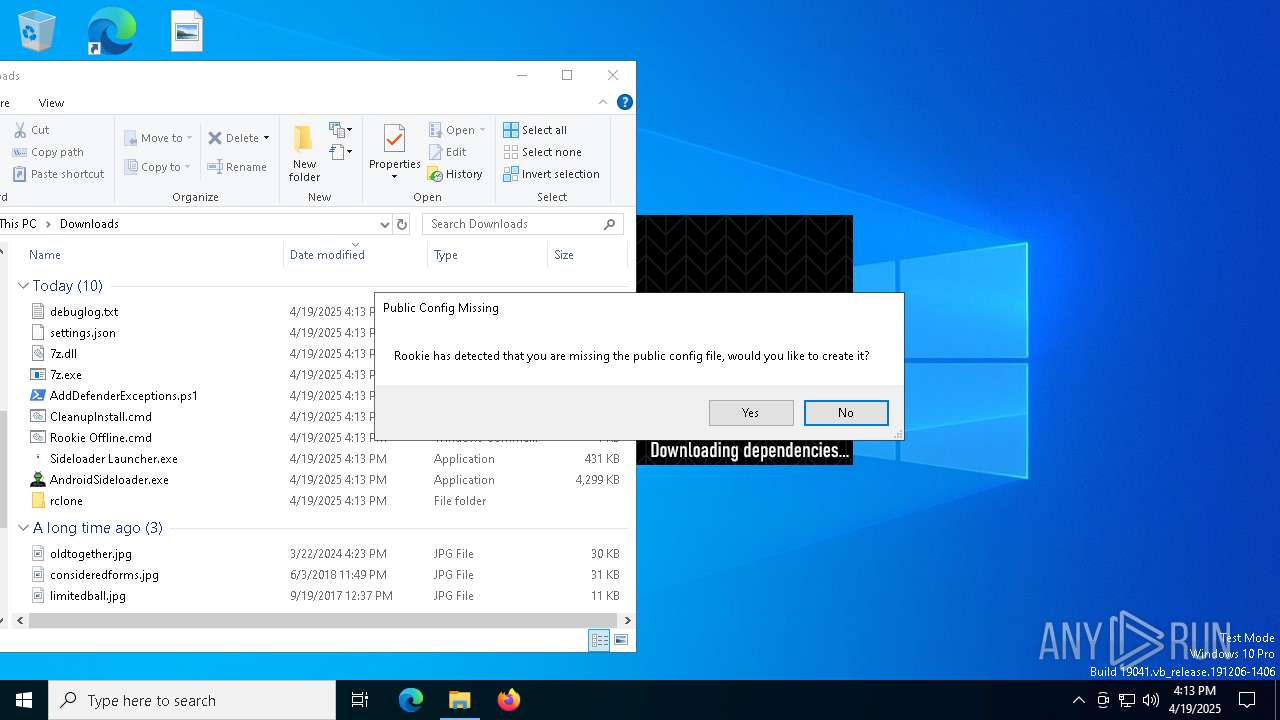
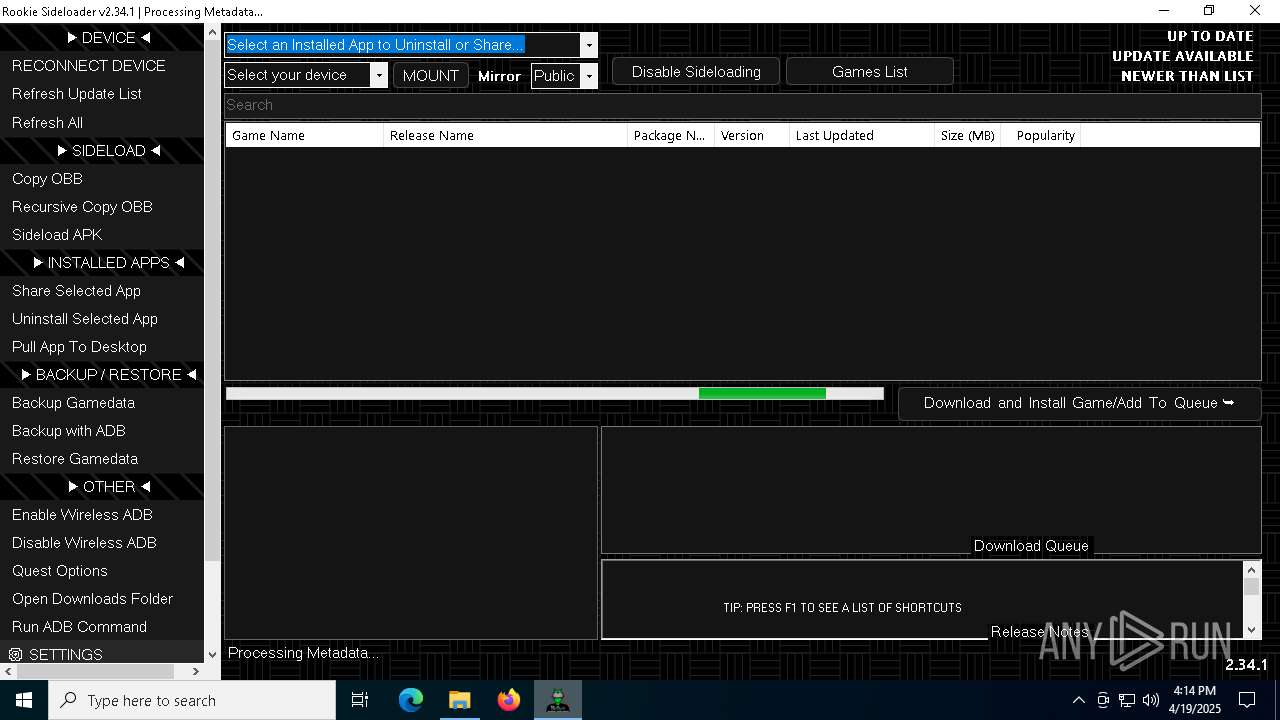
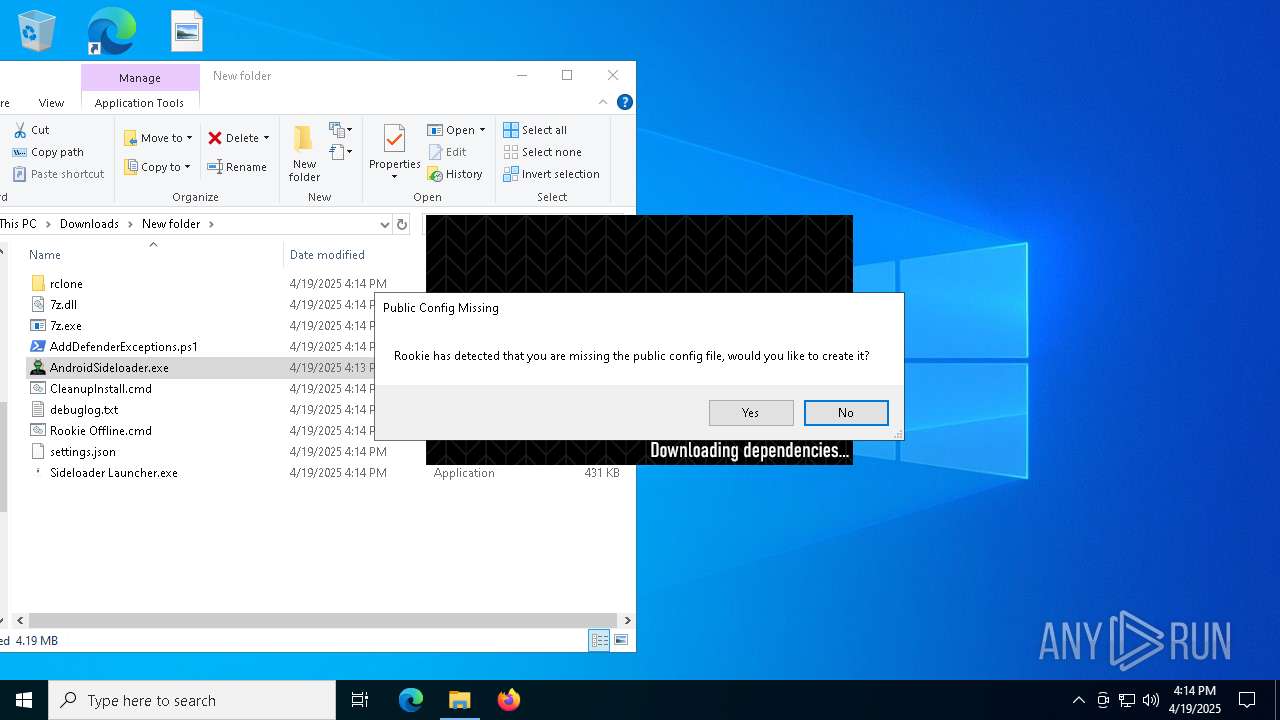
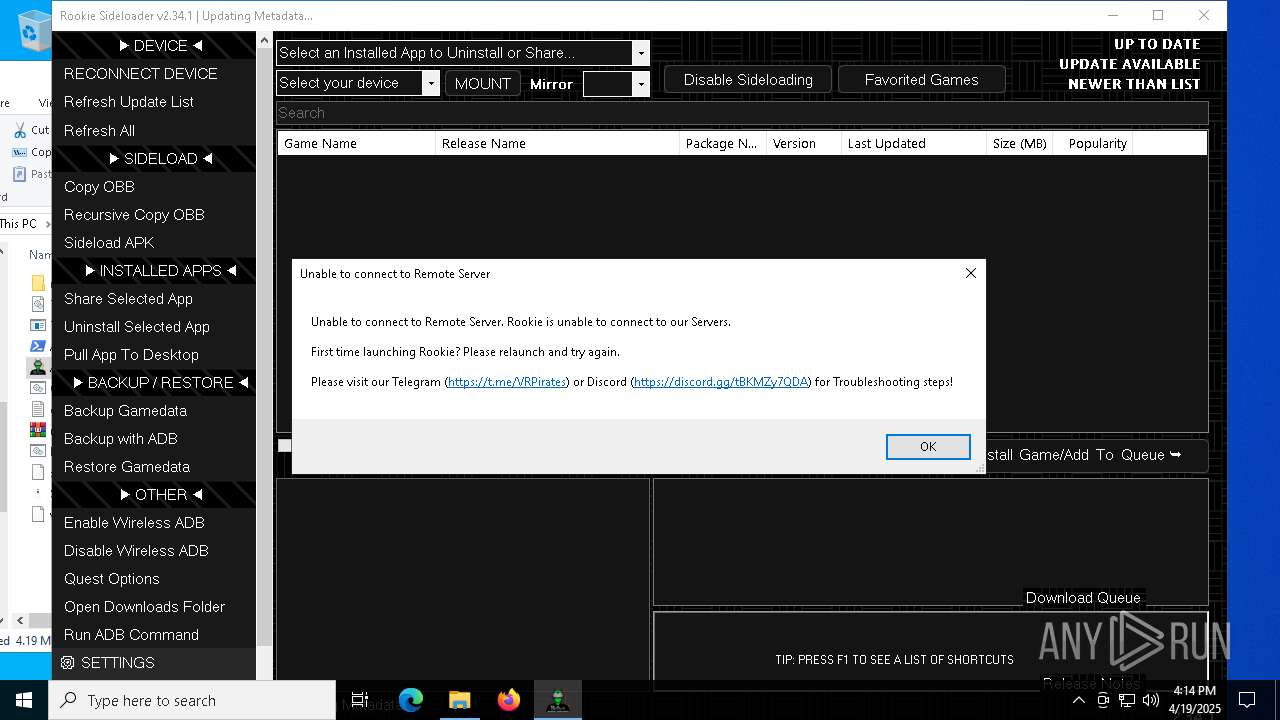
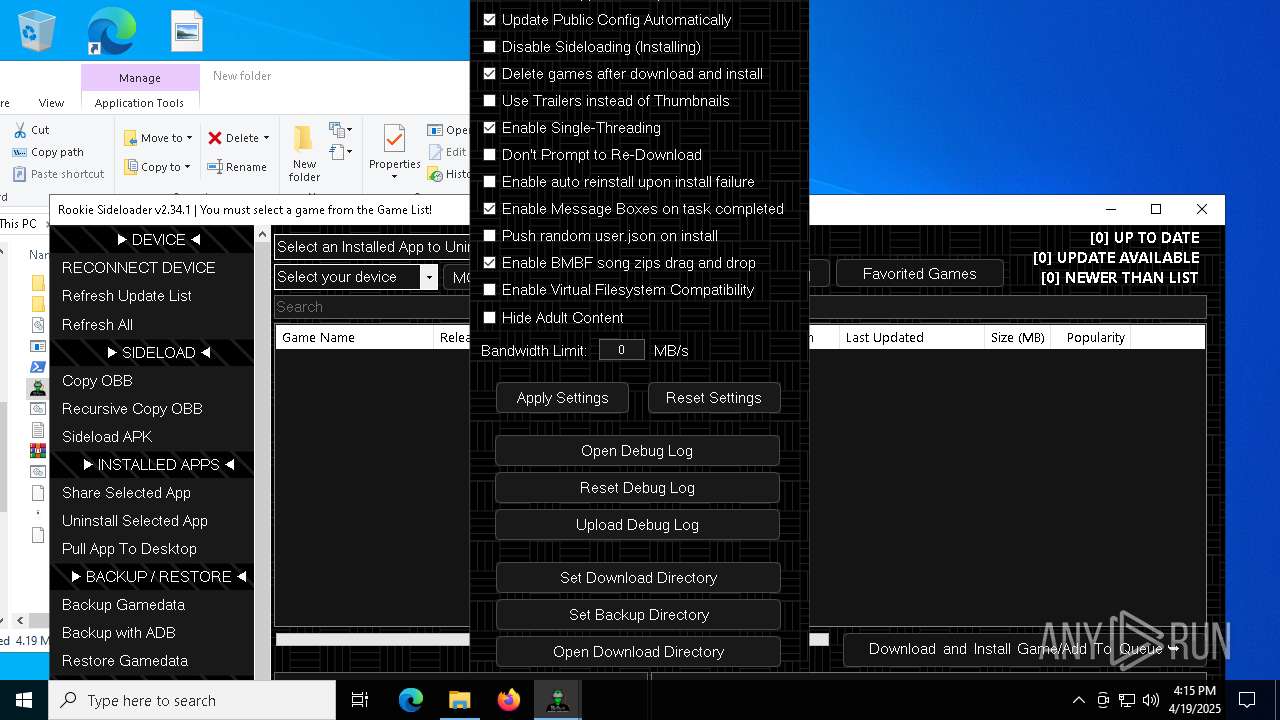
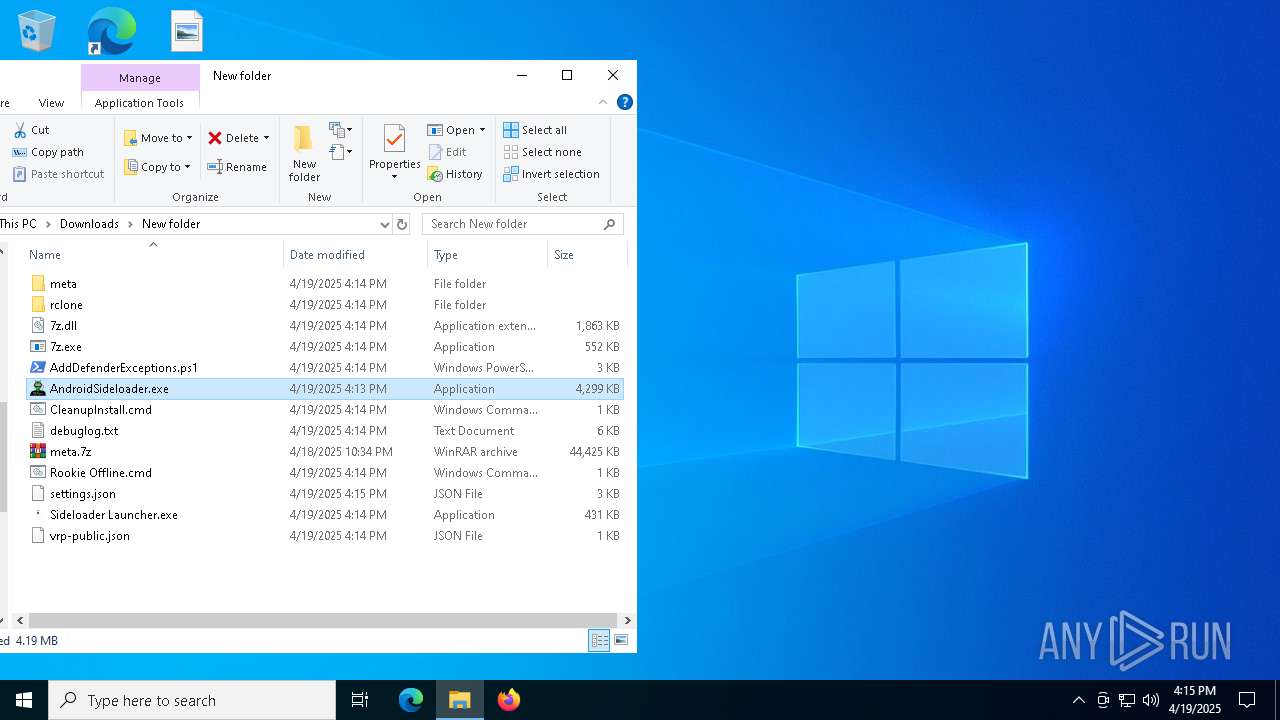
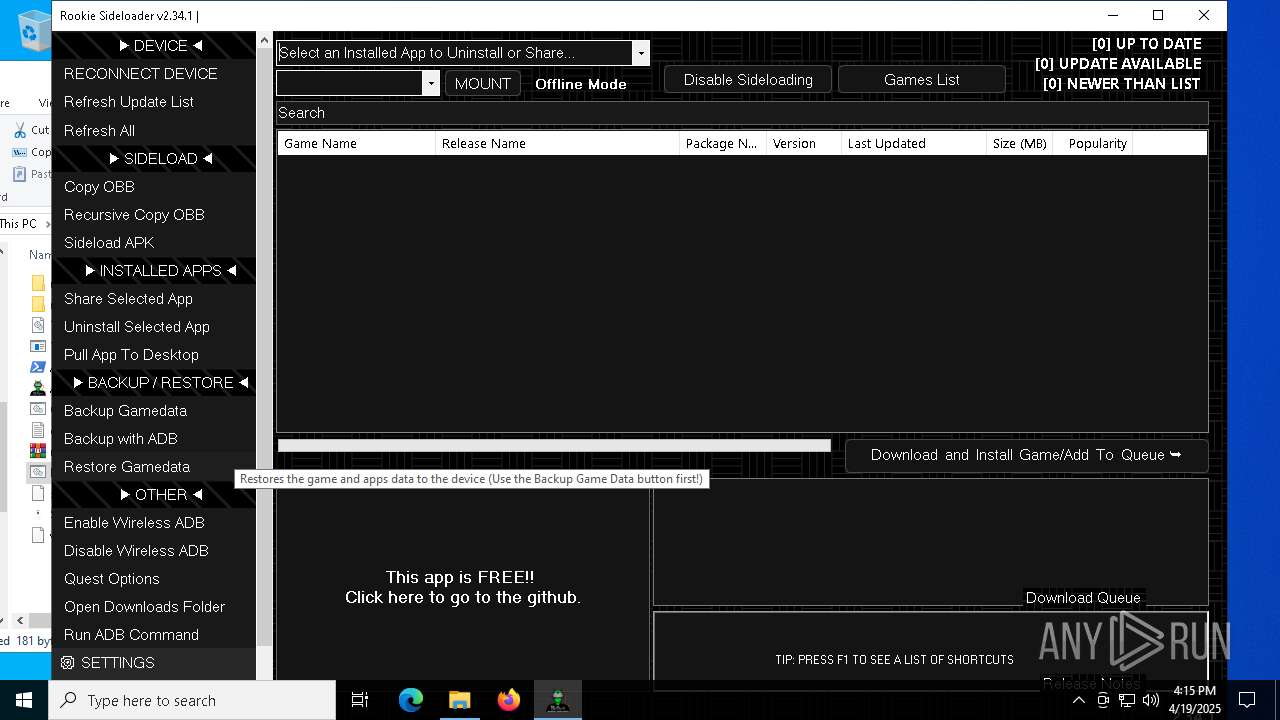
| File name: | AndroidSideloader.exe |
| Full analysis: | https://app.any.run/tasks/c4fa3bdc-0f20-4859-b9fe-1f1482058c96 |
| Verdict: | Malicious activity |
| Analysis date: | April 19, 2025, 16:13:08 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections |
| MD5: | 552E9C39473CA27A5DE66AB0C87ACEAA |
| SHA1: | D5DDB02A112B2233074EE257C5CC15C711B09291 |
| SHA256: | 5FBEC60B550076E3436AB83683211F3DB39EEE46BD14139A18A36B79F929F67E |
| SSDEEP: | 98304:UcEQQLhicXQ+9nWuWqVM5XflB2bz14ZPE:I |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- AndroidSideloader.exe (PID: 5576)
- AndroidSideloader.exe (PID: 2344)
- AndroidSideloader.exe (PID: 5952)
Executable content was dropped or overwritten
- AndroidSideloader.exe (PID: 5576)
- 7z.exe (PID: 5116)
- AndroidSideloader.exe (PID: 2344)
Drops 7-zip archiver for unpacking
- AndroidSideloader.exe (PID: 5576)
- AndroidSideloader.exe (PID: 2344)
Application launched itself
- adb.exe (PID: 4208)
- adb.exe (PID: 4988)
- adb.exe (PID: 7084)
- cmd.exe (PID: 1196)
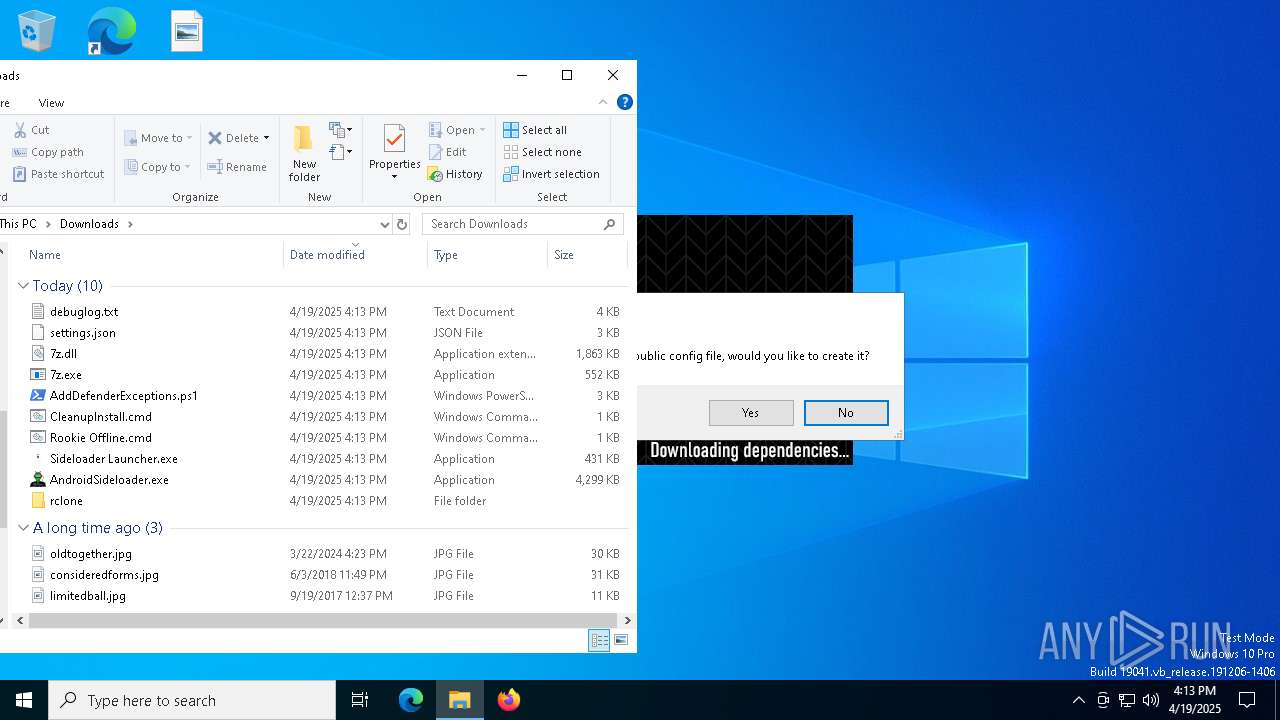
RCLONE has been detected
- rclone.exe (PID: 5056)
- rclone.exe (PID: 1452)
- rclone.exe (PID: 2392)
- rclone.exe (PID: 1348)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 1196)
INFO
Reads the computer name
- AndroidSideloader.exe (PID: 5576)
- 7z.exe (PID: 5116)
- 7z.exe (PID: 4488)
- adb.exe (PID: 5556)
- rclone.exe (PID: 5056)
- rclone.exe (PID: 1452)
- 7z.exe (PID: 4172)
- 7z.exe (PID: 5720)
- AndroidSideloader.exe (PID: 2344)
- adb.exe (PID: 872)
- rclone.exe (PID: 1348)
- rclone.exe (PID: 2392)
- 7z.exe (PID: 1020)
- adb.exe (PID: 5112)
- AndroidSideloader.exe (PID: 5952)
Checks supported languages
- AndroidSideloader.exe (PID: 5576)
- 7z.exe (PID: 5116)
- adb.exe (PID: 5124)
- adb.exe (PID: 4208)
- 7z.exe (PID: 4488)
- adb.exe (PID: 5556)
- rclone.exe (PID: 5056)
- rclone.exe (PID: 1452)
- adb.exe (PID: 6808)
- 7z.exe (PID: 4172)
- adb.exe (PID: 4988)
- adb.exe (PID: 6324)
- 7z.exe (PID: 5720)
- adb.exe (PID: 872)
- AndroidSideloader.exe (PID: 2344)
- rclone.exe (PID: 2392)
- 7z.exe (PID: 1020)
- rclone.exe (PID: 1348)
- adb.exe (PID: 6752)
- adb.exe (PID: 7084)
- adb.exe (PID: 5112)
- adb.exe (PID: 2064)
- adb.exe (PID: 1760)
- adb.exe (PID: 5720)
- adb.exe (PID: 5072)
- AndroidSideloader.exe (PID: 5952)
- adb.exe (PID: 5776)
- adb.exe (PID: 4572)
Disables trace logs
- AndroidSideloader.exe (PID: 5576)
- AndroidSideloader.exe (PID: 2344)
Checks proxy server information
- AndroidSideloader.exe (PID: 5576)
- AndroidSideloader.exe (PID: 2344)
- slui.exe (PID: 4488)
Reads the machine GUID from the registry
- AndroidSideloader.exe (PID: 5576)
- rclone.exe (PID: 1452)
- AndroidSideloader.exe (PID: 2344)
- rclone.exe (PID: 2392)
- AndroidSideloader.exe (PID: 5952)
Reads the software policy settings
- AndroidSideloader.exe (PID: 5576)
- rclone.exe (PID: 1452)
- slui.exe (PID: 6944)
- AndroidSideloader.exe (PID: 2344)
- rclone.exe (PID: 2392)
- slui.exe (PID: 4488)
The sample compiled with english language support
- AndroidSideloader.exe (PID: 5576)
- 7z.exe (PID: 5116)
- AndroidSideloader.exe (PID: 2344)
Create files in a temporary directory
- adb.exe (PID: 5556)
- rclone.exe (PID: 1452)
- rclone.exe (PID: 2392)
Manual execution by a user
- AndroidSideloader.exe (PID: 2344)
- cmd.exe (PID: 1196)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (63.1) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (23.8) |
| .dll | | | Win32 Dynamic Link Library (generic) (5.6) |
| .exe | | | Win32 Executable (generic) (3.8) |
| .exe | | | Generic Win/DOS Executable (1.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2071:03:22 06:06:22+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 3987968 |
| InitializedDataSize: | 413184 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x3cf84e |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.0.0.0 |
| ProductVersionNumber: | 2.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | Rookie Sideloader |
| CompanyName: | Rookie.AndroidSideloader |
| FileDescription: | AndroidSideloader |
| FileVersion: | 2.0.0.0 |
| InternalName: | AndroidSideloader.exe |
| LegalCopyright: | Copyright © 2020 |
| LegalTrademarks: | - |
| OriginalFileName: | AndroidSideloader.exe |
| ProductName: | AndroidSideloader |
| ProductVersion: | 2.0.0.0 |
| AssemblyVersion: | 2.0.0.0 |
Total processes
188
Monitored processes
57
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 872 | adb -L tcp:5037 fork-server server --reply-fd 600 | C:\RSL\platform-tools\adb.exe | — | adb.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1020 | "7z.exe" x "C:\Users\admin\Downloads\New folder\meta.7z" -y -o"C:\Users\admin\Downloads\New folder\meta" -p"gL59VfgPxoHR" -bsp1 | C:\Users\admin\Downloads\New folder\7z.exe | — | AndroidSideloader.exe | |||||||||||
User: admin Company: Igor Pavlov Integrity Level: MEDIUM Description: 7-Zip Console Exit code: 0 Version: 24.09 Modules
| |||||||||||||||
| 1164 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | 7z.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1196 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Downloads\New folder\Rookie Offline.cmd" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1348 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | rclone.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1348 | "C:\Users\admin\Downloads\New folder\rclone\rclone.exe" listremotes --config vrp.download.config --inplace | C:\Users\admin\Downloads\New folder\rclone\rclone.exe | AndroidSideloader.exe | ||||||||||||
User: admin Company: https://rclone.org Integrity Level: MEDIUM Description: Rclone Exit code: 0 Version: 1.68.2 Modules
| |||||||||||||||
| 1452 | "C:\Users\admin\Downloads\rclone\rclone.exe" sync ":http:/meta.7z" "C:\Users\admin\Downloads" --inplace --http-url https://go.vrpyourself.online/ --tpslimit 1.0 --tpslimit-burst 3 | C:\Users\admin\Downloads\rclone\rclone.exe | AndroidSideloader.exe | ||||||||||||
User: admin Company: https://rclone.org Integrity Level: MEDIUM Description: Rclone Exit code: 0 Version: 1.68.2 Modules
| |||||||||||||||
| 1748 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | adb.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1760 | "C:\RSL\platform-tools\adb.exe" shell df | C:\RSL\platform-tools\adb.exe | — | AndroidSideloader.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 2040 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | adb.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
20 537
Read events
20 523
Write events
14
Delete events
0
Modification events
| (PID) Process: | (5576) AndroidSideloader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\AndroidSideloader_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5576) AndroidSideloader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\AndroidSideloader_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5576) AndroidSideloader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\AndroidSideloader_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (5576) AndroidSideloader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\AndroidSideloader_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (5576) AndroidSideloader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\AndroidSideloader_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (5576) AndroidSideloader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\AndroidSideloader_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (5576) AndroidSideloader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\AndroidSideloader_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (5576) AndroidSideloader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\AndroidSideloader_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (5576) AndroidSideloader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\AndroidSideloader_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (5576) AndroidSideloader.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\AndroidSideloader_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
19
Suspicious files
6
Text files
4 537
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5576 | AndroidSideloader.exe | C:\Users\admin\Downloads\dependencies.7z | — | |
MD5:— | SHA256:— | |||
| 5576 | AndroidSideloader.exe | C:\Users\admin\Downloads\Sideloader Launcher.exe | executable | |
MD5:A53A5E70248EB3DA58DEFA74B0554704 | SHA256:98BC8CF1C6A59EF70D6431E1E92887984E5B21C8FBC85B4AD23CCC70589C4B1F | |||
| 5576 | AndroidSideloader.exe | C:\Users\admin\Downloads\7z.dll | executable | |
MD5:C4AABD70DC28C9516809B775A30FDD3F | SHA256:882063948D675EE41B5AE68DB3E84879350EC81CF88D15B9BABF2FA08E332863 | |||
| 5576 | AndroidSideloader.exe | C:\Users\admin\Downloads\settings.json | binary | |
MD5:BF33F0EE8DCED7D19A200C051E056453 | SHA256:0621E0F9C1A2EC3F12C22043916D3689DBB0B21AD2A3CBC112088B6834198012 | |||
| 5576 | AndroidSideloader.exe | C:\Users\admin\Downloads\Rookie Offline.cmd | text | |
MD5:513248E44025E42FD2B8F9280501A8BB | SHA256:7DD245A6267A6D9500EE6B13A29FBDD80CEF9A020162C0E24A228558C58FA092 | |||
| 5116 | 7z.exe | C:\RSL\platform-tools\AdbWinApi.dll | executable | |
MD5:D79A7C0A425F768FC9F9BCF2AA144D8F | SHA256:1AD523231DE449AF3BA0E8664D3AF332F0C5CC4F09141691CA05E35368FA811A | |||
| 5576 | AndroidSideloader.exe | C:\Users\admin\Downloads\AddDefenderExceptions.ps1 | text | |
MD5:D4C169C2F22D0138A973F81AC6BD5F3A | SHA256:D33272FAA34B9F435A3AE5844E2022D6A70232B42F957E31FA37F6501B12A128 | |||
| 5116 | 7z.exe | C:\RSL\platform-tools\AdbWinUsbApi.dll | executable | |
MD5:E6E1716F53624AFF7DBCE5891334669A | SHA256:51A61758A6F1F13DD36530199C0D65E227CD9D43765372B2942944CC3296CA2C | |||
| 5116 | 7z.exe | C:\RSL\platform-tools\NOTICE.txt | text | |
MD5:E7E8B9497810834CAB9522FE5DD80560 | SHA256:D25FAFFB58D73FEF75D10B7D9B49D8D9872CBB33018F23232D04E8C3EA9DC4DB | |||
| 5116 | 7z.exe | C:\RSL\platform-tools\mke2fs.conf | text | |
MD5:699098CA95F87BA48BB94A3E848549B3 | SHA256:AD58A58DCDD24D85055814CA9CAC67DB89D4E67C434E96774BDCE0D0A007D067 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
34
DNS requests
23
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.19.11.105:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6592 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6592 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 2.19.11.105:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
5576 | AndroidSideloader.exe | 140.82.121.4:443 | github.com | GITHUB | US | whitelisted |
5576 | AndroidSideloader.exe | 185.199.109.133:443 | raw.githubusercontent.com | FASTLY | US | whitelisted |
6544 | svchost.exe | 40.126.32.133:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5576 | AndroidSideloader.exe | 95.217.6.16:443 | downloads.rclone.org | Hetzner Online GmbH | FI | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
github.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
downloads.rclone.org |
| unknown |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
5576 | AndroidSideloader.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |
2344 | AndroidSideloader.exe | Misc activity | ET INFO Observed ZeroSSL SSL/TLS Certificate |