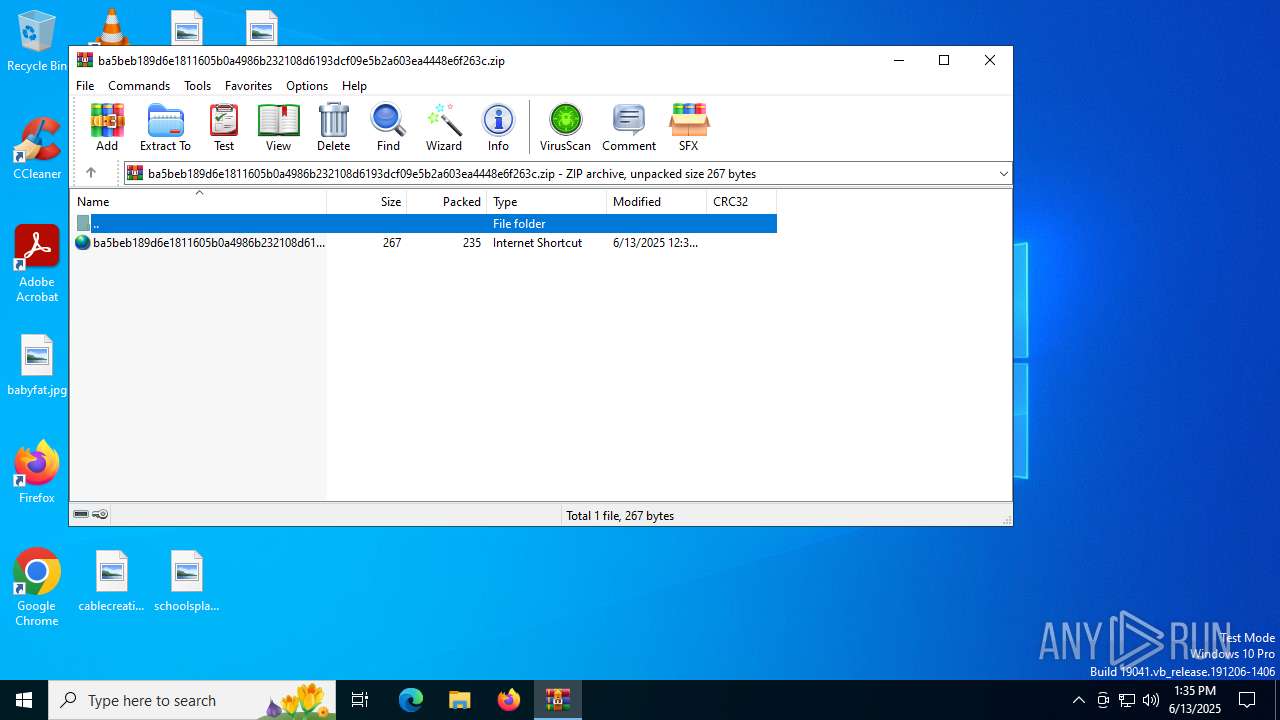
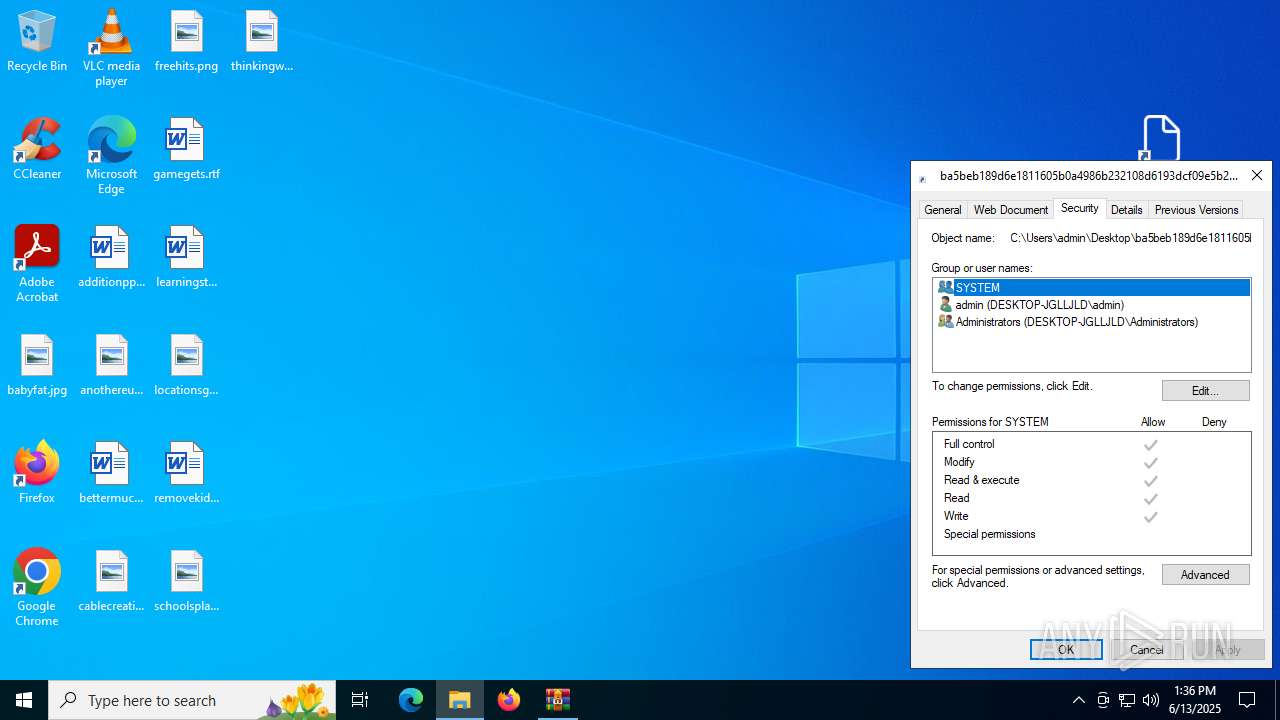
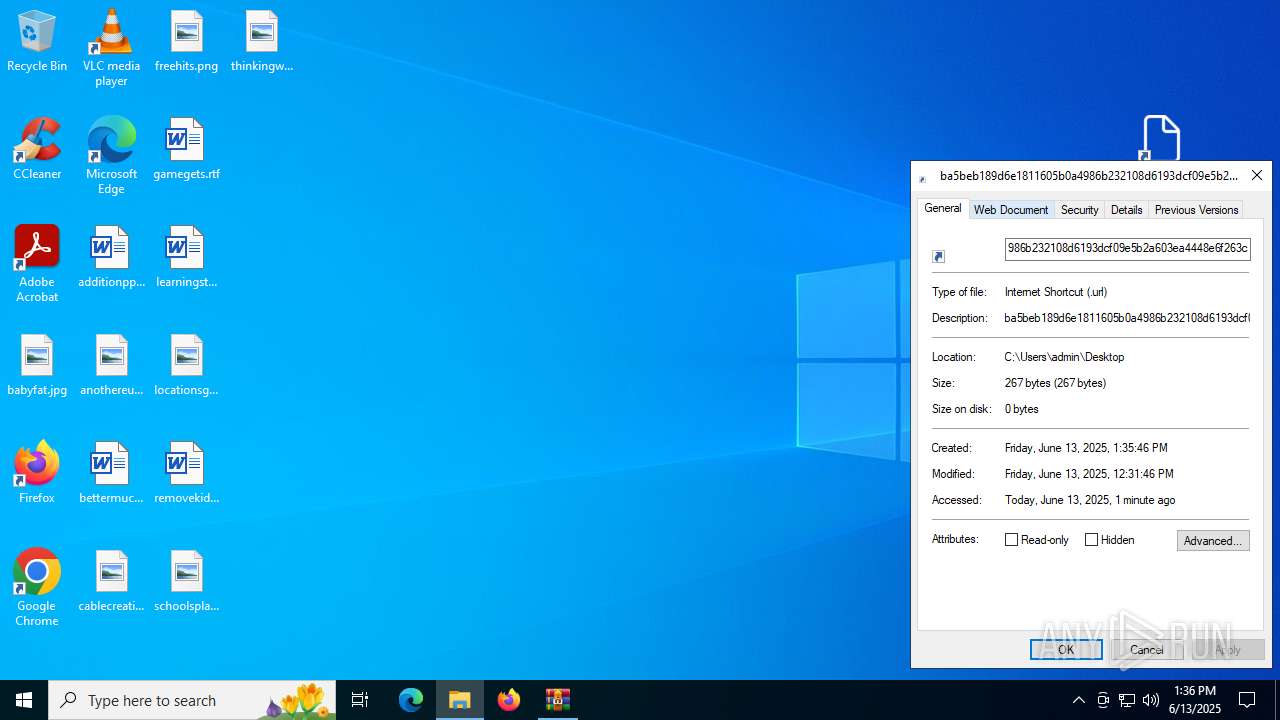
| File name: | ba5beb189d6e1811605b0a4986b232108d6193dcf09e5b2a603ea4448e6f263c.zip |
| Full analysis: | https://app.any.run/tasks/fd8bb7c8-f12d-47ec-9688-84a447c5f0c3 |
| Verdict: | Malicious activity |
| Analysis date: | June 13, 2025, 13:35:10 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
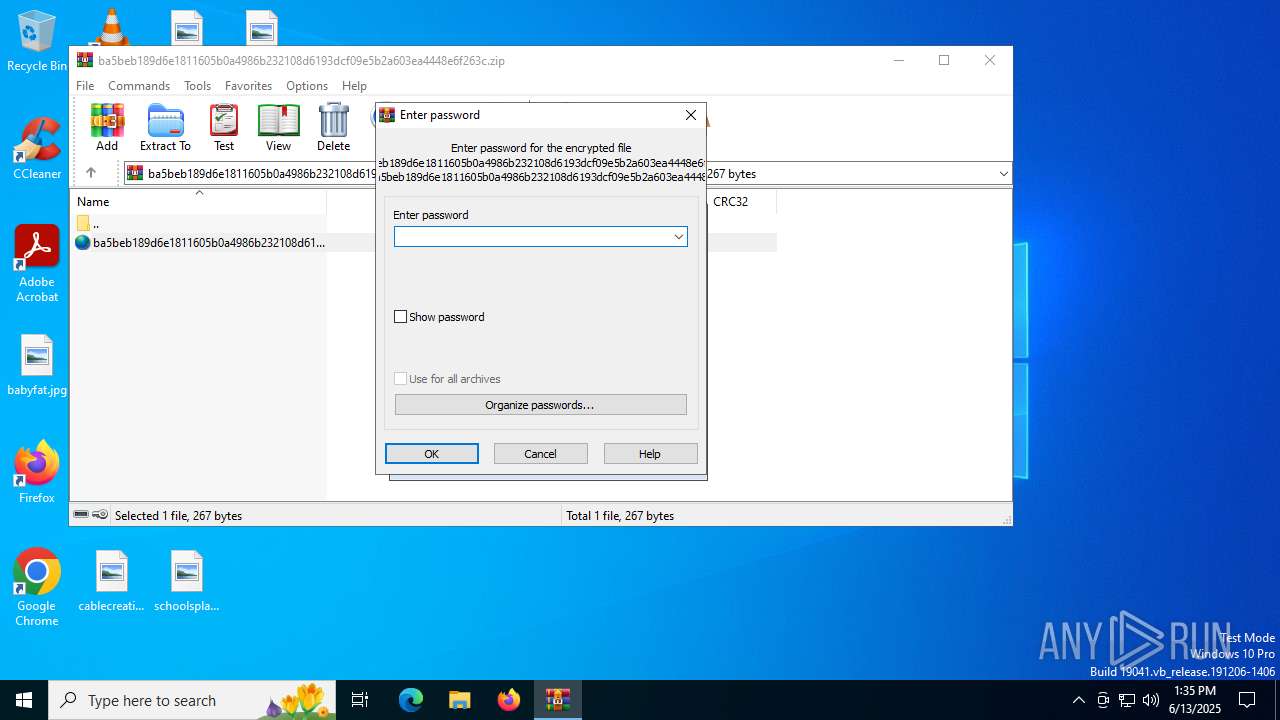
| File info: | Zip archive data, at least v5.1 to extract, compression method=AES Encrypted |
| MD5: | 58092BCAD6E08D3C252E3E35BAC2E64F |
| SHA1: | 9700627797E0EFC5368A30C4E43B53C665A555D9 |
| SHA256: | 5DFA643EE73F514D7080368FB9124C5E3AA9E5903A27478EC848E68C95DDF72A |
| SSDEEP: | 12:5fGAlYh0Guih1KbOuUgkWxdjvuNiKhcydLHuMBk9CYYTFv8Vllch0GuiPai:/ah7XhI+gk8ukKcX9CnAvch7XP |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 4192)
- iediagcmd.exe (PID: 2148)
Creates file in the systems drive root
- WinRAR.exe (PID: 4192)
SMB connection has been detected (probably for file transfer)
- explorer.exe (PID: 4772)
Uses RUNDLL32.EXE to load library
- svchost.exe (PID: 6732)
Uses pipe srvsvc via SMB (transferring data)
- explorer.exe (PID: 4772)
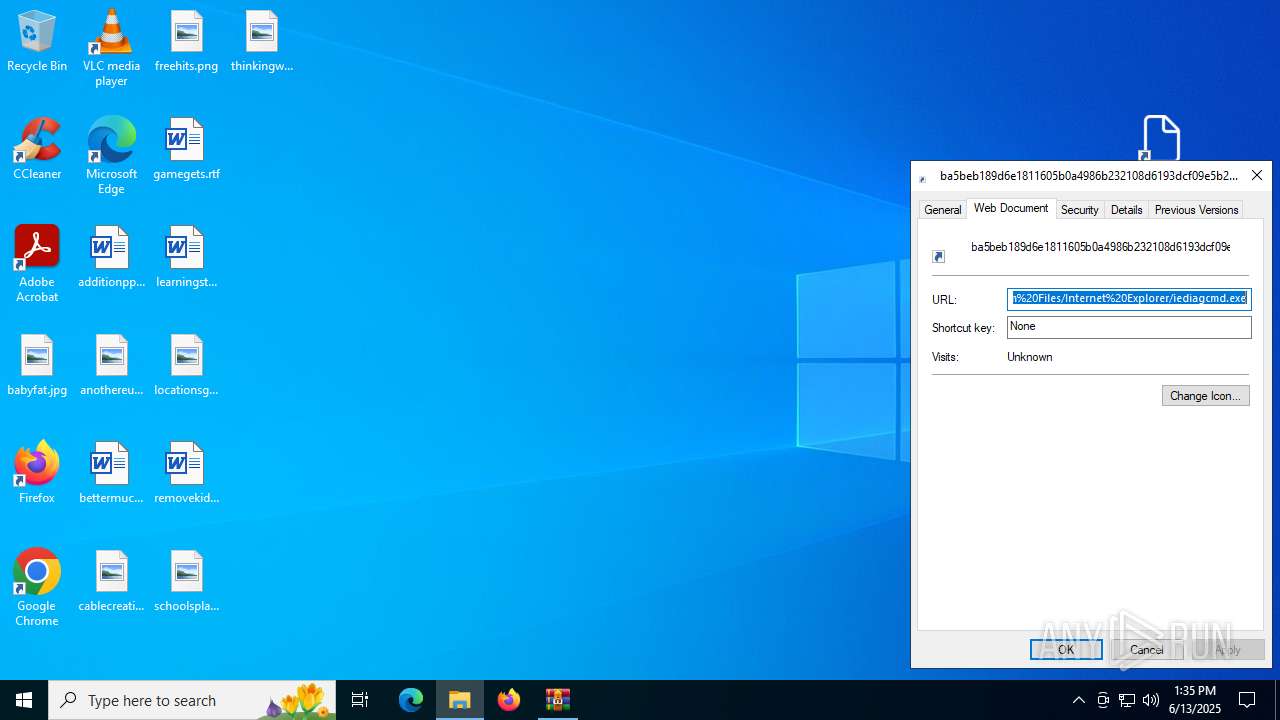
Abuses WebDav for code execution
- svchost.exe (PID: 6732)
Process uses IPCONFIG to discover network configuration
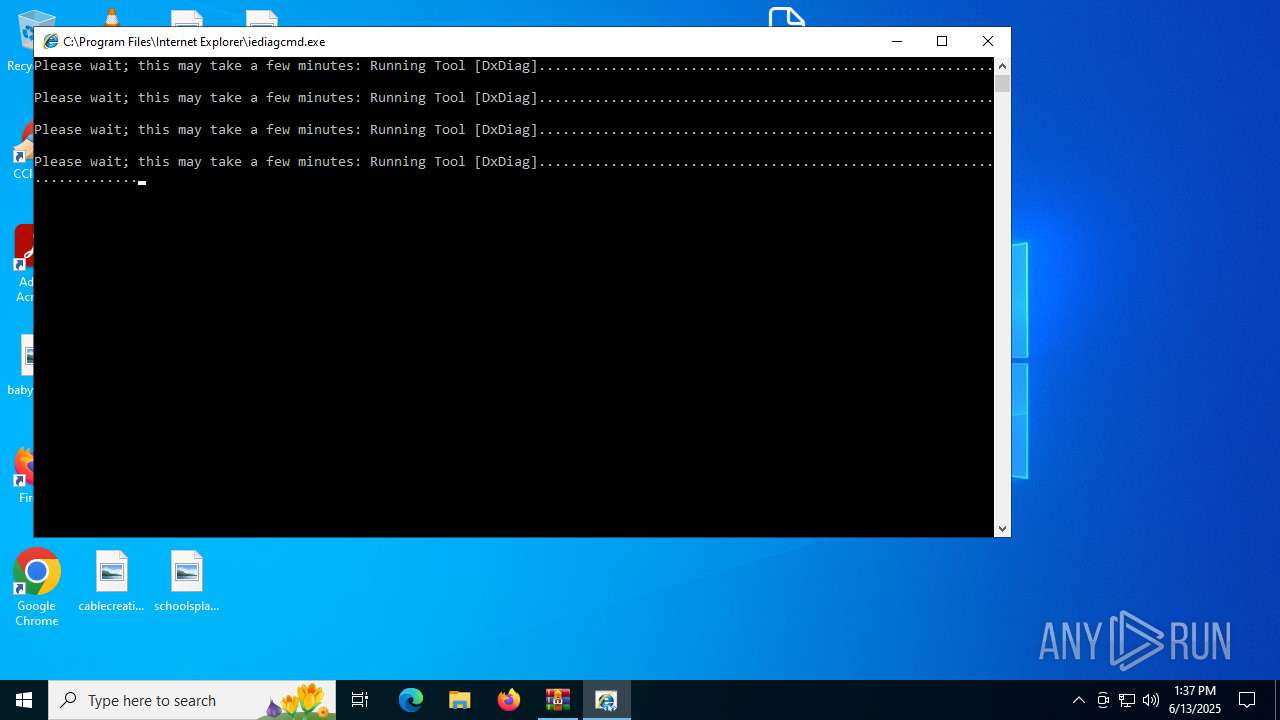
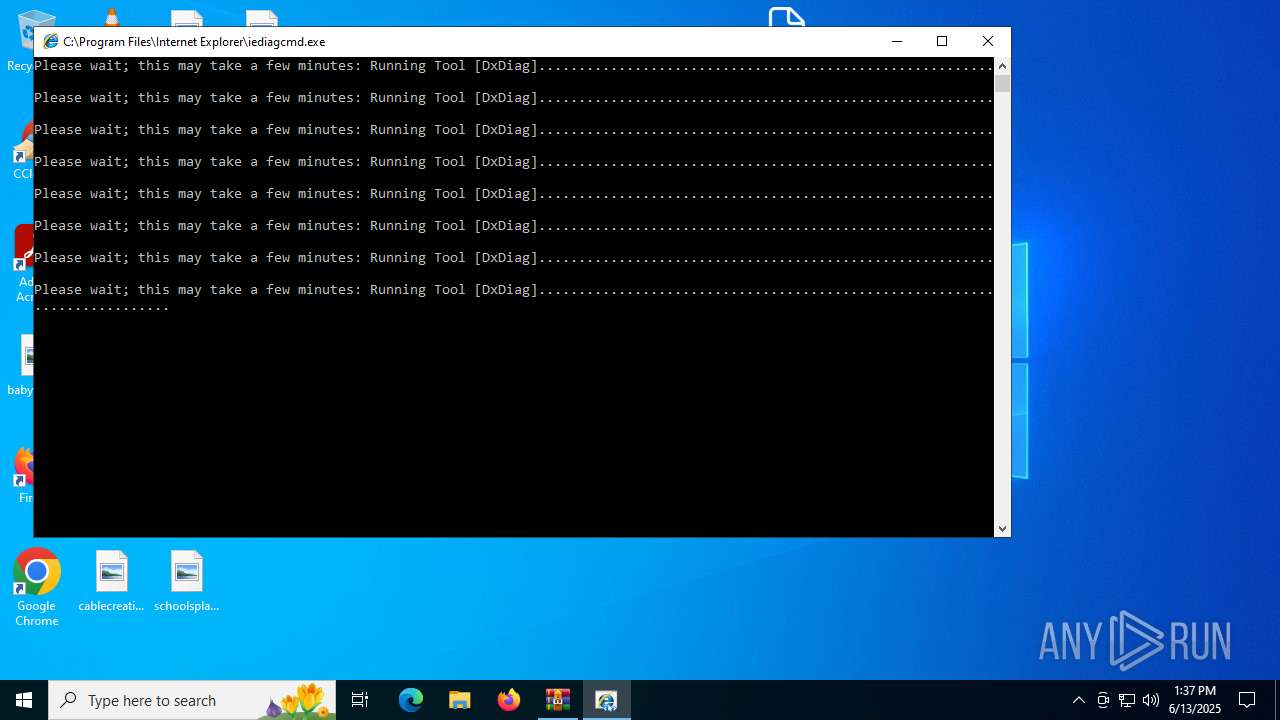
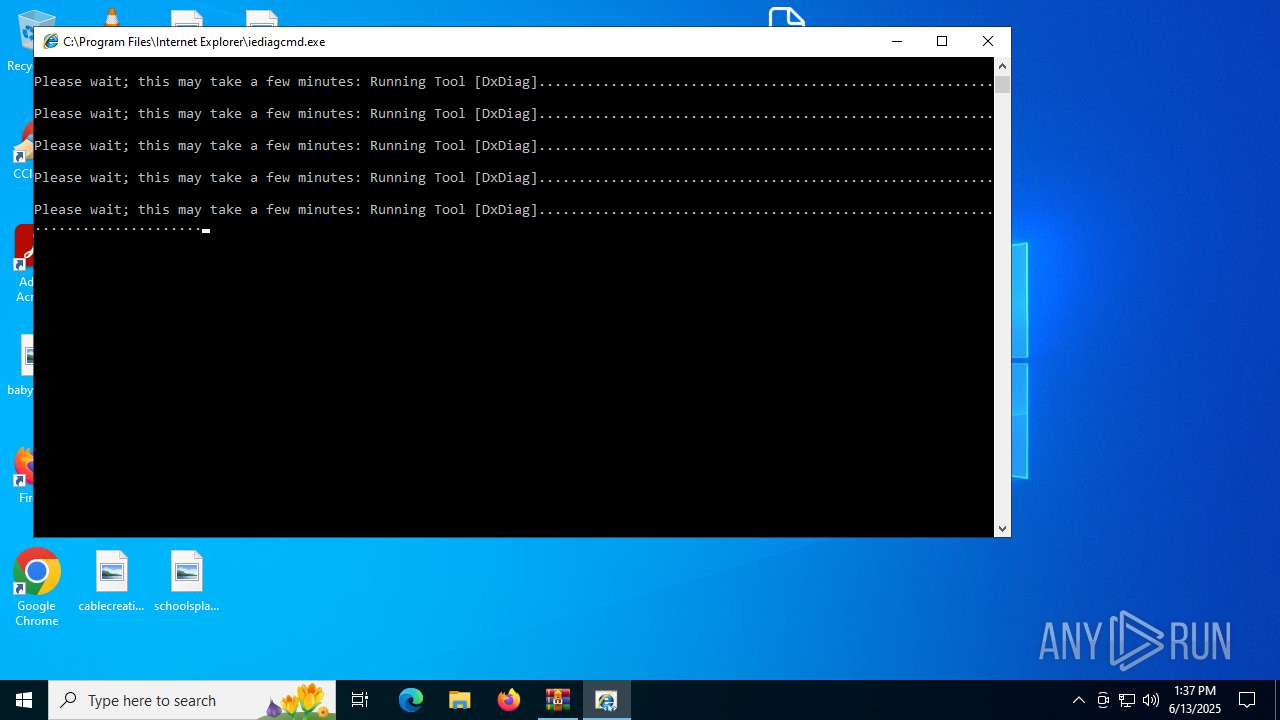
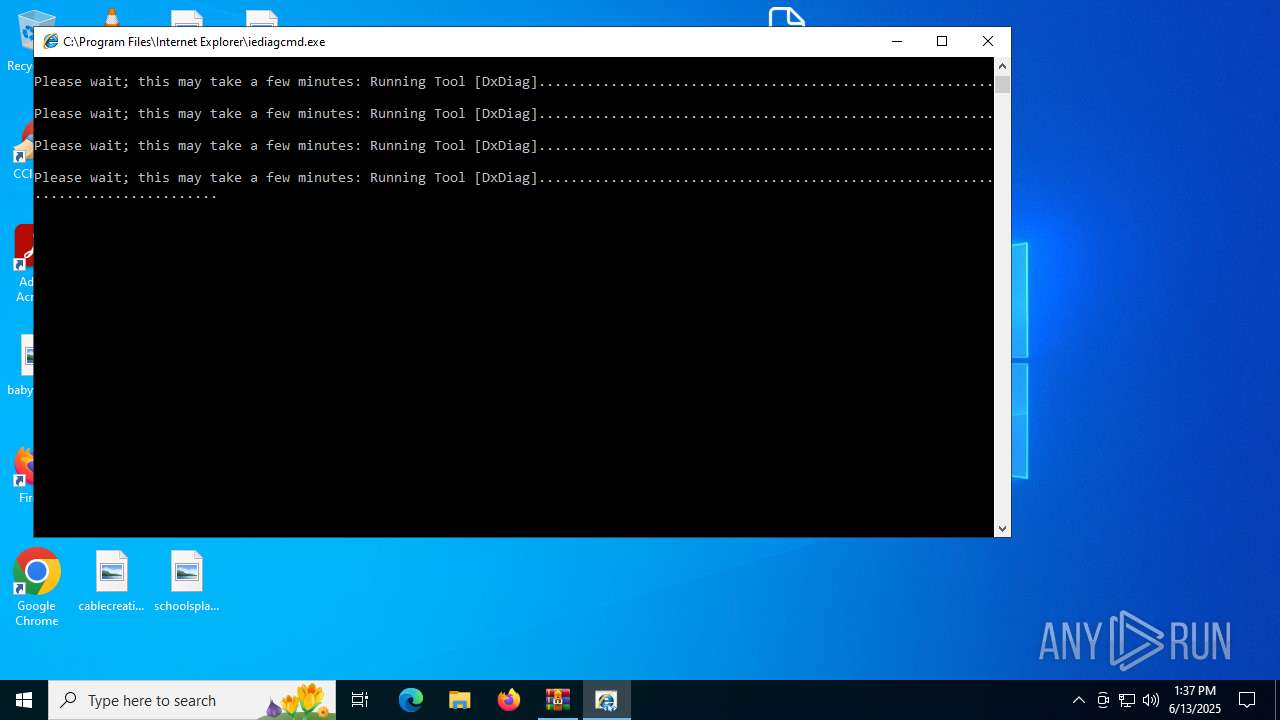
- iediagcmd.exe (PID: 2148)
Executable content was dropped or overwritten
- svchost.exe (PID: 6732)
Suspicious use of NETSH.EXE
- iediagcmd.exe (PID: 2148)
INFO
Local mutex for internet shortcut management
- WinRAR.exe (PID: 4192)
Creates files or folders in the user directory
- explorer.exe (PID: 4772)
- dxdiag.exe (PID: 2664)
Reads security settings of Internet Explorer
- explorer.exe (PID: 4772)
- dxdiag.exe (PID: 2664)
Reads the software policy settings
- explorer.exe (PID: 4772)
- dxdiag.exe (PID: 2664)
- slui.exe (PID: 3720)
Checks proxy server information
- explorer.exe (PID: 4772)
- iediagcmd.exe (PID: 2148)
- dxdiag.exe (PID: 2664)
- slui.exe (PID: 3720)
Reads the computer name
- iediagcmd.exe (PID: 2148)
Reads the machine GUID from the registry
- iediagcmd.exe (PID: 2148)
Checks supported languages
- iediagcmd.exe (PID: 2148)
Application launched itself
- msedge.exe (PID: 6004)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0003 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2025:06:13 12:31:46 |
| ZipCRC: | 0x28c368bb |
| ZipCompressedSize: | 235 |
| ZipUncompressedSize: | 267 |
| ZipFileName: | ba5beb189d6e1811605b0a4986b232108d6193dcf09e5b2a603ea4448e6f263c.url |
Total processes
190
Monitored processes
36
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1052 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | ipconfig.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1208 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=6524,i,3398967348410828301,6090067084311006919,262144 --variations-seed-version --mojo-platform-channel-handle=6656 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1212 | "ipconfig" /all | C:\Windows\System32\ipconfig.exe | — | iediagcmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: IP Configuration Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1480 | "C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=6188,i,3398967348410828301,6090067084311006919,262144 --variations-seed-version --mojo-platform-channel-handle=6228 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\133.0.3065.92\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 3221226029 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1660 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=gpu-process --string-annotations --gpu-preferences=UAAAAAAAAADgAAAEAAAAAAAAAAAAAAAAAABgAAEAAAAAAAAAAAAAAAAAAAACAAAAAAAAAAAAAAAAAAAAAAAAABAAAAAAAAAAEAAAAAAAAAAIAAAAAAAAAAgAAAAAAAAA --always-read-main-dll --field-trial-handle=2412,i,3398967348410828301,6090067084311006919,262144 --variations-seed-version --mojo-platform-channel-handle=2404 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1932 | "C:\WINDOWS\system32\netsh.exe" in tcp show global | C:\Windows\System32\netsh.exe | — | iediagcmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2044 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | netsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
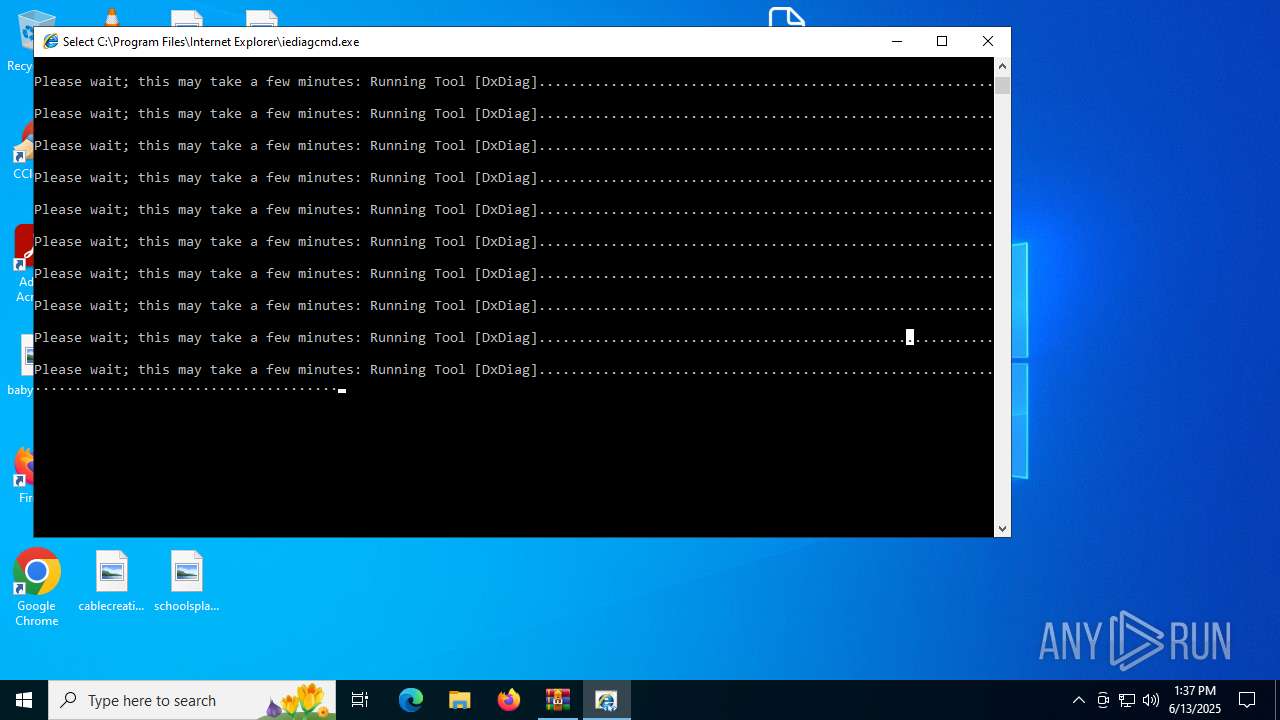
| 2148 | "C:\Program Files\Internet Explorer\iediagcmd.exe" | C:\Program Files\Internet Explorer\iediagcmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Diagnostics utility for Internet Explorer Version: 11.00.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2664 | "C:\WINDOWS\system32\dxdiag.exe" /x C:\Users\admin\AppData\Local\Temp\dxdiag.xml | C:\Windows\System32\dxdiag.exe | iediagcmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft DirectX Diagnostic Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2716 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=renderer --string-annotations --extension-process --renderer-sub-type=extension --video-capture-use-gpu-memory-buffer --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=7 --always-read-main-dll --field-trial-handle=4296,i,3398967348410828301,6090067084311006919,262144 --variations-seed-version --mojo-platform-channel-handle=4308 /prefetch:2 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
Total events
86 214
Read events
86 027
Write events
165
Delete events
22
Modification events
| (PID) Process: | (4772) explorer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\SessionInfo\1\ApplicationViewManagement\W32:00000000000502FA |
| Operation: | write | Name: | VirtualDesktop |
Value: 10000000303044563096AFED4A643448A750FA41CFC7F708 | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\ba5beb189d6e1811605b0a4986b232108d6193dcf09e5b2a603ea4448e6f263c.zip | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4192) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
1
Suspicious files
200
Text files
45
Unknown types
26
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2148 | iediagcmd.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\66AE3BFDF94A732B262342AD2154B86E_A0A493DFC200ABD74A599ECA1E199CDC | der | |
MD5:435DD6C5BBA2C6352BFB0B90B422AADE | SHA256:B856F1B34A12EEE1D7CB0D84935E4A8EA2DD1D5E236EDAB8D432461A6734F2FB | |||
| 4192 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb4192.5066\ba5beb189d6e1811605b0a4986b232108d6193dcf09e5b2a603ea4448e6f263c.url | url | |
MD5:33922ECB35A51A1F1999C4FEF4C10187 | SHA256:BA5BEB189D6E1811605B0A4986B232108D6193DCF09E5B2A603EA4448E6F263C | |||
| 4772 | explorer.exe | C:\Users\admin\AppData\Local\Microsoft\PenWorkspace\DiscoverCacheData.dat | binary | |
MD5:E49C56350AEDF784BFE00E444B879672 | SHA256:A8BD235303668981563DFB5AAE338CB802817C4060E2C199B7C84901D57B7E1E | |||
| 6732 | svchost.exe | C:\Windows\ServiceProfiles\LocalService\AppData\Local\Temp\TfsStore\Tfs_DAV\{B1B390AC-D16D-4E33-81F6-514D20EB62E3}.exe | executable | |
MD5:B2D5F620B672BF58A68731A68D62DC82 | SHA256:DA3BB6E38B3F4D83E69D31783F00C10CE062ABD008E81E983A9BD4317A9482AA | |||
| 4772 | explorer.exe | C:\Users\admin\Desktop\ba5beb189d6e1811605b0a4986b232108d6193dcf09e5b2a603ea4448e6f263c.url | url | |
MD5:33922ECB35A51A1F1999C4FEF4C10187 | SHA256:BA5BEB189D6E1811605B0A4986B232108D6193DCF09E5B2A603EA4448E6F263C | |||
| 4772 | explorer.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\AutomaticDestinations\f01b4d95cf55d32a.automaticDestinations-ms | binary | |
MD5:3544EFAC8FEF6CB387BB1CDCC1A0FA9A | SHA256:20F5E04B64FA9F1E3C65DD7BD6B51661D767EB9CD380736FEDE6BACB3F8B5A61 | |||
| 2664 | dxdiag.exe | C:\Users\admin\AppData\Local\D3DSCache\b349d32bb264b90e\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.val | binary | |
MD5:C0627BA18EF48A97CA50DB7FEC75E930 | SHA256:6DFB63072ECE7388CC695EB12A981D71CEA1C06D9A919ABF57AB0F4BA90F759D | |||
| 2664 | dxdiag.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A583E2A51BFBDC1E492A57B7C8325850 | der | |
MD5:144D698C7F3CCD662F9460D8F443A2BB | SHA256:C5714AC85358D727F4EA913F814CCADCD7F6E063D95B54B886CCF6BFC31612C1 | |||
| 2664 | dxdiag.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\45AE547469FB7137480E06153457A2DD | der | |
MD5:999F18B229A3BE4FE54BA752523824C3 | SHA256:31570767386CAECEF0F8907AFB58D20C77A6AB91A07FA4B3620802FE205D417E | |||
| 2664 | dxdiag.exe | C:\Users\admin\AppData\Local\D3DSCache\b349d32bb264b90e\F4EB2D6C-ED2B-4BDD-AD9D-F913287E6768.lock | text | |
MD5:F49655F856ACB8884CC0ACE29216F511 | SHA256:7852FCE59C67DDF1D6B8B997EAA1ADFAC004A9F3A91C37295DE9223674011FBA | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
109
DNS requests
56
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4520 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2664 | dxdiag.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
5924 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4520 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2664 | dxdiag.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicWinProPCA2011_2011-10-19.crl%20 | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2940 | svchost.exe | GET | 200 | 23.209.209.135:80 | http://x1.c.lencr.org/ | unknown | — | — | whitelisted |
5328 | SearchApp.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5708 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
4520 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4520 | SIHClient.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |