| File name: | 2025-07-04_a1abf560f59533c62ca03ae69d77bbc9_bkransomware_elex_rhadamanthys |
| Full analysis: | https://app.any.run/tasks/82a712c4-d151-4aa4-b405-b753228c9cf2 |
| Verdict: | Malicious activity |
| Analysis date: | July 04, 2025, 17:43:22 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 4 sections |
| MD5: | A1ABF560F59533C62CA03AE69D77BBC9 |
| SHA1: | A788ECA75ACF0A633AB51DB2D2AE00B5EE175D90 |
| SHA256: | 5E43D254611933170AEBF6D8F7E9779F57C3AC5ACE1F39FCBE16B717574C1B4F |
| SSDEEP: | 3072:sEeHMiMmMfM9OcgD7eHFzpEbC7etIOxzd9UIxeF7zbH8JKBO:BDyOcgDMFzwCCXnFeF/Dkz |
MALICIOUS
Changes the autorun value in the registry
- 2025-07-04_a1abf560f59533c62ca03ae69d77bbc9_bkransomware_elex_rhadamanthys.exe (PID: 5768)
- CTS.exe (PID: 5560)
- CTS.exe (PID: 6768)
SUSPICIOUS
Executable content was dropped or overwritten
- 2025-07-04_a1abf560f59533c62ca03ae69d77bbc9_bkransomware_elex_rhadamanthys.exe (PID: 5768)
- CTS.exe (PID: 6768)
Starts itself from another location
- 2025-07-04_a1abf560f59533c62ca03ae69d77bbc9_bkransomware_elex_rhadamanthys.exe (PID: 5768)
INFO
Reads the machine GUID from the registry
- 2025-07-04_a1abf560f59533c62ca03ae69d77bbc9_bkransomware_elex_rhadamanthys.exe (PID: 5768)
- CTS.exe (PID: 6768)
- CTS.exe (PID: 5560)
Checks supported languages
- 2025-07-04_a1abf560f59533c62ca03ae69d77bbc9_bkransomware_elex_rhadamanthys.exe (PID: 5768)
- CTS.exe (PID: 6768)
- CTS.exe (PID: 5560)
Launching a file from a Registry key
- 2025-07-04_a1abf560f59533c62ca03ae69d77bbc9_bkransomware_elex_rhadamanthys.exe (PID: 5768)
- CTS.exe (PID: 6768)
- CTS.exe (PID: 5560)
Create files in a temporary directory
- 2025-07-04_a1abf560f59533c62ca03ae69d77bbc9_bkransomware_elex_rhadamanthys.exe (PID: 5768)
Reads the computer name
- 2025-07-04_a1abf560f59533c62ca03ae69d77bbc9_bkransomware_elex_rhadamanthys.exe (PID: 5768)
Reads the software policy settings
- slui.exe (PID: 3620)
Checks proxy server information
- slui.exe (PID: 3620)
Manual execution by a user
- CTS.exe (PID: 5560)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2015:07:12 09:13:02+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 60928 |
| InitializedDataSize: | 18944 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x5cde |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
136
Monitored processes
4
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3620 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5560 | C:\Users\admin\AppData\Local\Temp\CTS.exe | C:\Users\admin\AppData\Local\Temp\CTS.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5768 | "C:\Users\admin\Desktop\2025-07-04_a1abf560f59533c62ca03ae69d77bbc9_bkransomware_elex_rhadamanthys.exe" | C:\Users\admin\Desktop\2025-07-04_a1abf560f59533c62ca03ae69d77bbc9_bkransomware_elex_rhadamanthys.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6768 | "C:\Users\admin\AppData\Local\Temp\CTS.exe" | C:\Users\admin\AppData\Local\Temp\CTS.exe | 2025-07-04_a1abf560f59533c62ca03ae69d77bbc9_bkransomware_elex_rhadamanthys.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
3 586
Read events
3 583
Write events
3
Delete events
0
Modification events
| (PID) Process: | (5768) 2025-07-04_a1abf560f59533c62ca03ae69d77bbc9_bkransomware_elex_rhadamanthys.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | CTS |
Value: C:\Users\admin\AppData\Local\Temp\CTS.exe | |||
| (PID) Process: | (6768) CTS.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | CTS |
Value: C:\Users\admin\AppData\Local\Temp\CTS.exe | |||
| (PID) Process: | (5560) CTS.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | CTS |
Value: C:\Users\admin\AppData\Local\Temp\CTS.exe | |||
Executable files
50
Suspicious files
1
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
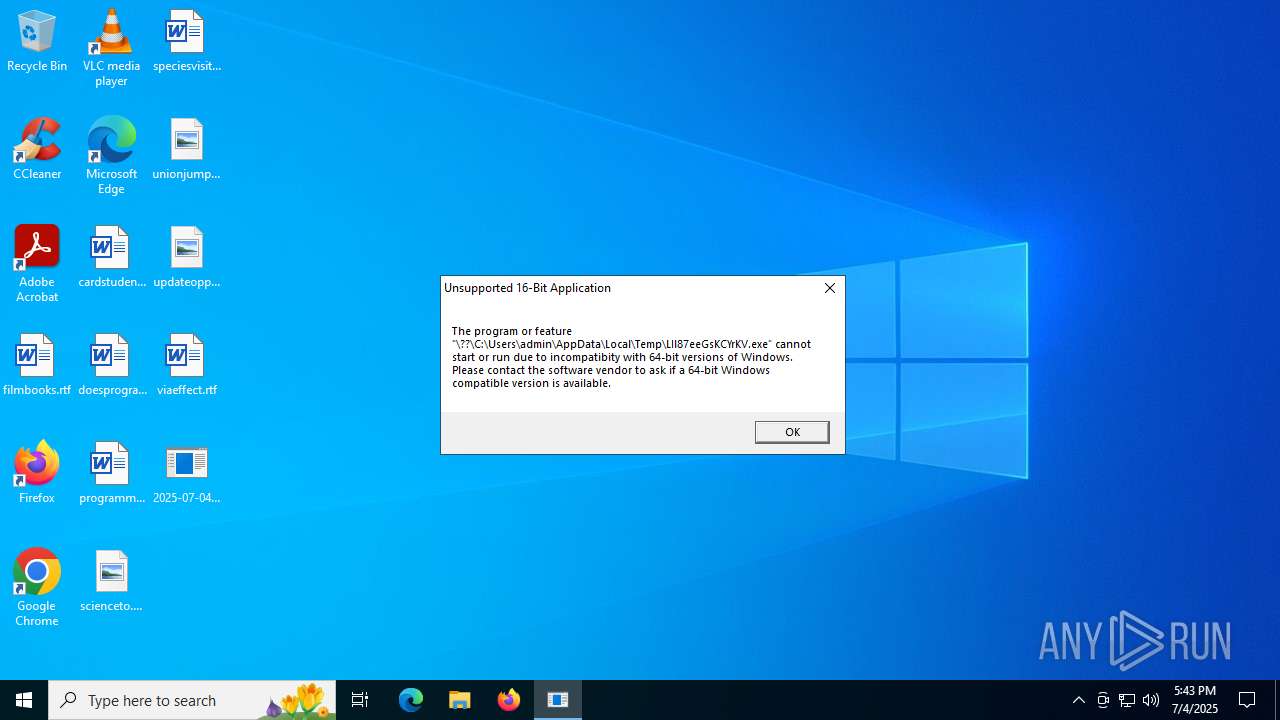
| 5768 | 2025-07-04_a1abf560f59533c62ca03ae69d77bbc9_bkransomware_elex_rhadamanthys.exe | C:\Users\admin\AppData\Local\Temp\LIl87eeGsKCYrKV.exe | binary | |
MD5:E1296DFE2CF3638C45F0CCFE213C538E | SHA256:45A432329D74D9A88AA6173A3E9BC951B52A0FDC0BF3FA2EBEB6413EF3B627E4 | |||
| 6768 | CTS.exe | C:\Users\admin\AppData\Local\dummy\officebackgroundtaskhandler.exe_c2rdll(20190323113912E90).log | executable | |
MD5:30D4A60D59D95F057D99FD9596FD0642 | SHA256:16A8B9E4B643F18EDE40F71EA63633453577D67987E192FF1CFCD9B37FC64053 | |||
| 6768 | CTS.exe | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\officesetup.exe_Rules.xml | executable | |
MD5:AC23831A20F6B1CDBF4EE43E002D957F | SHA256:FB106EB2F74D6422034E29EBECACC724307C6608B5AEB0ADE6D62D0F885EBBB6 | |||
| 6768 | CTS.exe | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\mspub.exe_Rules.xml | executable | |
MD5:2688CC9E9E0CFA985C1D667E569DECCB | SHA256:3E210AB8BE5F07FC19D2B42BC372692F660BBC88C8D20C895C3062655243554F | |||
| 6768 | CTS.exe | C:\Users\admin\AppData\Local\Microsoft\CLR_v4.0\UsageLogs\mmc.exe.log | executable | |
MD5:CD03C9C3EC8A1909992C58C5B5072861 | SHA256:BAE6295D9EFCFBE417E3E5ACA94CC63D4FF9F2D232F548326ACBE5A00C04723F | |||
| 6768 | CTS.exe | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\excel.exe_Rules.xml | executable | |
MD5:E5E0CDAF9AA459151DEE7B7152B3ABF0 | SHA256:8A0272EDDB711774837E3BB7DC8E6D559E84E052518D98DAF0084D70703B6E5A | |||
| 6768 | CTS.exe | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\setup.def.en-us_professional2019retail_04640089-6fb7-4a4d-ae33-18e0c4a879d8_tx_db_platform_def_.exe_Rules.xml | executable | |
MD5:FAC0D0ED933C2D22AC0433E1F167DD22 | SHA256:2A408477A63C6E9A533DCCA224B2D52DA4DAAD0B1ECD616BE71A1D707BCE14E5 | |||
| 6768 | CTS.exe | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\msaccess.exe_Rules.xml | executable | |
MD5:100D2CF767055C18937A0E9D715466AD | SHA256:CC91996B04DA592A413C4DE2AAD98671C0CD756D1B52295B51D0955FAA46B049 | |||
| 6768 | CTS.exe | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\sdxhelper.exe_Rules.xml | executable | |
MD5:3F0FE0881972E16B6F77C9DA1C5B3CF5 | SHA256:F65A3B4F500E7230468CF1C0BF6835B5AC8349258BF9FB560F75CCB273574032 | |||
| 6768 | CTS.exe | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\setuplanguagepack.x64.de-de_.exe_Rules.xml | executable | |
MD5:4626FA5DC3D9D18FF65928A8B58E5F04 | SHA256:295ACDF32A31D9325C9AC26F6B9D07FC4D1B1B31ACE7F98AD61D328109C1200D | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
21
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4100 | RUXIMICS.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4100 | RUXIMICS.exe | GET | 200 | 23.48.23.190:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.190:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4100 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4100 | RUXIMICS.exe | 23.48.23.190:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.48.23.190:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4100 | RUXIMICS.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |