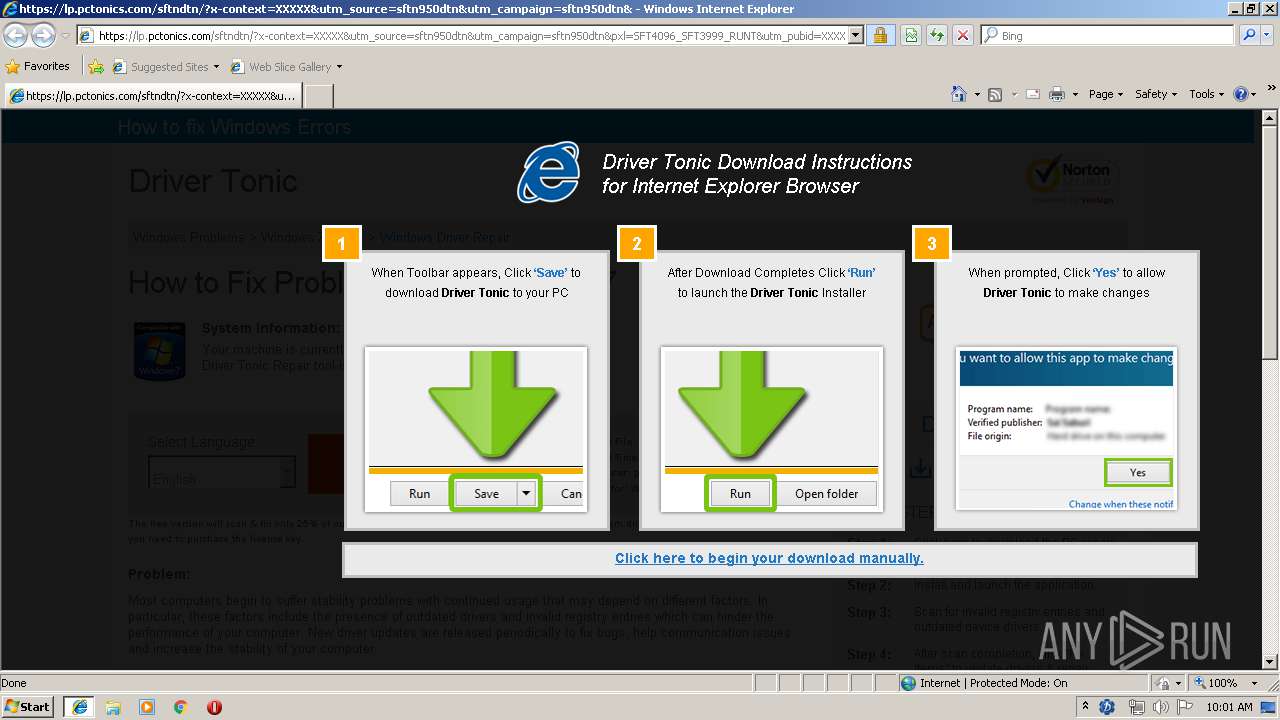
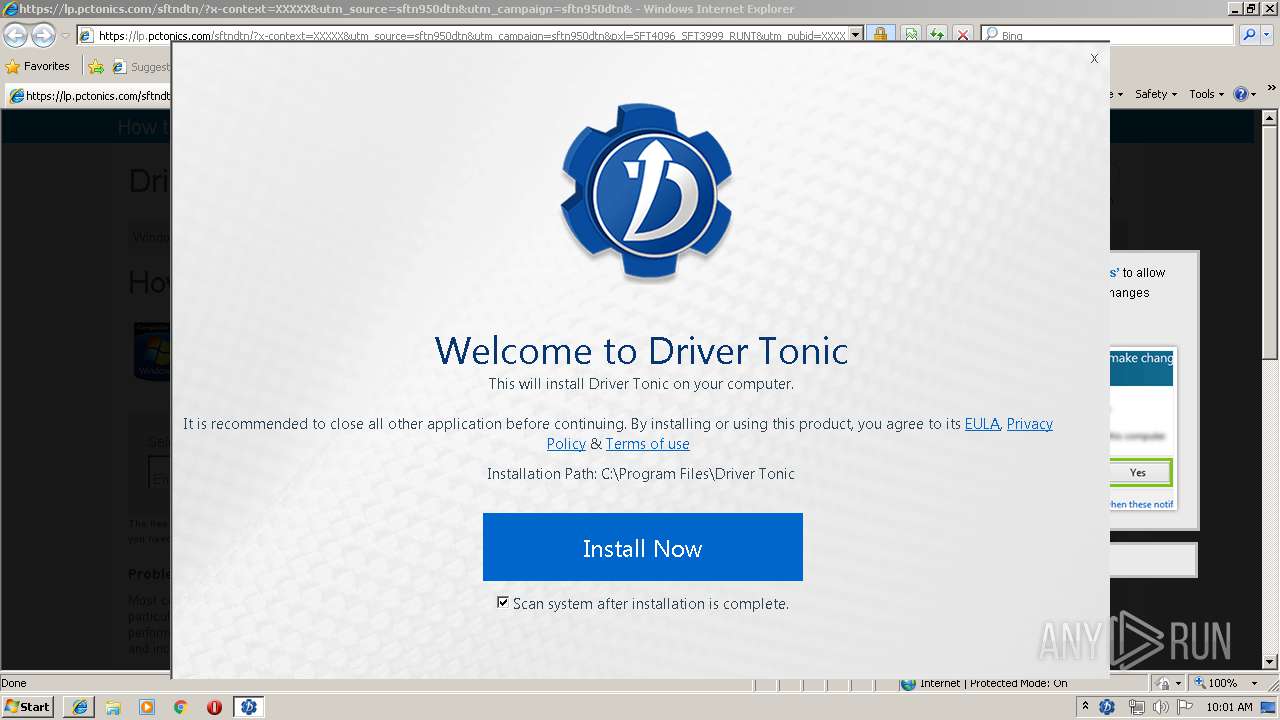
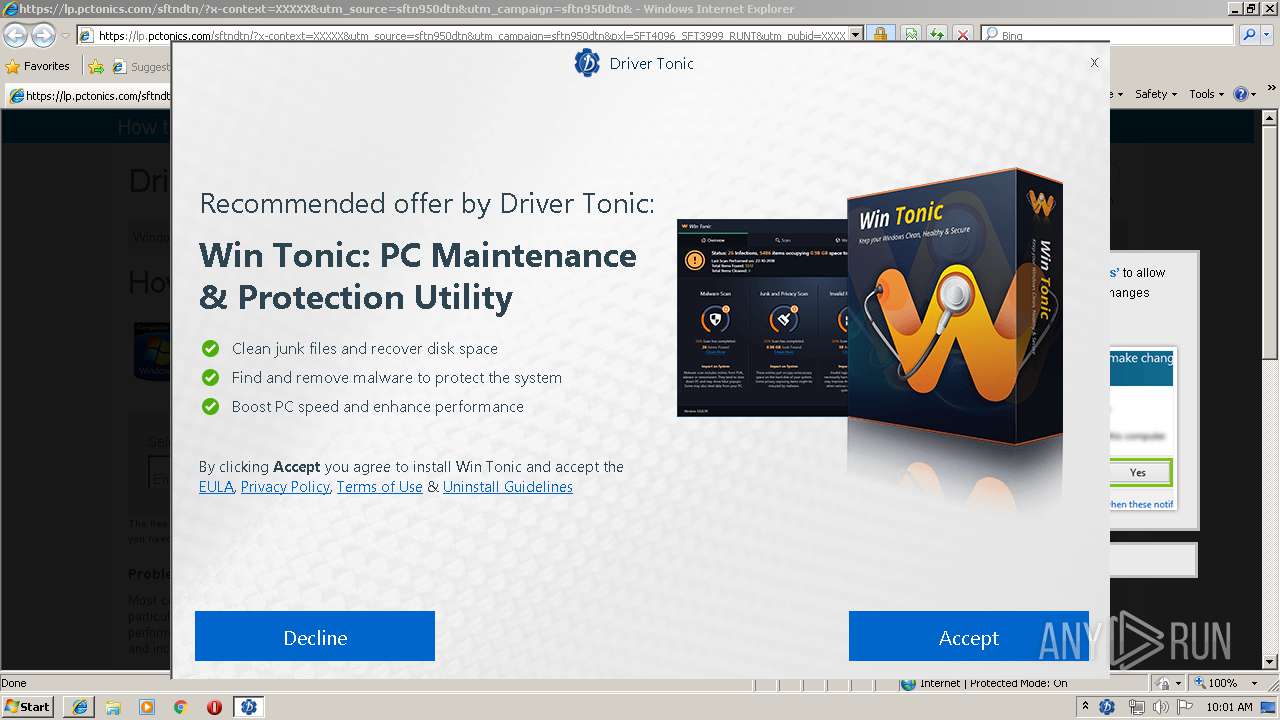
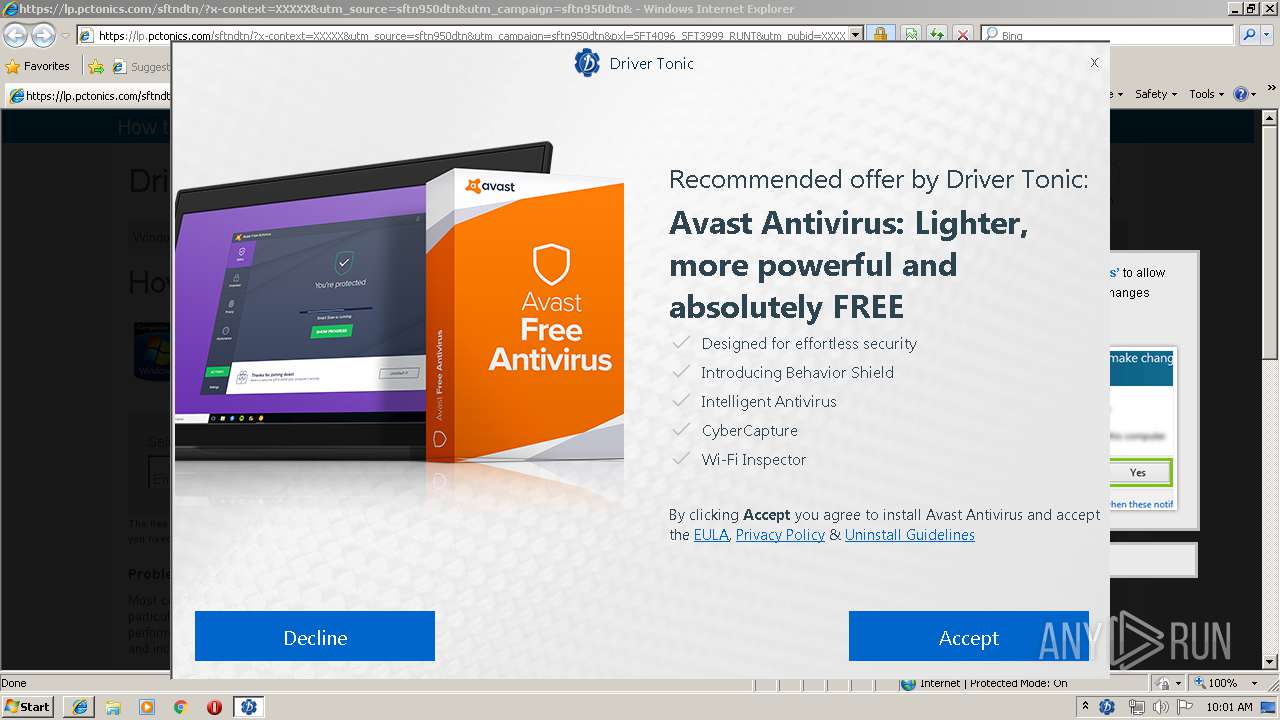
| URL: | https://googleads.g.doubleclick.net/pcs/click?xai=AKAOjsuHornD_WCnnNUd3kP7d-eY63eSFSWx_UU9ijEEfbPAuEq9DC46J4X2p_5GZqtbiTZFj6gIpgDvjZH4fxUEuXJ7Xq_B4u-sPfVjkmZ8fEa9slJKEoeFBJZgRa8FVGxMH5RFFFg-fH0MMovJmM_XAY3Kka3ceNDdluhpiuHt2ViLkMlRySTGbsJDEiFe1Y7JsGGjSCViER1XtdlAMwqrH13KW__OF1K8U51t-C5tqniVYLg_vrISpecor4bzuTPRIIpCv82lk1uJLdqtIUV7MXs5Q-J9feVn1vMvnp5I6XiMA5Bbe9-f_2GJsSAc2WQ&sai=AMfl-YRyegCcuQsU4UqJv7Ag5Is2c-0bUk3qkb5fVnEO6Cp4dKOsuQLyvmCVdC8X5ke1di08rZkGNIB1JECVYBXBiLlSTsDFSVx2SU26RnDlMw&sig=Cg0ArKJSzLsRzVNHcBvm&adurl=https://lp.pctonics.com/sftndtn/%3Fx-context%3DXXXXX%26utm_source%3Dsftn950dtn%26utm_campaign%3Dsftn950dtn%26pxl%3DSFT4096_SFT3999_RUNT%26utm_pubid%3DXXXXX%26x-at%3D&nx=CLICK_X&ny=CLICK_Y |
| Full analysis: | https://app.any.run/tasks/1d81b703-3bd1-4252-a6e6-aae59cab8374 |
| Verdict: | Malicious activity |
| Analysis date: | April 26, 2019, 09:01:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 76399F47462CF057E0B0365831119380 |
| SHA1: | 7CAB4717374D1BFEC1FC61C003A8727683A4169B |
| SHA256: | 5E1DA347BDE7C4AEE507D95D7340B39EB8D72CBBBCE4A0AE8B7037E138F57696 |
| SSDEEP: | 12:27EYIylWwws2ODUe7Mh0H5j4ZG+O39KToMi4hJL3dvzI2zRV0pbikEgH8mpkEeoe:27EEwsbDUe7MyZj44lz4htdk2zRVvkE9 |
MALICIOUS
Application was dropped or rewritten from another process
- drivertonic[1].exe (PID: 3716)
- drivertonic[1].exe (PID: 2936)
- dtn.exe (PID: 2908)
- dtncsetup.exe (PID: 856)
Changes settings of System certificates
- drivertonic[1].exe (PID: 2936)
- dtn.exe (PID: 2908)
Uses Task Scheduler to run other applications
- dtncsetup.tmp (PID: 3092)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 3552)
SUSPICIOUS
Executable content was dropped or overwritten
- iexplore.exe (PID: 3868)
- iexplore.exe (PID: 2668)
- dtncsetup.exe (PID: 856)
- drivertonic[1].exe (PID: 2936)
- dtncsetup.tmp (PID: 3092)
Reads internet explorer settings
- drivertonic[1].exe (PID: 2936)
Uses RUNDLL32.EXE to load library
- drivertonic[1].exe (PID: 2936)
Reads Internet Cache Settings
- rundll32.exe (PID: 3480)
- rundll32.exe (PID: 3120)
Adds / modifies Windows certificates
- drivertonic[1].exe (PID: 2936)
Reads the Windows organization settings
- dtncsetup.tmp (PID: 3092)
Reads Windows owner or organization settings
- dtncsetup.tmp (PID: 3092)
Creates files in the user directory
- dtncsetup.tmp (PID: 3092)
Uses TASKKILL.EXE to kill process
- dtncsetup.tmp (PID: 3092)
INFO
Changes internet zones settings
- iexplore.exe (PID: 3868)
Application launched itself
- iexplore.exe (PID: 3868)
Reads Internet Cache Settings
- iexplore.exe (PID: 2668)
Creates files in the user directory
- iexplore.exe (PID: 2668)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 2356)
Changes settings of System certificates
- iexplore.exe (PID: 3868)
Reads internet explorer settings
- iexplore.exe (PID: 2668)
Reads settings of System Certificates
- iexplore.exe (PID: 3868)
- drivertonic[1].exe (PID: 2936)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3868)
Creates files in the program directory
- dtncsetup.tmp (PID: 3092)
Creates a software uninstall entry
- dtncsetup.tmp (PID: 3092)
Application was dropped or rewritten from another process
- dtncsetup.tmp (PID: 3092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
50
Monitored processes
12
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 856 | C:\Users\admin\AppData\Local\Temp\~ubfcasy.tmp\dtncsetup.exe /verysilent /inswtc /insavst | C:\Users\admin\AppData\Local\Temp\~ubfcasy.tmp\dtncsetup.exe | drivertonic[1].exe | ||||||||||||
User: admin Company: pctonics.com Integrity Level: HIGH Description: Driver Tonic Setup Exit code: 0 Version: 1.0.1.7 Modules
| |||||||||||||||
| 1412 | "C:\Windows\System32\taskkill.exe" /f /im "dtn.exe" | C:\Windows\System32\taskkill.exe | — | dtncsetup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 128 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2356 | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 26.0 r0 Exit code: 0 Version: 26,0,0,131 Modules
| |||||||||||||||
| 2668 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3868 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2908 | "C:\Program Files\Driver Tonic\dtn.exe" getdetails | C:\Program Files\Driver Tonic\dtn.exe | dtncsetup.tmp | ||||||||||||
User: admin Company: pctonics.com Integrity Level: HIGH Description: Driver Tonic Exit code: 0 Version: 1.0.1.7 Modules
| |||||||||||||||
| 2936 | "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\drivertonic[1].exe" | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\drivertonic[1].exe | iexplore.exe | ||||||||||||
User: admin Company: pctonics.com Integrity Level: HIGH Description: Driver Tonic Setup Exit code: 0 Version: 1.0.1.7 Modules
| |||||||||||||||
| 3092 | "C:\Users\admin\AppData\Local\Temp\is-I9LHU.tmp\dtncsetup.tmp" /SL5="$400EC,10500799,172544,C:\Users\admin\AppData\Local\Temp\~ubfcasy.tmp\dtncsetup.exe" /verysilent /inswtc /insavst | C:\Users\admin\AppData\Local\Temp\is-I9LHU.tmp\dtncsetup.tmp | dtncsetup.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3120 | "C:\Windows\system32\rundll32.exe" "C:\Windows\system32\WININET.dll",DispatchAPICall 1 | C:\Windows\system32\rundll32.exe | — | drivertonic[1].exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3480 | "C:\Windows\system32\rundll32.exe" "C:\Windows\system32\WININET.dll",DispatchAPICall 1 | C:\Windows\system32\rundll32.exe | — | drivertonic[1].exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3552 | "C:\Windows\System32\schtasks.exe" /delete /tn "Driver Tonic_launcher" /f | C:\Windows\System32\schtasks.exe | — | dtncsetup.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Manages scheduled tasks Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 349
Read events
1 141
Write events
206
Delete events
2
Modification events
| (PID) Process: | (3868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000071000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {DB52368B-6801-11E9-A370-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (3868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (3868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 1 | |||
| (PID) Process: | (3868) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E307040005001A000900010014002203 | |||
Executable files
29
Suspicious files
15
Text files
77
Unknown types
19
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3868 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3868 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2668 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab32D5.tmp | — | |
MD5:— | SHA256:— | |||
| 2668 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar32E5.tmp | — | |
MD5:— | SHA256:— | |||
| 2668 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab32F6.tmp | — | |
MD5:— | SHA256:— | |||
| 2668 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar32F7.tmp | — | |
MD5:— | SHA256:— | |||
| 2668 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab33E2.tmp | — | |
MD5:— | SHA256:— | |||
| 2668 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar33E3.tmp | — | |
MD5:— | SHA256:— | |||
| 2668 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\57SXRVPF\sftndtn[1].txt | — | |
MD5:— | SHA256:— | |||
| 2668 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@lp.pctonics[2].txt | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
30
DNS requests
15
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2936 | drivertonic[1].exe | GET | 200 | 216.245.208.194:80 | http://www.winactiv.com/mtrack/?metd=trackBlog&x-fetch=1&utm_source=dtninstlr&utm_campaign=dtninstlr&pxl=DTN3231_DTN3159_RUNT | US | — | — | malicious |
2908 | dtn.exe | GET | 200 | 91.199.212.52:80 | http://crt.usertrust.com/USERTrustRSAAddTrustCA.crt | GB | der | 1.37 Kb | whitelisted |
2668 | iexplore.exe | GET | 200 | 13.32.222.187:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
2668 | iexplore.exe | GET | 200 | 13.32.222.187:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
2668 | iexplore.exe | GET | 200 | 13.32.222.187:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
2668 | iexplore.exe | GET | 200 | 13.32.222.187:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
2668 | iexplore.exe | GET | 200 | 13.32.222.187:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
2668 | iexplore.exe | GET | 200 | 13.32.222.187:80 | http://x.ss2.us/x.cer | US | der | 1.27 Kb | whitelisted |
2668 | iexplore.exe | GET | 200 | 67.27.159.254:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 55.6 Kb | whitelisted |
2668 | iexplore.exe | GET | 200 | 67.27.159.254:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/47BEABC922EAE80E78783462A79F45C254FDE68B.crt | US | der | 969 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2668 | iexplore.exe | 172.217.18.98:443 | googleads.g.doubleclick.net | Google Inc. | US | whitelisted |
3868 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2668 | iexplore.exe | 216.245.208.198:443 | lp.pctonics.com | Limestone Networks, Inc. | US | unknown |
2668 | iexplore.exe | 67.27.159.254:80 | www.download.windowsupdate.com | Level 3 Communications, Inc. | US | malicious |
2668 | iexplore.exe | 13.32.223.80:443 | img.pctonics.com | Amazon.com, Inc. | US | unknown |
2668 | iexplore.exe | 172.217.16.196:443 | www.google.com | Google Inc. | US | whitelisted |
2668 | iexplore.exe | 172.217.21.195:443 | www.google.no | Google Inc. | US | whitelisted |
2668 | iexplore.exe | 13.32.223.90:443 | img.pctonics.com | Amazon.com, Inc. | US | suspicious |
3868 | iexplore.exe | 216.245.208.198:443 | lp.pctonics.com | Limestone Networks, Inc. | US | unknown |
2668 | iexplore.exe | 13.32.222.187:80 | x.ss2.us | Amazon.com, Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
googleads.g.doubleclick.net |
| whitelisted |
lp.pctonics.com |
| unknown |
www.download.windowsupdate.com |
| whitelisted |
ajax.googleapis.com |
| whitelisted |
ssl.google-analytics.com |
| whitelisted |
stats.g.doubleclick.net |
| whitelisted |
img.pctonics.com |
| whitelisted |
code.jquery.com |
| whitelisted |
www.google.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2668 | iexplore.exe | Generic Protocol Command Decode | SURICATA STREAM excessive retransmissions |
2936 | drivertonic[1].exe | Generic Protocol Command Decode | SURICATA STREAM excessive retransmissions |