| URL: | https://hariracro1978.blogspot.com/ |
| Full analysis: | https://app.any.run/tasks/8ef17a93-2ac8-4532-ac30-53766b22d0f1 |
| Verdict: | Malicious activity |
| Analysis date: | February 18, 2019, 09:57:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 39F68DEC858B91D8CA5F9223266BA059 |
| SHA1: | C173D52C7FA8FE2450AF2B9D627D07E3F1A7B430 |
| SHA256: | 5EA850949711E453CEDF7C30EE8378B7E6E47A96C2BF623502C19FBBDE7DE9C1 |
| SSDEEP: | 3:N84mEIXzKK:24mEcKK |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Changes internet zones settings
- iexplore.exe (PID: 2984)
Reads internet explorer settings
- iexplore.exe (PID: 3552)
Application launched itself
- iexplore.exe (PID: 2984)
Creates files in the user directory
- iexplore.exe (PID: 3552)
- iexplore.exe (PID: 2984)
Reads Internet Cache Settings
- iexplore.exe (PID: 3552)
Reads settings of System Certificates
- iexplore.exe (PID: 2984)
Changes settings of System certificates
- iexplore.exe (PID: 2984)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2984)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
33
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2984 | "C:\Program Files\Internet Explorer\iexplore.exe" https://hariracro1978.blogspot.com/ | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3552 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2984 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
471
Read events
396
Write events
71
Delete events
4
Modification events
| (PID) Process: | (2984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (2984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000069000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {B075CD83-3363-11E9-BAD8-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (2984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (2984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 3 | |||
| (PID) Process: | (2984) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E30702000100120009003A0008003700 | |||
Executable files
0
Suspicious files
0
Text files
36
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2984 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\RB73MZ6Y\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 2984 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3552 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\hariracro1978_blogspot_com[1].txt | — | |
MD5:— | SHA256:— | |||
| 3552 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\hariracro1978_blogspot_com[1].htm | html | |
MD5:— | SHA256:— | |||
| 3552 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@girtelo[1].txt | text | |
MD5:— | SHA256:— | |||
| 3552 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\PP6KS563\comments[1].css | text | |
MD5:— | SHA256:— | |||
| 3552 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\BWPPCY0O\article[1].css | text | |
MD5:— | SHA256:— | |||
| 3552 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\MSHist012019021820190219\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3552 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\U2ZG9DE0\prl_girtelo_club[1].htm | html | |
MD5:— | SHA256:— | |||
| 3552 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\U2ZG9DE0\base[1].css | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
18
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3552 | iexplore.exe | GET | 302 | 104.27.139.166:80 | http://vip.girtelo.club/tracker?offer_id=2560&aff_id=225&pl=518:100&cb=1&gl=off | US | — | — | suspicious |
3552 | iexplore.exe | GET | 200 | 104.27.139.166:80 | http://prl.girtelo.club/prelands/518/css/comments.css | US | text | 3.43 Kb | suspicious |
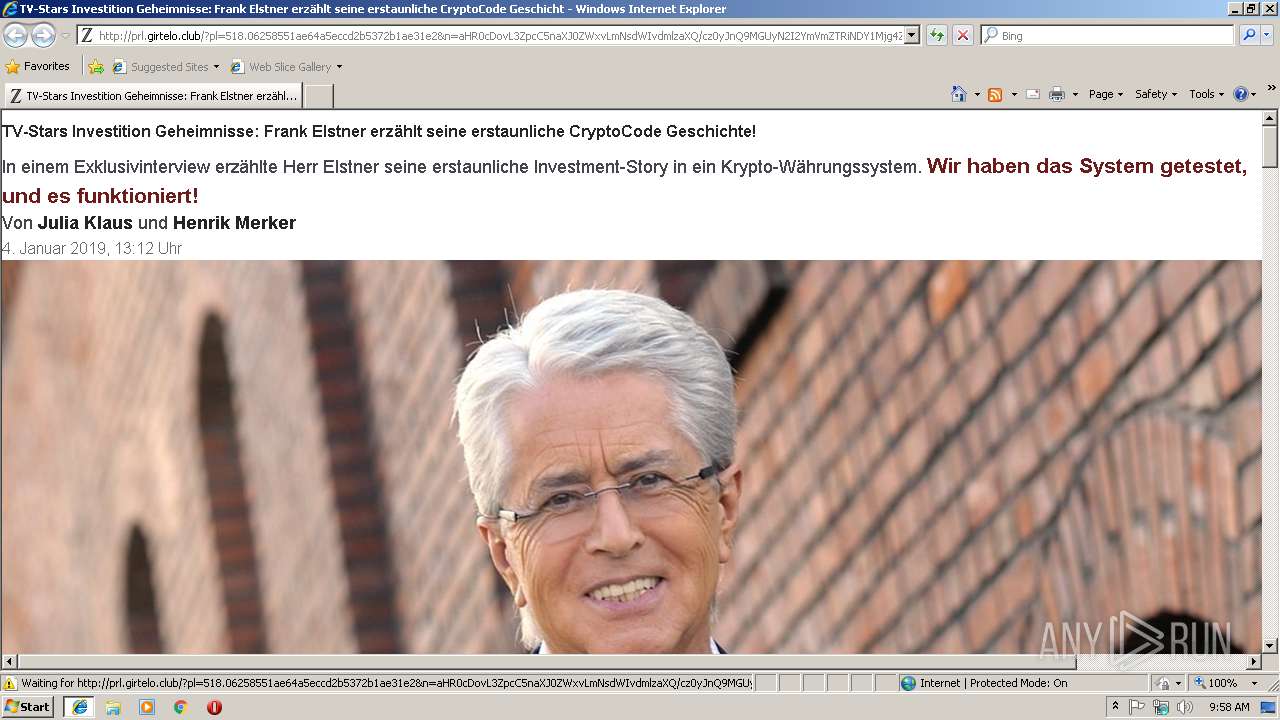
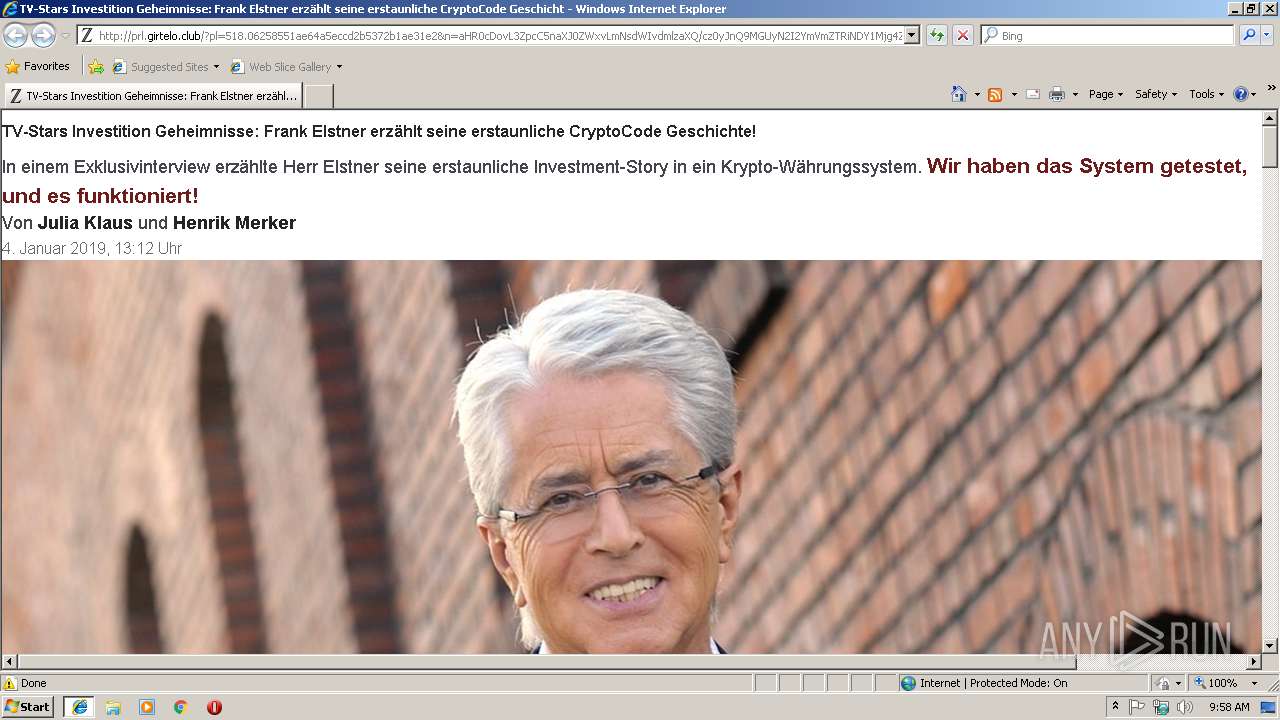
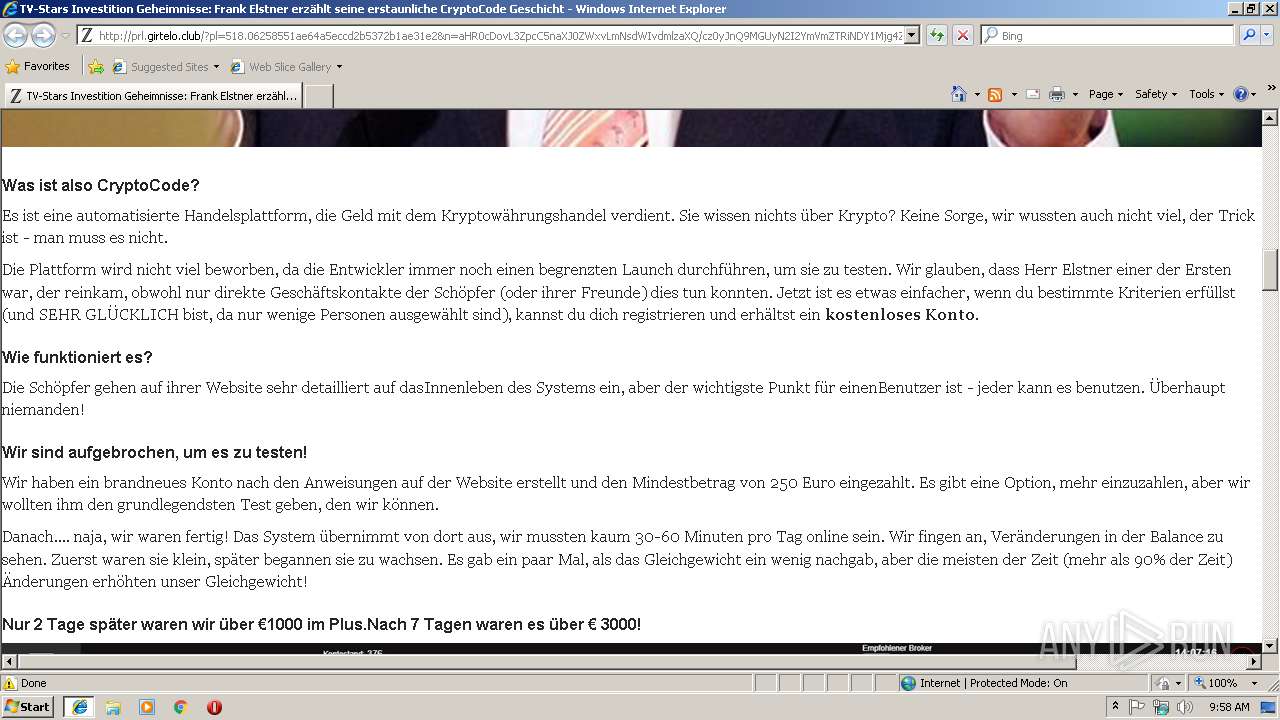
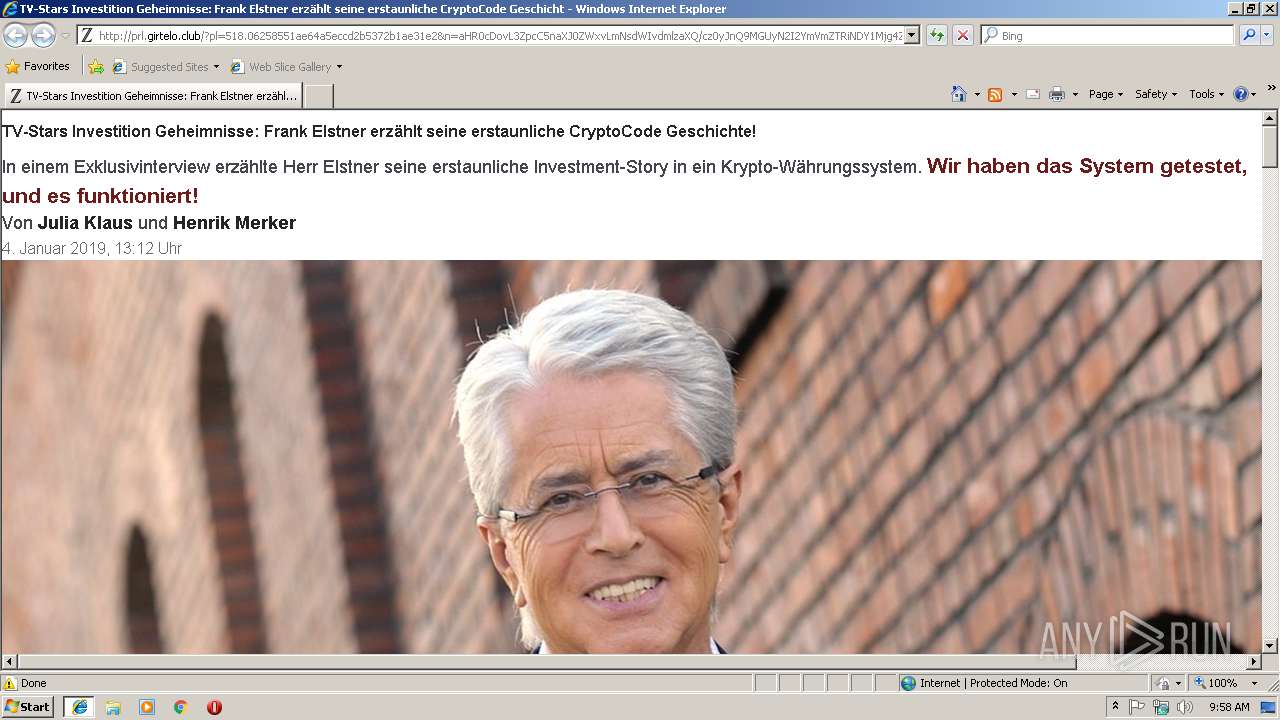
3552 | iexplore.exe | GET | 200 | 104.27.139.166:80 | http://prl.girtelo.club/?pl=518.06258551ae64a5eccd2b5372b1ae31e2&n=aHR0cDovL3ZpcC5naXJ0ZWxvLmNsdWIvdmlzaXQ/cz0yJnQ9MGUyN2I2YmVmZTRiNDY1Mjg4ZmIxMDU2NGU1MDFmZmYmbj1hSFIwY0RvdkwyUmxMbU55ZVhCMGJ5MWpiMlJsWVhCd0xuWnBjQzVuYVhKMFpXeHZMbU5zZFdJdlAzTmxjM05wYjI0OU1HVXlOMkkyWW1WbVpUUmlORFkxTWpnNFptSXhNRFUyTkdVMU1ERm1abVltWVdabVgybGtQVEl5TlNaallqMHhKbVp3Y0QweEptSndQVEU9 | US | html | 43.0 Kb | suspicious |
3552 | iexplore.exe | GET | 200 | 104.27.139.166:80 | http://prl.girtelo.club/prelands/518/css/gallery.css | US | text | 1.36 Kb | suspicious |
3552 | iexplore.exe | GET | 200 | 104.27.139.166:80 | http://prl.girtelo.club/prelands/518/css/content.css | US | text | 10.4 Kb | suspicious |
3552 | iexplore.exe | GET | 200 | 104.27.139.166:80 | http://prl.girtelo.club/prelands/518/css/normalize.css | US | text | 859 b | suspicious |
3552 | iexplore.exe | GET | 404 | 104.27.139.166:80 | http://prl.girtelo.club/prelands/518/fonts/TabletGothic-Regular.woff2)%20format(%22woff2%22),%20url(../fonts/TabletGothic-Regular.woff)%20format(%22woff%22 | US | html | 252 b | suspicious |
3552 | iexplore.exe | GET | 200 | 104.27.139.166:80 | http://prl.girtelo.club/prelands/518/css/faq.css | US | text | 1.14 Kb | suspicious |
3552 | iexplore.exe | GET | 404 | 104.27.139.166:80 | http://prl.girtelo.club/prelands/518/fonts/TabletGothic-Bold.woff2)%20format(%22woff2%22),%20url(../fonts/TabletGothic-Bold.woff)%20format(%22woff%22 | US | html | 249 b | suspicious |
3552 | iexplore.exe | GET | 200 | 104.27.139.166:80 | http://prl.girtelo.club/prelands/518/css/base.css | US | text | 8.09 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3552 | iexplore.exe | 172.217.16.193:443 | hariracro1978.blogspot.com | Google Inc. | US | whitelisted |
2984 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3552 | iexplore.exe | 172.217.18.3:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3552 | iexplore.exe | 172.217.21.201:443 | resources.blogblog.com | Google Inc. | US | whitelisted |
2984 | iexplore.exe | 104.27.139.166:80 | vip.girtelo.club | Cloudflare Inc | US | shared |
3552 | iexplore.exe | 172.217.22.99:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
3552 | iexplore.exe | 104.27.139.166:80 | vip.girtelo.club | Cloudflare Inc | US | shared |
2984 | iexplore.exe | 172.217.16.193:443 | hariracro1978.blogspot.com | Google Inc. | US | whitelisted |
3552 | iexplore.exe | 216.58.205.225:443 | themes.googleusercontent.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
hariracro1978.blogspot.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
resources.blogblog.com |
| whitelisted |
www.blogger.com |
| shared |
fonts.gstatic.com |
| whitelisted |
themes.googleusercontent.com |
| whitelisted |
vip.girtelo.club |
| suspicious |
prl.girtelo.club |
| suspicious |