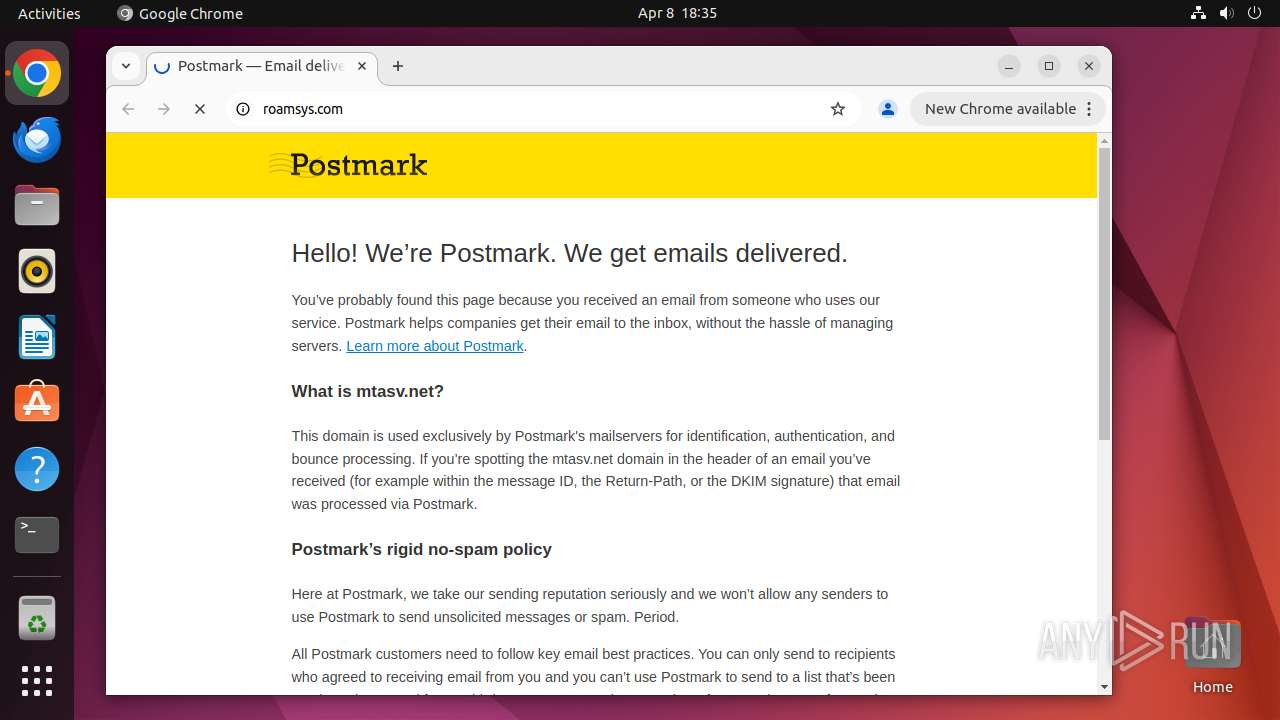
| URL: | pmbounces.roamsys.com |
| Full analysis: | https://app.any.run/tasks/e9a6b203-667a-4806-b423-367ff2a6a9fb |
| Verdict: | Malicious activity |
| Threats: | A loader is malicious software that infiltrates devices to deliver malicious payloads. This malware is capable of infecting victims’ computers, analyzing their system information, and installing other types of threats, such as trojans or stealers. Criminals usually deliver loaders through phishing emails and links by relying on social engineering to trick users into downloading and running their executables. Loaders employ advanced evasion and persistence tactics to avoid detection. |
| Analysis date: | April 08, 2025, 17:35:03 |
| OS: | Ubuntu 22.04.2 |
| Tags: | |
| MD5: | 2A33406A5DA834BB21DDEF67D15573AD |
| SHA1: | EC7186FFCD4BDEE93B05A4A83E0B8346EA6B0CE5 |
| SHA256: | 5E4764EDD46551216D73B4B912B3D4EC3D5FB44198E444DB7612AA98DBB46831 |
| SSDEEP: | 3:dzjKhXn:dzjKhXn |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executes commands using command-line interpreter
- chrome (PID: 40666)
- sudo (PID: 40665)
Process requests binary or script from the Internet
- chrome (PID: 40712)
INFO
Checks timezone
- chrome (PID: 40666)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
308
Monitored processes
88
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 40664 | /bin/sh -c "DISPLAY=:0 sudo -iu user google-chrome pmbounces\.roamsys\.com " | /usr/bin/dash | — | any-guest-agent |
User: root Integrity Level: UNKNOWN | ||||
| 40665 | sudo -iu user google-chrome pmbounces.roamsys.com | /usr/bin/sudo | — | dash |
User: root Integrity Level: UNKNOWN | ||||
| 40666 | /usr/bin/google-chrome pmbounces.roamsys.com | /opt/google/chrome/chrome | — | sudo |
User: user Integrity Level: UNKNOWN | ||||
| 40667 | /usr/bin/locale-check C.UTF-8 | /usr/bin/locale-check | — | chrome |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 40668 | readlink -f /usr/bin/google-chrome | /usr/bin/readlink | — | chrome |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 40669 | dirname /opt/google/chrome/google-chrome | /usr/bin/dirname | — | chrome |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 40670 | mkdir -p /home/user/.local/share/applications | /usr/bin/mkdir | — | chrome |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
| 40671 | cat | /usr/bin/cat | — | chrome |
User: user Integrity Level: UNKNOWN | ||||
| 40672 | cat | /usr/bin/cat | — | chrome |
User: user Integrity Level: UNKNOWN | ||||
| 40673 | "/opt/google/chrome/chrome pmbounces\.roamsys\.c" | /opt/google/chrome/chrome | — | chrome |
User: user Integrity Level: UNKNOWN Exit code: 0 | ||||
Executable files
2
Suspicious files
286
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 40666 | chrome | /home/user/.config/google-chrome/ShaderCache/data_3 | binary | |
MD5:— | SHA256:— | |||
| 40666 | chrome | /home/user/.config/google-chrome/ShaderCache/data_2 | binary | |
MD5:— | SHA256:— | |||
| 40666 | chrome | /home/user/.config/google-chrome/ShaderCache/data_0 | binary | |
MD5:— | SHA256:— | |||
| 40666 | chrome | /home/user/.config/google-chrome/Default/GPUCache/data_3 | binary | |
MD5:— | SHA256:— | |||
| 40666 | chrome | /home/user/.config/google-chrome/Default/GPUCache/data_2 | binary | |
MD5:— | SHA256:— | |||
| 40666 | chrome | /home/user/.config/google-chrome/Default/GPUCache/data_0 | binary | |
MD5:— | SHA256:— | |||
| 40709 | chrome | /home/user/.cache/mesa_shader_cache/index | binary | |
MD5:— | SHA256:— | |||
| 40811 | chrome | /home/user/.cache/mesa_shader_cache/index | binary | |
MD5:— | SHA256:— | |||
| 40666 | chrome | /home/user/.config/google-chrome/Default/History | binary | |
MD5:— | SHA256:— | |||
| 40666 | chrome | /home/user/.config/google-chrome/Default/DawnWebGPUCache/data_3 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
39
DNS requests
54
Threats
19
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 204 | 185.125.190.97:80 | http://connectivity-check.ubuntu.com/ | unknown | — | — | whitelisted |
40712 | chrome | GET | 200 | 3.132.254.202:80 | http://pmbounces.roamsys.com/modernizr.js | unknown | — | — | unknown |
40712 | chrome | GET | 200 | 3.132.254.202:80 | http://pmbounces.roamsys.com/landing.css | unknown | — | — | unknown |
40712 | chrome | GET | 200 | 142.250.184.206:80 | http://www.google-analytics.com/ga.js | unknown | — | — | whitelisted |
40712 | chrome | GET | 200 | 3.132.254.202:80 | http://pmbounces.roamsys.com/ | unknown | — | — | unknown |
40712 | chrome | GET | 200 | 3.132.254.202:80 | http://pmbounces.roamsys.com/logo@2x.png | unknown | — | — | unknown |
40712 | chrome | GET | 200 | 142.250.184.206:80 | http://www.google-analytics.com/r/__utm.gif?utmwv=5.7.2&utms=1&utmn=1679236208&utmhn=pmbounces.roamsys.com&utmcs=UTF-8&utmsr=1280x720&utmvp=991x562&utmsc=24-bit&utmul=en-gb&utmje=0&utmfl=-&utmdt=Postmark%20%E2%80%94%20Email%20delivery%20for%20web%20apps&utmhid=598027177&utmr=-&utmp=%2F&utmht=1744133711297&utmac=UA-507677-17&utmcc=__utma%3D199676335.701859818.1744133711.1744133711.1744133711.1%3B%2B__utmz%3D199676335.1744133711.1.1.utmcsr%3D(direct)%7Cutmccn%3D(direct)%7Cutmcmd%3D(none)%3B&utmjid=2133171687&utmredir=1&utmu=qAAAAAAAAAAAAAAAAAAAAAAE~ | unknown | — | — | whitelisted |
40712 | chrome | GET | 200 | 3.132.254.202:80 | http://pmbounces.roamsys.com/favicon.ico | unknown | — | — | unknown |
40712 | chrome | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/k7gxgnnbcbx27yzcp3wdpr3nw4_2025.4.7.1/jflhchccmppkfebkiaminageehmchikm_2025.04.07.01_all_pzqexqgg2q2vehus2ide76rcve.crx3 | unknown | — | — | whitelisted |
40712 | chrome | GET | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ngifsy4k4mu7bcrdyhc4vjaocy_2025.4.2.0/gonpemdgkjcecdgbnaabipppbmgfggbe_2025.04.02.00_all_adnkhxd45xqajkfutwmwv6agl33q.crx3 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 185.125.190.97:80 | connectivity-check.ubuntu.com | Canonical Group Limited | GB | whitelisted |
484 | avahi-daemon | 224.0.0.251:5353 | — | — | — | unknown |
— | — | 212.102.56.178:443 | odrs.gnome.org | Datacamp Limited | DE | whitelisted |
512 | snapd | 185.125.188.54:443 | api.snapcraft.io | Canonical Group Limited | GB | whitelisted |
40712 | chrome | 142.250.186.131:443 | clientservices.googleapis.com | GOOGLE | US | whitelisted |
40712 | chrome | 142.250.185.170:443 | safebrowsingohttpgateway.googleapis.com | GOOGLE | US | whitelisted |
40712 | chrome | 142.250.153.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
40712 | chrome | 3.132.254.202:80 | pmbounces.roamsys.com | AMAZON-02 | US | suspicious |
40712 | chrome | 3.129.235.117:443 | pmbounces.roamsys.com | AMAZON-02 | US | suspicious |
40712 | chrome | 151.101.1.91:443 | google-ohttp-relay-safebrowsing.fastly-edge.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
connectivity-check.ubuntu.com |
| whitelisted |
odrs.gnome.org |
| whitelisted |
api.snapcraft.io |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
safebrowsingohttpgateway.googleapis.com |
| whitelisted |
pmbounces.roamsys.com |
| unknown |
pm.mtasv.net |
| unknown |
accounts.google.com |
| whitelisted |
google-ohttp-relay-safebrowsing.fastly-edge.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
40712 | chrome | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
40712 | chrome | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
40712 | chrome | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
40712 | chrome | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
40712 | chrome | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
40712 | chrome | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
40712 | chrome | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
40712 | chrome | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
40712 | chrome | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |
40712 | chrome | Generic Protocol Command Decode | SURICATA QUIC failed decrypt |