| File name: | App_file_x64.exe.7z |
| Full analysis: | https://app.any.run/tasks/af100e65-de8b-476d-a35a-c0dd79ba8900 |
| Verdict: | Malicious activity |
| Analysis date: | February 06, 2024, 23:32:18 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | B4D9A3F0CC39290E03FCA02B3F8E2DA8 |
| SHA1: | 22D1F26C0A5C06BB0AA7CB0FEC228B7C4D2C7D3D |
| SHA256: | 5F25C2F4DC5AE83882588DD60CC8DBAE741BB18AF40B51629244997BA32A9597 |
| SSDEEP: | 98304:Dkh0VaWFBrcuFHMa89f36TRp1IM22Whvq/nIRicCGaFKLt/4Q5RfJRxBdjf3xkZN:ATbL4qCog16GbA |
MALICIOUS
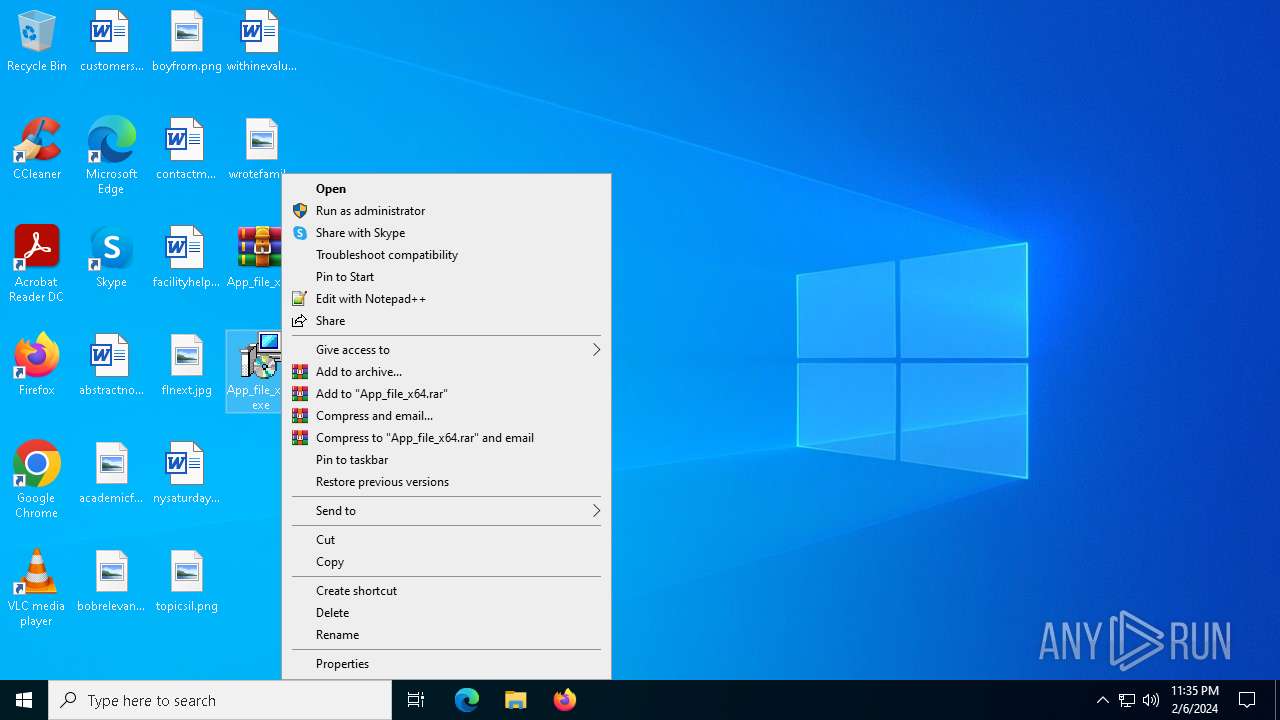
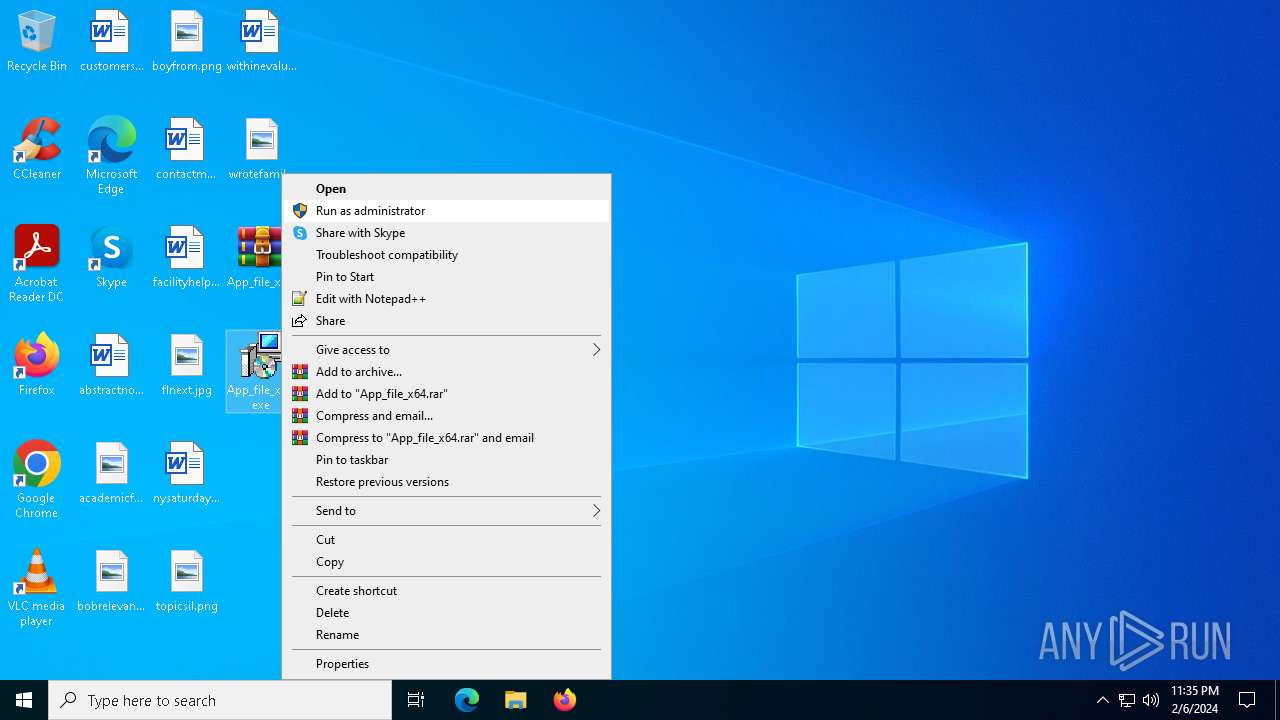
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6956)
Scans artifacts that could help determine the target
- App_file_x64.exe (PID: 6624)
SUSPICIOUS
Reads Microsoft Outlook installation path
- App_file_x64.exe (PID: 6624)
Reads Internet Explorer settings
- App_file_x64.exe (PID: 6624)
Checks Windows Trust Settings
- App_file_x64.exe (PID: 6624)
Reads security settings of Internet Explorer
- App_file_x64.exe (PID: 6624)
Checks for Java to be installed
- jusched.exe (PID: 5504)
INFO
Reads the computer name
- App_file_x64.exe (PID: 6624)
Checks proxy server information
- App_file_x64.exe (PID: 6624)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6956)
Checks supported languages
- App_file_x64.exe (PID: 6624)
- jusched.exe (PID: 5504)
Manual execution by a user
- App_file_x64.exe (PID: 6624)
- jusched.exe (PID: 5504)
Process checks Internet Explorer phishing filters
- App_file_x64.exe (PID: 6624)
Reads the machine GUID from the registry
- App_file_x64.exe (PID: 6624)
Reads the software policy settings
- App_file_x64.exe (PID: 6624)
Creates files or folders in the user directory
- App_file_x64.exe (PID: 6624)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
280
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3732 | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe -Embedding | C:\Users\admin\AppData\Local\Microsoft\OneDrive\19.043.0304.0013\FileCoAuth.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft OneDriveFile Co-Authoring Executable Exit code: 0 Version: 19.043.0304.0013 Modules
| |||||||||||||||
| 5504 | "C:\Program Files (x86)\Common Files\Java\Java Update\jusched.exe" | C:\Program Files (x86)\Common Files\Java\Java Update\jusched.exe | — | runonce.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java Update Scheduler Exit code: 4294967292 Version: 2.8.271.9 Modules
| |||||||||||||||
| 6624 | "C:\Users\admin\Desktop\App_file_x64.exe" | C:\Users\admin\Desktop\App_file_x64.exe | explorer.exe | ||||||||||||
User: admin Company: LM Studio Integrity Level: HIGH Description: Discover, download, and run LLMs locally Exit code: 0 Version: 0.2.6 Modules
| |||||||||||||||
| 6956 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\App_file_x64.exe.7z" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
4 704
Read events
4 675
Write events
29
Delete events
0
Modification events
| (PID) Process: | (6956) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General |
| Operation: | write | Name: | VerInfo |
Value: 003C050012F8FE6A437AD701 | |||
| (PID) Process: | (6956) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\SpybotAntiBeaconPortable-safer-networking.org_3.7.0.paf.zip | |||
| (PID) Process: | (6956) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\MicrosoftEdgePolicyTemplates.cab | |||
| (PID) Process: | (6956) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\MicrosoftEdgePolicyTemplates.zip | |||
| (PID) Process: | (6956) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6956) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6956) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6956) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6956) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (6956) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\General |
| Operation: | write | Name: | LastFolder |
Value: C:\Users\admin\Desktop | |||
Executable files
1
Suspicious files
3
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3732 | FileCoAuth.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\logs\Common\FileCoAuth-2024-02-06.2335.3732.1.odl | binary | |
MD5:5CBB736E79C6DD4836A8E65E83975C1F | SHA256:B1826037EF5CB52471A309A544A38A9457A1BC670535FE4DD7E65BF8AD11C79C | |||
| 6624 | App_file_x64.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\61424c3d98c12d2c6116907a_discords-404-page[1].png | image | |
MD5:A78C3455CF49BCA92E08E7C2D4CF6D0D | SHA256:540E98B588C749CF9505B8C9615BE98633A116435BD3CD6642835956E32D9B54 | |||
| 3732 | FileCoAuth.exe | C:\Users\admin\AppData\Local\Microsoft\OneDrive\logs\Common\FileCoAuth-2024-02-06.2335.3732.1.aodl | binary | |
MD5:923BF0E545D9C37CA8874C8D6C4A30E6 | SHA256:AB32C675D35DDBEBFCF8B11720C3E550024E8D0DF557838F17186377E3D0FE65 | |||
| 6956 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6956.34510\App_file_x64.exe | executable | |
MD5:6B9E5C0D87E8E11FE1EE9E4F7EC1B8BB | SHA256:79E7AC368ED32889059E4614B62CE85A19832687137DAB6FEA7432181E0DD2BF | |||
| 6956 | WinRAR.exe | C:\Users\admin\AppData\Roaming\WinRAR\version.dat | binary | |
MD5:90192E3708C1BF4B63EC60E9998CDF30 | SHA256:2C2421C5C55A1A2B0491F3C3680B447BFF0EE5A0BF7648C4A16A4AC727975D32 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
149
TCP/UDP connections
87
DNS requests
44
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6492 | msedge.exe | GET | 302 | 184.30.21.171:443 | https://go.microsoft.com/fwlink/?linkid=2133855&bucket=15 | unknown | — | — | unknown |
5756 | svchost.exe | HEAD | 200 | 23.48.23.7:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/873489b1-33b2-480a-baa2-641b9e09edcd?P1=1707511006&P2=404&P3=2&P4=BoyP3S057eZ1orXuwuBzkEwSubslg5JjRmwk%2fJlbeCVz4Ah8J4K7O3Odgpq%2frVlieDC%2bAELbMN5ozdgT0r0PTA%3d%3d | unknown | — | — | unknown |
5756 | svchost.exe | GET | 206 | 23.48.23.7:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/873489b1-33b2-480a-baa2-641b9e09edcd?P1=1707511006&P2=404&P3=2&P4=BoyP3S057eZ1orXuwuBzkEwSubslg5JjRmwk%2fJlbeCVz4Ah8J4K7O3Odgpq%2frVlieDC%2bAELbMN5ozdgT0r0PTA%3d%3d | unknown | binary | 1.09 Kb | unknown |
5756 | svchost.exe | GET | 206 | 23.48.23.7:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/873489b1-33b2-480a-baa2-641b9e09edcd?P1=1707511006&P2=404&P3=2&P4=BoyP3S057eZ1orXuwuBzkEwSubslg5JjRmwk%2fJlbeCVz4Ah8J4K7O3Odgpq%2frVlieDC%2bAELbMN5ozdgT0r0PTA%3d%3d | unknown | binary | 2.26 Kb | unknown |
5756 | svchost.exe | GET | 206 | 23.48.23.7:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/873489b1-33b2-480a-baa2-641b9e09edcd?P1=1707511006&P2=404&P3=2&P4=BoyP3S057eZ1orXuwuBzkEwSubslg5JjRmwk%2fJlbeCVz4Ah8J4K7O3Odgpq%2frVlieDC%2bAELbMN5ozdgT0r0PTA%3d%3d | unknown | binary | 6.64 Kb | unknown |
5756 | svchost.exe | GET | 206 | 23.48.23.7:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/873489b1-33b2-480a-baa2-641b9e09edcd?P1=1707511006&P2=404&P3=2&P4=BoyP3S057eZ1orXuwuBzkEwSubslg5JjRmwk%2fJlbeCVz4Ah8J4K7O3Odgpq%2frVlieDC%2bAELbMN5ozdgT0r0PTA%3d%3d | unknown | binary | 2.96 Kb | unknown |
5756 | svchost.exe | GET | 206 | 23.48.23.7:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/873489b1-33b2-480a-baa2-641b9e09edcd?P1=1707511006&P2=404&P3=2&P4=BoyP3S057eZ1orXuwuBzkEwSubslg5JjRmwk%2fJlbeCVz4Ah8J4K7O3Odgpq%2frVlieDC%2bAELbMN5ozdgT0r0PTA%3d%3d | unknown | binary | 9.28 Kb | unknown |
5756 | svchost.exe | HEAD | 200 | 23.48.23.7:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/78c34df8-0979-4065-b0a1-02478ab0702c?P1=1707511007&P2=404&P3=2&P4=Smf1W2g9xiyeLAi30h39VNrKljZ6ZJvUAMCvTwoVRJe0laZpbF%2ff2KKy3H%2bLu3vpqHYEyGeKStm5zGSYJnoqNw%3d%3d | unknown | binary | 6.64 Kb | unknown |
1828 | SIHClient.exe | GET | 304 | 13.85.23.86:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19044.1288/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.1288&MK=DELL&MD=DELL | unknown | — | — | unknown |
5756 | svchost.exe | GET | 206 | 23.48.23.7:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/78c34df8-0979-4065-b0a1-02478ab0702c?P1=1707511007&P2=404&P3=2&P4=Smf1W2g9xiyeLAi30h39VNrKljZ6ZJvUAMCvTwoVRJe0laZpbF%2ff2KKy3H%2bLu3vpqHYEyGeKStm5zGSYJnoqNw%3d%3d | unknown | binary | 253 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.251:5353 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3720 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
6492 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1612 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5612 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4188 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6492 | msedge.exe | 184.30.17.189:443 | go.microsoft.com | AKAMAI-AS | DE | unknown |
6492 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
6492 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.edge.skype.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
msedge.b.tlu.dl.delivery.mp.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |