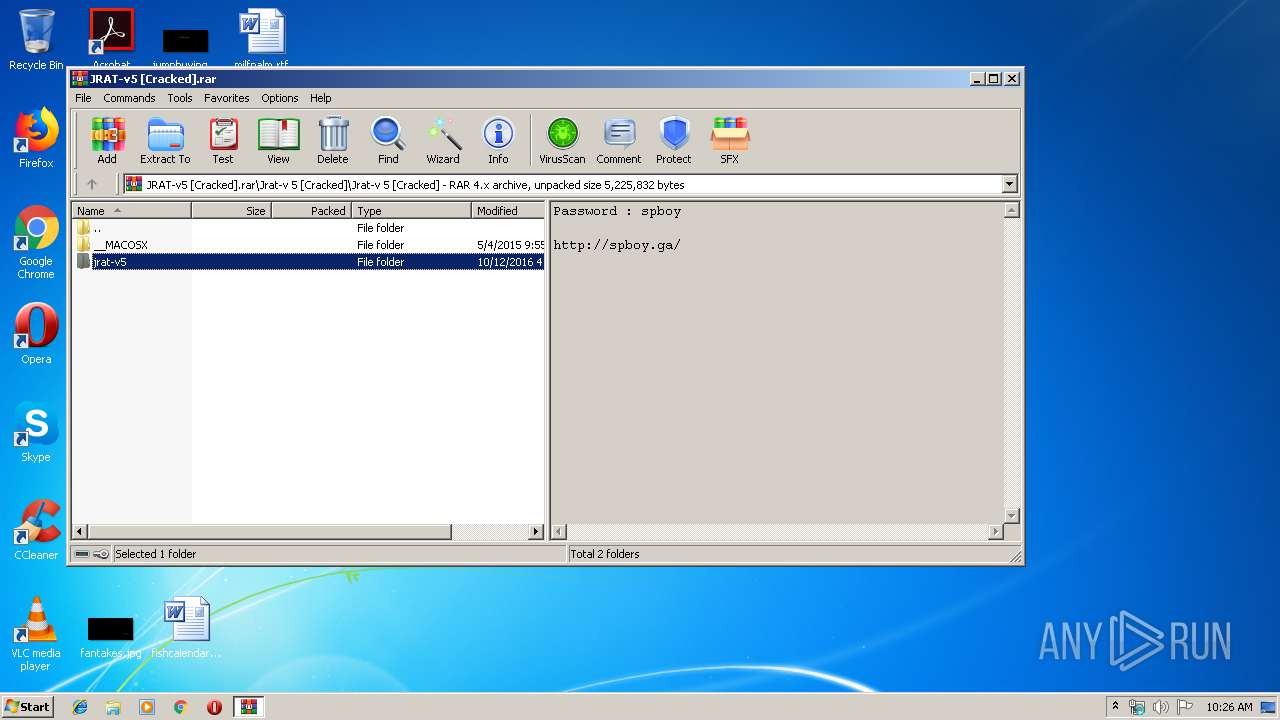
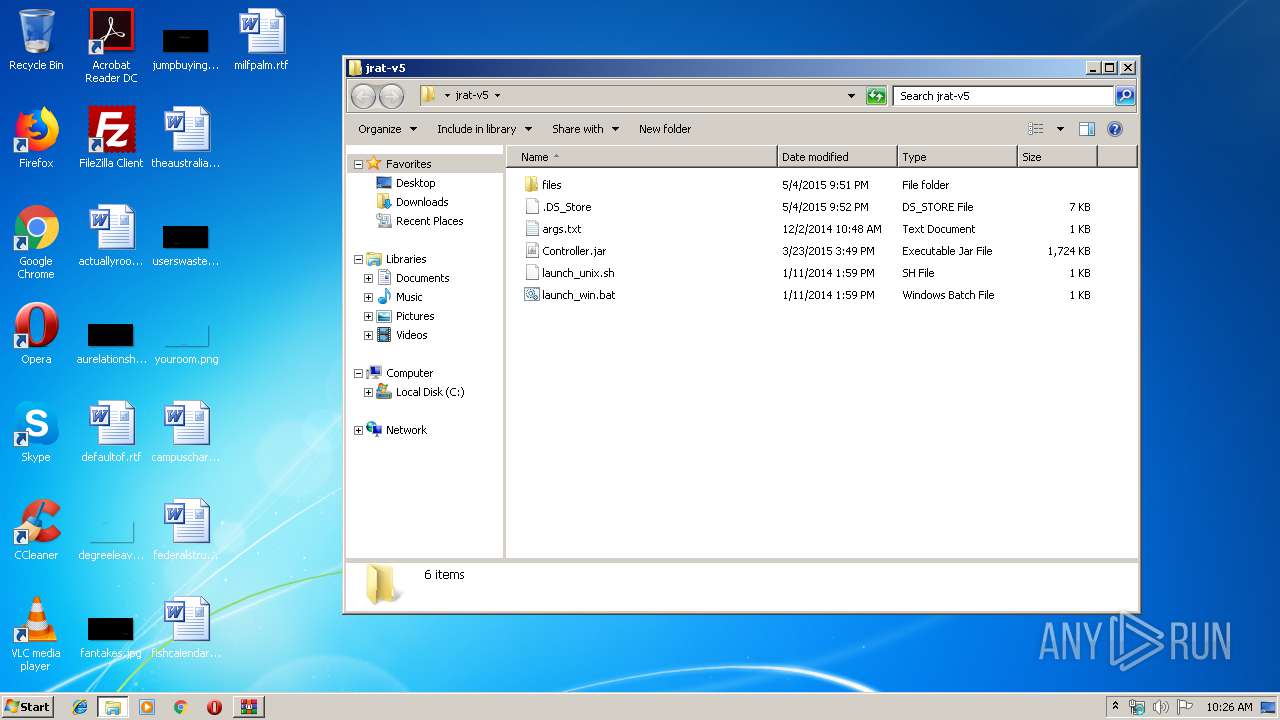
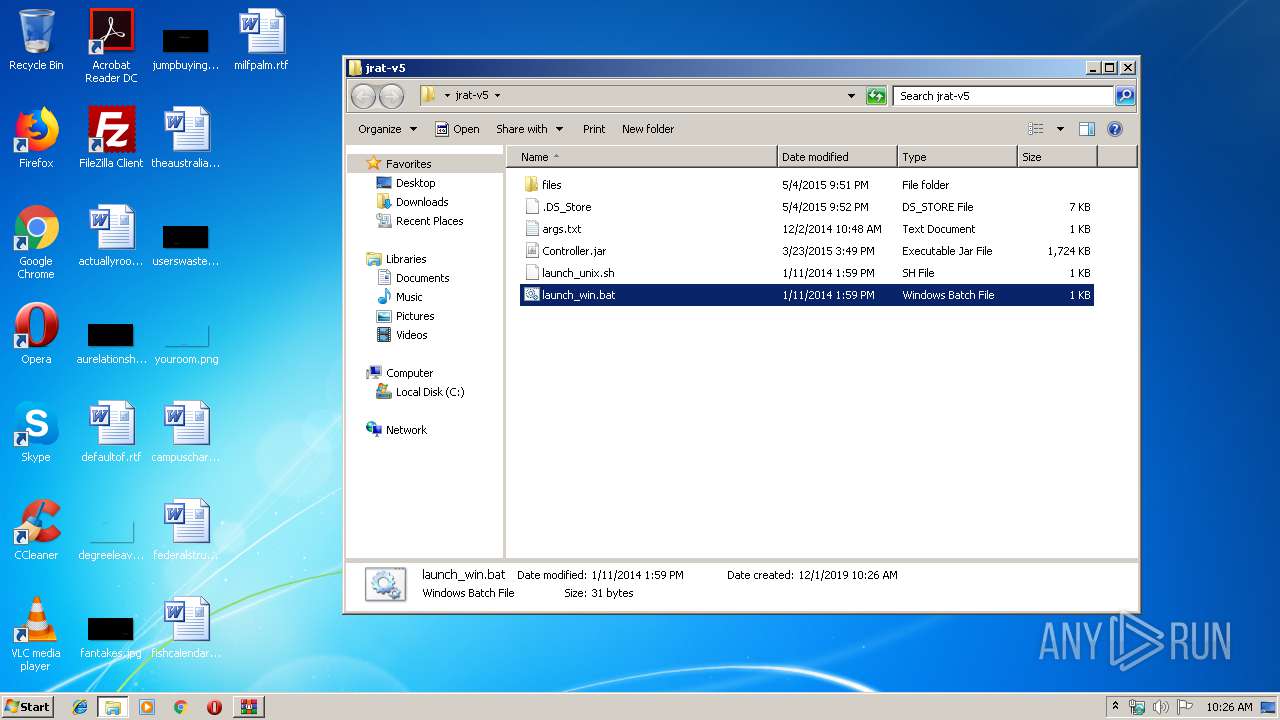
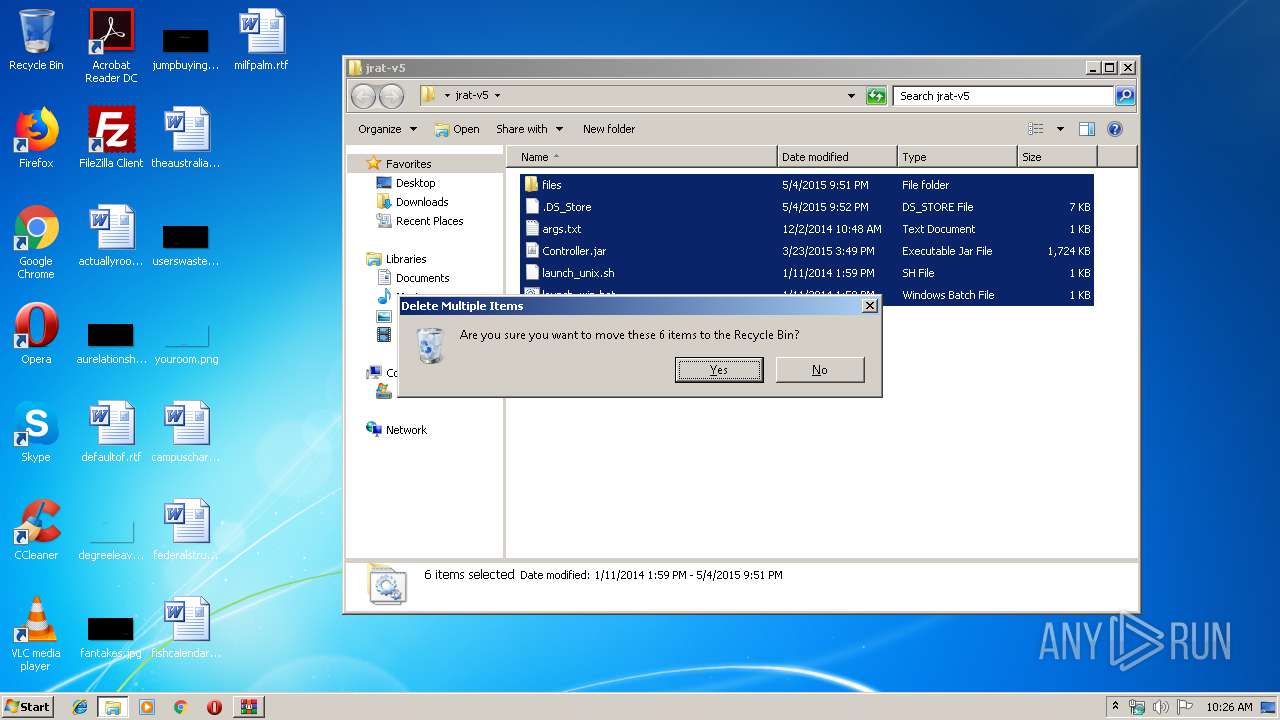
| File name: | JRAT-v5 [Cracked].rar |
| Full analysis: | https://app.any.run/tasks/0a3c50db-3b32-44fc-a216-9afb7a489140 |
| Verdict: | Malicious activity |
| Analysis date: | December 01, 2019, 10:25:49 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | 9AF69B1ECA1F2ADFE0CD3D1C18A99C13 |
| SHA1: | 9CC6EE1CEBC940A1F980D2DE14BBB1E3C05FF73B |
| SHA256: | 600A8AE0B72522092220C54CF8776EDEF0E05563686CAADA0E8BF97C0E906824 |
| SSDEEP: | 98304:I5tEd4baQPwTfUcv0TNnZ+7nZCm3qwnab/gSYS2B2YJxGODqJ:5dIQfunCnU58a8Aq3xGO2J |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates files in the user directory
- java.exe (PID: 820)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2204)
INFO
Manual execution by user
- cmd.exe (PID: 2188)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 404 |
|---|---|
| UncompressedSize: | 6148 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2015:05:04 21:52:12 |
| PackingMethod: | Best Compression |
| ArchivedFileName: | Jrat-v 5 [Cracked]\Jrat-v 5 [Cracked]\jrat-v5\.DS_Store |
Total processes
41
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
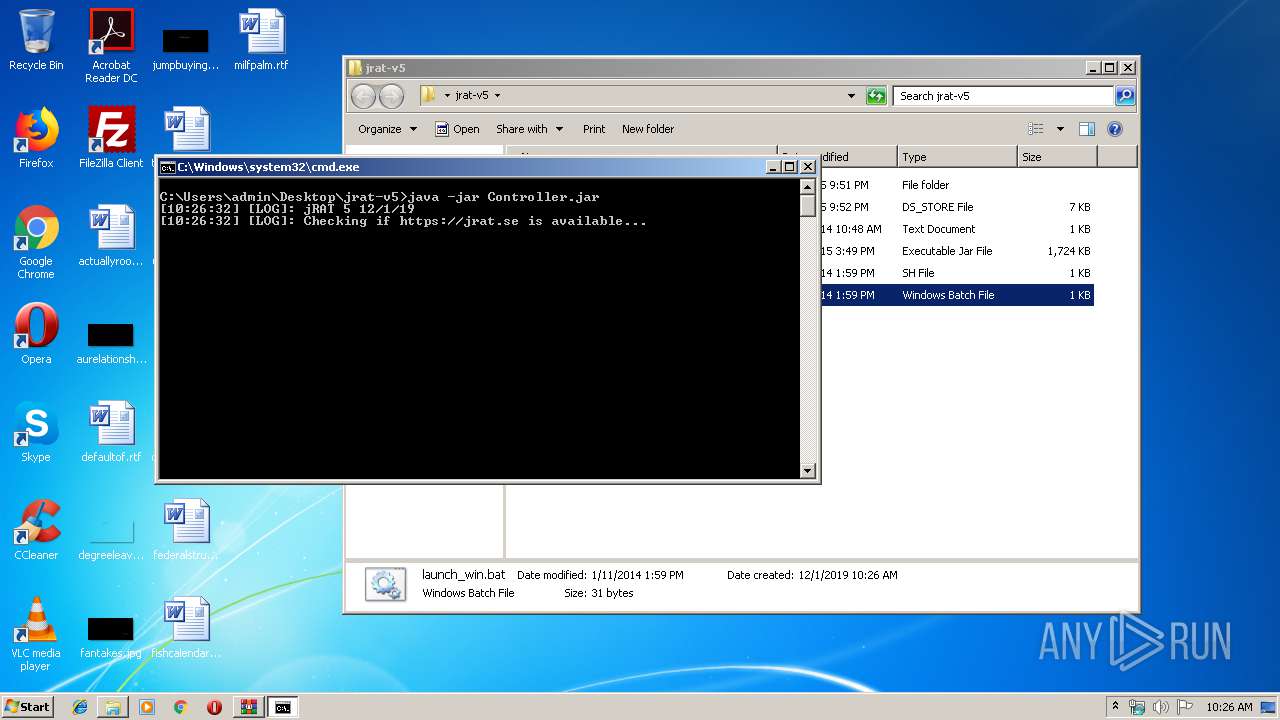
| 820 | java -jar Controller.jar | C:\ProgramData\Oracle\Java\javapath\java.exe | cmd.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 1 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2188 | cmd /c ""C:\Users\admin\Desktop\jrat-v5\launch_win.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2204 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\JRAT-v5 [Cracked].rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
445
Read events
433
Write events
12
Delete events
0
Modification events
| (PID) Process: | (2204) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2204) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2204) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2204) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\JRAT-v5 [Cracked].rar | |||
| (PID) Process: | (2204) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2204) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2204) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2204) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2204) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\acppage.dll,-6002 |
Value: Windows Batch File | |||
| (PID) Process: | (2204) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
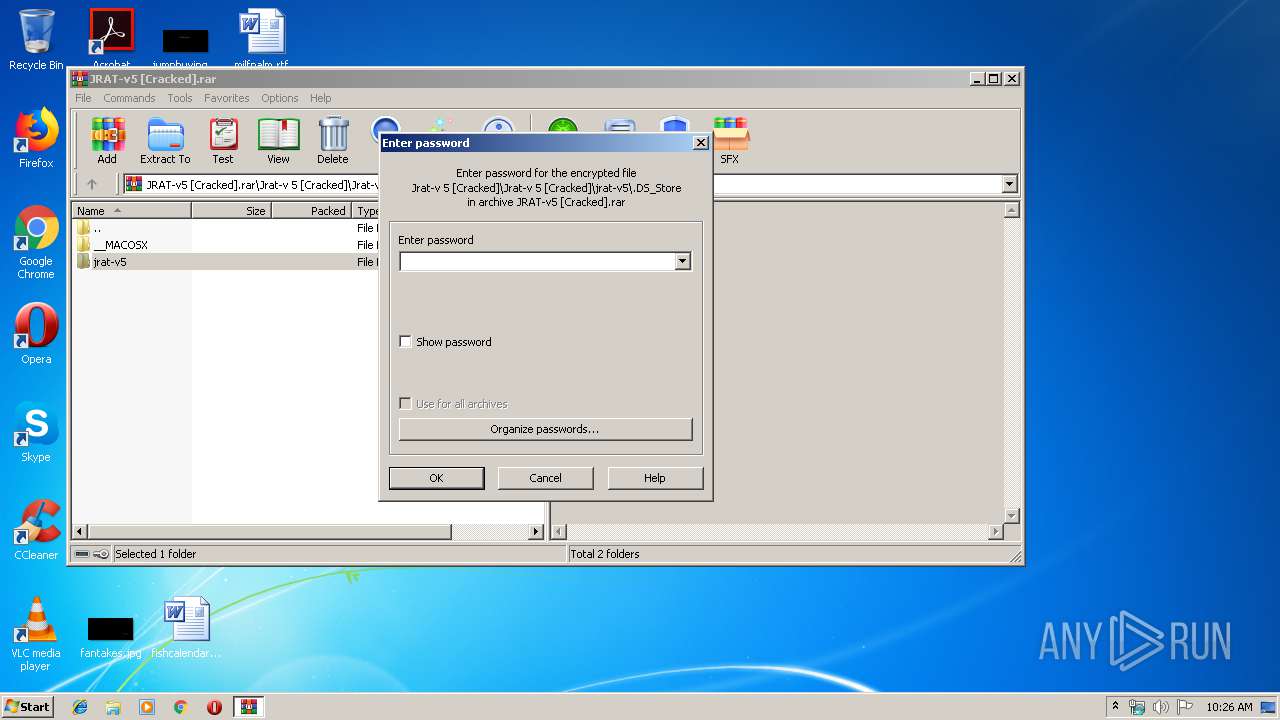
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
Executable files
6
Suspicious files
7
Text files
62
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2204 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2204.48212\Jrat-v 5 [Cracked]\Jrat-v 5 [Cracked]\jrat-v5\.DS_Store | ds_store | |
MD5:— | SHA256:— | |||
| 2204 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2204.48212\Jrat-v 5 [Cracked]\Jrat-v 5 [Cracked]\jrat-v5\files\args.txt | text | |
MD5:7CF243C2D9F34E67B84392AF58ACFB51 | SHA256:6BE2C420D91ECA524FBBDF1B38E67B6E45042E21DF9151AEE99FBF78ABF081B9 | |||
| 2204 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2204.48212\Jrat-v 5 [Cracked]\Jrat-v 5 [Cracked]\jrat-v5\files\Builder.exe | executable | |
MD5:4C9BCAF176B3BD8A7911F19FA8077490 | SHA256:DD811322B3C78642E3CA888D95F9C6F7D7B56247979358731BCAC341F29C6822 | |||
| 2204 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2204.48212\Jrat-v 5 [Cracked]\Jrat-v 5 [Cracked]\jrat-v5\Controller.jar | java | |
MD5:89FF401BC7177F8AB99DA16D6C8DEAF7 | SHA256:23B3FDA87490614383CD0D9A543E18541AF7A384B2CBC7606690A986F20493F5 | |||
| 2204 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2204.48212\Jrat-v 5 [Cracked]\Jrat-v 5 [Cracked]\jrat-v5\files\help\Building\Allowed OS.txt | text | |
MD5:0FA22E14F8AC90F0D5325F4342B1D3D5 | SHA256:421B4EA52CBD991B9F7574E1BB88154AECFFAEDF7F5D38588D80A2A63391ACE4 | |||
| 2204 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2204.48212\Jrat-v 5 [Cracked]\Jrat-v 5 [Cracked]\jrat-v5\files\domains.txt | text | |
MD5:3B67CA6E35C6FCB4F76EE630A1622D9B | SHA256:3BF11C79B63FCF7515B4063DC14615776B6466ED0FCBA85E8E8F23FE4FA1951A | |||
| 2204 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2204.48212\Jrat-v 5 [Cracked]\Jrat-v 5 [Cracked]\jrat-v5\files\help\Building\Final.txt | text | |
MD5:79CF1C4E71D0F41F9F3FBC9F062A7654 | SHA256:63B3328A95B3599862AA41F18F05F0016D45ADEB2577188F9388531C3F812BF1 | |||
| 2204 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2204.48212\Jrat-v 5 [Cracked]\Jrat-v 5 [Cracked]\jrat-v5\files\help\Building\Output.txt | text | |
MD5:57D29B12CD8D16FD486A41F8DEF978DC | SHA256:78A4700A6A0DA0E576A9D2EA7B19BCC22ABC6CD1199196DF8718A38BFD0DC58F | |||
| 2204 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2204.48212\Jrat-v 5 [Cracked]\Jrat-v 5 [Cracked]\jrat-v5\files\db.dat | binary | |
MD5:F0683F18498C7173B2CAF97D8ABF7271 | SHA256:22393F3CE3684BA7D5C23BA96F75DF50CB4D802557AAA7039A01BC4A76783261 | |||
| 2204 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2204.48212\Jrat-v 5 [Cracked]\Jrat-v 5 [Cracked]\jrat-v5\files\help\Building\Debug Messages.txt | text | |
MD5:40FD599C076B040142BC711C3C16D4C2 | SHA256:27ED169836BA901FAC6C1FBAF6FF236A474AF59A62B54D78C4A69BD6D77F0E21 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
2
Threats
2
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
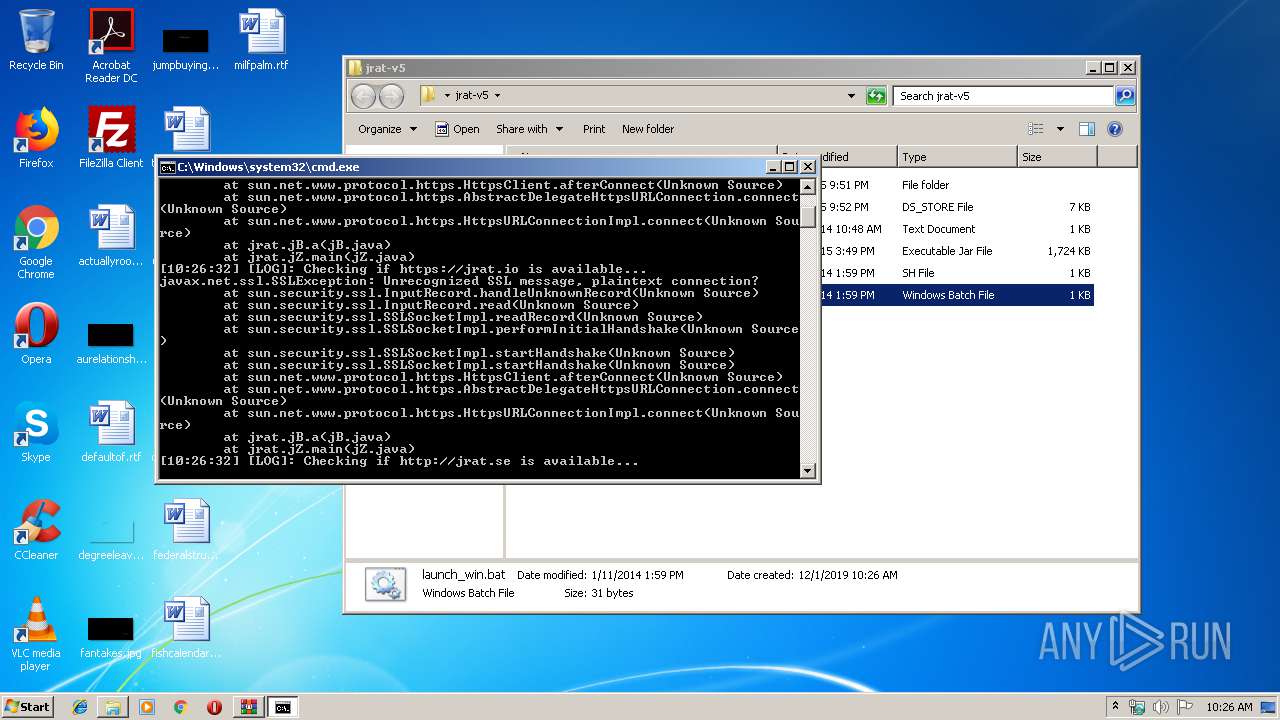
820 | java.exe | 94.140.116.29:443 | jrat.io | Makonix SIA | LV | unknown |
820 | java.exe | 140.82.56.237:443 | jrat.se | — | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
jrat.se |
| malicious |
jrat.io |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
820 | java.exe | Generic Protocol Command Decode | SURICATA Applayer Mismatch protocol both directions |
820 | java.exe | Generic Protocol Command Decode | SURICATA Applayer Mismatch protocol both directions |