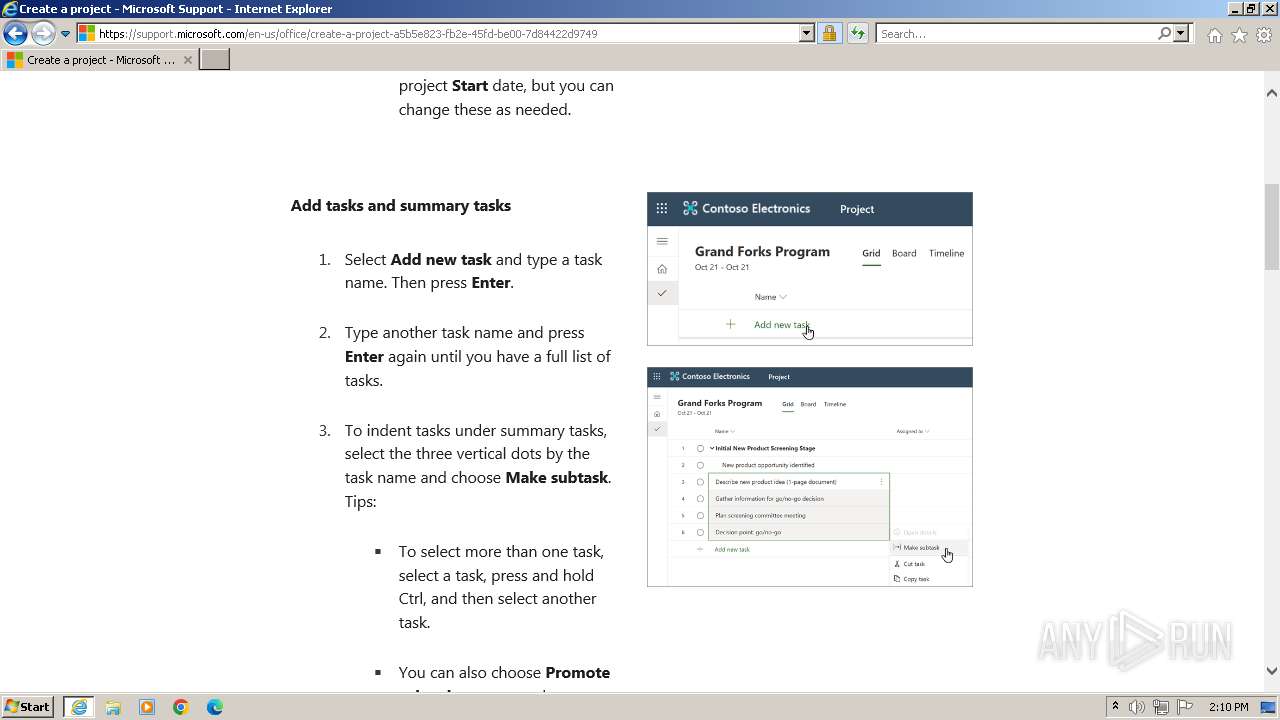
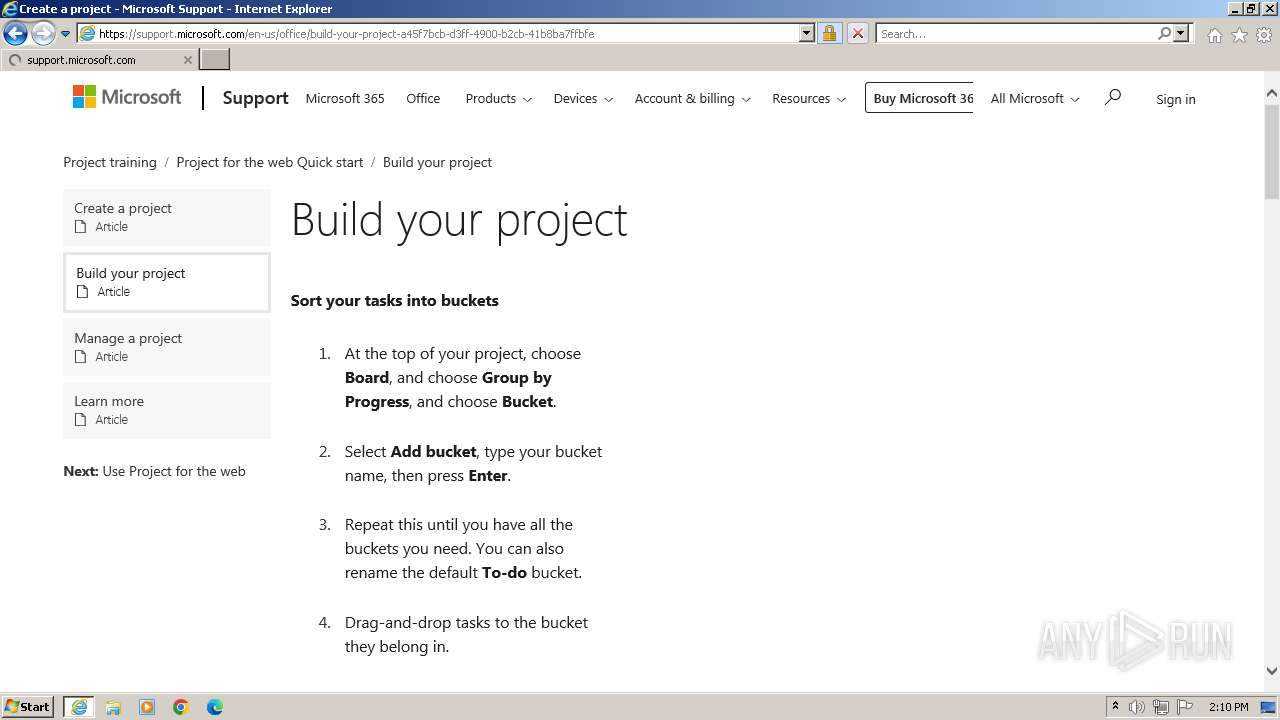
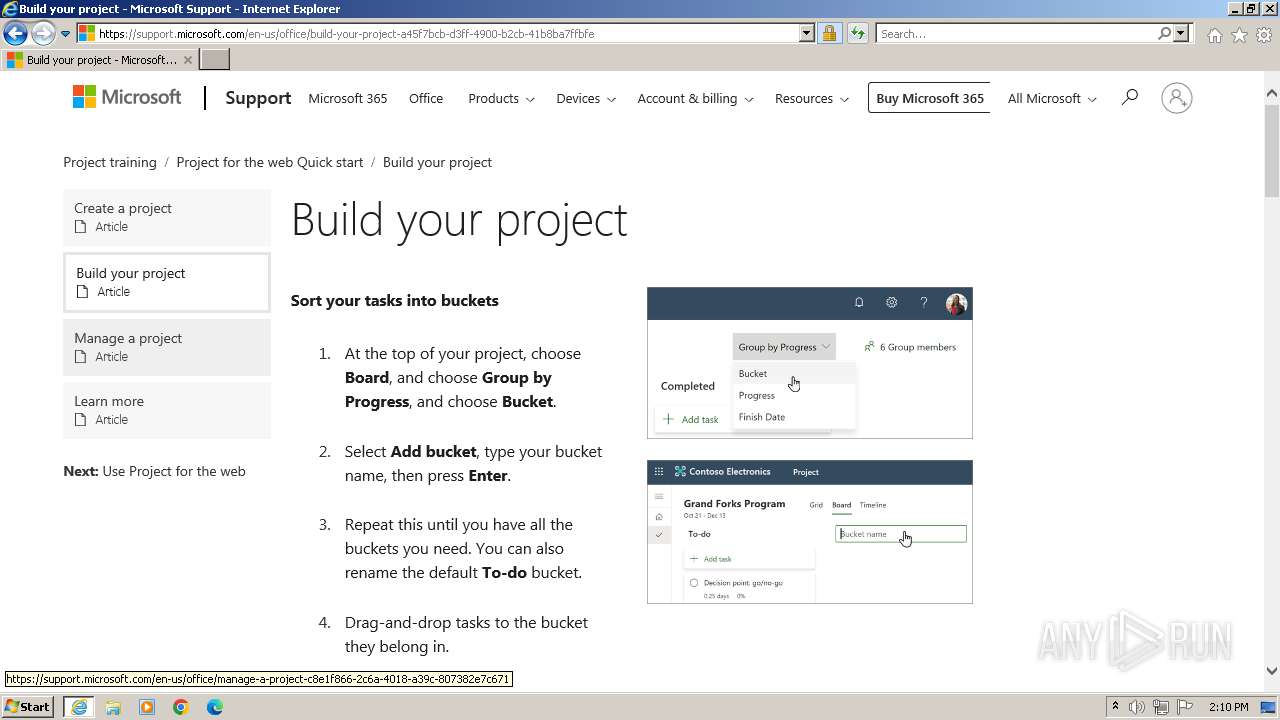
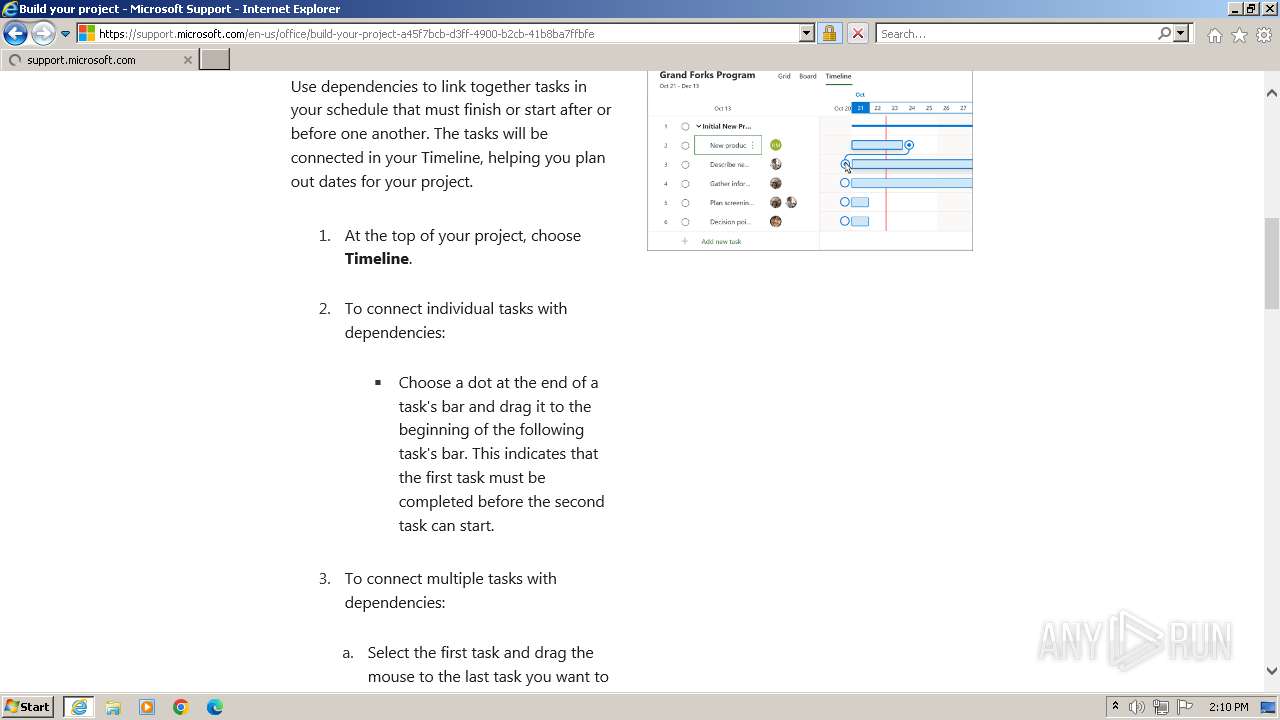
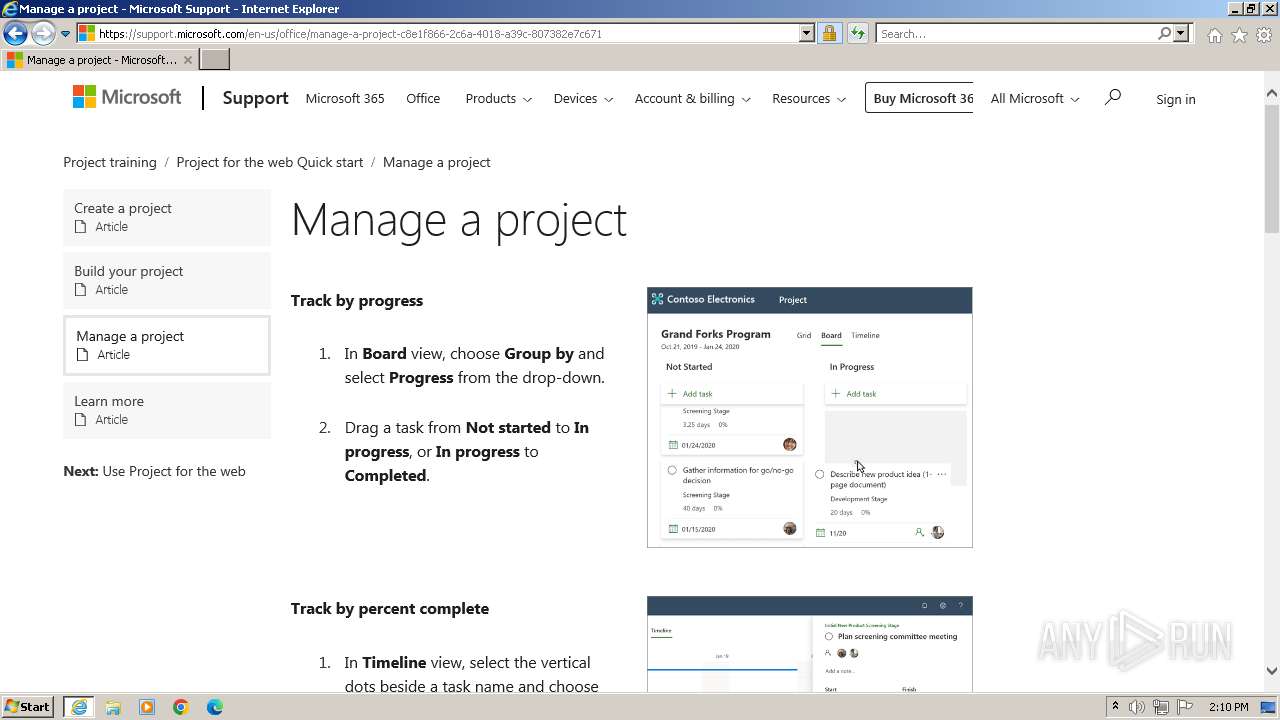
| URL: | https://urldefense.com/v3/__https://t.information.microsoft.com/r/?id=ha9cab49,1dd2468f,1dd24693__;!!Om87Lau1Cg!PIJuZzLNtWHY7AH4NhDwjJXSIxG0EUEv3A9CQNcr6mODwruxBFj_X-_VXx_HYFGOuycuoODQCw4dfQ4Z14cAidDScqck2Do$ |
| Full analysis: | https://app.any.run/tasks/a42ddf10-944e-4da0-a77d-c3c08568ec2d |
| Verdict: | Malicious activity |
| Analysis date: | October 23, 2023, 13:10:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| SHA1: | 99E9794C057607A0A9F586C44B187B1DA37AF460 |
| SHA256: | 5E683F446043D3F2A40492699A79CA7E414408B5AAAA55BA7E5024BD8A81DE84 |
| SSDEEP: | 6:2UJtIrhVkKMKLDaHBVcAO6f8NduSDhYDeWvgDpcB:2U04aLDqBVcb6kHDhYDesMcB |
MALICIOUS
PHISHING was detected
- iexplore.exe (PID: 3124)
SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 3820)
Manual execution by a user
- wmpnscfg.exe (PID: 1440)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 1440)
Reads the computer name
- wmpnscfg.exe (PID: 1440)
Checks supported languages
- wmpnscfg.exe (PID: 1440)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
40
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1440 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3124 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3820 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3820 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://urldefense.com/v3/__https://t.information.microsoft.com/r/?id=ha9cab49,1dd2468f,1dd24693__;!!Om87Lau1Cg!PIJuZzLNtWHY7AH4NhDwjJXSIxG0EUEv3A9CQNcr6mODwruxBFj_X-_VXx_HYFGOuycuoODQCw4dfQ4Z14cAidDScqck2Dof7f81a39-5f63-5b42-9efd-1f13b5431005quot; | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
20 527
Read events
20 452
Write events
72
Delete events
3
Modification events
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
Executable files
0
Suspicious files
40
Text files
176
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3124 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\72BA427A91F50409B9EAC87F2B59B951_B60F9D16E3C6B9D1675C5B66DD367947 | binary | |
MD5:457C8D67B21F0F5C34A0B4C89D1BE6BC | SHA256:95149C7C730EEB0C792A45D5D1E21CF9676FF3FED13877B24FB24192F4802B87 | |||
| 3124 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3124 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_D7393C8F62BDE4D4CB606228BC7A711E | binary | |
MD5:D82A1C176714B8A713CE97251C47EF30 | SHA256:C00500BC412237A4F9AFE335F8699988B7379094D86F0DBEA864D19651F17106 | |||
| 3124 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\PUK58ZSW.txt | text | |
MD5:FB8B33C51C3D76821E36609AEF728ED5 | SHA256:5CD47A88D8B79D3319A4F22FBC478AEC1491BC6BD53A34CE89730F069E29F5FB | |||
| 3124 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\80237EE4964FC9C409AAF55BF996A292_C5130A0BDC8C859A2757D77746C10868 | binary | |
MD5:38973C32ADE268658B40DF59E8D2AD54 | SHA256:A33E2D655298881688D99F104558A2A045463D9F591FFE94B6FEE60549DD67B6 | |||
| 3124 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_BACC6CD2B29F18349081C9FD2343833B | binary | |
MD5:0E19E475496CFF760609B86A61453ADC | SHA256:3E4AA889298543AF4F3864D64BB652A4A7061D1C77B4CC1C586CD9B98AE1ECFF | |||
| 3124 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\80237EE4964FC9C409AAF55BF996A292_C5130A0BDC8C859A2757D77746C10868 | binary | |
MD5:8FFA704D93BD4438462F793951DD24CC | SHA256:C8A56FCDD31C70FB3436BCAF06E84C877001AEC124D09D8ED77C072C474A5395 | |||
| 3124 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_BACC6CD2B29F18349081C9FD2343833B | binary | |
MD5:F52CD6E96B4F1355A826941D408732EA | SHA256:E3CA151F4D24E177E3A0CD8F48C7F77258BE03F892FCE02DE51E86A936DFFEC0 | |||
| 3124 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\12D25EEC119B36D4F609776800B40F1F_02F47AFC75C8FDA4640A34F2ED71C796 | binary | |
MD5:7B176BD73900393480F40C2293ED1058 | SHA256:47F2CD28DBD7378D8C67573DD192BA691962A9759A8D8CE67D707A610892544E | |||
| 3124 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_0FB9553B978E7F00C6B2309507DEB64A | binary | |
MD5:1406232988EBA73D8C8D6549D95FBB44 | SHA256:2CC5489089F6AC84D397CF5ED8DA3FD33D231106F69530A793BF3A7AADCE00E0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
75
DNS requests
48
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3124 | iexplore.exe | GET | 200 | 104.18.15.101:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | binary | 1.42 Kb | unknown |
3124 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e585de52940bd244 | unknown | compressed | 4.66 Kb | unknown |
3124 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | unknown | binary | 471 b | unknown |
3124 | iexplore.exe | GET | 200 | 104.18.15.101:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEBN9U5yqfDGppDNwGWiEeo0%3D | unknown | binary | 2.18 Kb | unknown |
3124 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | unknown | binary | 471 b | unknown |
3124 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | binary | 471 b | unknown |
3124 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | binary | 471 b | unknown |
3124 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
3124 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEALnkXH7gCHpP%2BLZg4NMUMA%3D | unknown | binary | 471 b | unknown |
3124 | iexplore.exe | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRS%2FsoQjbTlq1Jokw0nyC%2FyFeJLtQQUAKuR%2FCFiJpeaqHkbYUGQYKliZ%2F0CEzMAq3jSnC6NJvnfgWkAAACreNI%3D | unknown | binary | 1.74 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3124 | iexplore.exe | 52.204.90.22:443 | — | AMAZON-AES | US | unknown |
3124 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
3124 | iexplore.exe | 104.18.15.101:80 | ocsp.comodoca.com | CLOUDFLARENET | — | unknown |
3124 | iexplore.exe | 104.18.14.101:80 | ocsp.comodoca.com | CLOUDFLARENET | — | unknown |
3124 | iexplore.exe | 52.177.62.210:443 | t.information.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
3124 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
3124 | iexplore.exe | 204.79.197.203:80 | oneocsp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
t.information.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
oneocsp.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
support.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3124 | iexplore.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Phishing domain observed in TLS SNI ( .azurefd .net) |