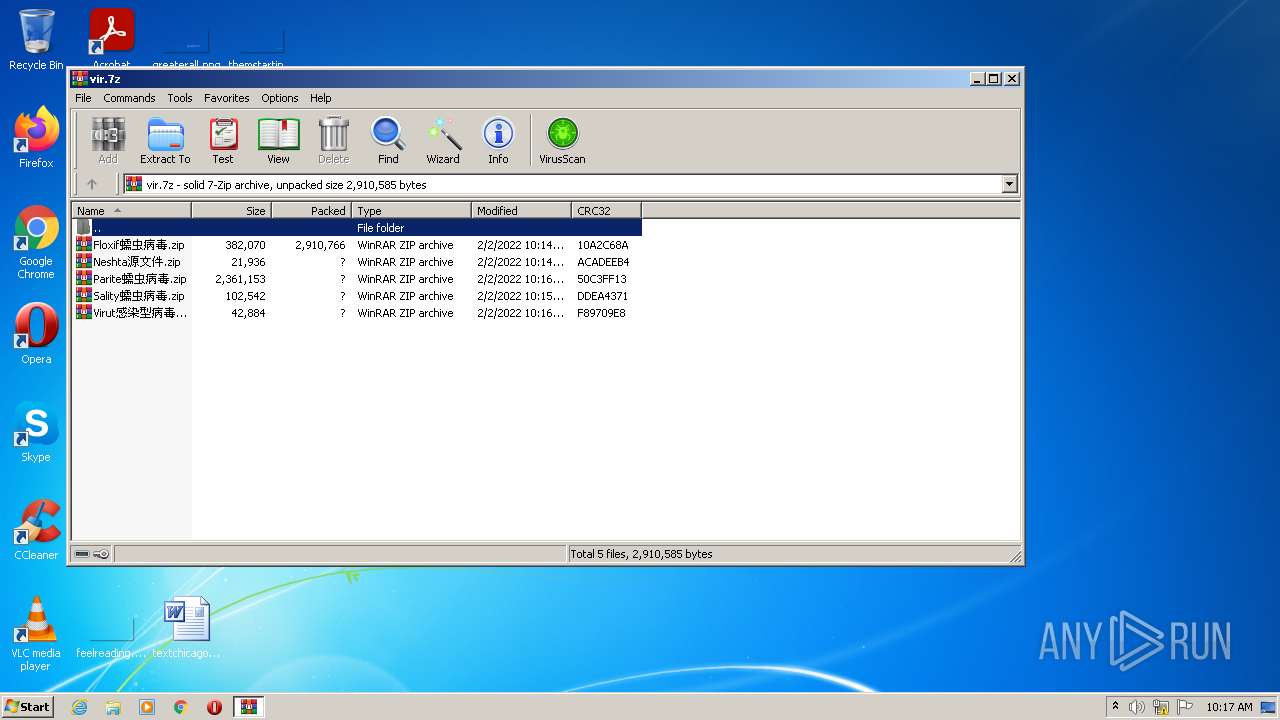
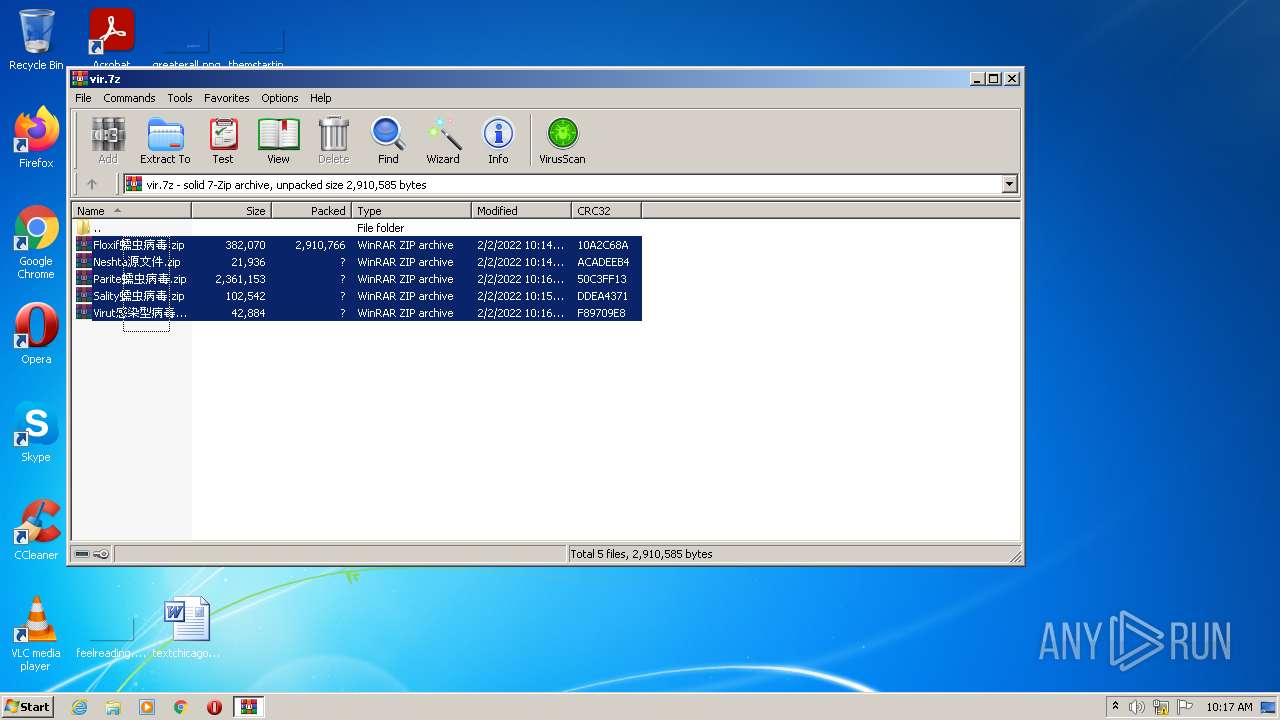
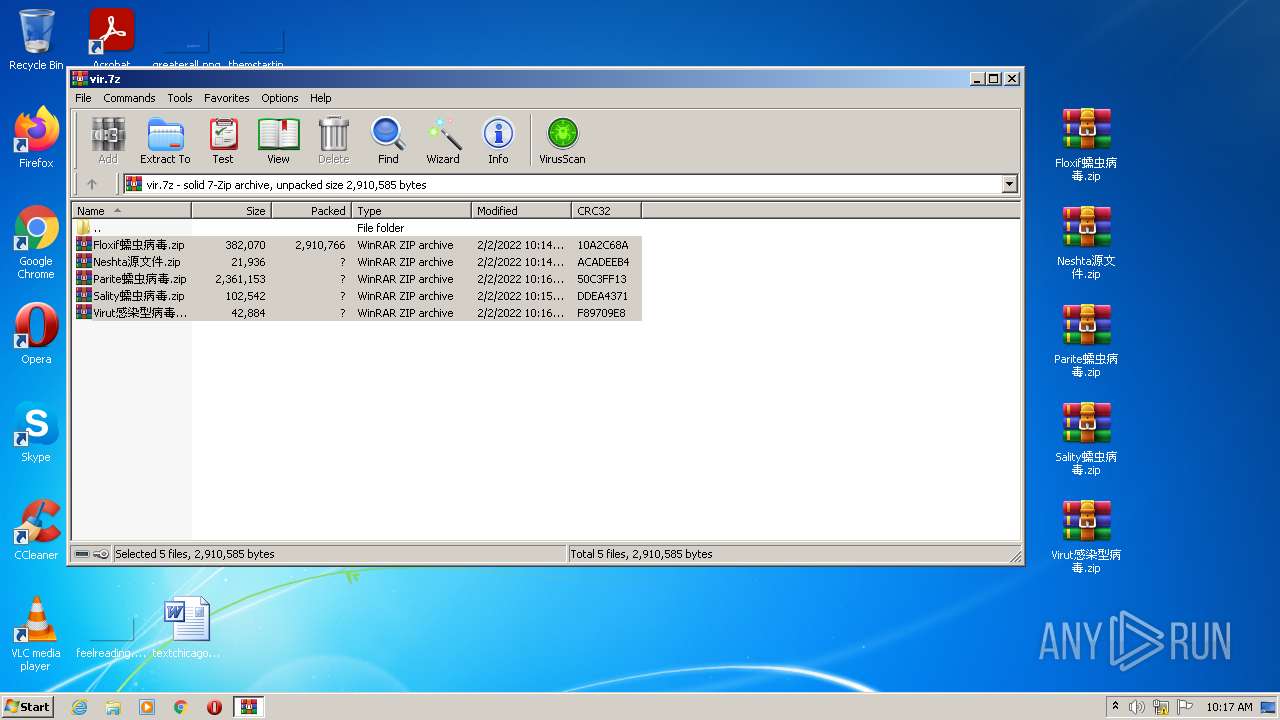
| File name: | vir.7z |
| Full analysis: | https://app.any.run/tasks/2405717a-90bf-479d-a588-d071d92337bf |
| Verdict: | Malicious activity |
| Analysis date: | February 02, 2022, 10:17:30 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | DABFA9FDCC98A90D3F4D7DE7A0CA2FFE |
| SHA1: | A2FC70B146ADB4F993B40C27ADAD3FAB211635C6 |
| SHA256: | 5E4DC8B261092D2C18A7421BC7F0A725ECDFE987BE4D8ED401ECBFDEF3D8455B |
| SSDEEP: | 49152:YGS91Gb3W90pID6a7znQU58iupunmWrBQvDJBDqf188hsuTqMQHiwSqp8:wG7k6kxQU5cpuDWNBD+87uTeHJSv |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3512)
Drops executable file immediately after starts
- WinRAR.exe (PID: 2456)
Application was dropped or rewritten from another process
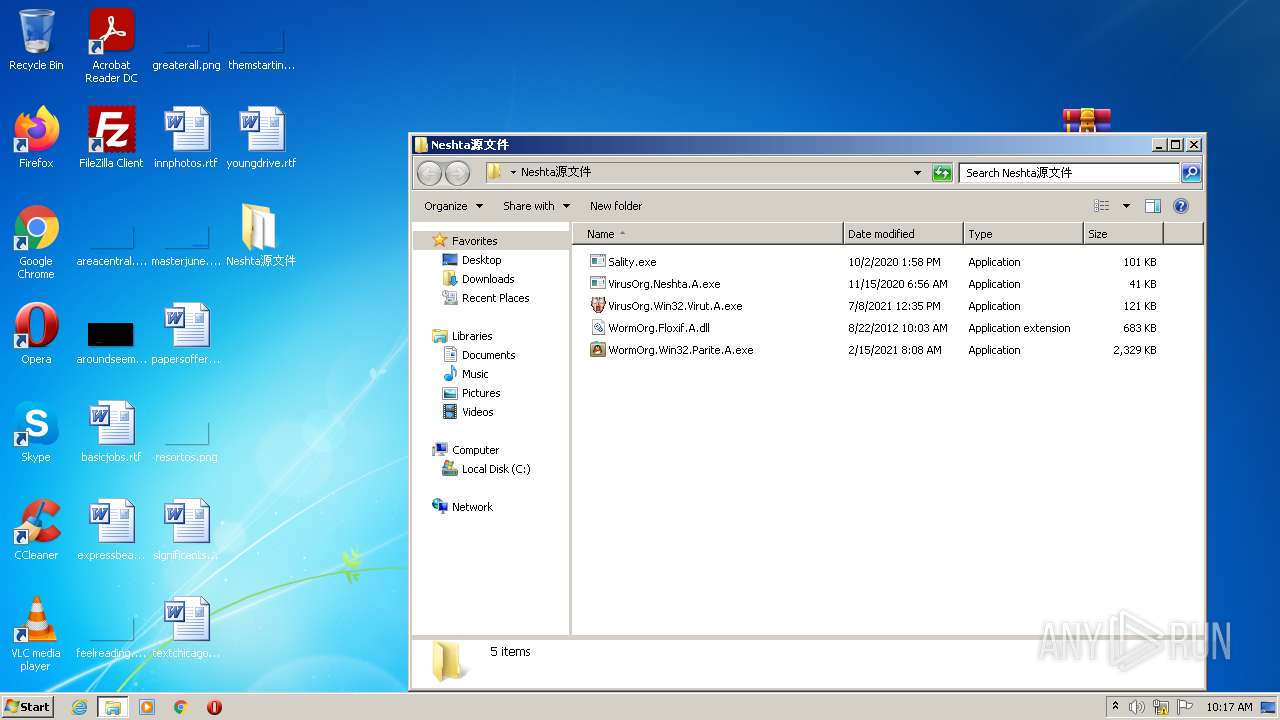
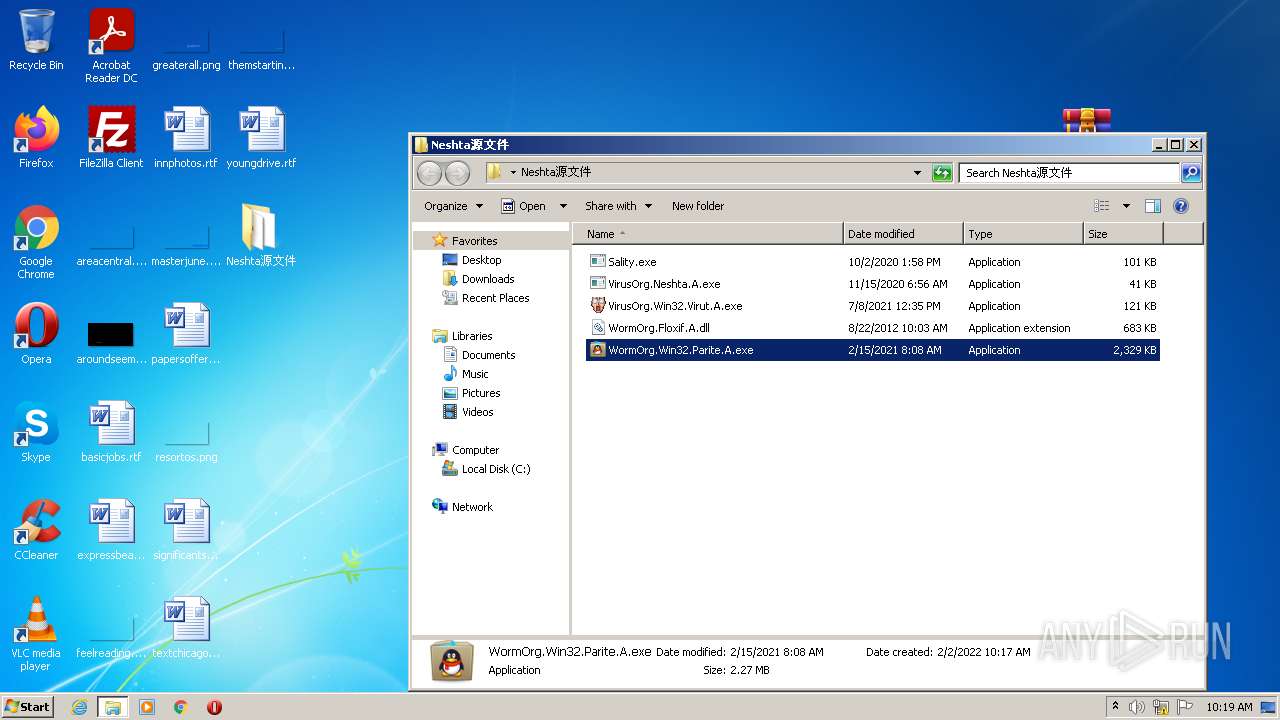
- VirusOrg.Neshta.A.exe (PID: 3476)
- Sality.exe (PID: 3716)
- WormOrg.Win32.Parite.A.exe (PID: 1772)
- WormOrg.Win32.Parite.A.exe (PID: 3840)
- Sality.exe (PID: 2456)
- VirusOrg.Win32.Virut.A.exe (PID: 2248)
Changes Security Center notification settings
- Sality.exe (PID: 3716)
UAC/LUA settings modification
- Sality.exe (PID: 3716)
Application was injected by another process
- taskeng.exe (PID: 2040)
- Dwm.exe (PID: 1176)
- ctfmon.exe (PID: 612)
- DllHost.exe (PID: 3140)
- Explorer.EXE (PID: 1108)
- WerFault.exe (PID: 2808)
- conhost.exe (PID: 2988)
- csrss.exe (PID: 668)
- wininit.exe (PID: 640)
Changes firewall settings
- Sality.exe (PID: 3716)
Runs injected code in another process
- Sality.exe (PID: 3716)
- VirusOrg.Win32.Virut.A.exe (PID: 2248)
SUSPICIOUS
Reads the computer name
- WinRAR.exe (PID: 1104)
- WinRAR.exe (PID: 2456)
- DllHost.exe (PID: 3140)
- Sality.exe (PID: 3716)
- WormOrg.Win32.Parite.A.exe (PID: 1772)
- WormOrg.Win32.Parite.A.exe (PID: 3840)
- VirusOrg.Win32.Virut.A.exe (PID: 2248)
- Sality.exe (PID: 2456)
Checks supported languages
- WinRAR.exe (PID: 1104)
- WinRAR.exe (PID: 2456)
- VirusOrg.Neshta.A.exe (PID: 3476)
- DllHost.exe (PID: 3140)
- Sality.exe (PID: 3716)
- WormOrg.Win32.Parite.A.exe (PID: 1772)
- conhost.exe (PID: 2988)
- Dwm.exe (PID: 1176)
- WormOrg.Win32.Parite.A.exe (PID: 3840)
- Sality.exe (PID: 2456)
- VirusOrg.Win32.Virut.A.exe (PID: 2248)
Creates files in the Windows directory
- VirusOrg.Neshta.A.exe (PID: 3476)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2456)
- Sality.exe (PID: 3716)
Drops a file with too old compile date
- WinRAR.exe (PID: 2456)
- Sality.exe (PID: 3716)
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 2456)
- Sality.exe (PID: 3716)
Changes default file association
- VirusOrg.Neshta.A.exe (PID: 3476)
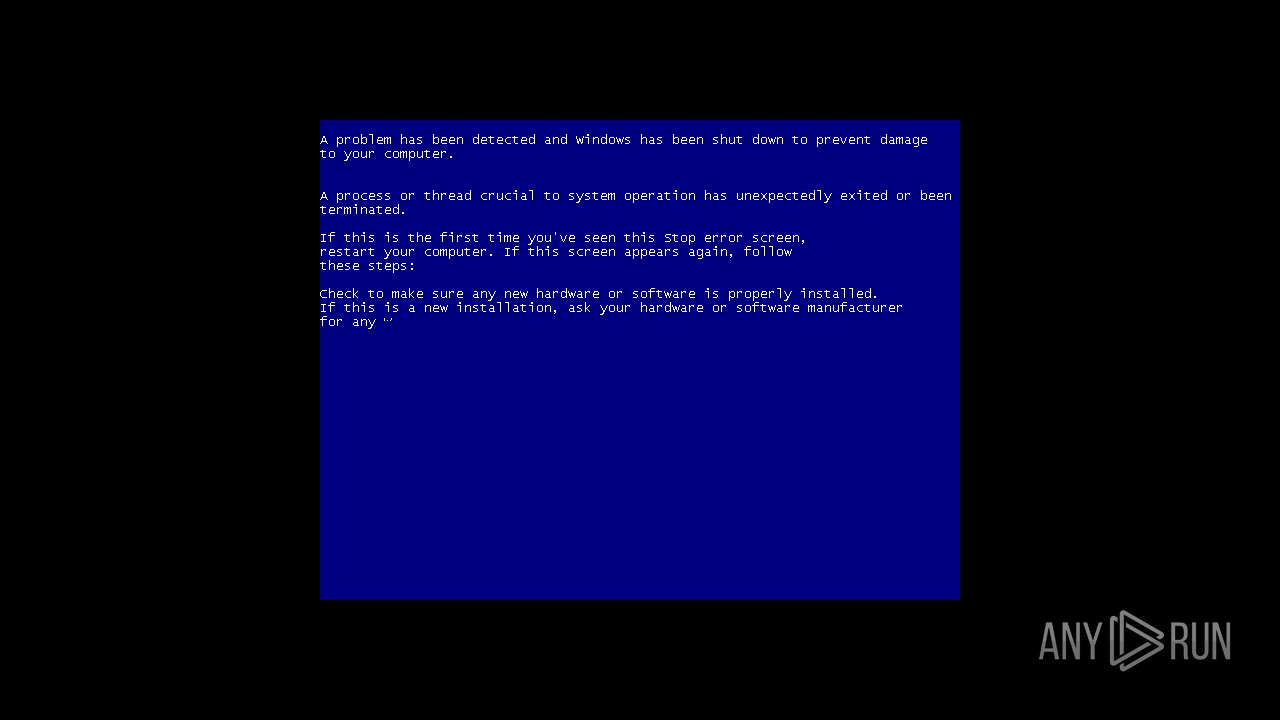
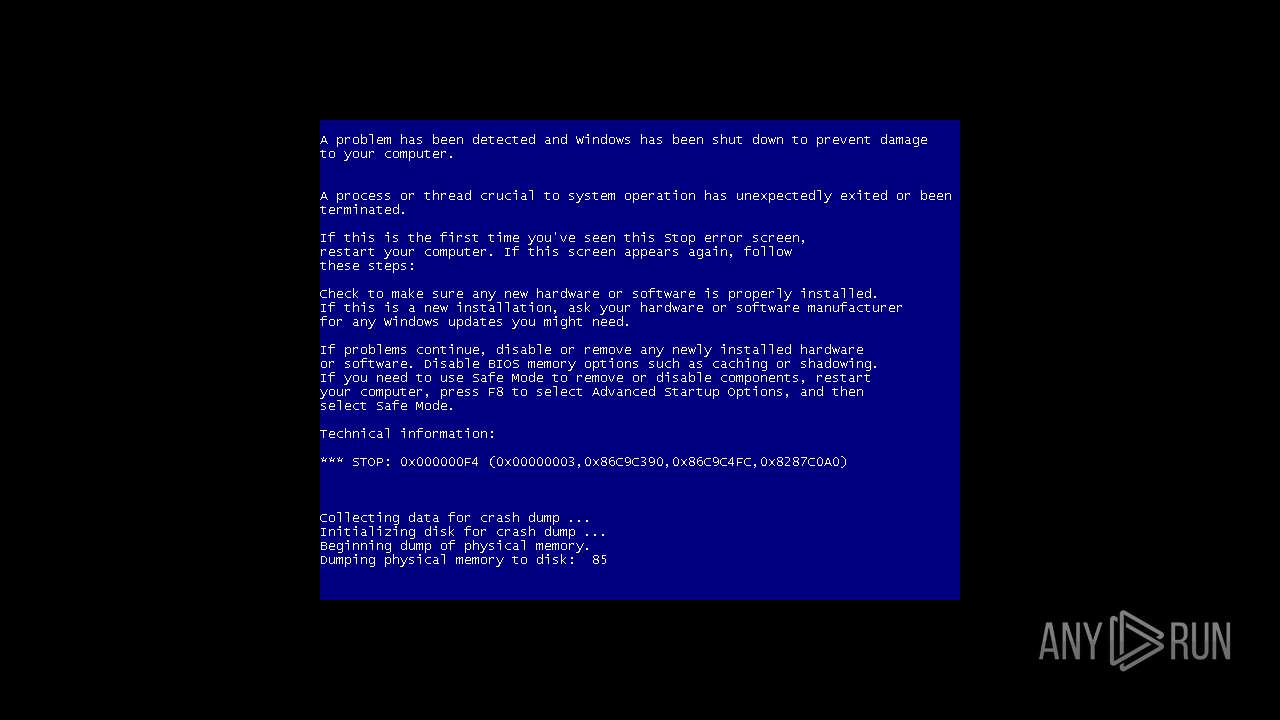
Executes application which crashes
- Explorer.EXE (PID: 1108)
Reads default file associations for system extensions
- Explorer.EXE (PID: 1108)
INFO
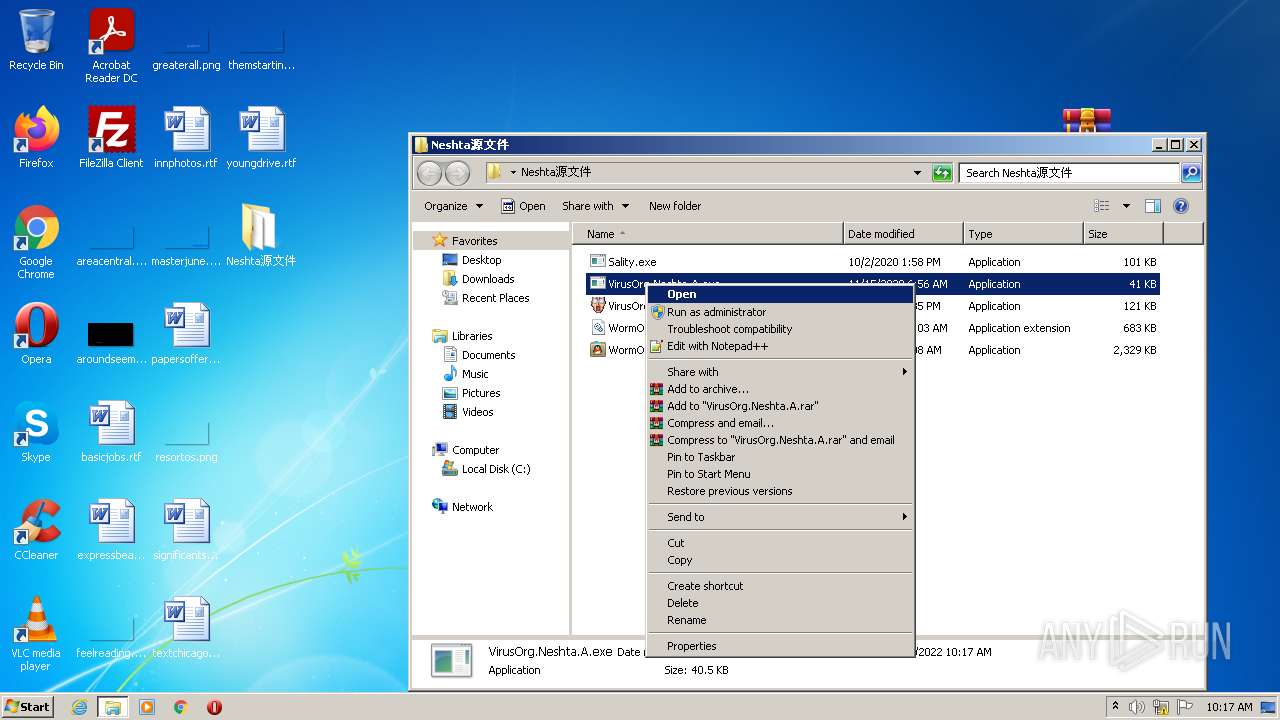
Manual execution by user
- WinRAR.exe (PID: 2456)
- VirusOrg.Neshta.A.exe (PID: 3476)
- Sality.exe (PID: 3716)
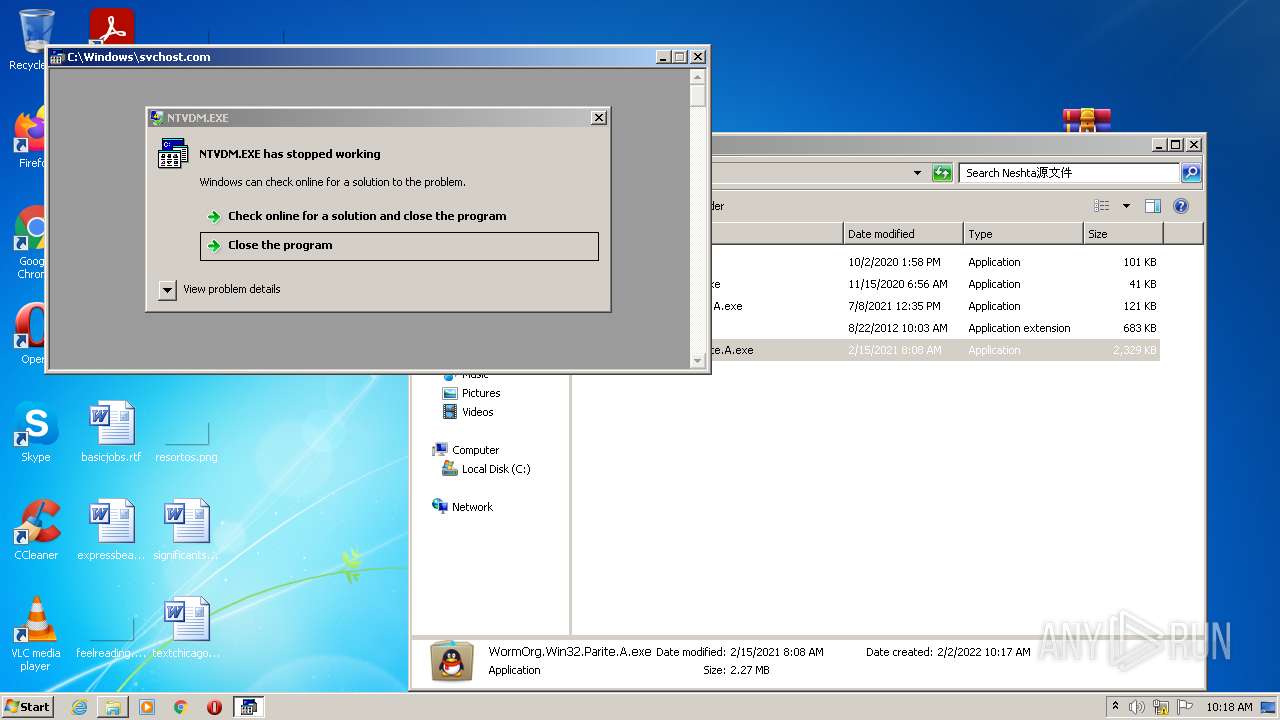
- ntvdm.exe (PID: 2516)
- WormOrg.Win32.Parite.A.exe (PID: 1772)
- WormOrg.Win32.Parite.A.exe (PID: 3840)
- ntvdm.exe (PID: 292)
- Sality.exe (PID: 2456)
- VirusOrg.Win32.Virut.A.exe (PID: 2248)
Dropped object may contain TOR URL's
- WinRAR.exe (PID: 2456)
Checks supported languages
- ntvdm.exe (PID: 2516)
- ntvdm.exe (PID: 292)
- WerFault.exe (PID: 2808)
Reads the computer name
- WerFault.exe (PID: 2808)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
Total processes
65
Monitored processes
20
Malicious processes
7
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | "C:\Windows\system32\ntvdm.exe" -i2 | C:\Windows\system32\ntvdm.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 3221225477 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 612 | C:\Windows\System32\ctfmon.exe | C:\Windows\System32\ctfmon.exe | taskeng.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: CTF Loader Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 640 | wininit.exe | C:\Windows\system32\wininit.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Start-Up Application Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 668 | %SystemRoot%\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,12288,512 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ServerDll=sxssrv,4 ProfileControl=Off MaxRequestThreads=16 | C:\Windows\system32\csrss.exe | — | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Client Server Runtime Process Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1104 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\vir.7z" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 1108 | C:\Windows\Explorer.EXE | C:\Windows\Explorer.EXE | — | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1176 | "C:\Windows\system32\Dwm.exe" | C:\Windows\system32\Dwm.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Desktop Window Manager Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1772 | "C:\Users\admin\Desktop\Neshta???\WormOrg.Win32.Parite.A.exe" | C:\Users\admin\Desktop\Neshta???\WormOrg.Win32.Parite.A.exe | Explorer.EXE | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 2 Modules
| |||||||||||||||
| 2040 | taskeng.exe {D0F9F501-9242-4B74-B2E9-F518725CD611} | C:\Windows\system32\taskeng.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Engine Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2248 | "C:\Users\admin\Desktop\Neshta???\VirusOrg.Win32.Virut.A.exe" | C:\Users\admin\Desktop\Neshta???\VirusOrg.Win32.Virut.A.exe | Explorer.EXE | ||||||||||||
User: admin Company: ELEMENTAL SOFT Integrity Level: HIGH Description: ChiyoGanbaru Exit code: 0 Version: 1, 0, 0, 1 Modules
| |||||||||||||||
Total events
16 654
Read events
12 423
Write events
4 231
Delete events
0
Modification events
| (PID) Process: | (1104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1104) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (1104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (1104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\vir.7z | |||
| (PID) Process: | (1104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1104) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
9
Suspicious files
12
Text files
5
Unknown types
25
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2456 | WinRAR.exe | C:\Users\admin\Desktop\Neshta???\VirusOrg.Neshta.A.exe | executable | |
MD5:36FD5E09C417C767A952B4609D73A54B | SHA256:980BAC6C9AFE8EFC9C6FE459A5F77213B0D8524EB00DE82437288EB96138B9A2 | |||
| 2456 | WinRAR.exe | C:\Users\admin\Desktop\Neshta???\VirusOrg.Win32.Virut.A.exe | executable | |
MD5:606A95B422C08C106744A6E312413AAB | SHA256:D6C9D4F03B0E7404132B1382CAFABA4F59DCB62106160B66488B02E16BE26874 | |||
| 2456 | WinRAR.exe | C:\Users\admin\Desktop\Neshta???\WormOrg.Win32.Parite.A.exe | executable | |
MD5:CD86B04047BA72D5A4629806D274AD1E | SHA256:11E3BCDFC858E427A33D6907F4B5174F4C146E4F5ECB6AFAB3FDD2C9D5E48DD5 | |||
| 1104 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1104.21588\Floxif????.zip | compressed | |
MD5:0E2B0BD28A8FB318894F4AC2DC2A2C6A | SHA256:778CB81FF7519706D2A0932936CA9DFE820BB92FD599728A965BA36CF672C59F | |||
| 1104 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1104.21588\Parite????.zip | compressed | |
MD5:6C5A08CBCA9629A5C20AABE74C798604 | SHA256:341B08D5522A8916314648219EEA375C2D8DECAA26053ACA5E24DFFCA2BBFB86 | |||
| 1104 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1104.21588\Neshta???.zip | compressed | |
MD5:B5D19F2CEEBC4F67D2BA02F57623BC2B | SHA256:8A96C952FDD1E3B96BD2F9DAB9895745DD7F98D80018AAEF01D02F123B1FD065 | |||
| 1108 | Explorer.EXE | C:\Users\admin\Desktop\Floxif????.zip | compressed | |
MD5:0E2B0BD28A8FB318894F4AC2DC2A2C6A | SHA256:778CB81FF7519706D2A0932936CA9DFE820BB92FD599728A965BA36CF672C59F | |||
| 1104 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1104.21588\Virut?????.zip | compressed | |
MD5:6C48B8BE5B8A29506EAA045E265849A2 | SHA256:82DB3D2C2CECC18A178261ED0349F6D378BAD2E1C86AF547F6D51143FA156B83 | |||
| 1104 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa1104.21588\Sality????.zip | compressed | |
MD5:4B716BCAEE813564CEC74065AC305BA6 | SHA256:6A438DB46E6AF2936495E44D01D46A8D31385798522B12E7481E514067DB51FD | |||
| 1108 | Explorer.EXE | C:\Users\admin\Desktop\Parite????.zip | compressed | |
MD5:6C5A08CBCA9629A5C20AABE74C798604 | SHA256:341B08D5522A8916314648219EEA375C2D8DECAA26053ACA5E24DFFCA2BBFB86 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report