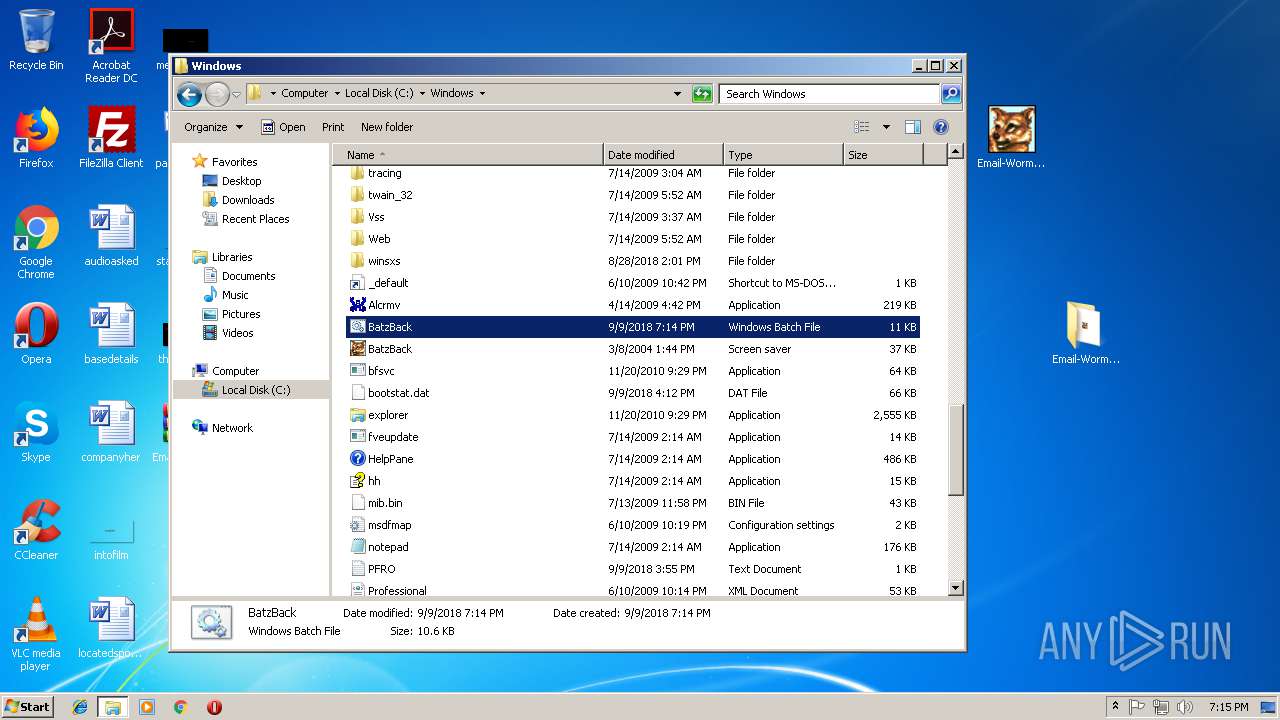
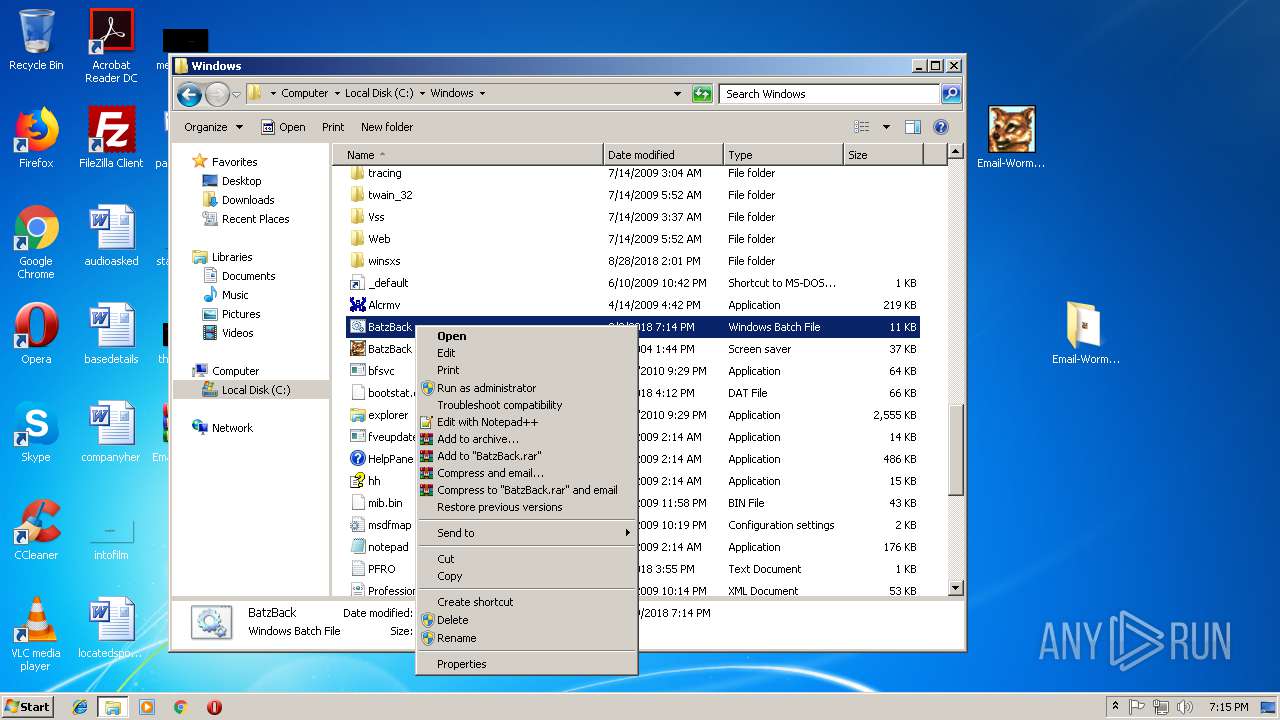
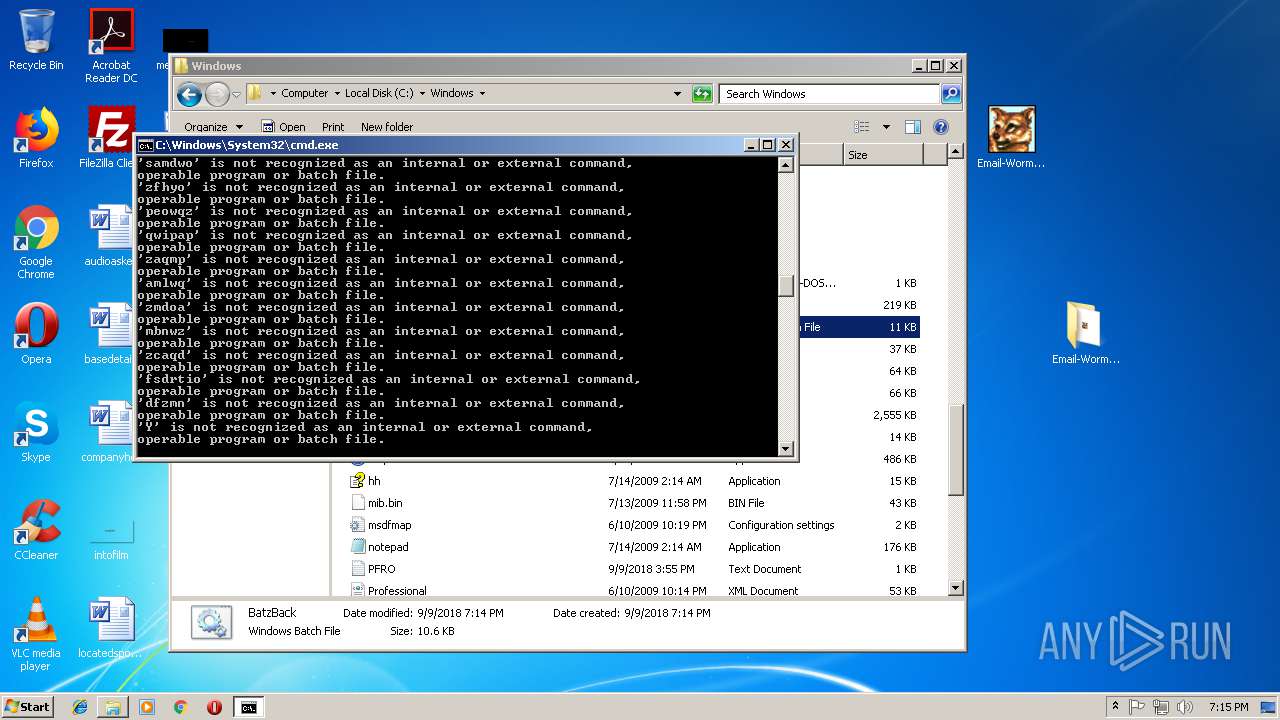
| File name: | Email-Worm.Win32.Batzback.a.zip |
| Full analysis: | https://app.any.run/tasks/d44befaa-2778-4589-baf9-d70a6988d4c7 |
| Verdict: | Malicious activity |
| Analysis date: | September 09, 2018, 18:13:12 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract |
| MD5: | F0048F1FBA8FAAC5A367A15DC4846587 |
| SHA1: | 7DA8C453762E9515A01D89B21F6BC2BA63DA8124 |
| SHA256: | 5FF66149B9C8DA72DFAE770FA5FC1A1E2ECA82EAF0F9C5813DE601A26F80EA33 |
| SSDEEP: | 768:2O+p813RV0Ebq19QI+sit+hHHH/q9SdiKoshYj/:b+p83H7bi9QI+sTdHf4SBosKj/ |
MALICIOUS
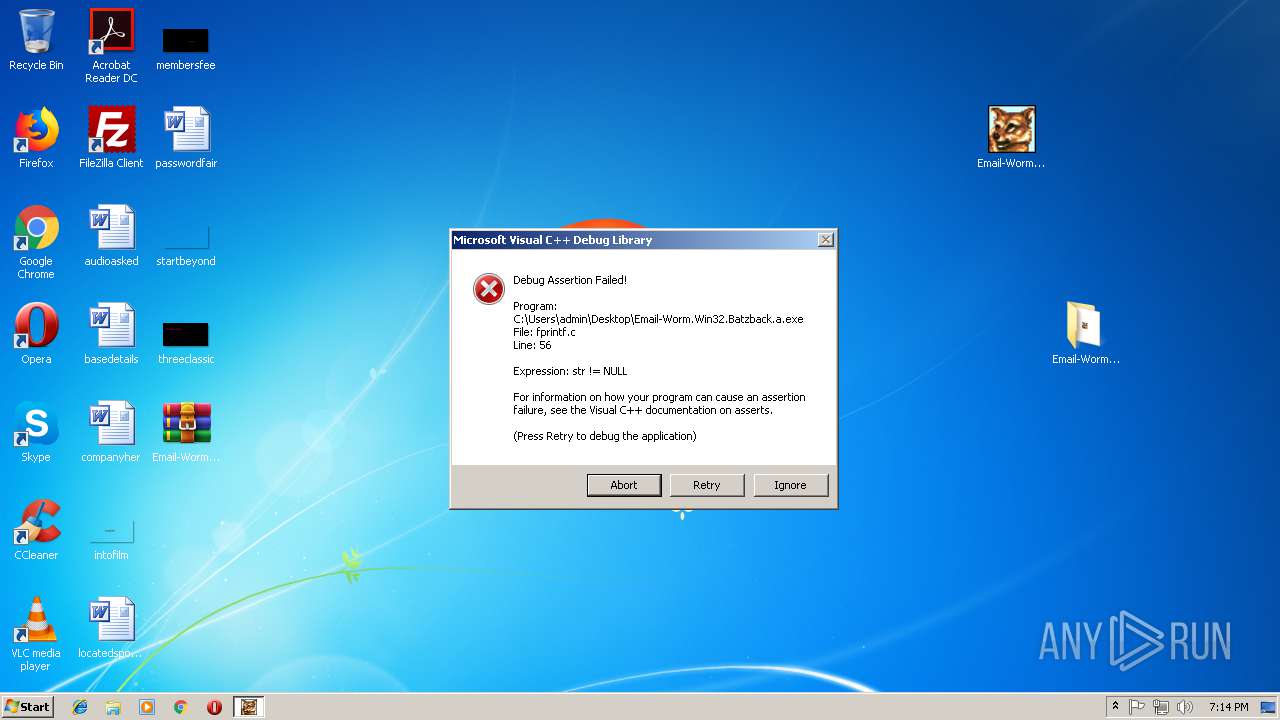
Changes the autorun value in the registry
- Email-Worm.Win32.Batzback.a.exe (PID: 4016)
- Email-Worm.Win32.Batzback.a.exe (PID: 3424)
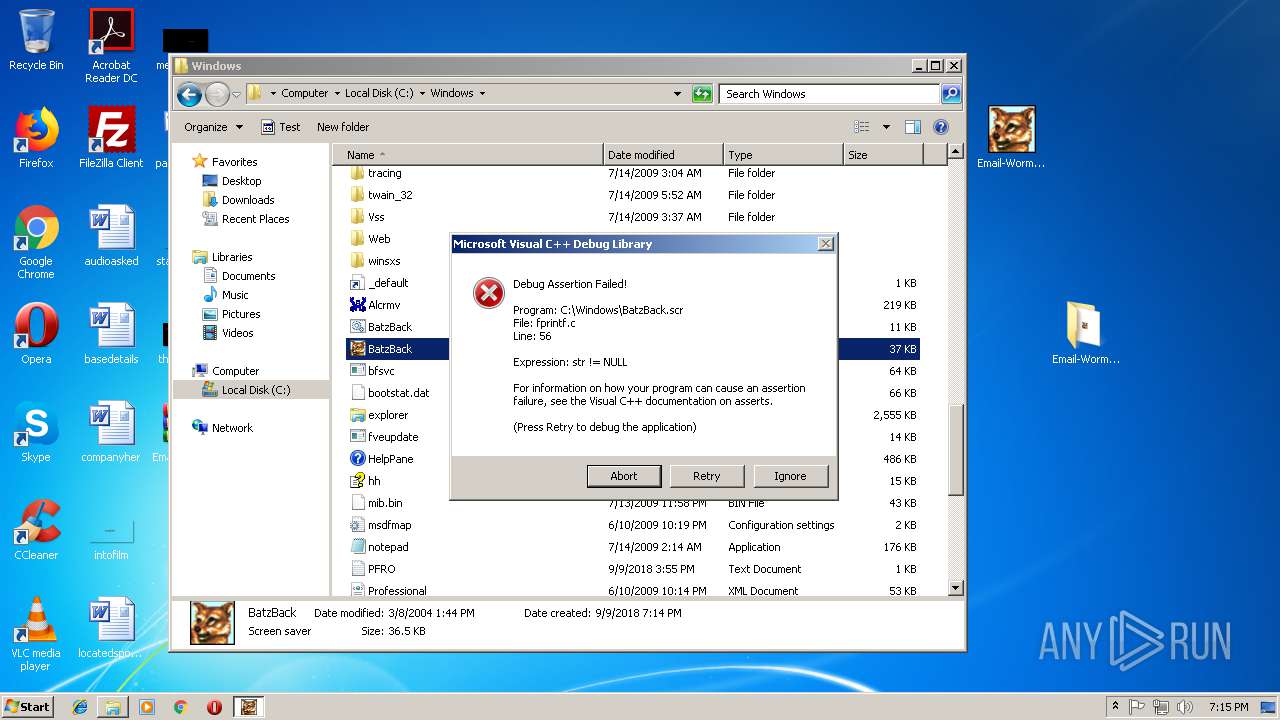
- BatzBack.scr (PID: 3296)
- Email-Worm.Win32.Batzback.a.exe (PID: 2792)
- BatzBack.scr (PID: 452)
- BatzBack.scr (PID: 3684)
Application was dropped or rewritten from another process
- Email-Worm.Win32.Batzback.a.exe (PID: 4016)
- Email-Worm.Win32.Batzback.a.exe (PID: 3424)
- BatzBack.scr (PID: 3684)
- Email-Worm.Win32.Batzback.a.exe (PID: 2792)
- BatzBack.scr (PID: 452)
- BatzBack.scr (PID: 3296)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3912)
- Email-Worm.Win32.Batzback.a.exe (PID: 2792)
- Email-Worm.Win32.Batzback.a.exe (PID: 3424)
Starts CMD.EXE for commands execution
- Email-Worm.Win32.Batzback.a.exe (PID: 3424)
- Email-Worm.Win32.Batzback.a.exe (PID: 2792)
Creates files in the Windows directory
- Email-Worm.Win32.Batzback.a.exe (PID: 3424)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2013:08:01 21:03:04 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Email-Worm.Win32.Batzback.a/ |
Total processes
70
Monitored processes
15
Malicious processes
2
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 272 | "C:\Program Files\Google\Update\GoogleUpdate.exe" /ua /installsource scheduler | C:\Program Files\Google\Update\GoogleUpdate.exe | — | taskeng.exe | |||||||||||
User: SYSTEM Company: Google Inc. Integrity Level: SYSTEM Description: Google Installer Exit code: 0 Version: 1.3.33.17 Modules
| |||||||||||||||
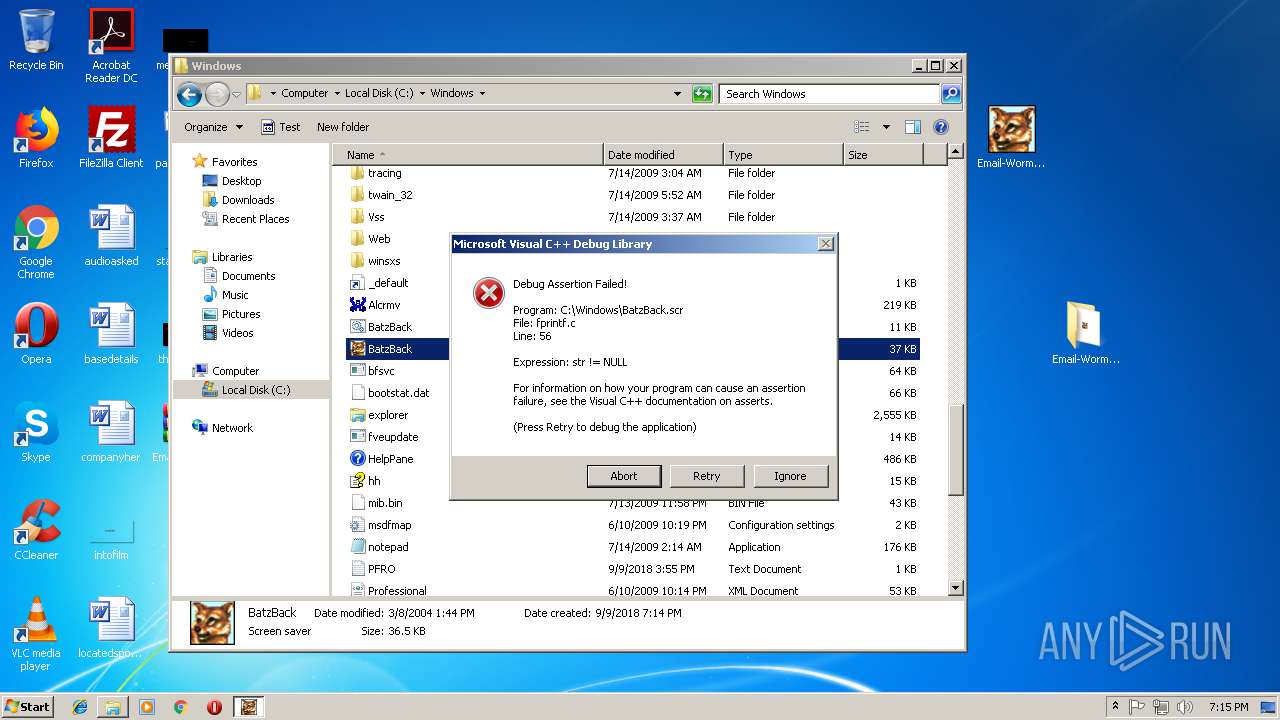
| 452 | "C:\Windows\BatzBack.scr" /S | C:\Windows\BatzBack.scr | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 2147483651 Modules
| |||||||||||||||
| 820 | "C:\Windows\System32\cmd.exe" /C "C:\Windows\BatzBack.Bat" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 255 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1396 | "C:\Windows\System32\NOTEPAD.EXE" C:\Windows\BatzBack.Bat | C:\Windows\System32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2692 | cmd /c ""C:\Windows\BatzBack.Bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 255 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2792 | "C:\Users\admin\Desktop\Email-Worm.Win32.Batzback.a.exe" | C:\Users\admin\Desktop\Email-Worm.Win32.Batzback.a.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3036 | cmd /c ""C:\Windows\BatzBack.Bat" " | C:\Windows\system32\cmd.exe | — | Email-Worm.Win32.Batzback.a.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 255 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3232 | cmd /c ""C:\Windows\BatzBack.Bat" " | C:\Windows\system32\cmd.exe | — | Email-Worm.Win32.Batzback.a.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 255 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3296 | "C:\Windows\BatzBack.scr" /S | C:\Windows\BatzBack.scr | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 2147483651 Modules
| |||||||||||||||
| 3424 | "C:\Users\admin\Desktop\Email-Worm.Win32.Batzback.a.exe" | C:\Users\admin\Desktop\Email-Worm.Win32.Batzback.a.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
517
Read events
476
Write events
41
Delete events
0
Modification events
| (PID) Process: | (3912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3912) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Email-Worm.Win32.Batzback.a.zip | |||
| (PID) Process: | (3912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (3912) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
5
Suspicious files
0
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2792 | Email-Worm.Win32.Batzback.a.exe | C:\Windows\BatzBack.scr | executable | |
MD5:1AD398260F65F5121E65D3C66E520903 | SHA256:E669931C039815510947AB19A578AAEF8DE1F76D763DE6306B2A0DED22AB3AB8 | |||
| 3424 | Email-Worm.Win32.Batzback.a.exe | C:\Windows\system32\BatzBack.scr | executable | |
MD5:1AD398260F65F5121E65D3C66E520903 | SHA256:E669931C039815510947AB19A578AAEF8DE1F76D763DE6306B2A0DED22AB3AB8 | |||
| 3424 | Email-Worm.Win32.Batzback.a.exe | C:\Windows\script.ini | text | |
MD5:88851E33134BA261192A7CFA43D29B2D | SHA256:0B10464AEA6720ED9B6263FBF950FA6D55C50257B26690FE03A142FAC2291400 | |||
| 3424 | Email-Worm.Win32.Batzback.a.exe | C:\Windows\BatzBack.scr | executable | |
MD5:1AD398260F65F5121E65D3C66E520903 | SHA256:E669931C039815510947AB19A578AAEF8DE1F76D763DE6306B2A0DED22AB3AB8 | |||
| 3424 | Email-Worm.Win32.Batzback.a.exe | C:\Windows\BatzBack.Bat | text | |
MD5:A966D64144078F8951DD2B931C09B20A | SHA256:F3283214B1E83832CE83687DA9165AD9F05C9A304F4B5E1B3E81FA7ED6D97A6A | |||
| 2792 | Email-Worm.Win32.Batzback.a.exe | C:\Windows\BatzBack.Bat | text | |
MD5:A966D64144078F8951DD2B931C09B20A | SHA256:F3283214B1E83832CE83687DA9165AD9F05C9A304F4B5E1B3E81FA7ED6D97A6A | |||
| 2792 | Email-Worm.Win32.Batzback.a.exe | C:\Windows\system32\BatzBack.scr | executable | |
MD5:1AD398260F65F5121E65D3C66E520903 | SHA256:E669931C039815510947AB19A578AAEF8DE1F76D763DE6306B2A0DED22AB3AB8 | |||
| 3912 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3912.49433\Email-Worm.Win32.Batzback.a\Email-Worm.Win32.Batzback.a | executable | |
MD5:1AD398260F65F5121E65D3C66E520903 | SHA256:E669931C039815510947AB19A578AAEF8DE1F76D763DE6306B2A0DED22AB3AB8 | |||
| 2792 | Email-Worm.Win32.Batzback.a.exe | C:\Windows\script.ini | text | |
MD5:88851E33134BA261192A7CFA43D29B2D | SHA256:0B10464AEA6720ED9B6263FBF950FA6D55C50257B26690FE03A142FAC2291400 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report