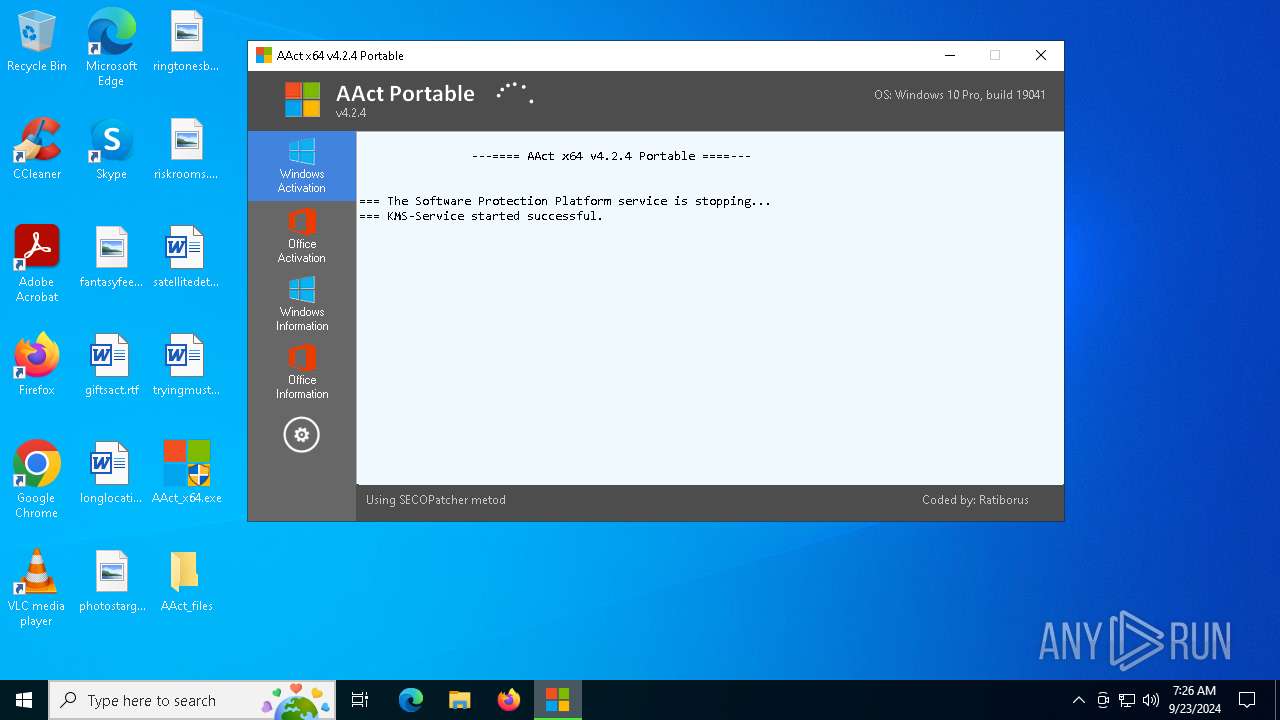
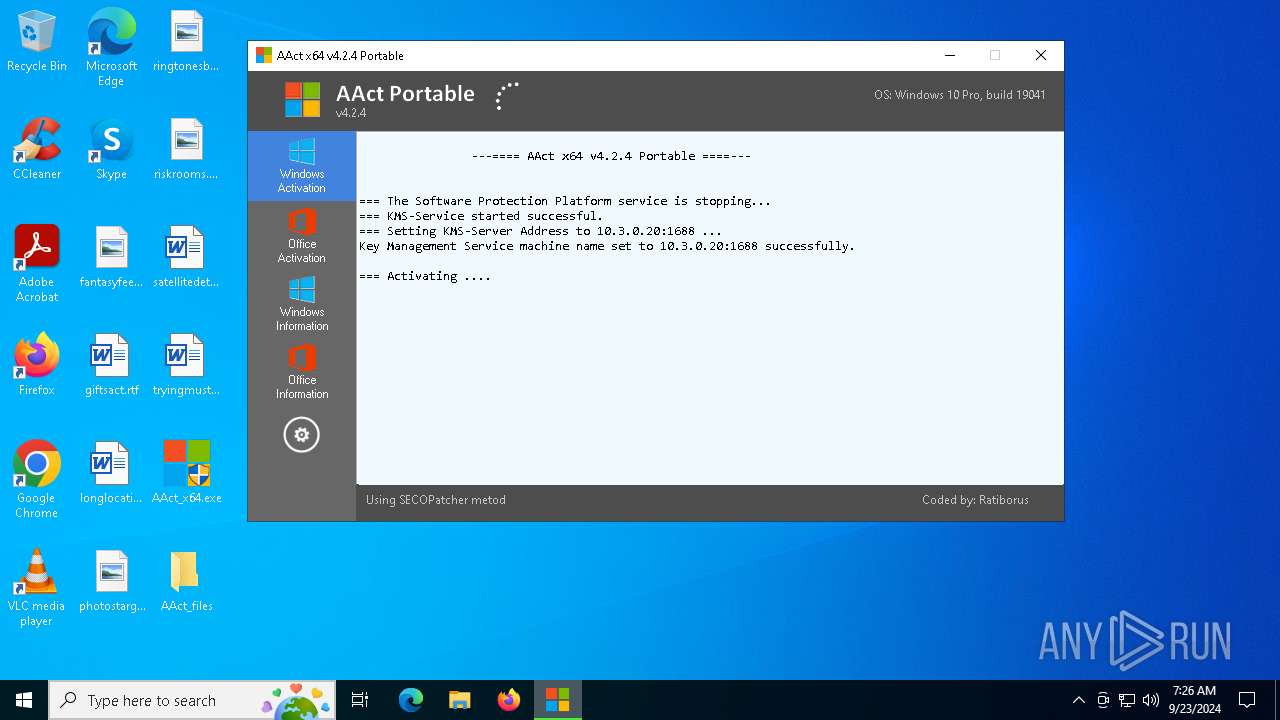
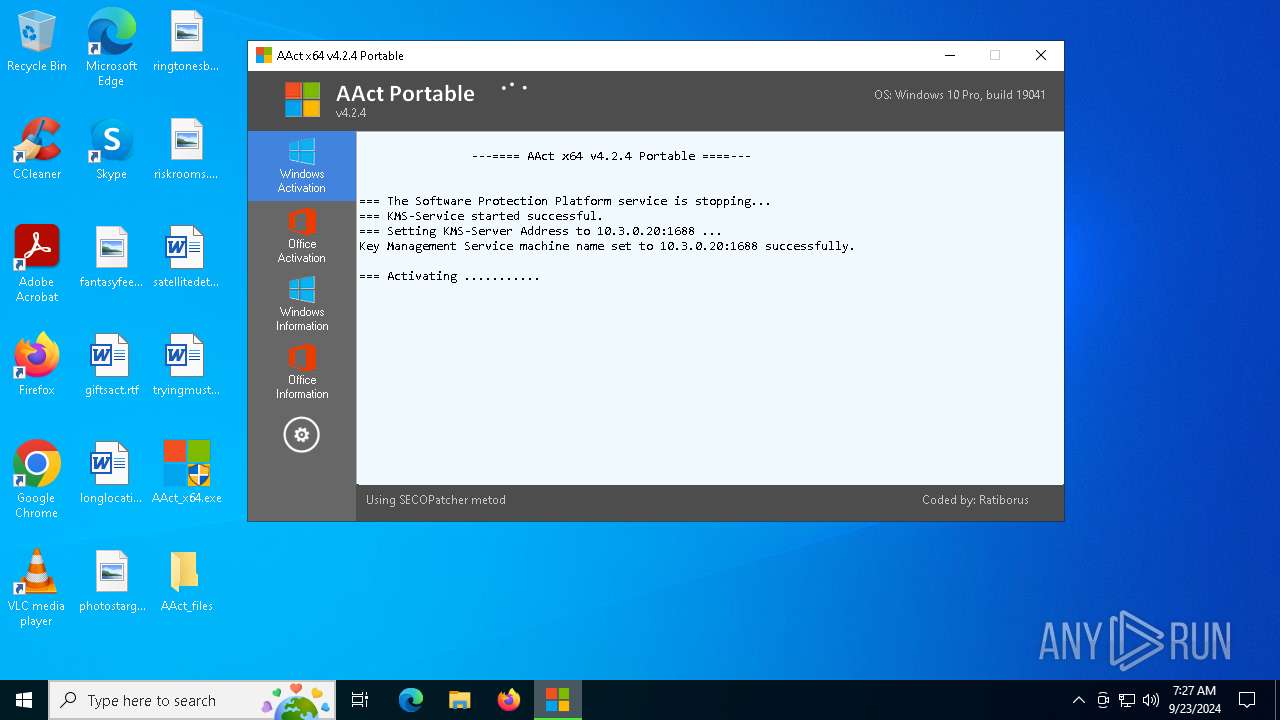
| File name: | AAct_x64.exe |
| Full analysis: | https://app.any.run/tasks/3870c51e-7aeb-4fe7-94c1-e5fbe0772a84 |
| Verdict: | Malicious activity |
| Analysis date: | September 23, 2024, 07:26:27 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | EF5908E09E7C9F398C7DBB62943B284E |
| SHA1: | 4FF446B59120496598F8CFD31D6762008F3A2185 |
| SHA256: | 5F70695A25BED9FEBF754233DCA7E616C0602B143B3F0074500A13FCF8B8B25A |
| SSDEEP: | 98304:GBCKRBjwOHMHQDxRWrfcpcBNEfLRGlmCVEiBaJhgsv0kkb2eV+ZaiXlUml6dfWaK:+myl1 |
MALICIOUS
Uses WMIC.EXE to add exclusions to the Windows Defender
- cmd.exe (PID: 6592)
- cmd.exe (PID: 2040)
- cmd.exe (PID: 6360)
- cmd.exe (PID: 6044)
- cmd.exe (PID: 7112)
Starts NET.EXE for service management
- net.exe (PID: 6544)
- cmd.exe (PID: 6476)
SUSPICIOUS
Found strings related to reading or modifying Windows Defender settings
- AAct_x64.exe (PID: 1184)
Starts CMD.EXE for commands execution
- AAct_x64.exe (PID: 1184)
Hides command output
- cmd.exe (PID: 3448)
Starts SC.EXE for service management
- cmd.exe (PID: 3448)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 3140)
- cmd.exe (PID: 5208)
- cmd.exe (PID: 4824)
- cmd.exe (PID: 6296)
- AAct_x64.exe (PID: 1184)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- cmd.exe (PID: 6248)
Executable content was dropped or overwritten
- AAct_x64.exe (PID: 1184)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 448)
- cmd.exe (PID: 2944)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 3812)
- cmd.exe (PID: 6928)
- cmd.exe (PID: 5724)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 5240)
The process executes VB scripts
- cmd.exe (PID: 5268)
- cmd.exe (PID: 4296)
- cmd.exe (PID: 7004)
- cmd.exe (PID: 1700)
- cmd.exe (PID: 6856)
- cmd.exe (PID: 6760)
The process downloads a VBScript from the remote host
- cmd.exe (PID: 6760)
INFO
Reads Environment values
- AAct_x64.exe (PID: 1184)
Checks supported languages
- AAct_x64.exe (PID: 1184)
Reads product name
- AAct_x64.exe (PID: 1184)
Reads the computer name
- AAct_x64.exe (PID: 1184)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 7160)
- WMIC.exe (PID: 5160)
- WMIC.exe (PID: 5796)
- WMIC.exe (PID: 6280)
Checks operating system version
- AAct_x64.exe (PID: 1184)
UPX packer has been detected
- AAct_x64.exe (PID: 1184)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (47) |
|---|---|---|
| .exe | | | UPX compressed Win32 Executable (46) |
| .exe | | | Generic Win/DOS Executable (3.4) |
| .exe | | | DOS Executable Generic (3.4) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2021:10:07 10:36:49+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 2.5 |
| CodeSize: | 1732608 |
| InitializedDataSize: | 73728 |
| UninitializedDataSize: | 1609728 |
| EntryPoint: | 0x330080 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.2.4.0 |
| ProductVersionNumber: | 4.2.4.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Unknown (0) |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| FileDescription: | AAct x64 |
Total processes
214
Monitored processes
86
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 448 | "C:\WINDOWS\System32\cmd.exe" /c taskkill.exe /t /f /IM SppExtComObj.Exe | C:\Windows\System32\cmd.exe | — | AAct_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 128 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | "C:\Users\admin\Desktop\AAct_files\KMSSS.exe" -Port 1688 -PWin RandomKMSPID -PO14 RandomKMSPID -PO15 RandomKMSPID -PO16 RandomKMSPID | C:\Users\admin\Desktop\AAct_files\KMSSS.exe | — | AAct_x64.exe | |||||||||||
User: admin Company: MSFree Inc. Integrity Level: HIGH Description: KMS emulator by Ratiborus. Version: 2.0.7.0 Modules
| |||||||||||||||
| 1184 | "C:\Users\admin\Desktop\AAct_x64.exe" | C:\Users\admin\Desktop\AAct_x64.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: AAct x64 Modules
| |||||||||||||||
| 1568 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1700 | "C:\WINDOWS\System32\cmd.exe" /c cscript.exe C:\WINDOWS\System32\slmgr.vbs //NoLogo /ckms | C:\Windows\System32\cmd.exe | — | AAct_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1716 | "C:\WINDOWS\System32\cmd.exe" /c ver.exe | C:\Windows\System32\cmd.exe | — | AAct_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1804 | icacls "C:\WINDOWS\System32\SECOPatcher.dll" /findsid *S-1-5-32-545 | C:\Windows\System32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2040 | "C:\WINDOWS\System32\cmd.exe" /c WMIC /NAMESPACE:\\root\Microsoft\Windows\Defender PATH MSFT_MpPreference call Add ExclusionPath="C:\Users\admin\Desktop\AAct_files" | C:\Windows\System32\cmd.exe | — | AAct_x64.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 2147749889 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2080 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | reg.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2224 | cscript.exe C:\WINDOWS\System32\slmgr.vbs //NoLogo /skms 10.3.0.20:1688 | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
Total events
4 289
Read events
4 287
Write events
2
Delete events
0
Modification events
| (PID) Process: | (1184) AAct_x64.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Script Host\Settings |
| Operation: | write | Name: | Enabled |
Value: 1 | |||
| (PID) Process: | (6632) reg.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SppExtComObj.Exe |
| Operation: | write | Name: | Debugger |
Value: rundll32.exe SECOPatcher.dll,PatcherMain | |||
Executable files
2
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1184 | AAct_x64.exe | C:\Users\admin\Desktop\AAct_files\KMSSS.exe | executable | |
MD5:01A80AAD5DABED1C1580F7E00213CF9D | SHA256:FD7499214ABAA13BF56D006AB7DE78EB8D6ADF17926C24ACE024D067049BC81D | |||
| 1184 | AAct_x64.exe | C:\Users\admin\Desktop\AAct_files\SECOPatcher.dll | executable | |
MD5:8998BE879286D69A2522109650FEC7B8 | SHA256:03B9136FB9414EBA54D0890D9EFAD1CC0E40ABD55EBE2A5BD5554EA7BCC6D2BE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
25
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6660 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2772 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2772 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
608 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4200 | RUXIMICS.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6660 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6660 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
608 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |