| File name: | HALION.EXE |
| Full analysis: | https://app.any.run/tasks/fdbe8de4-742a-4a0f-a314-fe5b856f497f |
| Verdict: | Malicious activity |
| Analysis date: | July 17, 2019, 21:12:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 13231DAC6EF500BBB8FCBA48C5DFD94A |
| SHA1: | 33648E19739D732706DF26BEBB4096E521A5F570 |
| SHA256: | 5F1584932DC410CD94DAEFD6DE5001AE3B942DCBDAE869B1EB38D6EF061BD666 |
| SSDEEP: | 98304:tyqUHTUy3Z3B1hxPq39AenaZUKlvcEox1:t1KUyZhxPWAeaO9r |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- HALION.EXE (PID: 3960)
Removes files from Windows directory
- HALION.EXE (PID: 3960)
Creates files in the Windows directory
- HALION.EXE (PID: 3960)
Creates a software uninstall entry
- HALION.EXE (PID: 3960)
Creates files in the program directory
- HALION.EXE (PID: 3960)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Wise Installer executable (96.9) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (1.3) |
| .exe | | | Win32 Executable (generic) (0.9) |
| .exe | | | Generic Win/DOS Executable (0.4) |
| .exe | | | DOS Executable Generic (0.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2000:04:25 16:37:12+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 8704 |
| InitializedDataSize: | 5632 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x21af |
| OSVersion: | 4 |
| ImageVersion: | 4.1423 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Team |
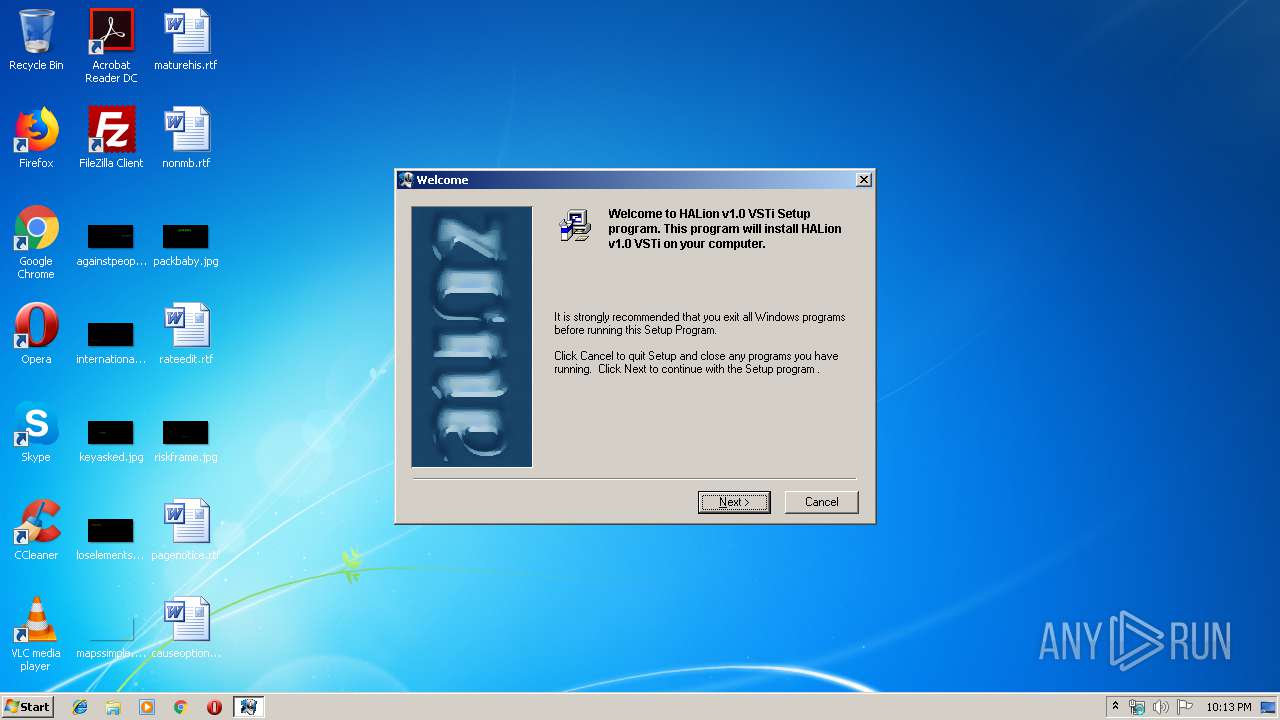
| FileDescription: | HALion Installation |
| FileVersion: | - |
| LegalCopyright: | Team |
Total processes
36
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3688 | "C:\Users\admin\AppData\Local\Temp\HALION.EXE" | C:\Users\admin\AppData\Local\Temp\HALION.EXE | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3960 | "C:\Users\admin\AppData\Local\Temp\HALION.EXE" | C:\Users\admin\AppData\Local\Temp\HALION.EXE | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
2
Read events
0
Write events
2
Delete events
0
Modification events
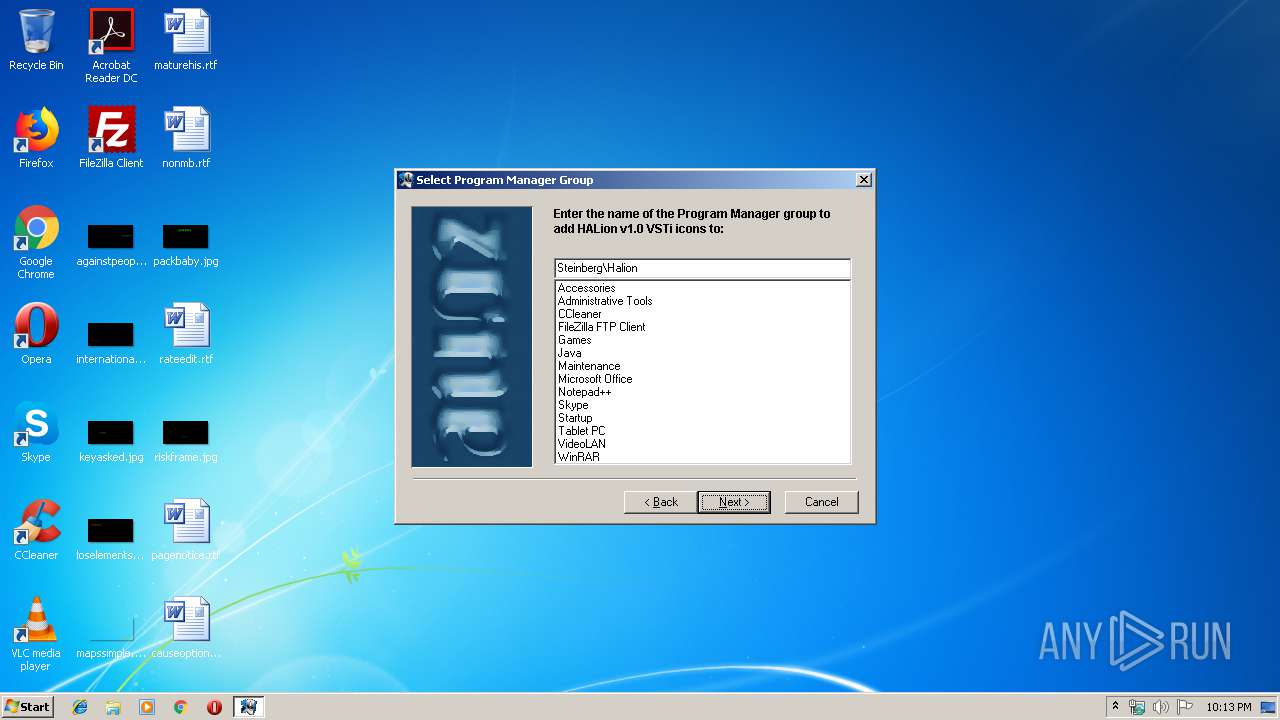
| (PID) Process: | (3960) HALION.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\HALion v1.0 VSTi |
| Operation: | write | Name: | DisplayName |
Value: HALion v1.0 VSTi | |||
| (PID) Process: | (3960) HALION.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\HALion v1.0 VSTi |
| Operation: | write | Name: | UninstallString |
Value: C:\PROGRA~1\STEINB~1\VSTPLU~1\Halion\UNWISE.EXE C:\PROGRA~1\STEINB~1\VSTPLU~1\Halion\HALion.log | |||
Executable files
4
Suspicious files
5
Text files
0
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3960 | HALION.EXE | C:\Users\admin\AppData\Local\Temp\~GLH0000.TMP | — | |
MD5:— | SHA256:— | |||
| 3960 | HALION.EXE | C:\Program Files\Steinberg\VstPlugins\Halion\~GLH0001.TMP | — | |
MD5:— | SHA256:— | |||
| 3960 | HALION.EXE | C:\Program Files\Steinberg\VstPlugins\Halion\Demo Material\Ueberschall\~GLH0002.TMP | — | |
MD5:— | SHA256:— | |||
| 3960 | HALION.EXE | C:\Program Files\Steinberg\VstPlugins\Halion\Demo Material\Ueberschall\Drumskills Samples\~GLH0003.TMP | — | |
MD5:— | SHA256:— | |||
| 3960 | HALION.EXE | C:\Program Files\Steinberg\VstPlugins\Halion\Demo Material\Ueberschall\Drumskills Samples\~GLH0004.TMP | — | |
MD5:— | SHA256:— | |||
| 3960 | HALION.EXE | C:\Program Files\Steinberg\VstPlugins\Halion\Demo Material\Ueberschall\Drumskills Samples\~GLH0005.TMP | — | |
MD5:— | SHA256:— | |||
| 3960 | HALION.EXE | C:\Program Files\Steinberg\VstPlugins\Halion\Demo Material\Ueberschall\Drumskills Samples\~GLH0006.TMP | — | |
MD5:— | SHA256:— | |||
| 3960 | HALION.EXE | C:\Program Files\Steinberg\VstPlugins\Halion\Demo Material\Ueberschall\Drumskills Samples\Images\~GLH0007.TMP | — | |
MD5:— | SHA256:— | |||
| 3960 | HALION.EXE | C:\Program Files\Steinberg\VstPlugins\Halion\Demo Material\Ueberschall\Drumskills Samples\Images\~GLH0008.TMP | — | |
MD5:— | SHA256:— | |||
| 3960 | HALION.EXE | C:\Program Files\Steinberg\VstPlugins\Halion\Demo Material\Ueberschall\Drumskills Samples\Images\~GLH0009.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report