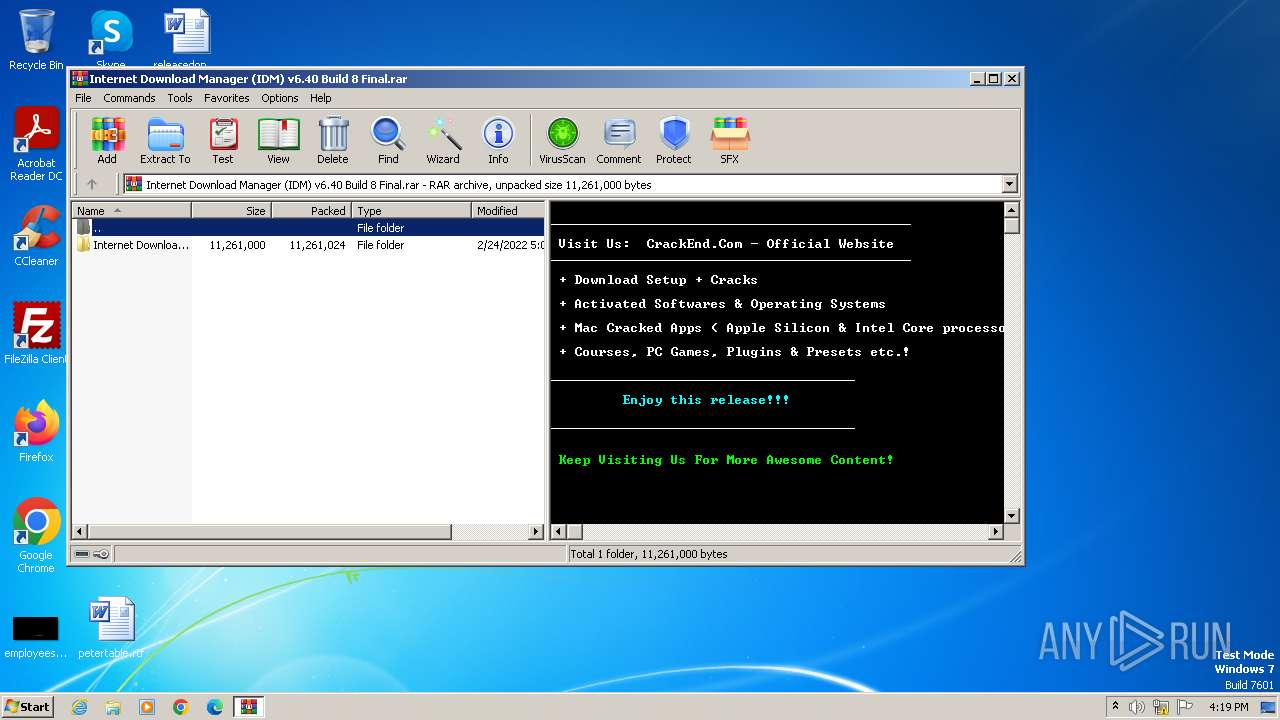
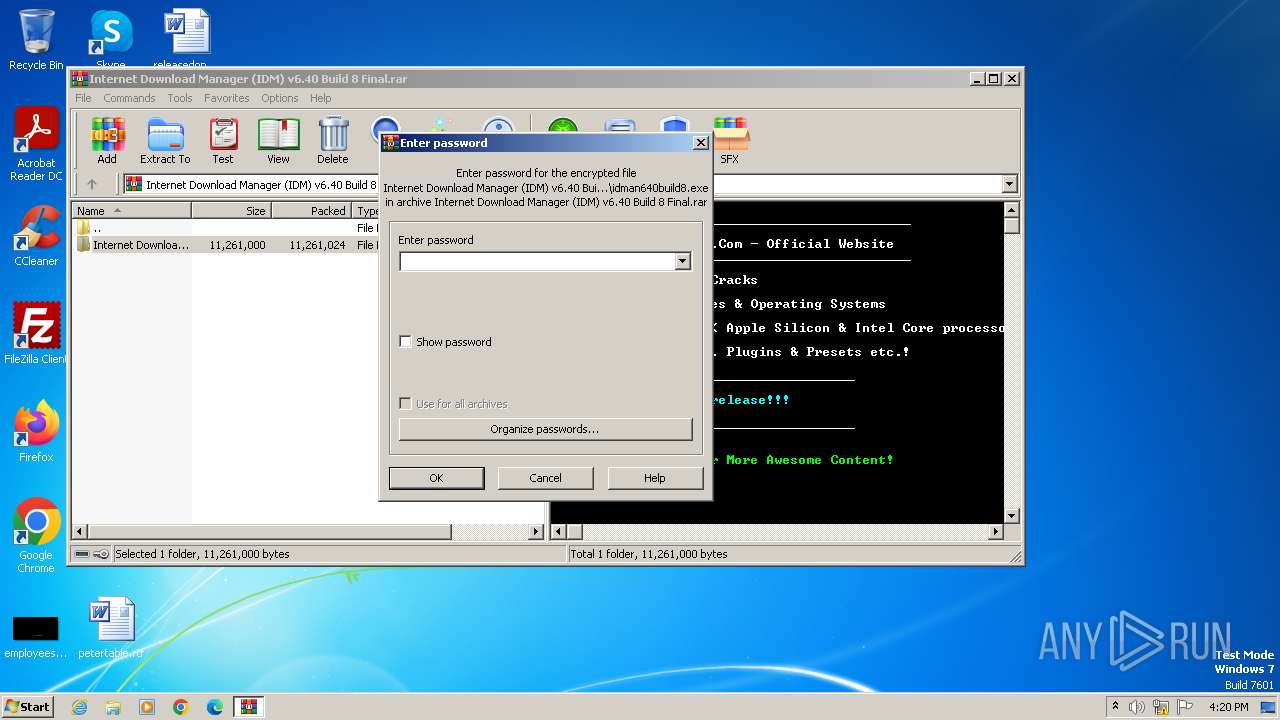
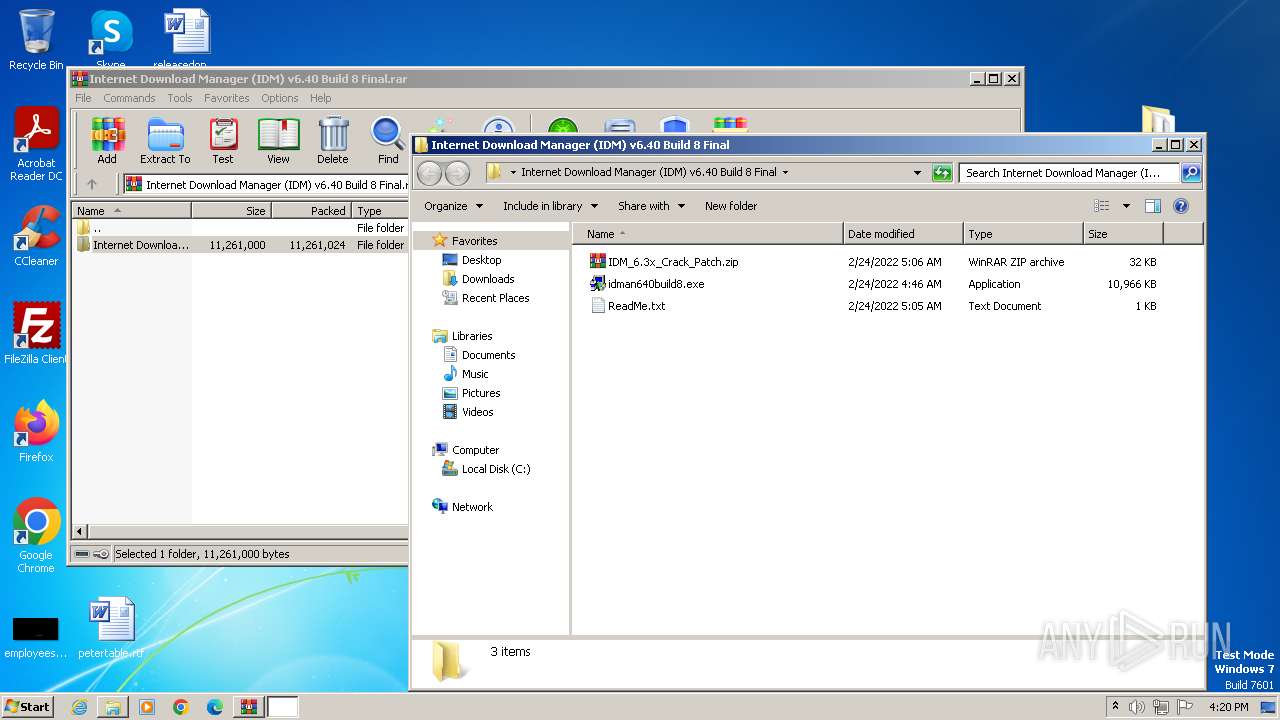
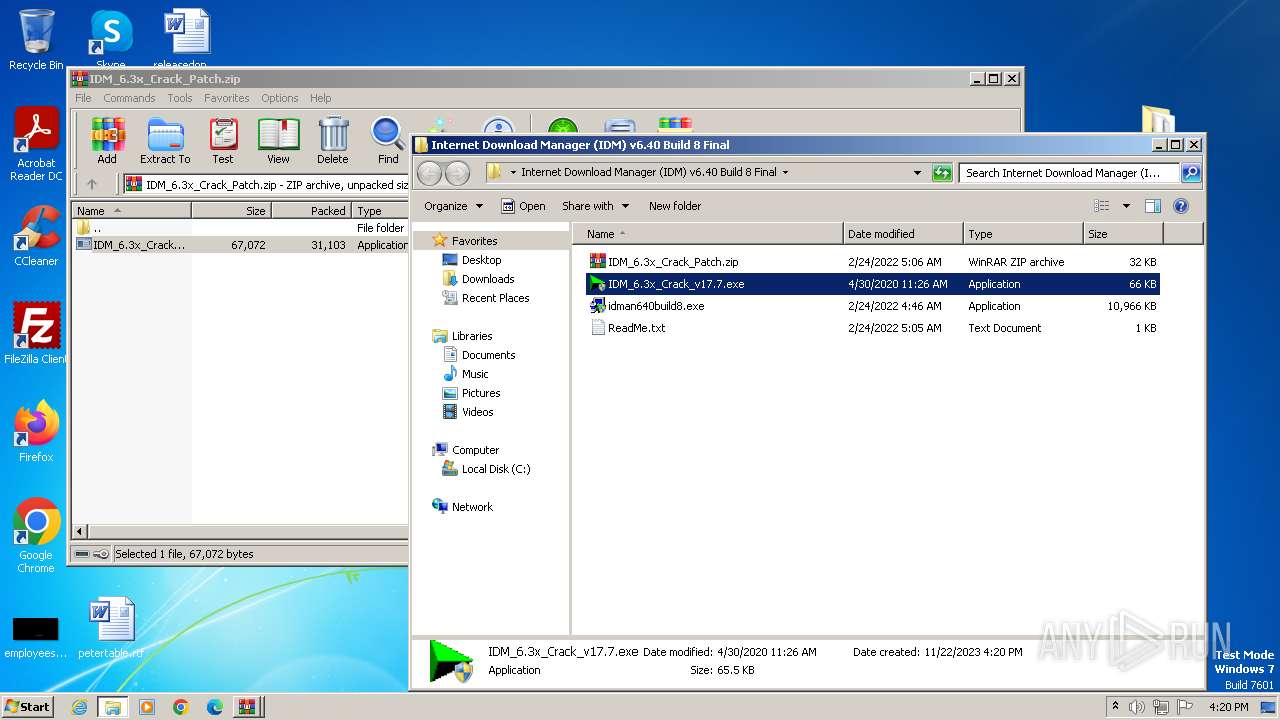
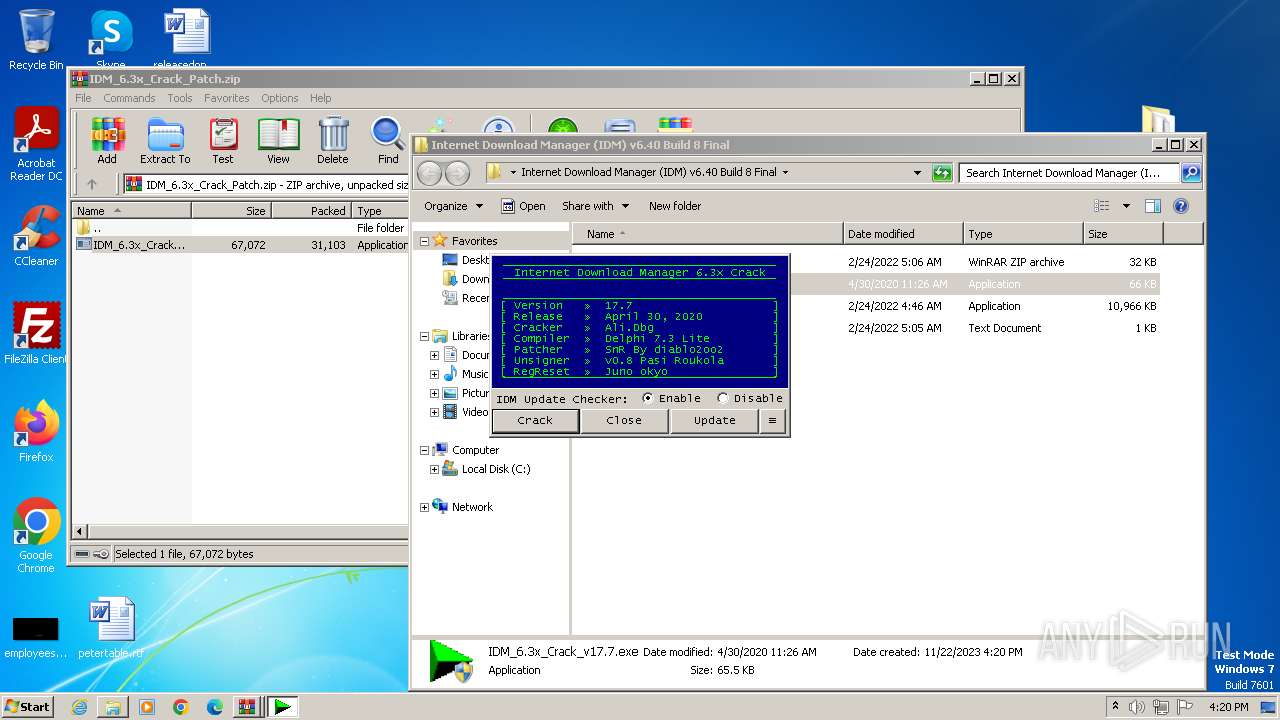
| File name: | Internet Download Manager (IDM) v6.40 Build 8 Final.rar |
| Full analysis: | https://app.any.run/tasks/f18e75bc-7c76-43aa-ad45-a91118f8943f |
| Verdict: | Malicious activity |
| Analysis date: | November 22, 2023, 16:19:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | DCB3FCDD791D9D65335336D38C0C4404 |
| SHA1: | 53473CDE543E635D0CF3ACB0F6B2B5F1D2218E7D |
| SHA256: | 5F6F9D6CE3A8BCD544EF0109308D440633F43FE8E386A3A5CD24D74B0B287AF6 |
| SSDEEP: | 98304:pjEJsk8vTG+IP6fzXDViRXGxQG8/9sR25lyJAFb/AWqBMfhjiVddy8HZj3G6VHPO:/rijPmjo1A/HCW7UH |
MALICIOUS
Creates a writable file in the system directory
- rundll32.exe (PID: 3536)
Drops the executable file immediately after the start
- IDMan.exe (PID: 3988)
- IDM_6.3x_Crack_v17.7.exe (PID: 328)
- wscript.exe (PID: 1416)
- UnSigner.exe (PID: 2992)
- UnSigner.exe (PID: 4076)
Starts NET.EXE for service management
- Uninstall.exe (PID: 3892)
- net.exe (PID: 2068)
Gets a file object corresponding to the file in a specified path (SCRIPT)
- wscript.exe (PID: 1416)
Accesses environment variables (SCRIPT)
- wscript.exe (PID: 1416)
Deletes a file (SCRIPT)
- wscript.exe (PID: 1416)
Copies file to a new location (SCRIPT)
- wscript.exe (PID: 1416)
Actions looks like stealing of personal data
- IDMan.exe (PID: 3996)
SUSPICIOUS
The process creates files with name similar to system file names
- IDM1.tmp (PID: 3880)
Starts application with an unusual extension
- idman640build8.exe (PID: 3756)
Reads the Internet Settings
- IDM1.tmp (PID: 3880)
- IDMan.exe (PID: 3988)
- runonce.exe (PID: 3592)
- Uninstall.exe (PID: 3892)
- IDMan.exe (PID: 3800)
- IDM_6.3x_Crack_v17.7.exe (PID: 328)
- IDMan.exe (PID: 3996)
Reads security settings of Internet Explorer
- IDMan.exe (PID: 3988)
- IDMan.exe (PID: 3800)
- IDMan.exe (PID: 3996)
Checks Windows Trust Settings
- IDMan.exe (PID: 3988)
- IDMan.exe (PID: 3800)
- IDMan.exe (PID: 3996)
Reads settings of System Certificates
- IDMan.exe (PID: 3988)
- IDMan.exe (PID: 3800)
- IDMan.exe (PID: 3996)
Creates/Modifies COM task schedule object
- IDMan.exe (PID: 3988)
- Uninstall.exe (PID: 3892)
Uses RUNDLL32.EXE to load library
- Uninstall.exe (PID: 3892)
Drops a system driver (possible attempt to evade defenses)
- rundll32.exe (PID: 3536)
Creates or modifies Windows services
- Uninstall.exe (PID: 3892)
The process executes VB scripts
- IDM_6.3x_Crack_v17.7.exe (PID: 328)
Searches for installed software
- IDM_6.3x_Crack_v17.7.exe (PID: 328)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 1416)
Checks whether a specific file exists (SCRIPT)
- wscript.exe (PID: 1416)
Gets full path of the running script (SCRIPT)
- wscript.exe (PID: 1416)
Uses TASKKILL.EXE to kill process
- IDM_6.3x_Crack_v17.7.exe (PID: 328)
Uses REG/REGEDIT.EXE to modify registry
- IDM_6.3x_Crack_v17.7.exe (PID: 328)
INFO
Manual execution by a user
- idman640build8.exe (PID: 3412)
- idman640build8.exe (PID: 3756)
- firefox.exe (PID: 4056)
- wmpnscfg.exe (PID: 1852)
- WinRAR.exe (PID: 3616)
- IDM_6.3x_Crack_v17.7.exe (PID: 1508)
- IDM_6.3x_Crack_v17.7.exe (PID: 328)
- IDMan.exe (PID: 3996)
- wmpnscfg.exe (PID: 2820)
- chrome.exe (PID: 4028)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3448)
- rundll32.exe (PID: 3536)
- WinRAR.exe (PID: 3616)
Create files in a temporary directory
- idman640build8.exe (PID: 3756)
- IDM1.tmp (PID: 3880)
- IDMan.exe (PID: 3988)
- IDMan.exe (PID: 3800)
- IDM_6.3x_Crack_v17.7.exe (PID: 328)
- IDMan.exe (PID: 3996)
Checks supported languages
- idman640build8.exe (PID: 3756)
- IDM1.tmp (PID: 3880)
- idmBroker.exe (PID: 3768)
- IDMan.exe (PID: 3988)
- Uninstall.exe (PID: 3892)
- MediumILStart.exe (PID: 916)
- wmpnscfg.exe (PID: 1852)
- IDMan.exe (PID: 3800)
- IEMonitor.exe (PID: 2784)
- IDM_6.3x_Crack_v17.7.exe (PID: 328)
- UnSigner.exe (PID: 2992)
- UnSigner.exe (PID: 4076)
- IDMan.exe (PID: 3996)
- IEMonitor.exe (PID: 2252)
- wmpnscfg.exe (PID: 2820)
Reads the machine GUID from the registry
- IDM1.tmp (PID: 3880)
- IDMan.exe (PID: 3988)
- wmpnscfg.exe (PID: 1852)
- MediumILStart.exe (PID: 916)
- IDMan.exe (PID: 3800)
- wmpnscfg.exe (PID: 2820)
- IDMan.exe (PID: 3996)
Creates files in the program directory
- IDM1.tmp (PID: 3880)
- IDMan.exe (PID: 3988)
- wscript.exe (PID: 1416)
Creates files or folders in the user directory
- IDM1.tmp (PID: 3880)
- IDMan.exe (PID: 3988)
- IDMan.exe (PID: 3800)
- IDMan.exe (PID: 3996)
Reads the computer name
- IDMan.exe (PID: 3988)
- IDM1.tmp (PID: 3880)
- Uninstall.exe (PID: 3892)
- wmpnscfg.exe (PID: 1852)
- MediumILStart.exe (PID: 916)
- IDMan.exe (PID: 3800)
- IEMonitor.exe (PID: 2784)
- IDM_6.3x_Crack_v17.7.exe (PID: 328)
- IDMan.exe (PID: 3996)
- wmpnscfg.exe (PID: 2820)
Application launched itself
- firefox.exe (PID: 4056)
- firefox.exe (PID: 4036)
- chrome.exe (PID: 4028)
Creates files in the driver directory
- rundll32.exe (PID: 3536)
Reads the time zone
- runonce.exe (PID: 3592)
The process uses the downloaded file
- chrome.exe (PID: 3244)
- chrome.exe (PID: 3088)
Checks proxy server information
- IDMan.exe (PID: 3996)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
114
Monitored processes
63
Malicious processes
8
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 272 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=4156 --field-trial-handle=1164,i,8751920619963005831,18294832257267788968,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 328 | "C:\Users\admin\Desktop\Internet Download Manager (IDM) v6.40 Build 8 Final\IDM_6.3x_Crack_v17.7.exe" | C:\Users\admin\Desktop\Internet Download Manager (IDM) v6.40 Build 8 Final\IDM_6.3x_Crack_v17.7.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 448 | reg.exe import C:\Users\admin\AppData\Local\Temp\IDMRegClean.reg | C:\Windows\System32\reg.exe | — | IDM_6.3x_Crack_v17.7.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 552 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2116 --field-trial-handle=1164,i,8751920619963005831,18294832257267788968,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 752 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="4036.1.1578651998\927319490" -parentBuildID 20230710165010 -prefsHandle 1424 -prefMapHandle 1420 -prefsLen 28600 -prefMapSize 244195 -appDir "C:\Program Files\Mozilla Firefox\browser" - {91c395d3-8897-4bd3-9823-ed27d6502d1f} 4036 "\\.\pipe\gecko-crash-server-pipe.4036" 1436 d226d50 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 916 | "C:\Program Files\Internet Download Manager\MediumILStart.exe" | C:\Program Files\Internet Download Manager\MediumILStart.exe | — | IDMan.exe | |||||||||||
User: admin Company: Internet Download Manager, Tonec Inc. Integrity Level: MEDIUM Description: IDM module Exit code: 0 Version: 6, 35, 9, 1 Modules
| |||||||||||||||
| 1208 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=4092 --field-trial-handle=1164,i,8751920619963005831,18294832257267788968,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1416 | wscript.exe "C:\Users\admin\AppData\Local\Temp\IDM_BAK.vbs" /idmdir:"C:\Program Files\Internet Download Manager\" | C:\Windows\System32\wscript.exe | — | IDM_6.3x_Crack_v17.7.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1508 | "C:\Users\admin\Desktop\Internet Download Manager (IDM) v6.40 Build 8 Final\IDM_6.3x_Crack_v17.7.exe" | C:\Users\admin\Desktop\Internet Download Manager (IDM) v6.40 Build 8 Final\IDM_6.3x_Crack_v17.7.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1616 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="4036.0.910329073\1953128927" -parentBuildID 20230710165010 -prefsHandle 1116 -prefMapHandle 1108 -prefsLen 28523 -prefMapSize 244195 -appDir "C:\Program Files\Mozilla Firefox\browser" - {43e64908-56dc-4c88-afe6-723be394dc4b} 4036 "\\.\pipe\gecko-crash-server-pipe.4036" 1188 d2a71a0 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 1 Version: 115.0.2 Modules
| |||||||||||||||
Total events
35 472
Read events
34 913
Write events
388
Delete events
171
Modification events
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3448) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3880) IDM1.tmp | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Control\Session Manager |
| Operation: | write | Name: | PendingFileRenameOperations |
Value: \??\C:\Users\admin\AppData\Local\Temp\IDM_Setup_Temp\IDM1.tmp | |||
| (PID) Process: | (3880) IDM1.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\AppID\{AC746233-E9D3-49CD-862F-068F7B7CCCA4} |
| Operation: | write | Name: | RunAs |
Value: Interactive User | |||
Executable files
21
Suspicious files
259
Text files
106
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3448.49088\Internet Download Manager (IDM) v6.40 Build 8 Final\idman640build8.exe | executable | |
MD5:80FAB5F13A6A1686C9591881CDC364E0 | SHA256:BC4DDDA7C4FABE5091E961B166280AFEEAF8DE617348757FC68D65DC5752A975 | |||
| 3880 | IDM1.tmp | C:\Users\admin\AppData\Local\Temp\IDM_Setup_Temp\IDMSetup2.log | binary | |
MD5:1C92BCB479B9EE7BBC5F5E6754B125B2 | SHA256:95EFFBCC2269DB3E96C984D8249D14DBCDD8D4CF6A43143CBA0D7D20F96DF991 | |||
| 3448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3448.49088\Internet Download Manager (IDM) v6.40 Build 8 Final\ReadMe.txt | text | |
MD5:56C223D36B9DA5812E8A7FB1DBFB3117 | SHA256:1DBE59E0F10225877EEC65B3CD2183D40DA602DF8525FFBB39310C7209A5F6D4 | |||
| 3880 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\IDM Help.lnk | binary | |
MD5:1609E5C6CCC2E6D143DF27F5F52701BF | SHA256:2F7E92E970AF8BFAF14098D509F6BE679FC3FC9CEA8DF72BF35B63E92FAF8F4D | |||
| 3448 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3448.49088\Internet Download Manager (IDM) v6.40 Build 8 Final\IDM_6.3x_Crack_Patch.zip | compressed | |
MD5:9CAAAECE522D513110767BB2A99C7A06 | SHA256:D16CA231B35D48AC00A603BFA0F859A8F5081210F3B0C423B5FC1FA8D1087470 | |||
| 3880 | IDM1.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\Uninstall IDM.lnk | binary | |
MD5:98563BBAEBCA19FABDD25F7F67F62E85 | SHA256:4BBB0034C2F7FB05D1FB4DA6A69AC7F4FB1888C560F40BB141DE79488A495B06 | |||
| 3880 | IDM1.tmp | C:\ProgramData\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\license.lnk | binary | |
MD5:42AE7FAE142D9E917F5378AAC019CB8F | SHA256:1586F12D840F52F65E2E5590C65AC93EF3D74331CF58248AA8D40F3B51C60DC1 | |||
| 3880 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\Uninstall IDM.lnk | binary | |
MD5:577FC6B6E64DD333DD0A0C2CF2710621 | SHA256:54521661DD16243EEDB8EDB335A1312750389307B71FD048991200ED9589E228 | |||
| 3880 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\license.lnk | binary | |
MD5:14B104CF9B533A477D34D0AF44CBD52F | SHA256:CB5732804CA648FF4523DF9713B890C25EE3815CDB1D99E6D2092865624BC960 | |||
| 3880 | IDM1.tmp | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Internet Download Manager\TUTORIALS.lnk | binary | |
MD5:CAC2E01AD03932CDB448FC87BF31D6D9 | SHA256:BB5431651CFFDAA9BEF7298B33F2BB4CA50492FED4269C32640AFDC5F86EF374 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
49
DNS requests
103
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3988 | IDMan.exe | GET | 200 | 87.248.202.1:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?9e9dcd5ef0e7ccab | unknown | compressed | 61.6 Kb | unknown |
4036 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | text | 90 b | unknown |
4036 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | text | 8 b | unknown |
4036 | firefox.exe | POST | 200 | 184.24.77.51:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
4036 | firefox.exe | POST | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 472 b | unknown |
4036 | firefox.exe | POST | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 472 b | unknown |
4036 | firefox.exe | POST | 200 | 184.24.77.51:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
4036 | firefox.exe | POST | 200 | 142.250.186.163:80 | http://ocsp.pki.goog/gts1c3 | unknown | binary | 472 b | unknown |
4036 | firefox.exe | POST | 200 | 184.24.77.51:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
4036 | firefox.exe | POST | 200 | 184.24.77.51:80 | http://r3.o.lencr.org/ | unknown | binary | 503 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3988 | IDMan.exe | 87.248.202.1:80 | ctldl.windowsupdate.com | LLNW | NL | unknown |
4036 | firefox.exe | 169.61.27.133:443 | secure.internetdownloadmanager.com | SOFTLAYER | US | unknown |
4036 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
4036 | firefox.exe | 34.117.237.239:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
4036 | firefox.exe | 3.218.237.85:443 | spocs.getpocket.com | AMAZON-AES | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
test.internetdownloadmanager.com |
| whitelisted |
secure.internetdownloadmanager.com |
| whitelisted |
www.internetdownloadmanager.com |
| whitelisted |
mirror3.internetdownloadmanager.com |
| whitelisted |
mirror5.internetdownloadmanager.com |
| whitelisted |
registeridm.com |
| unknown |
detectportal.firefox.com |
| whitelisted |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
example.org |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3996 | IDMan.exe | Potential Corporate Privacy Violation | ET POLICY Outgoing Basic Auth Base64 HTTP Password detected unencrypted |