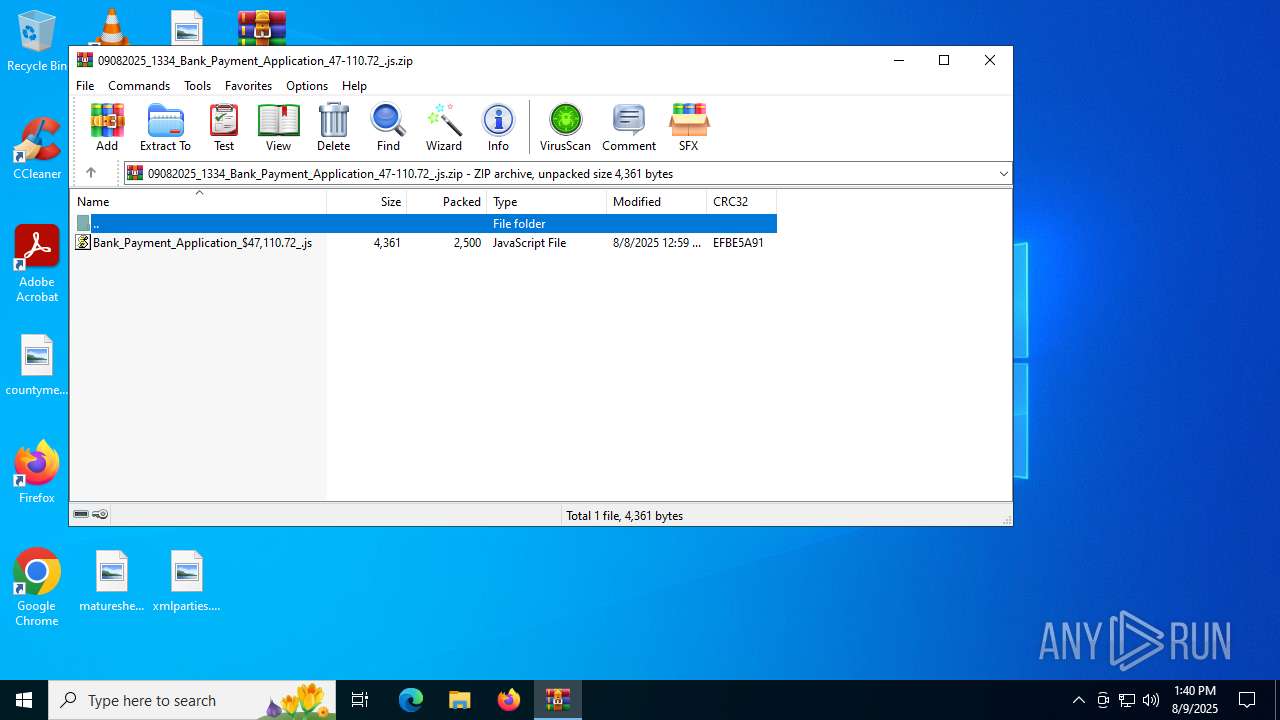
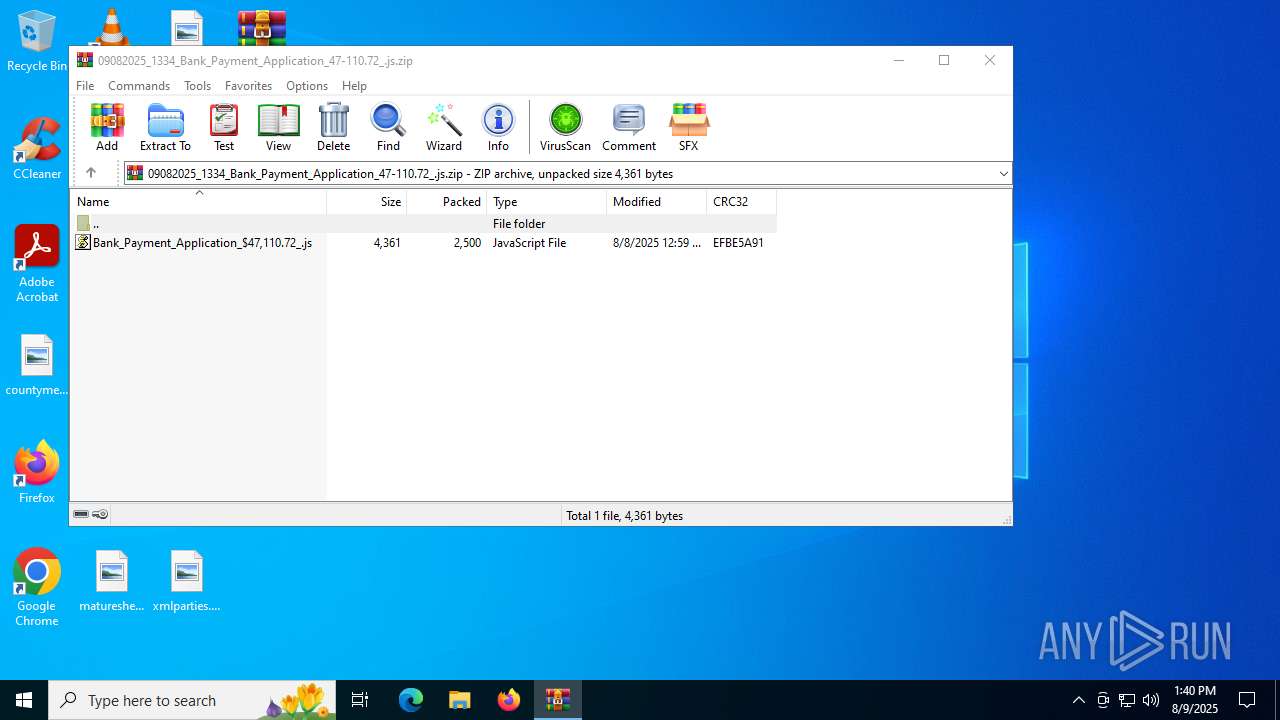
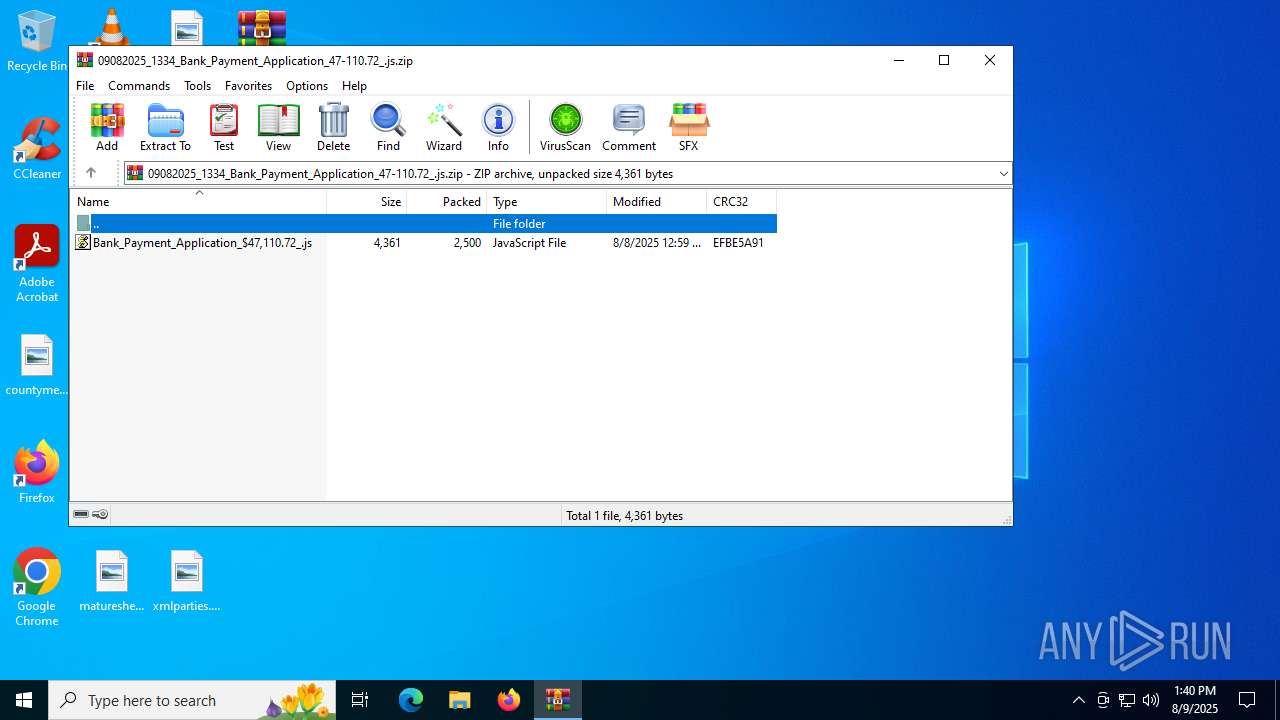
| File name: | 09082025_1334_Bank_Payment_Application_47-110.72_.js.zip |
| Full analysis: | https://app.any.run/tasks/03613c00-d518-4d84-a6f9-fd490b1ba250 |
| Verdict: | Malicious activity |
| Analysis date: | August 09, 2025, 13:39:52 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 184E36581D31061A5CA02CAC6890B4E6 |
| SHA1: | E45F04149A1325A3539BEC65082C099C3D3B6B71 |
| SHA256: | 5E7097D3638F6470213C7BDCD40902AF4F341AA7FBF691B0044FF7FAE4DBAA0B |
| SSDEEP: | 96:fzEiyhINHxHkgJWGLDEVmbmw8tFSxGzWYVtkCp:fgiAI9BntLDsmTycRY/ |
MALICIOUS
Accesses environment variables (SCRIPT)
- wscript.exe (PID: 1980)
Generic archive extractor
- WinRAR.exe (PID: 3148)
Creates internet connection object (SCRIPT)
- wscript.exe (PID: 1980)
Sends HTTP request (SCRIPT)
- wscript.exe (PID: 1980)
Gets TEMP folder path (SCRIPT)
- wscript.exe (PID: 1980)
Opens an HTTP connection (SCRIPT)
- wscript.exe (PID: 1980)
Checks whether a specified folder exists (SCRIPT)
- wscript.exe (PID: 1980)
Creates a new folder (SCRIPT)
- wscript.exe (PID: 1980)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 1980)
SUSPICIOUS
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 1980)
Creates a Stream, which may work with files, input/output devices, pipes, or TCP/IP sockets (SCRIPT)
- wscript.exe (PID: 1980)
Writes binary data to a Stream object (SCRIPT)
- wscript.exe (PID: 1980)
Creates a Folder object (SCRIPT)
- wscript.exe (PID: 1980)
Saves data to a binary file (SCRIPT)
- wscript.exe (PID: 1980)
Executable content was dropped or overwritten
- wscript.exe (PID: 1980)
Runs shell command (SCRIPT)
- wscript.exe (PID: 1980)
Executes application which crashes
- RegAsm.exe (PID: 4884)
- RegAsm.exe (PID: 632)
INFO
Checks proxy server information
- wscript.exe (PID: 1980)
- WerFault.exe (PID: 2972)
- WerFault.exe (PID: 1096)
- slui.exe (PID: 4836)
Manual execution by a user
- wscript.exe (PID: 1980)
- STEIN.exe (PID: 5012)
Checks supported languages
- 8urRPdE.exe (PID: 6812)
- STEIN.exe (PID: 5012)
- RegAsm.exe (PID: 4884)
- RegAsm.exe (PID: 632)
Reads the computer name
- 8urRPdE.exe (PID: 6812)
- RegAsm.exe (PID: 4884)
- STEIN.exe (PID: 5012)
- RegAsm.exe (PID: 632)
Reads the machine GUID from the registry
- 8urRPdE.exe (PID: 6812)
- STEIN.exe (PID: 5012)
Reads the software policy settings
- WerFault.exe (PID: 2972)
- WerFault.exe (PID: 1096)
- slui.exe (PID: 4836)
Creates files or folders in the user directory
- WerFault.exe (PID: 2972)
- WerFault.exe (PID: 1096)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:08:08 01:59:52 |
| ZipCRC: | 0xefbe5a91 |
| ZipCompressedSize: | 2500 |
| ZipUncompressedSize: | 4361 |
| ZipFileName: | Bank_Payment_Application_$47,110.72_.js |
Total processes
143
Monitored processes
10
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | STEIN.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 3221225477 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 1096 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 632 -s 812 | C:\Windows\SysWOW64\WerFault.exe | RegAsm.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1980 | "C:\Windows\System32\WScript.exe" C:\Users\admin\Desktop\Bank_Payment_Application_$47,110.72_.js | C:\Windows\System32\wscript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 2200 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2972 | C:\WINDOWS\SysWOW64\WerFault.exe -u -p 4884 -s 860 | C:\Windows\SysWOW64\WerFault.exe | RegAsm.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3148 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\09082025_1334_Bank_Payment_Application_47-110.72_.js.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4836 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4884 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | 8urRPdE.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Assembly Registration Utility Exit code: 3221225477 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 5012 | "C:\Users\admin\Desktop\STEIN.exe" | C:\Users\admin\Desktop\STEIN.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 6812 | "C:\Users\admin\AppData\Local\Temp\YiY8ke\8urRPdE.exe" | C:\Users\admin\AppData\Local\Temp\YiY8ke\8urRPdE.exe | — | wscript.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
Total events
23 334
Read events
23 324
Write events
10
Delete events
0
Modification events
| (PID) Process: | (3148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3148) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\09082025_1334_Bank_Payment_Application_47-110.72_.js.zip | |||
| (PID) Process: | (1980) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1980) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1980) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1980) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings\Telemetry\wscript.exe |
| Operation: | write | Name: | JScriptSetScriptStateStarted |
Value: E5FA180000000000 | |||
Executable files
2
Suspicious files
4
Text files
4
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2972 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_RegAsm.exe_caa62fbecbf82d39b04ededb9c09d954ce930eb_8b3461a9_35ec556c-11ba-4043-80bc-50d7a85145b3\Report.wer | — | |
MD5:— | SHA256:— | |||
| 2972 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\RegAsm.exe.4884.dmp | — | |
MD5:— | SHA256:— | |||
| 1096 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportQueue\AppCrash_RegAsm.exe_caa62fbecbf82d39b04ededb9c09d954ce930eb_8b3461a9_6fce29cf-0796-4f6a-afa2-6c7e77cfcd55\Report.wer | — | |
MD5:— | SHA256:— | |||
| 1096 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\RegAsm.exe.632.dmp | — | |
MD5:— | SHA256:— | |||
| 2972 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERFDF3.tmp.dmp | binary | |
MD5:8DA94CD8CC95FC3E846D4A8CFCBC07CD | SHA256:B40F1B90B7A9B3C16CEC1492579749A1FBEFC58DFCCD5314D5CBAC343CB2EC72 | |||
| 1980 | wscript.exe | C:\Users\admin\AppData\Local\Temp\YiY8ke\8urRPdE.exe | executable | |
MD5:28346CA79CAC92228739D18C6E0BE8CD | SHA256:69FDE004D3896C5C5523E296F7031F5550080FCB739FD2C0D71E99B71F75F8FB | |||
| 1980 | wscript.exe | C:\Users\admin\AppData\Local\Temp\YiY8ke\STEIN.exe | executable | |
MD5:28346CA79CAC92228739D18C6E0BE8CD | SHA256:69FDE004D3896C5C5523E296F7031F5550080FCB739FD2C0D71E99B71F75F8FB | |||
| 2972 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WERFEC0.tmp.xml | xml | |
MD5:3739F126E09BB68435BE018FB2F8314C | SHA256:D5BF98C76B16AFF01B1646EF19FDEA5B2BECF42DE9A14390407A4DFFC5EDD3A2 | |||
| 1980 | wscript.exe | C:\Users\admin\AppData\Local\Temp\AY8RHr.zip | compressed | |
MD5:071D3D049362337671279D8F732F137F | SHA256:B1173F303F2876B28A4736B681F52666A1EFAB818148062A74D0309A6A12A6A8 | |||
| 1980 | wscript.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\jry4h6[1].zip | compressed | |
MD5:071D3D049362337671279D8F732F137F | SHA256:B1173F303F2876B28A4736B681F52666A1EFAB818148062A74D0309A6A12A6A8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
45
TCP/UDP connections
50
DNS requests
19
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.5:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.5:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.5:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 108.181.20.35:443 | https://files.catbox.moe/jry4h6.zip | unknown | compressed | 333 Kb | malicious |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.160.64:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | POST | 400 | 20.190.160.14:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
— | — | POST | 400 | 40.126.32.72:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 203 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.216.77.5:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.216.77.5:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.216.77.5:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
files.catbox.moe |
| malicious |
login.live.com |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
1980 | wscript.exe | Potentially Bad Traffic | ET INFO Observed File Sharing Service Download Domain (files .catbox .moe in TLS SNI) |
— | — | Misc activity | ET INFO Observed UA-CPU Header |
— | — | Misc activity | ET INFO Observed UA-CPU Header |