| File name: | New order-Export_052020.pdf |
| Full analysis: | https://app.any.run/tasks/22d8a0bb-0ae8-4620-8b82-6a5912bf3d82 |
| Verdict: | Malicious activity |
| Analysis date: | May 30, 2020, 02:51:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/pdf |
| File info: | PDF document, version 1.5 |
| MD5: | BA7547FDAE1A13D5BCAA15E86B7FC977 |
| SHA1: | 557EEBB377004AA60D2C6090D738C05ECB013647 |
| SHA256: | 5EC9D7319266A455BB70F8A898A7D9A92E9C43F1B229BD14FF2FC8351F20CD4E |
| SSDEEP: | 192:icN9Nompm8QbtGHt70RS8YDVckLqGVdrEkW8Q5Yx5NQDLK/6D5k/X6+bl:jo6m/tGHFdnHEkPF/6Di/XHl |
MALICIOUS
No malicious indicators.SUSPICIOUS
Changes IE settings (feature browser emulation)
- AcroRd32.exe (PID: 564)
Creates files in the program directory
- AdobeARM.exe (PID: 1760)
Starts Internet Explorer
- AcroRd32.exe (PID: 564)
INFO
Application launched itself
- AcroRd32.exe (PID: 564)
- RdrCEF.exe (PID: 2244)
- iexplore.exe (PID: 2672)
Reads the hosts file
- RdrCEF.exe (PID: 2244)
Changes internet zones settings
- iexplore.exe (PID: 3460)
- iexplore.exe (PID: 2672)
Reads Internet Cache Settings
- AcroRd32.exe (PID: 1948)
- iexplore.exe (PID: 3460)
- AcroRd32.exe (PID: 564)
- iexplore.exe (PID: 2672)
- iexplore.exe (PID: 3924)
- iexplore.exe (PID: 580)
Reads internet explorer settings
- iexplore.exe (PID: 3924)
- iexplore.exe (PID: 580)
Creates files in the user directory
- iexplore.exe (PID: 3460)
- iexplore.exe (PID: 580)
Reads settings of System Certificates
- AcroRd32.exe (PID: 564)
- iexplore.exe (PID: 3460)
- iexplore.exe (PID: 2672)
- iexplore.exe (PID: 580)
Changes settings of System certificates
- iexplore.exe (PID: 2672)
- iexplore.exe (PID: 3460)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3460)
- iexplore.exe (PID: 2672)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| | | Adobe Portable Document Format (100) |
EXIF
| PDFVersion: | 1.5 |
|---|---|
| Linearized: | No |
| PageCount: | 1 |
| Creator: | PDFescape Online - https://www.pdfescape.com |
| CreateDate: | 2020:05:07 01:40:39Z |
| Producer: | www.ilovepdf.com |
| ModifyDate: | 2020:05:29 05:29:01Z |
XMP
| XMPToolkit: | 3-Heights(TM) XMP Library 4.12.26.4 (http://www.pdf-tools.com) |
|---|---|
| CreateDate: | 2020:05:07 01:40:39Z |
| CreatorTool: | PDFescape Online - https://www.pdfescape.com |
| MetadataDate: | 2020:05:29 05:29:01Z |
| ModifyDate: | 2020:05:29 05:29:01Z |
| DocumentID: | uuid:f43109b8-3a21-3c44-bf48-72e1a7d1bd32 |
| VersionID: | 1 |
| RenditionClass: | default |
| Producer: | www.ilovepdf.com |
| PDFVersion: | 1.5 |
| Format: | application/pdf |
Total processes
48
Monitored processes
11
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 564 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\Desktop\New order-Export_052020.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | explorer.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 0 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 580 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2672 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1760 | "C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe" /PRODUCT:Reader /VERSION:15.0 /MODE:3 | C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Reader and Acrobat Manager Exit code: 0 Version: 1.824.27.2646 Modules
| |||||||||||||||
| 1948 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\Desktop\New order-Export_052020.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 0 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 2120 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe | — | AdobeARM.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat SpeedLauncher Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2244 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16448250 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 2336 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="2244.1.1436681683\666256164" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
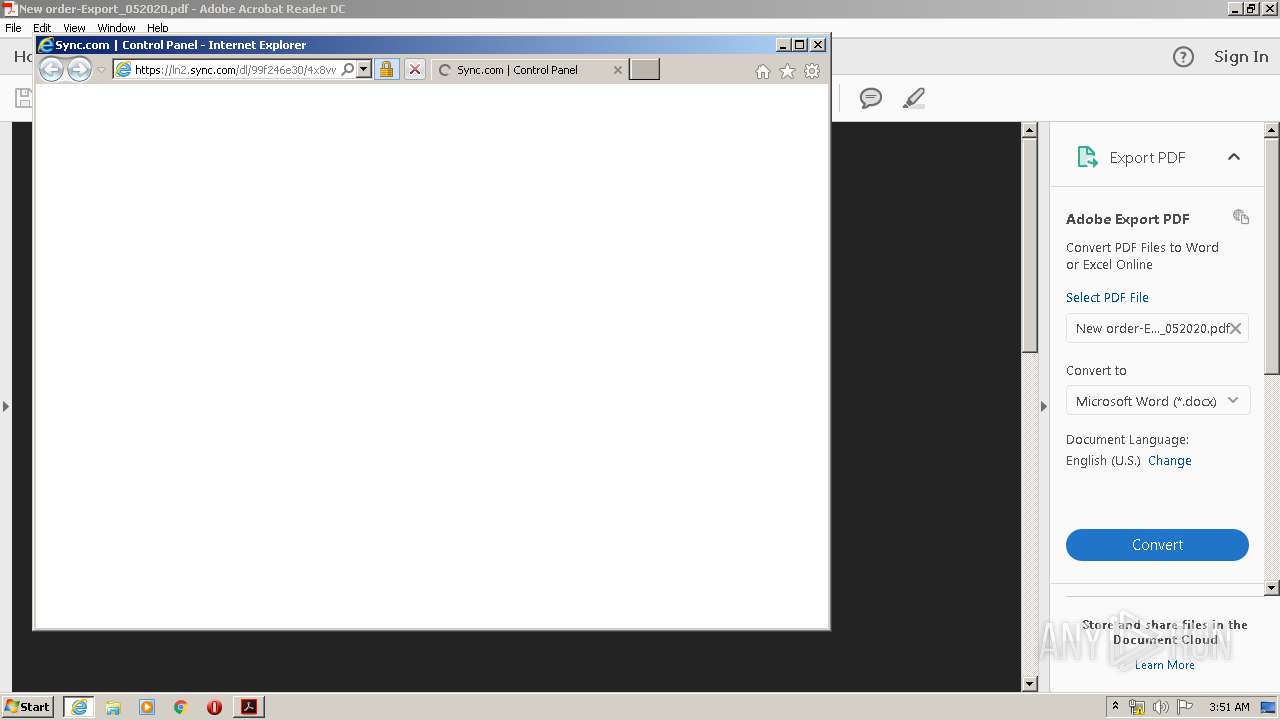
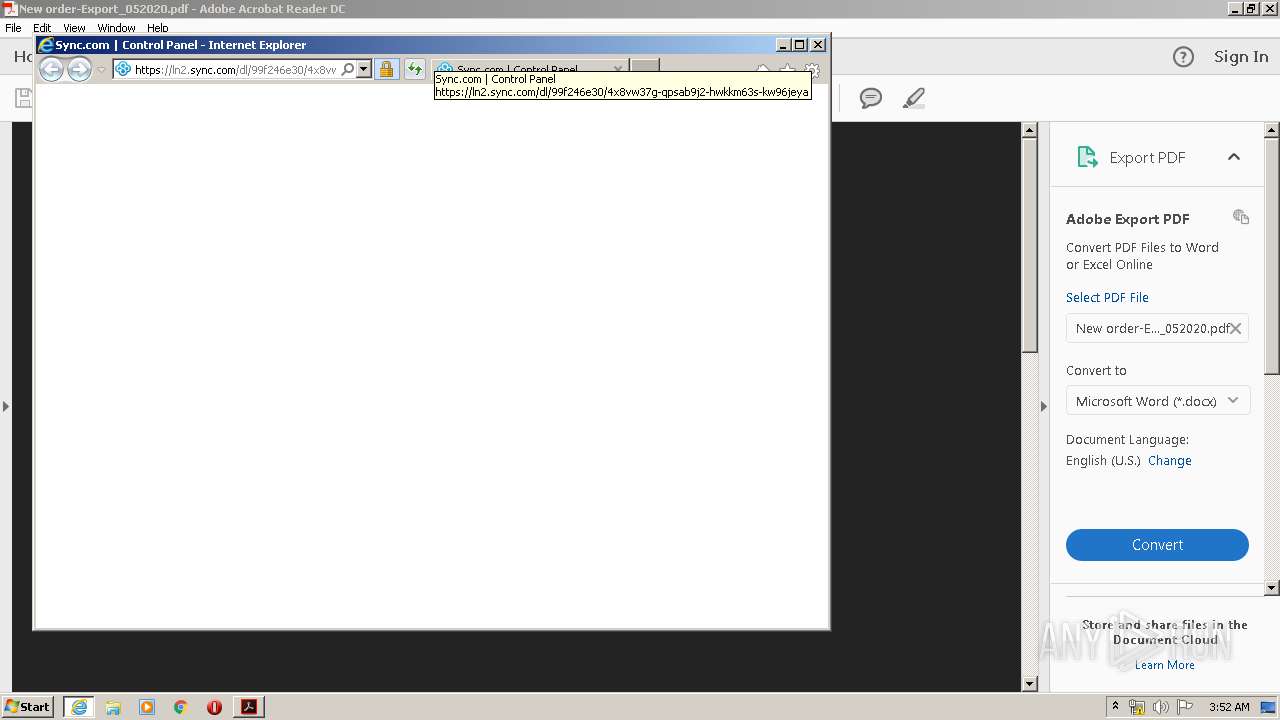
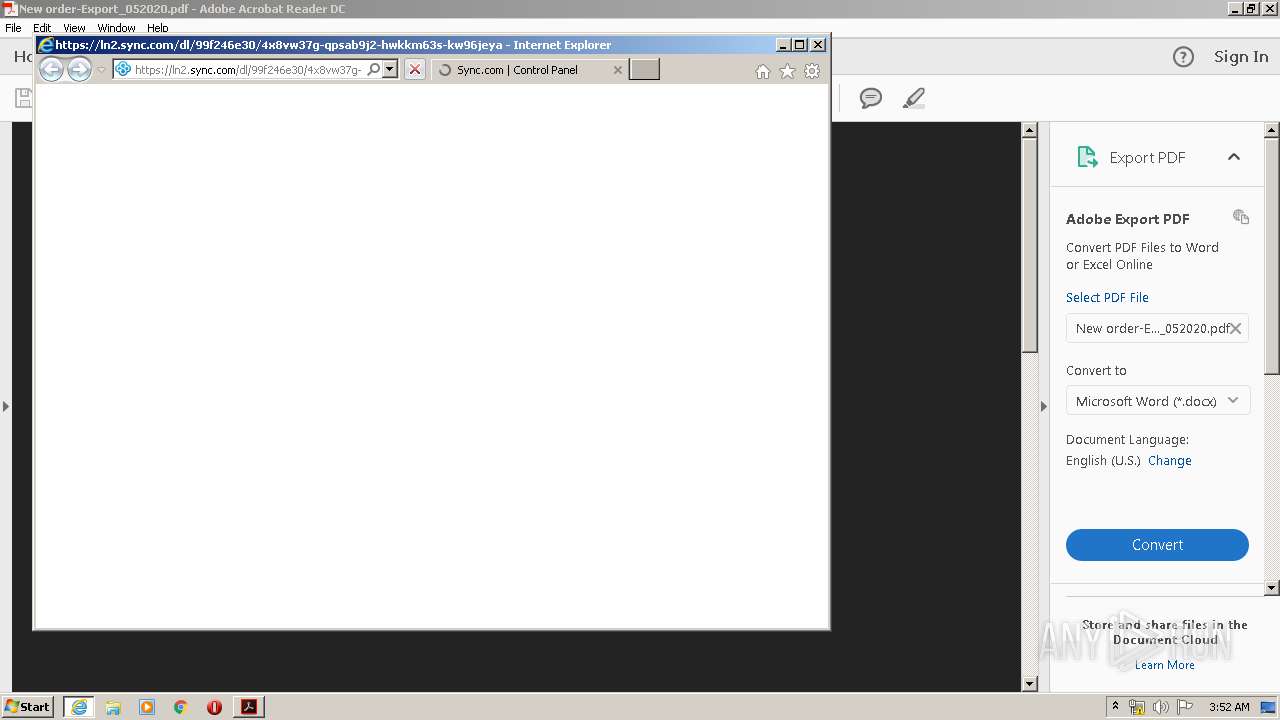
| 2672 | "C:\Program Files\Internet Explorer\iexplore.exe" https://ln2.sync.com/dl/99f246e30/4x8vw37g-qpsab9j2-hwkkm63s-kw96jeya | C:\Program Files\Internet Explorer\iexplore.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3460 | "C:\Program Files\Internet Explorer\iexplore.exe" https://ln2.sync.com/dl/99f246e30/4x8vw37g-qpsab9j2-hwkkm63s-kw96jeya | C:\Program Files\Internet Explorer\iexplore.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3864 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="2244.0.1835810530\1401274634" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
Total events
12 755
Read events
2 183
Write events
7 100
Delete events
3 472
Modification events
| (PID) Process: | (1948) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (1948) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | bExpandRHPInViewer |
Value: 1 | |||
| (PID) Process: | (1948) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\NoTimeOut |
| Operation: | write | Name: | smailto |
Value: 5900 | |||
| (PID) Process: | (564) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BROWSER_EMULATION |
| Operation: | write | Name: | AcroRd32.exe |
Value: 10001 | |||
| (PID) Process: | (564) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral\cRecentFiles\c1 |
| Operation: | write | Name: | aFS |
Value: DOS | |||
| (PID) Process: | (564) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral\cRecentFiles\c1 |
| Operation: | write | Name: | tDIText |
Value: /C/Users/admin/Desktop/New order-Export_052020.pdf | |||
| (PID) Process: | (564) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral\cRecentFiles\c1 |
| Operation: | write | Name: | tFileName |
Value: New order-Export_052020.pdf | |||
| (PID) Process: | (564) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral\cRecentFiles\c1 |
| Operation: | write | Name: | tFileSource |
Value: local | |||
| (PID) Process: | (564) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral\cRecentFiles\c1 |
| Operation: | write | Name: | sFileAncestors |
Value: 5B5D00 | |||
| (PID) Process: | (564) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral\cRecentFiles\c1 |
| Operation: | write | Name: | sDI |
Value: 2F432F55736572732F61646D696E2F4465736B746F702F4E6577206F726465722D4578706F72745F3035323032302E70646600 | |||
Executable files
0
Suspicious files
28
Text files
45
Unknown types
37
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1948 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages-journal | — | |
MD5:— | SHA256:— | |||
| 1948 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\Cache\AdobeFnt16.lst.1948 | — | |
MD5:— | SHA256:— | |||
| 1948 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeFnt16.lst.1948 | — | |
MD5:— | SHA256:— | |||
| 3924 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabBA88.tmp | — | |
MD5:— | SHA256:— | |||
| 3924 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarBA89.tmp | — | |
MD5:— | SHA256:— | |||
| 564 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeSysFnt15.lst | ps | |
MD5:— | SHA256:— | |||
| 1948 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages | sqlite | |
MD5:— | SHA256:— | |||
| 3924 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\AF3BA1CDD96BBC740C9CE3754F348BED_0AFA80FBB2E9062E22CDFD987DFF444F | binary | |
MD5:— | SHA256:— | |||
| 1948 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\UserCache.bin | binary | |
MD5:— | SHA256:— | |||
| 3460 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
34
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
564 | AcroRd32.exe | GET | 304 | 88.221.144.98:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/277_15_23_20070.zip | IT | — | — | whitelisted |
564 | AcroRd32.exe | GET | 304 | 88.221.144.98:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/281_15_23_20070.zip | IT | — | — | whitelisted |
564 | AcroRd32.exe | GET | 304 | 88.221.144.98:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/278_15_23_20070.zip | IT | — | — | whitelisted |
564 | AcroRd32.exe | GET | 304 | 88.221.144.98:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/280_15_23_20070.zip | IT | — | — | whitelisted |
3924 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://status.rapidssl.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRhhZrQET0hvbSHUJmNfBKqR%2FiT7wQUU8oXWfxrwAMhLxqu5KqoHIJW2nUCEA0mQt3sJpoS7XdnAOG%2Bh1U%3D | US | der | 471 b | shared |
3460 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
3924 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAilokbNS1yMg9cCtLurU0k%3D | US | der | 471 b | whitelisted |
3460 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
3460 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
564 | AcroRd32.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3924 | iexplore.exe | 52.201.110.51:443 | ln2.sync.com | Amazon.com, Inc. | US | unknown |
3460 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
564 | AcroRd32.exe | 2.21.41.101:443 | armmf.adobe.com | GTT Communications Inc. | FR | suspicious |
3924 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3460 | iexplore.exe | 52.201.110.51:443 | ln2.sync.com | Amazon.com, Inc. | US | unknown |
3460 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
— | — | 2.21.41.101:443 | armmf.adobe.com | GTT Communications Inc. | FR | suspicious |
564 | AcroRd32.exe | 88.221.144.98:80 | acroipm2.adobe.com | Akamai International B.V. | IT | whitelisted |
— | — | 88.221.144.98:80 | acroipm2.adobe.com | Akamai International B.V. | IT | whitelisted |
564 | AcroRd32.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ln2.sync.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
status.rapidssl.com |
| shared |
viewer.sync.com |
| whitelisted |
www.sync-rewards.com |
| whitelisted |
preview1.sync.com |
| whitelisted |
www.bing.com |
| whitelisted |
api.bing.com |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |