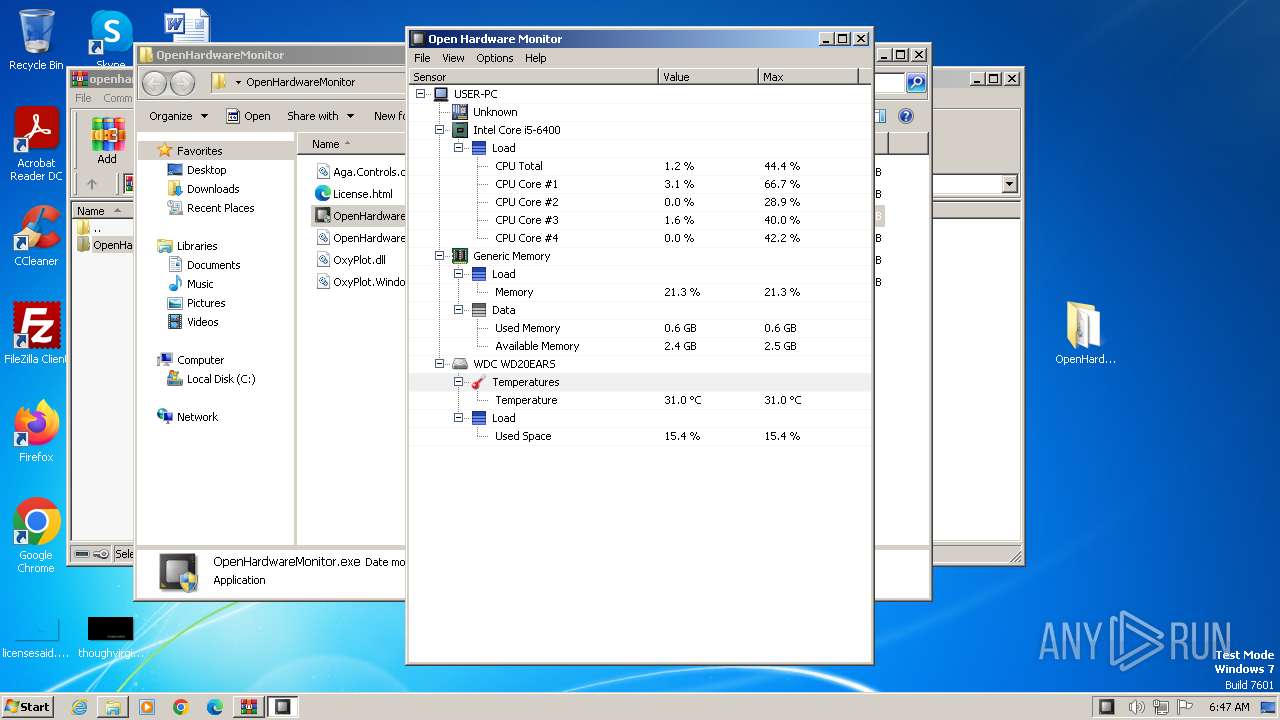
| File name: | openhardwaremonitor-v0.9.6.zip |
| Full analysis: | https://app.any.run/tasks/cee6153d-c0ed-47f1-80a8-415ce76684f1 |
| Verdict: | Malicious activity |
| Analysis date: | January 07, 2024, 06:46:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 6F649C4615A01A4911283F2FECC00211 |
| SHA1: | BE8214DE9EBE3B9DC7470F3F10321AA2043F20F0 |
| SHA256: | 5E238C36AE5F8A8AB9AA5E6FA3C568967D61953393384C7C8FD6370F8BC86B85 |
| SSDEEP: | 12288:X1lKssKgSWgd+8RzGs4VcyB/kMNikz6FXSTjKTe9IAaV:X1Qssi+8R54vhtNf+FpxAq |
MALICIOUS
Creates a writable file in the system directory
- OpenHardwareMonitor.exe (PID: 696)
- mofcomp.exe (PID: 1924)
Starts Visual C# compiler
- OpenHardwareMonitor.exe (PID: 696)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- OpenHardwareMonitor.exe (PID: 696)
Uses .NET C# to load dll
- OpenHardwareMonitor.exe (PID: 696)
INFO
Create files in a temporary directory
- mofcomp.exe (PID: 1924)
- OpenHardwareMonitor.exe (PID: 696)
- csc.exe (PID: 1384)
- cvtres.exe (PID: 2428)
Manual execution by a user
- OpenHardwareMonitor.exe (PID: 1504)
- OpenHardwareMonitor.exe (PID: 696)
Reads the computer name
- OpenHardwareMonitor.exe (PID: 696)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 124)
- OpenHardwareMonitor.exe (PID: 696)
- csc.exe (PID: 1384)
Checks supported languages
- OpenHardwareMonitor.exe (PID: 696)
- csc.exe (PID: 1384)
- cvtres.exe (PID: 2428)
Reads the machine GUID from the registry
- OpenHardwareMonitor.exe (PID: 696)
- csc.exe (PID: 1384)
- cvtres.exe (PID: 2428)
Reads Environment values
- OpenHardwareMonitor.exe (PID: 696)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2020:12:27 16:06:36 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | OpenHardwareMonitor/ |
Total processes
47
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\openhardwaremonitor-v0.9.6.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 696 | "C:\Users\admin\Desktop\OpenHardwareMonitor\OpenHardwareMonitor.exe" | C:\Users\admin\Desktop\OpenHardwareMonitor\OpenHardwareMonitor.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Open Hardware Monitor Exit code: 0 Version: 0.9.6.0 Modules
| |||||||||||||||
| 1384 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\gydn0pxk\gydn0pxk.cmdline" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\csc.exe | — | OpenHardwareMonitor.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.3761.0 built by: NET48REL1 Modules
| |||||||||||||||
| 1504 | "C:\Users\admin\Desktop\OpenHardwareMonitor\OpenHardwareMonitor.exe" | C:\Users\admin\Desktop\OpenHardwareMonitor\OpenHardwareMonitor.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Open Hardware Monitor Exit code: 3221226540 Version: 0.9.6.0 Modules
| |||||||||||||||
| 1924 | "C:\Windows\system32\WBEM\mofcomp.exe" C:\Windows\system32\WBEM\Framework\root\OpenHardwareMonitor\OpenHardwareMonitor_SN__Version_0.9.6.0.mof | C:\Windows\System32\wbem\mofcomp.exe | — | OpenHardwareMonitor.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: The Managed Object Format (MOF) Compiler Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2428 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES2EDC.tmp" "c:\Users\admin\AppData\Local\Temp\gydn0pxk\CSC47F36701327448B28EEE9891433DD4E4.TMP" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.10.25028.0 built by: VCTOOLSD15RTM Modules
| |||||||||||||||
Total events
1 467
Read events
1 457
Write events
10
Delete events
0
Modification events
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (124) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1924) mofcomp.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\WBEM\CIMOM |
| Operation: | write | Name: | Autorecover MOFs timestamp |
Value: 133331385132656250 | |||
Executable files
7
Suspicious files
3
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1384 | csc.exe | C:\Users\admin\AppData\Local\Temp\gydn0pxk\CSC47F36701327448B28EEE9891433DD4E4.TMP | binary | |
MD5:3CC30B670F638F8141220BDE660484E6 | SHA256:654C49F9900595426BCE67553D23A95D33FD6E4DF628F4F7B1A24F6496561625 | |||
| 124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa124.055\OpenHardwareMonitor\OxyPlot.dll | executable | |
MD5:F07E485AB092D993A4B2BFBABF6B1D75 | SHA256:D3A00F3B9FBF82C4EE9FCF495A0FCC80F9F26711B4BB4FE15E0B769D47488B50 | |||
| 124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa124.055\OpenHardwareMonitor\OpenHardwareMonitor.exe | executable | |
MD5:A261F824AB957A5331AF53C7722FA2DE | SHA256:EC767A74C5659A05BDB7AC10BD42C2EA6D44FA946286029B2866AED476AD83BC | |||
| 124 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa124.055\OpenHardwareMonitor\License.html | html | |
MD5:56E35FD2E011977C42260637515E7E6A | SHA256:B14E66270C828C445662328127F68042A1D6B17E7382E150E542A2045B1A9075 | |||
| 696 | OpenHardwareMonitor.exe | C:\Windows\system32\WBEM\Framework\root\OpenHardwareMonitor\OpenHardwareMonitor_SN__Version_0.9.6.0.mof | text | |
MD5:53081D691AFEDCC6E7812977756AF792 | SHA256:C9A8665215AEBF1D61FEC975F5E3F4E89521522F651D1105B8F608211A7A26A5 | |||
| 696 | OpenHardwareMonitor.exe | C:\Users\admin\Desktop\OpenHardwareMonitor\OpenHardwareMonitorLib.sys | executable | |
MD5:845AF1BA23C8D5E64DEF61BCC441604C | SHA256:206EE7A7C3F4D9496F742CCB84718F556ECB4BA2A95FE7E0CDF3A003FFBE4597 | |||
| 1924 | mofcomp.exe | C:\Users\admin\AppData\Local\Temp\tmp2DA3.tmp | binary | |
MD5:AC5F369CCCFF6008E1B74D088962C215 | SHA256:9B5BFCAF0119CEAC5546374F3EDE9E16555884FC2ECFB3638B959E2322E0819F | |||
| 696 | OpenHardwareMonitor.exe | C:\Users\admin\AppData\Local\Temp\gydn0pxk\gydn0pxk.0.cs | text | |
MD5:07A1D0AD3304D4589BB083A5E4187D7D | SHA256:FDFE8A3908694C6E084A051C54BE36225C2395B43A860852FB51EBC1095597D4 | |||
| 1924 | mofcomp.exe | C:\Windows\system32\wbem\AutoRecover\00F67A77883EFBAE535B360A10E07FD8.mof | text | |
MD5:40D27E57134BA6CBAA718D1A843B0759 | SHA256:30C73FEFD18B8F03641A984C81E67D06C9356A5E99281903B8D6BA0F5C7BABAD | |||
| 696 | OpenHardwareMonitor.exe | C:\Users\admin\AppData\Local\Temp\gydn0pxk\gydn0pxk.cmdline | text | |
MD5:FDB3C762762DA9B3B4877CDB68986A28 | SHA256:0A61987B841963E5E67CCEFE5F6BC658A54C1178DC983EC1A6C5558A71B9F85A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |