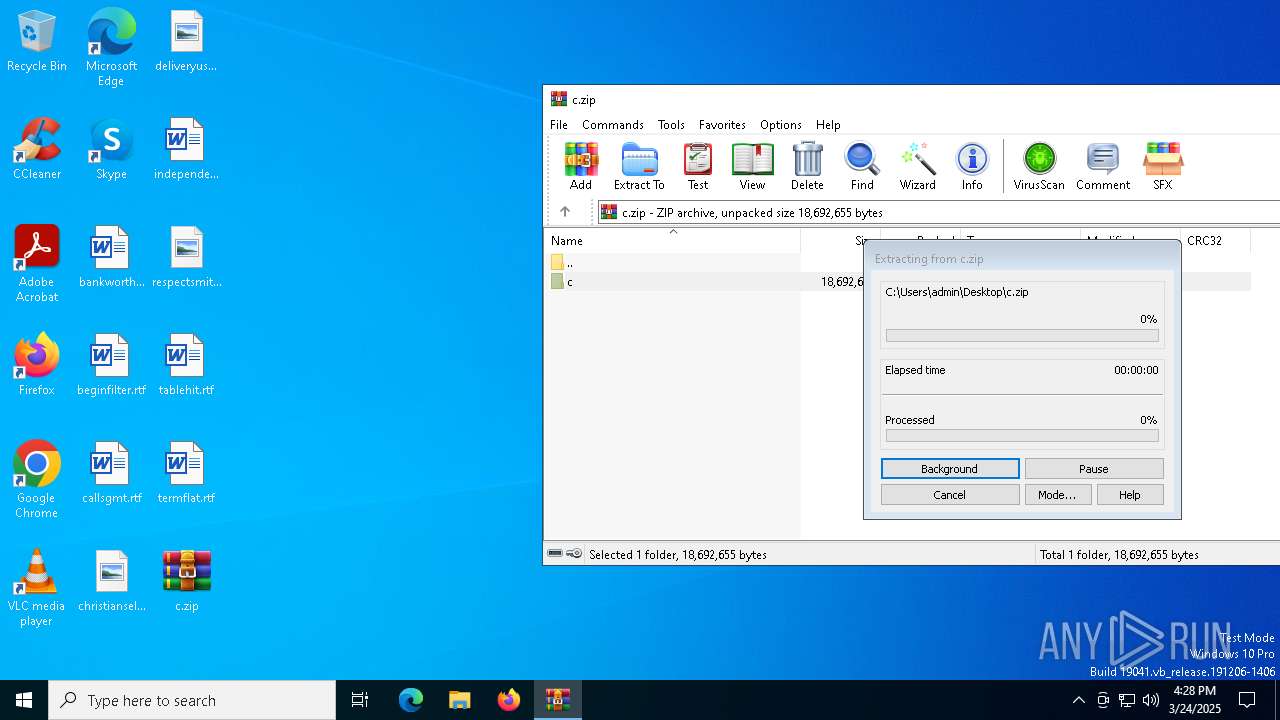
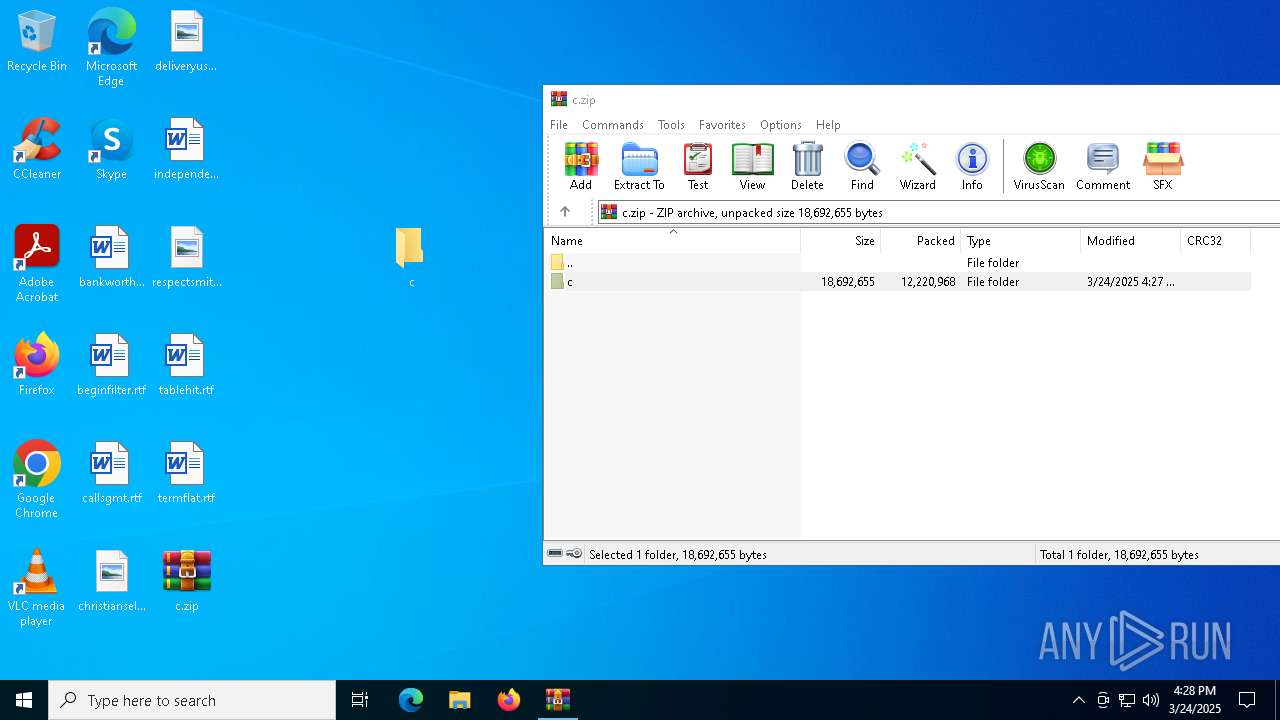
| File name: | c.zip |
| Full analysis: | https://app.any.run/tasks/df8ffdd6-aac9-4436-a721-304833f9d159 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 16:27:50 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 59B5D9CBBFD99A992D254EC3001ABFA4 |
| SHA1: | 706E90597EF11B0D63FAB2A0723C6F945196C7C7 |
| SHA256: | 5F85AAC4E49835D03C34143D5068C13FEA5ABEB83AB94D3BA50064CA3F378FBF |
| SSDEEP: | 98304:8EIrXOUTjrsYH+qj6l3BUAssAOPAfh4cruZPmedsLGCVeI+PXvfb/lI0emIjjej3:YZvDOgCgzJGIHIUfsfpD |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 1276)
SUSPICIOUS
Process drops legitimate windows executable
- WinRAR.exe (PID: 1276)
- python-3.13.2-amd64.exe (PID: 8048)
- msiexec.exe (PID: 7148)
Executable content was dropped or overwritten
- python-3.13.2-amd64.exe (PID: 4652)
- python-3.13.2-amd64.exe (PID: 8048)
- python-3.13.2-amd64.exe (PID: 1812)
Searches for installed software
- python-3.13.2-amd64.exe (PID: 8048)
- dllhost.exe (PID: 7528)
Reads security settings of Internet Explorer
- python-3.13.2-amd64.exe (PID: 8048)
Starts itself from another location
- python-3.13.2-amd64.exe (PID: 8048)
Executes as Windows Service
- VSSVC.exe (PID: 7832)
There is functionality for taking screenshot (YARA)
- python-3.13.2-amd64.exe (PID: 8048)
The process drops C-runtime libraries
- python-3.13.2-amd64.exe (PID: 8048)
- msiexec.exe (PID: 7148)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7148)
Process drops python dynamic module
- msiexec.exe (PID: 7148)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1276)
- firefox.exe (PID: 3020)
- msiexec.exe (PID: 7148)
Manual execution by a user
- firefox.exe (PID: 960)
Application launched itself
- firefox.exe (PID: 960)
- firefox.exe (PID: 3020)
The sample compiled with english language support
- WinRAR.exe (PID: 1276)
- firefox.exe (PID: 3020)
- python-3.13.2-amd64.exe (PID: 4652)
- python-3.13.2-amd64.exe (PID: 8048)
- msiexec.exe (PID: 7148)
Autorun file from Downloads
- firefox.exe (PID: 3020)
Checks supported languages
- python-3.13.2-amd64.exe (PID: 4652)
- python-3.13.2-amd64.exe (PID: 1812)
- msiexec.exe (PID: 7148)
- python-3.13.2-amd64.exe (PID: 8048)
Reads the computer name
- python-3.13.2-amd64.exe (PID: 8048)
- msiexec.exe (PID: 7148)
Create files in a temporary directory
- python-3.13.2-amd64.exe (PID: 4652)
- python-3.13.2-amd64.exe (PID: 8048)
Process checks computer location settings
- python-3.13.2-amd64.exe (PID: 8048)
Creates files or folders in the user directory
- python-3.13.2-amd64.exe (PID: 8048)
- msiexec.exe (PID: 7148)
Reads the software policy settings
- slui.exe (PID: 5156)
- slui.exe (PID: 4572)
- msiexec.exe (PID: 7148)
Manages system restore points
- SrTasks.exe (PID: 7368)
Reads the machine GUID from the registry
- python-3.13.2-amd64.exe (PID: 8048)
- msiexec.exe (PID: 7148)
Mutex for Python MSI log
- msiexec.exe (PID: 7148)
- python-3.13.2-amd64.exe (PID: 8048)
Checks proxy server information
- slui.exe (PID: 4572)
Creates a software uninstall entry
- msiexec.exe (PID: 7148)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2025:03:24 17:27:06 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | c/ |
Total processes
166
Monitored processes
25
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 660 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 960 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 1276 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\c.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1812 | "C:\Users\admin\AppData\Local\Temp\{FD718849-50EB-4F6C-8BA2-480FCD808DB3}\.be\python-3.13.2-amd64.exe" -q -burn.elevated BurnPipe.{1ECE3B74-CF99-4D48-82F6-F7FCA58FD34D} {BF506FD2-95A1-4B36-A75B-D38F84F7135B} 8048 | C:\Users\admin\AppData\Local\Temp\{FD718849-50EB-4F6C-8BA2-480FCD808DB3}\.be\python-3.13.2-amd64.exe | python-3.13.2-amd64.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: HIGH Description: Python 3.13.2 (64-bit) Version: 3.13.2150.0 Modules
| |||||||||||||||
| 2420 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2152 -parentBuildID 20240213221259 -prefsHandle 2144 -prefMapHandle 2080 -prefsLen 31031 -prefMapSize 244583 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {857e4245-14ce-4c5d-8f3c-51f22eac1999} 3020 "\\.\pipe\gecko-crash-server-pipe.3020" 28479a83110 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 3020 | "C:\Program Files\Mozilla Firefox\firefox.exe" | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 3240 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2728 -childID 1 -isForBrowser -prefsHandle 2724 -prefMapHandle 2668 -prefsLen 31447 -prefMapSize 244583 -jsInitHandle 1532 -jsInitLen 235124 -parentBuildID 20240213221259 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {87209785-0759-41de-8f80-2a903ee3f50b} 3020 "\\.\pipe\gecko-crash-server-pipe.3020" 2840bb39f50 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
| 4572 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4652 | "C:\Users\admin\Downloads\python-3.13.2-amd64.exe" | C:\Users\admin\Downloads\python-3.13.2-amd64.exe | firefox.exe | ||||||||||||
User: admin Company: Python Software Foundation Integrity Level: MEDIUM Description: Python 3.13.2 (64-bit) Version: 3.13.2150.0 Modules
| |||||||||||||||
| 5112 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=1912 -parentBuildID 20240213221259 -prefsHandle 1840 -prefMapHandle 1832 -prefsLen 31031 -prefMapSize 244583 -appDir "C:\Program Files\Mozilla Firefox\browser" - {11d3ca99-53c9-469d-838f-ab8b9154267e} 3020 "\\.\pipe\gecko-crash-server-pipe.3020" 2847f1ee810 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Version: 123.0 Modules
| |||||||||||||||
Total events
53 653
Read events
48 276
Write events
5 293
Delete events
84
Modification events
| (PID) Process: | (1276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\c.zip | |||
| (PID) Process: | (1276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3020) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (3020) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | SlowContextMenuEntries |
Value: 6024B221EA3A6910A2DC08002B30309D0A010000BD0E0C47735D584D9CEDE91E22E23282770100000114020000000000C0000000000000468D0000006078A409B011A54DAFA526D86198A780390100009AD298B2EDA6DE11BA8CA68E55D895936E000000 | |||
Executable files
86
Suspicious files
385
Text files
3 082
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
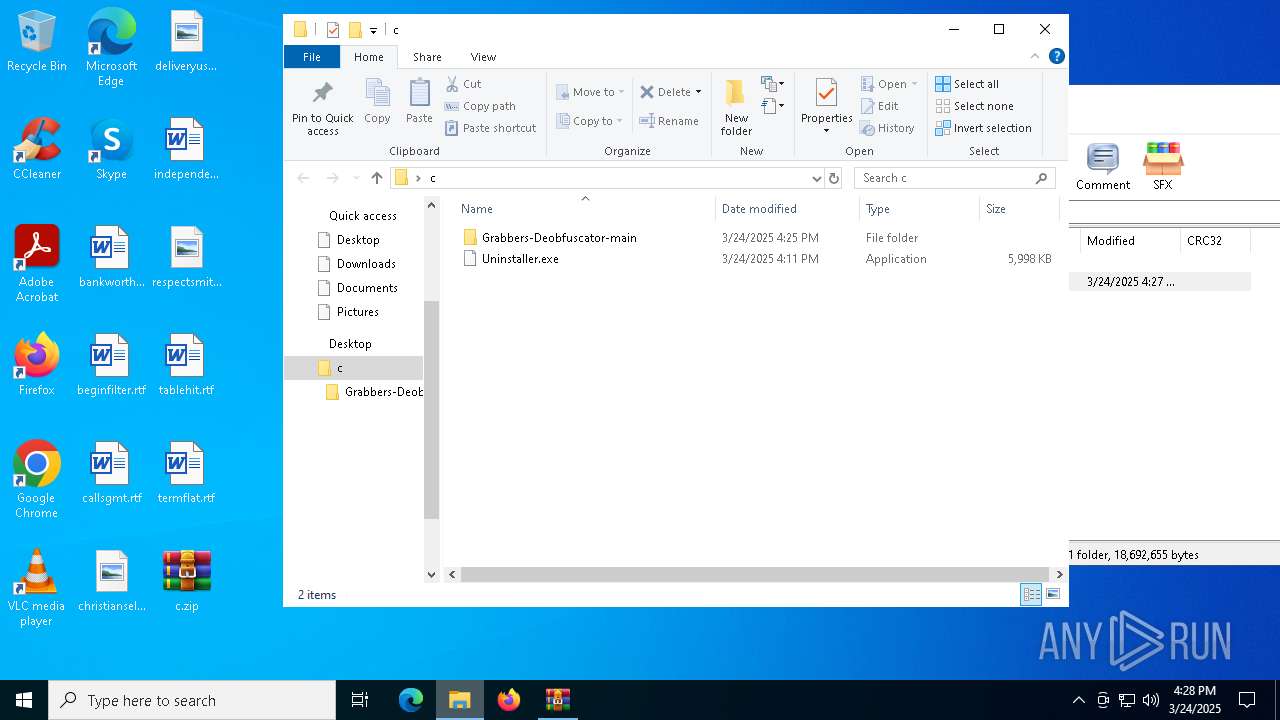
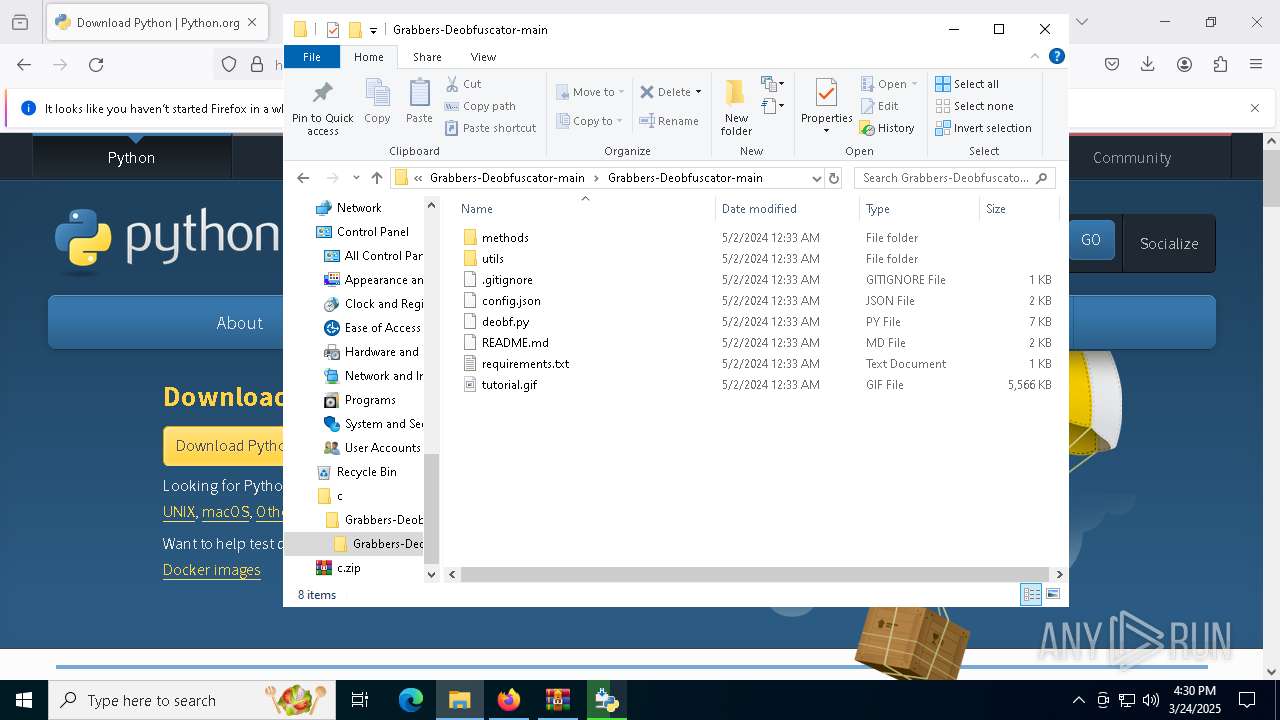
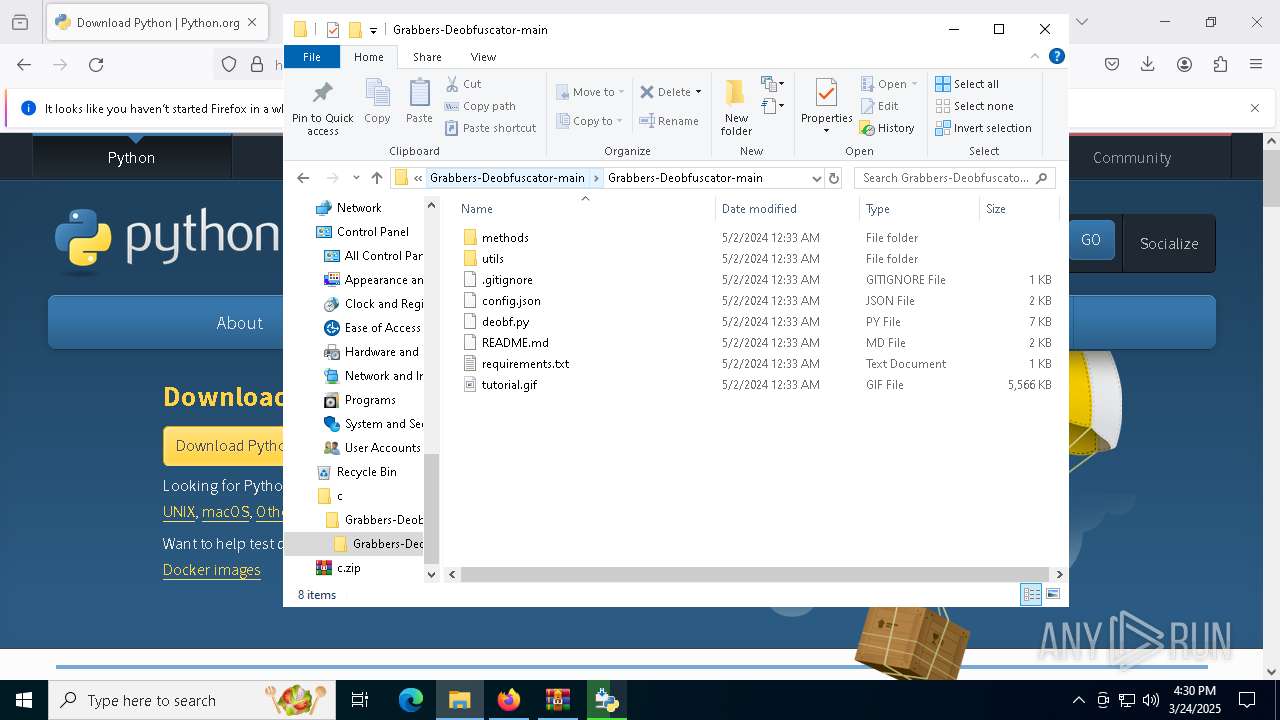
| 1276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1276.1153\c\Grabbers-Deobfuscator-main\Grabbers-Deobfuscator-main\tutorial.gif | — | |
MD5:— | SHA256:— | |||
| 1276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1276.1153\c\Grabbers-Deobfuscator-main\Grabbers-Deobfuscator-main\methods\other.py | text | |
MD5:3C81DB58E15D886A0AC087048FD4EAFB | SHA256:3C0F0714975CB012AED71AE396F038F2FA2F4A289825FE5E3C009F7693F01115 | |||
| 1276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1276.1153\c\Grabbers-Deobfuscator-main\Grabbers-Deobfuscator-main\methods\empyrean.py | text | |
MD5:68C486C90545F3D750A6600FCA3A9998 | SHA256:EA28F330301A9CBF0742C6AA3ABE503D7CF773A073FA8D693B0A390754F0E1B8 | |||
| 1276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1276.1153\c\Grabbers-Deobfuscator-main\Grabbers-Deobfuscator-main\methods\notobf.py | text | |
MD5:2677E35326EF5D285A346C5785B49B85 | SHA256:A054A1A2C2329DFC8078CCAE527DBC259396765754B0A09E88CDAFF60CB89FBA | |||
| 1276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1276.1153\c\Grabbers-Deobfuscator-main\Grabbers-Deobfuscator-main\methods\blank.py | text | |
MD5:A9EEC0C273D5C9ADD43B72745C3BC715 | SHA256:E831EA73EC311352B6EF5A0DE295771B2DD84147A450D64F40DCF620FA9386E8 | |||
| 1276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1276.1153\c\Grabbers-Deobfuscator-main\Grabbers-Deobfuscator-main\methods\luna.py | text | |
MD5:DABCBB5288A4CD2E6BD4502149CC47CA | SHA256:99EBD4549A057DC88070579456D1815D7C954CC4A200ED6FD43BFF542118981F | |||
| 1276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1276.1153\c\Grabbers-Deobfuscator-main\Grabbers-Deobfuscator-main\methods\ben.py | text | |
MD5:04915DC08E2AA81160CF532B7D3F940B | SHA256:C28E4FF38D046E64AF3D89D8DB3EBA4823B09B8223208929AFAE31D8C68DD6AE | |||
| 1276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1276.1153\c\Grabbers-Deobfuscator-main\Grabbers-Deobfuscator-main\utils\bin\fernflower.jar | compressed | |
MD5:BE01DBC47A455DDDFC724D5EFE13B490 | SHA256:74B609647D74E4CE04E9BEEF230A7460E74DE03BF41703F961BBE704D4938B8F | |||
| 1276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1276.1153\c\Grabbers-Deobfuscator-main\Grabbers-Deobfuscator-main\utils\bin\pycdas | binary | |
MD5:D1BE2DE3BDBB4FDB92E082E08ACA4CBE | SHA256:24D64B99F88CE539ABABF41503C33793110ECA52D90BB25D5D9F8382FB96F040 | |||
| 1276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1276.1153\c\Grabbers-Deobfuscator-main\Grabbers-Deobfuscator-main\utils\bin\pycdas.exe | executable | |
MD5:C106613CF4FC594260CED59577936BFA | SHA256:52370A2D59198239421954E1CB46284218D3C8BA70A1C161D2B5AB1CC7ED4D96 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
68
TCP/UDP connections
162
DNS requests
179
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.185:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 23.48.23.185:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5024 | backgroundTaskHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
3020 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
3020 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3020 | firefox.exe | POST | 200 | 184.24.77.48:80 | http://r10.o.lencr.org/ | unknown | — | — | whitelisted |
3020 | firefox.exe | POST | 200 | 184.24.77.44:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
3020 | firefox.exe | POST | 200 | 184.24.77.44:80 | http://r11.o.lencr.org/ | unknown | — | — | whitelisted |
3020 | firefox.exe | POST | 200 | 172.217.16.195:80 | http://o.pki.goog/s/wr3/cgo | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.185:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 23.48.23.185:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3216 | svchost.exe | 20.198.162.78:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
6544 | svchost.exe | 20.190.159.23:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 23.54.109.203:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Google Hosted Libraries (ajax .googleapis .com) |