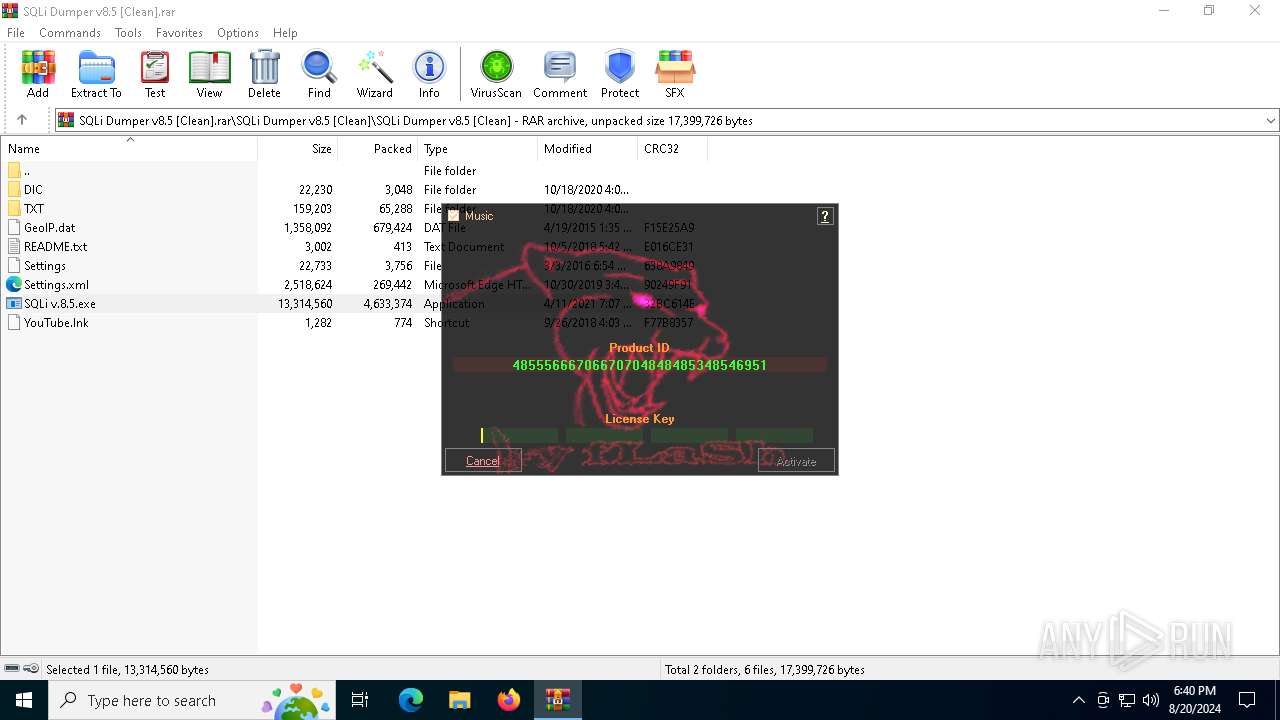
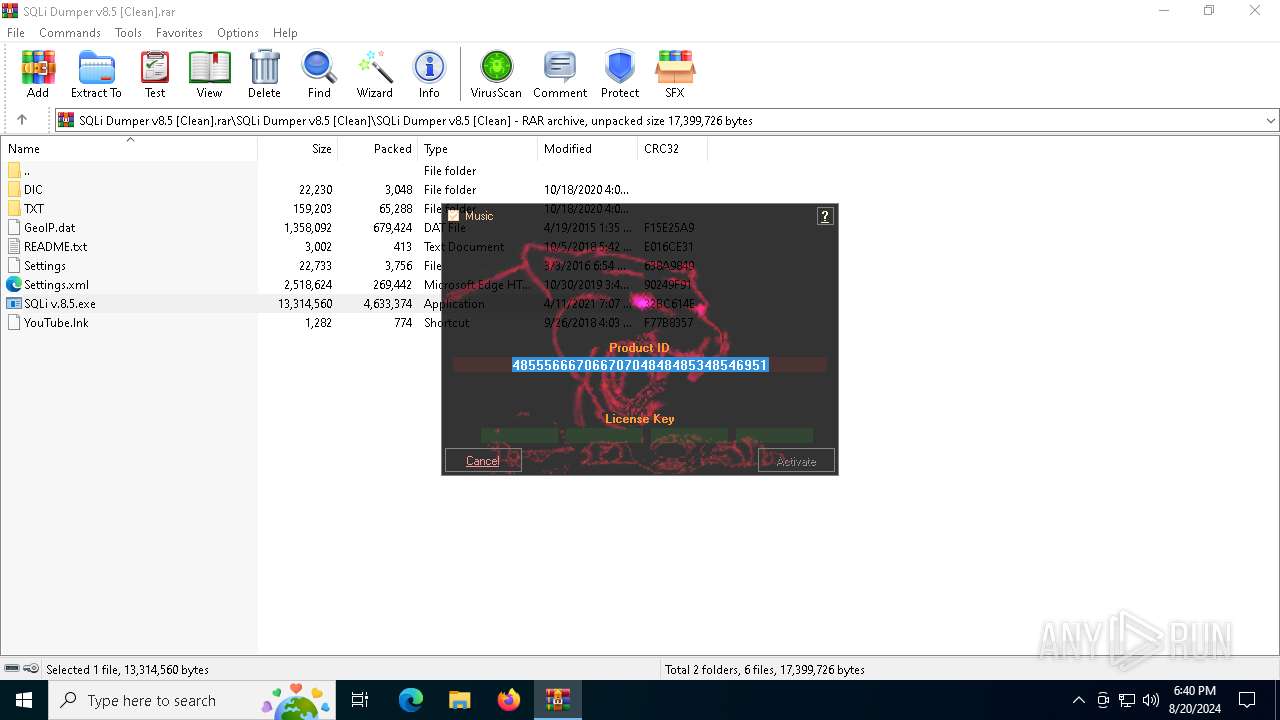
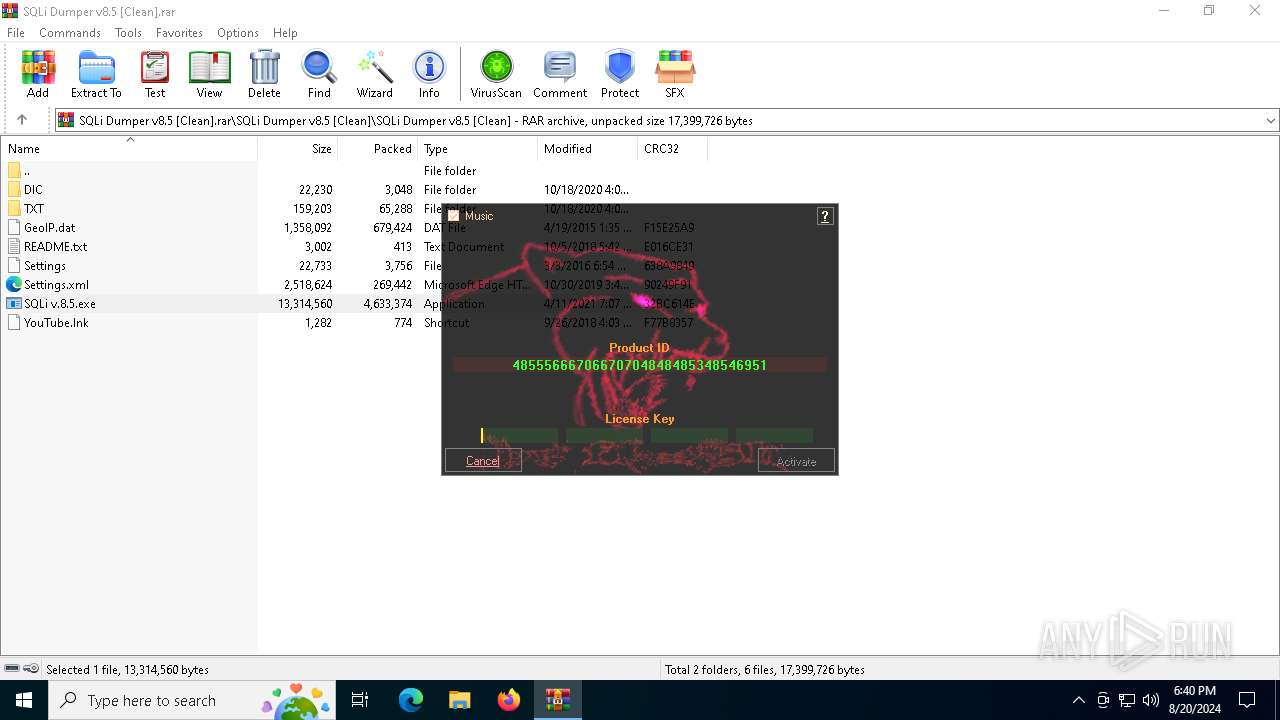
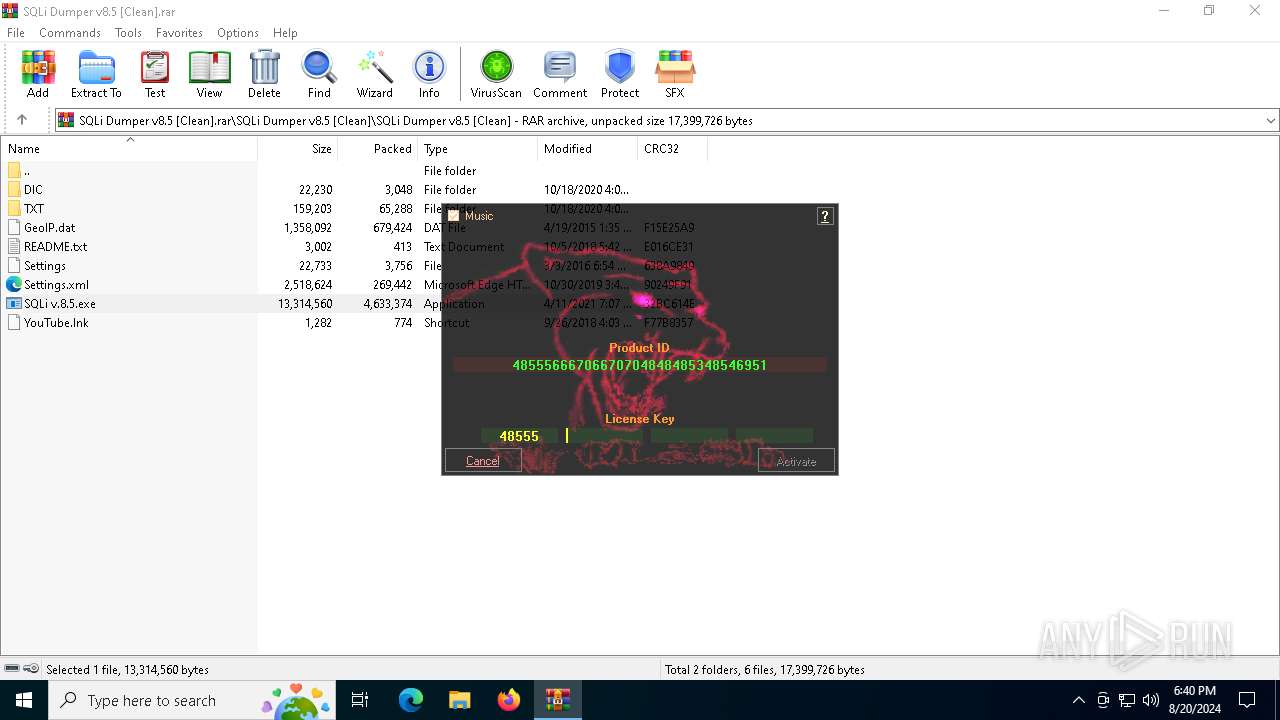
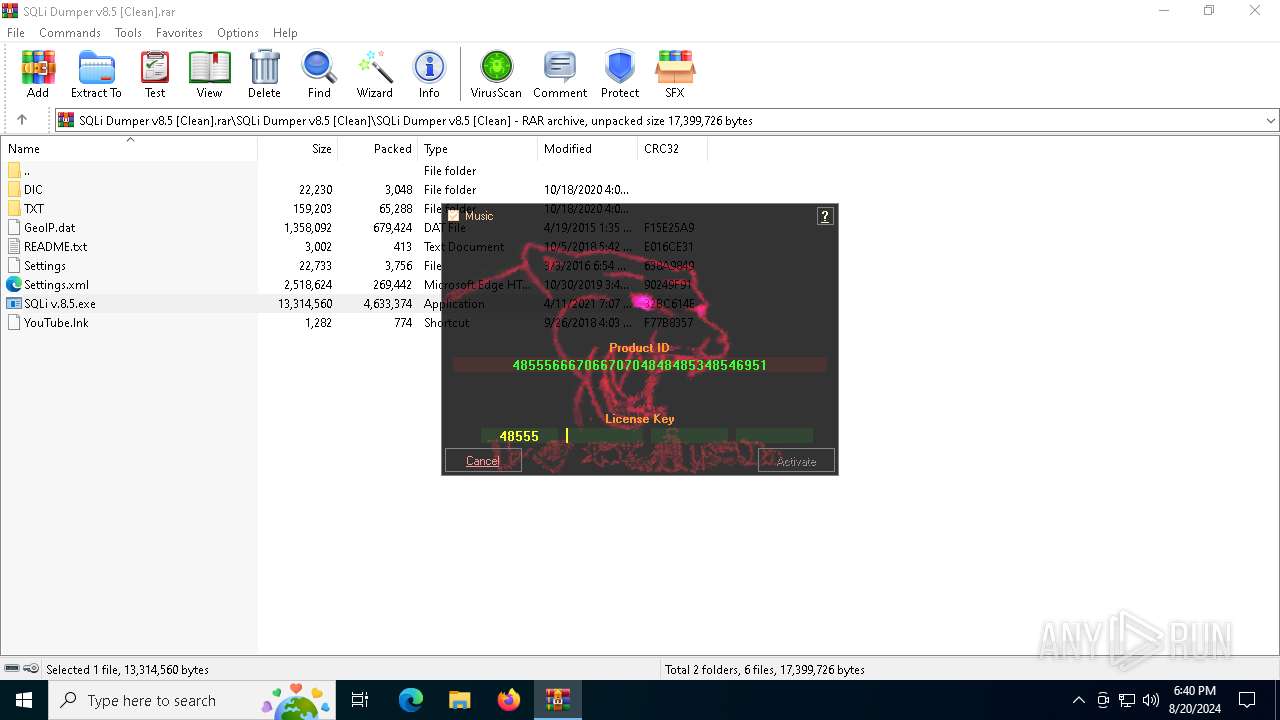
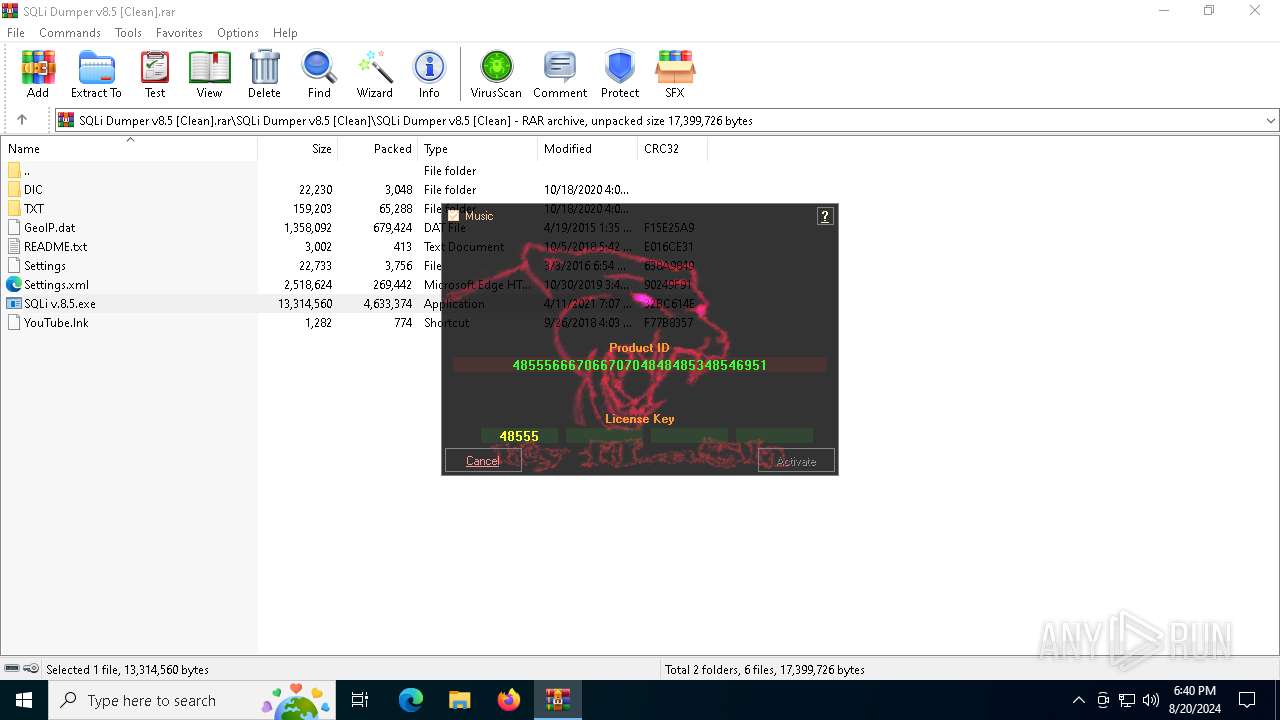
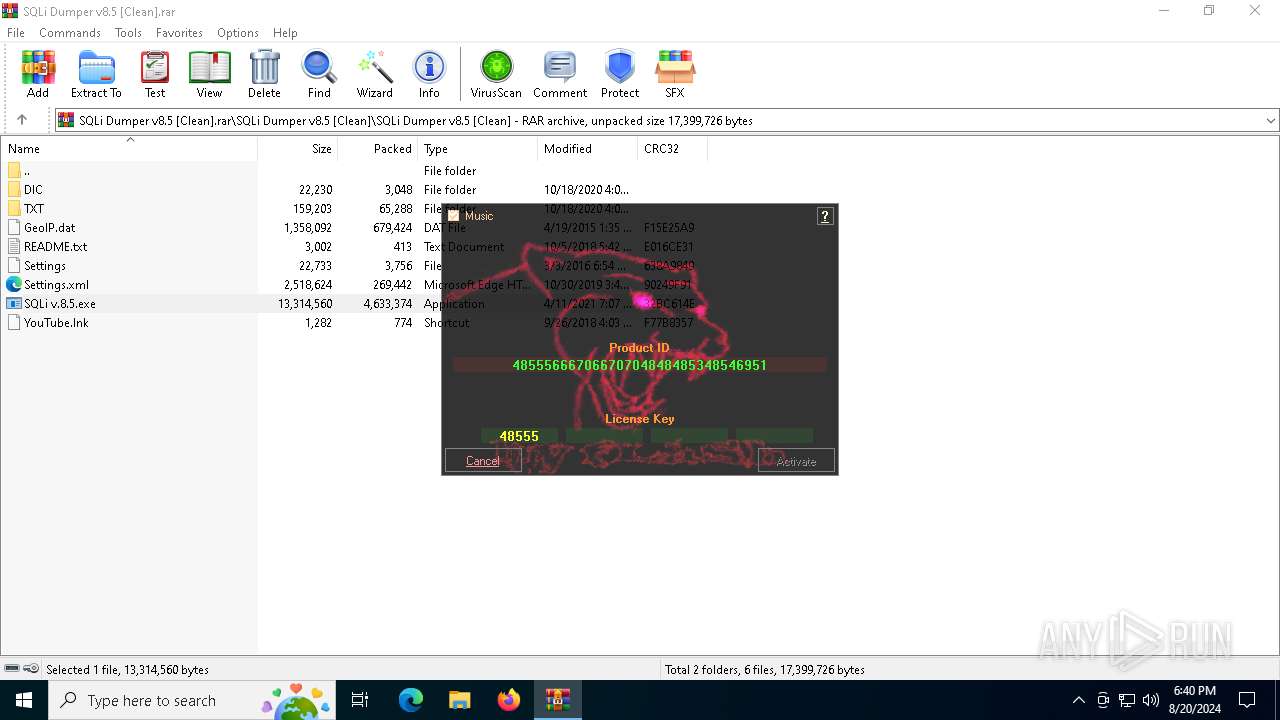
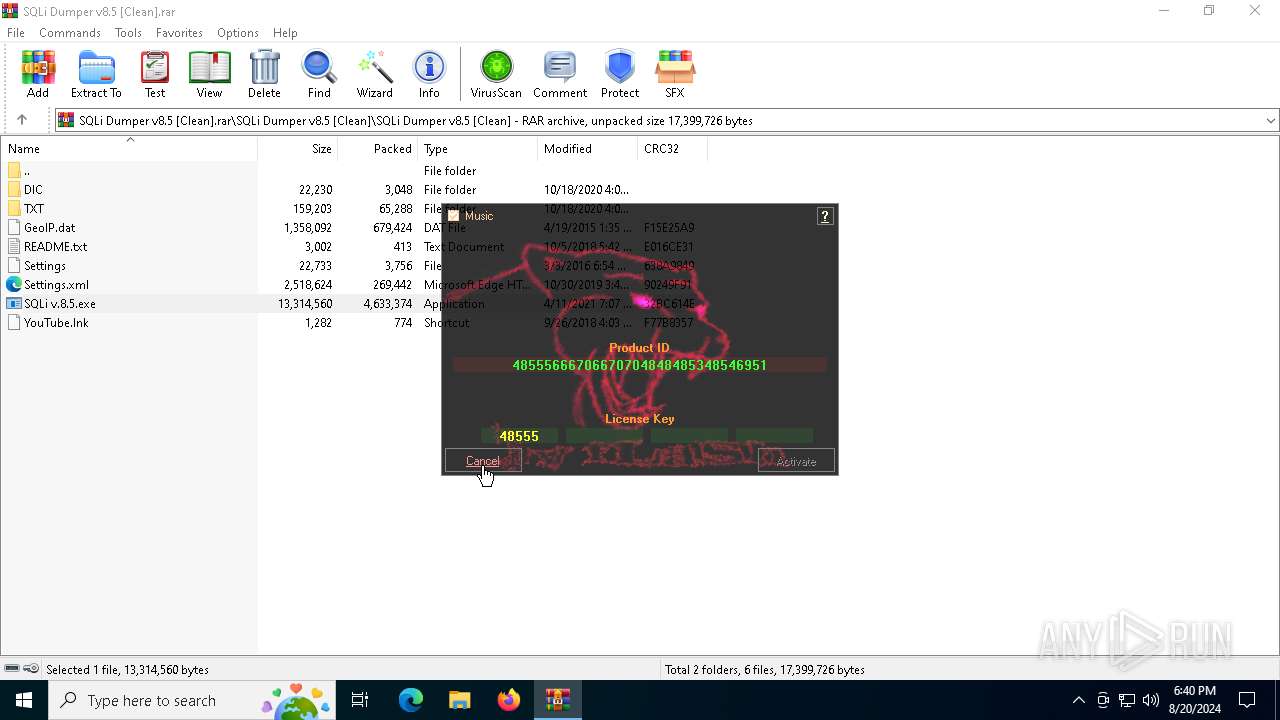
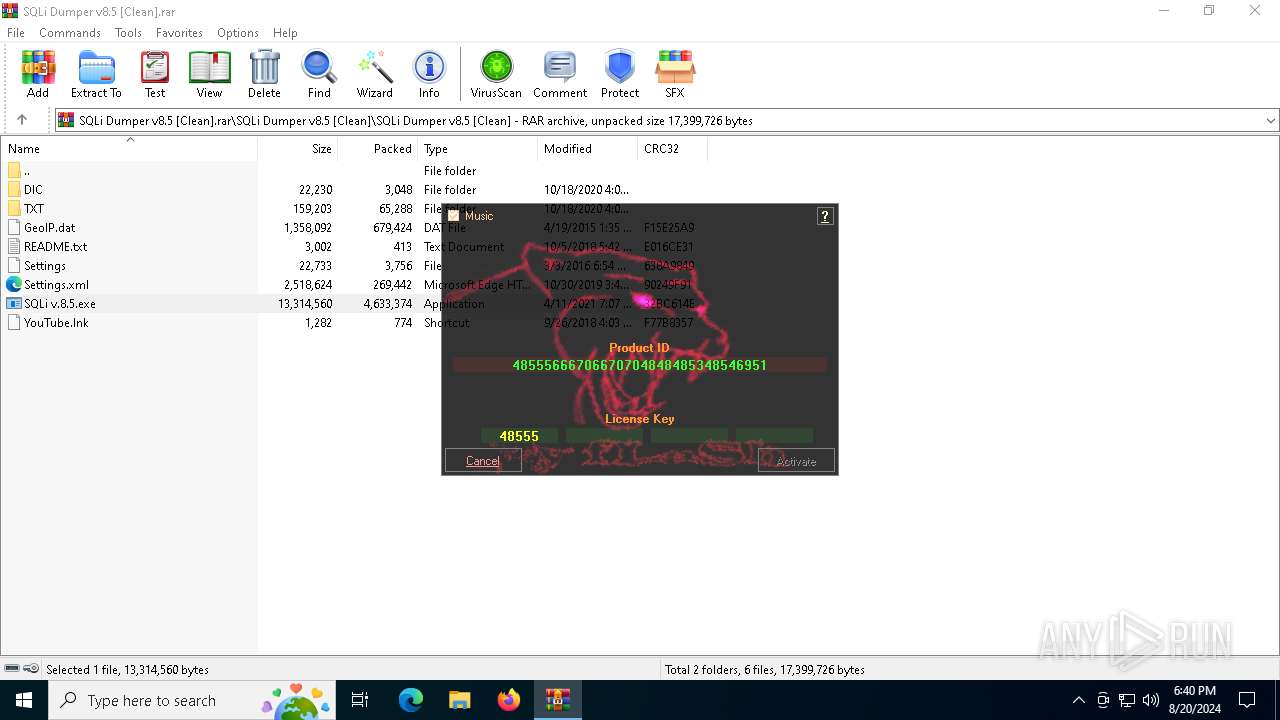
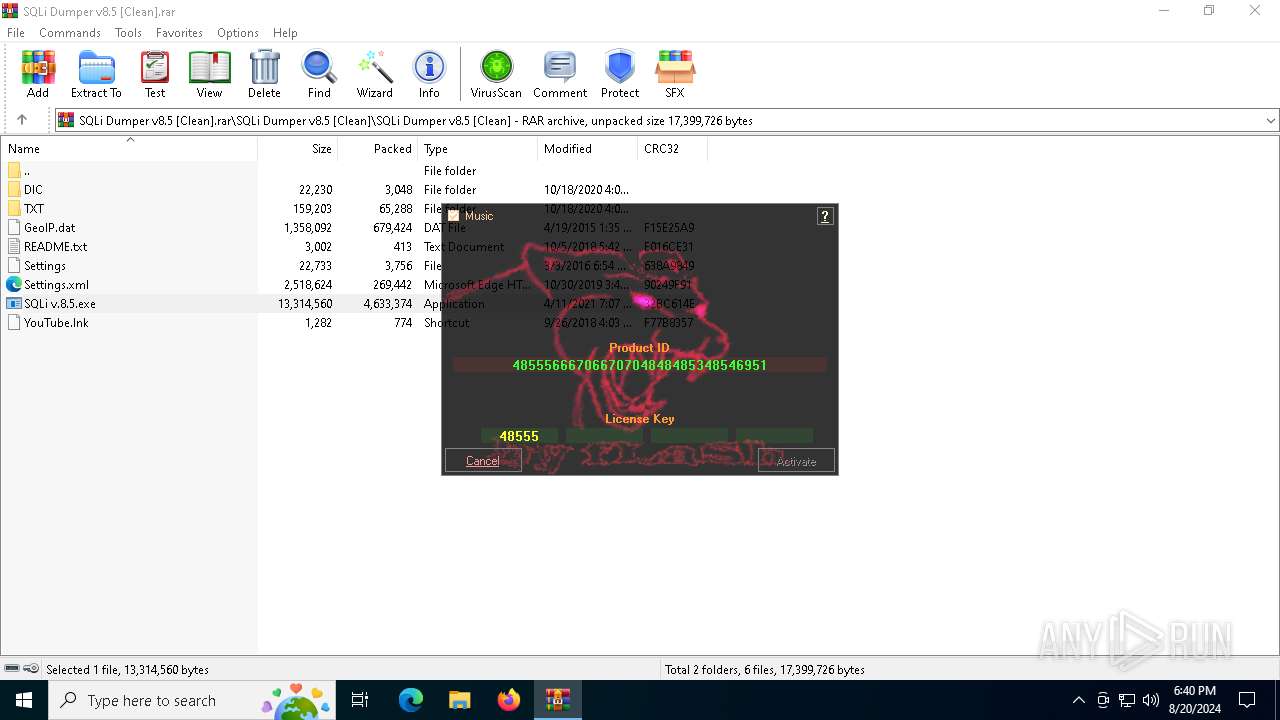
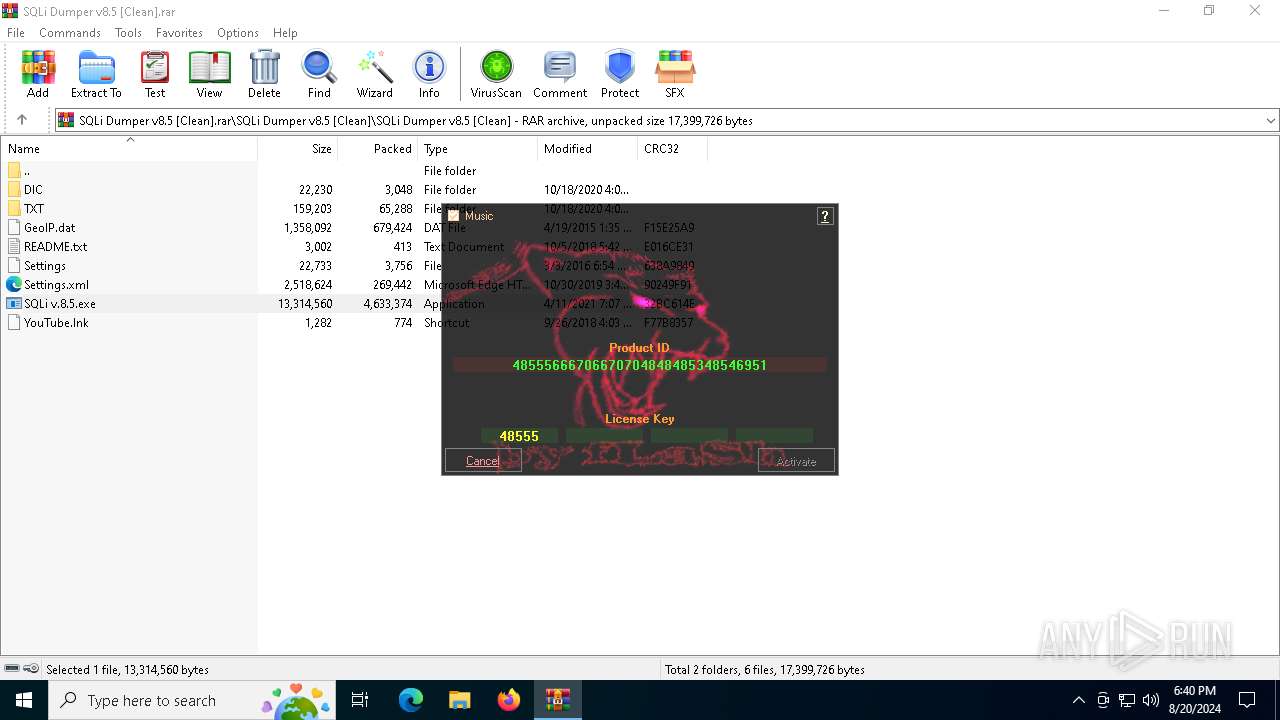
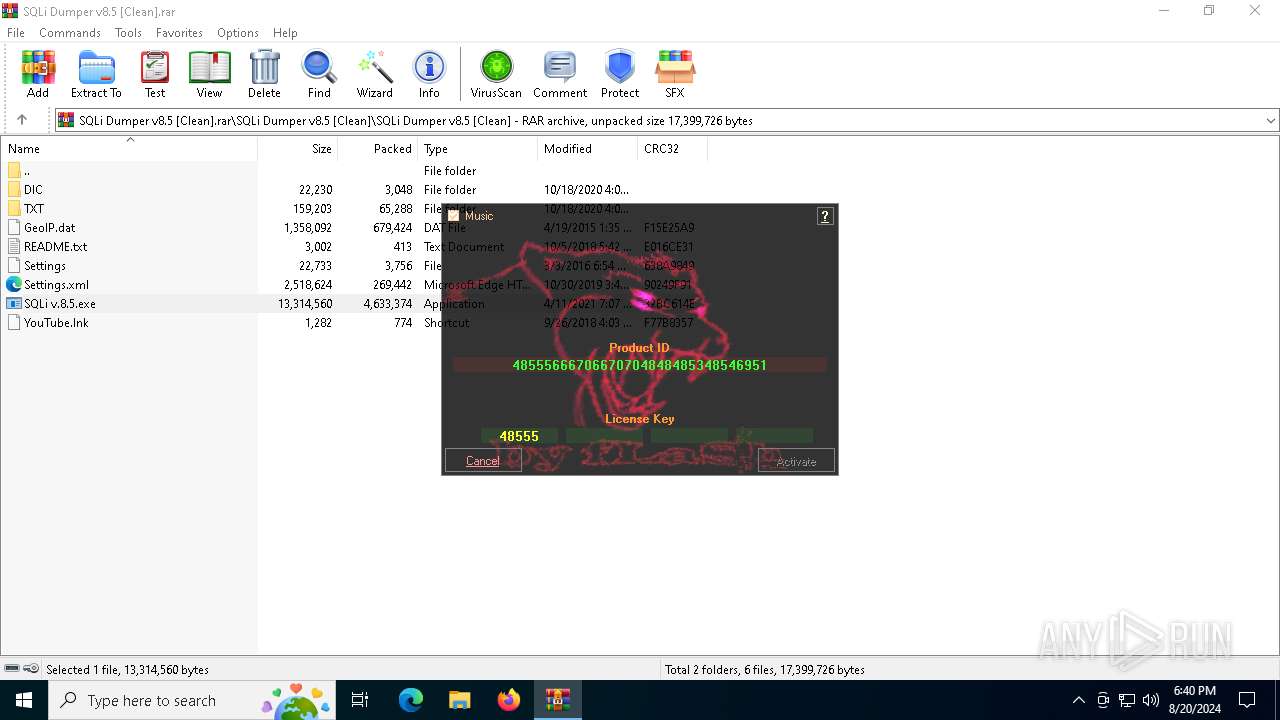
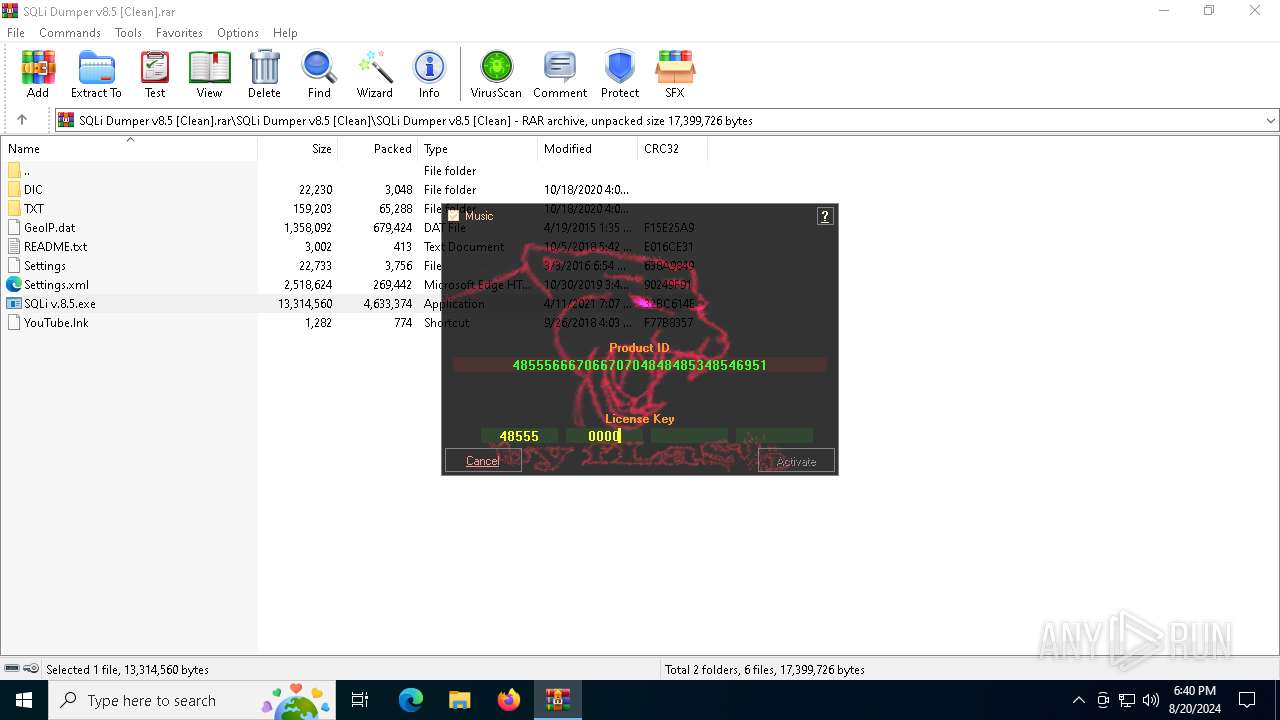
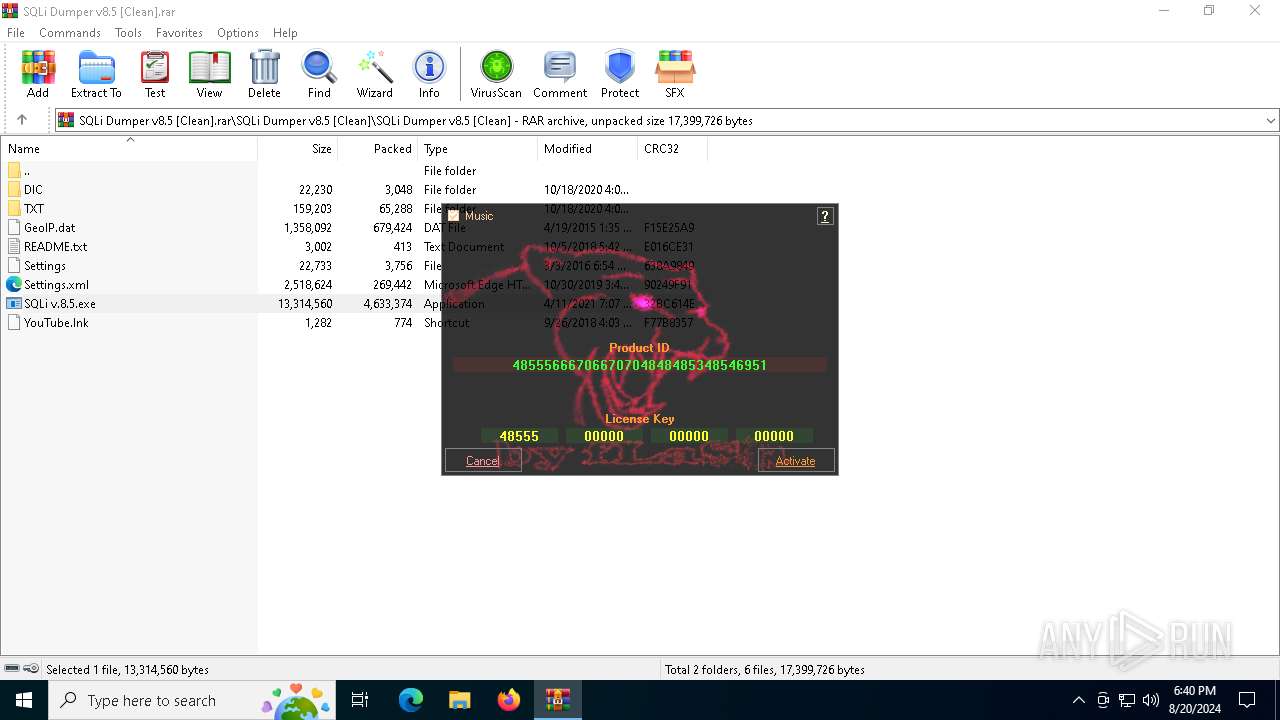
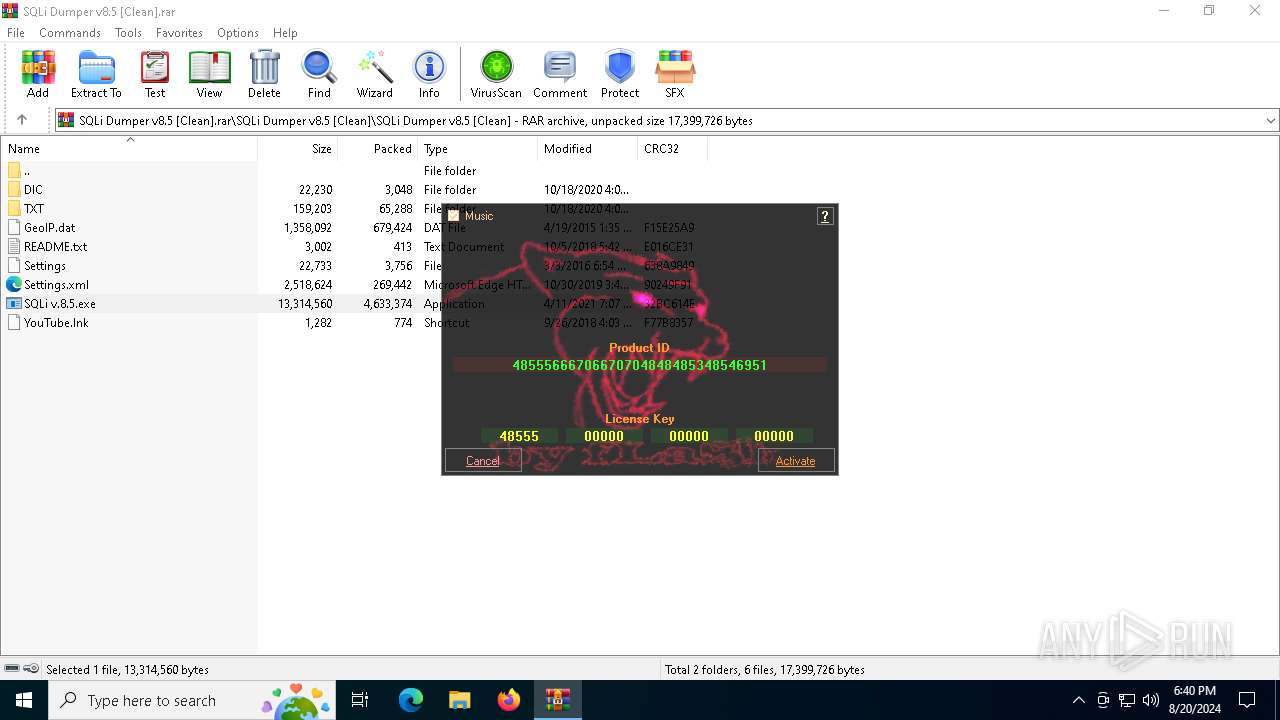
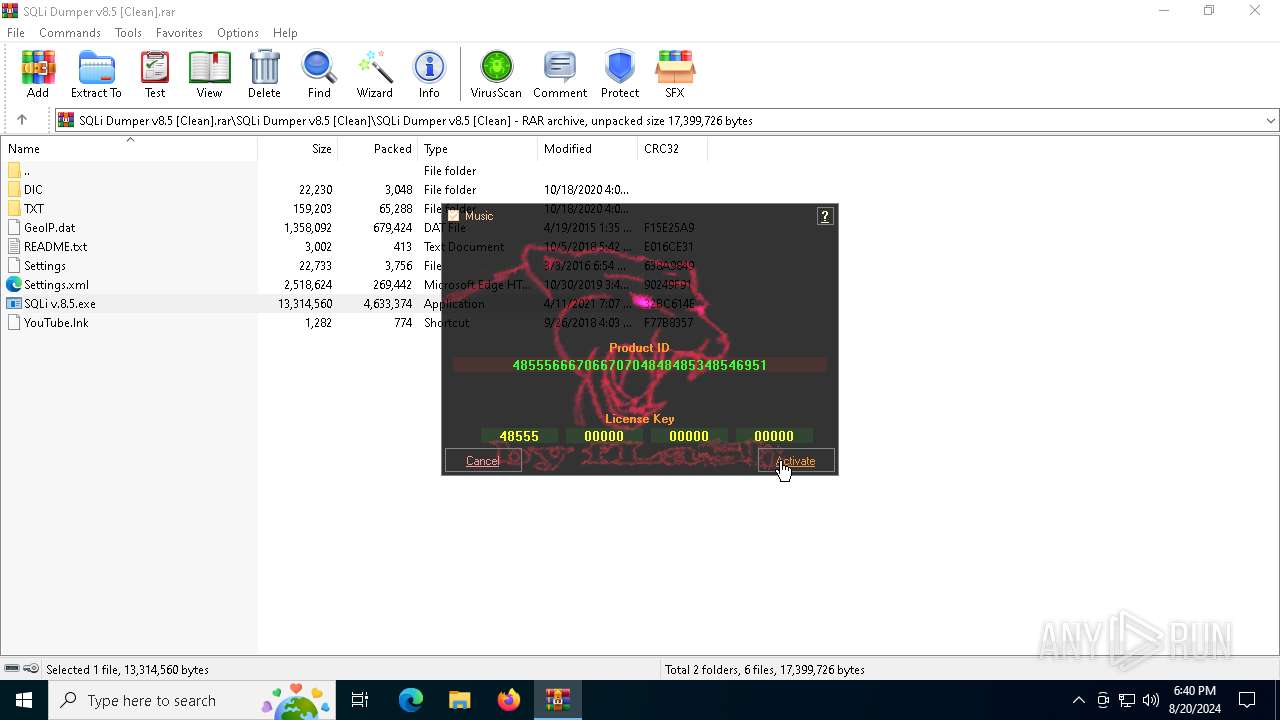
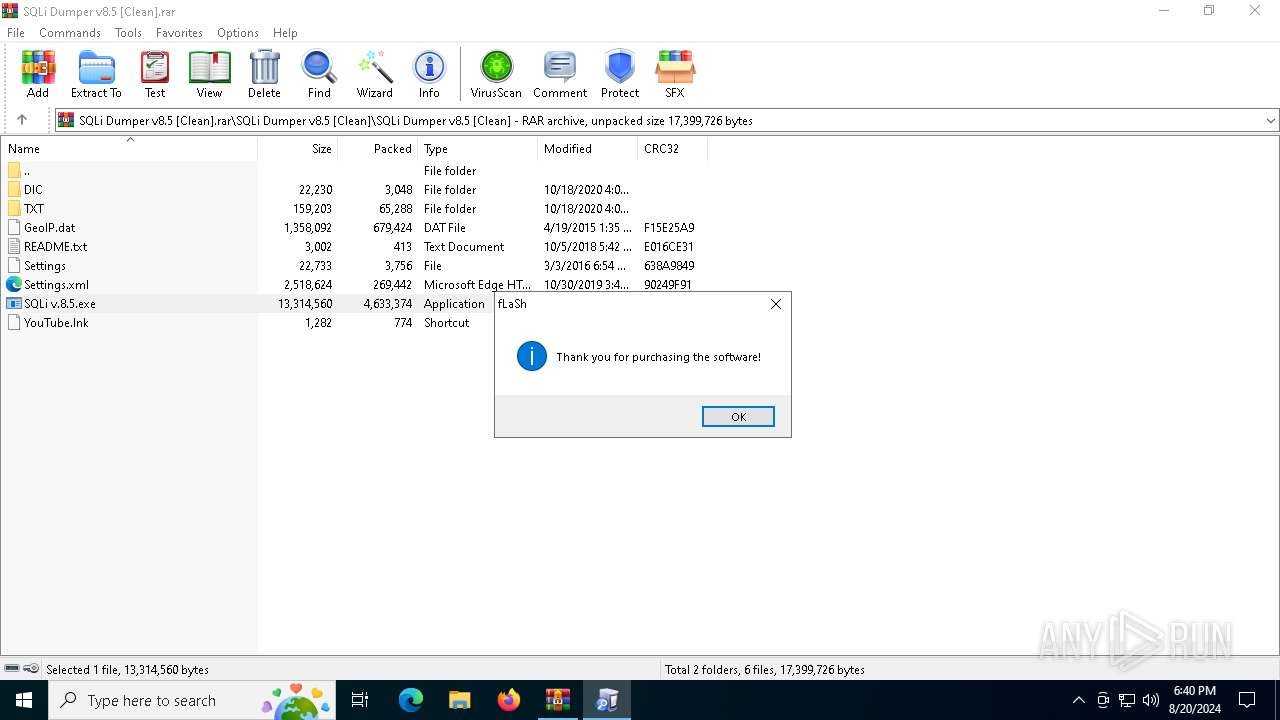
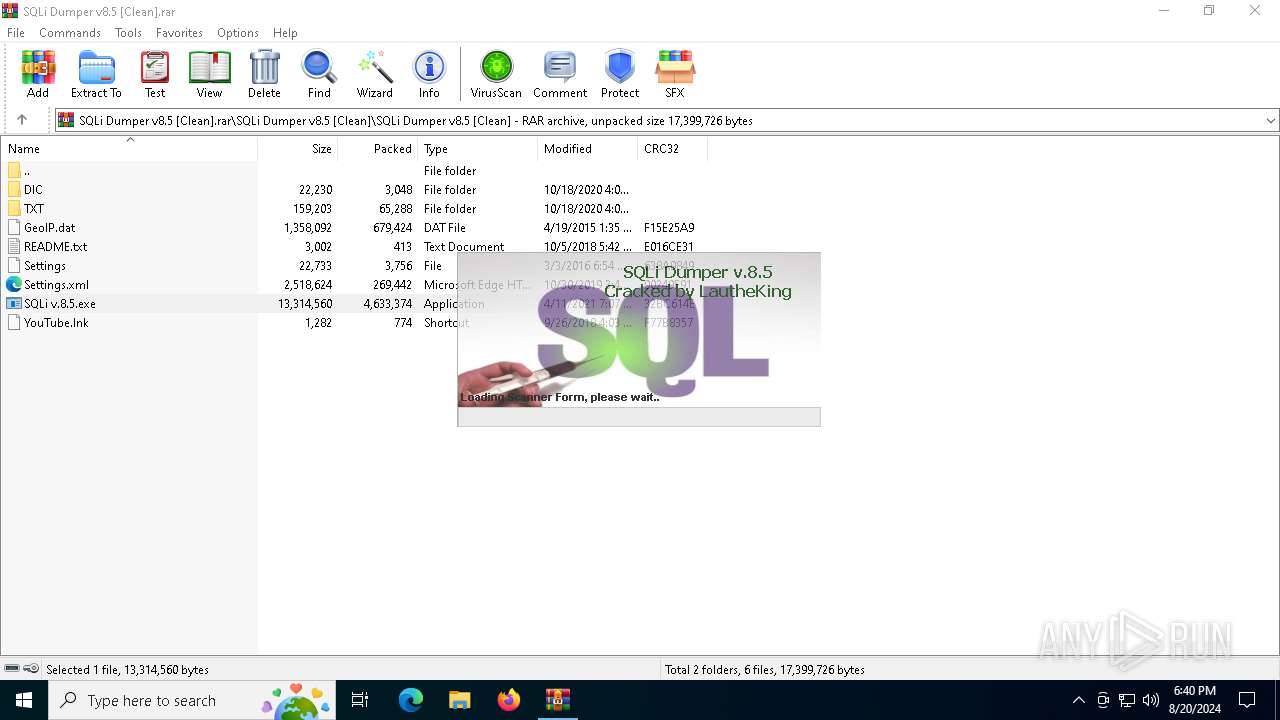
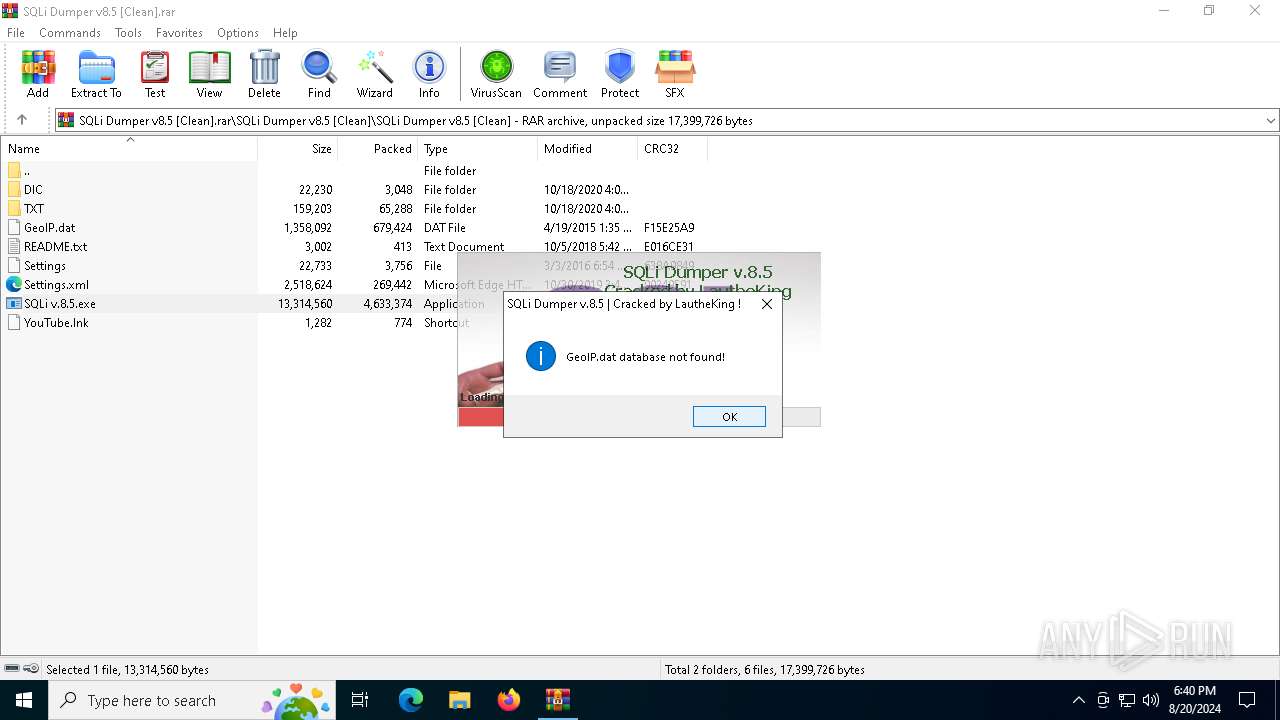
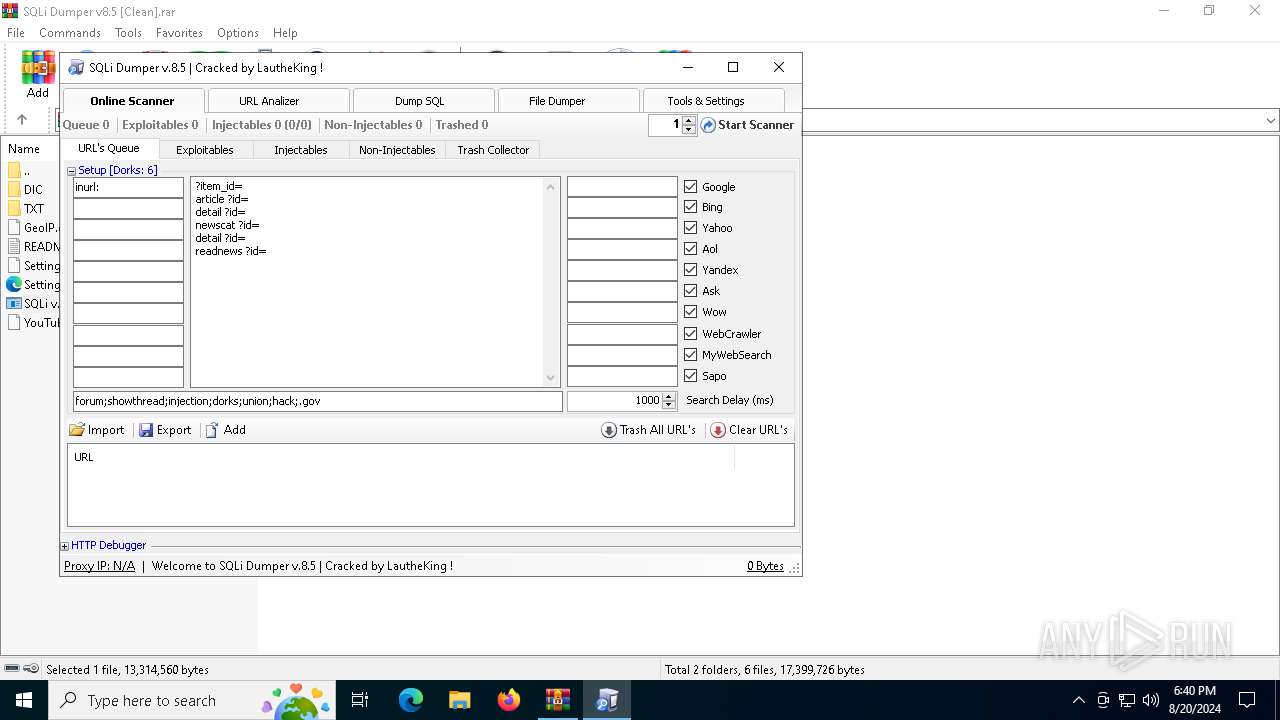
| File name: | SQLi Dumper v8.5 [Clean].rar |
| Full analysis: | https://app.any.run/tasks/5a5e5e46-1e70-43f5-8de4-3468e979229f |
| Verdict: | Malicious activity |
| Analysis date: | August 20, 2024, 18:39:41 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | D91BE36F8618562C808FB80F358591F7 |
| SHA1: | BBC665A912CF0CA2255B6D2090EA7C1461429726 |
| SHA256: | 5E38BC98D4ECBEEEE7DE498244406B801BF0FE12AFF0C5D92307BE40B4CEECE1 |
| SSDEEP: | 98304:D3c6n8TWWOjAt+i5DQ5GN6JCrTs1FIu0DK+TkBJOpVHiT8kCFPlEx7BEipybvZ8u:j8A0tLxR+W |
MALICIOUS
Changes the autorun value in the registry
- pebloso.exe (PID: 3176)
BITRAT has been detected (YARA)
- pebloso.exe (PID: 6824)
SUSPICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 6968)
- SQLi v.8.5.exe (PID: 6516)
- pebloso.exe (PID: 3176)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6968)
- SQLi v.8.5.exe (PID: 6516)
- 0.exe (PID: 6488)
Executable content was dropped or overwritten
- SQLi v.8.5.exe (PID: 6516)
- pebloso.exe (PID: 3176)
Application launched itself
- pebloso.exe (PID: 3176)
Detected use of alternative data streams (AltDS)
- pebloso.exe (PID: 6824)
Reads Internet Explorer settings
- 0.exe (PID: 6488)
Reads Microsoft Outlook installation path
- 0.exe (PID: 6488)
Reads the date of Windows installation
- SQLi v.8.5.exe (PID: 6516)
INFO
Checks supported languages
- pebloso.exe (PID: 3176)
- SQLi v.8.5.exe (PID: 6516)
- pebloso.exe (PID: 6824)
- 0.exe (PID: 6488)
Reads Environment values
- 0.exe (PID: 6488)
Disables trace logs
- 0.exe (PID: 6488)
Checks proxy server information
- SQLi v.8.5.exe (PID: 6516)
- 0.exe (PID: 6488)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6968)
Reads the computer name
- SQLi v.8.5.exe (PID: 6516)
- pebloso.exe (PID: 6824)
- 0.exe (PID: 6488)
- pebloso.exe (PID: 3176)
Create files in a temporary directory
- SQLi v.8.5.exe (PID: 6516)
- pebloso.exe (PID: 3176)
- 0.exe (PID: 6488)
Process checks Internet Explorer phishing filters
- 0.exe (PID: 6488)
Creates files or folders in the user directory
- pebloso.exe (PID: 6824)
Reads the software policy settings
- 0.exe (PID: 6488)
UPX packer has been detected
- pebloso.exe (PID: 6824)
Process checks computer location settings
- SQLi v.8.5.exe (PID: 6516)
Reads the machine GUID from the registry
- 0.exe (PID: 6488)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
129
Monitored processes
5
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3176 | "C:\Users\admin\AppData\Local\Temp\pebloso.exe" | C:\Users\admin\AppData\Local\Temp\pebloso.exe | SQLi v.8.5.exe | ||||||||||||
User: admin Company: ekzoboko Integrity Level: MEDIUM Description: werwiksdi Exit code: 0 Version: 1.1.2.3 Modules
| |||||||||||||||
| 6488 | "C:\Users\admin\AppData\Local\Temp\0.exe" | C:\Users\admin\AppData\Local\Temp\0.exe | SQLi v.8.5.exe | ||||||||||||
User: admin Company: SQLi Trush Corp Integrity Level: MEDIUM Description: SQLi Dumper v8.0 Version: 8.0.0.0 Modules
| |||||||||||||||
| 6516 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6968.771\SQLi Dumper v8.5 [Clean]\SQLi Dumper v8.5 [Clean]\SQLi v.8.5.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6968.771\SQLi Dumper v8.5 [Clean]\SQLi Dumper v8.5 [Clean]\SQLi v.8.5.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: barboroy Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 6824 | "C:\Users\admin\AppData\Local\Temp\pebloso.exe" | C:\Users\admin\AppData\Local\Temp\pebloso.exe | pebloso.exe | ||||||||||||
User: admin Company: ekzoboko Integrity Level: MEDIUM Description: werwiksdi Version: 1.1.2.3 Modules
| |||||||||||||||
| 6968 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\SQLi Dumper v8.5 [Clean].rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
15 985
Read events
15 933
Write events
50
Delete events
2
Modification events
| (PID) Process: | (6968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\SQLi Dumper v8.5 [Clean].rar | |||
| (PID) Process: | (6968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6968) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
4
Suspicious files
2
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6516 | SQLi v.8.5.exe | C:\Users\admin\AppData\Local\Temp\0.exe | executable | |
MD5:F558500B09118C2D5482C0097D41B986 | SHA256:4081A78BA280D28C56551983E515486A1DACF9BA26A3E76A71060982CC9E5ED7 | |||
| 6968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6968.771\SQLi Dumper v8.5 [Clean]\SQLi Dumper v8.5 [Clean]\Settings.xml | xml | |
MD5:F4291A1ABBE4073316788FB7C05F0BD8 | SHA256:D40E5B12D2E39D64A819FB50C20C4A740237E9C908338359059AB9BF79656BF9 | |||
| 6968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6968.771\SQLi Dumper v8.5 [Clean]\SQLi Dumper v8.5 [Clean]\Settings | xml | |
MD5:6CADCD28429156CBC1D77447BBDDDF42 | SHA256:88AD0488FE62D131F1CA29A7DE9470038E436F33F76CE1A83D6B41BDF3DC6C7C | |||
| 6968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6968.771\SQLi Dumper v8.5 [Clean]\SQLi Dumper v8.5 [Clean]\GeoIP.dat | binary | |
MD5:CB9AD69965F9F4CFF8572983F60BE67C | SHA256:56C7079DC309168D9C41DD4A7A61033ACD264A120CA8D2E2182ABB5B9AE6B0A3 | |||
| 6968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6968.771\SQLi Dumper v8.5 [Clean]\SQLi Dumper v8.5 [Clean]\TXT\URL NonInjectables.xml | xml | |
MD5:796F81553D4C28791127DF6F10CAFA2D | SHA256:AE5B6A2A6389D8323428DA34D762A4EFB9E292598765B5AE719BB9C3FBB9D802 | |||
| 6968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6968.771\SQLi Dumper v8.5 [Clean]\SQLi Dumper v8.5 [Clean]\YouTube.lnk | lnk | |
MD5:686C7F583EA8B588077A0CE49F4DAB41 | SHA256:E18918CE19299F7EF793997D91DFC7CEDD2D2691B1B28628595F026954B8AD80 | |||
| 6968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6968.771\SQLi Dumper v8.5 [Clean]\SQLi Dumper v8.5 [Clean]\SQLi v.8.5.exe | executable | |
MD5:D887C03A2D230DC196C8B3AC47030B9E | SHA256:B693010F3F342FB06DD959F2553B7937D5DAEAF9B4B7FD800ED5A9A6D8A099E7 | |||
| 6488 | 0.exe | C:\Users\admin\AppData\Local\Temp\DIC\dic_file_dump.txt | text | |
MD5:351CACFFC2884FCD4E69BB1FB04DDEB5 | SHA256:C67BCC0B4ED5E5EF72AA1134C0838D9201A97C2BF462FDFF0AC9052A53B286A2 | |||
| 6968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6968.771\SQLi Dumper v8.5 [Clean]\SQLi Dumper v8.5 [Clean]\TXT\URL Injectables.xml | xml | |
MD5:50E7BB8DE761C3E86334E5A79ECFBDF3 | SHA256:16ED017A419D044A75CBA55EDCFE216BD69BADB47950A909D8523921C5489FE4 | |||
| 6968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6968.771\SQLi Dumper v8.5 [Clean]\SQLi Dumper v8.5 [Clean]\TXT\URL Trash.txt | text | |
MD5:DD0FFD123520876006ECFC59FA5F009B | SHA256:13779619EDA4B83DAAF5DE5E91AE3A363D88D391B646B6A1203CD5305D401C28 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
53
DNS requests
26
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6488 | 0.exe | GET | 404 | 104.20.3.235:80 | http://pastebin.com/raw/3vsJLpWu | unknown | — | — | shared |
6488 | 0.exe | GET | 404 | 151.101.130.114:80 | http://www.ask.com/web?q=%3fitem_id%3d | unknown | — | — | whitelisted |
6488 | 0.exe | GET | 404 | 212.82.100.137:80 | http://search.aol.com/aol/search?&q=%3fitem_id%3d | unknown | — | — | whitelisted |
6488 | 0.exe | GET | 404 | 213.13.145.10:80 | http://pesquisa.sapo.pt/?q=%3fitem_id%3d | unknown | — | — | whitelisted |
6488 | 0.exe | GET | 404 | 77.88.55.88:80 | http://www.yandex.com/yandsearch?text=%3fitem_id%3d | unknown | — | — | whitelisted |
6488 | 0.exe | GET | 404 | 13.107.21.200:80 | http://www.bing.com/search?q=%3fitem_id%3d&count=50 | unknown | — | — | whitelisted |
6488 | 0.exe | GET | 404 | 172.64.151.32:80 | http://www.webcrawler.com/search/web?q=%3fitem_id%3d | unknown | — | — | whitelisted |
6488 | 0.exe | GET | 404 | 213.13.145.10:80 | http://pesquisa.sapo.pt/?q=%3fitem_id%3d | unknown | — | — | whitelisted |
6488 | 0.exe | GET | 404 | 13.107.21.200:80 | http://www.bing.com/search?q=%3fitem_id%3d&count=50 | unknown | — | — | whitelisted |
6488 | 0.exe | GET | 404 | 77.88.55.88:80 | http://www.yandex.com/yandsearch?text=%3fitem_id%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2480 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2480 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6488 | 0.exe | 104.20.3.235:80 | pastebin.com | CLOUDFLARENET | — | unknown |
6824 | pebloso.exe | 80.85.156.209:8080 | — | Chelyabinsk-Signal LLC | RU | malicious |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
pastebin.com |
| shared |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
arc.msn.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
171.39.242.20.in-addr.arpa |
| unknown |
4.8.2.0.0.0.0.0.0.0.0.0.0.0.0.0.2.0.0.0.2.0.c.0.0.3.0.1.3.0.6.2.ip6.arpa |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2256 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
1 ETPRO signatures available at the full report