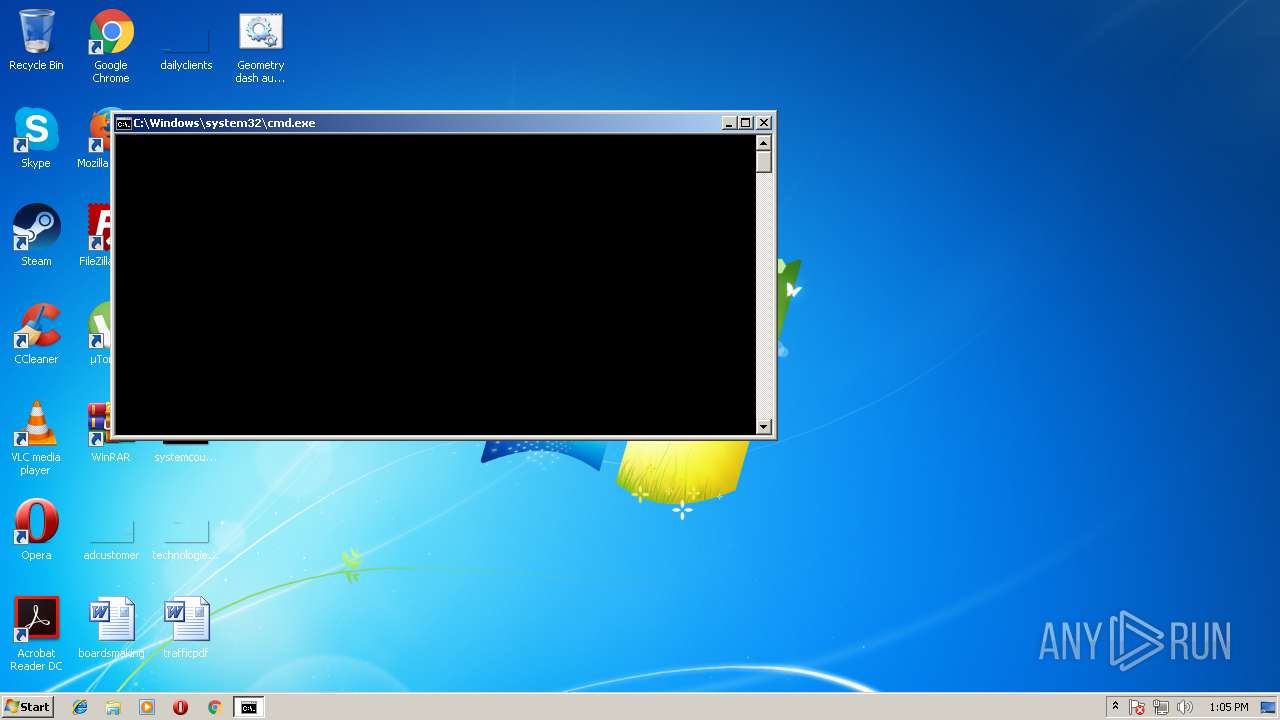
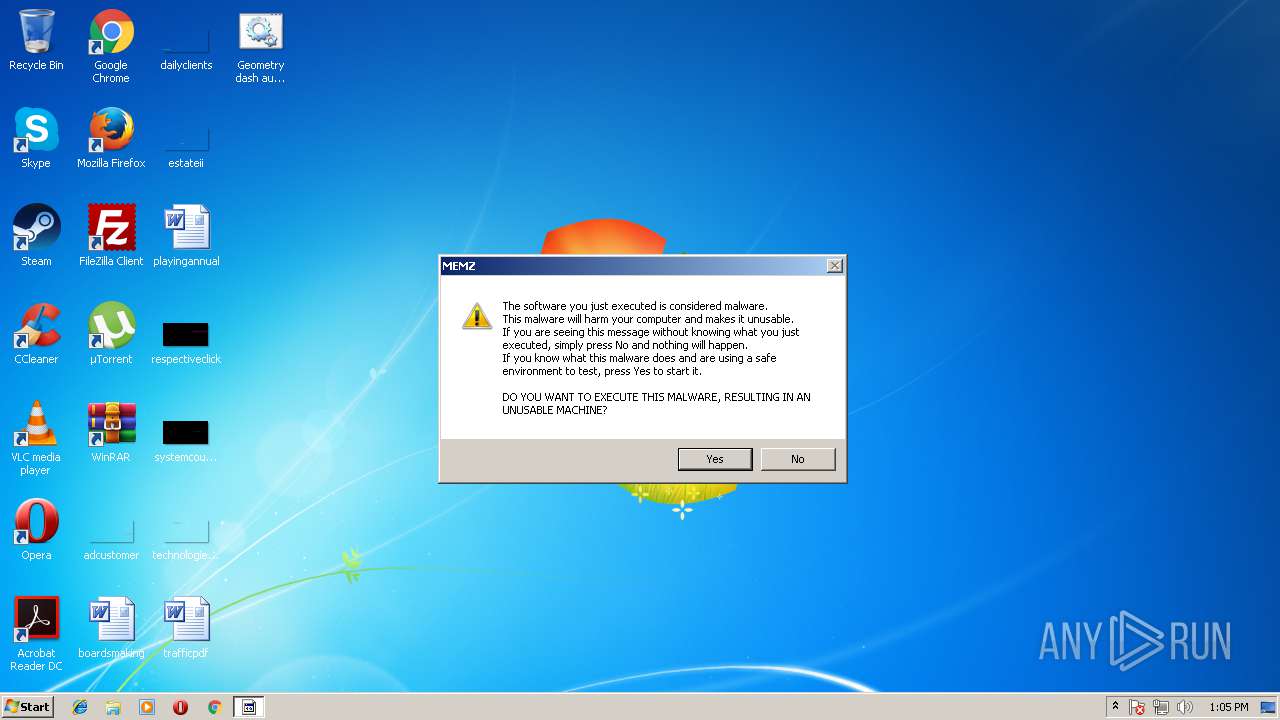
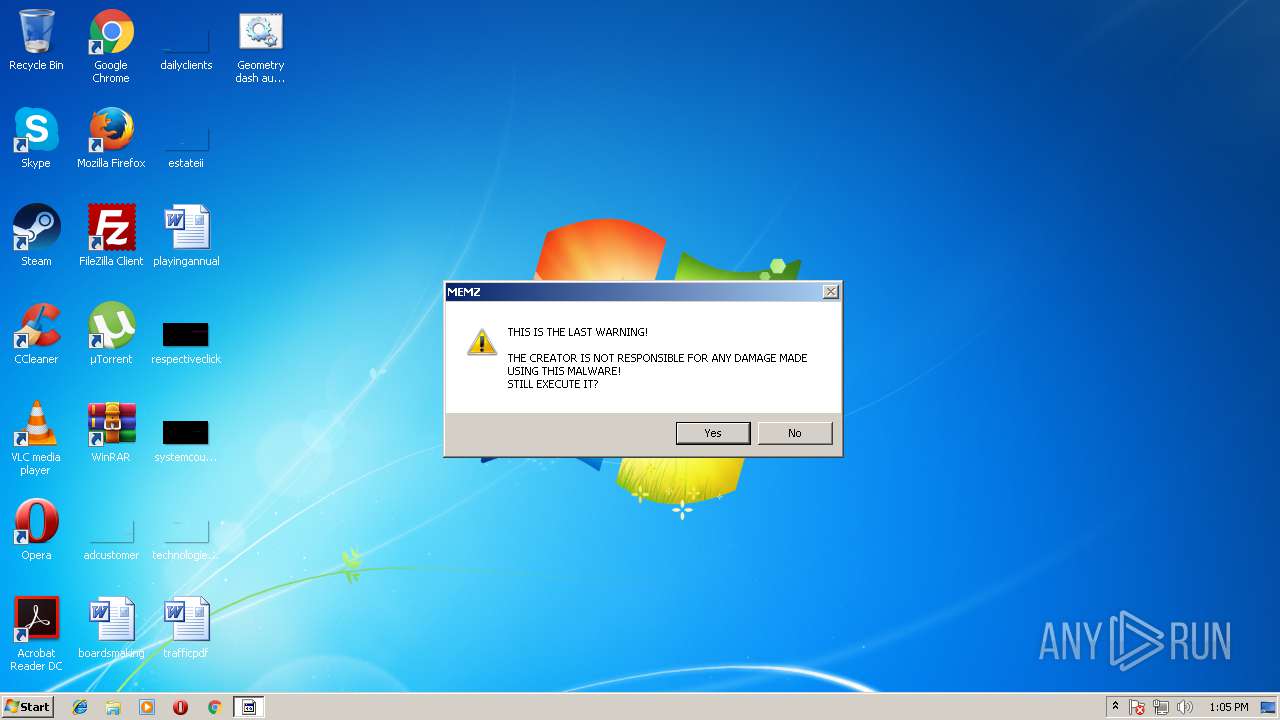
| File name: | Geometry dash auto speedhack.bat |
| Full analysis: | https://app.any.run/tasks/fdf3e03b-ba59-4fe2-b5b9-430a18391ab6 |
| Verdict: | Malicious activity |
| Analysis date: | August 04, 2018, 12:05:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with CRLF line terminators |
| MD5: | 4E2A7F369378A76D1DF4D8C448F712AF |
| SHA1: | 1192B4D01254A8704E6D6AE17DC2EC28A7AD5A49 |
| SHA256: | 5E2CD213FF47B7657ABD9167C38FFD8B53C13261FE22ADDDEA92B5A2D9E320AD |
| SSDEEP: | 192:AOyUySl0UaDz2gWsIzlmj+BxZ3yqueWQx0lZicyC8Sh31xcjBzyxwn7AVhllz3:AVODaDSHMql3yqlxy5L1xcjwrlz3 |
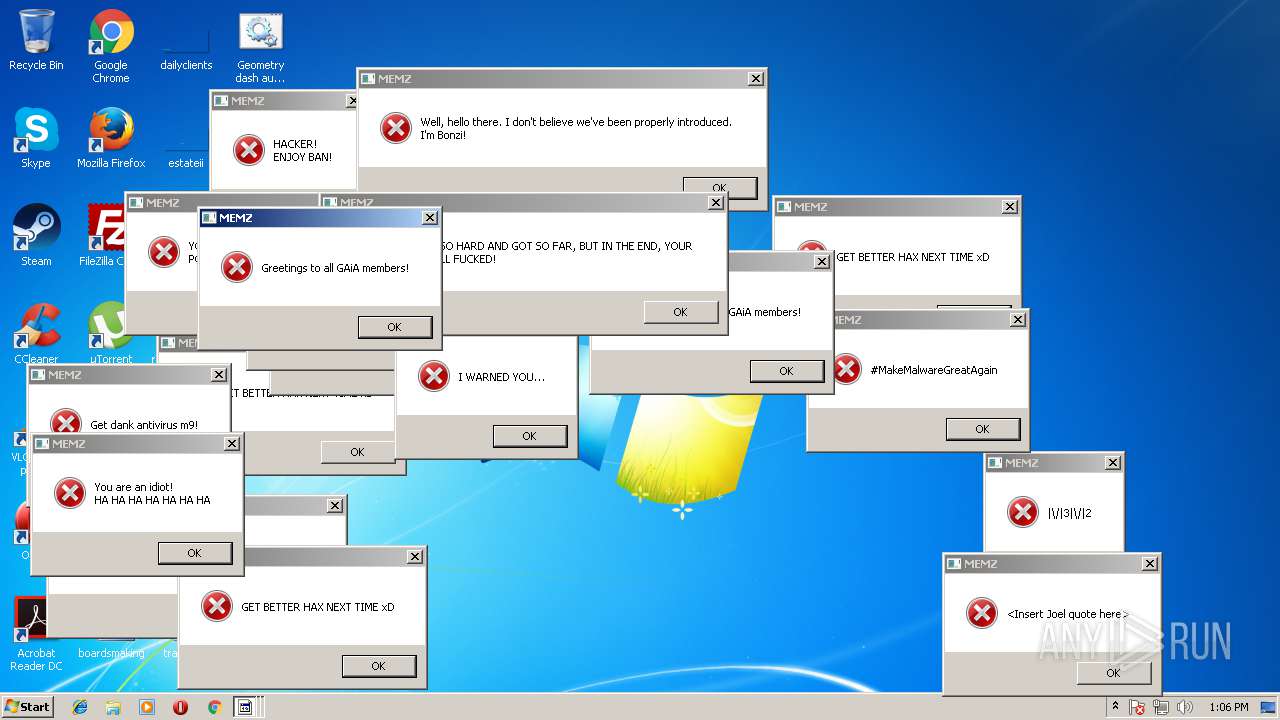
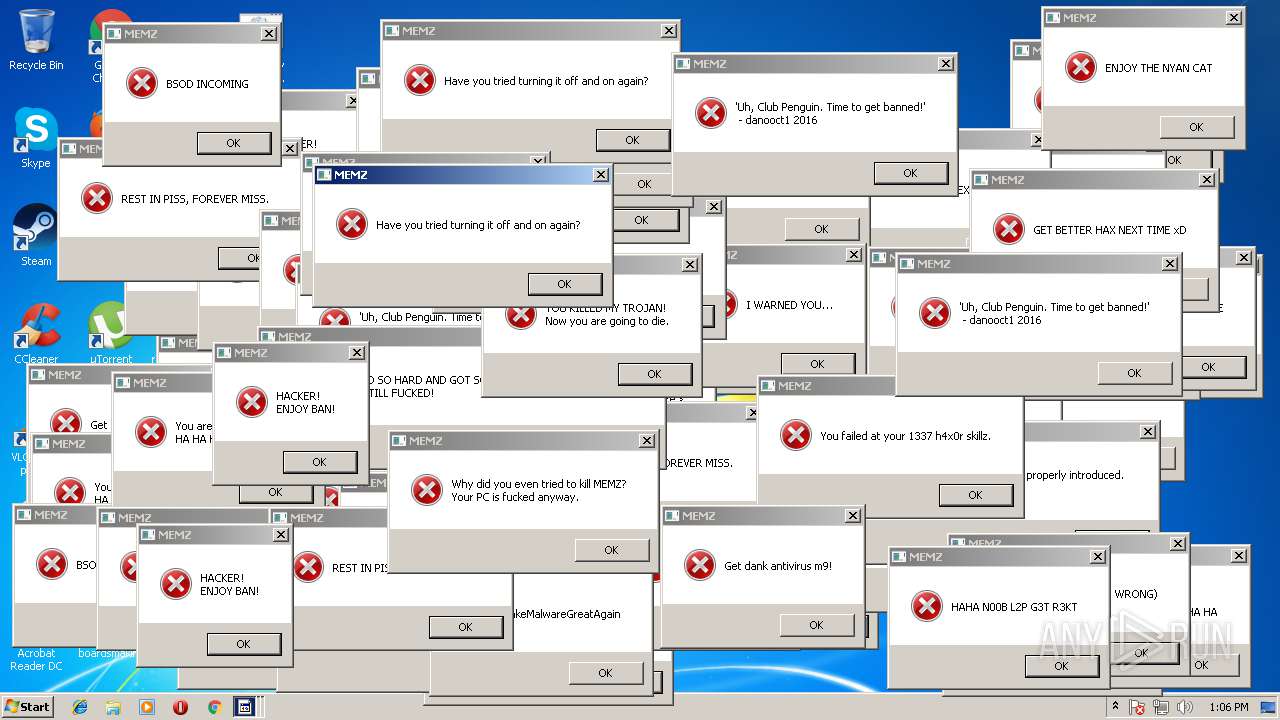
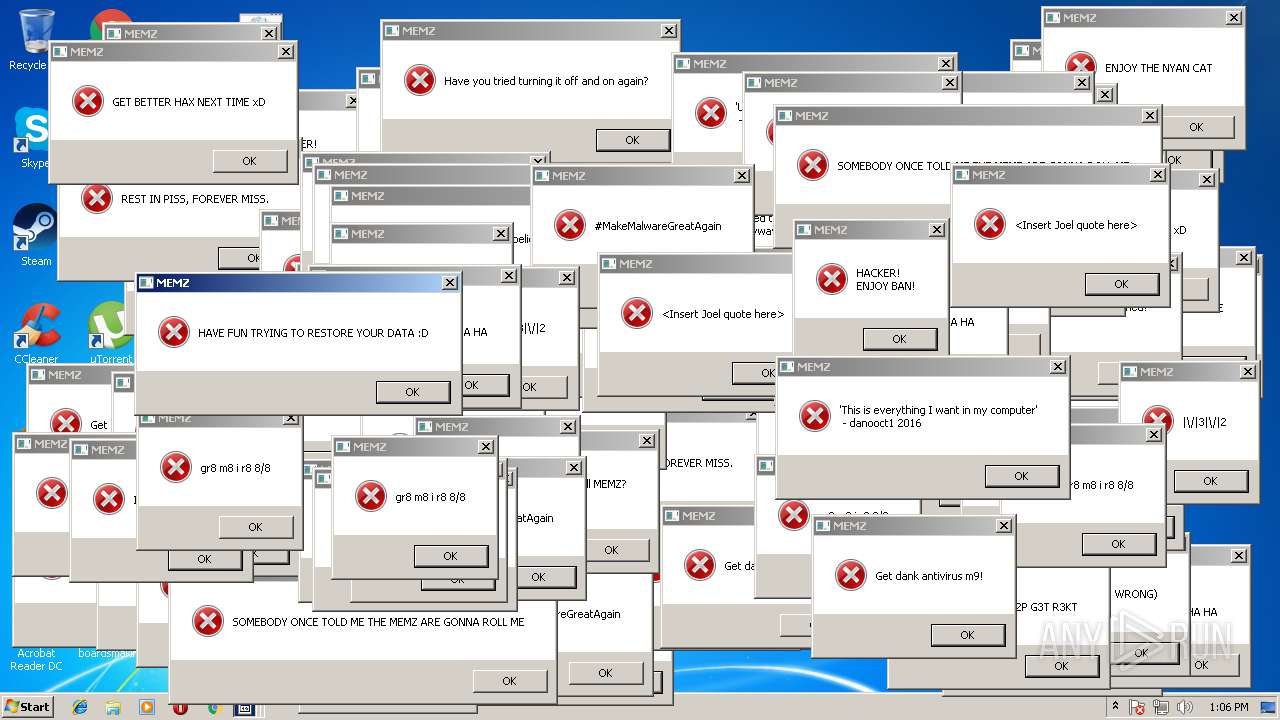
MALICIOUS
Application was dropped or rewritten from another process
- MEMZ.exe (PID: 3464)
- MEMZ.exe (PID: 3544)
- MEMZ.exe (PID: 3504)
- MEMZ.exe (PID: 2320)
- MEMZ.exe (PID: 1452)
- MEMZ.exe (PID: 3180)
- MEMZ.exe (PID: 2704)
- MEMZ.exe (PID: 1860)
- MEMZ.exe (PID: 2300)
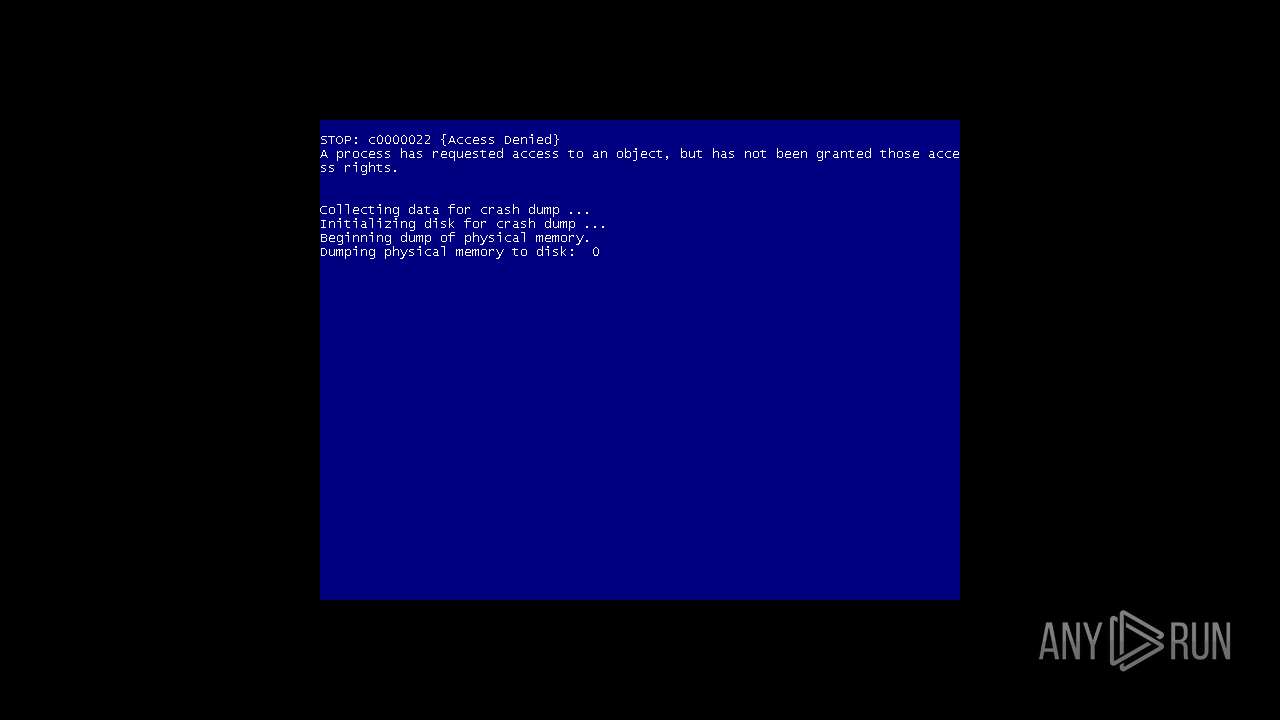
Low-level write access rights to disk partition
- MEMZ.exe (PID: 2300)
SUSPICIOUS
Executes scripts
- cmd.exe (PID: 3492)
Creates files in the user directory
- cscript.exe (PID: 3660)
Executable content was dropped or overwritten
- cscript.exe (PID: 3660)
Application launched itself
- MEMZ.exe (PID: 3504)
Low-level read access rights to disk partition
- MEMZ.exe (PID: 2300)
INFO
Dropped object may contain URL's
- cscript.exe (PID: 3660)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
49
Monitored processes
12
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1452 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1860 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2300 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /main | C:\Users\admin\AppData\Roaming\MEMZ.exe | MEMZ.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 1073807364 Modules
| |||||||||||||||
| 2320 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2704 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3180 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" /watchdog | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | MEMZ.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3332 | "C:\Windows\System32\notepad.exe" \note.txt | C:\Windows\System32\notepad.exe | — | MEMZ.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Exit code: 1073807364 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3464 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" | C:\Users\admin\AppData\Roaming\MEMZ.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 3492 | cmd /c ""C:\Users\admin\Desktop\Geometry dash auto speedhack.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3504 | "C:\Users\admin\AppData\Roaming\MEMZ.exe" | C:\Users\admin\AppData\Roaming\MEMZ.exe | cmd.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
927
Read events
889
Write events
38
Delete events
0
Modification events
| (PID) Process: | (3660) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3660) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3660) cscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\Discardable\PostSetup\Component Categories\{56FFCC30-D398-11D0-B2AE-00A0C908FA49}\Enum |
| Operation: | write | Name: | Implementing |
Value: 1C00000001000000E2070800060004000C0005002F00640000000000 | |||
| (PID) Process: | (3492) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3492) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3504) MEMZ.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3504) MEMZ.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2300) MEMZ.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2300) MEMZ.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
1
Suspicious files
1
Text files
66
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3492 | cmd.exe | C:\Users\admin\Desktop\x | text | |
MD5:— | SHA256:— | |||
| 3492 | cmd.exe | C:\Users\admin\Desktop\x.js | text | |
MD5:8EEC8704D2A7BC80B95B7460C06F4854 | SHA256:AA01B8864B43E92077A106ED3D4656A511F3BA1910FBA40C78A32EE6A621D596 | |||
| 3660 | cscript.exe | C:\Users\admin\AppData\Roaming\MEMZ.exe | executable | |
MD5:19DBEC50735B5F2A72D4199C4E184960 | SHA256:A3D5715A81F2FBEB5F76C88C9C21EEEE87142909716472F911FF6950C790C24D | |||
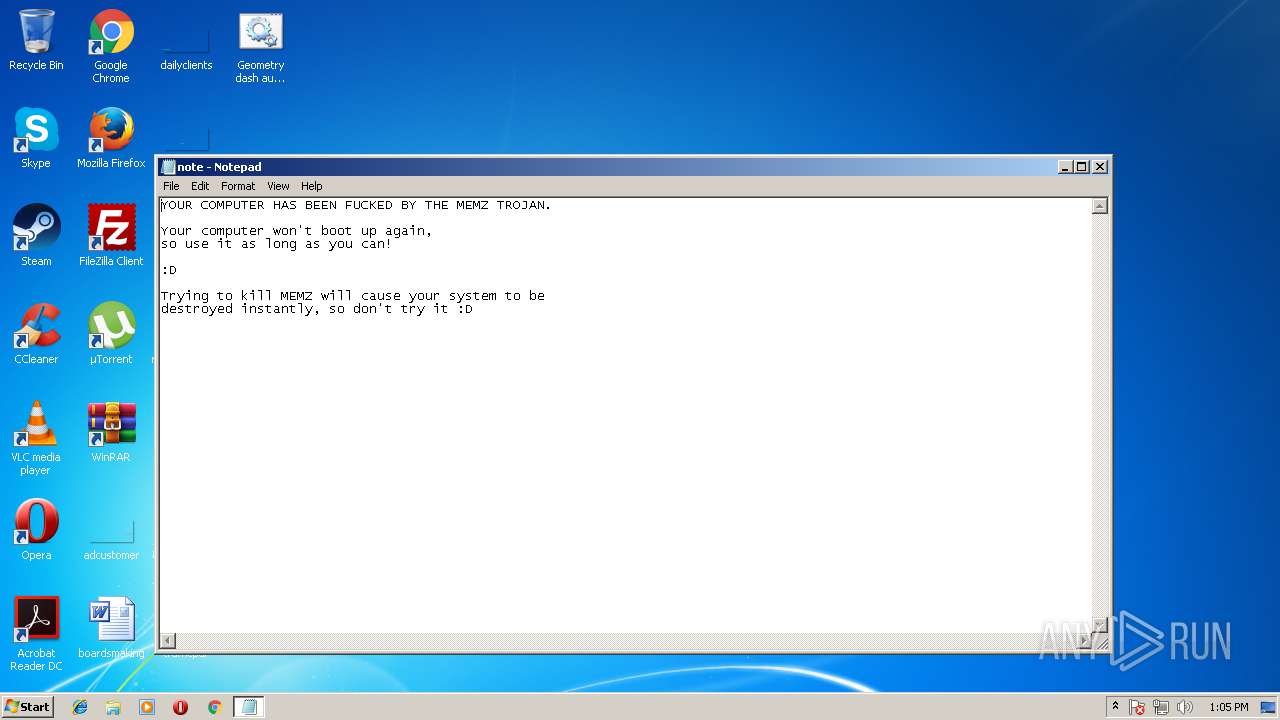
| 2300 | MEMZ.exe | C:\note.txt | text | |
MD5:AFA6955439B8D516721231029FB9CA1B | SHA256:8E9F20F6864C66576536C0B866C6FFDCF11397DB67FE120E972E244C3C022270 | |||
| 3660 | cscript.exe | C:\Users\admin\Desktop\z.zip | compressed | |
MD5:63EE4412B95D7AD64C54B4BA673470A7 | SHA256:44C1857B1C4894B3DFBACCBE04905652E634283DCF6B06C25A74B17021E2A268 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report