| File name: | startxback.cmd |
| Full analysis: | https://app.any.run/tasks/95581745-2ca6-4af7-9ba2-40de561514d1 |
| Verdict: | Malicious activity |
| Analysis date: | January 01, 2025, 00:41:29 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text |
| MD5: | 4BD0CA5276016A3CA1ACC6B5872F4259 |
| SHA1: | 04B001BA73F4CAD190EF62596B17AC950E796AFE |
| SHA256: | 5E723C959F5A791CF798AA0EFC48CB432B1AFCB0A069D35BDA4E07192E3EF51B |
| SSDEEP: | 48:/mgzquFy07banPRc1H0CHDfsNHmY/nM/VKqPniUskMW7C4OXTzKvuEkuKSyB7Zho:3Fyn5i/rwBnM/VT/iEazz3pZqp |
MALICIOUS
Changes the autorun value in the registry
- ie4uinit.exe (PID: 396)
- explorer.exe (PID: 4576)
Create files in the Startup directory
- explorer.exe (PID: 4576)
SUSPICIOUS
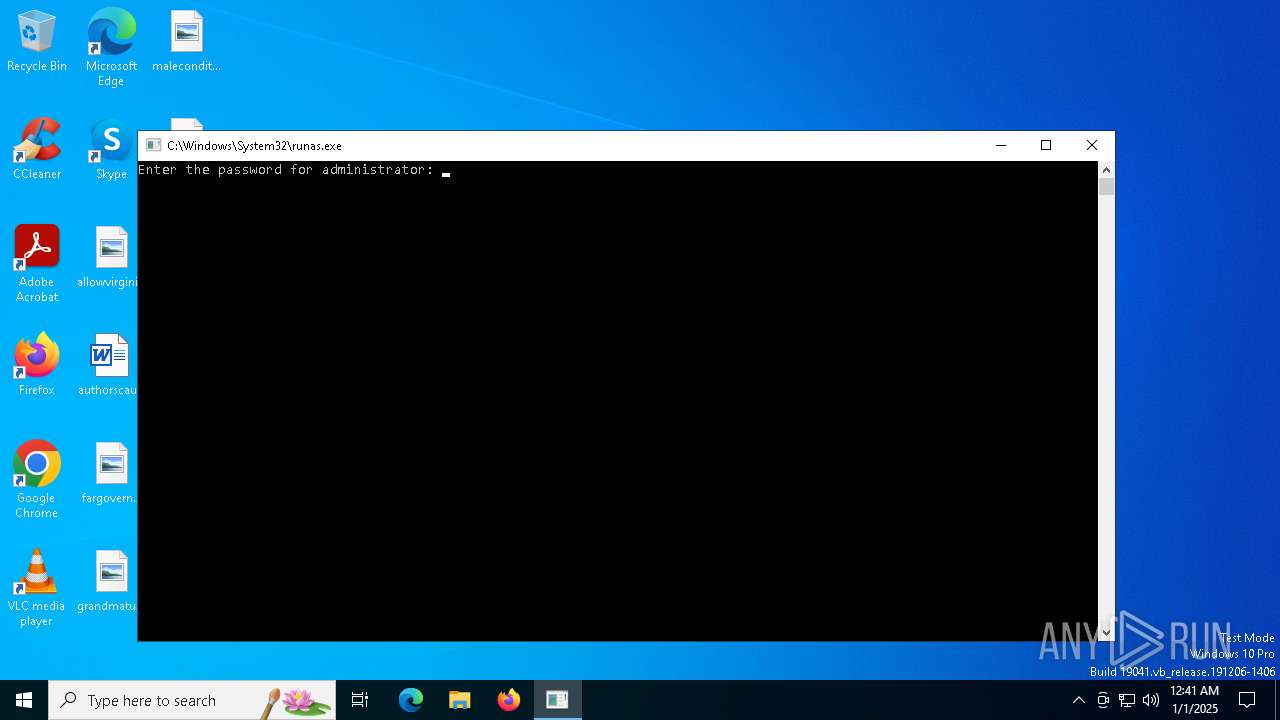
Starts another process probably with elevated privileges via RUNAS.EXE
- runas.exe (PID: 6296)
Executing commands from ".cmd" file
- runas.exe (PID: 6296)
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 6996)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 6996)
Application launched itself
- cmd.exe (PID: 6996)
- ie4uinit.exe (PID: 396)
- setup.exe (PID: 7116)
- setup.exe (PID: 4684)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 6996)
- runas.exe (PID: 6296)
- powershell.exe (PID: 7140)
Executes script without checking the security policy
- powershell.exe (PID: 7140)
Manipulates environment variables
- powershell.exe (PID: 7140)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 6996)
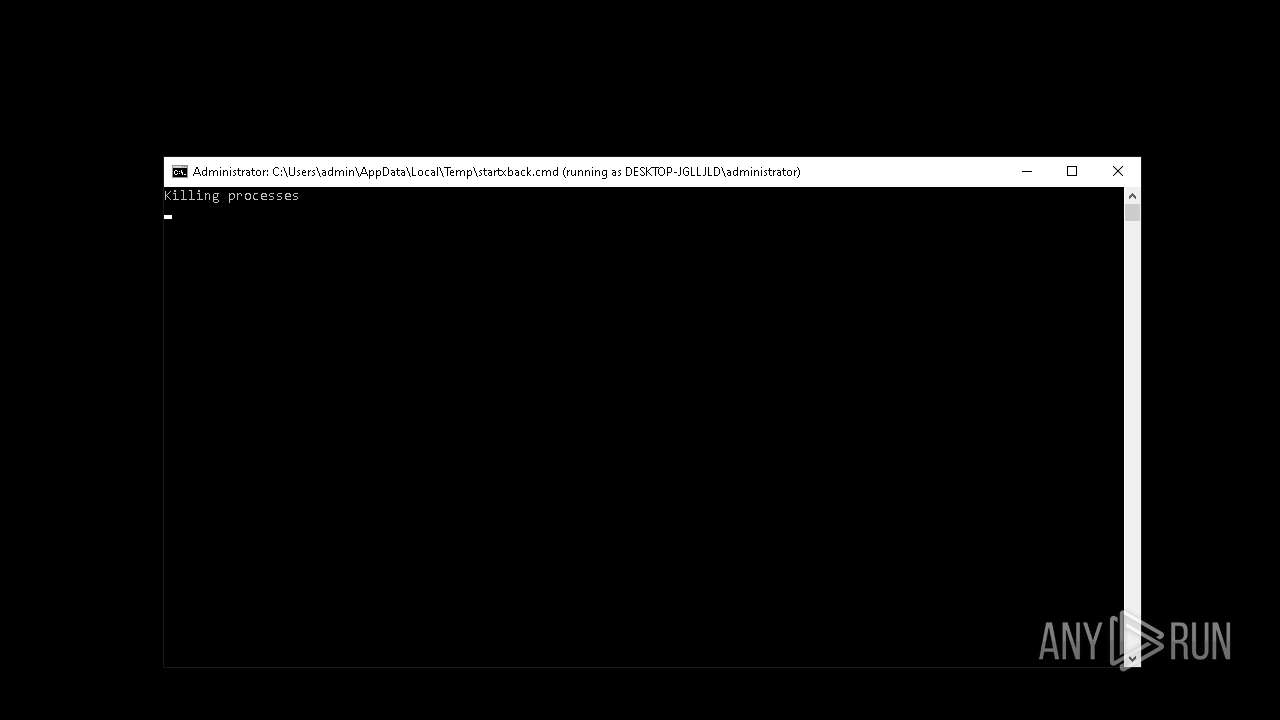
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 6176)
Write to the desktop.ini file (may be used to cloak folders)
- ie4uinit.exe (PID: 396)
- explorer.exe (PID: 4576)
Changes internet zones settings
- ie4uinit.exe (PID: 396)
Uses RUNDLL32.EXE to load library
- ie4uinit.exe (PID: 6004)
INFO
The process uses the downloaded file
- powershell.exe (PID: 7140)
- explorer.exe (PID: 4576)
Reads the time zone
- explorer.exe (PID: 4576)
Reads Microsoft Office registry keys
- explorer.exe (PID: 4576)
- setup.exe (PID: 7116)
Reads security settings of Internet Explorer
- ie4uinit.exe (PID: 396)
- explorer.exe (PID: 4576)
- ie4uinit.exe (PID: 6004)
Local mutex for internet shortcut management
- explorer.exe (PID: 4576)
- ie4uinit.exe (PID: 396)
Reads the software policy settings
- explorer.exe (PID: 4576)
- dllhost.exe (PID: 4856)
Creates files in the program directory
- ie4uinit.exe (PID: 396)
- chrmstp.exe (PID: 6952)
- setup.exe (PID: 4684)
Application launched itself
- chrmstp.exe (PID: 6952)
- chrmstp.exe (PID: 7024)
Checks supported languages
- setup.exe (PID: 6188)
- setup.exe (PID: 7116)
- setup.exe (PID: 4684)
- setup.exe (PID: 2072)
Reads the computer name
- setup.exe (PID: 4684)
Checks transactions between databases Windows and Oracle
- explorer.exe (PID: 4576)
Checks proxy server information
- dllhost.exe (PID: 4856)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
158
Monitored processes
26
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 396 | "C:\Windows\System32\ie4uinit.exe" -UserConfig | C:\Windows\System32\ie4uinit.exe | explorer.exe | ||||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: IE Per-User Initialization Utility Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2072 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\Installer\setup.exe" --type=crashpad-handler /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler --database=C:\WINDOWS\SystemTemp\MsEdgeCrashpad --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=122.0.6261.70 "--annotation=exe=C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\Installer\setup.exe" --annotation=plat=Win64 "--annotation=prod=Microsoft Edge" --annotation=ver=122.0.2365.59 --initial-client-data=0x230,0x260,0x264,0x234,0x268,0x7ff61c6169a8,0x7ff61c6169b4,0x7ff61c6169c0 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\Installer\setup.exe | — | setup.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Installer Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 4576 | "C:\WINDOWS\explorer.exe" | C:\Windows\explorer.exe | powershell.exe | ||||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4684 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\Installer\setup.exe" --msedge --channel=stable --system-level --verbose-logging --installerdata="C:\Program Files (x86)\Microsoft\Edge\Application\master_preferences" --create-shortcuts=1 --install-level=0 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\Installer\setup.exe | — | setup.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Edge Installer Exit code: 99 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 4856 | C:\WINDOWS\system32\DllHost.exe /Processid:{CA8C87C1-929D-45BA-94DB-EF8E6CB346AD} | C:\Windows\System32\dllhost.exe | svchost.exe | ||||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5712 | taskkill /f /im explorer.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5748 | "C:\Windows\System32\unregmp2.exe" /FirstLogon | C:\Windows\System32\unregmp2.exe | — | explorer.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Windows Media Player Setup Utility Exit code: 0 Version: 12.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6004 | C:\Windows\System32\ie4uinit.exe -ClearIconCache | C:\Windows\System32\ie4uinit.exe | — | ie4uinit.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: IE Per-User Initialization Utility Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6072 | "C:\Windows\System32\unregmp2.exe" /FirstLogon | C:\Windows\System32\unregmp2.exe | — | explorer.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Windows Media Player Setup Utility Exit code: 0 Version: 12.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6176 | "C:\WINDOWS\system32\cmd.exe" /c taskkill /f /im explorer.exe | C:\Windows\System32\cmd.exe | — | powershell.exe | |||||||||||
User: Administrator Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
47 866
Read events
47 224
Write events
614
Delete events
28
Modification events
| (PID) Process: | (4576) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | ExplorerStartupTraceRecorded |
Value: 1 | |||
| (PID) Process: | (4576) explorer.exe | Key: | HKEY_CURRENT_USER\Control Panel\Appearance |
| Operation: | write | Name: | SchemeLangID |
Value: 0904 | |||
| (PID) Process: | (4576) explorer.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop\WindowMetrics |
| Operation: | write | Name: | AppliedDPI |
Value: 96 | |||
| (PID) Process: | (4576) explorer.exe | Key: | HKEY_CURRENT_USER\Control Panel\Desktop\WindowMetrics |
| Operation: | write | Name: | Shell Icon Size |
Value: 32 | |||
| (PID) Process: | (4576) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.bat\OpenWithProgids |
| Operation: | write | Name: | batfile |
Value: | |||
| (PID) Process: | (4576) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.bmp\OpenWithProgids |
| Operation: | write | Name: | Paint.Picture |
Value: | |||
| (PID) Process: | (4576) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.db\OpenWithProgids |
| Operation: | write | Name: | dbfile |
Value: | |||
| (PID) Process: | (4576) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.dib\OpenWithProgids |
| Operation: | write | Name: | Paint.Picture |
Value: | |||
| (PID) Process: | (4576) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.dll\OpenWithProgids |
| Operation: | write | Name: | dllfile |
Value: | |||
| (PID) Process: | (4576) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.doc\OpenWithProgids |
| Operation: | write | Name: | Word.Document.8 |
Value: | |||
Executable files
7
Suspicious files
29
Text files
57
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 396 | ie4uinit.exe | C:\Users\Administrator\AppData\Local\Temp\RGI8205.tmp | ini | |
MD5:0D6E3B5966C8910612CBB86683829EFD | SHA256:6B5C97558FDF8CC87169CAD942F04A633BF2B9931D50BF22D91E632C0EA596AF | |||
| 396 | ie4uinit.exe | C:\Users\Administrator\AppData\Local\Temp\RGI81F5.tmp | text | |
MD5:0D6E3B5966C8910612CBB86683829EFD | SHA256:6B5C97558FDF8CC87169CAD942F04A633BF2B9931D50BF22D91E632C0EA596AF | |||
| 396 | ie4uinit.exe | C:\Users\Administrator\AppData\Local\Microsoft\Internet Explorer\IECompatData\iecompatdata.xml | xml | |
MD5:4FB9EF95197331833AEC896BEABBBE64 | SHA256:C5FB79289E4120352C3D011EA7CD3D52EBE3498437CFD6B14FE40506E7D3B94E | |||
| 7140 | powershell.exe | C:\Users\Administrator\AppData\Local\Temp\__PSScriptPolicyTest_ra52eyvh.clq.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5748 | unregmp2.exe | C:\Users\Administrator\AppData\Local\Temp\wmsetup.log | text | |
MD5:9239E2F1A5D8AE40A2372B52EE7BB834 | SHA256:04CFBE94284F9118B83F67937A0347A01EAC34C1C0B26BB9A9FEEF143CC15FE7 | |||
| 4576 | explorer.exe | C:\Users\Administrator\AppData\Roaming\Microsoft\Windows\Libraries\~usic.tmp | xml | |
MD5:0A67BFBF08799A9125CE554276B3B29A | SHA256:A10926F744E9998D4050756324191F02DAF22C969BA6FD4F415DDE90C5835125 | |||
| 396 | ie4uinit.exe | C:\Users\Administrator\AppData\Local\Microsoft\Internet Explorer\ie4uinit-UserConfig.log | text | |
MD5:C8D430CCC9C1DDEDF995B398B259F94C | SHA256:C3107ABE74BDF1344557735365DCC9EF555EC370C57170F01F28F583D0B577EE | |||
| 396 | ie4uinit.exe | C:\Users\Administrator\Favorites\Bing.url | text | |
MD5:1E7E5E93C2A5AADAF932F93D25C57F3E | SHA256:8B94D04FECE582E4182E8E73F46FB86EB8E965C69C526C42805ABB9E43641E35 | |||
| 396 | ie4uinit.exe | C:\Users\Administrator\Favorites\Links\desktop.ini | text | |
MD5:3C106F431417240DA12FD827323B7724 | SHA256:E469ED17B4B54595B335DC51817A52B81FCF13AAD7B7B994626F84EC097C5D57 | |||
| 4576 | explorer.exe | C:\Users\Administrator\AppData\Roaming\Microsoft\Windows\Libraries\Music.library-ms | xml | |
MD5:0A67BFBF08799A9125CE554276B3B29A | SHA256:A10926F744E9998D4050756324191F02DAF22C969BA6FD4F415DDE90C5835125 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
28
DNS requests
10
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4856 | dllhost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4856 | dllhost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2380 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 92.123.104.32:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| unknown |