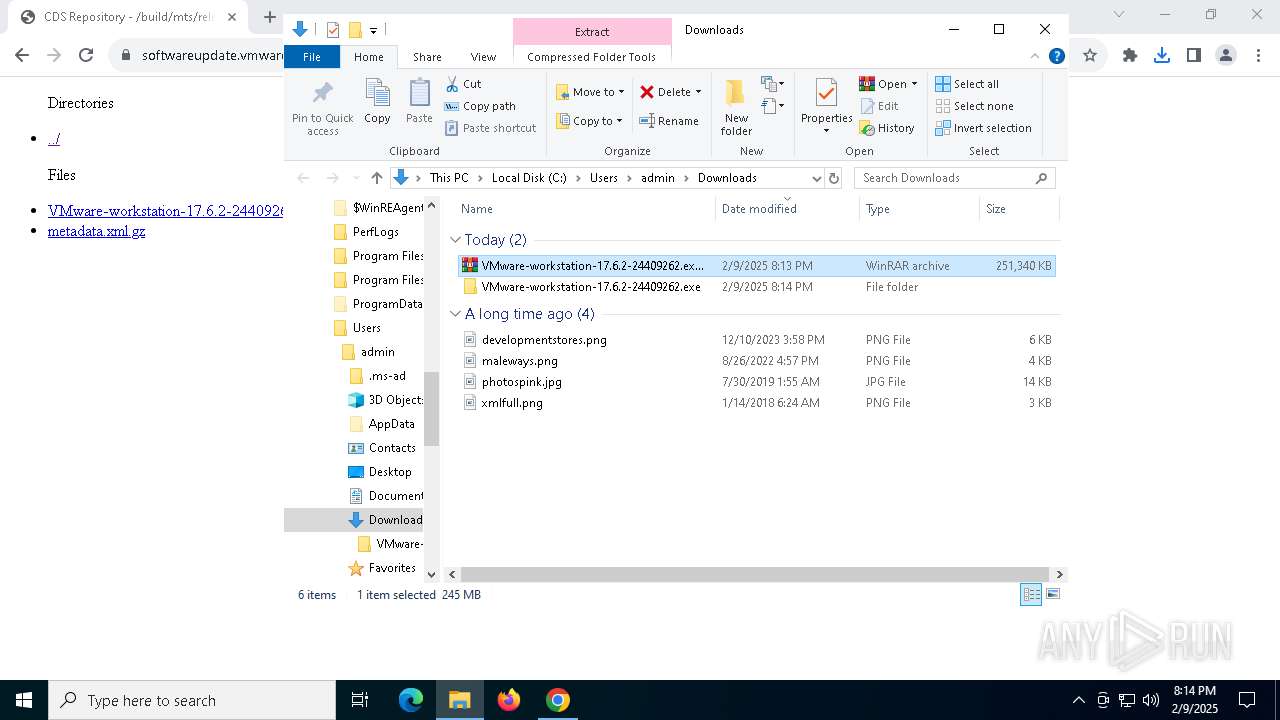
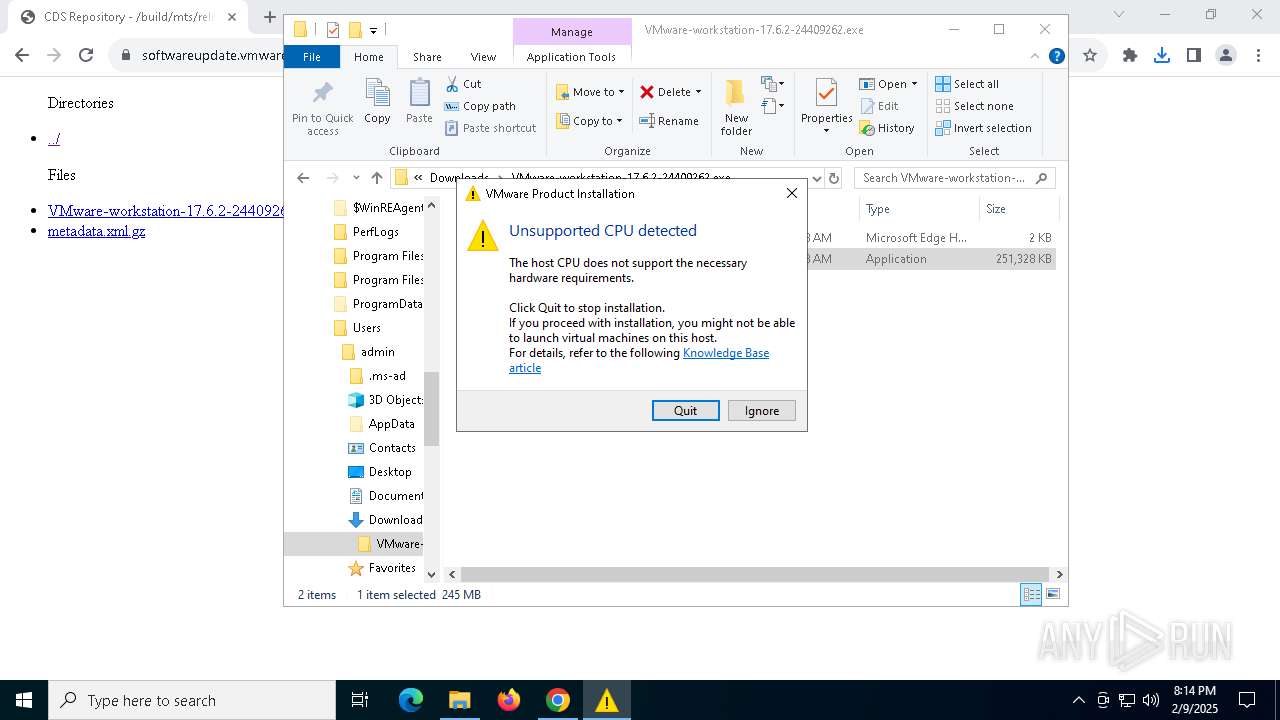
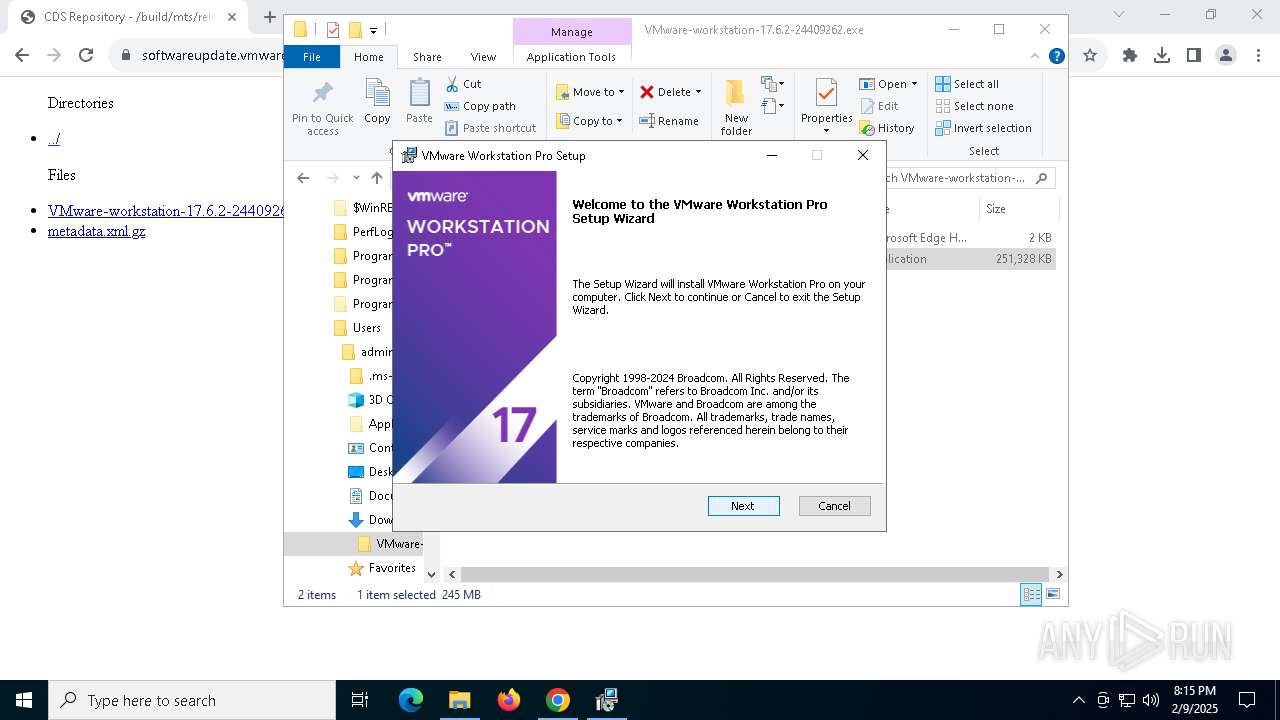
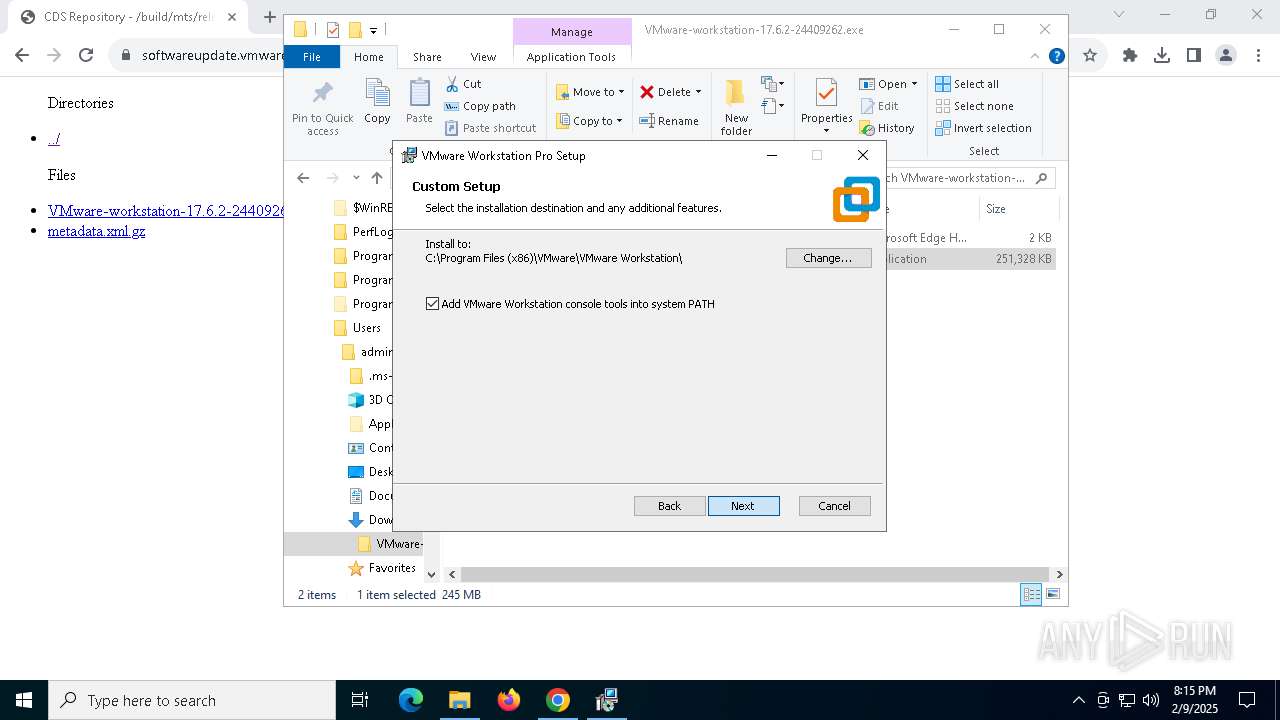
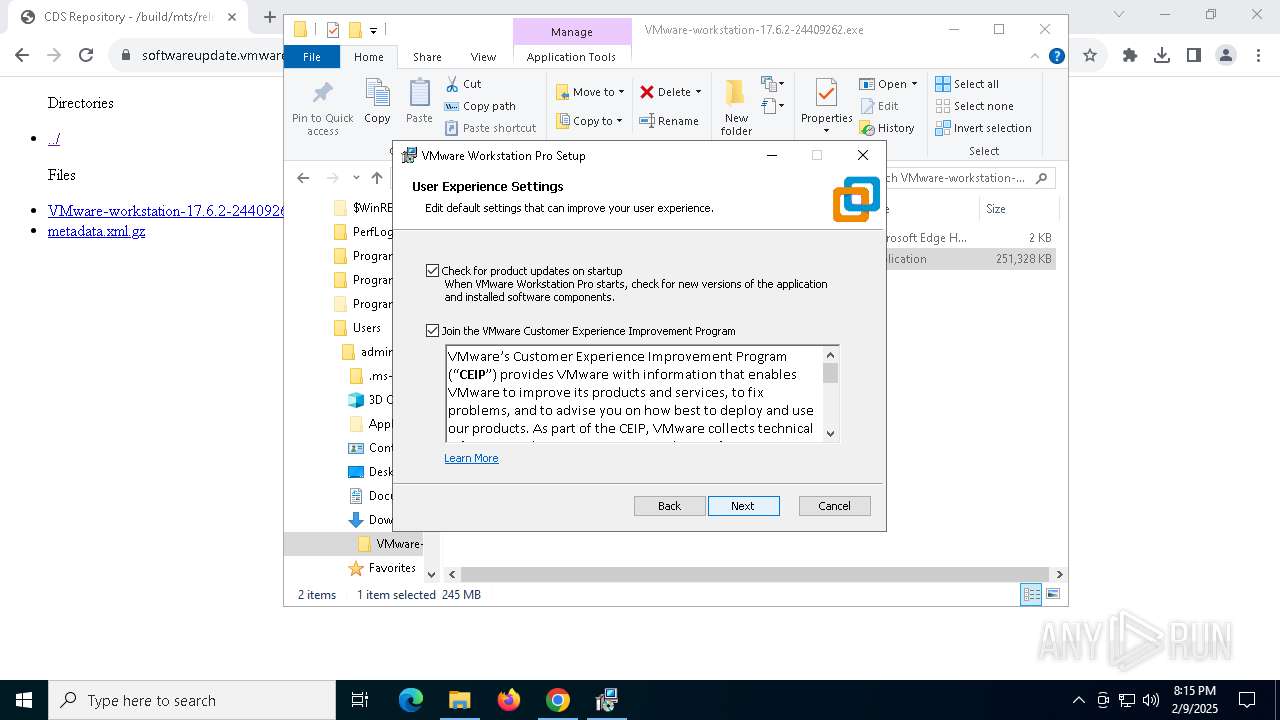
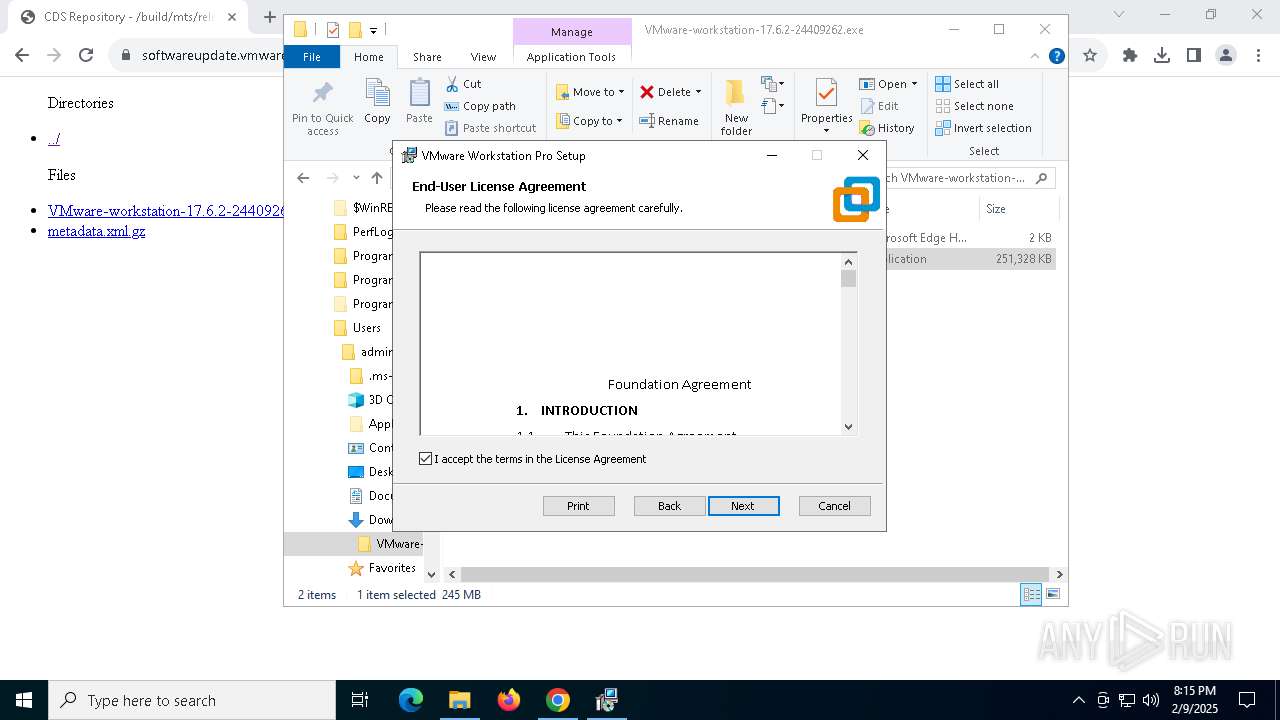
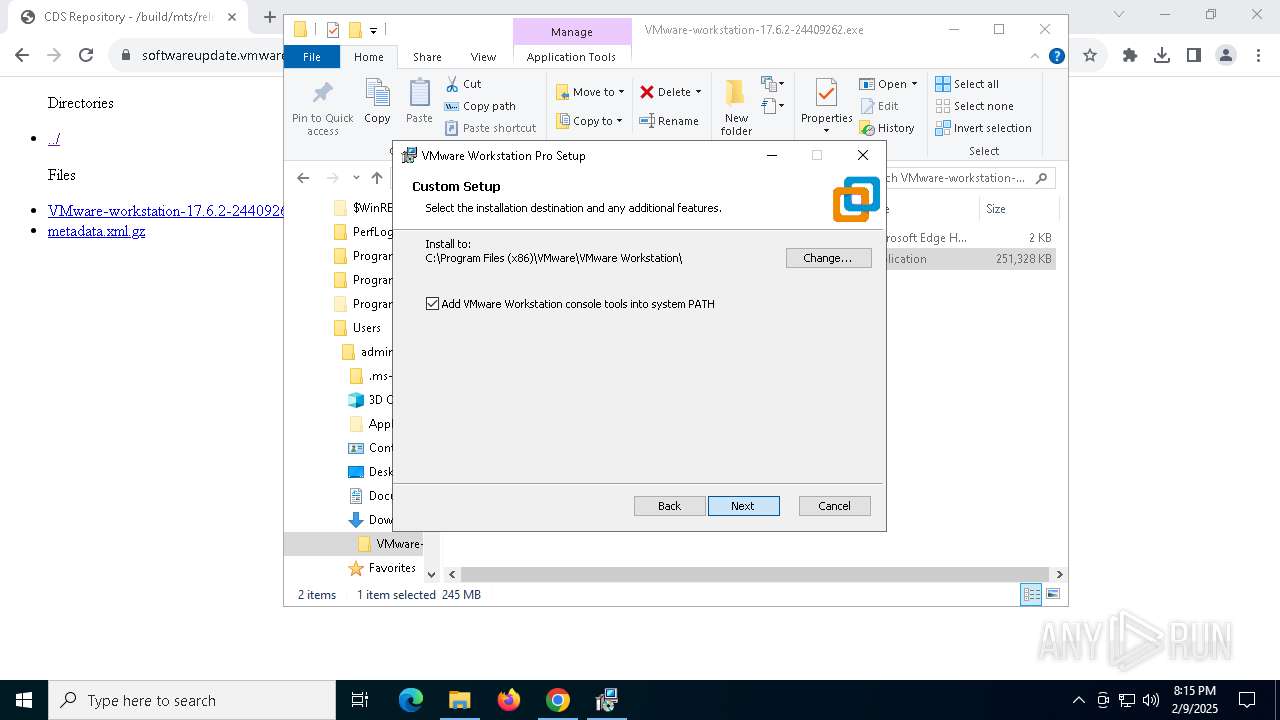
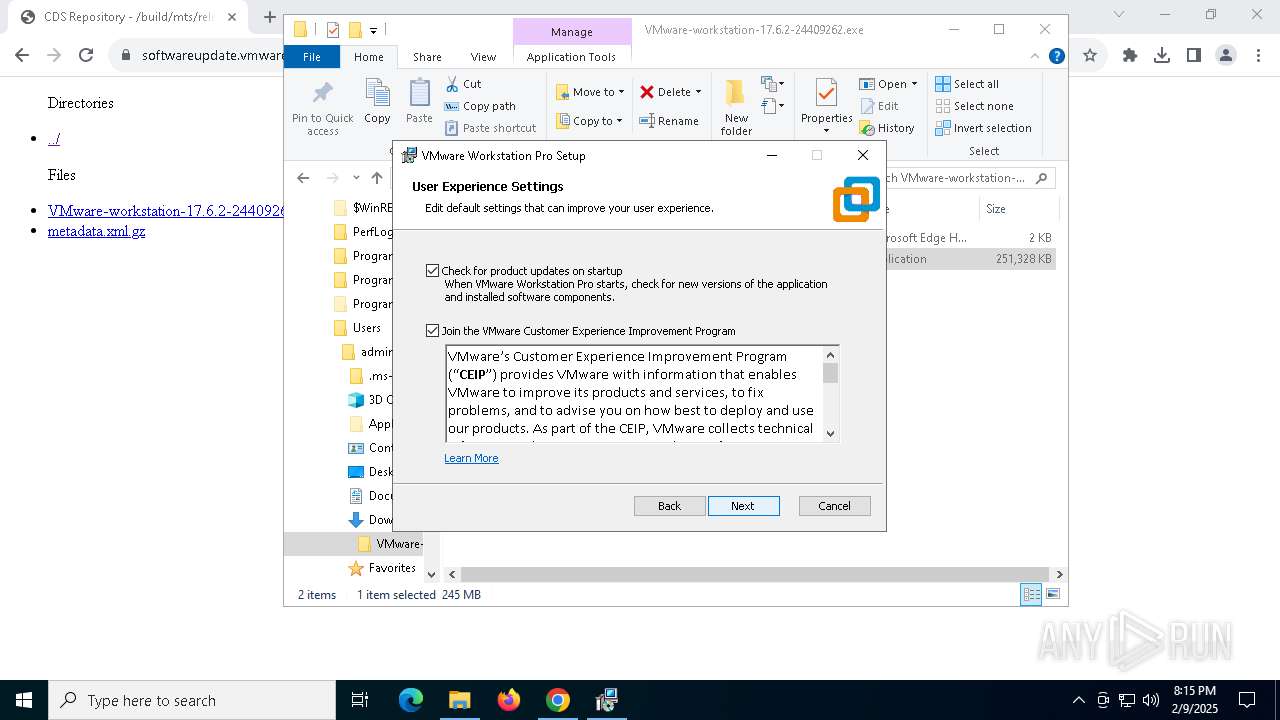
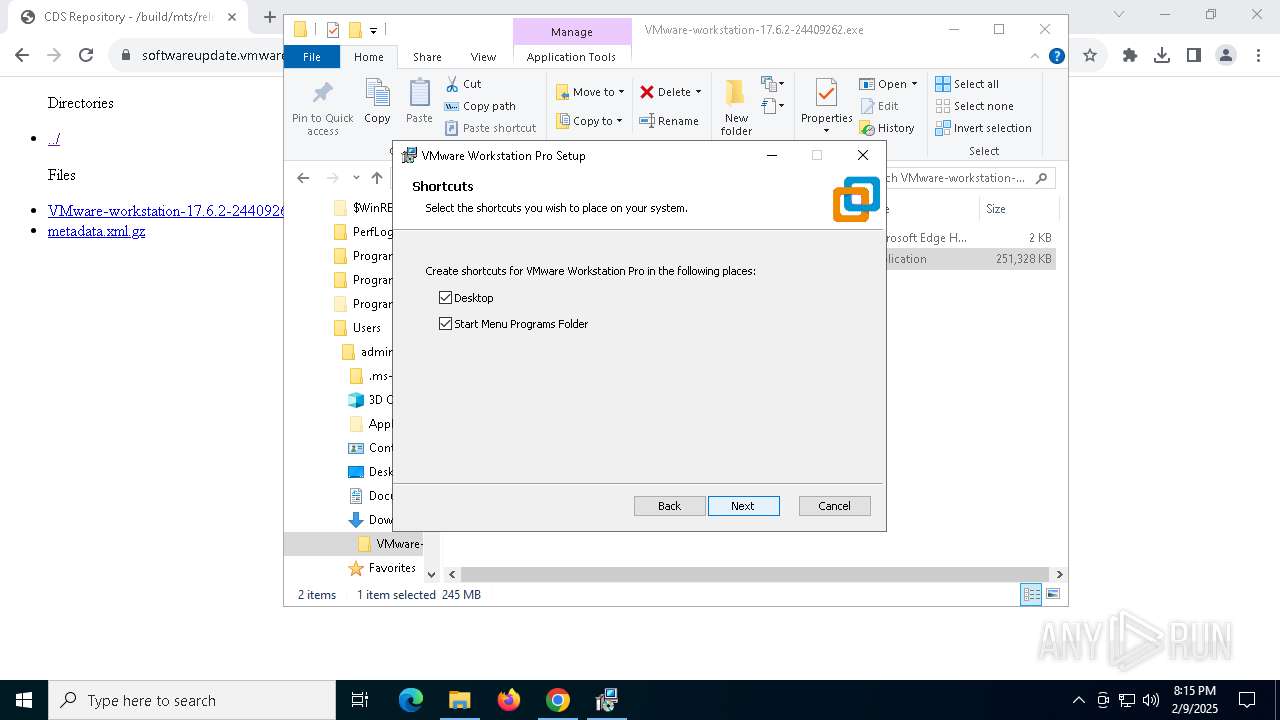
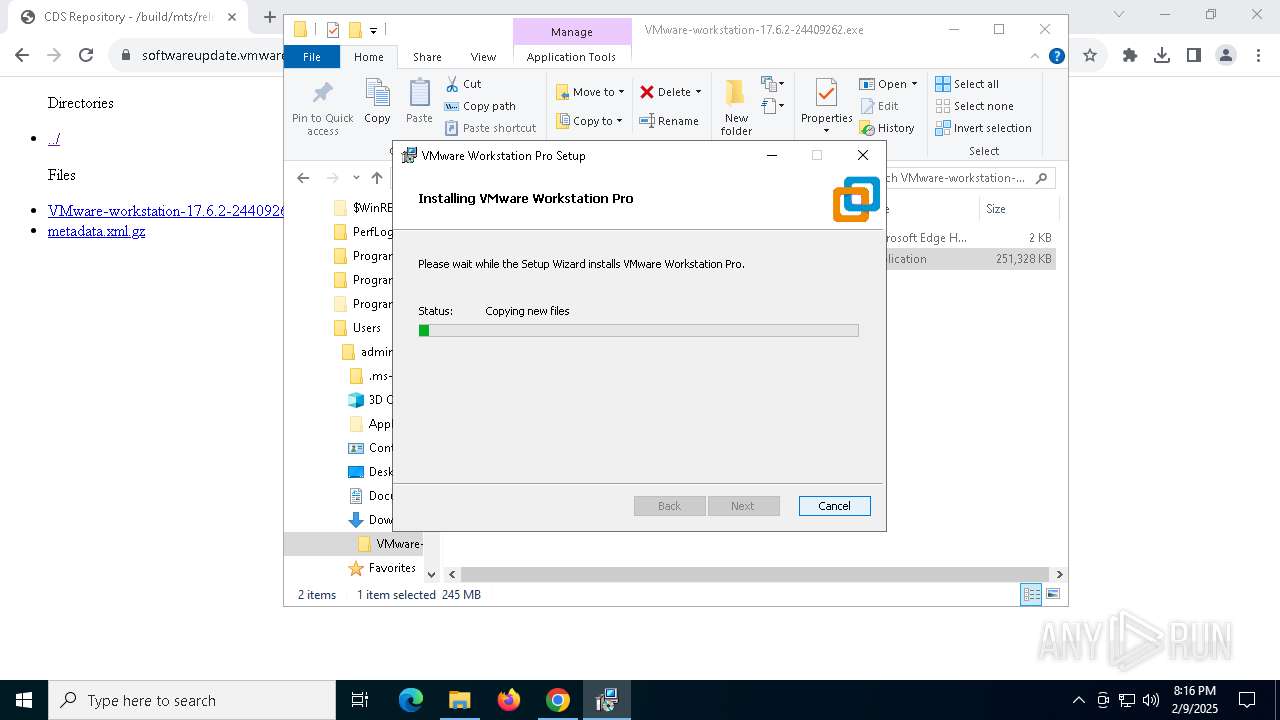
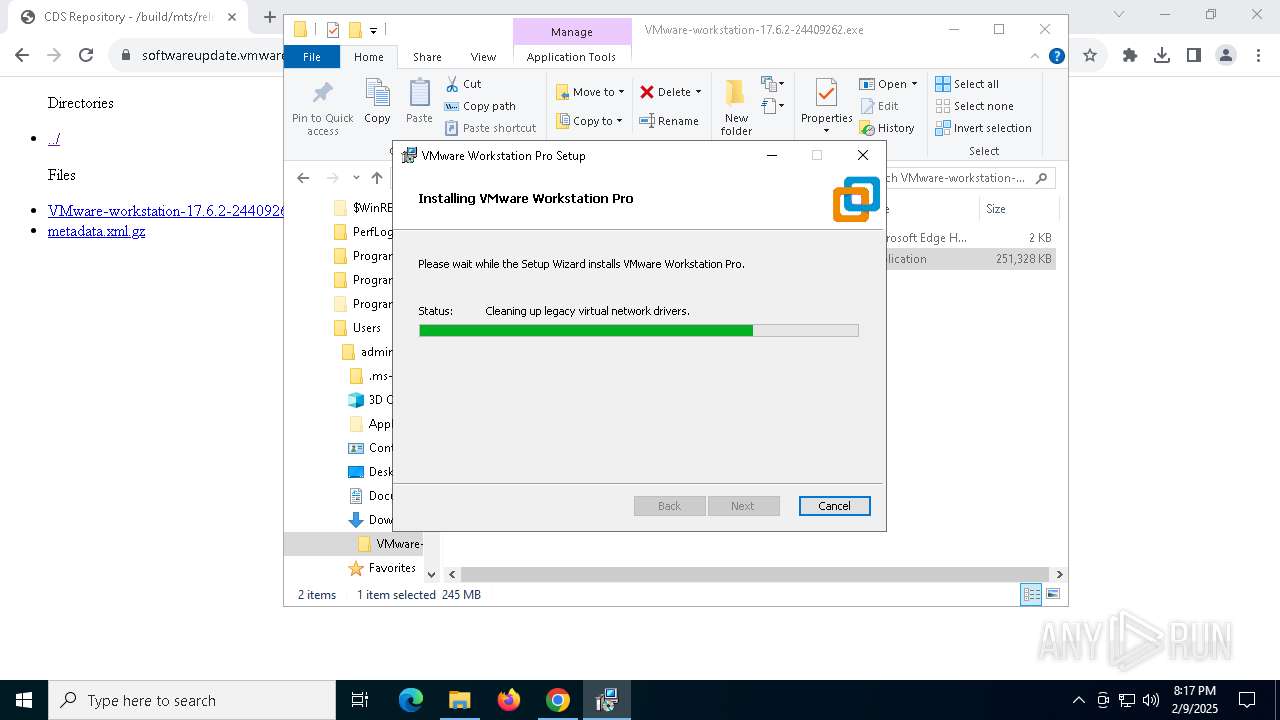
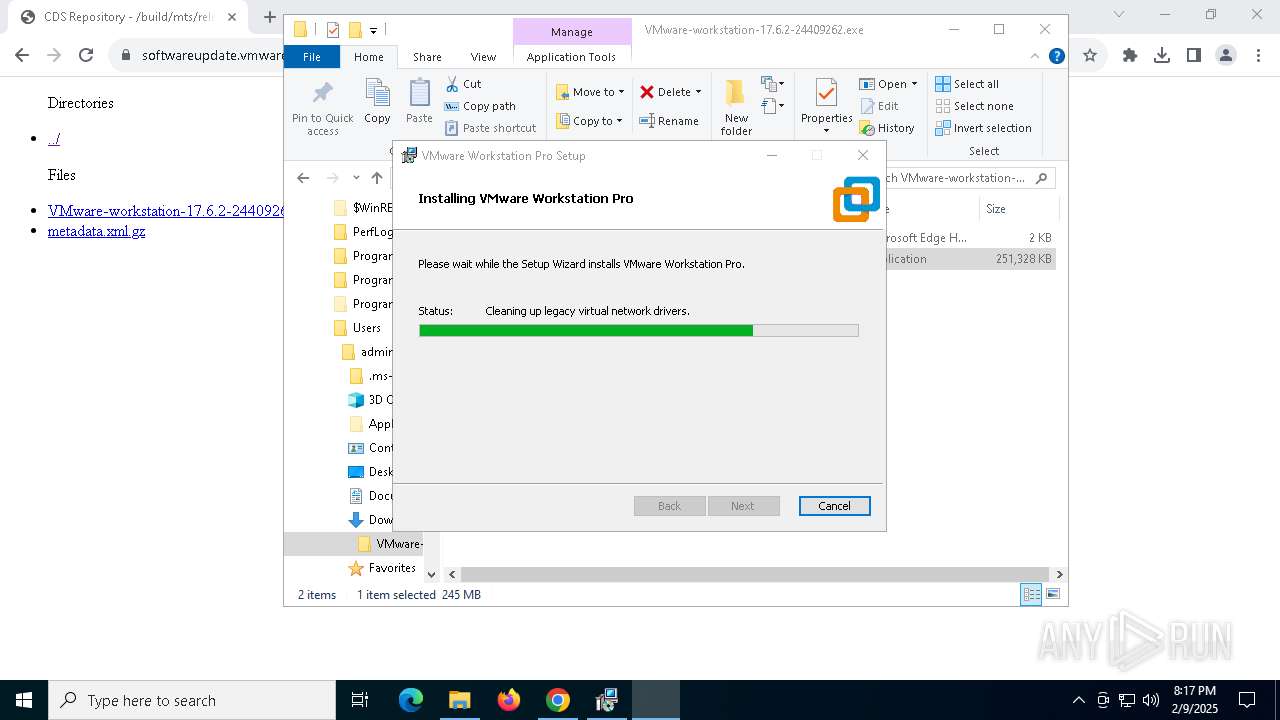
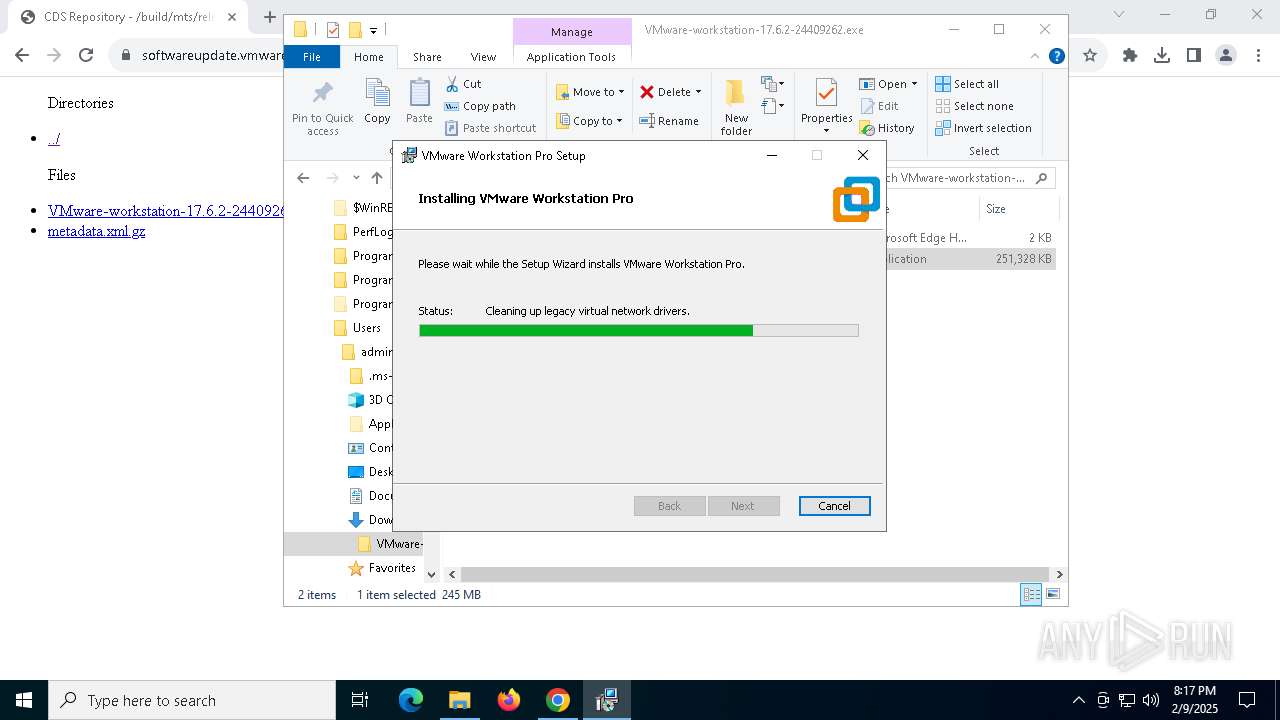
| URL: | https://softwareupdate.vmware.com/cds/vmw-desktop/ws/17.6.2/24409262/windows/ |
| Full analysis: | https://app.any.run/tasks/8edc9348-94e4-464a-b570-a147063a57b9 |
| Verdict: | Malicious activity |
| Analysis date: | February 09, 2025, 20:12:31 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 994124C539801BCA8792B9415AF895B6 |
| SHA1: | 5A6E294BF395F4BA5D61A6BA83462045E498F934 |
| SHA256: | 5E9BB1352DEDE6728C01A1AC3E01D65C635082C8933959AA07157E6764CCA5C5 |
| SSDEEP: | 3:N8HlL+AZ2BWKTo+OKSWdBRwTXKSaKQ:22BWmOcwbKSaKQ |
MALICIOUS
Changes the autorun value in the registry
- VC_redist.x86.exe (PID: 6964)
- VC_redist.x64.exe (PID: 5892)
- msiexec.exe (PID: 6932)
Reads a specific registry key of the VM
- vnetlib64.exe (PID: 2676)
- vnetlib64.exe (PID: 4336)
- msiexec.exe (PID: 5720)
- vnetlib64.exe (PID: 4392)
- msiexec.exe (PID: 6932)
- vnetlib64.exe (PID: 2216)
- vnetlib64.exe (PID: 5200)
- msiexec.exe (PID: 2976)
- vnetlib64.exe (PID: 732)
- vnetlib64.exe (PID: 2168)
- vnetlib64.exe (PID: 6740)
- vnetlib64.exe (PID: 4512)
- vnetlib64.exe (PID: 5208)
- vnetlib64.exe (PID: 3896)
- vnetlib64.exe (PID: 364)
- vnetlib64.exe (PID: 6836)
- vnetlib64.exe (PID: 3936)
- vnetlib64.exe (PID: 424)
- vnetlib64.exe (PID: 4520)
- vnetlib64.exe (PID: 4468)
- vnetlib64.exe (PID: 2144)
- vnetlib64.exe (PID: 7016)
- vnetlib64.exe (PID: 1224)
- vnetlib64.exe (PID: 6096)
- vnetlib64.exe (PID: 2828)
- vnetlib64.exe (PID: 5316)
- vnetlib64.exe (PID: 3568)
- vnetlib64.exe (PID: 4864)
- vnetlib64.exe (PID: 4548)
- vmnat.exe (PID: 1852)
- vnetlib64.exe (PID: 3724)
- vnetlib64.exe (PID: 5008)
- vnetlib64.exe (PID: 7196)
- vnetlib64.exe (PID: 7520)
- msiexec.exe (PID: 7012)
SUSPICIOUS
Process drops legitimate windows executable
- VMware-workstation-17.6.2-24409262.exe (PID: 1916)
- vcredist_x86.exe (PID: 5300)
- vcredist_x86.exe (PID: 3612)
- vcredist_x64.exe (PID: 1140)
- vcredist_x64.exe (PID: 3420)
- msiexec.exe (PID: 7012)
- msiexec.exe (PID: 6932)
Executable content was dropped or overwritten
- vcredist_x86.exe (PID: 3612)
- VMware-workstation-17.6.2-24409262.exe (PID: 1916)
- vcredist_x86.exe (PID: 5300)
- vcredist_x64.exe (PID: 1140)
- vcredist_x64.exe (PID: 3420)
- drvinst.exe (PID: 5864)
- vnetlib64.exe (PID: 4864)
- vnetlib64.exe (PID: 7520)
- drvinst.exe (PID: 7604)
Starts a Microsoft application from unusual location
- vcredist_x86.exe (PID: 3612)
- vcredist_x86.exe (PID: 5300)
- VC_redist.x86.exe (PID: 6964)
- vcredist_x64.exe (PID: 1140)
- vcredist_x64.exe (PID: 3420)
- VC_redist.x64.exe (PID: 5892)
Reads security settings of Internet Explorer
- vcredist_x86.exe (PID: 5300)
- vcredist_x64.exe (PID: 3420)
- VMware-workstation-17.6.2-24409262.exe (PID: 1916)
Searches for installed software
- vcredist_x86.exe (PID: 5300)
- dllhost.exe (PID: 3744)
- vcredist_x64.exe (PID: 3420)
Starts itself from another location
- vcredist_x86.exe (PID: 5300)
- vcredist_x64.exe (PID: 3420)
Executes as Windows Service
- VSSVC.exe (PID: 3536)
- vmnat.exe (PID: 1852)
- vmnetdhcp.exe (PID: 5208)
- vmware-usbarbitrator64.exe (PID: 7808)
Reads the Windows owner or organization settings
- VMware-workstation-17.6.2-24409262.exe (PID: 1916)
- msiexec.exe (PID: 6932)
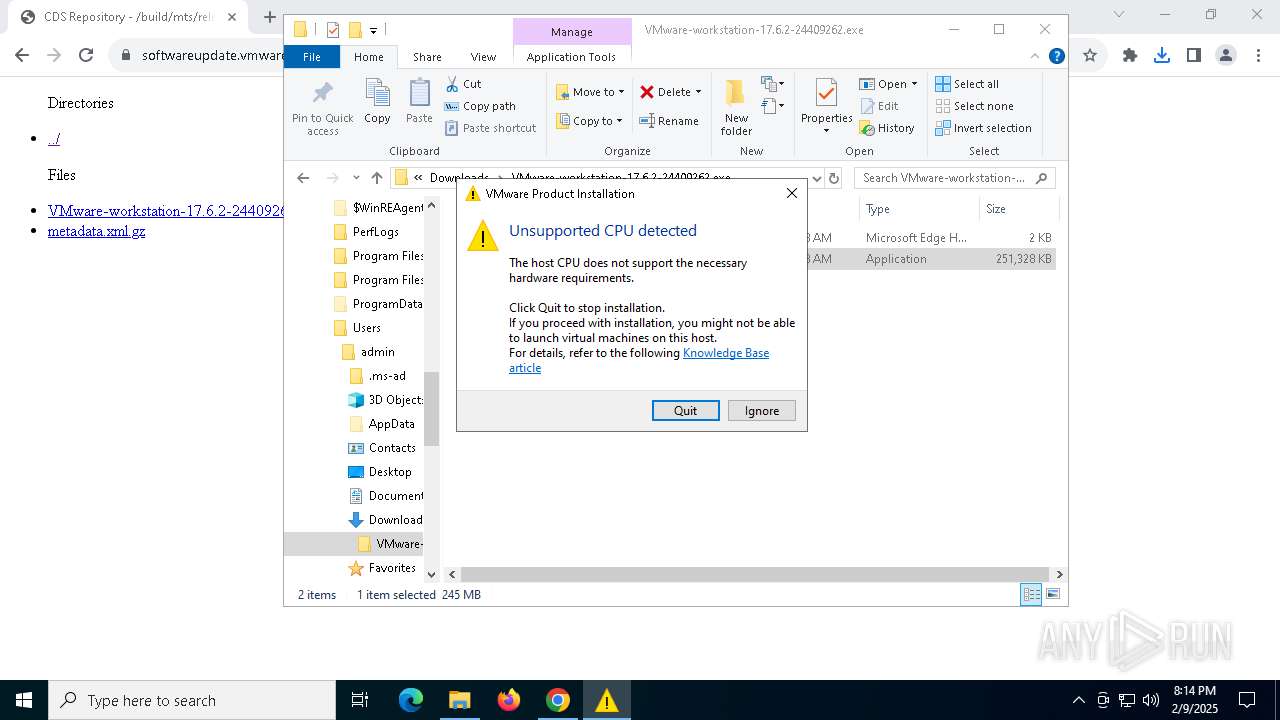
Executes application which crashes
- msiexec.exe (PID: 2120)
Process checks presence of unattended files
- VMware-workstation-17.6.2-24409262.exe (PID: 1916)
- msiexec.exe (PID: 6932)
Checks Windows Trust Settings
- VMware-workstation-17.6.2-24409262.exe (PID: 1916)
- msiexec.exe (PID: 6932)
- drvinst.exe (PID: 5864)
- vnetlib64.exe (PID: 4864)
- drvinst.exe (PID: 1172)
- drvinst.exe (PID: 6016)
- vnetlib64.exe (PID: 7520)
- msiexec.exe (PID: 7012)
- vnetlib64.exe (PID: 4548)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 6932)
- drvinst.exe (PID: 5864)
- vnetlib64.exe (PID: 4864)
- vnetlib64.exe (PID: 7520)
- drvinst.exe (PID: 7604)
- msiexec.exe (PID: 7012)
The process checks if it is being run in the virtual environment
- vnetlib64.exe (PID: 2676)
- vnetlib64.exe (PID: 5316)
- msiexec.exe (PID: 2976)
- drvinst.exe (PID: 1172)
- vnetlib64.exe (PID: 3568)
- vnetlib64.exe (PID: 4548)
- drvinst.exe (PID: 3128)
- vnetlib64.exe (PID: 7520)
Drops 7-zip archiver for unpacking
- msiexec.exe (PID: 6932)
Creates files in the driver directory
- drvinst.exe (PID: 5864)
- vnetlib64.exe (PID: 4864)
- drvinst.exe (PID: 1172)
- vnetlib64.exe (PID: 3568)
- vnetlib64.exe (PID: 4548)
- vnetlib64.exe (PID: 5008)
- drvinst.exe (PID: 6016)
- vnetlib64.exe (PID: 7520)
Creates or modifies Windows services
- vnetlib64.exe (PID: 4864)
- vnetlib64.exe (PID: 3568)
- vnetlib64.exe (PID: 4548)
- drvinst.exe (PID: 3128)
- drvinst.exe (PID: 7224)
Creates/Modifies COM task schedule object
- vnetlib64.exe (PID: 3568)
INFO
Manual execution by a user
- VMware-workstation-17.6.2-24409262.exe (PID: 4648)
- WinRAR.exe (PID: 5864)
- VMware-workstation-17.6.2-24409262.exe (PID: 1512)
- VMware-workstation-17.6.2-24409262.exe (PID: 1916)
- VMware-workstation-17.6.2-24409262.exe (PID: 6156)
- WinRAR.exe (PID: 6216)
Application launched itself
- chrome.exe (PID: 6352)
- msiexec.exe (PID: 6932)
Checks supported languages
- VMware-workstation-17.6.2-24409262.exe (PID: 1512)
- vcredist_x86.exe (PID: 3612)
- VMware-workstation-17.6.2-24409262.exe (PID: 1916)
- vcredist_x86.exe (PID: 5300)
- VC_redist.x86.exe (PID: 6964)
- vcredist_x64.exe (PID: 1140)
- vcredist_x64.exe (PID: 3420)
- msiexec.exe (PID: 6932)
- msiexec.exe (PID: 2120)
- msiexec.exe (PID: 1480)
- msiexec.exe (PID: 5720)
- msiexec.exe (PID: 4684)
- msiexec.exe (PID: 2976)
- msiexec.exe (PID: 7012)
- vnetlib64.exe (PID: 2676)
- vnetlib64.exe (PID: 4336)
- vnetlib64.exe (PID: 4864)
- VC_redist.x64.exe (PID: 5892)
- vnetlib64.exe (PID: 4392)
- vnetlib64.exe (PID: 5200)
- vnetlib64.exe (PID: 732)
- vnetlib64.exe (PID: 2168)
- vnetlib64.exe (PID: 3724)
- vnetlib64.exe (PID: 4512)
- vnetlib64.exe (PID: 6740)
- vnetlib64.exe (PID: 5208)
- vnetlib64.exe (PID: 364)
- vnetlib64.exe (PID: 3896)
- vnetlib64.exe (PID: 6836)
- vnetlib64.exe (PID: 424)
- vnetlib64.exe (PID: 3936)
- vnetlib64.exe (PID: 6096)
- vnetlib64.exe (PID: 4520)
- vnetlib64.exe (PID: 4468)
- vnetlib64.exe (PID: 2144)
- vnetlib64.exe (PID: 1224)
- vnetlib64.exe (PID: 7016)
- vnetlib64.exe (PID: 2828)
- vnetlib64.exe (PID: 5316)
- vnetlib64.exe (PID: 3568)
- drvinst.exe (PID: 1172)
- vnetlib64.exe (PID: 4548)
- drvinst.exe (PID: 5864)
- vmnetdhcp.exe (PID: 5208)
- vmnat.exe (PID: 1852)
- vnetlib64.exe (PID: 5008)
- drvinst.exe (PID: 6016)
- vnetlib64.exe (PID: 2216)
- drvinst.exe (PID: 3128)
- vnetlib64.exe (PID: 7196)
- drvinst.exe (PID: 7224)
- vnetlib64.exe (PID: 7520)
Create files in a temporary directory
- VMware-workstation-17.6.2-24409262.exe (PID: 1512)
- VMware-workstation-17.6.2-24409262.exe (PID: 1916)
- vcredist_x86.exe (PID: 5300)
- vcredist_x64.exe (PID: 3420)
- msiexec.exe (PID: 7012)
The sample compiled with english language support
- VMware-workstation-17.6.2-24409262.exe (PID: 1916)
- vcredist_x86.exe (PID: 3612)
- vcredist_x86.exe (PID: 5300)
- vcredist_x64.exe (PID: 3420)
- vcredist_x64.exe (PID: 1140)
- chrome.exe (PID: 4336)
- chrome.exe (PID: 4500)
- msiexec.exe (PID: 6932)
- msiexec.exe (PID: 7012)
- drvinst.exe (PID: 5864)
- vnetlib64.exe (PID: 4864)
- vnetlib64.exe (PID: 7520)
- drvinst.exe (PID: 7604)
Reads the computer name
- VMware-workstation-17.6.2-24409262.exe (PID: 1512)
- VMware-workstation-17.6.2-24409262.exe (PID: 1916)
- vcredist_x86.exe (PID: 5300)
- VC_redist.x86.exe (PID: 6964)
- vcredist_x64.exe (PID: 3420)
- VC_redist.x64.exe (PID: 5892)
- msiexec.exe (PID: 6932)
- msiexec.exe (PID: 2120)
- msiexec.exe (PID: 1480)
- msiexec.exe (PID: 5720)
- msiexec.exe (PID: 4684)
- msiexec.exe (PID: 2976)
- vnetlib64.exe (PID: 2676)
- vnetlib64.exe (PID: 4336)
- drvinst.exe (PID: 5864)
- vnetlib64.exe (PID: 4864)
- vnetlib64.exe (PID: 2216)
- vnetlib64.exe (PID: 4392)
- vnetlib64.exe (PID: 5200)
- vnetlib64.exe (PID: 732)
- vnetlib64.exe (PID: 4512)
- vnetlib64.exe (PID: 3724)
- vnetlib64.exe (PID: 2168)
- vnetlib64.exe (PID: 6740)
- msiexec.exe (PID: 7012)
- vnetlib64.exe (PID: 3896)
- vnetlib64.exe (PID: 364)
- vnetlib64.exe (PID: 6836)
- vnetlib64.exe (PID: 424)
- vnetlib64.exe (PID: 3936)
- vnetlib64.exe (PID: 5208)
- vnetlib64.exe (PID: 4520)
- vnetlib64.exe (PID: 6096)
- vnetlib64.exe (PID: 4468)
- vnetlib64.exe (PID: 2144)
- vnetlib64.exe (PID: 1224)
- vnetlib64.exe (PID: 7016)
- vnetlib64.exe (PID: 2828)
- vnetlib64.exe (PID: 5316)
- vnetlib64.exe (PID: 3568)
- drvinst.exe (PID: 1172)
- vnetlib64.exe (PID: 4548)
- vmnat.exe (PID: 1852)
- vmnetdhcp.exe (PID: 5208)
- drvinst.exe (PID: 6016)
- drvinst.exe (PID: 3128)
- vnetlib64.exe (PID: 7520)
- drvinst.exe (PID: 7224)
- vnetlib64.exe (PID: 5008)
- vnetlib64.exe (PID: 7196)
Manages system restore points
- SrTasks.exe (PID: 4244)
- SrTasks.exe (PID: 6004)
- SrTasks.exe (PID: 7004)
Process checks computer location settings
- vcredist_x86.exe (PID: 5300)
- vcredist_x64.exe (PID: 3420)
Reads the machine GUID from the registry
- VMware-workstation-17.6.2-24409262.exe (PID: 1916)
- msiexec.exe (PID: 2976)
- drvinst.exe (PID: 5864)
- vnetlib64.exe (PID: 4864)
- msiexec.exe (PID: 6932)
- drvinst.exe (PID: 1172)
- vnetlib64.exe (PID: 4548)
- drvinst.exe (PID: 6016)
- vnetlib64.exe (PID: 7520)
- msiexec.exe (PID: 7012)
Creates files or folders in the user directory
- VMware-workstation-17.6.2-24409262.exe (PID: 1916)
- WerFault.exe (PID: 5968)
Checks proxy server information
- VMware-workstation-17.6.2-24409262.exe (PID: 1916)
Reads the software policy settings
- VMware-workstation-17.6.2-24409262.exe (PID: 1916)
- msiexec.exe (PID: 6932)
- drvinst.exe (PID: 5864)
- vnetlib64.exe (PID: 4864)
- vnetlib64.exe (PID: 4548)
- drvinst.exe (PID: 1172)
- drvinst.exe (PID: 6016)
- vnetlib64.exe (PID: 7520)
- msiexec.exe (PID: 7012)
Creates files in the program directory
- VMware-workstation-17.6.2-24409262.exe (PID: 1916)
- vmnat.exe (PID: 1852)
- vmnetdhcp.exe (PID: 5208)
Executable content was dropped or overwritten
- chrome.exe (PID: 4336)
- chrome.exe (PID: 4500)
- msiexec.exe (PID: 6932)
- msiexec.exe (PID: 7012)
- msiexec.exe (PID: 2976)
Creates a software uninstall entry
- msiexec.exe (PID: 6932)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
238
Monitored processes
91
Malicious processes
19
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 364 | "C:\Program Files (x86)\VMware\VMware Workstation\vnetlib64.exe" -- remove adapter vmnet10 | C:\Program Files (x86)\VMware\VMware Workstation\vnetlib64.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: VMware, Inc. Integrity Level: SYSTEM Description: VMware network install library executable Exit code: 4 Version: 17.6.2 build-24409262 Modules
| |||||||||||||||
| 424 | "C:\Program Files (x86)\VMware\VMware Workstation\vnetlib64.exe" -- remove adapter vmnet12 | C:\Program Files (x86)\VMware\VMware Workstation\vnetlib64.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: VMware, Inc. Integrity Level: SYSTEM Description: VMware network install library executable Exit code: 4 Version: 17.6.2 build-24409262 Modules
| |||||||||||||||
| 624 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5212 --field-trial-handle=1936,i,15458221282030508450,2067445989120076214,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 624 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | "C:\Program Files (x86)\VMware\VMware Workstation\vnetlib64.exe" -- remove adapter vmnet3 | C:\Program Files (x86)\VMware\VMware Workstation\vnetlib64.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: VMware, Inc. Integrity Level: SYSTEM Description: VMware network install library executable Exit code: 4 Version: 17.6.2 build-24409262 Modules
| |||||||||||||||
| 1140 | "C:\Users\admin\AppData\Local\Temp\{1D6AA927-3BE5-4104-BA3D-78382FDFF732}~setup\vcredist_x64.exe" /Q /norestart | C:\Users\admin\AppData\Local\Temp\{1D6AA927-3BE5-4104-BA3D-78382FDFF732}~setup\vcredist_x64.exe | VMware-workstation-17.6.2-24409262.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2015-2022 Redistributable (x64) - 14.36.32532 Exit code: 0 Version: 14.36.32532.0 Modules
| |||||||||||||||
| 1172 | DrvInst.exe "4" "1" "C:\Program Files (x86)\VMware\VMware Workstation\netbridge.inf" "9" "498636d73" "0000000000000204" "WinSta0\Default" "0000000000000208" "208" "C:\Program Files (x86)\VMware\VMware Workstation" | C:\Windows\System32\drvinst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1224 | "C:\Program Files (x86)\VMware\VMware Workstation\vnetlib64.exe" -- remove adapter vmnet18 | C:\Program Files (x86)\VMware\VMware Workstation\vnetlib64.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: VMware, Inc. Integrity Level: SYSTEM Description: VMware network install library executable Exit code: 4 Version: 17.6.2 build-24409262 Modules
| |||||||||||||||
| 1460 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5708 --field-trial-handle=1936,i,15458221282030508450,2067445989120076214,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1480 | C:\Windows\System32\MsiExec.exe -Embedding F47EEC7E016F95F1447C2593F4967F11 C | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
67 878
Read events
66 388
Write events
1 396
Delete events
94
Modification events
| (PID) Process: | (6352) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6352) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6352) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6352) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (1612) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000B27D86232F7BDB01 | |||
| (PID) Process: | (5864) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (5864) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (5864) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (5864) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Downloads\VMware-workstation-17.6.2-24409262.exe.tar | |||
| (PID) Process: | (5864) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
Executable files
242
Suspicious files
569
Text files
336
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6352 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF137b9c.TMP | — | |
MD5:— | SHA256:— | |||
| 6352 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6352 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF137b9c.TMP | — | |
MD5:— | SHA256:— | |||
| 6352 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF137bab.TMP | — | |
MD5:— | SHA256:— | |||
| 6352 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF137b9c.TMP | — | |
MD5:— | SHA256:— | |||
| 6352 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6352 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6352 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6352 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF137bab.TMP | — | |
MD5:— | SHA256:— | |||
| 6352 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF137bab.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
44
TCP/UDP connections
49
DNS requests
40
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1176 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7124 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjhkYWYwZDctOTExOS00MGQ5LTgyNjAtN2FlY2ZjMDg0NmNj/1.0.0.17_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
7124 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adrga7eefaxjfdmmgfkiaxjg4yjq_2024.7.12.235938/eeigpngbgcognadeebkilcpcaedhellh_2024.07.12.235938_all_a6r64uyugl6fjh3lupjqo6w7ai.crx3 | unknown | — | — | whitelisted |
4976 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7124 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adrga7eefaxjfdmmgfkiaxjg4yjq_2024.7.12.235938/eeigpngbgcognadeebkilcpcaedhellh_2024.07.12.235938_all_a6r64uyugl6fjh3lupjqo6w7ai.crx3 | unknown | — | — | whitelisted |
7124 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/adrga7eefaxjfdmmgfkiaxjg4yjq_2024.7.12.235938/eeigpngbgcognadeebkilcpcaedhellh_2024.07.12.235938_all_a6r64uyugl6fjh3lupjqo6w7ai.crx3 | unknown | — | — | whitelisted |
7124 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | — | — | whitelisted |
7124 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvYjhkYWYwZDctOTExOS00MGQ5LTgyNjAtN2FlY2ZjMDg0NmNj/1.0.0.17_llkgjffcdpffmhiakmfcdcblohccpfmo.crx | unknown | — | — | whitelisted |
7124 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | unknown | — | — | whitelisted |
7124 | svchost.exe | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ongefacmyvngvcidcat6p3ofwa_1219/efniojlnjndmcbiieegkicadnoecjjef_1219_all_acjh4pdvfd32tac4b2qvbli7sxka.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.31.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 104.126.37.147:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
1076 | svchost.exe | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 172.66.0.165:443 | softwareupdate.vmware.com | — | US | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
— | — | 172.217.218.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
softwareupdate.vmware.com |
| whitelisted |
accounts.google.com |
| whitelisted |
www.google.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
VMware-workstation-17.6.2-24409262.exe | Start Pre-load DLLs.
|
VMware-workstation-17.6.2-24409262.exe | Start Pre-load DLLs.
|
VMware-workstation-17.6.2-24409262.exe | Win32U_GetFileAttributes: GetFileAttributesExW("C:\Users\admin\Downloads\VMware-workstation-17.6.2-24409262.exe\1033.bmp", ...) failed, error: 2
|
VMware-workstation-17.6.2-24409262.exe | Win32U_GetFileAttributes: GetFileAttributesExW("C:\Users\admin\AppData\Local\Temp\{1D6AA927-3BE5-4104-BA3D-78382FDFF732}~setup\", ...) failed, error: 2
|
vmnat.exe | CodeSet_Init: no ICU
|
vmnetdhcp.exe | CodeSet_Init: no ICU
|