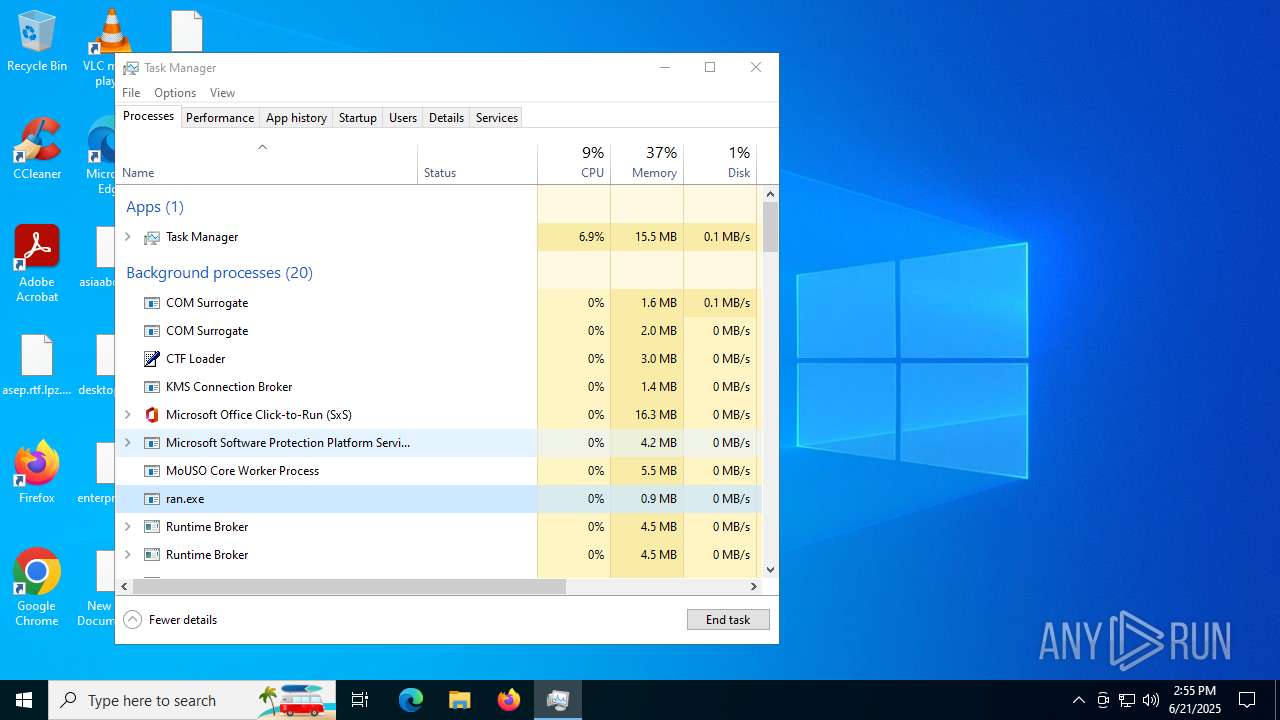
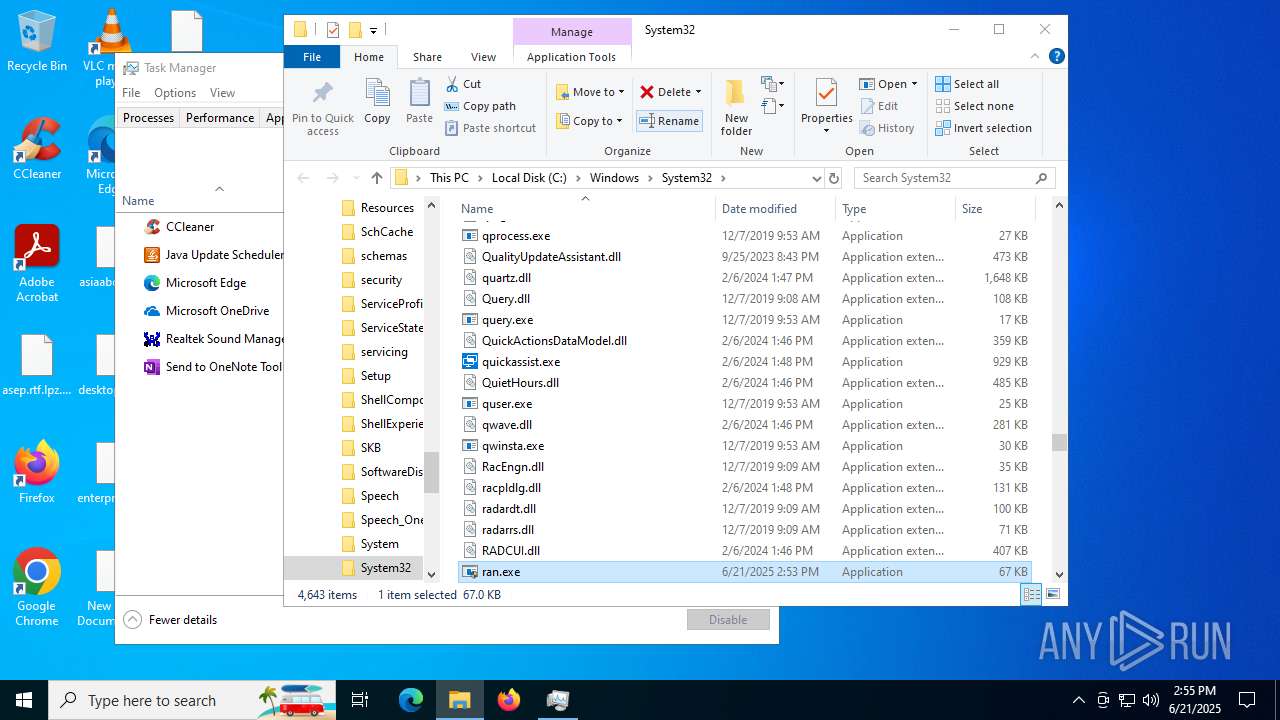
| File name: | ran.exe |
| Full analysis: | https://app.any.run/tasks/1f69c76f-92f1-47a2-8132-8fc82936bee8 |
| Verdict: | Malicious activity |
| Analysis date: | June 21, 2025, 14:53:30 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows, 6 sections |
| MD5: | 8259E1E7EB00D46D5F71BB9EB8D55DF1 |
| SHA1: | FF7B5099DF660BF50E9297E73E99776E91E40C14 |
| SHA256: | 5F4727541F473EF316FF8E4A1F9F6387F1A0293765E3BF660DC0D4EC23522432 |
| SSDEEP: | 768:gPf25p6gNRdFQiZGsw0X0PW+pChHlr6F07ehqyHssssskCHs8sfyk7EZS8KiWO:gPfFg7dFQiZ1w0X0PWxhHl9YwgRi |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- ran.exe (PID: 2076)
Reads the date of Windows installation
- ran.exe (PID: 2076)
Reads security settings of Internet Explorer
- ran.exe (PID: 2076)
Starts itself from another location
- ran.exe (PID: 2076)
Detected use of alternative data streams (AltDS)
- svchost.exe (PID: 2260)
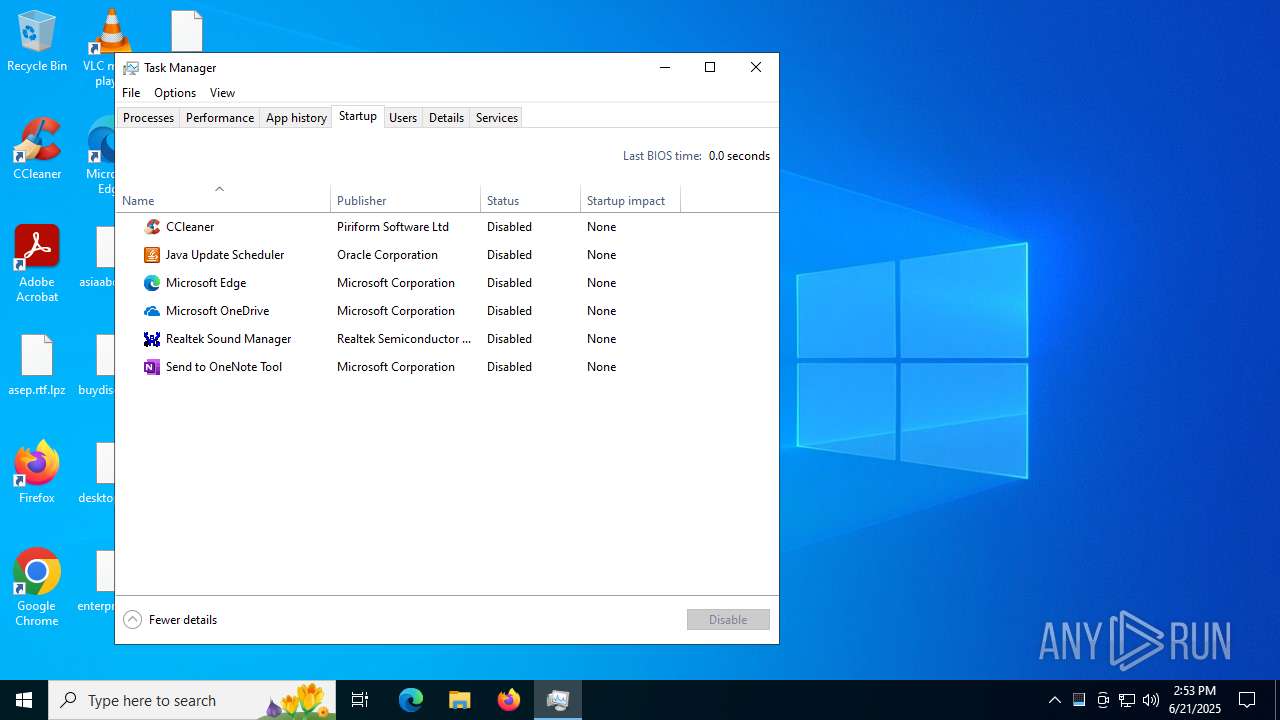
The process executes via Task Scheduler
- updater.exe (PID: 4100)
- ran.exe (PID: 4144)
- PLUGScheduler.exe (PID: 4108)
Application launched itself
- updater.exe (PID: 4100)
Searches for installed software
- svchost.exe (PID: 1488)
INFO
Reads the computer name
- ran.exe (PID: 2076)
- ran.exe (PID: 5168)
- OfficeClickToRun.exe (PID: 3012)
- updater.exe (PID: 4100)
- TrustedInstaller.exe (PID: 5108)
- ran.exe (PID: 4144)
- PLUGScheduler.exe (PID: 4108)
Checks supported languages
- ran.exe (PID: 2076)
- ran.exe (PID: 5168)
- OfficeClickToRun.exe (PID: 3012)
- PLUGScheduler.exe (PID: 4108)
- ran.exe (PID: 4144)
- updater.exe (PID: 5024)
- updater.exe (PID: 4100)
- TrustedInstaller.exe (PID: 5108)
Process checks computer location settings
- ran.exe (PID: 2076)
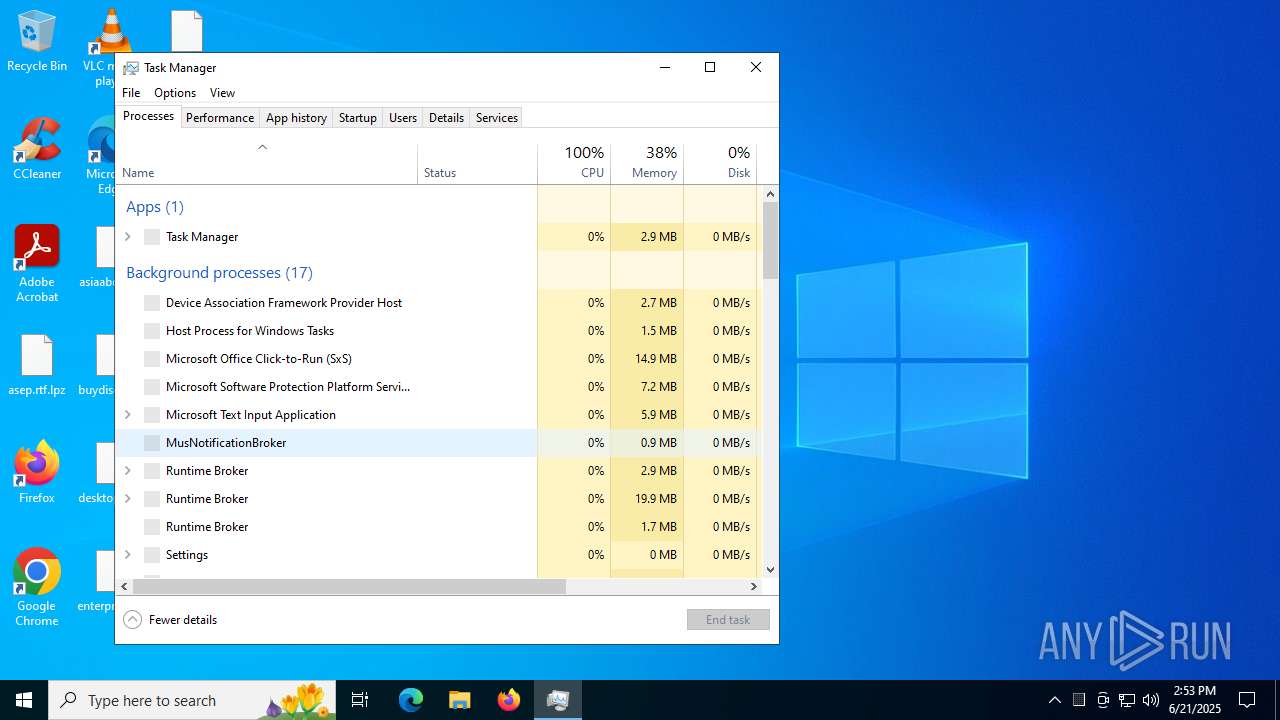
Manual execution by a user
- Taskmgr.exe (PID: 5340)
- Taskmgr.exe (PID: 6612)
- notepad.exe (PID: 2368)
- svchost.exe (PID: 2040)
- svchost.exe (PID: 2152)
- sppsvc.exe (PID: 2288)
- svchost.exe (PID: 2336)
- svchost.exe (PID: 2416)
- svchost.exe (PID: 2420)
- svchost.exe (PID: 2432)
- svchost.exe (PID: 2560)
- svchost.exe (PID: 2568)
- svchost.exe (PID: 2764)
- spoolsv.exe (PID: 2660)
- svchost.exe (PID: 2584)
- svchost.exe (PID: 2848)
- svchost.exe (PID: 2932)
- svchost.exe (PID: 3000)
- OfficeClickToRun.exe (PID: 3012)
- svchost.exe (PID: 3032)
- svchost.exe (PID: 2244)
- svchost.exe (PID: 2712)
- svchost.exe (PID: 2492)
- svchost.exe (PID: 2576)
- svchost.exe (PID: 2572)
- svchost.exe (PID: 2260)
- svchost.exe (PID: 3236)
- svchost.exe (PID: 3308)
- svchost.exe (PID: 3868)
- svchost.exe (PID: 3812)
- svchost.exe (PID: 2668)
- svchost.exe (PID: 3116)
- svchost.exe (PID: 3924)
- svchost.exe (PID: 3984)
- svchost.exe (PID: 3996)
- svchost.exe (PID: 3632)
- svchost.exe (PID: 3948)
- svchost.exe (PID: 4356)
- svchost.exe (PID: 4224)
- svchost.exe (PID: 3916)
- svchost.exe (PID: 4084)
- svchost.exe (PID: 4832)
- TrustedInstaller.exe (PID: 5108)
- svchost.exe (PID: 5184)
- svchost.exe (PID: 5484)
- svchost.exe (PID: 4500)
- Taskmgr.exe (PID: 5160)
- svchost.exe (PID: 5920)
- svchost.exe (PID: 636)
- svchost.exe (PID: 1488)
- Taskmgr.exe (PID: 1388)
- svchost.exe (PID: 5704)
- svchost.exe (PID: 5784)
Reads security settings of Internet Explorer
- Taskmgr.exe (PID: 6612)
- notepad.exe (PID: 2368)
- svchost.exe (PID: 2576)
- svchost.exe (PID: 3948)
- svchost.exe (PID: 3632)
- svchost.exe (PID: 4224)
- Taskmgr.exe (PID: 1388)
Reads the time zone
- svchost.exe (PID: 2576)
- svchost.exe (PID: 2244)
- svchost.exe (PID: 5184)
Creates files in the program directory
- svchost.exe (PID: 2432)
- svchost.exe (PID: 3868)
- svchost.exe (PID: 5184)
- PLUGScheduler.exe (PID: 4108)
Reads Microsoft Office registry keys
- OfficeClickToRun.exe (PID: 3012)
Disables trace logs
- svchost.exe (PID: 3308)
Reads the software policy settings
- OfficeClickToRun.exe (PID: 3012)
- consent.exe (PID: 952)
Reads the machine GUID from the registry
- OfficeClickToRun.exe (PID: 3012)
Checks proxy server information
- OfficeClickToRun.exe (PID: 3012)
- svchost.exe (PID: 3632)
Process checks whether UAC notifications are on
- updater.exe (PID: 4100)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:06:21 14:53:19+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.44 |
| CodeSize: | 42496 |
| InitializedDataSize: | 31744 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa31c |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
290
Monitored processes
63
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 636 | C:\WINDOWS\system32\svchost.exe -k netsvcs -p -s Appinfo | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 952 | consent.exe 636 316 000001C731A30170 | C:\Windows\System32\consent.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Consent UI for administrative applications Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1388 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\Windows\System32\Taskmgr.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1488 | C:\WINDOWS\system32\svchost.exe -k LocalSystemNetworkRestricted -p -s PcaSvc | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2040 | C:\WINDOWS\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s AudioEndpointBuilder | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2076 | "C:\Users\admin\AppData\Local\Temp\ran.exe" | C:\Users\admin\AppData\Local\Temp\ran.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2076 | C:\WINDOWS\system32\svchost.exe -k LocalServiceNetworkRestricted -p -s WinHttpAutoProxySvc | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2152 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2244 | C:\WINDOWS\System32\svchost.exe -k LocalServiceNoNetwork -p -s DPS | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2260 | C:\WINDOWS\System32\svchost.exe -k LocalSystemNetworkRestricted -p -s TrkWks | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
60 924
Read events
43 962
Write events
16 912
Delete events
50
Modification events
| (PID) Process: | (2076) ran.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2076) ran.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2076) ran.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2076) ran.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6612) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | delete value | Name: | Preferences |
Value: | |||
| (PID) Process: | (6612) Taskmgr.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\TaskManager |
| Operation: | write | Name: | Preferences |
Value: 0D00000060000000600000006800000068000000E3010000DC010000000001000000008000000080D8010080DF010080000100016B00000034000000130300008C020000E80300000000000000000000000000000F000000010000000000000058AAEE82F77F00000000000000000000000000002E0100001E0000008990000000000000FF00000001015002000000000D0000000000000098AAEE82F77F00000000000000000000FFFFFFFF960000001E0000008B900000010000000000000000101001000000000300000000000000B0AAEE82F77F00000000000000000000FFFFFFFF780000001E0000008C900000020000000000000001021200000000000400000000000000C8AAEE82F77F00000000000000000000FFFFFFFF960000001E0000008D900000030000000000000000011001000000000200000000000000E8AAEE82F77F00000000000000000000FFFFFFFF320000001E0000008A90000004000000000000000008200100000000050000000000000000ABEE82F77F00000000000000000000FFFFFFFFC80000001E0000008E90000005000000000000000001100100000000060000000000000028ABEE82F77F00000000000000000000FFFFFFFF040100001E0000008F90000006000000000000000001100100000000070000000000000050ABEE82F77F00000000000000000000FFFFFFFF49000000490000009090000007000000000000000004250000000000080000000000000080AAEE82F77F00000000000000000000FFFFFFFF49000000490000009190000008000000000000000004250000000000090000000000000070ABEE82F77F00000000000000000000FFFFFFFF490000004900000092900000090000000000000000042508000000000A0000000000000088ABEE82F77F00000000000000000000FFFFFFFF4900000049000000939000000A0000000000000000042508000000000B00000000000000A8ABEE82F77F00000000000000000000FFFFFFFF490000004900000039A000000B0000000000000000042509000000001C00000000000000C8ABEE82F77F00000000000000000000FFFFFFFFC8000000490000003AA000000C0000000000000000011009000000001D00000000000000F0ABEE82F77F00000000000000000000FFFFFFFF64000000490000004CA000000D0000000000000000021508000000001E0000000000000010ACEE82F77F00000000000000000000FFFFFFFF64000000490000004DA000000E000000000000000002150800000000030000000A000000010000000000000058AAEE82F77F0000000000000000000000000000D70000001E0000008990000000000000FF00000001015002000000000400000000000000C8AAEE82F77F0000000000000000000001000000960000001E0000008D900000010000000000000001011000000000000300000000000000B0AAEE82F77F00000000000000000000FFFFFFFF640000001E0000008C900000020000000000000000021000000000000C0000000000000040ACEE82F77F0000000000000000000003000000640000001E00000094900000030000000000000001021000000000000D0000000000000068ACEE82F77F00000000000000000000FFFFFFFF640000001E00000095900000040000000000000000011001000000000E0000000000000090ACEE82F77F0000000000000000000005000000320000001E00000096900000050000000000000001042001000000000F00000000000000B8ACEE82F77F0000000000000000000006000000320000001E00000097900000060000000000000001042001000000001000000000000000D8ACEE82F77F0000000000000000000007000000460000001E00000098900000070000000000000001011001000000001100000000000000F8ACEE82F77F00000000000000000000FFFFFFFF640000001E0000009990000008000000000000000001100100000000060000000000000028ABEE82F77F0000000000000000000009000000040100001E0000008F9000000900000000000000010110010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000040000000B000000010000000000000058AAEE82F77F0000000000000000000000000000D70000001E0000009E90000000000000FF0000000101500200000000120000000000000020ADEE82F77F00000000000000000000FFFFFFFF2D0000001E0000009B90000001000000000000000004200100000000140000000000000040ADEE82F77F00000000000000000000FFFFFFFF640000001E0000009D90000002000000000000000001100100000000130000000000000068ADEE82F77F00000000000000000000FFFFFFFF640000001E0000009C900000030000000000000000011001000000000300000000000000B0AAEE82F77F00000000000000000000FFFFFFFF640000001E0000008C90000004000000000000000102100000000000070000000000000050ABEE82F77F000000000000000000000500000049000000490000009090000005000000000000000104210000000000080000000000000080AAEE82F77F000000000000000000000600000049000000490000009190000006000000000000000104210000000000090000000000000070ABEE82F77F0000000000000000000007000000490000004900000092900000070000000000000001042108000000000A0000000000000088ABEE82F77F0000000000000000000008000000490000004900000093900000080000000000000001042108000000000B00000000000000A8ABEE82F77F0000000000000000000009000000490000004900000039A00000090000000000000001042109000000001C00000000000000C8ABEE82F77F000000000000000000000A00000064000000490000003AA000000A00000000000000000110090000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000200000008000000010000000000000058AAEE82F77F0000000000000000000000000000C60000001E000000B090000000000000FF0000000101500200000000150000000000000088ADEE82F77F00000000000000000000FFFFFFFF6B0000001E000000B1900000010000000000000000042500000000001600000000000000B8ADEE82F77F00000000000000000000FFFFFFFF6B0000001E000000B2900000020000000000000000042500000000001800000000000000E0ADEE82F77F00000000000000000000FFFFFFFF6B0000001E000000B490000003000000000000000004250000000000170000000000000008AEEE82F77F00000000000000000000FFFFFFFF6B0000001E000000B390000004000000000000000004250000000000190000000000000040AEEE82F77F00000000000000000000FFFFFFFFA00000001E000000B5900000050000000000000000042001000000001A0000000000000070AEEE82F77F00000000000000000000FFFFFFFF7D0000001E000000B6900000060000000000000000042001000000001B00000000000000A0AEEE82F77F00000000000000000000FFFFFFFF7D0000001E000000B790000007000000000000000004200100000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000010000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA00000000000000000000000000000000000000000000009D200000200000009100000064000000320000006400000050000000320000003200000028000000500000003C0000005000000050000000320000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C00000050000000500000009700000032000000780000003200000050000000500000005000000050000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000DA000000000000000000000000000000000000009D200000200000009100000064000000320000009700000050000000320000003200000028000000500000003C000000500000005000000032000000500000005000000050000000500000005000000050000000500000002800000050000000230000002300000023000000230000005000000050000000500000003200000032000000320000007800000078000000500000003C0000005000000064000000780000003200000078000000780000003200000050000000500000005000000050000000C8000000000000000100000002000000030000000400000005000000060000000700000008000000090000000A0000000B0000000C0000000D0000000E0000000F000000100000001100000012000000130000001400000015000000160000001700000018000000190000001A0000001B0000001C0000001D0000001E0000001F000000200000002100000022000000230000002400000025000000260000002700000028000000290000002A0000002B0000002C0000002D0000002E0000002F00000000000000000000001F00000000000000B400000032000000D8000000640000006400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000100000002000000030000000400000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000001000000000000000000000000000000 | |||
| (PID) Process: | (2076) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad\d4-da-6d-d6-67-03 |
| Operation: | write | Name: | WpadDecisionReason |
Value: 1 | |||
| (PID) Process: | (2076) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad\d4-da-6d-d6-67-03 |
| Operation: | write | Name: | WpadDecisionTime |
Value: A4F6756ABCE2DB01 | |||
| (PID) Process: | (2076) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad\d4-da-6d-d6-67-03 |
| Operation: | write | Name: | WpadDecision |
Value: 0 | |||
| (PID) Process: | (2076) svchost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Wpad\d4-da-6d-d6-67-03 |
| Operation: | delete value | Name: | WpadDetectedUrl |
Value: | |||
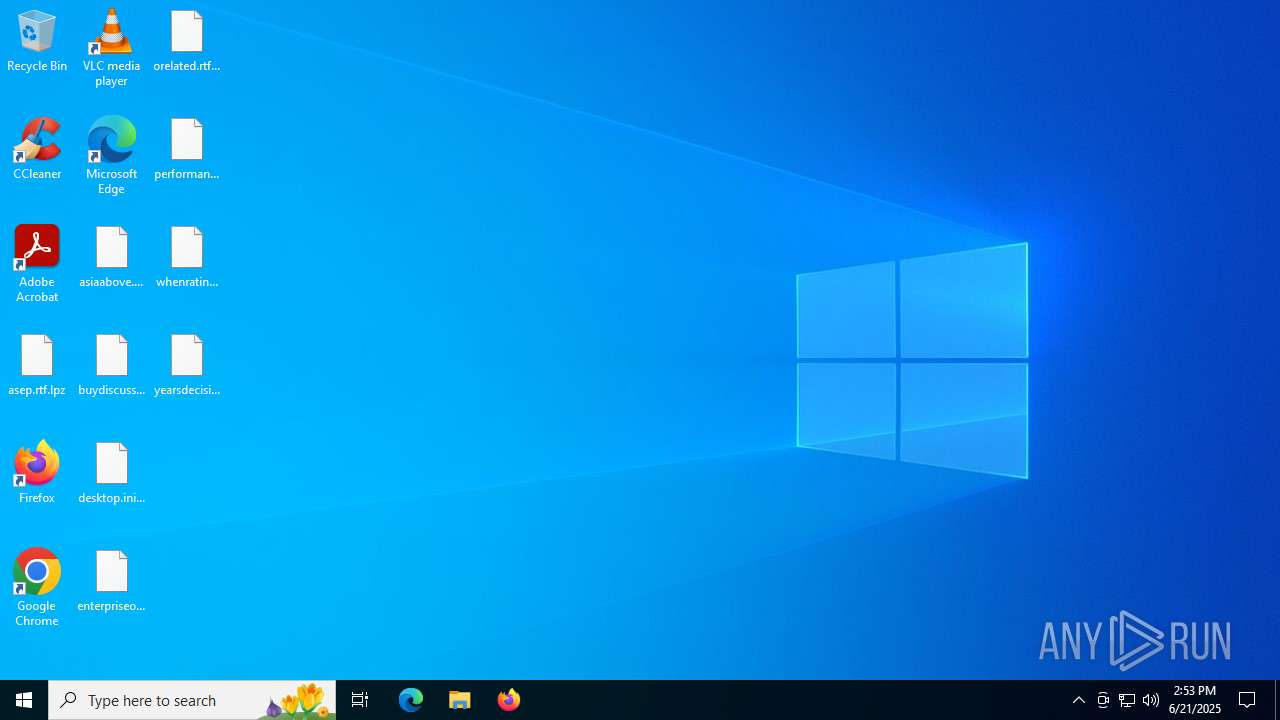
Executable files
1
Suspicious files
134
Text files
43
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
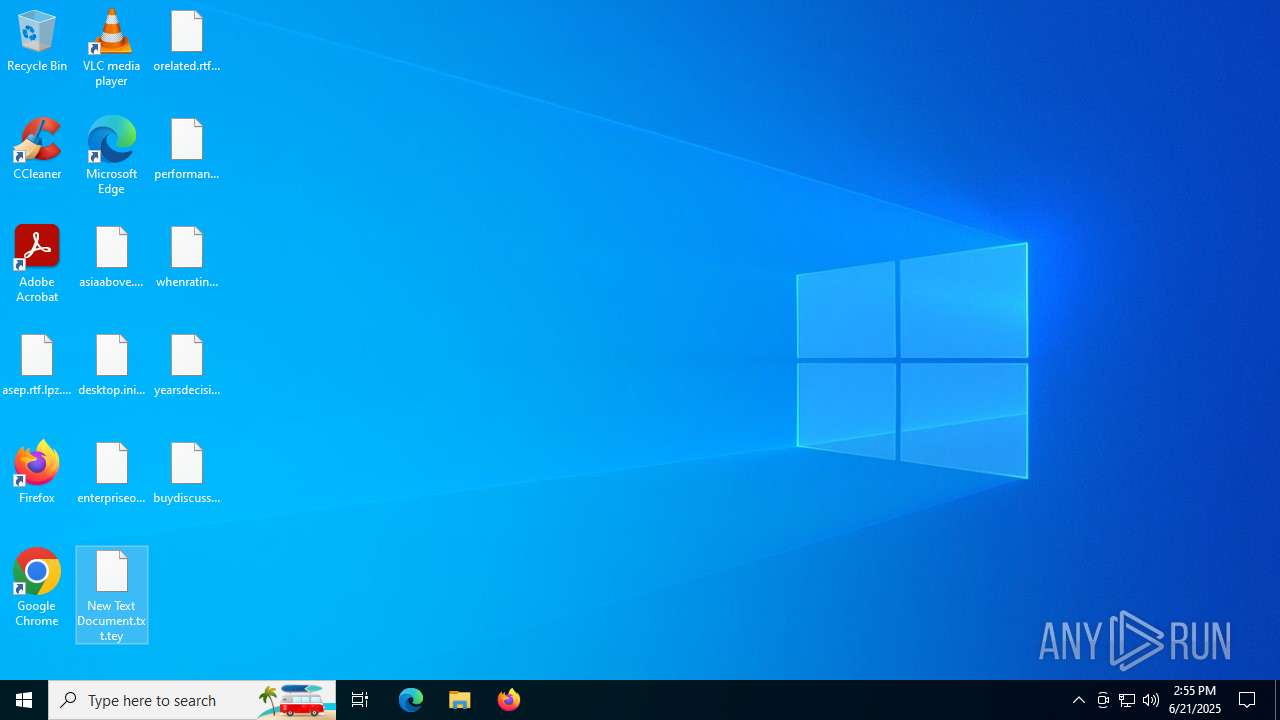
| 5168 | ran.exe | C:\Users\admin\Desktop\enterpriseold.jpg.qat | binary | |
MD5:8568E50B64BF497A67DEC08983DDB524 | SHA256:060D3BA0CD14468D37970CE68AC081996CB6BF5B39E45402FD068D77D147A9E8 | |||
| 5168 | ran.exe | C:\Users\admin\Documents\descriptionfine.rtf.rwx | binary | |
MD5:29E1758A88E174B50BD61D8635D49BF0 | SHA256:36F2E892FCE079DA3F7344623DAB6C30CB7E76ACDC1C45E31B5FFC5BCB39AEE2 | |||
| 2076 | ran.exe | C:\Windows\System32\ran.exe | executable | |
MD5:8259E1E7EB00D46D5F71BB9EB8D55DF1 | SHA256:5F4727541F473EF316FF8E4A1F9F6387F1A0293765E3BF660DC0D4EC23522432 | |||
| 5168 | ran.exe | C:\Users\admin\Desktop\buydiscuss.png.ucz | binary | |
MD5:B6F5D86D6D65C4C77D85B1DC12D334D7 | SHA256:CC94E9530F98C8500DC3509364D96C92FE59DBE6637B6A27975145CF526F0BED | |||
| 5168 | ran.exe | C:\Users\admin\Desktop\desktop.ini.nez | binary | |
MD5:892E4D0A43C35BB058C20D37F227B1DF | SHA256:BA3C687FBE8B8578A25BDF7273455C1EAB76F40FEF57B969005113F985EC71BE | |||
| 5168 | ran.exe | C:\Users\admin\Desktop\orelated.rtf.gga | binary | |
MD5:E874BA54EBE0EAFF0C905095BF10E214 | SHA256:CF83EBFD94FD6062CD95DDC392362ED644D15F18E89BA58167DCEE23FA37093E | |||
| 5168 | ran.exe | C:\Users\admin\Desktop\asep.rtf.lpz | binary | |
MD5:4810D7D8C3BAB2BCE6A8698FCDB3F052 | SHA256:3714EF8F6B253F2D9077D9DDE642EBCA9383797315A63C3A9E46BC932ECC0672 | |||
| 5168 | ran.exe | C:\Users\admin\Documents\virtualinitial.rtf.jgp | binary | |
MD5:9EDAD41F8B62F5D4F8EC73F53D5F1071 | SHA256:3F768EA649A1557A1C9184AA4234BB23008D5CB6EE4812B1620D99CC026D956E | |||
| 5168 | ran.exe | C:\Users\admin\Desktop\asiaabove.jpg.via | binary | |
MD5:5CED7E0D5C4974FAF17EEDD3E163CA88 | SHA256:7F6322F45860037AB61EA000E138337101B6622558FDC23853F7D039B8A81467 | |||
| 5168 | ran.exe | C:\Users\admin\Documents\largercanada.rtf.epl | binary | |
MD5:B11CF1ED9C50D6A0E48C81AD986AA73C | SHA256:FCEEA0CBF0B719C65CD429694DF1810F74C8AB12168E29319FD530A9367A7582 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
60
DNS requests
36
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
7020 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.25.50.8:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3624 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3624 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
3268 | msedge.exe | GET | 200 | 150.171.28.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:Diz2EWRjQC4zweOEZU_sdirQwVfsxIdrKlah4dgDOsI&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
5704 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3820 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
5596 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5476 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | svchost.exe | 172.211.123.248:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
7020 | svchost.exe | 20.190.159.129:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7020 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 184.25.50.8:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |