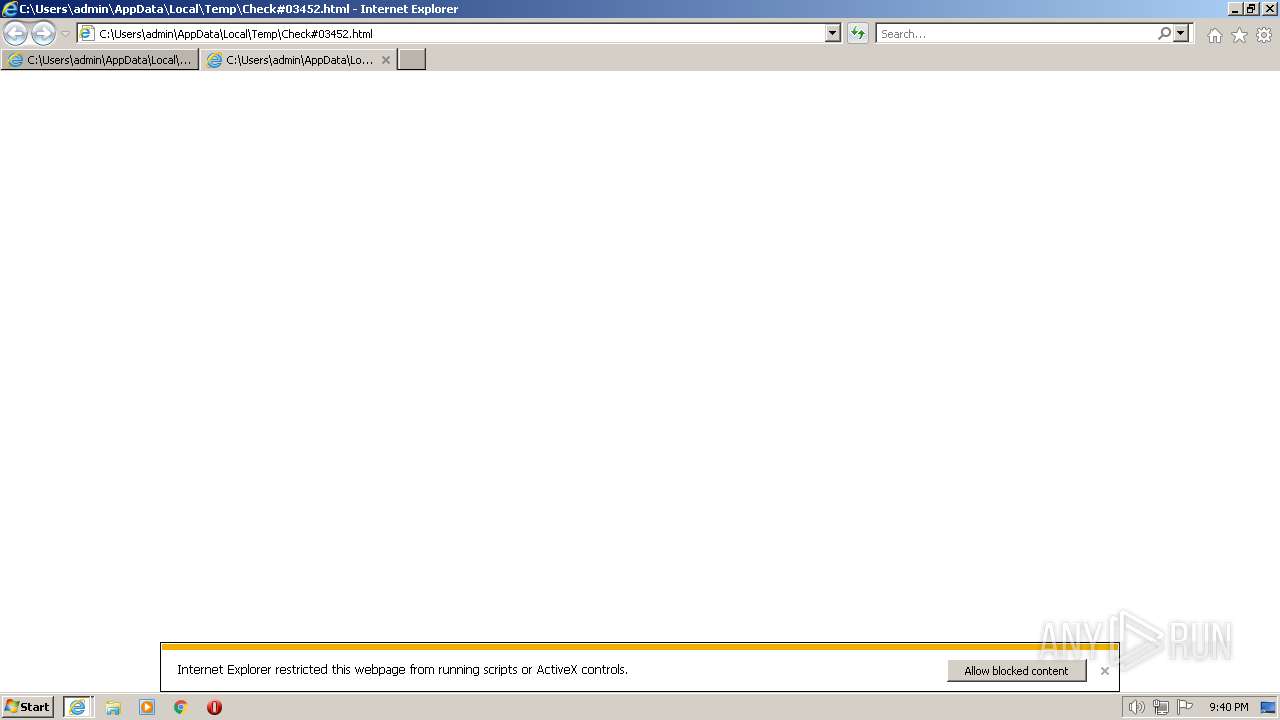
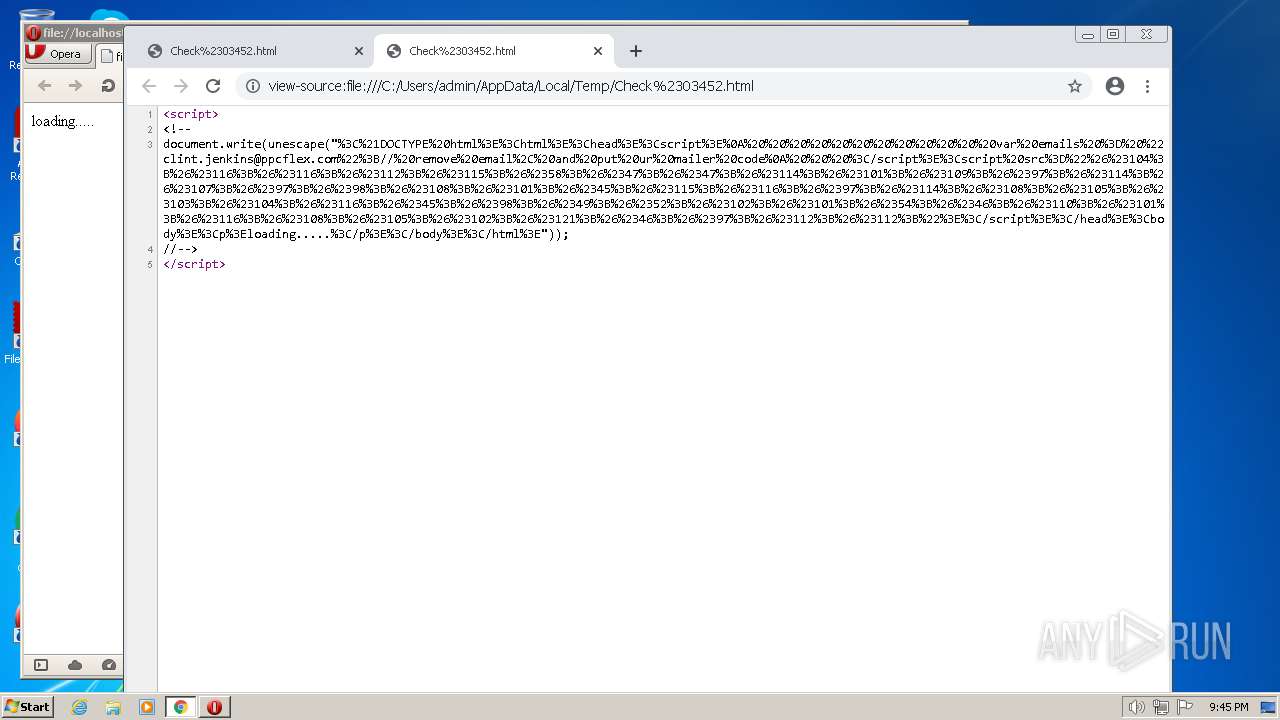
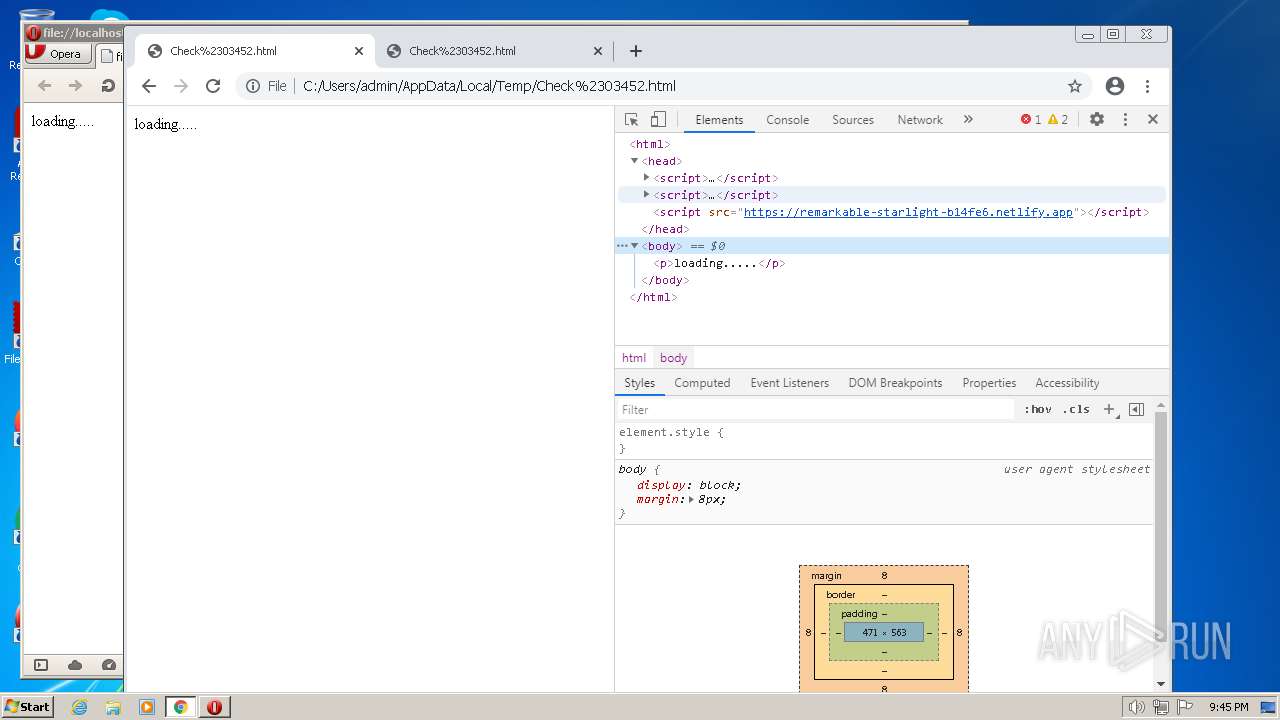
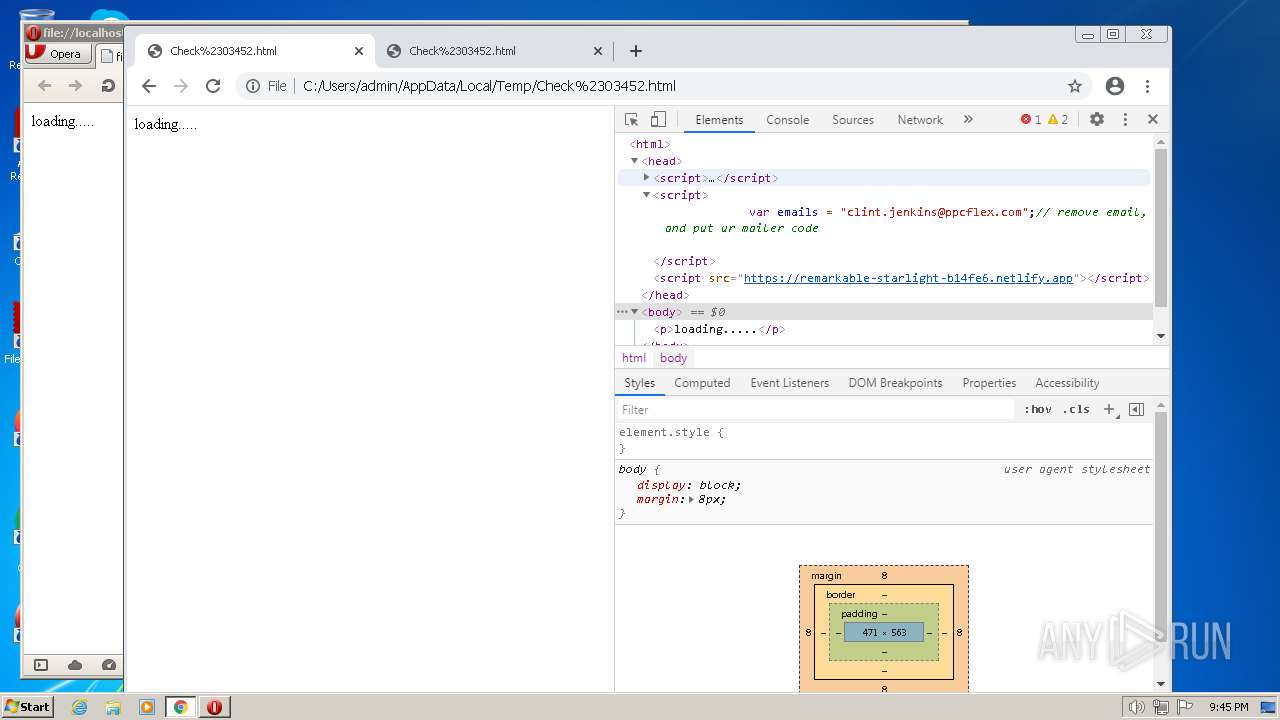
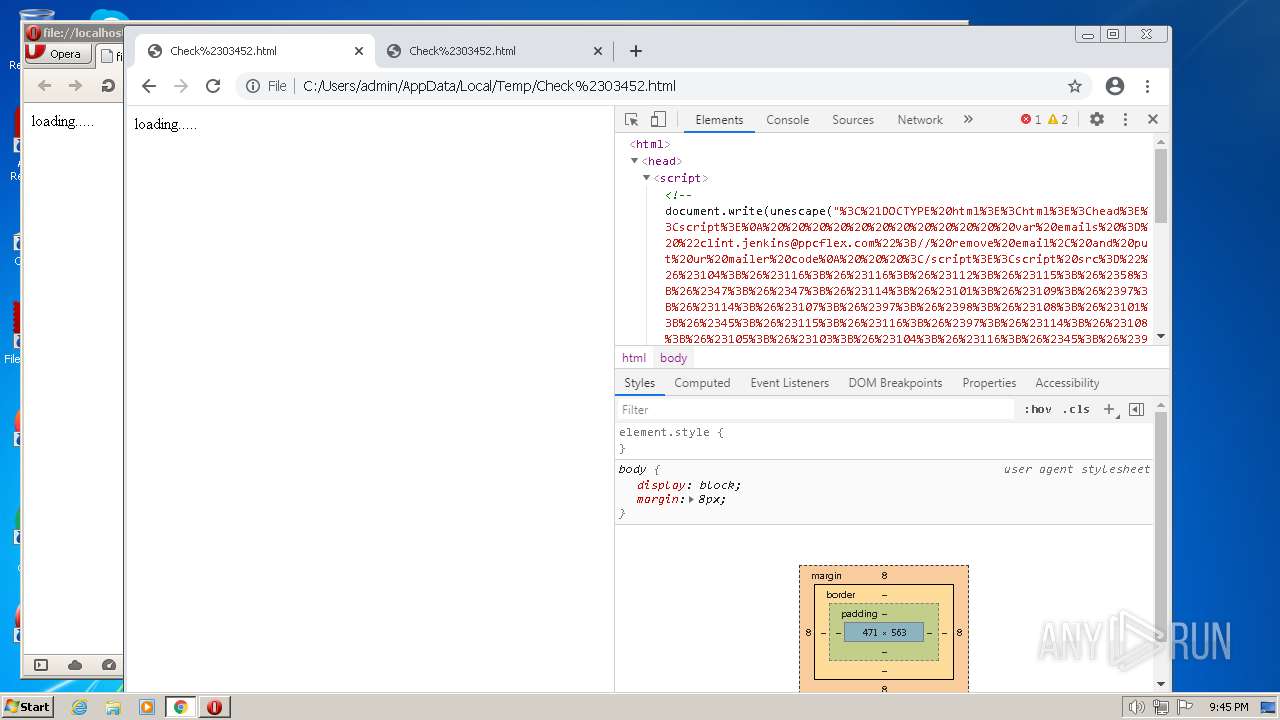
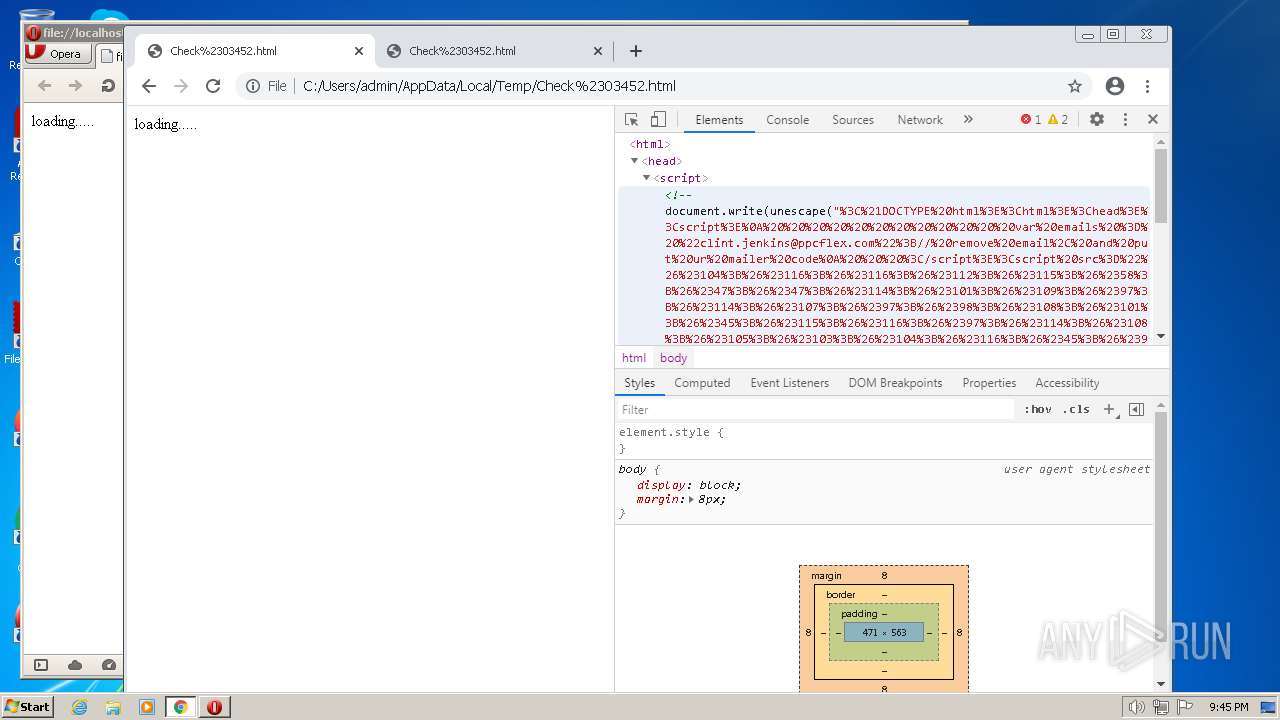
| File name: | Check#03452.html |
| Full analysis: | https://app.any.run/tasks/bde3bc85-7249-4517-b666-a03b67570161 |
| Verdict: | Malicious activity |
| Analysis date: | December 05, 2022, 21:40:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, ASCII text, with very long lines, with CRLF line terminators |
| MD5: | C4CB9C9BF6CF57CBA7113FF363DB0A8B |
| SHA1: | 6829CC4F8312FA086F335E3E508DBAFA57B7F758 |
| SHA256: | 5F6E55A30C109255066B656419D33F1BFFBEC813455E1ECF8D1355C64A448504 |
| SSDEEP: | 24:7o0dqAGAWGQndRlBA+BA5aTTUzUzN+MK/b:7oaqGulL2U/UzaKT |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Manual execution by a user
- chrome.exe (PID: 3092)
- opera.exe (PID: 1464)
Application launched itself
- iexplore.exe (PID: 1960)
- iexplore.exe (PID: 1540)
- chrome.exe (PID: 3092)
Drops a file that was compiled in debug mode
- chrome.exe (PID: 1456)
Executable content was dropped or overwritten
- chrome.exe (PID: 1456)
Drops the executable file immediately after the start
- chrome.exe (PID: 1456)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .html | | | HyperText Markup Language (100) |
|---|
Total processes
72
Monitored processes
36
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 268 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1104,3656219737670116171,11973629718961294773,131072 --enable-features=PasswordImport --lang=en-US --instant-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1956 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 404 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1104,3656219737670116171,11973629718961294773,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1856 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 632 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1540 CREDAT:5649409 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1020 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1104,3656219737670116171,11973629718961294773,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=27 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1032 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1240 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1104,3656219737670116171,11973629718961294773,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1032 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1456 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1104,3656219737670116171,11973629718961294773,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1832 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1464 | "C:\Program Files\Opera\opera.exe" | C:\Program Files\Opera\opera.exe | Explorer.EXE | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Exit code: 0 Version: 1748 Modules
| |||||||||||||||
| 1540 | "C:\Program Files\Internet Explorer\iexplore.exe" "C:\Users\admin\AppData\Local\Temp\Check#03452.html" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1808 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1104,3656219737670116171,11973629718961294773,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=668 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1828 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --field-trial-handle=1104,3656219737670116171,11973629718961294773,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=1032 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
16 281
Read events
15 956
Write events
319
Delete events
6
Modification events
| (PID) Process: | (1540) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (1540) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (1540) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 31000818 | |||
| (PID) Process: | (1540) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (1540) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 31000818 | |||
| (PID) Process: | (1540) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1540) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1540) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1540) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1540) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
1
Suspicious files
91
Text files
158
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3092 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\BrowserMetrics\BrowserMetrics-638E6571-C14.pma | — | |
MD5:— | SHA256:— | |||
| 1540 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF418CE1634FA032FC.TMP | gmc | |
MD5:— | SHA256:— | |||
| 1540 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF165C883B2312487F.TMP | gmc | |
MD5:— | SHA256:— | |||
| 1540 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFDE91B4CFB81F1E8E.TMP | gmc | |
MD5:— | SHA256:— | |||
| 1540 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Last Active\{8373AD45-74E5-11ED-80DA-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 1540 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{7A82DBC7-74E5-11ED-80DA-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 1540 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{7A82DBC8-74E5-11ED-80DA-12A9866C77DE}.dat | binary | |
MD5:— | SHA256:— | |||
| 1540 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DFC30BF48395432F39.TMP | gmc | |
MD5:— | SHA256:— | |||
| 1540 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF9516512D02DF1445.TMP | gmc | |
MD5:— | SHA256:— | |||
| 3168 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\CrashpadMetrics.pma | binary | |
MD5:03C4F648043A88675A920425D824E1B3 | SHA256:F91DBB7C64B4582F529C968C480D2DCE1C8727390482F31E4355A27BB3D9B450 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
37
TCP/UDP connections
58
DNS requests
23
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
868 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | — | — | whitelisted |
868 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/YGkwa4MXjfWSuERyWQYP_A_4/aapLKTSZ439A-0g3nqJr3Q | US | crx | 384 Kb | whitelisted |
868 | svchost.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/APhHMzuprJvS7ixvnAk_gdI_1/anGnv31dmOJhheXBnYQ3gw | US | crx | 384 Kb | whitelisted |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 9.67 Kb | whitelisted |
1540 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/Omniroot2025.crl | US | der | 7.78 Kb | whitelisted |
1464 | opera.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 740 b | whitelisted |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 12.2 Kb | whitelisted |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 9.16 Kb | whitelisted |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 9.36 Kb | whitelisted |
868 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ac5q25btpqhkjhcekqoslcldvuya_1.3.36.141/ihnlcenocehgdaegdmhbidjhnhdchfmm_1.3.36.141_win_ehzjmd5kjmert7jdgsrj4xqxj4.crx3 | US | binary | 14.7 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 204.79.197.200:443 | www.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 142.250.185.67:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
2008 | chrome.exe | 142.250.185.174:443 | clients2.google.com | GOOGLE | US | whitelisted |
2008 | chrome.exe | 142.250.186.164:443 | www.google.com | GOOGLE | US | whitelisted |
2008 | chrome.exe | 142.250.186.45:443 | accounts.google.com | GOOGLE | US | suspicious |
2008 | chrome.exe | 142.250.185.67:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
2008 | chrome.exe | 142.250.186.161:443 | clients2.googleusercontent.com | GOOGLE | US | whitelisted |
2008 | chrome.exe | 142.250.185.234:443 | fonts.googleapis.com | GOOGLE | US | whitelisted |
2008 | chrome.exe | 142.250.186.131:443 | www.gstatic.com | GOOGLE | US | whitelisted |
2008 | chrome.exe | 34.141.55.250:443 | remarkable-starlight-b14fe6.netlify.app | GOOGLE-CLOUD-PLATFORM | DE | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
clients2.google.com |
| whitelisted |
www.google.com |
| malicious |
clients2.googleusercontent.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
remarkable-starlight-b14fe6.netlify.app |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Suspicious Netlify Hosted DNS Request - Possible Phishing Landing |
2008 | chrome.exe | Misc activity | ET INFO Suspicious Netlify Hosted TLS SNI Request - Possible Phishing Landing |
2008 | chrome.exe | Misc activity | ET INFO Suspicious Netlify Hosted TLS SNI Request - Possible Phishing Landing |
— | — | Misc activity | ET INFO Suspicious Netlify Hosted DNS Request - Possible Phishing Landing |
1464 | opera.exe | Misc activity | ET INFO Suspicious Netlify Hosted TLS SNI Request - Possible Phishing Landing |
1464 | opera.exe | Misc activity | ET INFO Suspicious Netlify Hosted TLS SNI Request - Possible Phishing Landing |