| download: | tmp-vre.exe |
| Full analysis: | https://app.any.run/tasks/94e58ba5-97ab-4dae-b325-dda5014cee30 |
| Verdict: | Malicious activity |
| Analysis date: | April 15, 2019, 01:39:38 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 8E73FE1BE78E17AA2647B5530E4F770B |
| SHA1: | D23F646945C113305613B905E669A008781C5D99 |
| SHA256: | 5E9CCB97AA205A87B962BAC00DB14A0C919C414B42CDC1325FD1FFAC69B4B354 |
| SSDEEP: | 98304:7xZd2yn7ZogA4sy1sXnf0fnNaMBohKFUPM/jAOcwMbOED3NnH7NxBt0m2l+9Ig:7oy7eg/sXcfNNBjxafD3NnbjuE9 |
MALICIOUS
Loads dropped or rewritten executable
- java.exe (PID: 2752)
- java.exe (PID: 2168)
Application was dropped or rewritten from another process
- MakeLink.exe (PID: 1592)
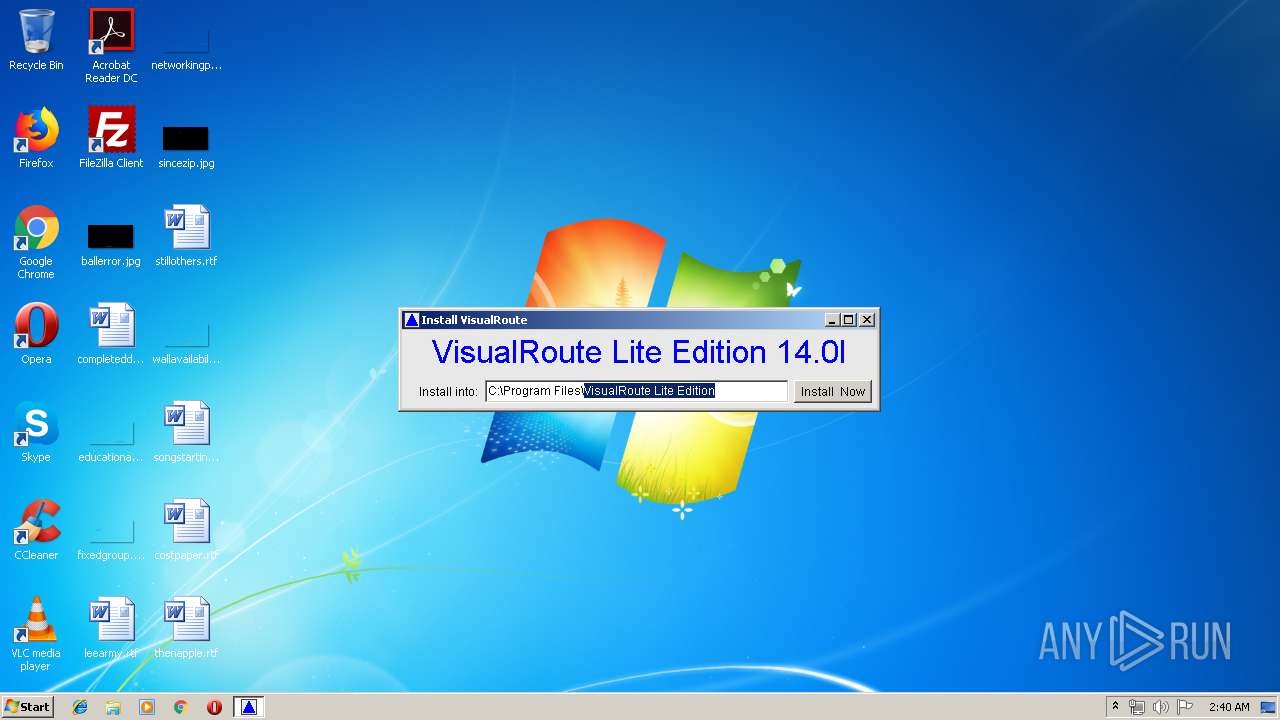
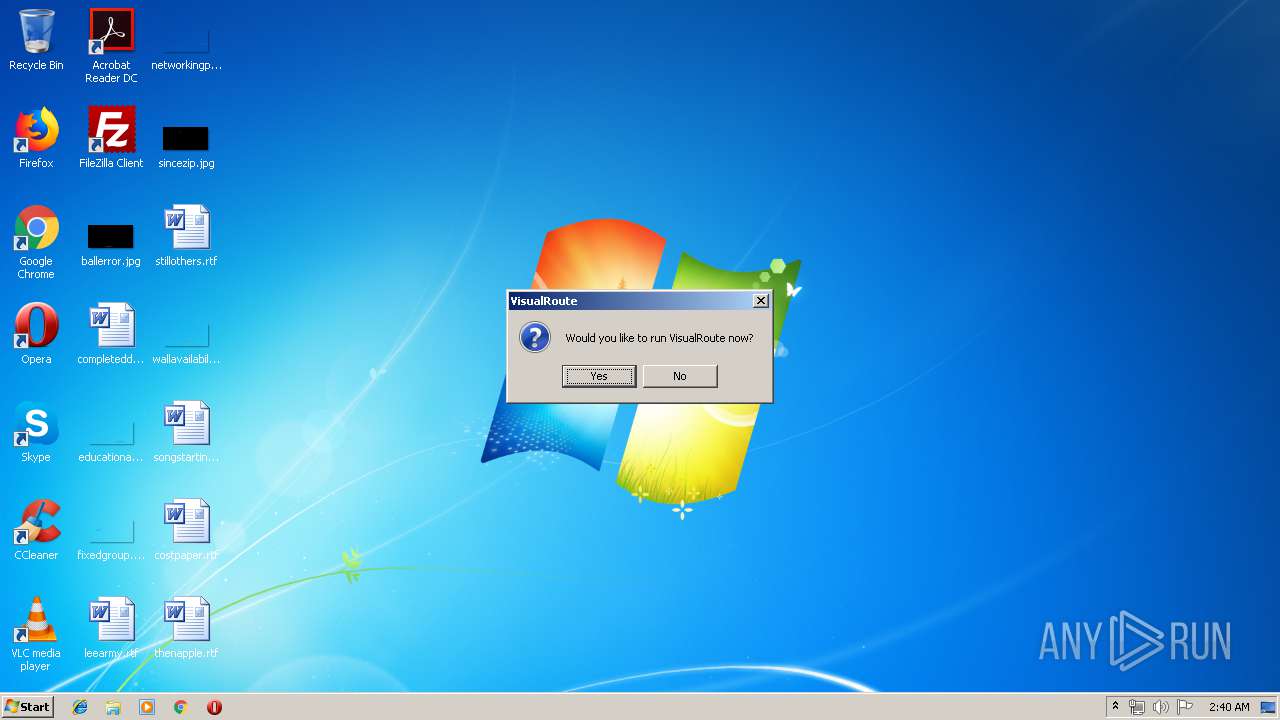
- VisualRoute.exe (PID: 2368)
- VisualRoute.exe (PID: 2304)
SUSPICIOUS
Executable content was dropped or overwritten
- java.exe (PID: 2752)
- java.exe (PID: 1520)
- java.exe (PID: 1500)
- java.exe (PID: 2280)
Creates files in the program directory
- MakeLink.exe (PID: 1592)
- java.exe (PID: 2752)
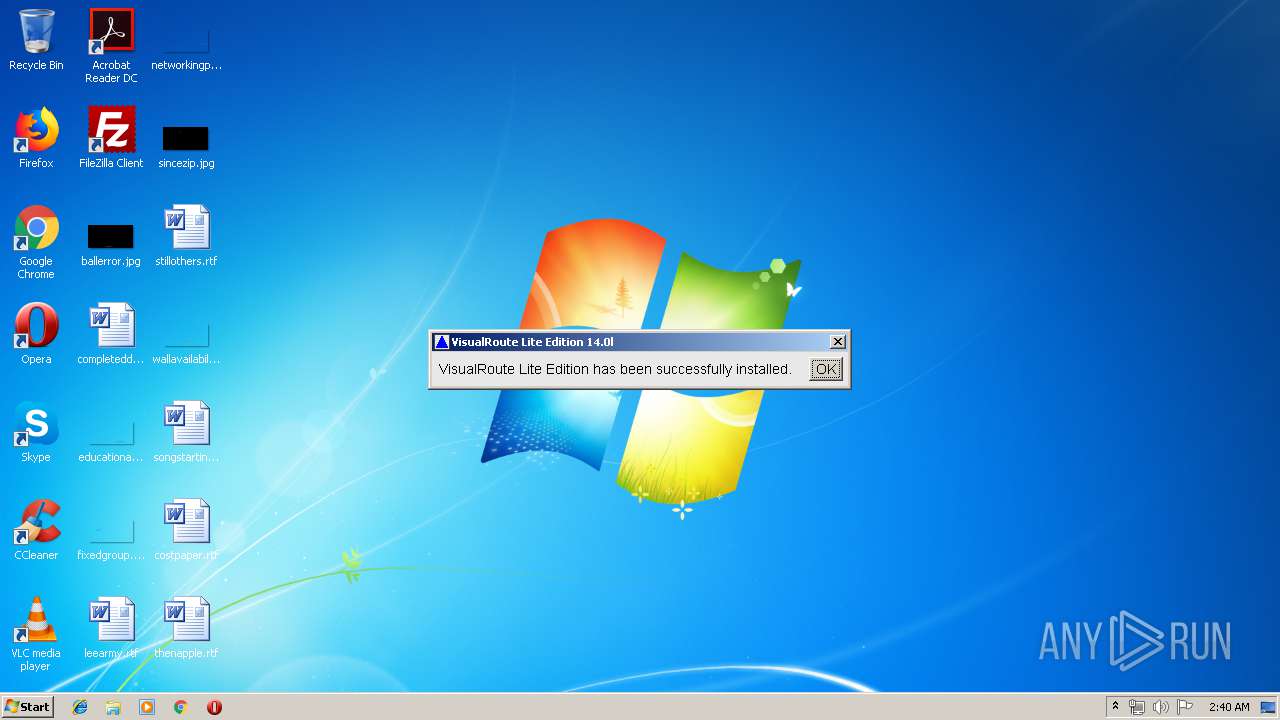
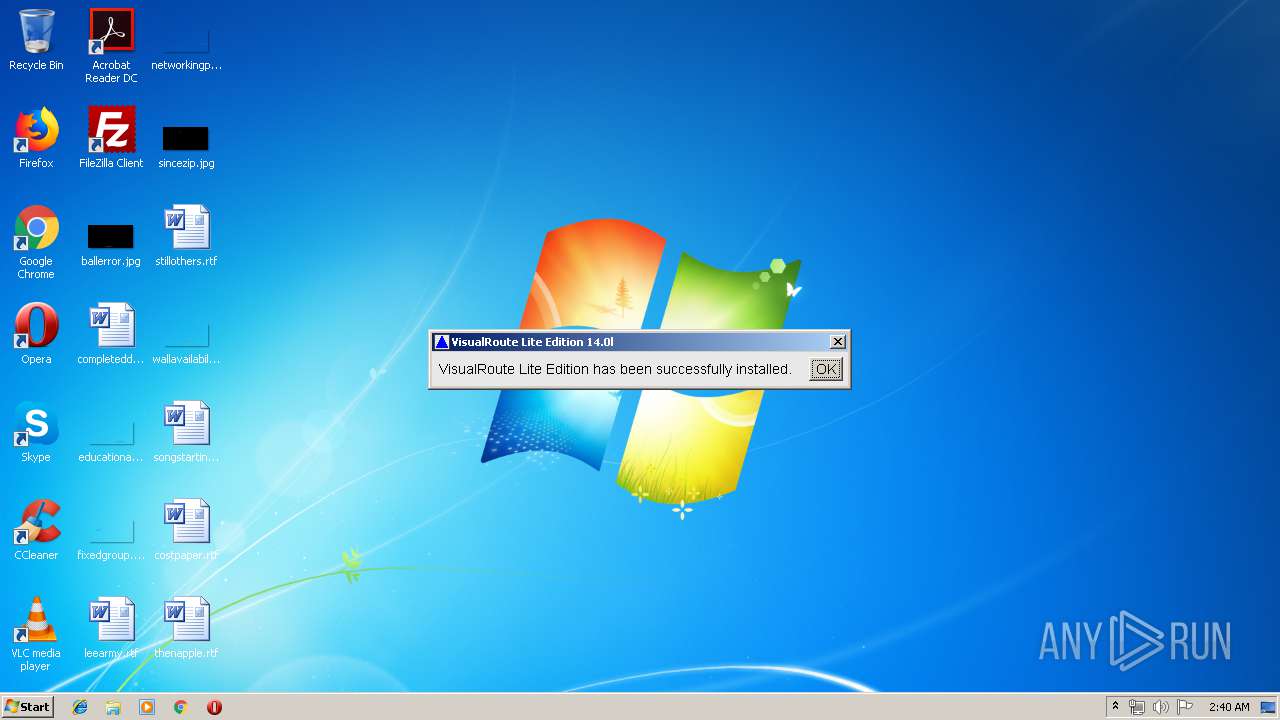
Creates a software uninstall entry
- java.exe (PID: 2752)
Starts Internet Explorer
- java.exe (PID: 2280)
INFO
Dropped object may contain Bitcoin addresses
- java.exe (PID: 2752)
- java.exe (PID: 2280)
Reads internet explorer settings
- iexplore.exe (PID: 3848)
Changes internet zones settings
- iexplore.exe (PID: 1096)
Reads Internet Cache Settings
- iexplore.exe (PID: 3848)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (67.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.2) |
| .exe | | | Win32 Executable (generic) (9.7) |
| .exe | | | Generic Win/DOS Executable (4.3) |
| .exe | | | DOS Executable Generic (4.3) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2005:12:19 19:55:35+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 6656 |
| InitializedDataSize: | 5632 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x26c8 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 19-Dec-2005 18:55:35 |
| Detected languages: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 4 |
| Time date stamp: | 19-Dec-2005 18:55:35 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0000185C | 0x00001A00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.99769 |
.rdata | 0x00003000 | 0x0000062A | 0x00000800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.11709 |
.data | 0x00004000 | 0x000005A4 | 0x00000600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.353 |
.rsrc | 0x00005000 | 0x00000604 | 0x00000800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.9741 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.81042 | 542 | Latin 1 / Western European | English - United States | RT_MANIFEST |
234 | 2.16096 | 20 | Latin 1 / Western European | English - United States | RT_GROUP_ICON |
Imports
ADVAPI32.dll |
KERNEL32.dll |
MSVCRT.dll |
SHELL32.dll |
USER32.dll |
Total processes
47
Monitored processes
12
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 760 | "C:\Users\admin\AppData\Local\Temp\tmp-vre.exe" | C:\Users\admin\AppData\Local\Temp\tmp-vre.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1096 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | java.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1500 | java -mx256m jexepackboot E "C:\Program Files\VisualRoute Lite Edition\VisualRoute.exe" "C:\Users\admin\AppData\Local\Temp\X441900" | C:\ProgramData\Oracle\Java\javapath\java.exe | VisualRoute.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 12345 Version: 8.0.920.14 Modules
| |||||||||||||||
| 1520 | java -mx256m jexepackboot E "C:\Program Files\VisualRoute Lite Edition\VisualRoute.exe" "C:\Users\admin\AppData\Local\Temp\X43E940" /install | C:\ProgramData\Oracle\Java\javapath\java.exe | VisualRoute.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 12345 Version: 8.0.920.14 Modules
| |||||||||||||||
| 1592 | "C:\Users\admin\AppData\Local\Temp\X435DB4\MakeLink" C:\Users\admin\AppData\Local\Temp\X435DB4\makelinks.txt | C:\Users\admin\AppData\Local\Temp\X435DB4\MakeLink.exe | — | java.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2168 | java -mx256m jexepackboot R "C:\Program Files\VisualRoute Lite Edition\VisualRoute.exe" "C:\Users\admin\AppData\Local\Temp\X43E940" /install | C:\ProgramData\Oracle\Java\javapath\java.exe | — | VisualRoute.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2280 | java -mx256m jexepackboot R "C:\Program Files\VisualRoute Lite Edition\VisualRoute.exe" "C:\Users\admin\AppData\Local\Temp\X441900" | C:\ProgramData\Oracle\Java\javapath\java.exe | VisualRoute.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
| 2304 | "C:\Program Files\VisualRoute Lite Edition\VisualRoute.exe" | C:\Program Files\VisualRoute Lite Edition\VisualRoute.exe | — | java.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2368 | "C:\Program Files\VisualRoute Lite Edition\VisualRoute.exe" -Q* /install | C:\Program Files\VisualRoute Lite Edition\VisualRoute.exe | — | java.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2752 | java -mx256m jexepackboot ER "C:\Users\admin\AppData\Local\Temp\tmp-vre.exe" "C:\Users\admin\AppData\Local\Temp\X435DB4" | C:\ProgramData\Oracle\Java\javapath\java.exe | tmp-vre.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: HIGH Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
Total events
594
Read events
520
Write events
74
Delete events
0
Modification events
| (PID) Process: | (2752) java.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: java.exe | |||
| (PID) Process: | (2752) java.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\VisualRoute.exe |
| Operation: | write | Name: | |
Value: C:\Program Files\VisualRoute Lite Edition\VisualRoute.exe | |||
| (PID) Process: | (2752) java.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\App Paths\VisualRoute.exe |
| Operation: | write | Name: | Path |
Value: C:\Program Files\VisualRoute Lite Edition | |||
| (PID) Process: | (2752) java.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\VisualRoute Lite Edition |
| Operation: | write | Name: | DisplayName |
Value: VisualRoute Lite Edition | |||
| (PID) Process: | (2752) java.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\VisualRoute Lite Edition |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files\VisualRoute Lite Edition\Uninstall.exe" "C:\Program Files\VisualRoute Lite Edition" | |||
| (PID) Process: | (2168) java.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: java.exe | |||
| (PID) Process: | (2168) java.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2168) java.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2280) java.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: java.exe | |||
| (PID) Process: | (1096) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
Executable files
25
Suspicious files
38
Text files
407
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2752 | java.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | text | |
MD5:— | SHA256:— | |||
| 2752 | java.exe | C:\Users\admin\AppData\Local\Temp\X435DB4\src\data\cities.txt+ | binary | |
MD5:— | SHA256:— | |||
| 2752 | java.exe | C:\Users\admin\AppData\Local\Temp\X435DB4\packlist.txt | text | |
MD5:— | SHA256:— | |||
| 2752 | java.exe | C:\Users\admin\AppData\Local\Temp\X435DB4\src\data\countrycodes.txt | text | |
MD5:— | SHA256:— | |||
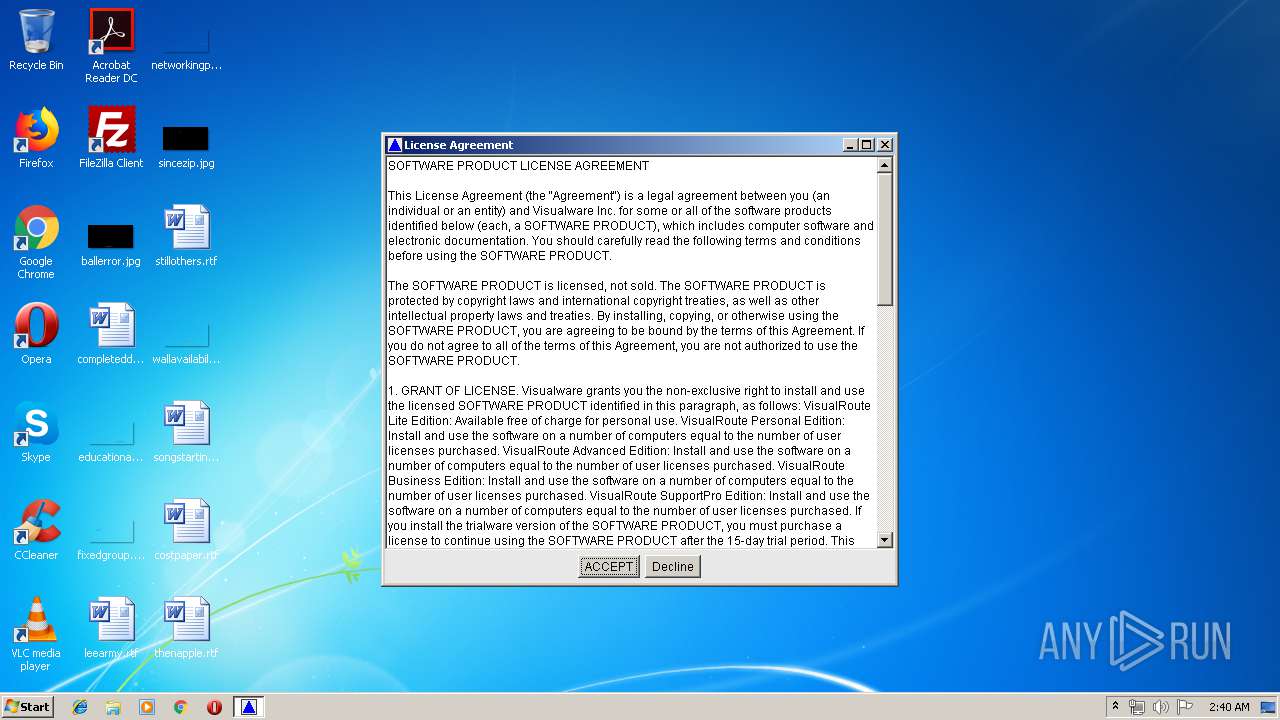
| 2752 | java.exe | C:\Users\admin\AppData\Local\Temp\X435DB4\LicenseAgreement.class | class | |
MD5:4B5933A6927997F56F7B4623CAC4BE5F | SHA256:26C6D5EA64F4FC3AE29530F27E7C0337545E5E974001E60288A5E214056E1CD2 | |||
| 2752 | java.exe | C:\Users\admin\AppData\Local\Temp\X435DB4\src\data\domains.txt+ | binary | |
MD5:— | SHA256:— | |||
| 2752 | java.exe | C:\Users\admin\AppData\Local\Temp\X435DB4\src\data\geo.vdb | binary | |
MD5:— | SHA256:— | |||
| 2752 | java.exe | C:\Users\admin\AppData\Local\Temp\X435DB4\src\data\ip2cc.db | binary | |
MD5:— | SHA256:— | |||
| 3508 | tmp-vre.exe | C:\Users\admin\AppData\Local\Temp\X435DB4\jexepackboot.class | class | |
MD5:EEC36E37CEA2A02ED0AD4D29F4402293 | SHA256:5189CD87E4D46DAB11E7E204BDE8ADAF9226346C7428085FE182A380764A882E | |||
| 2752 | java.exe | C:\Users\admin\AppData\Local\Temp\X435DB4\src\data\ports.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
5
DNS requests
3
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
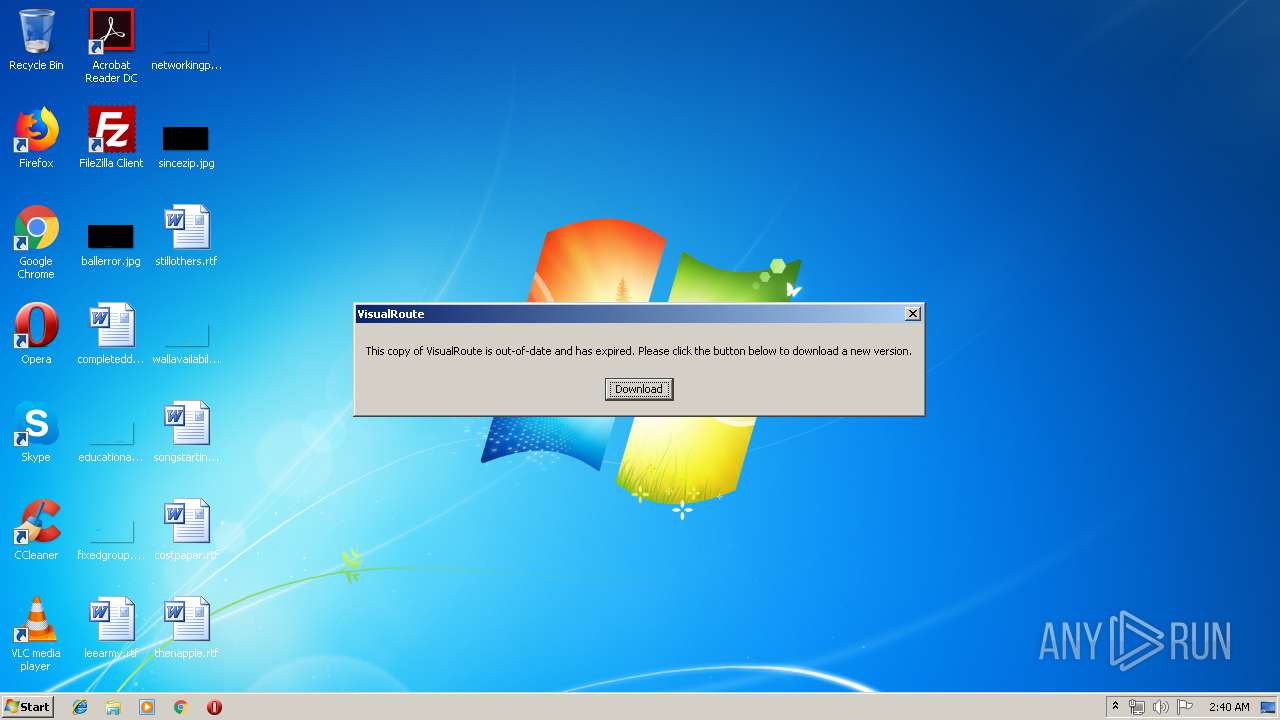
2280 | java.exe | GET | 200 | 38.100.141.80:80 | http://www.visualroute.com/updates/updates.txt | US | text | 86 b | malicious |
3848 | iexplore.exe | GET | 200 | 38.100.141.76:80 | http://www.visualware.com/indexm.html | US | html | 1.55 Kb | malicious |
2280 | java.exe | GET | 200 | 38.100.141.80:80 | http://www.visualroute.com/clientconfig/fixedagents14.bin | US | binary | 128 b | malicious |
3848 | iexplore.exe | GET | 302 | 38.100.141.76:80 | http://www.visualware.com/promovr/banner468x60.gif | US | html | 303 b | malicious |
3848 | iexplore.exe | GET | 200 | 38.100.141.76:80 | http://www.visualware.com/indexm.html | US | html | 1.55 Kb | malicious |
3848 | iexplore.exe | GET | 302 | 38.100.141.76:80 | http://www.visualware.com/gimages/logo.gif | US | html | 303 b | malicious |
1096 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3848 | iexplore.exe | 38.100.141.76:80 | www.visualware.com | Cogent Communications | US | suspicious |
2280 | java.exe | 38.100.141.80:80 | www.visualroute.com | Cogent Communications | US | malicious |
3848 | iexplore.exe | 38.100.141.80:80 | www.visualroute.com | Cogent Communications | US | malicious |
1096 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.visualroute.com |
| malicious |
www.bing.com |
| whitelisted |
www.visualware.com |
| malicious |