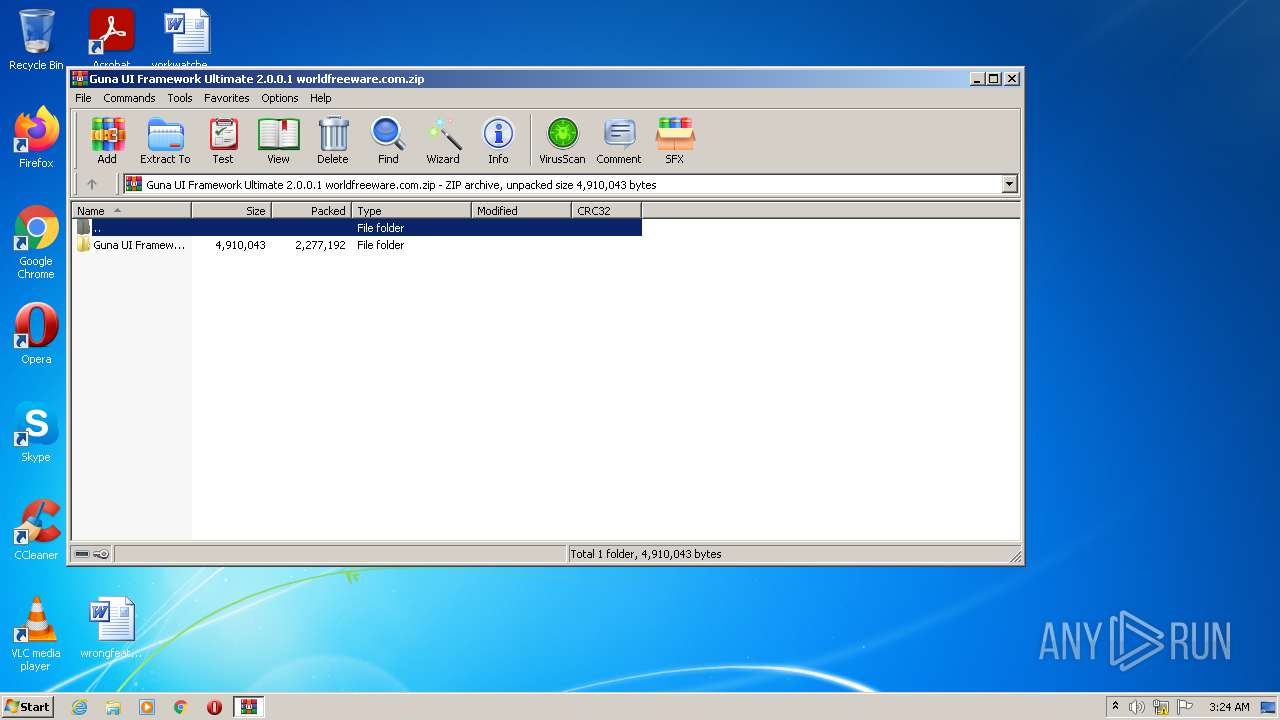
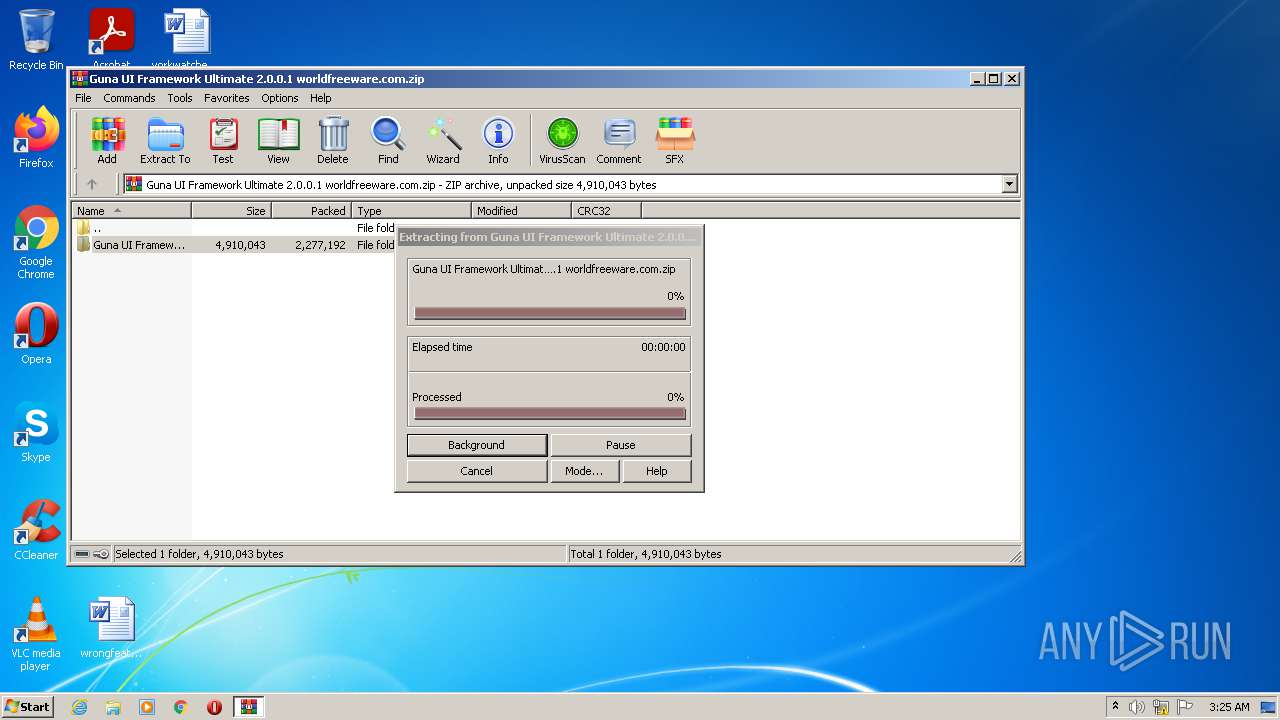
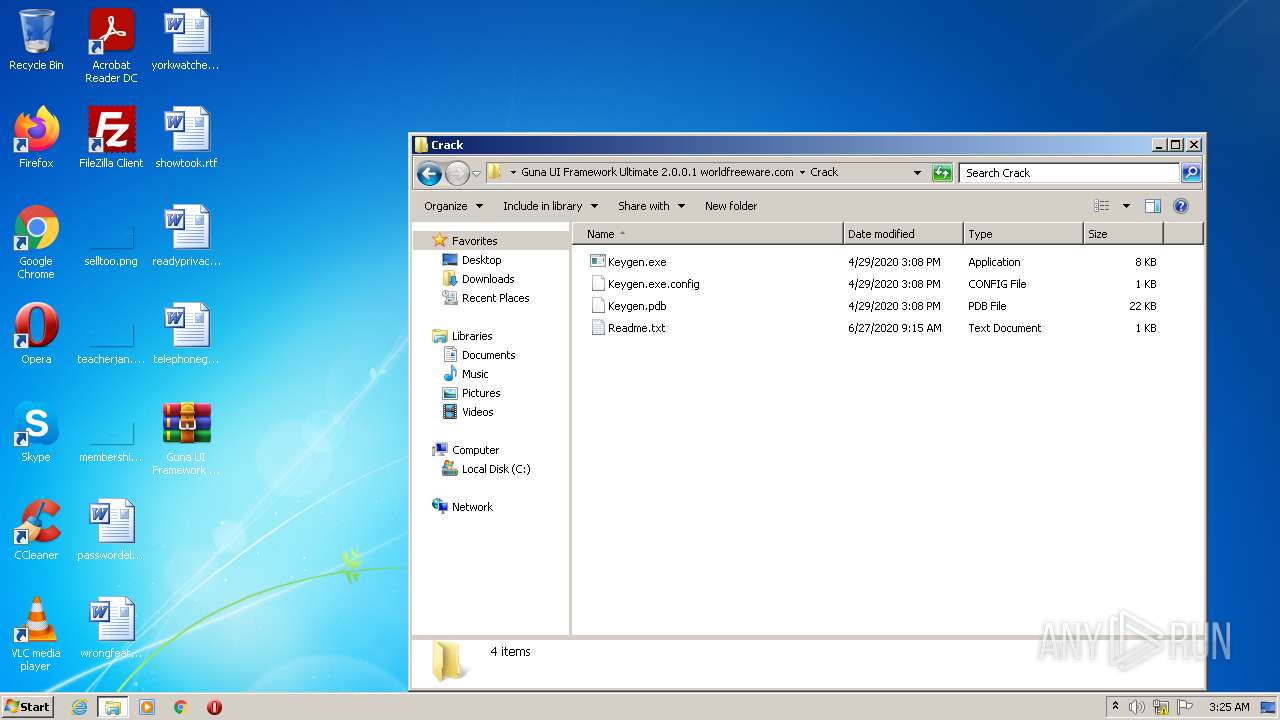
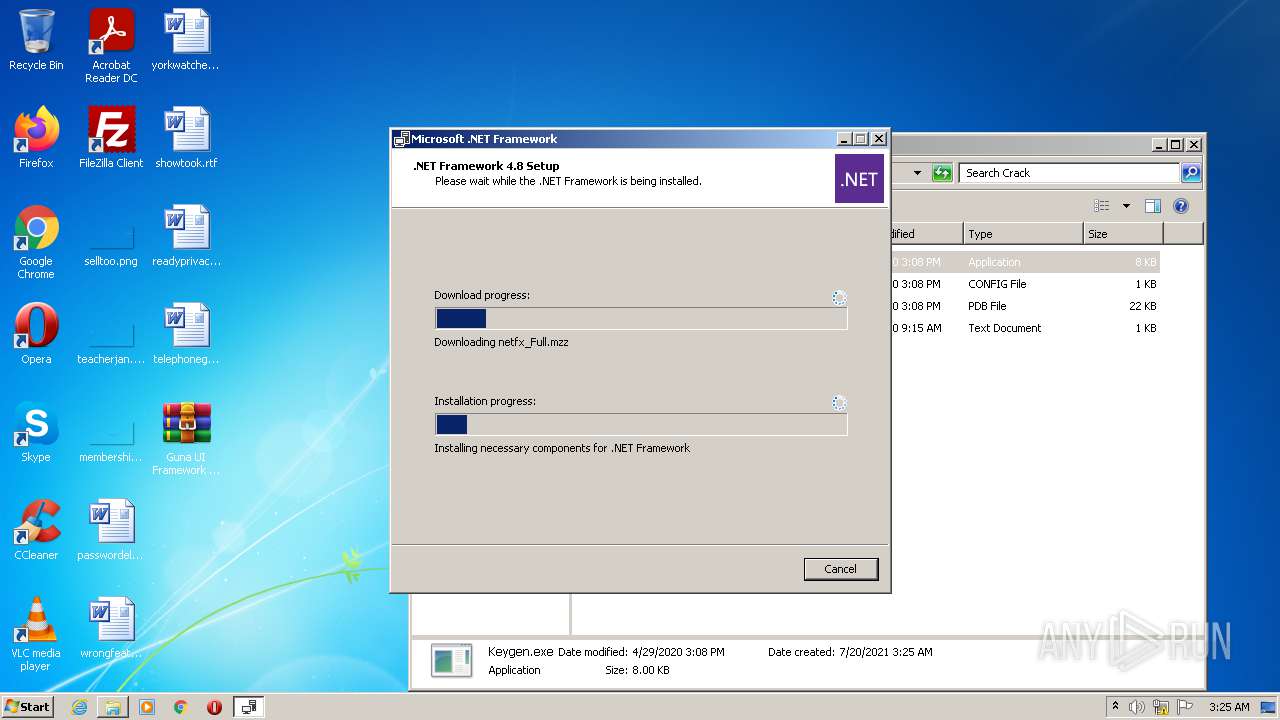
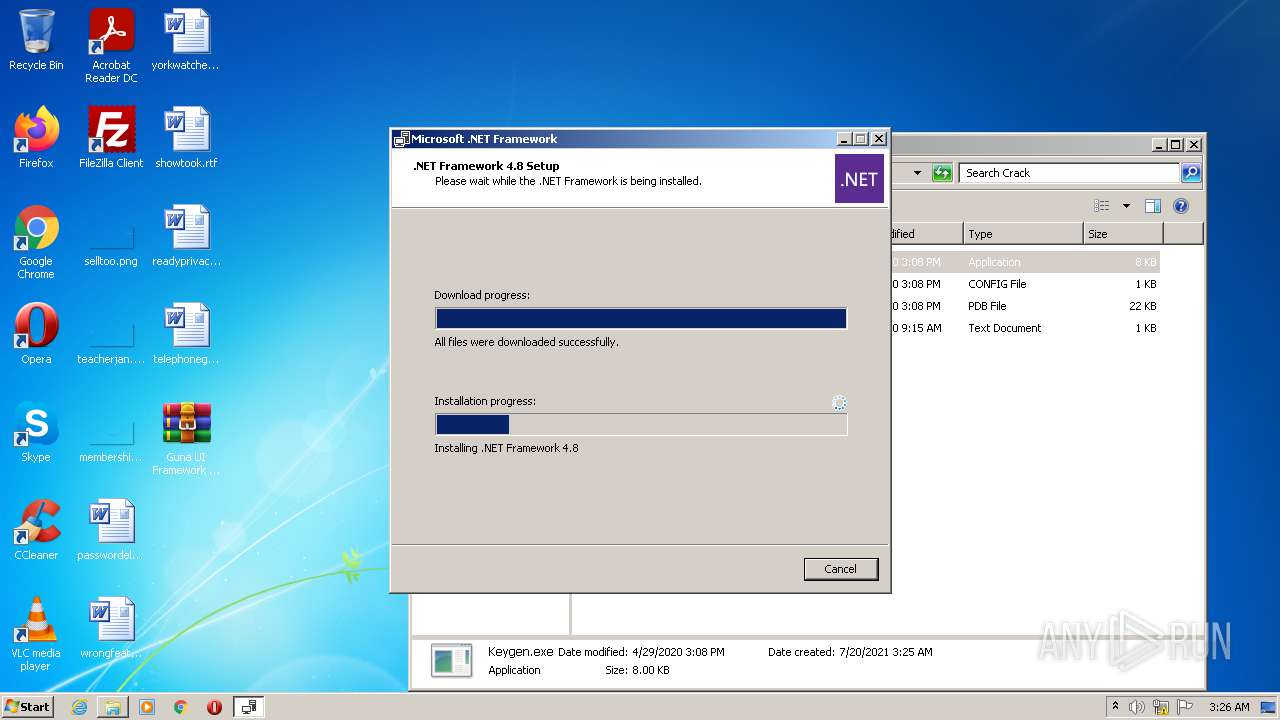
| File name: | Guna UI Framework Ultimate 2.0.0.1 worldfreeware.com.zip |
| Full analysis: | https://app.any.run/tasks/6fc4bafd-c14e-4a67-b139-9521892e6f01 |
| Verdict: | Malicious activity |
| Analysis date: | July 20, 2021, 02:24:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 340AD223F6BB20C94553F97DE6299032 |
| SHA1: | CFCBCBF0B13A7C65BEAD03C337EB62E3F65343B8 |
| SHA256: | 5F0C8A01CDB94D3ABF07217701444DEF69BFBF9296047815D144439A9EF39150 |
| SSDEEP: | 49152:rheNSnWwsoWKxdG99hPFkGwq4cyWvnfmnyz6gtgwBMy:rheoZsoW4dq9hPxwPctnunY6gtgwKy |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3512)
- Setup.exe (PID: 3432)
- MsiExec.exe (PID: 3588)
- Keygen.exe (PID: 1820)
- msiexec.exe (PID: 1828)
- MsiExec.exe (PID: 1008)
- svchost.exe (PID: 768)
- aspnet_regiis.exe (PID: 2108)
- mscorsvw.exe (PID: 3836)
- ngen.exe (PID: 2524)
Application was dropped or rewritten from another process
- Keygen.exe (PID: 1820)
- ndp48-web.exe (PID: 1892)
- ndp48-web.exe (PID: 1996)
- Setup.exe (PID: 3432)
- SetupUtility.exe (PID: 2548)
- SetupUtility.exe (PID: 1984)
- ServiceModelReg.exe (PID: 1916)
- regtlibv12.exe (PID: 116)
- regtlibv12.exe (PID: 932)
- regtlibv12.exe (PID: 3876)
- regtlibv12.exe (PID: 4068)
- regtlibv12.exe (PID: 2424)
- regtlibv12.exe (PID: 3512)
- regtlibv12.exe (PID: 3124)
- ngen.exe (PID: 2524)
- aspnet_regiis.exe (PID: 2108)
- mscorsvw.exe (PID: 3836)
Actions looks like stealing of personal data
- ndp48-web.exe (PID: 1892)
Changes settings of System certificates
- Setup.exe (PID: 3432)
Changes the autorun value in the registry
- msiexec.exe (PID: 1828)
Loads the Task Scheduler COM API
- ngen.exe (PID: 2524)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1532)
- iexplore.exe (PID: 2868)
- iexplore.exe (PID: 404)
- ndp48-web.exe (PID: 1892)
- Setup.exe (PID: 3432)
- TMPB357.tmp.exe (PID: 332)
- msiexec.exe (PID: 1828)
Drops a file with too old compile date
- WinRAR.exe (PID: 1532)
- msiexec.exe (PID: 1828)
Checks supported languages
- WinRAR.exe (PID: 1532)
- Keygen.exe (PID: 1820)
- ndp48-web.exe (PID: 1892)
- Setup.exe (PID: 3432)
- SetupUtility.exe (PID: 1984)
- SetupUtility.exe (PID: 2548)
- TMPB357.tmp.exe (PID: 332)
- ServiceModelReg.exe (PID: 1916)
- regtlibv12.exe (PID: 2424)
- regtlibv12.exe (PID: 932)
- regtlibv12.exe (PID: 116)
- regtlibv12.exe (PID: 3876)
- regtlibv12.exe (PID: 4068)
- regtlibv12.exe (PID: 3512)
- mofcomp.exe (PID: 2776)
- mofcomp.exe (PID: 1936)
- aspnet_regiis.exe (PID: 2108)
- mofcomp.exe (PID: 2516)
- regtlibv12.exe (PID: 3124)
- ngen.exe (PID: 2524)
- mscorsvw.exe (PID: 3836)
Reads the computer name
- WinRAR.exe (PID: 1532)
- Keygen.exe (PID: 1820)
- ndp48-web.exe (PID: 1892)
- Setup.exe (PID: 3432)
- SetupUtility.exe (PID: 2548)
- SetupUtility.exe (PID: 1984)
- TMPB357.tmp.exe (PID: 332)
- ServiceModelReg.exe (PID: 1916)
- mofcomp.exe (PID: 2776)
- mofcomp.exe (PID: 1936)
- aspnet_regiis.exe (PID: 2108)
- mofcomp.exe (PID: 2516)
- mscorsvw.exe (PID: 3836)
- ngen.exe (PID: 2524)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 1532)
- iexplore.exe (PID: 404)
- iexplore.exe (PID: 2868)
- ndp48-web.exe (PID: 1892)
- msiexec.exe (PID: 1828)
Starts Internet Explorer
- Keygen.exe (PID: 1820)
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2868)
Reads Environment values
- Setup.exe (PID: 3432)
Reads CPU info
- Setup.exe (PID: 3432)
Executed as Windows Service
- msiexec.exe (PID: 1828)
Reads the Windows organization settings
- msiexec.exe (PID: 1828)
Reads Windows owner or organization settings
- msiexec.exe (PID: 1828)
Application launched itself
- msiexec.exe (PID: 1828)
Creates/Modifies COM task schedule object
- msiexec.exe (PID: 1828)
- aspnet_regiis.exe (PID: 2108)
Searches for installed software
- msiexec.exe (PID: 1828)
Creates a software uninstall entry
- msiexec.exe (PID: 1828)
Checks for the .NET to be installed
- msiexec.exe (PID: 1828)
Creates files in the Windows directory
- msiexec.exe (PID: 1828)
- lodctr.exe (PID: 3640)
- aspnet_regiis.exe (PID: 2108)
- lodctr.exe (PID: 3420)
- ngen.exe (PID: 2524)
- lodctr.exe (PID: 3096)
- lodctr.exe (PID: 2408)
- lodctr.exe (PID: 3184)
Removes files from Windows directory
- lodctr.exe (PID: 3640)
- msiexec.exe (PID: 1828)
- aspnet_regiis.exe (PID: 2108)
- lodctr.exe (PID: 3420)
- lodctr.exe (PID: 2408)
- lodctr.exe (PID: 3184)
- lodctr.exe (PID: 3096)
INFO
Checks supported languages
- iexplore.exe (PID: 404)
- iexplore.exe (PID: 2868)
- msiexec.exe (PID: 1828)
- MsiExec.exe (PID: 3588)
- MsiExec.exe (PID: 1008)
- wevtutil.exe (PID: 3392)
- lodctr.exe (PID: 3640)
- wevtutil.exe (PID: 3592)
- lodctr.exe (PID: 2328)
- lodctr.exe (PID: 3492)
- lodctr.exe (PID: 3420)
- lodctr.exe (PID: 2408)
- lodctr.exe (PID: 3184)
- lodctr.exe (PID: 636)
- lodctr.exe (PID: 3096)
Manual execution by user
- Keygen.exe (PID: 1820)
Reads the computer name
- iexplore.exe (PID: 404)
- iexplore.exe (PID: 2868)
- MsiExec.exe (PID: 3588)
- MsiExec.exe (PID: 1008)
- msiexec.exe (PID: 1828)
- wevtutil.exe (PID: 3392)
- wevtutil.exe (PID: 3592)
- lodctr.exe (PID: 3640)
- lodctr.exe (PID: 2328)
- lodctr.exe (PID: 3492)
- lodctr.exe (PID: 3420)
- lodctr.exe (PID: 3096)
- lodctr.exe (PID: 2408)
- lodctr.exe (PID: 3184)
- lodctr.exe (PID: 636)
Application launched itself
- iexplore.exe (PID: 404)
Changes internet zones settings
- iexplore.exe (PID: 404)
Reads settings of System Certificates
- iexplore.exe (PID: 2868)
- iexplore.exe (PID: 404)
- msiexec.exe (PID: 1828)
- Setup.exe (PID: 3432)
Checks Windows Trust Settings
- iexplore.exe (PID: 2868)
- iexplore.exe (PID: 404)
- Setup.exe (PID: 3432)
- msiexec.exe (PID: 1828)
Reads internet explorer settings
- iexplore.exe (PID: 2868)
Creates files in the user directory
- iexplore.exe (PID: 2868)
- iexplore.exe (PID: 404)
Changes settings of System certificates
- iexplore.exe (PID: 404)
Modifies the phishing filter of IE
- iexplore.exe (PID: 404)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 404)
- SetupUtility.exe (PID: 2548)
- Setup.exe (PID: 3432)
- msiexec.exe (PID: 1828)
- svchost.exe (PID: 768)
- mscorsvw.exe (PID: 3836)
Adds / modifies Windows certificates
- iexplore.exe (PID: 404)
Reads the date of Windows installation
- iexplore.exe (PID: 404)
Creates or modifies windows services
- msiexec.exe (PID: 1828)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
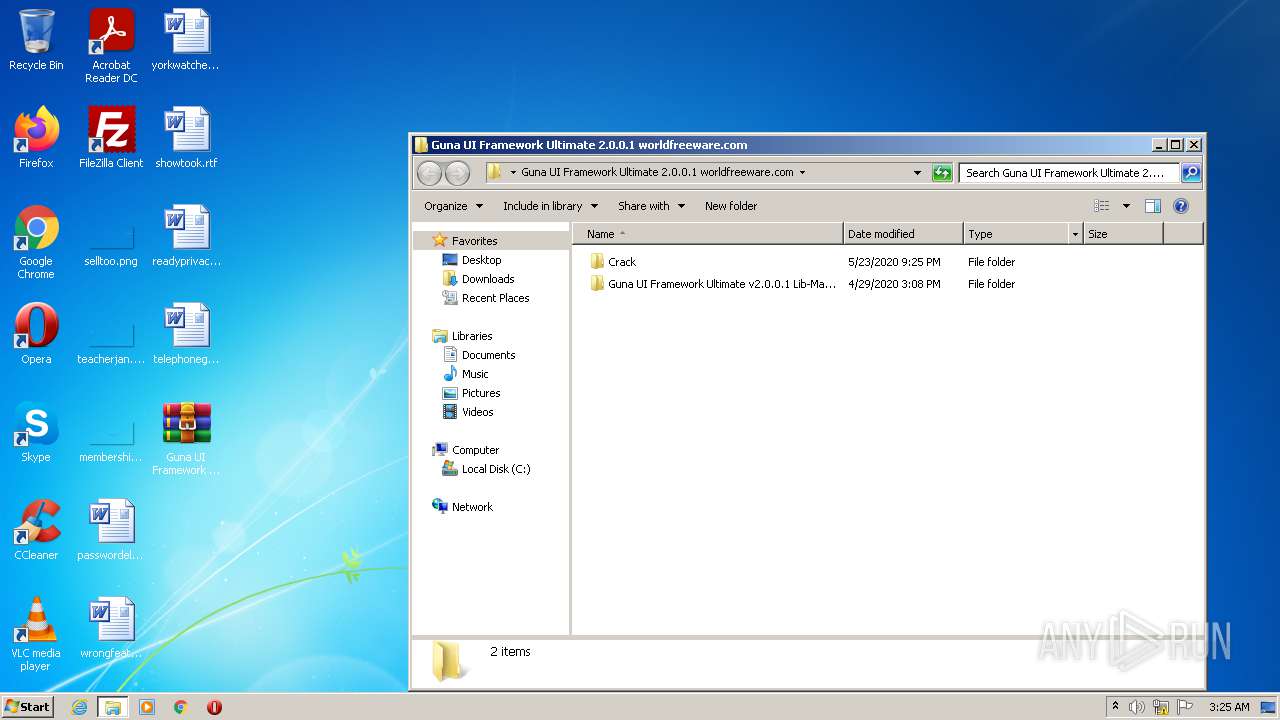
| ZipFileName: | Guna UI Framework Ultimate 2.0.0.1 worldfreeware.com/Crack/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2020:05:23 21:25:14 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
99
Monitored processes
39
Malicious processes
17
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\regtlibv12.exe" "C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorlib.tlb" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\regtlibv12.exe | — | MsiExec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: RegTLib Exit code: 0 Version: 14.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 332 | TMPB357.tmp.exe /Q /X:C:\2e22b0a275581af8288861d85274dd\TMPB357.tmp.exe.tmp | C:\2e22b0a275581af8288861d85274dd\TMPB357.tmp.exe | Setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Framework 4.8 Setup Exit code: 0 Version: 4.8.03761.00 Modules
| |||||||||||||||
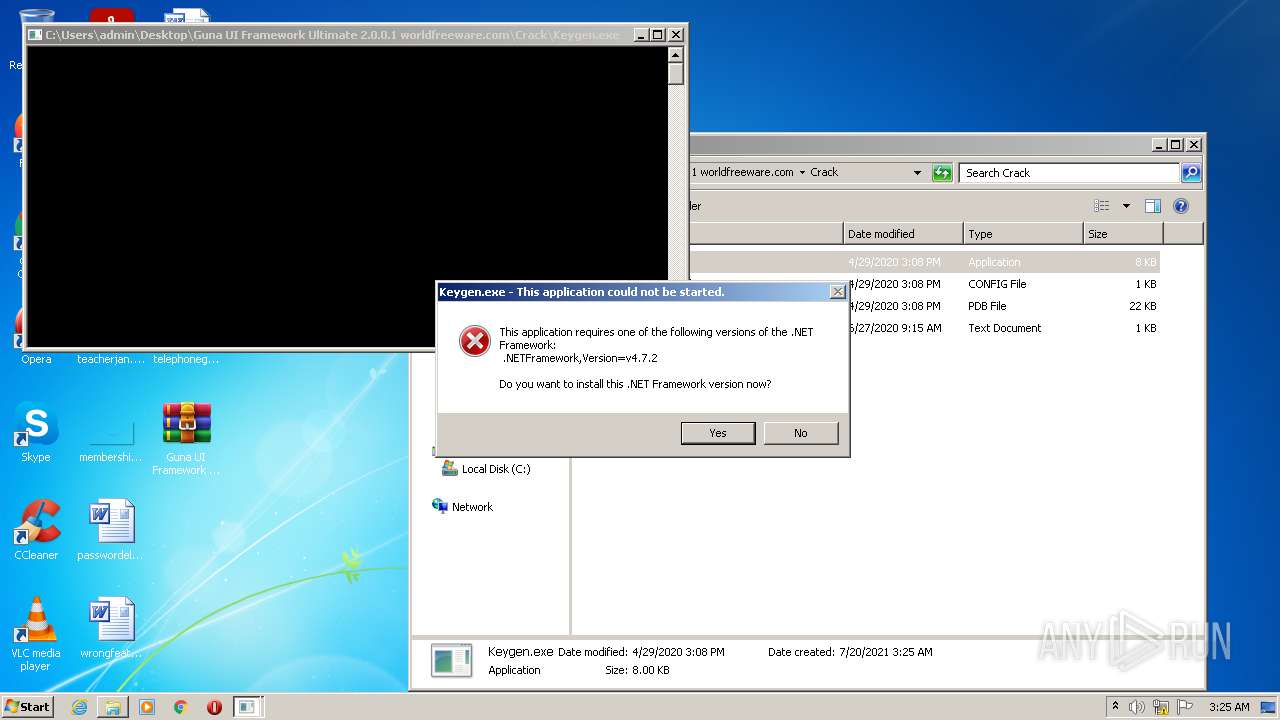
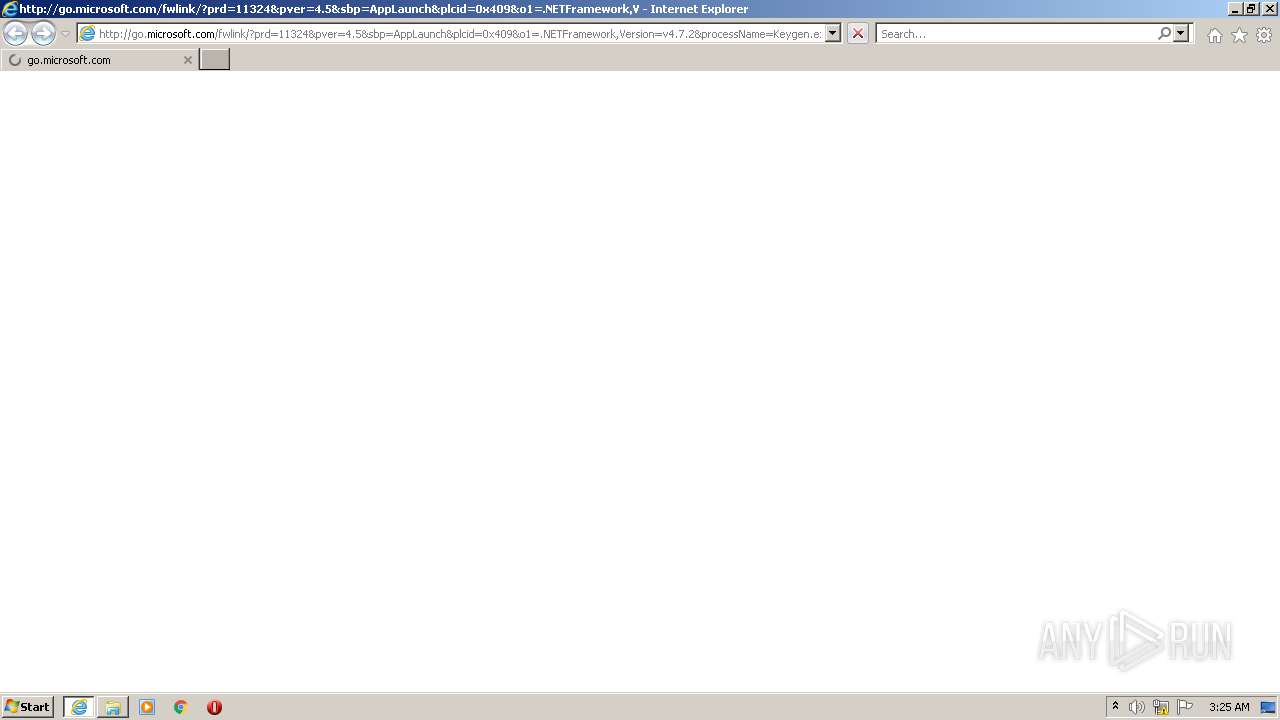
| 404 | "C:\Program Files\Internet Explorer\iexplore.exe" http://go.microsoft.com/fwlink/?prd=11324&pver=4.5&sbp=AppLaunch&plcid=0x409&o1=.NETFramework,Version=v4.7.2&processName=Keygen.exe&platform=0000&osver=5&isServer=0&shimver=4.0.30319.34209 | C:\Program Files\Internet Explorer\iexplore.exe | Keygen.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 636 | "C:\Windows\system32\lodctr.exe" C:\Windows\Microsoft.NET\Framework\v4.0.30319\_DataOracleClientPerfCounters_shared12_neutral.ini | C:\Windows\system32\lodctr.exe | — | MsiExec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Load PerfMon Counters Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 768 | C:\Windows\System32\svchost.exe -k LocalServiceNetworkRestricted | C:\Windows\System32\svchost.exe | — | services.exe | |||||||||||
User: LOCAL SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 932 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\regtlibv12.exe" "C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscoree.tlb" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\regtlibv12.exe | — | MsiExec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: RegTLib Exit code: 0 Version: 14.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 1008 | C:\Windows\system32\MsiExec.exe -Embedding 8196A786D027244DF124C4153B29731D E Global\MSI0000 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows� installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1532 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Guna UI Framework Ultimate 2.0.0.1 worldfreeware.com.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1820 | "C:\Users\admin\Desktop\Guna UI Framework Ultimate 2.0.0.1 worldfreeware.com\Crack\Keygen.exe" | C:\Users\admin\Desktop\Guna UI Framework Ultimate 2.0.0.1 worldfreeware.com\Crack\Keygen.exe | — | Explorer.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: GMW Exit code: 2148734720 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1828 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows� installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
85 969
Read events
69 638
Write events
14 529
Delete events
1 802
Modification events
| (PID) Process: | (1532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1532) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Guna UI Framework Ultimate 2.0.0.1 worldfreeware.com.zip | |||
| (PID) Process: | (1532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1532) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
2 485
Suspicious files
79
Text files
557
Unknown types
31
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1532.22927\Guna UI Framework Ultimate 2.0.0.1 worldfreeware.com\Guna UI Framework Ultimate v2.0.0.1 Lib-Master\.gitignore | text | |
MD5:— | SHA256:— | |||
| 1532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1532.22927\Guna UI Framework Ultimate 2.0.0.1 worldfreeware.com\Crack\Readme.txt | text | |
MD5:— | SHA256:— | |||
| 1532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1532.22927\Guna UI Framework Ultimate 2.0.0.1 worldfreeware.com\Crack\Keygen.pdb | pdb | |
MD5:061D770937FCA83E70FC3838EFE389A5 | SHA256:1771EDEB0F66BB54F43000DA2DDBEB7A84245CD19D98F4F3B5A765797B2713A7 | |||
| 1532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1532.22927\Guna UI Framework Ultimate 2.0.0.1 worldfreeware.com\Guna UI Framework Ultimate v2.0.0.1 Lib-Master\.gitattributes | text | |
MD5:13F0AECD22CC1F06C8225AE5E692FF31 | SHA256:45A7CBB7D9942BA7FFCE0B20BC8DBE2D1196533BC6E4BD245871D77FB1EEDFDC | |||
| 1532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1532.22927\Guna UI Framework Ultimate 2.0.0.1 worldfreeware.com\Guna UI Framework Ultimate v2.0.0.1 Lib-Master\Guna UI Activation\Guna UI Activation\bin\Debug\Guna UI Activation.vshost.exe | executable | |
MD5:FC9F896933B6123ABEBB21C8476448EC | SHA256:CC0D4C85639DD5E8D68C4B356C9DCF9C501BAE0190A08376BCED2BCC85E2CF79 | |||
| 1532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1532.22927\Guna UI Framework Ultimate 2.0.0.1 worldfreeware.com\Guna UI Framework Ultimate v2.0.0.1 Lib-Master\Guna UI Activation\Guna UI Activation.sln | text | |
MD5:36E1F640B83FB42B2708C0CAF61514B5 | SHA256:7E851F80A4C2A694F0855062435FCC7C31724693375E5CD3BBA05CBE09687DE0 | |||
| 1532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1532.22927\Guna UI Framework Ultimate 2.0.0.1 worldfreeware.com\Guna UI Framework Ultimate v2.0.0.1 Lib-Master\Guna UI Activation\Guna UI Activation\bin\Debug\Guna UI Activation.pdb | pdb | |
MD5:F2B5AD4ED64B52A0445E76C034DFAAA9 | SHA256:06B0B0EE40C54991306D2F0872E6055F63E18B6090625E29F246212F189E89F0 | |||
| 1532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1532.22927\Guna UI Framework Ultimate 2.0.0.1 worldfreeware.com\Guna UI Framework Ultimate v2.0.0.1 Lib-Master\Guna UI Activation\Guna UI Activation\My Project\Application.myapp | xml | |
MD5:CC4DAA93C203BF95D8098A0D6426BFDE | SHA256:D8244F945551135BCDBC41B350A9796DC368CDDC73EEF4AC625C76BDD6DFCD0D | |||
| 1532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1532.22927\Guna UI Framework Ultimate 2.0.0.1 worldfreeware.com\Crack\Keygen.exe.config | xml | |
MD5:9DBAD5517B46F41DBB0D8780B20AB87E | SHA256:47E5A0F101AF4151D7F13D2D6BFA9B847D5B5E4A98D1F4674B7C015772746CDF | |||
| 1532 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1532.22927\Guna UI Framework Ultimate 2.0.0.1 worldfreeware.com\Guna UI Framework Ultimate v2.0.0.1 Lib-Master\Guna UI Activation\Guna UI Activation\bin\Debug\Guna UI Activation.exe | executable | |
MD5:06082988BD64B3D6514AA5C1E1665349 | SHA256:93732E71605B2115FD5CEB1E4FAE438D9CC1637528755B999D9BF35622B7B70D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
26
TCP/UDP connections
41
DNS requests
20
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 302 | 23.15.254.176:80 | http://go.microsoft.com/fwlink/?prd=11324&pver=netfx&sbp=Net48Rel1&plcid=0x409&clcid=0x409&ar=03761.00&sar=x86&o1=netfx_Full.mzz | NL | — | — | whitelisted |
— | — | HEAD | 302 | 23.15.254.176:80 | http://go.microsoft.com/fwlink/?prd=11324&pver=netfx&sbp=Net48Rel1&plcid=0x409&clcid=0x409&ar=03761.00&sar=amd64&o1=netfx_Full_x86.msi | NL | — | — | whitelisted |
— | — | GET | 302 | 23.15.254.176:80 | http://go.microsoft.com/fwlink/?prd=11324&pver=netfx&sbp=Net48Rel1&plcid=0x409&clcid=0x409&ar=03761.00&sar=amd64&o1=netfx_Full_x86.msi | NL | — | — | whitelisted |
— | — | HEAD | 302 | 23.15.254.176:80 | http://go.microsoft.com/fwlink/?prd=11324&pver=netfx&sbp=Net48Rel1&plcid=0x409&clcid=0x409&ar=03761.00&sar=x86&o1=netfx_Full.mzz | NL | — | — | whitelisted |
2868 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
2868 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEDaqCx0Uw5IKBQAAAACH9mE%3D | US | der | 471 b | whitelisted |
2868 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | US | der | 471 b | whitelisted |
2868 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
2868 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAtb9ltrp%2FvQiykNkEU33uA%3D | US | der | 471 b | whitelisted |
2868 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2BnRyLFPYjID1ie%2Bx%2BdSjo%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2868 | iexplore.exe | 23.15.254.176:443 | go.microsoft.com | Akamai Technologies, Inc. | NL | malicious |
2868 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2868 | iexplore.exe | 13.107.213.45:443 | dotnet.microsoft.com | Microsoft Corporation | US | suspicious |
2868 | iexplore.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2868 | iexplore.exe | 2.18.233.62:443 | www.microsoft.com | Akamai International B.V. | — | whitelisted |
2868 | iexplore.exe | 2.16.170.26:443 | statics-marketingsites-wcus-ms-com.akamaized.net | Akamai International B.V. | DE | unknown |
2868 | iexplore.exe | 2.16.170.25:443 | img-prod-cms-rt-microsoft-com.akamaized.net | Akamai International B.V. | DE | unknown |
2868 | iexplore.exe | 13.107.246.45:443 | dotnet.microsoft.com | Microsoft Corporation | US | malicious |
2868 | iexplore.exe | 173.194.198.101:443 | www.google-analytics.com | Google Inc. | US | unknown |
2868 | iexplore.exe | 152.199.21.175:443 | az416426.vo.msecnd.net | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
dotnet.microsoft.com |
| whitelisted |
statics-marketingsites-wcus-ms-com.akamaized.net |
| whitelisted |
www.microsoft.com |
| whitelisted |
img-prod-cms-rt-microsoft-com.akamaized.net |
| whitelisted |
wcpstatic.microsoft.com |
| whitelisted |
www.google-analytics.com |
| whitelisted |
az416426.vo.msecnd.net |
| whitelisted |