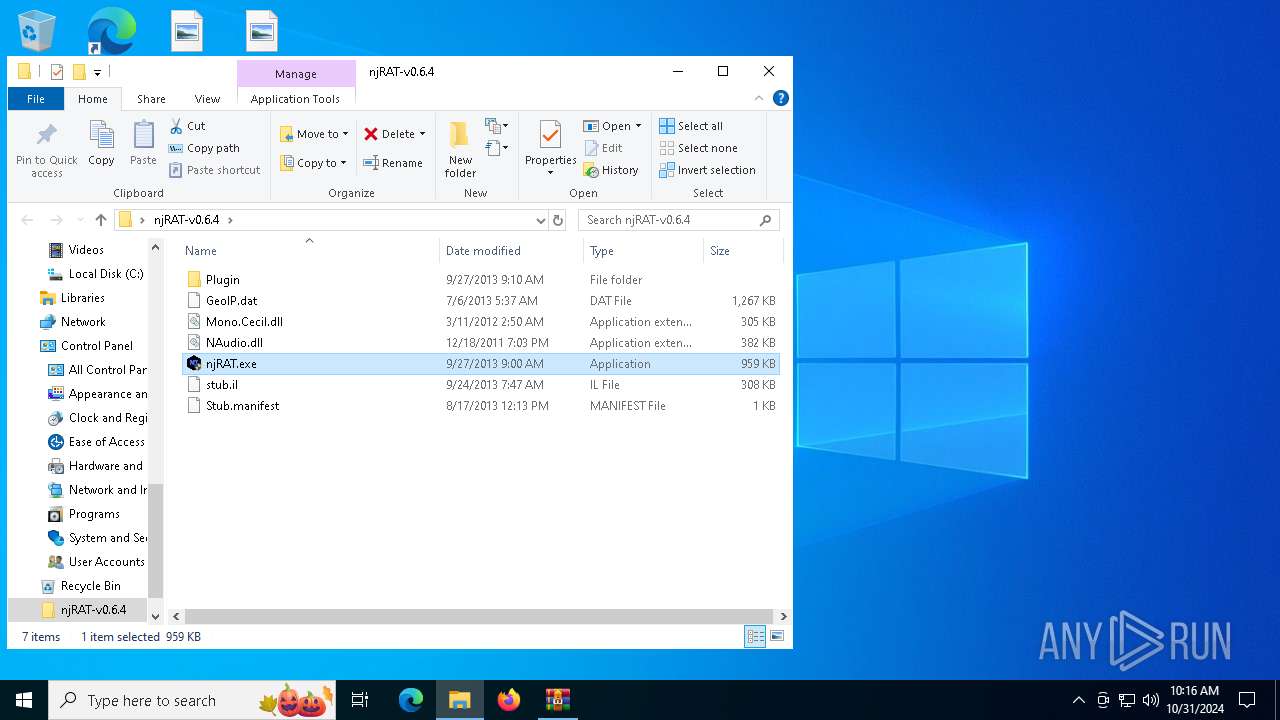
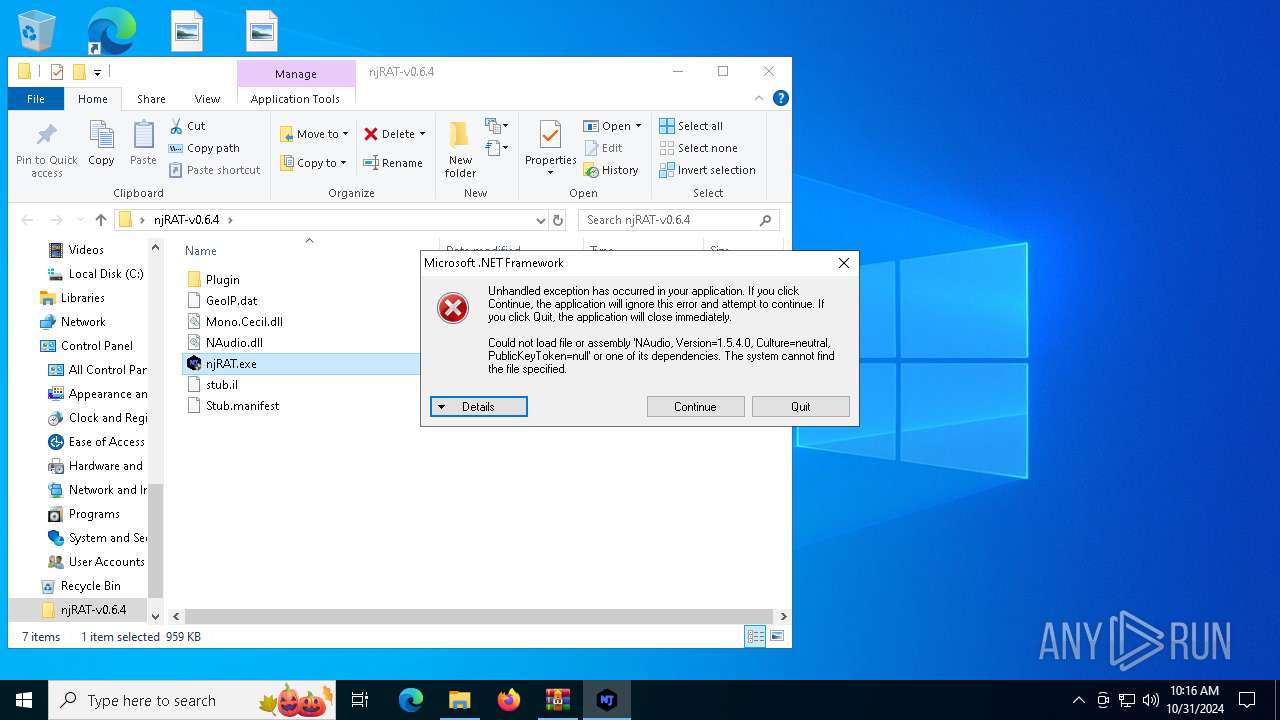
| File name: | njRAT-v0.6.4.zip |
| Full analysis: | https://app.any.run/tasks/f4301c38-7186-4d60-96db-5d3e0ad65123 |
| Verdict: | Malicious activity |
| Analysis date: | October 31, 2024, 10:16:33 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 3CCCE9D87CE9EA751ABEA094D1639D0A |
| SHA1: | 427867B229E02869AC68DE3A605998A585AD6A80 |
| SHA256: | 5FF121C57E4A2F2F75E4985660C9666A44B39EF2549B29B3A4D6A1E06E6E3F65 |
| SSDEEP: | 49152:pmRkTADhN5ulDigt8pri+kxs9/z/pH+3h:pmRulu48p2VU/z/S |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- njRAT.exe (PID: 1788)
- njq8.exe (PID: 2632)
- windows.exe (PID: 5464)
Starts itself from another location
- njq8.exe (PID: 2632)
Uses NETSH.EXE to add a firewall rule or allowed programs
- windows.exe (PID: 5464)
INFO
Manual execution by a user
- njRAT.exe (PID: 5172)
- njRAT.exe (PID: 1788)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6228)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2013:09:27 11:10:20 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | njRAT-v0.6.4/ |
Total processes
137
Monitored processes
10
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1788 | "C:\Users\admin\Desktop\njRAT-v0.6.4\njRAT.exe" | C:\Users\admin\Desktop\njRAT-v0.6.4\njRAT.exe | explorer.exe | ||||||||||||
User: admin Company: njq8 Integrity Level: HIGH Description: njRAT Version: 0.6.4.0 Modules
| |||||||||||||||
| 2172 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2236 | "C:\njRAT.exe" | C:\njRAT.exe | — | njRAT.exe | |||||||||||
User: admin Company: njq8 Integrity Level: HIGH Description: njRAT Version: 0.6.4.0 Modules
| |||||||||||||||
| 2632 | "C:\njq8.exe" | C:\njq8.exe | njRAT.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3648 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4228 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5172 | "C:\Users\admin\Desktop\njRAT-v0.6.4\njRAT.exe" | C:\Users\admin\Desktop\njRAT-v0.6.4\njRAT.exe | — | explorer.exe | |||||||||||
User: admin Company: njq8 Integrity Level: MEDIUM Description: njRAT Exit code: 3221226540 Version: 0.6.4.0 Modules
| |||||||||||||||
| 5464 | "C:\Users\admin\AppData\Local\Temp\windows.exe" | C:\Users\admin\AppData\Local\Temp\windows.exe | njq8.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 6228 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\njRAT-v0.6.4.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6296 | netsh firewall add allowedprogram "C:\Users\admin\AppData\Local\Temp\windows.exe" "windows.exe" ENABLE | C:\Windows\SysWOW64\netsh.exe | — | windows.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 060
Read events
3 956
Write events
91
Delete events
13
Modification events
| (PID) Process: | (6228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\njRAT-v0.6.4.zip | |||
| (PID) Process: | (6228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (6228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
| (PID) Process: | (6228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 13 |
Value: | |||
| (PID) Process: | (6228) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 12 |
Value: | |||
Executable files
13
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
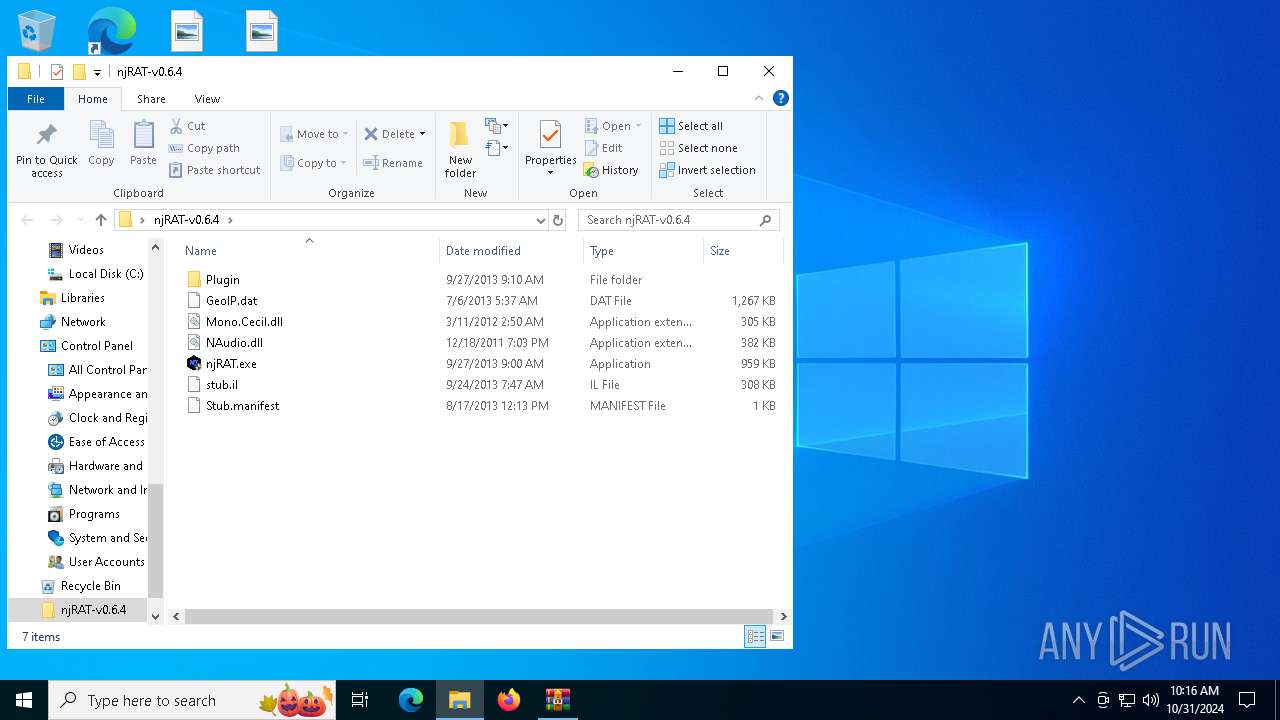
| 6228 | WinRAR.exe | C:\Users\admin\Desktop\njRAT-v0.6.4\Plugin\fm.dll | executable | |
MD5:51C2EE936DED2E55F8BCC8CBA6E3B330 | SHA256:F132324ACF09C0562A1CAD1288BFB4021BD991659126D21ECB9499938BF6ACB3 | |||
| 6228 | WinRAR.exe | C:\Users\admin\Desktop\njRAT-v0.6.4\njRAT.exe | executable | |
MD5:0431311B5F024D6E66B90D59491F2563 | SHA256:FD624AA205517580E83FAD7A4CE4D64863E95F62B34AC72647B1974A52822199 | |||
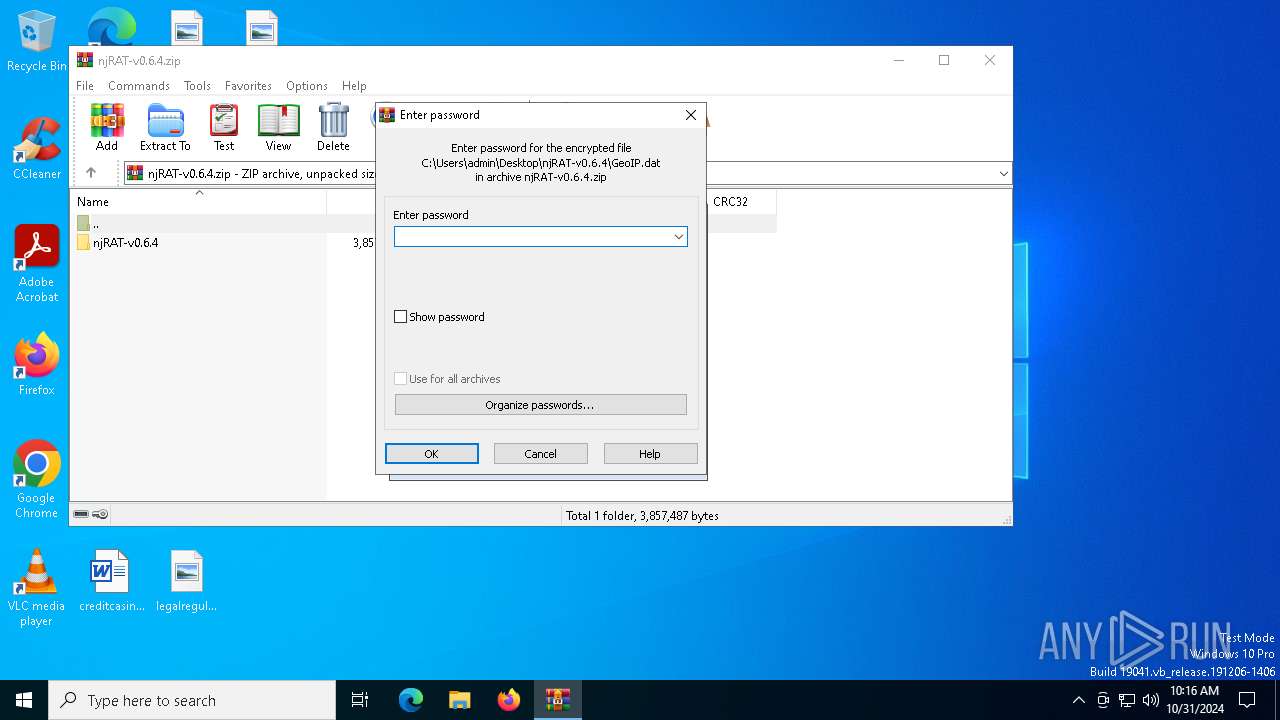
| 6228 | WinRAR.exe | C:\Users\admin\Desktop\njRAT-v0.6.4\GeoIP.dat | binary | |
MD5:797B96CC417D0CDE72E5C25D0898E95E | SHA256:8A0675001B5BC63D8389FC7ED80B4A7B0F9538C744350F00162533519E106426 | |||
| 6228 | WinRAR.exe | C:\Users\admin\Desktop\njRAT-v0.6.4\NAudio.dll | executable | |
MD5:422193AABD3D62275B2B98470279D9F2 | SHA256:CD9709BF1C7396F6FE3684B5177FA0890C706CA82E2B98BA58E8D8383632A3C8 | |||
| 6228 | WinRAR.exe | C:\Users\admin\Desktop\njRAT-v0.6.4\Plugin\pw.dll | executable | |
MD5:DB87DAF76C15F3808CEC149F639AA64F | SHA256:A3E4BEE1B6944AA9266BD58DE3F534A4C1896DF621881A5252A0D355A6E67C70 | |||
| 6228 | WinRAR.exe | C:\Users\admin\Desktop\njRAT-v0.6.4\Plugin\Mic.dll | executable | |
MD5:F4A19D968FF6F5AF1601B97F1756D6E3 | SHA256:FDE583027A692D210E8F1F73667FA0037705128ADE8BBFBC9B780F019EAD6672 | |||
| 6228 | WinRAR.exe | C:\Users\admin\Desktop\njRAT-v0.6.4\Plugin\cam.dll | executable | |
MD5:0A1CA904B3D688C01F4E5FAAE811922B | SHA256:B02C56D29447690CDAFD8F2F6877D526D1F6EFCAAE74017719C460D9B3EE38B8 | |||
| 6228 | WinRAR.exe | C:\Users\admin\Desktop\njRAT-v0.6.4\Stub.manifest | xml | |
MD5:4D18AC38A92D15A64E2B80447B025B7E | SHA256:835A00D6E7C43DB49AE7B3FA12559F23C2920B7530F4D3F960FD285B42B1EFB5 | |||
| 6228 | WinRAR.exe | C:\Users\admin\Desktop\njRAT-v0.6.4\Plugin\sc2.dll | executable | |
MD5:BE128028F705B0233DAD7D1F603BDF78 | SHA256:D3DCB25F9004F6FCE3F3D94406AD6845D996CDA2F106A203082AED39A84FAC4E | |||
| 6228 | WinRAR.exe | C:\Users\admin\Desktop\njRAT-v0.6.4\stub.il | text | |
MD5:1B92496B750A26F2450E34500A2C4215 | SHA256:A1B65F18C7E882B1606A4EF9387D8988E6FD755D7D03214B677AD528A487D73A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
43
DNS requests
24
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5852 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3740 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5236 | SIHClient.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5236 | SIHClient.exe | GET | 200 | 23.32.185.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4360 | SearchApp.exe | 104.126.37.162:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.zapto .org |
2172 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.zapto .org |
2172 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.zapto .org |
2172 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.zapto .org |
2172 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.zapto .org |
2172 | svchost.exe | Potentially Bad Traffic | ET POLICY DNS Query to DynDNS Domain *.zapto .org |