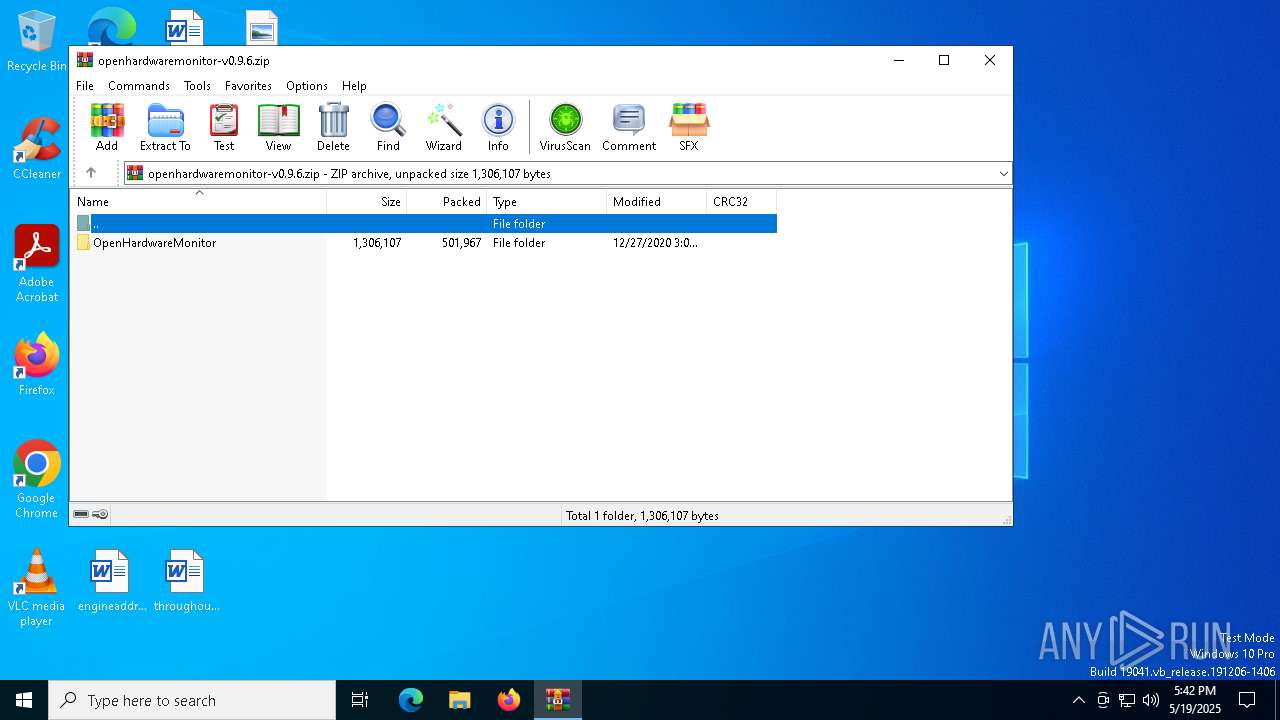
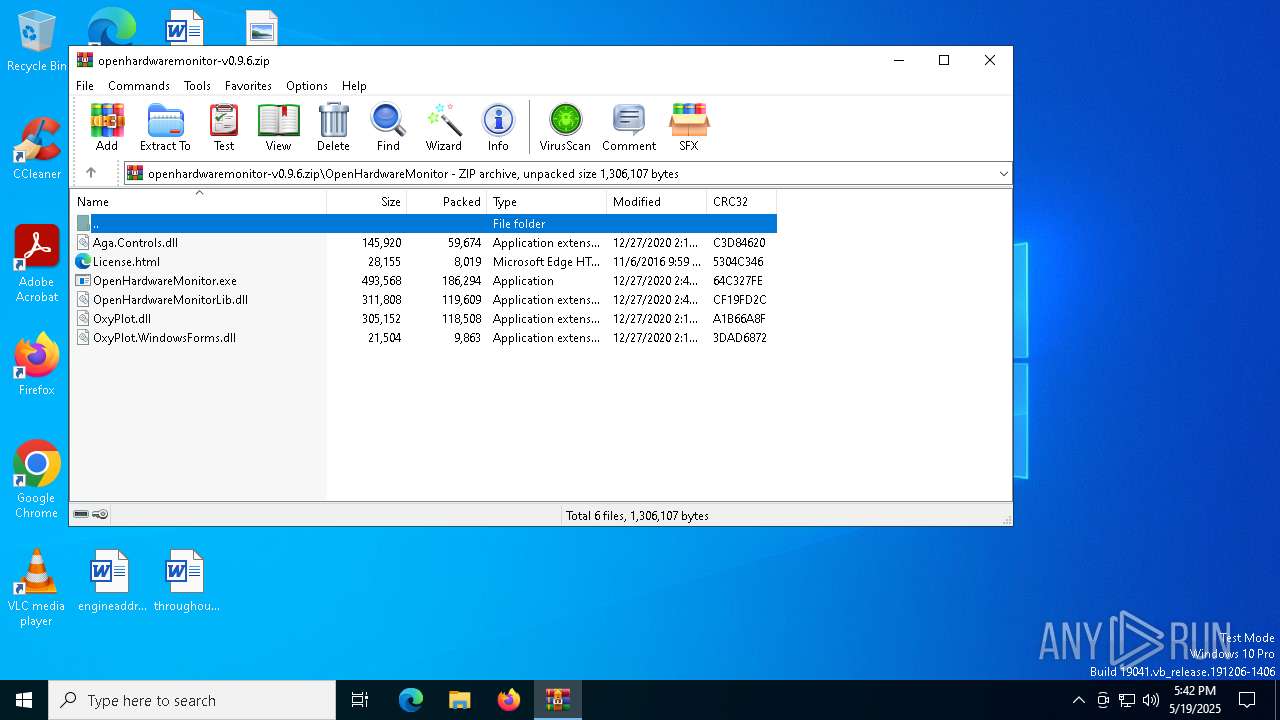
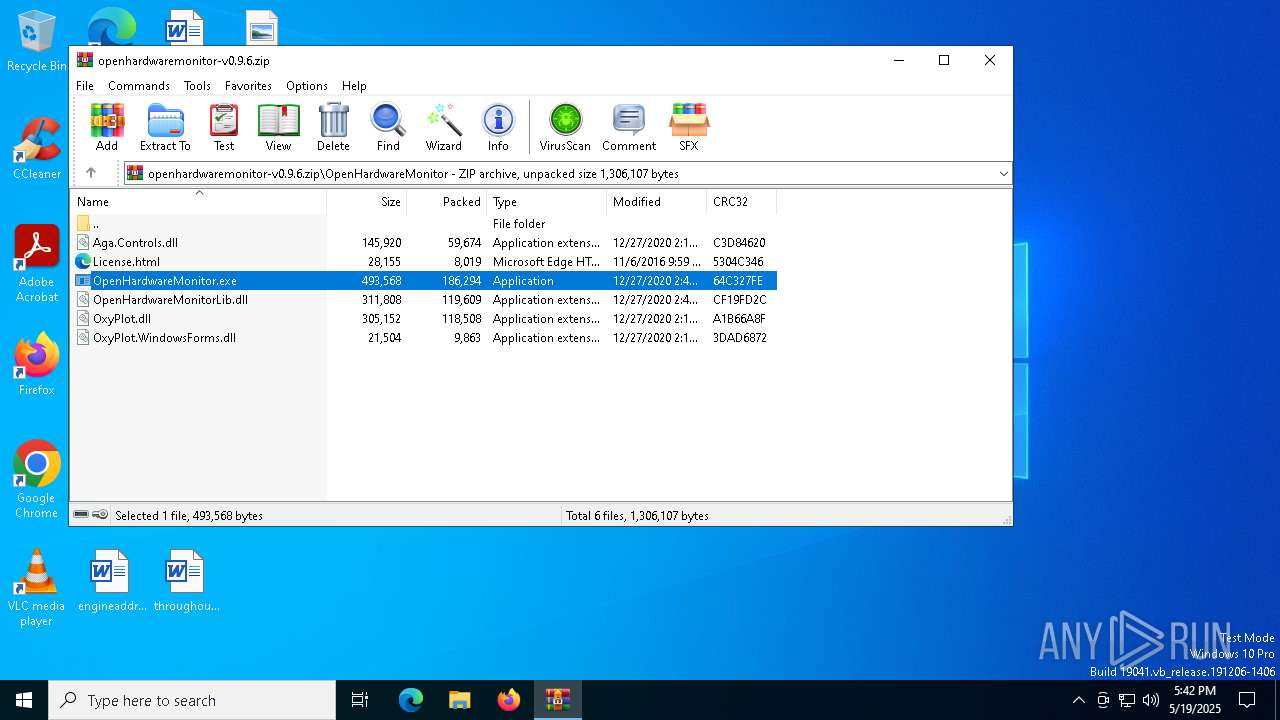
| File name: | openhardwaremonitor-v0.9.6.zip |
| Full analysis: | https://app.any.run/tasks/730837c1-bded-483b-b6d8-d5637d3f6c35 |
| Verdict: | Malicious activity |
| Analysis date: | May 19, 2025, 17:42:26 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | 6F649C4615A01A4911283F2FECC00211 |
| SHA1: | BE8214DE9EBE3B9DC7470F3F10321AA2043F20F0 |
| SHA256: | 5E238C36AE5F8A8AB9AA5E6FA3C568967D61953393384C7C8FD6370F8BC86B85 |
| SSDEEP: | 12288:X1lKssKgSWgd+8RzGs4VcyB/kMNikz6FXSTjKTe9IAaV:X1Qssi+8R54vhtNf+FpxAq |
MALICIOUS
Vulnerable driver has been detected
- OpenHardwareMonitor.exe (PID: 3100)
SUSPICIOUS
Generic archive extractor
- WinRAR.exe (PID: 1388)
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 1388)
Executable content was dropped or overwritten
- OpenHardwareMonitor.exe (PID: 3100)
- csc.exe (PID: 5528)
Drops a system driver (possible attempt to evade defenses)
- OpenHardwareMonitor.exe (PID: 3100)
There is functionality for taking screenshot (YARA)
- OpenHardwareMonitor.exe (PID: 3100)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1388)
Reads the machine GUID from the registry
- OpenHardwareMonitor.exe (PID: 3100)
- csc.exe (PID: 5528)
Checks supported languages
- OpenHardwareMonitor.exe (PID: 3100)
- cvtres.exe (PID: 6872)
- csc.exe (PID: 5528)
Reads the computer name
- OpenHardwareMonitor.exe (PID: 3100)
Create files in a temporary directory
- OpenHardwareMonitor.exe (PID: 3100)
- mofcomp.exe (PID: 5212)
- cvtres.exe (PID: 6872)
- csc.exe (PID: 5528)
The sample compiled with japanese language support
- OpenHardwareMonitor.exe (PID: 3100)
Reads Environment values
- OpenHardwareMonitor.exe (PID: 3100)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2020:12:27 16:06:36 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | OpenHardwareMonitor/ |
Total processes
140
Monitored processes
10
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1388 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\openhardwaremonitor-v0.9.6.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 2980 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | — | SppExtComObj.Exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3100 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1388.37094\OpenHardwareMonitor\OpenHardwareMonitor.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1388.37094\OpenHardwareMonitor\OpenHardwareMonitor.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Open Hardware Monitor Version: 0.9.6.0 Modules
| |||||||||||||||
| 4180 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4724 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5212 | "C:\WINDOWS\system32\WBEM\mofcomp.exe" C:\WINDOWS\system32\WBEM\Framework\root\OpenHardwareMonitor\OpenHardwareMonitor_SN__Version_0.9.6.0.mof | C:\Windows\System32\wbem\mofcomp.exe | — | OpenHardwareMonitor.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: The Managed Object Format (MOF) Compiler Exit code: 0 Version: 10.0.19041.3758 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5528 | "C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe" /noconfig /fullpaths @"C:\Users\admin\AppData\Local\Temp\yndrf012\yndrf012.cmdline" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\csc.exe | OpenHardwareMonitor.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual C# Command Line Compiler Exit code: 0 Version: 4.8.9037.0 built by: NET481REL1 Modules
| |||||||||||||||
| 5796 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1388.37094\OpenHardwareMonitor\OpenHardwareMonitor.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1388.37094\OpenHardwareMonitor\OpenHardwareMonitor.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Open Hardware Monitor Exit code: 3221226540 Version: 0.9.6.0 Modules
| |||||||||||||||
| 6872 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | mofcomp.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6872 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RES1AA9.tmp" "c:\Users\admin\AppData\Local\Temp\yndrf012\CSC21E2547BAAC14FE4B386AA9724F357D.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 Modules
| |||||||||||||||
Total events
3 371
Read events
3 363
Write events
8
Delete events
0
Modification events
| (PID) Process: | (1388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (1388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (1388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\openhardwaremonitor-v0.9.6.zip | |||
| (PID) Process: | (1388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1388) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
7
Suspicious files
5
Text files
5
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1388.37094\OpenHardwareMonitor\Aga.Controls.dll | executable | |
MD5:F17BE368ADE3F7CFBB6AA9DD734CE328 | SHA256:830E520CAF3E89DCCAA3C12E3BFC992221C164F2319A2BA57E402499C24290E3 | |||
| 1388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1388.37094\OpenHardwareMonitor\OpenHardwareMonitor.exe | executable | |
MD5:A261F824AB957A5331AF53C7722FA2DE | SHA256:EC767A74C5659A05BDB7AC10BD42C2EA6D44FA946286029B2866AED476AD83BC | |||
| 3100 | OpenHardwareMonitor.exe | C:\Windows\System32\wbem\Framework\root\OpenHardwareMonitor\OpenHardwareMonitor_SN__Version_0.9.6.0.cs | text | |
MD5:774F474D03C669154883A2673DFB1227 | SHA256:3977289C2F9E9F5BFC1496E0AD443A685D28E5272E8FA9AE1BC6B97F749E320D | |||
| 3100 | OpenHardwareMonitor.exe | C:\Users\admin\AppData\Local\Temp\yndrf012\yndrf012.0.cs | text | |
MD5:07A1D0AD3304D4589BB083A5E4187D7D | SHA256:FDFE8A3908694C6E084A051C54BE36225C2395B43A860852FB51EBC1095597D4 | |||
| 3100 | OpenHardwareMonitor.exe | C:\Windows\System32\wbem\Framework\root\OpenHardwareMonitor\OpenHardwareMonitor_SN__Version_0.9.6.0.mof | binary | |
MD5:166B0F824F4182DA753478C46F28FAE0 | SHA256:400C466FAB6C3DE04295EF5BC5D51EBB8648E1AFEC93C1B42E43F2306F16BC40 | |||
| 6872 | cvtres.exe | C:\Users\admin\AppData\Local\Temp\RES1AA9.tmp | binary | |
MD5:3E2C9B342584F160F4FF6FD87A2B141F | SHA256:D4801B7F68EC5DACD496BE10C04FEC7BF6552E4DBAD43CF8A9EA33D0CAC8C4B7 | |||
| 5528 | csc.exe | C:\Users\admin\AppData\Local\Temp\yndrf012\yndrf012.out | text | |
MD5:D0C786911ABB44D84DFACB0362275A49 | SHA256:E713B30349ADB8B89EBF2F9CCD6211462728879FC5D5CF7BB5CE23D42EE8CE22 | |||
| 5212 | mofcomp.exe | C:\Windows\System32\wbem\AutoRecover\00F67A77883EFBAE535B360A10E07FD8.mof | binary | |
MD5:CFCA18EDB8925DCB511E66FF5394310A | SHA256:80EB037E71A996EF04EE13DF1899AFBC0C522109640F87DAD417BDA85362A6E5 | |||
| 1388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1388.37094\OpenHardwareMonitor\OpenHardwareMonitorLib.dll | executable | |
MD5:84F1D429196CC4E89D22B2652E65F669 | SHA256:EF02B0991AAC678052BB79DFDFD5BFA0B42B1F34B209E35819BA606909655F58 | |||
| 1388 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1388.37094\OpenHardwareMonitor\License.html | html | |
MD5:56E35FD2E011977C42260637515E7E6A | SHA256:B14E66270C828C445662328127F68042A1D6B17E7382E150E542A2045B1A9075 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
20
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.17.147.64:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7648 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7648 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.17.147.64:80 | crl.microsoft.com | Akamai International B.V. | CZ | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
6544 | svchost.exe | 40.126.31.131:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | FR | unknown |
5496 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1616 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |