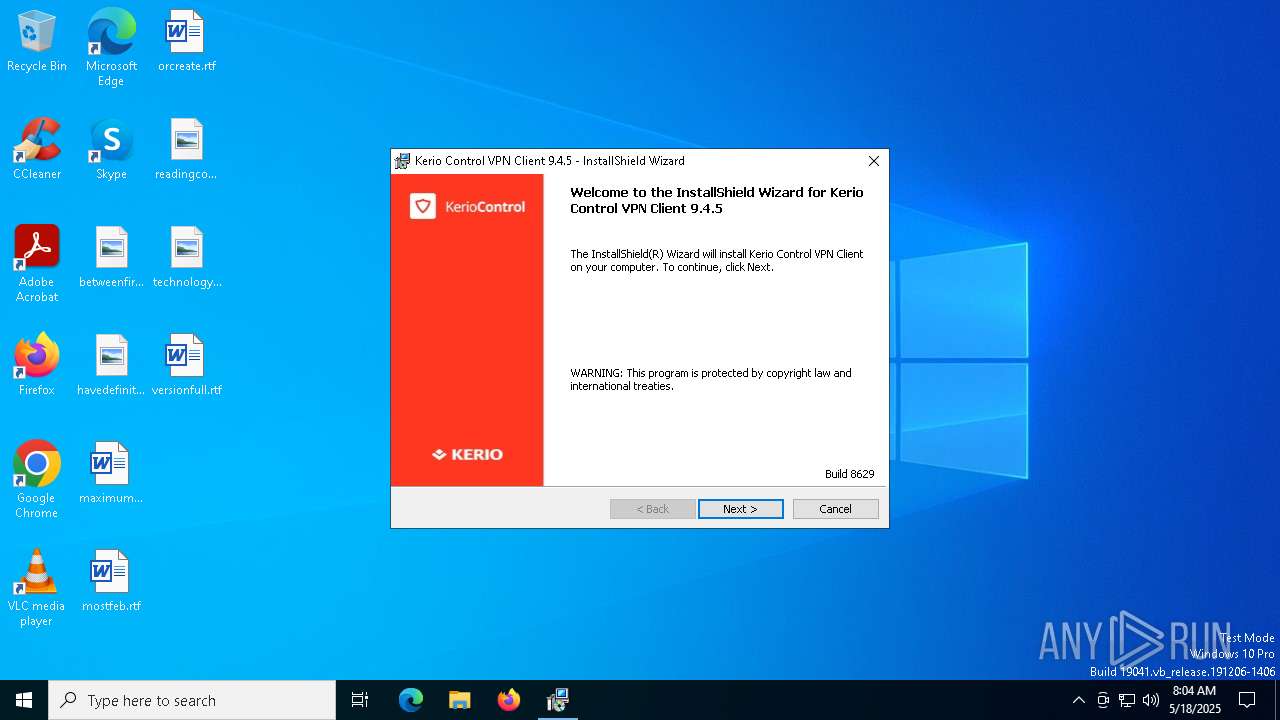
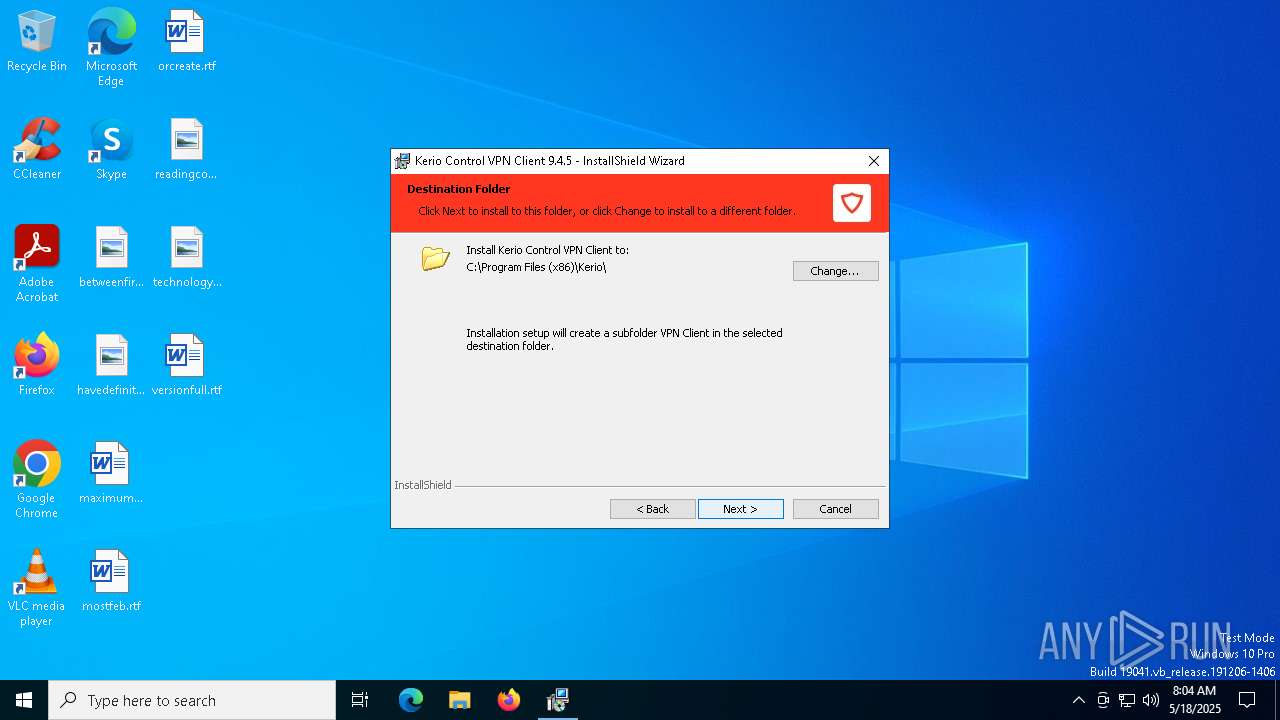
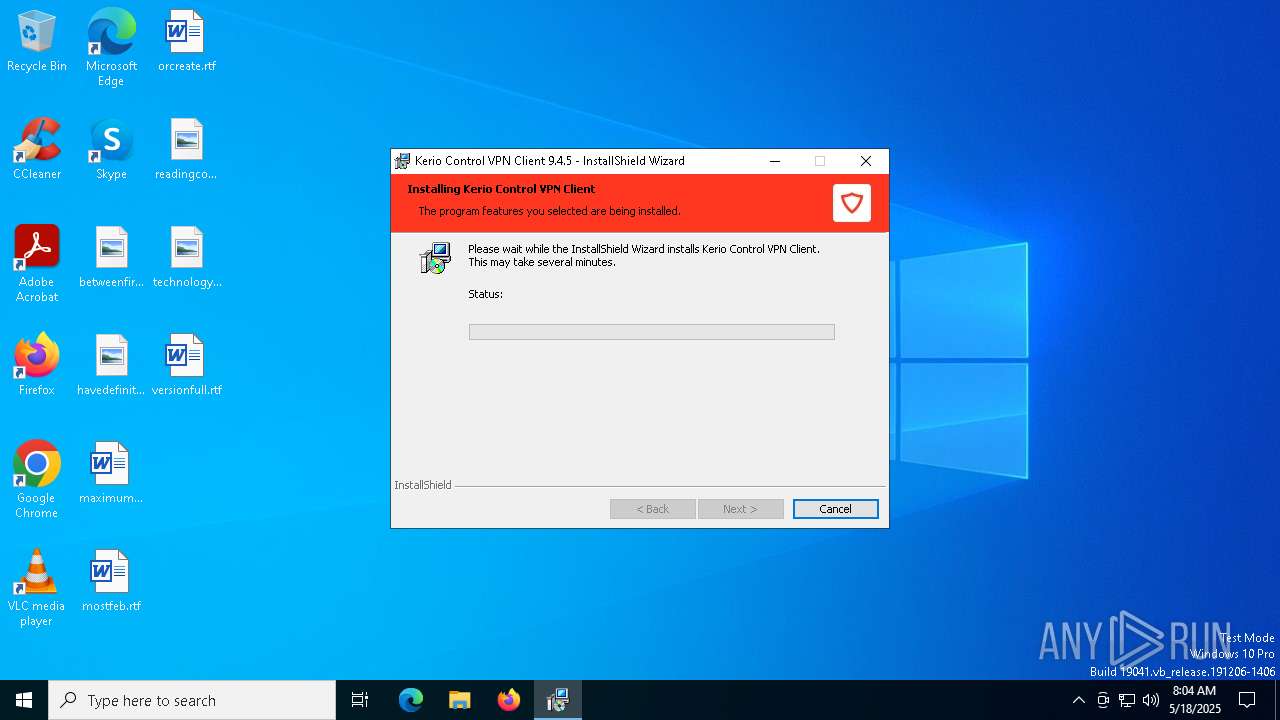
| File name: | kerio-control-vpnclient-9.4.5-8629-win64.msi |
| Full analysis: | https://app.any.run/tasks/fe548697-8c9d-484d-be50-4884a066e73e |
| Verdict: | Malicious activity |
| Analysis date: | May 18, 2025, 08:04:17 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.2, MSI Installer, Number of Characters: 0, Last Saved By: InstallShield, Number of Words: 0, Title: Installation Database, Comments: Setup of Kerio Control VPN Client, Keywords: Installer,MSI,Database,Kerio,VPN,Client, Subject: Kerio Control VPN Client, Author: Kerio Technologies Inc., Security: 1, Number of Pages: 200, Name of Creating Application: InstallShield 2015 - Professional Edition 22, Last Saved Time/Date: Mon Jan 27 16:37:41 2025, Create Time/Date: Mon Jan 27 16:37:41 2025, Last Printed: Mon Jan 27 16:37:41 2025, Revision Number: {B89E1422-50DB-447C-A407-30879A66B7A2}, Code page: 0, Template: AMD64;0,1033,1031,2052,1034,2070,1029,1040,1041,1043,1045,1049,1050,1053,1036,1038 |
| MD5: | 18CA5D4DC97B4089F67146D5A86ABCF1 |
| SHA1: | 4B502E4DA406A4A1608017CFC69521C9BC153B42 |
| SHA256: | 5FA24E50ED5CE119A798503F593920E91A2159F0C1CE2EC705AC255812B01B38 |
| SSDEEP: | 98304:EFyOc6ZkGzxwJDEwWcQj/95B58/YuaEiRFJdMVO6i8M/XZa13Efv1g1VeAeC5izm:cPMJDlmqPBC+wHLTM1G |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- MSIB9ED.tmp (PID: 7648)
SUSPICIOUS
Process drops legitimate windows executable
- msiexec.exe (PID: 7468)
- msiexec.exe (PID: 7548)
Starts application with an unusual extension
- msiexec.exe (PID: 7468)
- msiexec.exe (PID: 2564)
Application launched itself
- msiexec.exe (PID: 7468)
- msiexec.exe (PID: 7548)
Reads security settings of Internet Explorer
- MSIB9ED.tmp (PID: 7648)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7548)
Searches for installed software
- msiexec.exe (PID: 7468)
Executes as Windows Service
- VSSVC.exe (PID: 4400)
- kvpncsvc.exe (PID: 2984)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 7548)
- drvinst.exe (PID: 3300)
- drvinst.exe (PID: 4040)
The process drops C-runtime libraries
- msiexec.exe (PID: 7548)
Executable content was dropped or overwritten
- drvinst.exe (PID: 3300)
- drvinst.exe (PID: 4040)
Suspicious use of NETSH.EXE
- msiexec.exe (PID: 6872)
INFO
The sample compiled with english language support
- msiexec.exe (PID: 7468)
- msiexec.exe (PID: 7548)
- msiexec.exe (PID: 7676)
- drvinst.exe (PID: 3300)
- drvinst.exe (PID: 4040)
Reads the computer name
- msiexec.exe (PID: 7548)
- msiexec.exe (PID: 7588)
- MSIB9ED.tmp (PID: 7648)
- msiexec.exe (PID: 7232)
Create files in a temporary directory
- msiexec.exe (PID: 7588)
- msiexec.exe (PID: 7468)
- msiexec.exe (PID: 8176)
Checks supported languages
- msiexec.exe (PID: 7588)
- MSIB9ED.tmp (PID: 7648)
- msiexec.exe (PID: 7548)
- msiexec.exe (PID: 7232)
Executable content was dropped or overwritten
- msiexec.exe (PID: 7588)
- msiexec.exe (PID: 7468)
- msiexec.exe (PID: 7548)
- msiexec.exe (PID: 7676)
Process checks computer location settings
- MSIB9ED.tmp (PID: 7648)
Reads the machine GUID from the registry
- msiexec.exe (PID: 7548)
Reads the software policy settings
- msiexec.exe (PID: 7548)
Creates files or folders in the user directory
- msiexec.exe (PID: 7548)
Manages system restore points
- SrTasks.exe (PID: 7884)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (78) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (8.8) |
| .msp | | | Windows Installer Patch (7.2) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| Characters: | - |
|---|---|
| LastModifiedBy: | InstallShield |
| Words: | - |
| Title: | Installation Database |
| Comments: | Setup of Kerio Control VPN Client |
| Keywords: | Installer,MSI,Database,Kerio,VPN,Client |
| Subject: | Kerio Control VPN Client |
| Author: | Kerio Technologies Inc. |
| Security: | Password protected |
| Pages: | 200 |
| Software: | InstallShield? 2015 - Professional Edition 22 |
| ModifyDate: | 2025:01:27 16:37:41 |
| CreateDate: | 2025:01:27 16:37:41 |
| LastPrinted: | 2025:01:27 16:37:41 |
| RevisionNumber: | {B89E1422-50DB-447C-A407-30879A66B7A2} |
| CodePage: | Unknown (0) |
| Template: | AMD64;0,1033,1031,2052,1034,2070,1029,1040,1041,1043,1045,1049,1050,1053,1036,1038 |
Total processes
170
Monitored processes
40
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2152 | "C:\Program Files (x86)\Kerio\VPN Client\kvpncadm.exe" /regserver | C:\Program Files (x86)\Kerio\VPN Client\kvpncadm.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Kerio Technologies Inc. Integrity Level: SYSTEM Description: Kerio Control VPN Client Admin Config Exit code: 0 Version: 9.4.5.8629 T0 Modules
| |||||||||||||||
| 2564 | C:\Windows\syswow64\MsiExec.exe -Embedding E9AFF62C86A26329532A8370217E812F E Global\MSI0000 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2908 | "C:\Program Files (x86)\Kerio\VPN Client\kvpncgui.exe" | C:\Program Files (x86)\Kerio\VPN Client\kvpncgui.exe | — | MSI5549.tmp | |||||||||||
User: admin Company: Kerio Technologies Inc. Integrity Level: MEDIUM Description: Kerio Control VPN Client Version: 9.4.5.8629 T0 Modules
| |||||||||||||||
| 2984 | "C:\Program Files (x86)\Kerio\VPN Client\kvpncsvc.exe" | C:\Program Files (x86)\Kerio\VPN Client\kvpncsvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Kerio Technologies Inc. Integrity Level: SYSTEM Description: Kerio Control VPN Client Service Version: 9.4.5.8629 T0 Modules
| |||||||||||||||
| 3300 | DrvInst.exe "4" "1" "c:\program files (x86)\kerio\vpn client\vpndriver\kvnet.inf" "9" "41a6d8d87" "00000000000001C8" "WinSta0\Default" "00000000000001D0" "208" "c:\program files (x86)\kerio\vpn client\vpndriver" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4040 | DrvInst.exe "2" "211" "ROOT\KVNETID\0000" "C:\WINDOWS\INF\oem1.inf" "oem1.inf:fc9f1aa232f7f37d:kvnet.ndi:9.3.6.5716:kvnetid," "41a6d8d87" "00000000000001C8" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4300 | C:\Users\admin\AppData\Local\Temp\wac318D.tmp {EFB7539B-24F3-46B6-AF6E-3B021B51EFEF}:{3D0CE359-B06E-400A-9370-448799D80C96} | C:\Users\admin\AppData\Local\Temp\wac318D.tmp | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Flexera Software LLC Integrity Level: SYSTEM Description: InstallShield (R) 64-bit Setup Engine Exit code: 0 Version: 22.0.330 Modules
| |||||||||||||||
| 4400 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5548 | C:\Windows\System32\MsiExec.exe -Embedding EE8C1620D5003553EE5249AB09D4C365 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6388 | "C:\Windows\System32\netsh.exe" interface set interface name="Ethernet" newname="Kerio Virtual Network" | C:\Windows\System32\netsh.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
17 360
Read events
17 001
Write events
330
Delete events
29
Modification events
| (PID) Process: | (7548) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 7C1D00009734EF78CBC7DB01 | |||
| (PID) Process: | (7548) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: A8D830581AF749A20F8796AF674406910EE54D5AA8531BBA28E27B26EB133B60 | |||
| (PID) Process: | (7548) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001\SOFTWARE\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (7548) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\Config.Msi\ |
Value: | |||
| (PID) Process: | (7548) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | C:\Config.Msi\10cb14.rbs |
Value: 31180747 | |||
| (PID) Process: | (7548) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | write | Name: | C:\Config.Msi\10cb14.rbsLow |
Value: | |||
| (PID) Process: | (7548) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | delete value | Name: | C:\Config.Msi\10cb14.rbs |
Value: 쟋Ǜ | |||
| (PID) Process: | (7548) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Rollback\Scripts |
| Operation: | delete value | Name: | C:\Config.Msi\10cb14.rbsLow |
Value: 籄 | |||
| (PID) Process: | (7548) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001_Classes\Local Settings\MuiCache\3c\52C64B7E |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (7548) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1693682860-607145093-2874071422-1001_Classes\Local Settings\MuiCache\3c |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
90
Suspicious files
63
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7588 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\{3B11BF8D-281E-4627-A47A-5630116FC549}\ScriptRegistrator.msi | executable | |
MD5:31C6E41867FD566534AFC8BA32077329 | SHA256:F8F64808C822A8DCECC03B3A084F785B199C528EE32A62F0656818A628E87553 | |||
| 7548 | msiexec.exe | C:\Windows\Installer\MSICD35.tmp | binary | |
MD5:C71E9AB6512A03D33F73E2A367D9020A | SHA256:52BF37BBDDDB0704285DAE28E34E9E5628A25BC4534C003353BEA800F82EE26C | |||
| 7468 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIB9ED.tmp | executable | |
MD5:A0324B11652ED4ACC7D09CA17607AAD6 | SHA256:9007F7BB4F0E3D93FF42602185DA9253C5631392E50DEABE393CE34CA929E424 | |||
| 7548 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\3C3948BE6E525B8A8CEE9FAC91C9E392_C6F6AD193A5BB132667C3FC1E5AFF1F4 | binary | |
MD5:6F497DBEF830B06F4CBF5D9CB78E16D1 | SHA256:CB2A26ABC131B844E70DE4FD82EFEC55DB16636C7A9658F7120722040FCF7E95 | |||
| 7548 | msiexec.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\3C3948BE6E525B8A8CEE9FAC91C9E392_C6F6AD193A5BB132667C3FC1E5AFF1F4 | binary | |
MD5:5BFA51F3A417B98E7443ECA90FC94703 | SHA256:BEBE2853A3485D1C2E5C5BE4249183E0DDAFF9F87DE71652371700A89D937128 | |||
| 7548 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:E6AC26415EE405CF717B46747D4874B7 | SHA256:ECC245CC51D4ADA7B37624CF450BF973C8FEFE01AB317F33D524D12C55881E97 | |||
| 7548 | msiexec.exe | C:\Windows\Temp\~DFB883E39150895282.TMP | binary | |
MD5:E6AC26415EE405CF717B46747D4874B7 | SHA256:ECC245CC51D4ADA7B37624CF450BF973C8FEFE01AB317F33D524D12C55881E97 | |||
| 7548 | msiexec.exe | C:\Windows\Temp\~DF113815B9184EC91F.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
| 7548 | msiexec.exe | C:\Config.Msi\10cb14.rbs | binary | |
MD5:792E7CDA7213AB5CC0393701868708BB | SHA256:6628E291E74AEC0523BDD9EF762271F3B74A3707EFFFCB4DC26366E2315B3230 | |||
| 7548 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
28
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.41:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7548 | msiexec.exe | GET | 200 | 2.17.189.192:80 | http://crl.verisign.com/pca3.crl | unknown | — | — | whitelisted |
7548 | msiexec.exe | GET | 200 | 2.17.189.192:80 | http://ocsp.verisign.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ%2FxkCfyHfJr7GQ6M658NRZ4SHo%2FAQUCPVR6Pv%2BPT1kNnxoz1t4qN%2B5xTcCECj52c24aW1r3NfQlRJcKuI%3D | unknown | — | — | whitelisted |
7548 | msiexec.exe | GET | 200 | 2.17.189.192:80 | http://ocsp.verisign.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ%2FxkCfyHfJr7GQ6M658NRZ4SHo%2FAQUCPVR6Pv%2BPT1kNnxoz1t4qN%2B5xTcCECj52c24aW1r3NfQlRJcKuI%3D | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8052 | SIHClient.exe | GET | 200 | 92.123.22.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8052 | SIHClient.exe | GET | 200 | 92.123.22.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 23.216.77.41:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7548 | msiexec.exe | 2.17.189.192:80 | crl.verisign.com | AKAMAI-AS | DE | whitelisted |
6544 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
crl.verisign.com |
| whitelisted |
ocsp.verisign.com |
| whitelisted |
csc3-2004-crl.verisign.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |