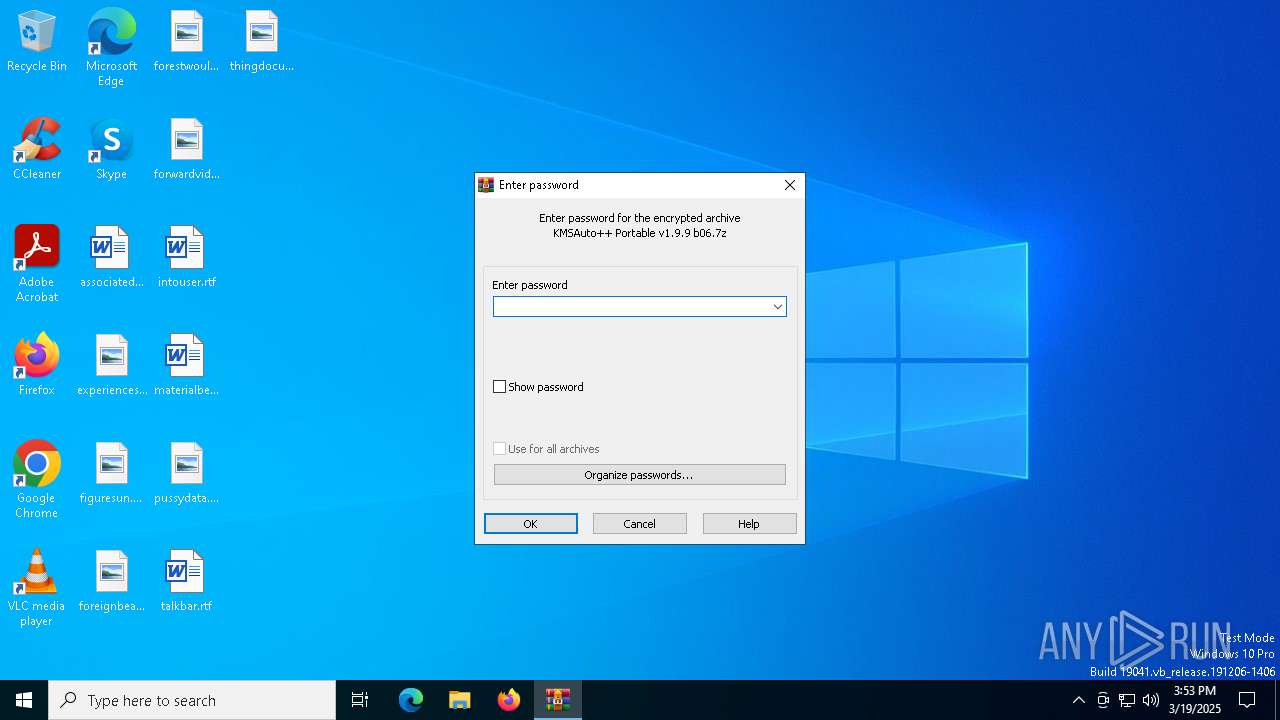
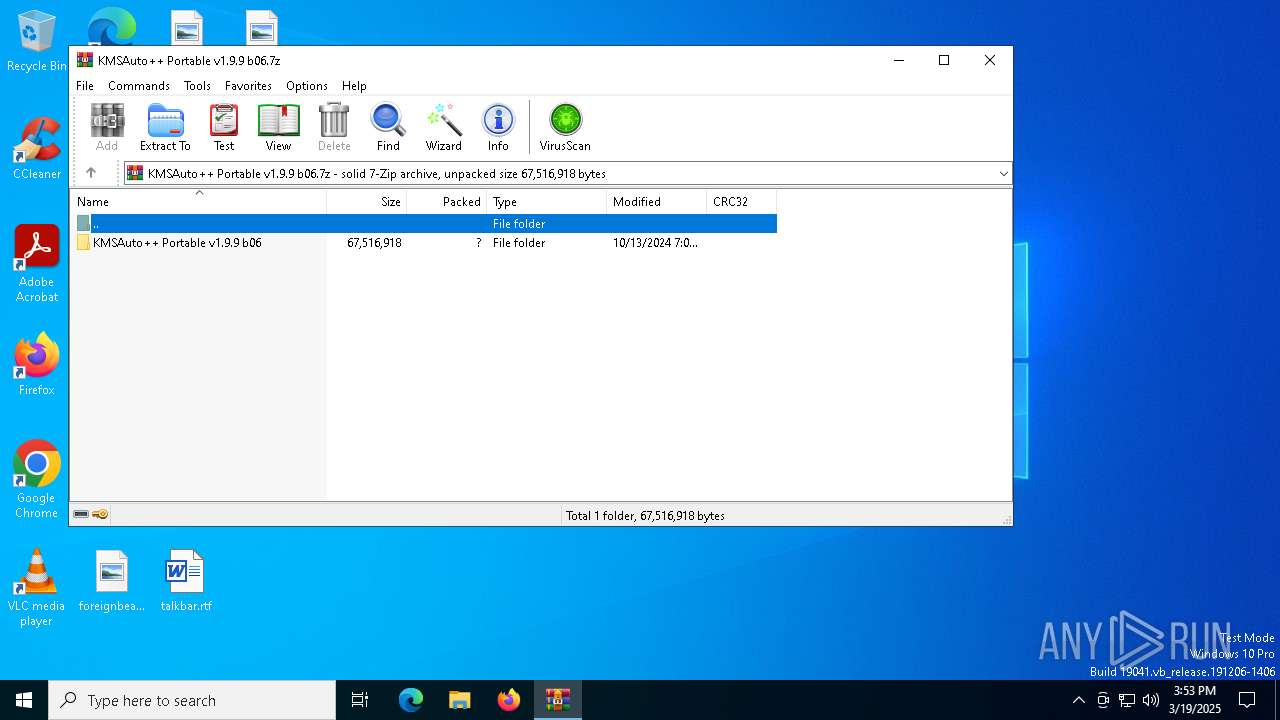
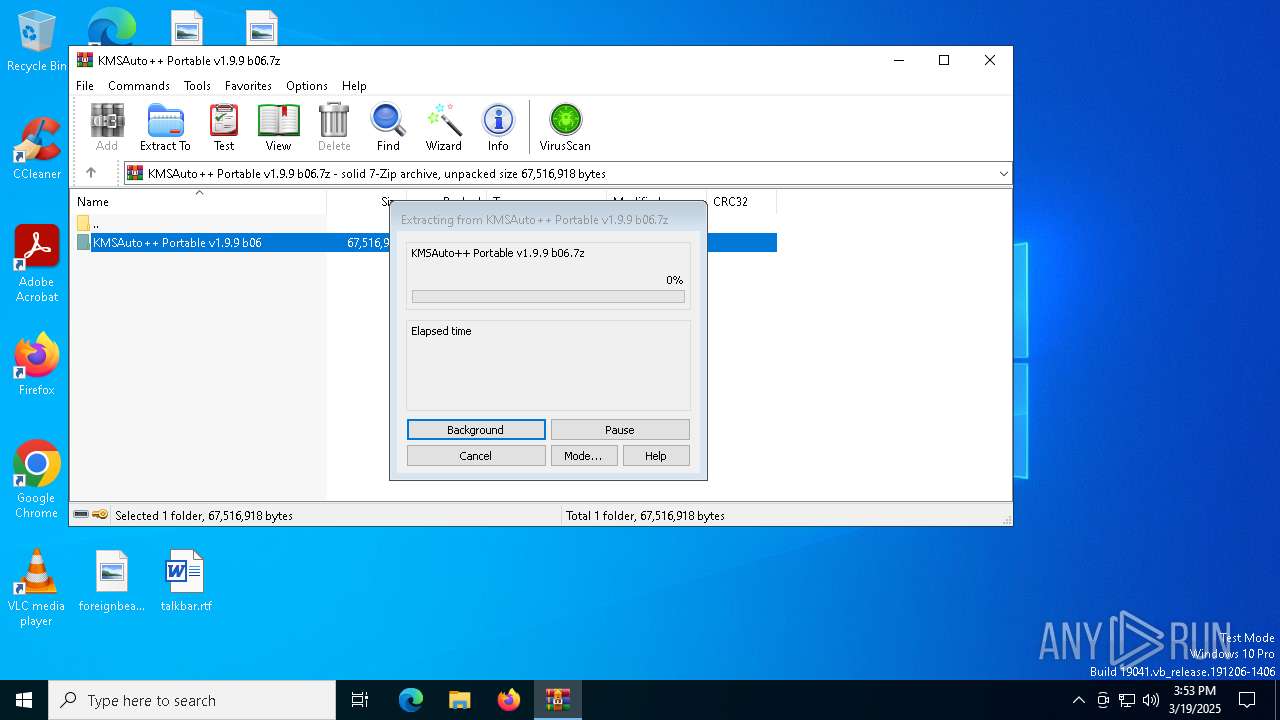
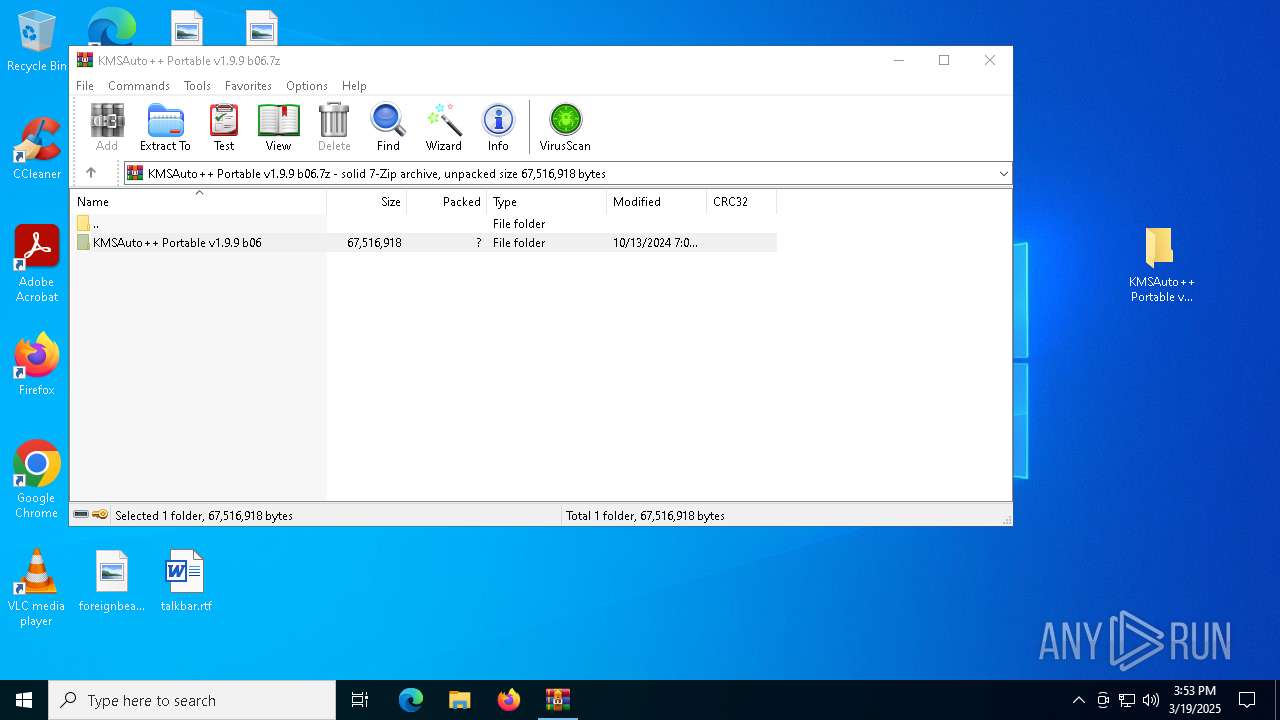
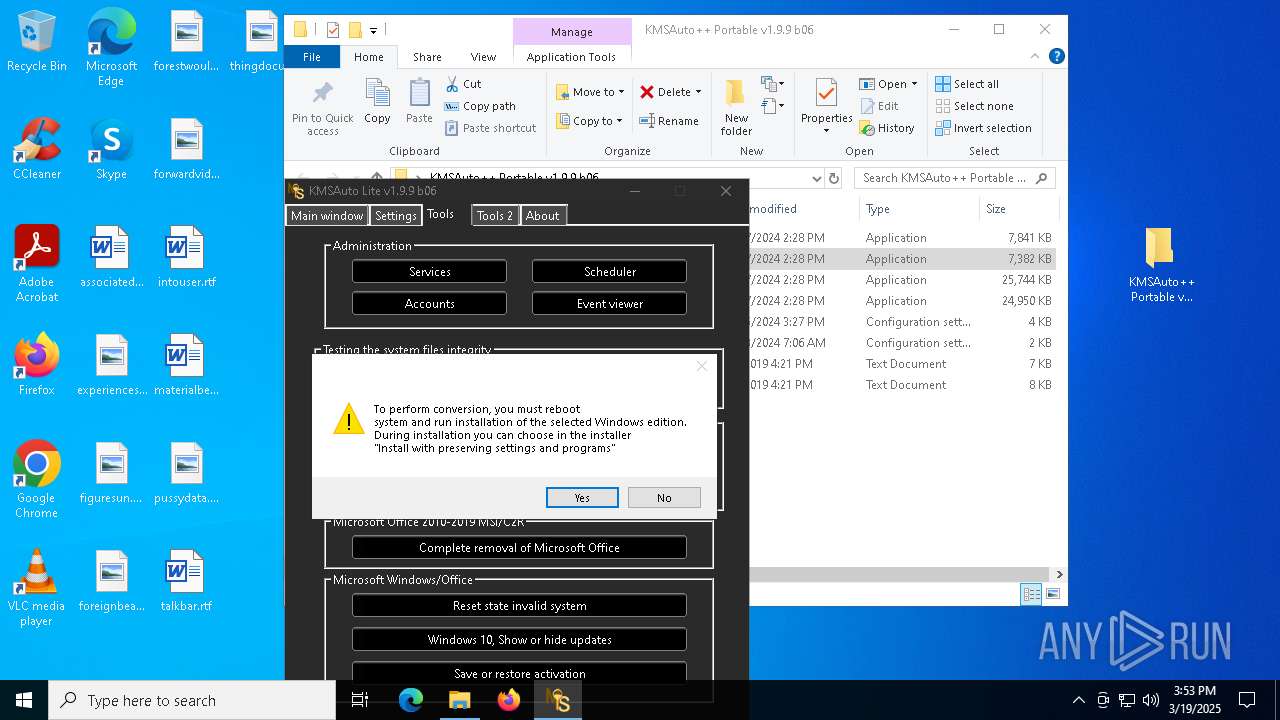
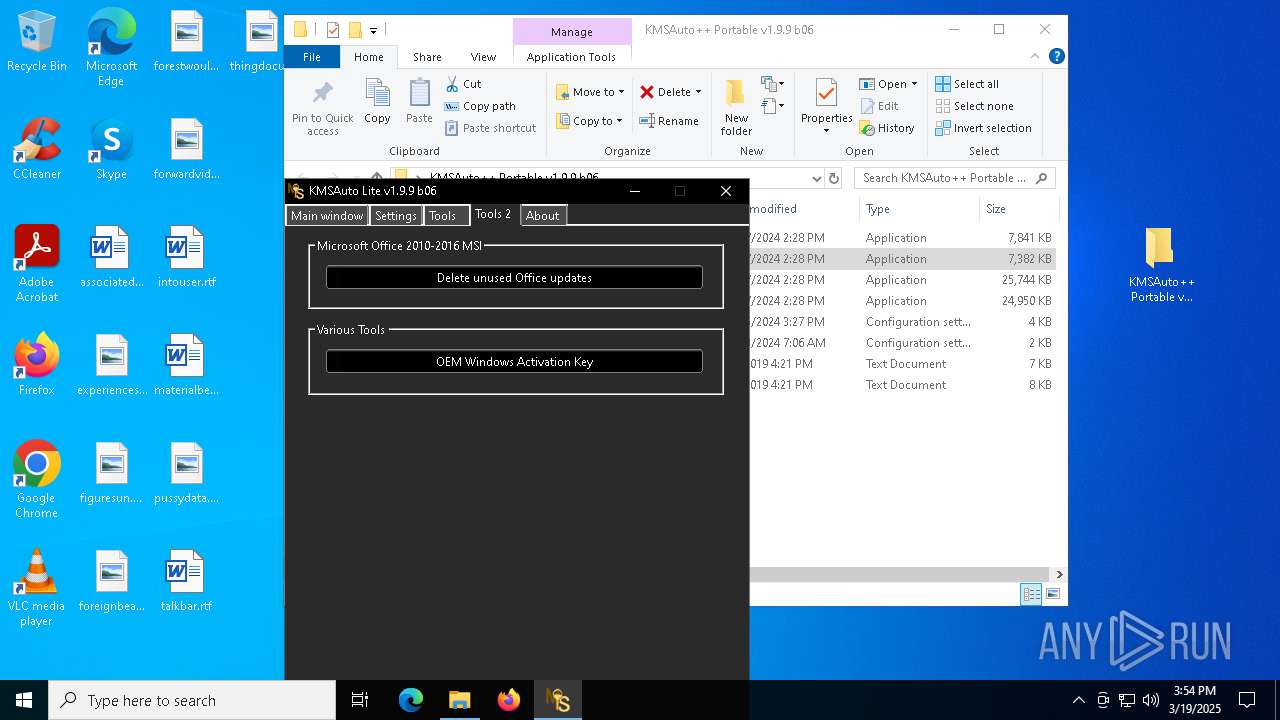
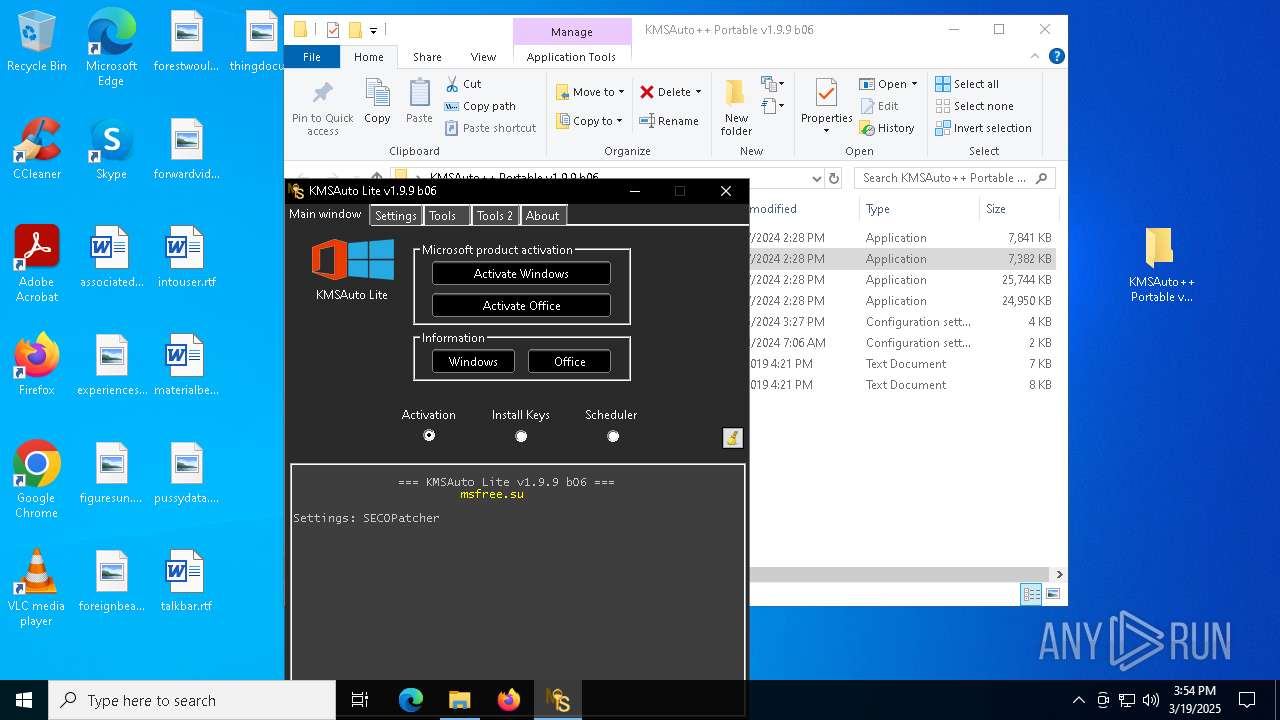
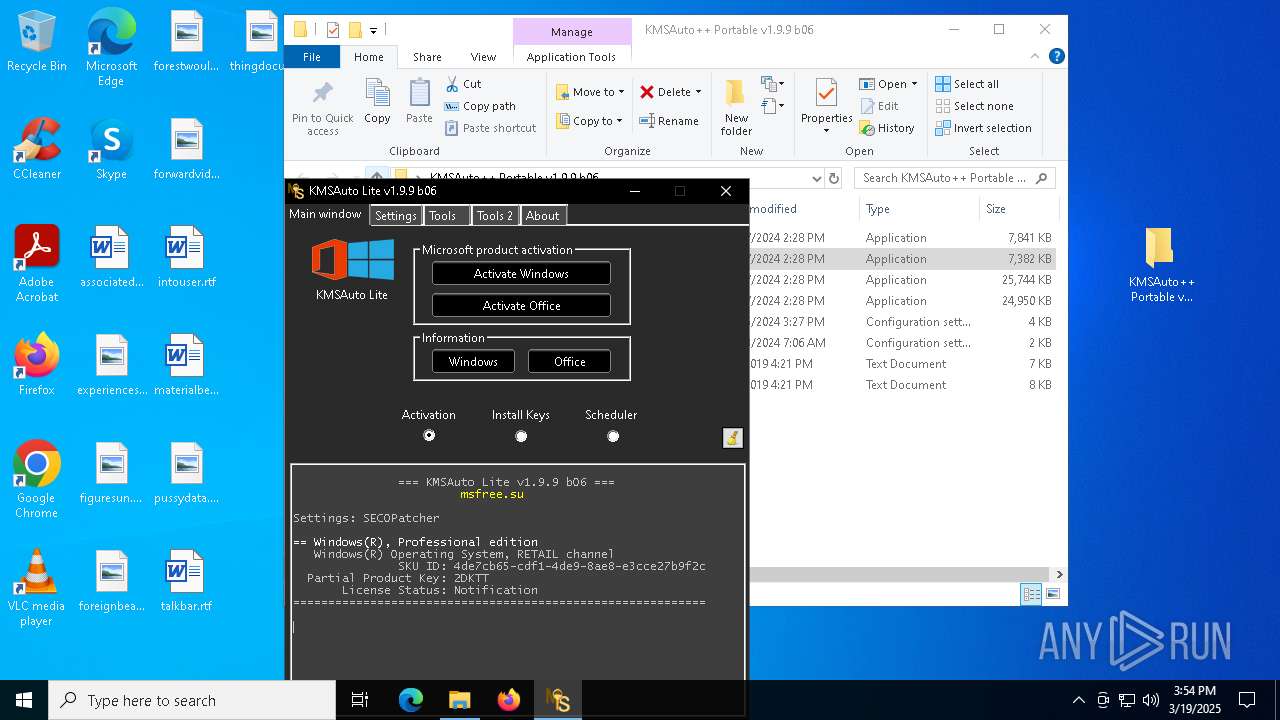
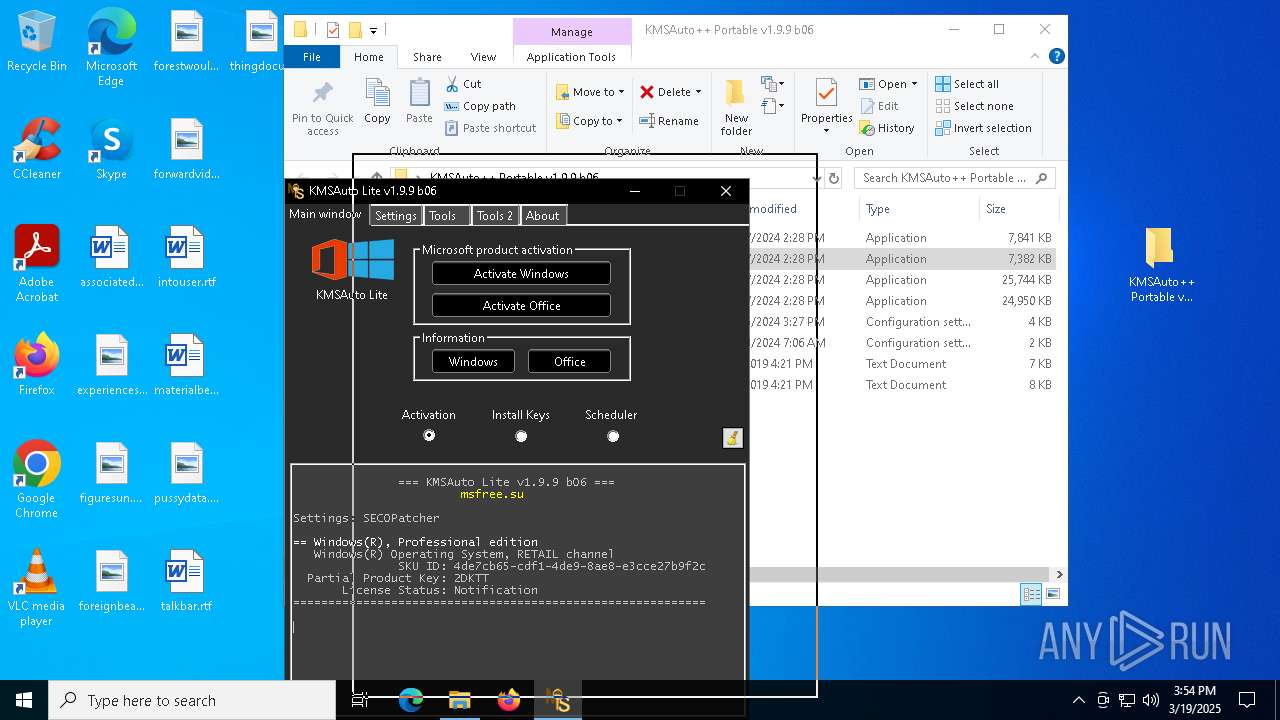
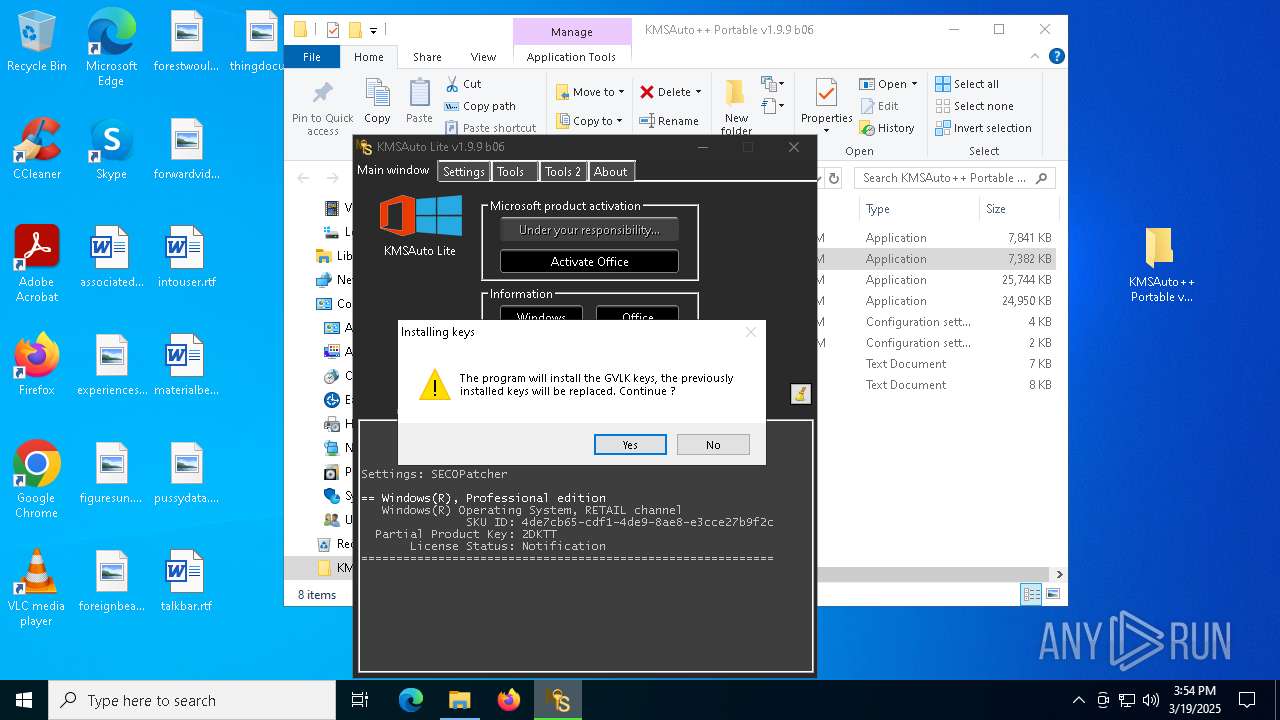
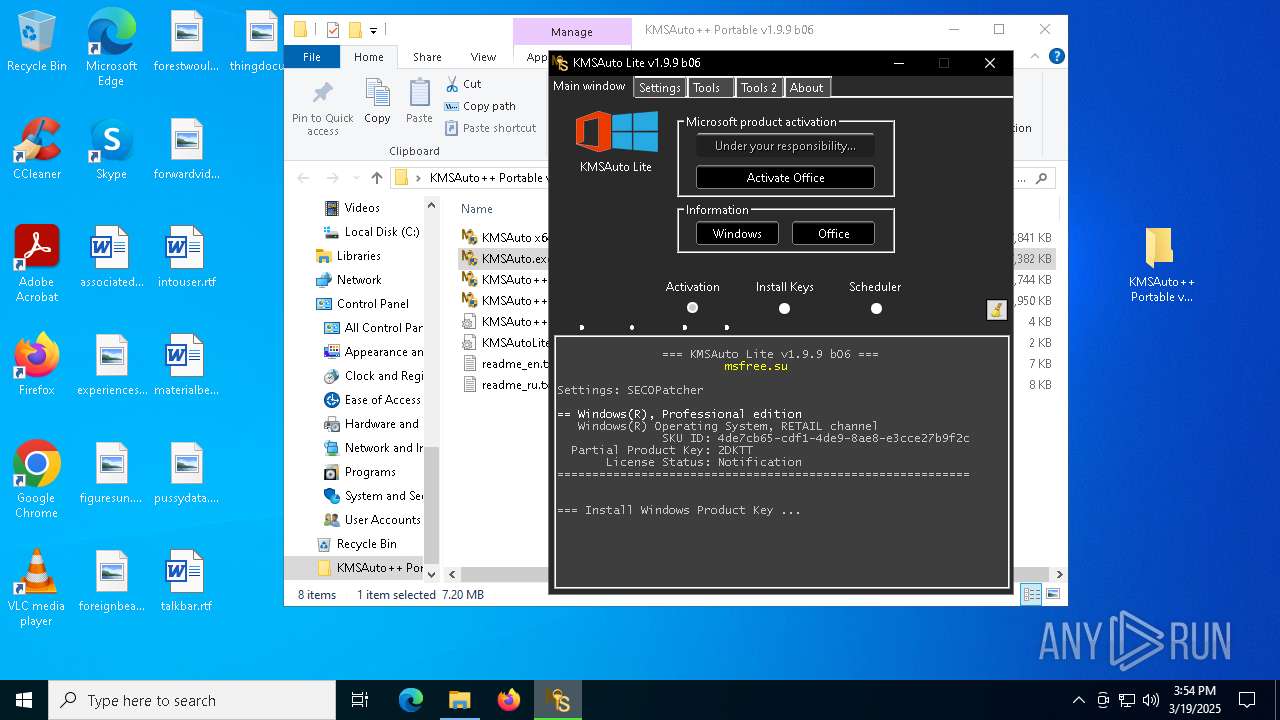
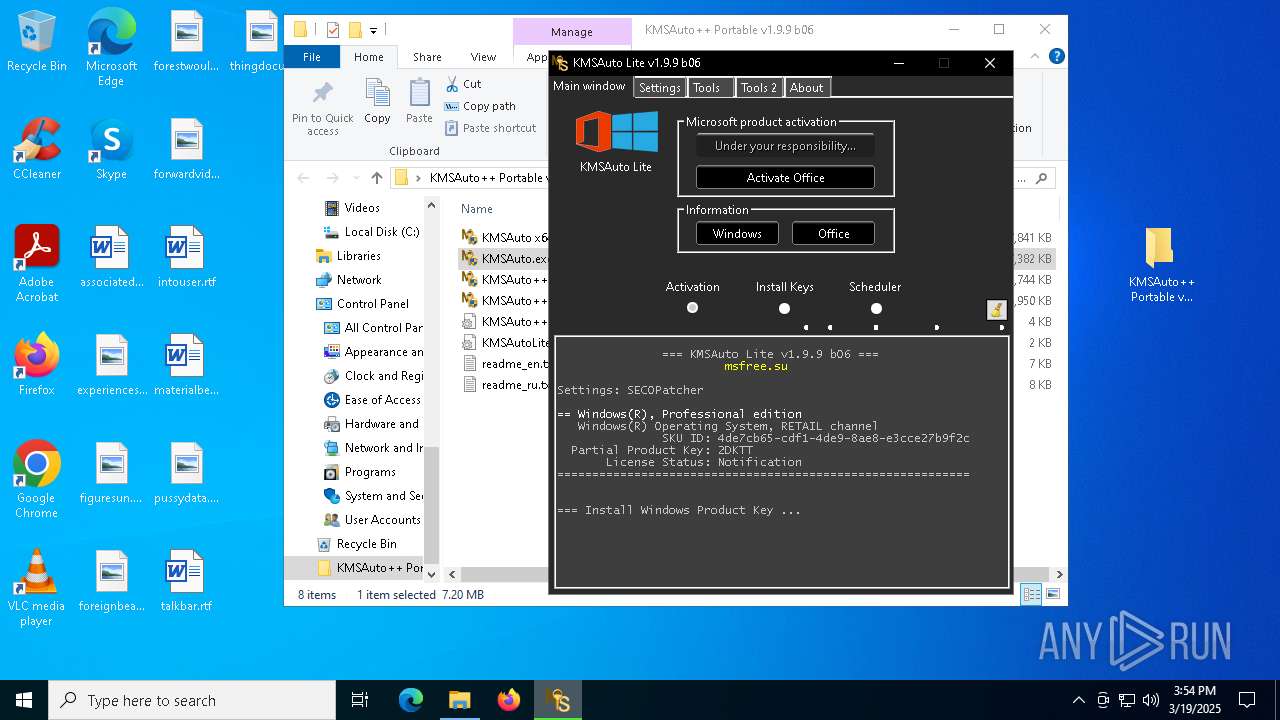
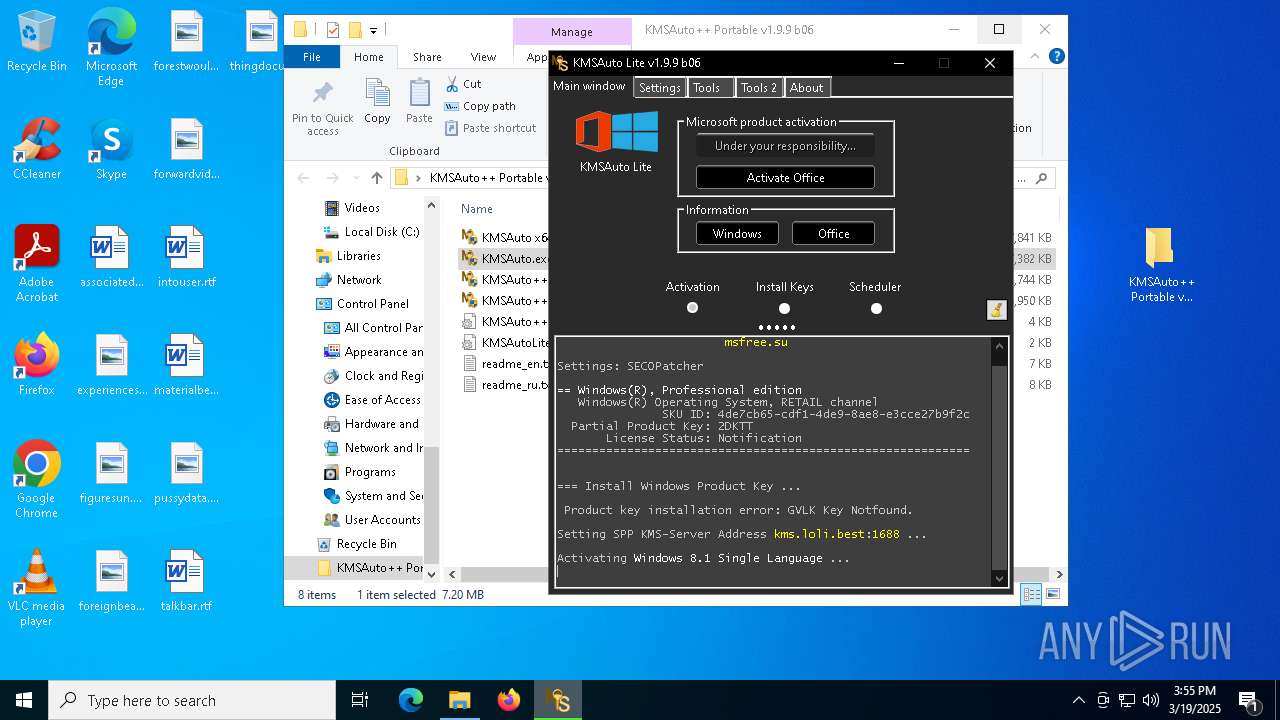
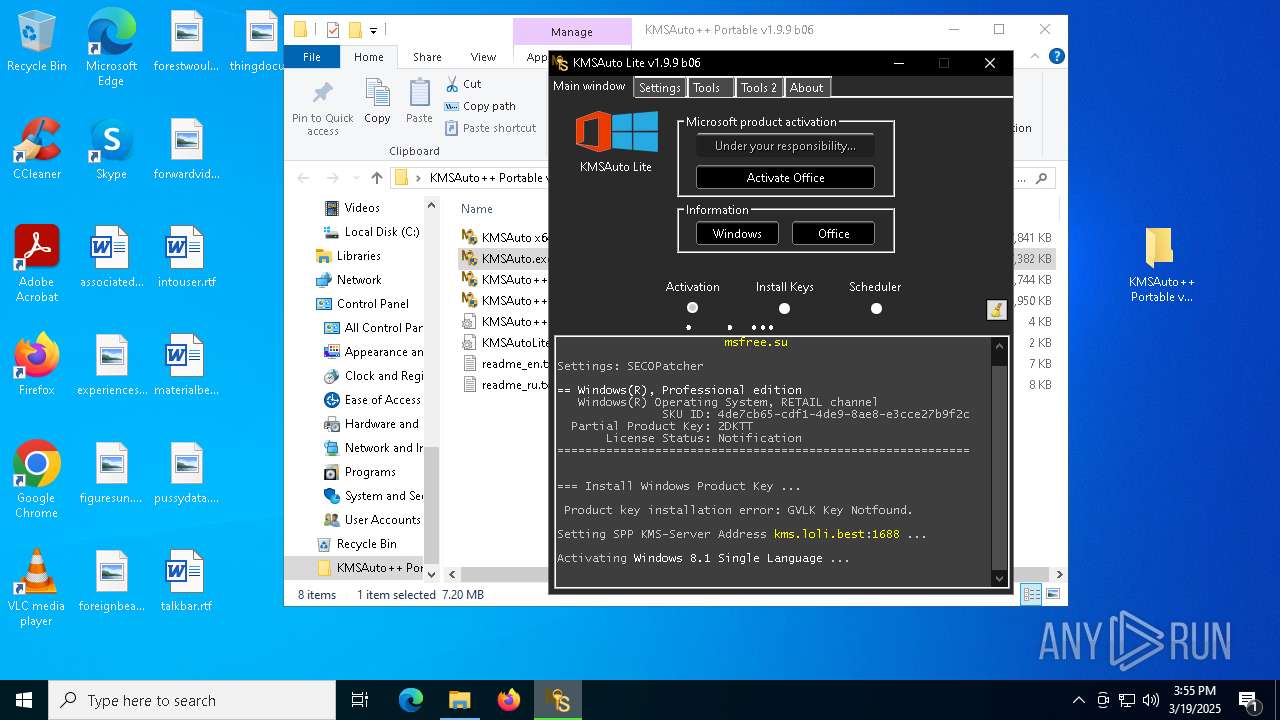
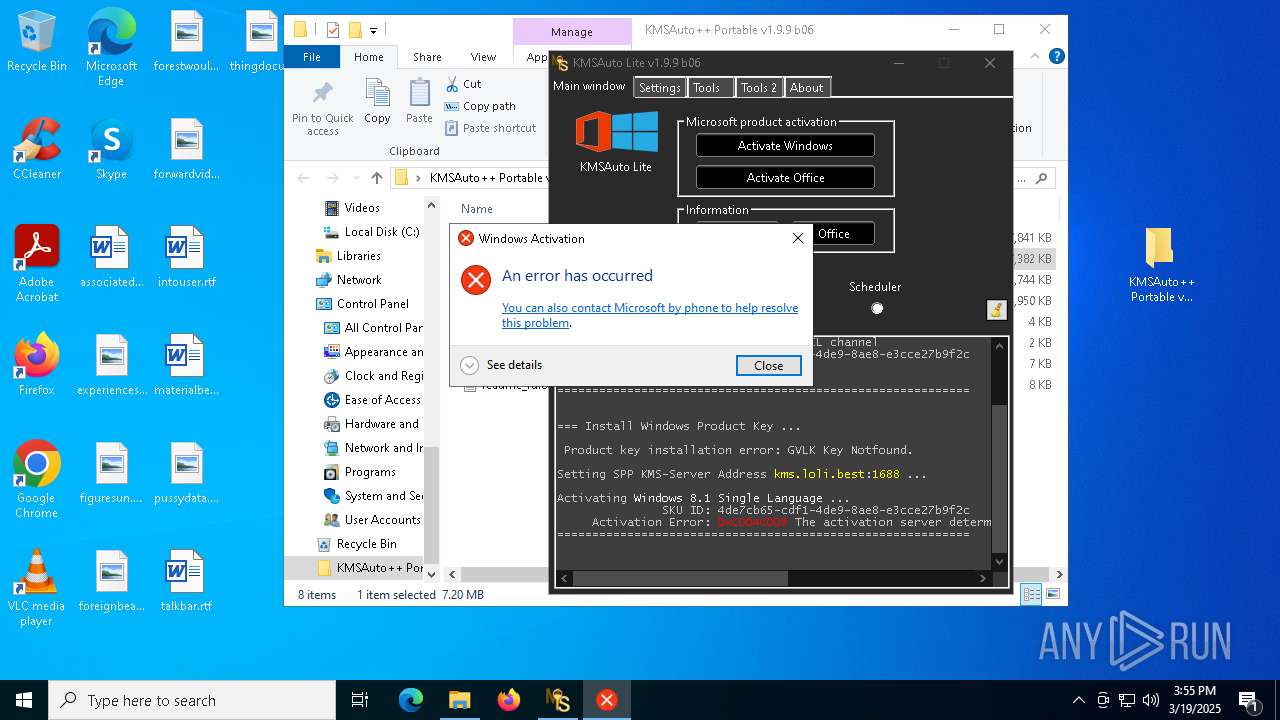
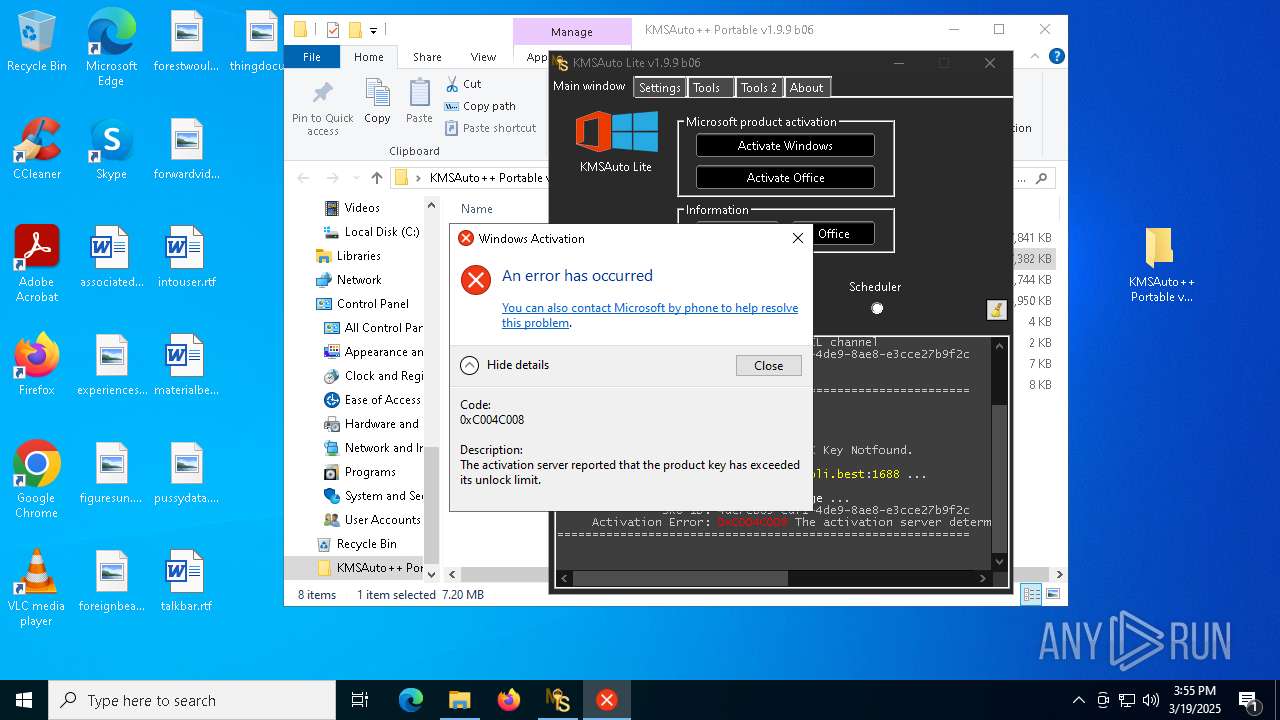
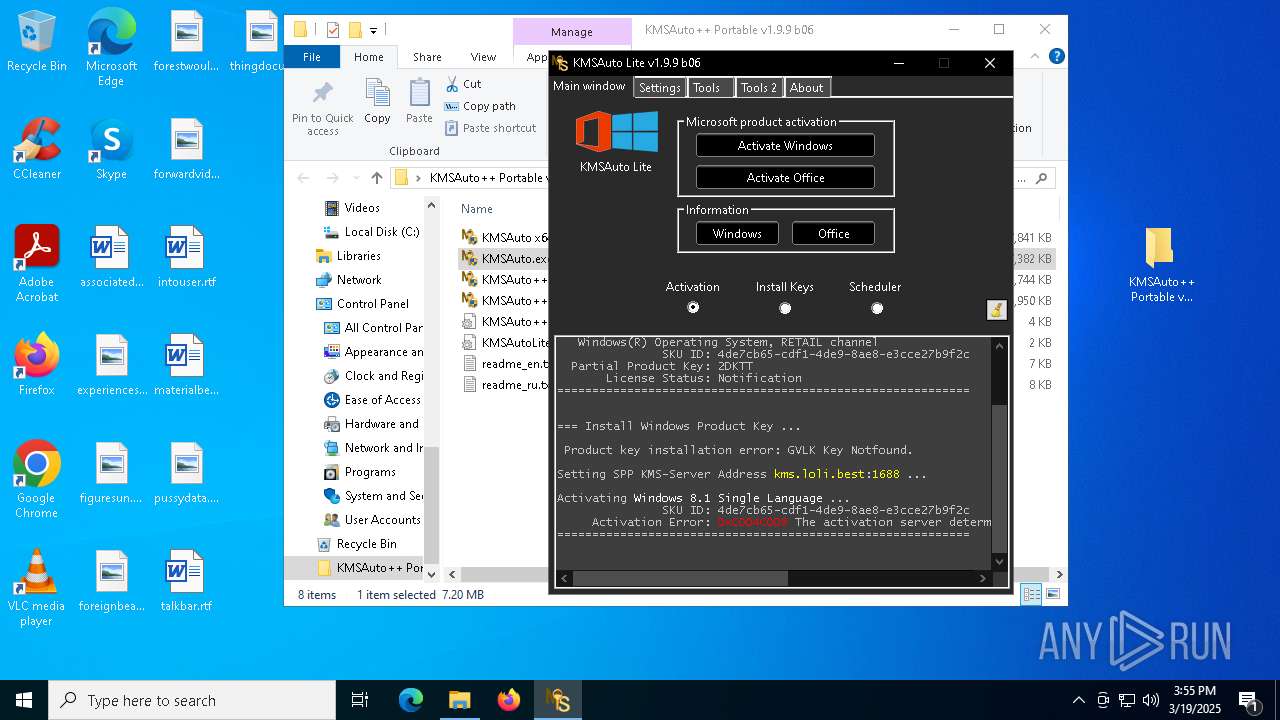
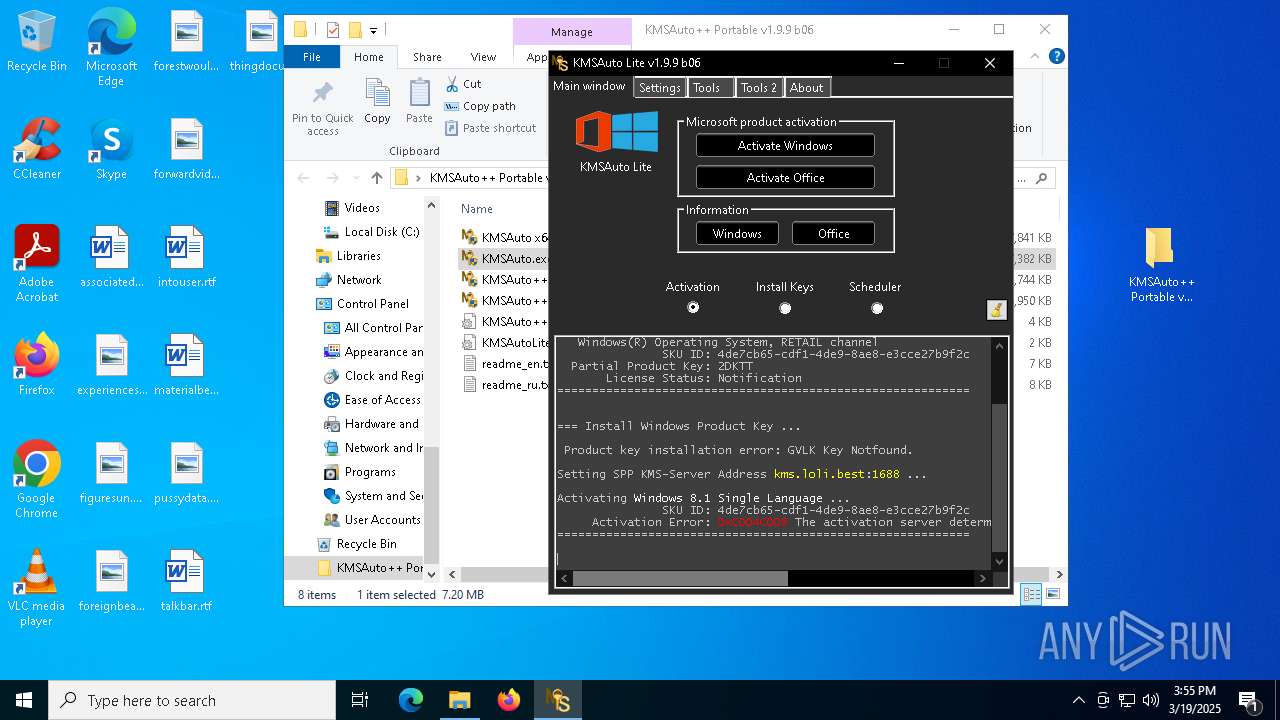
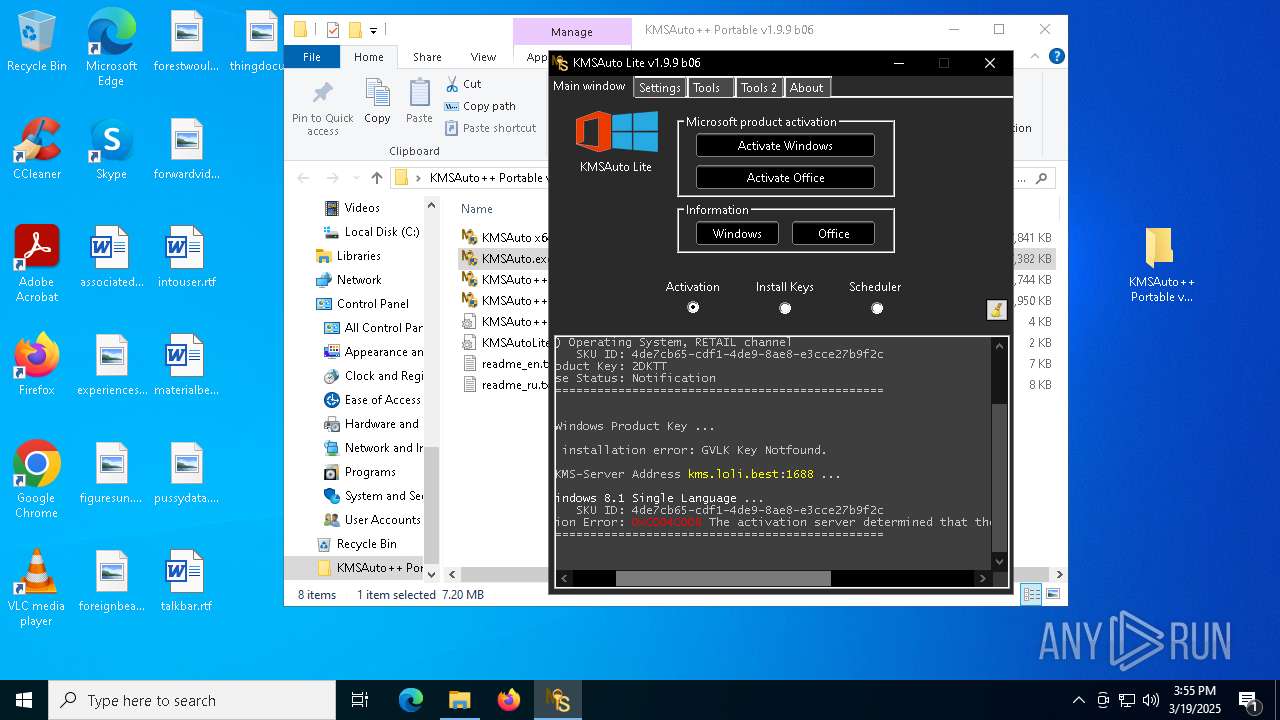
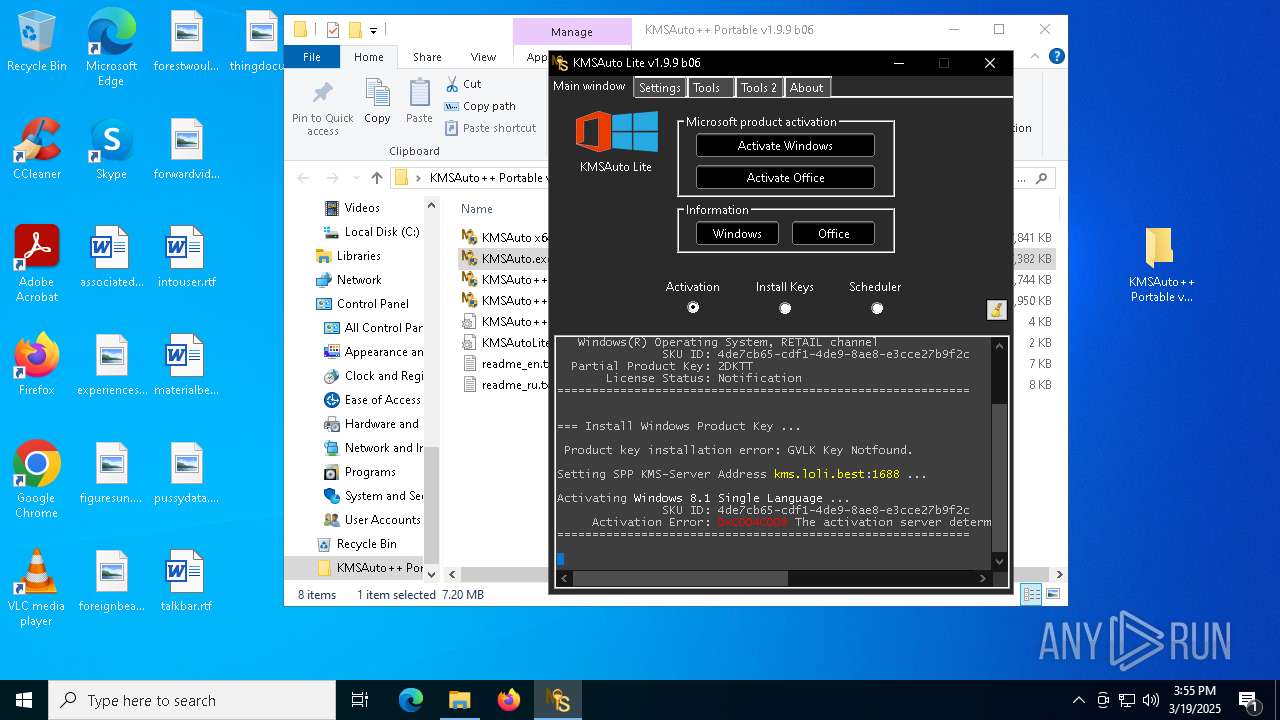
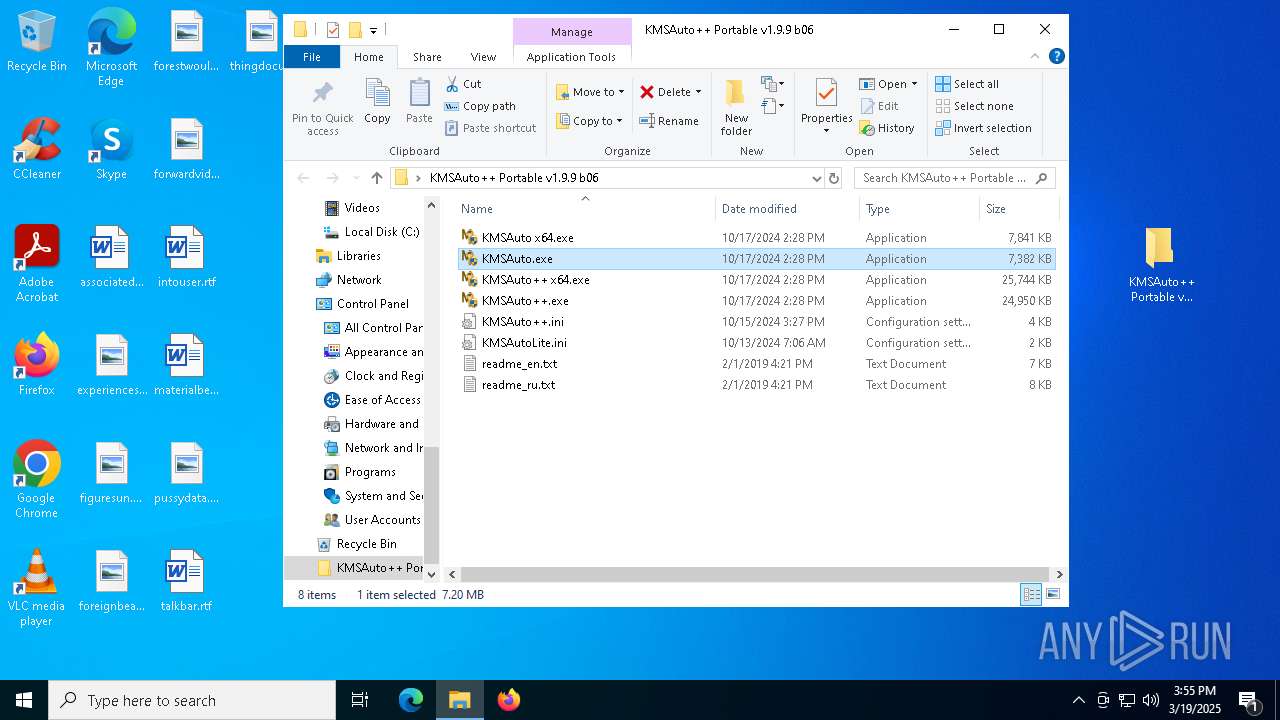
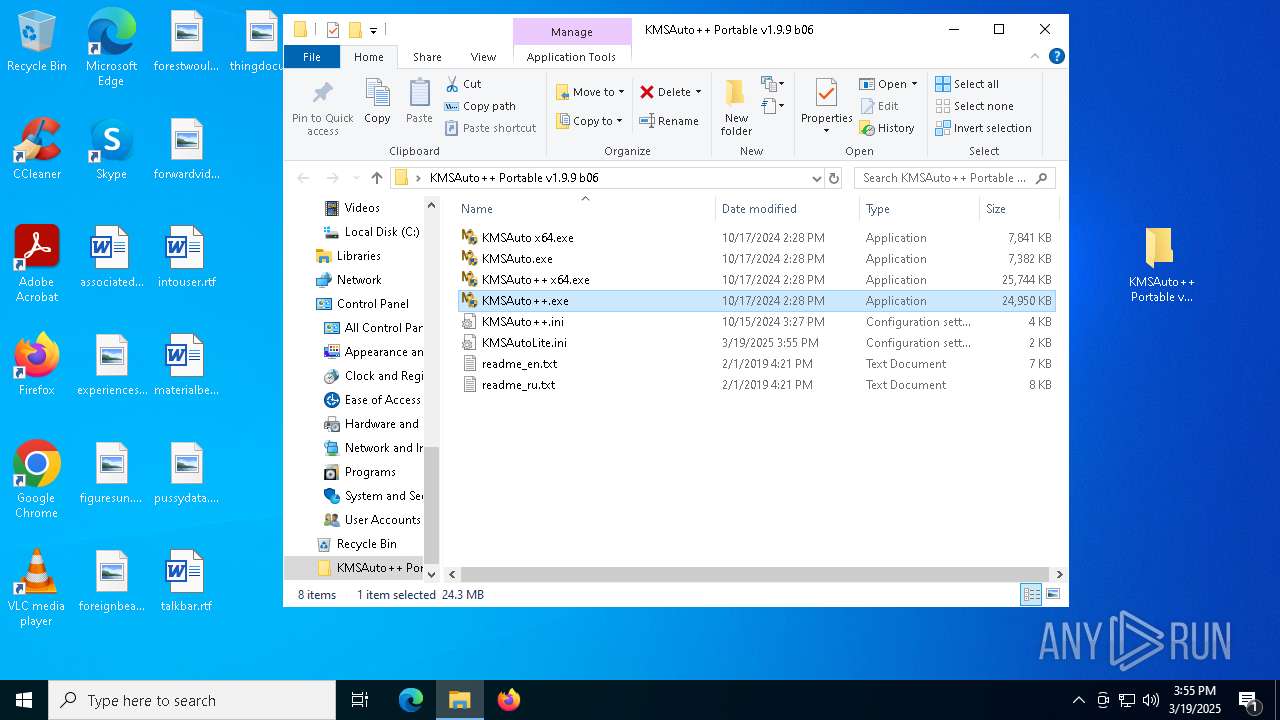
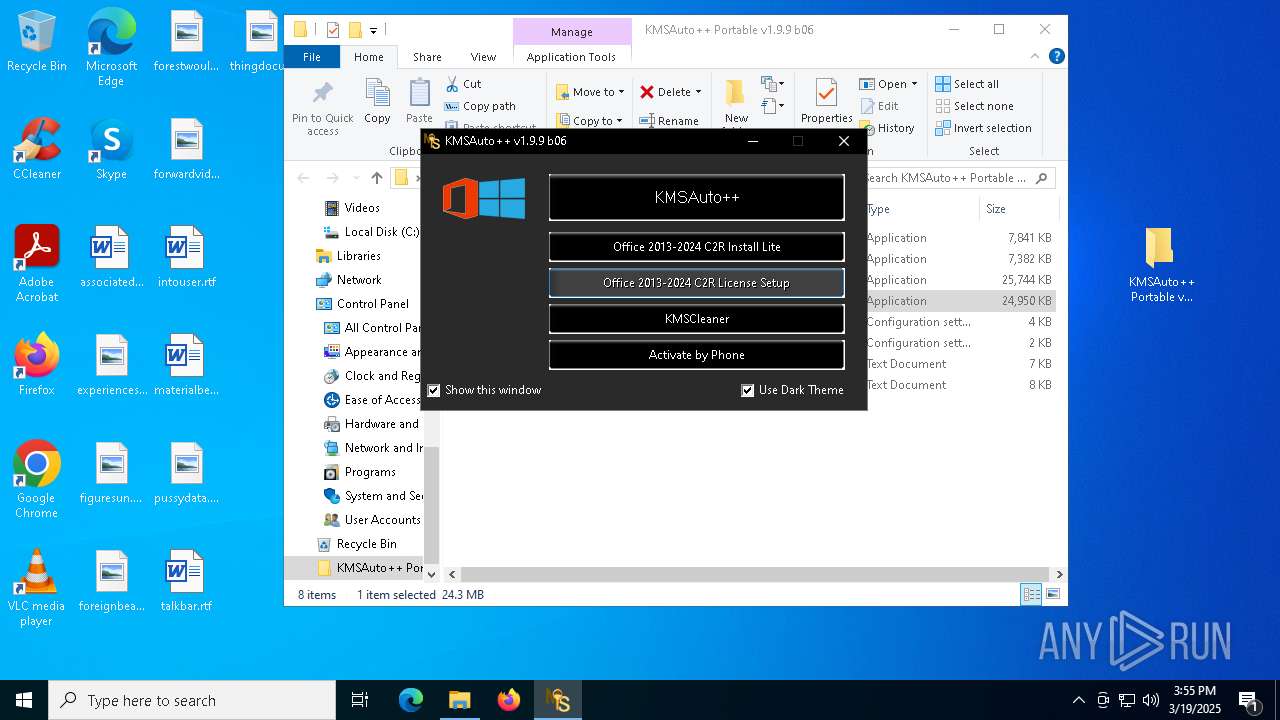
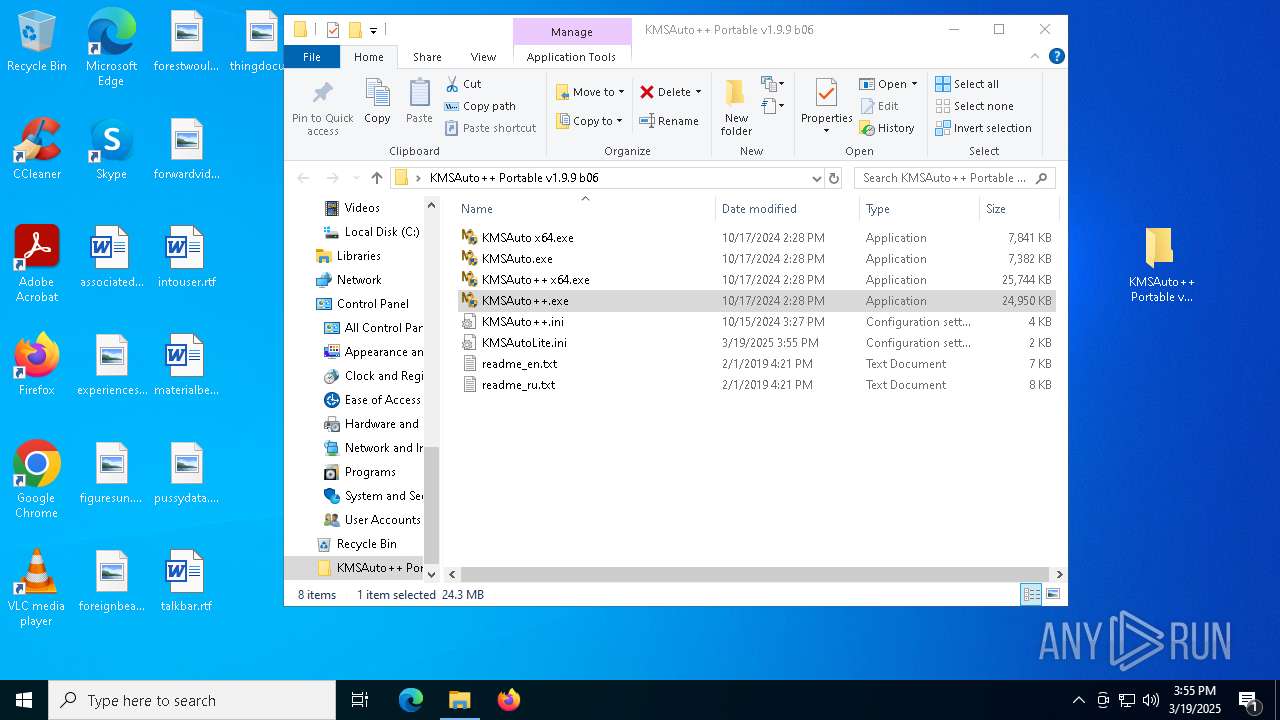
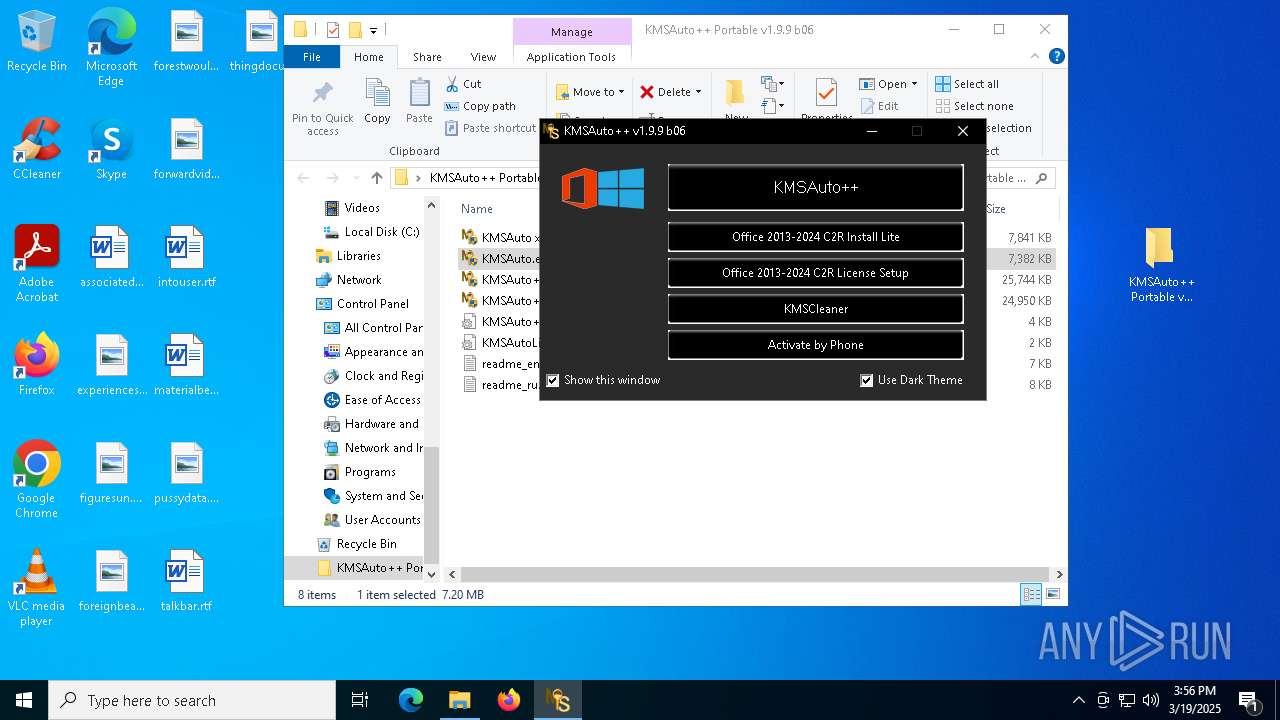
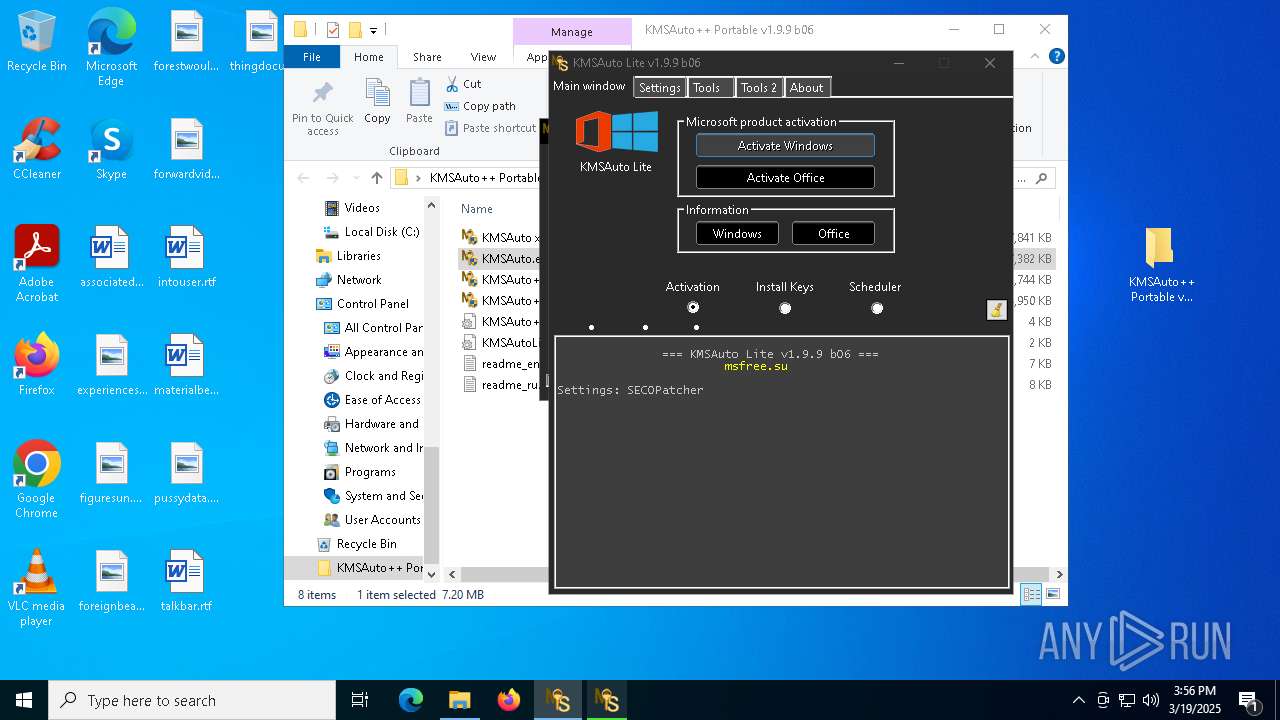
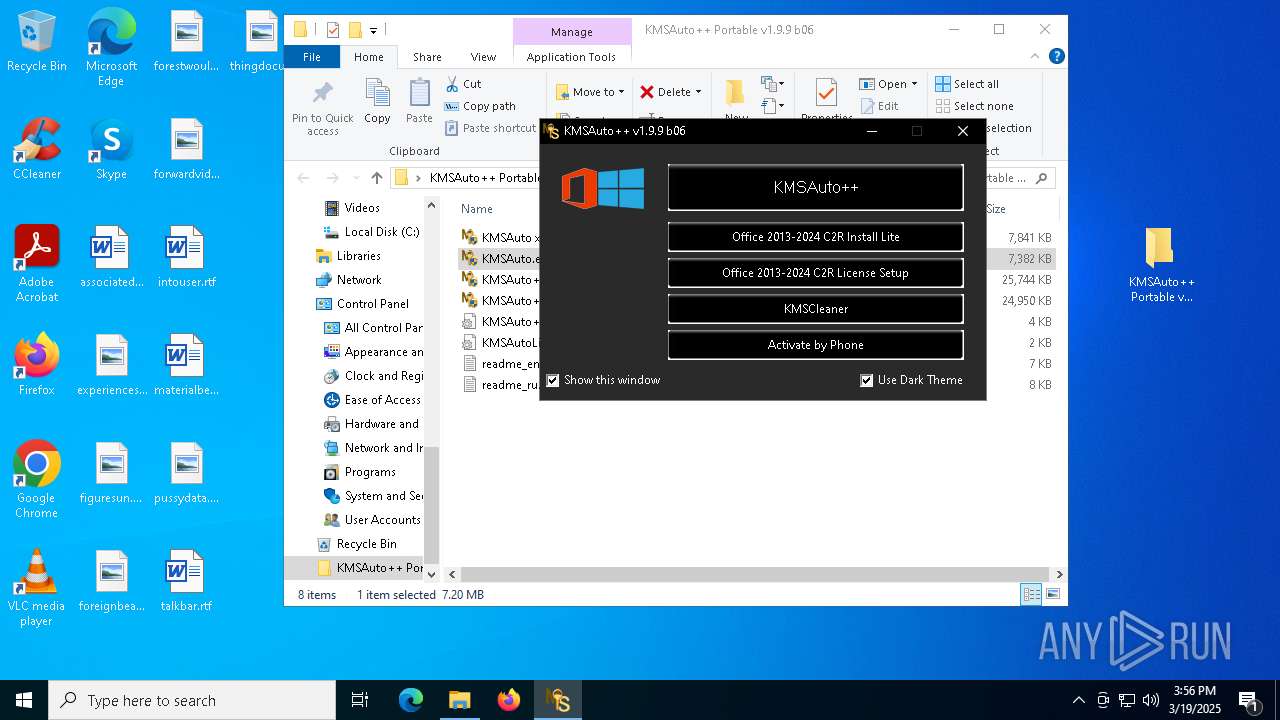
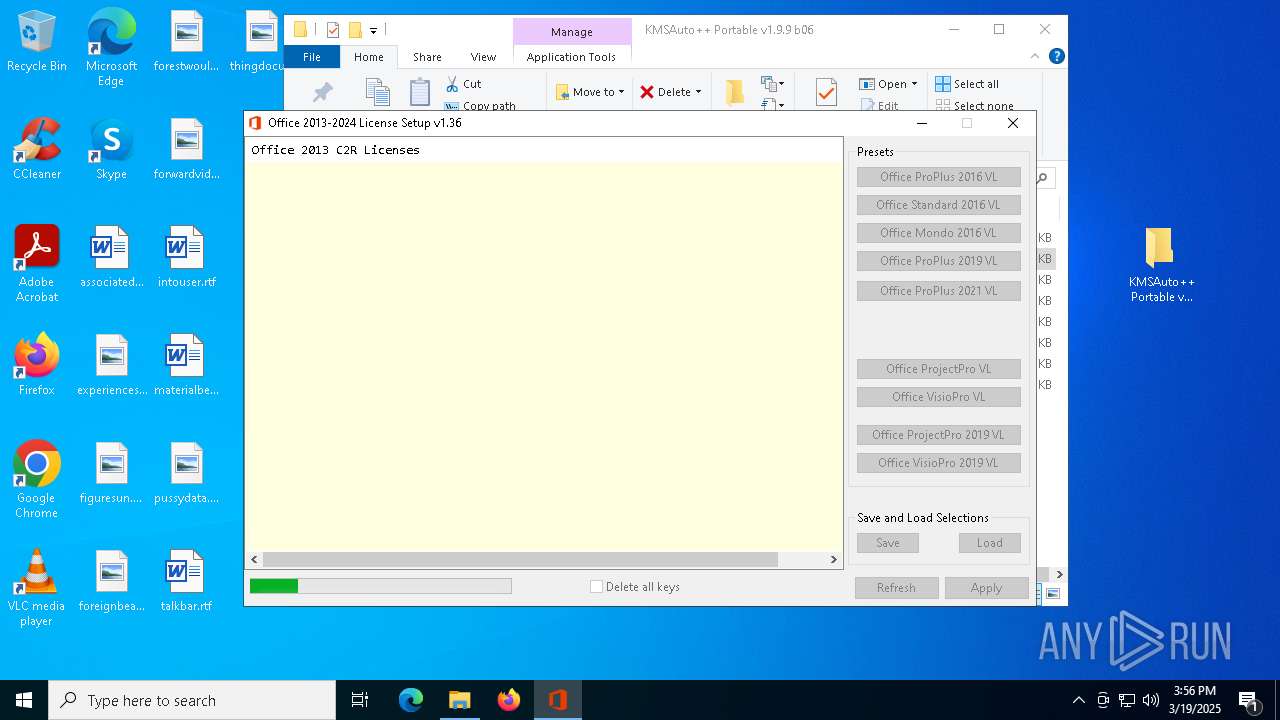
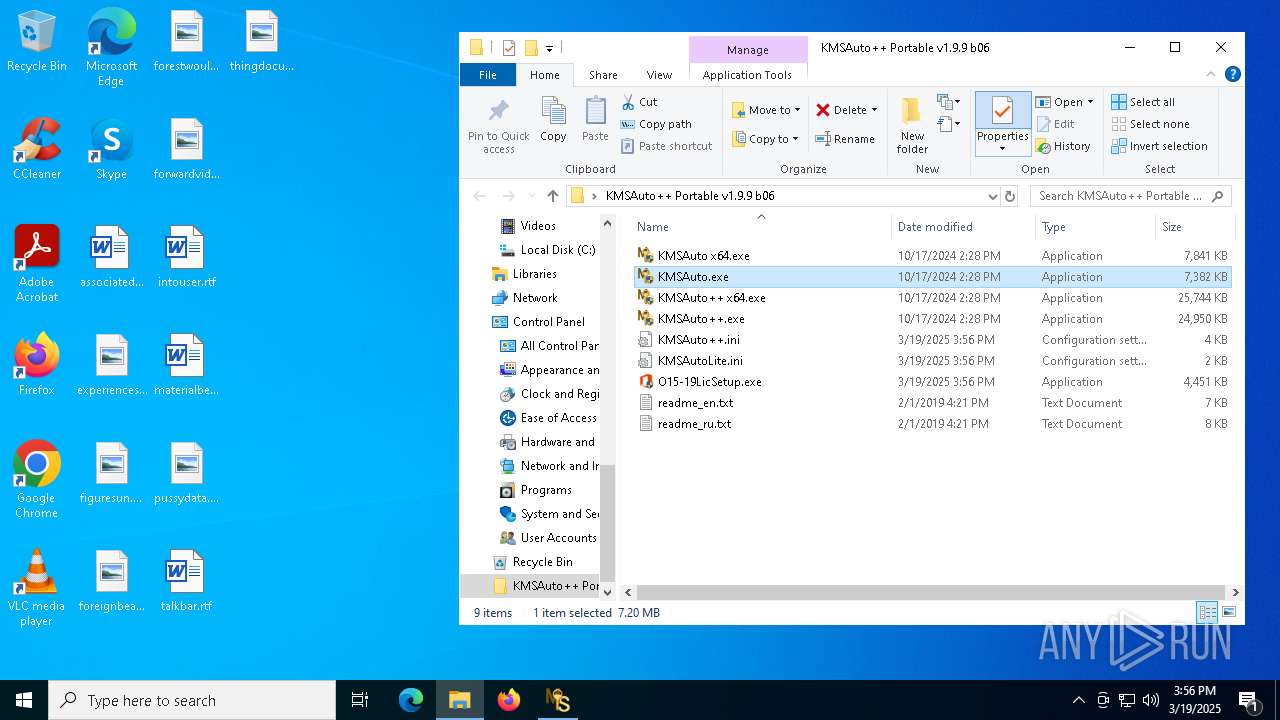
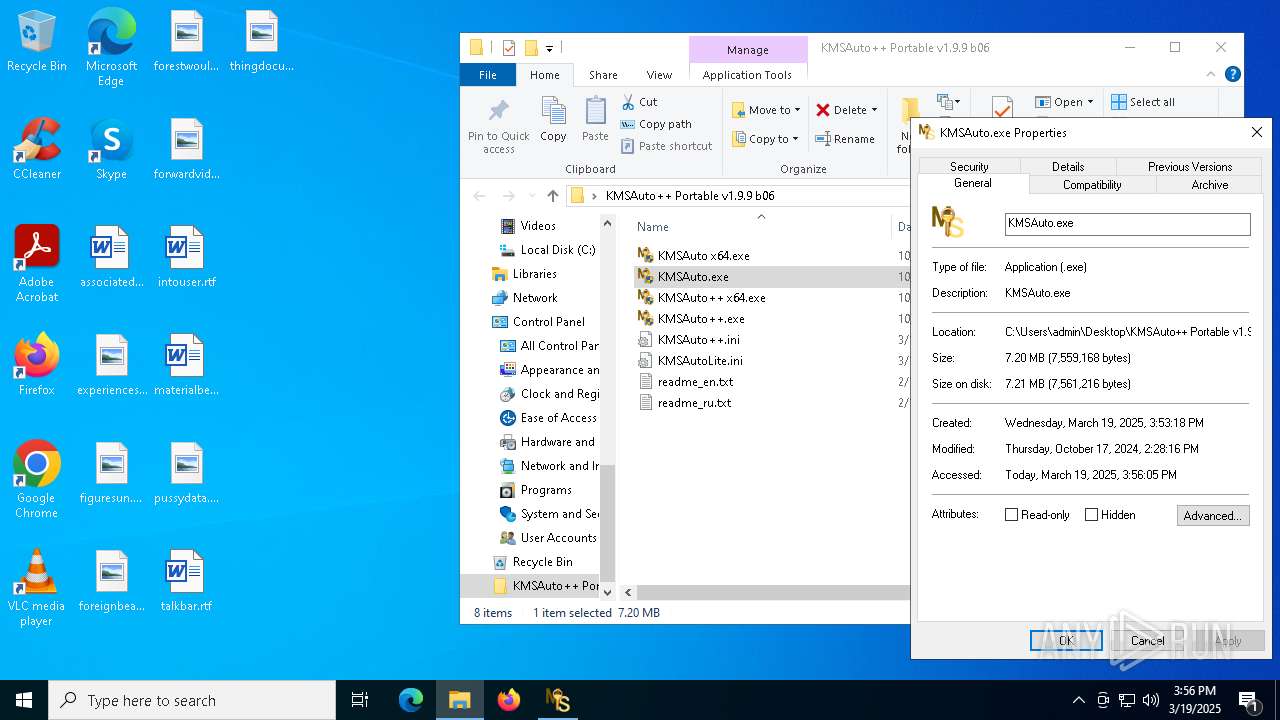
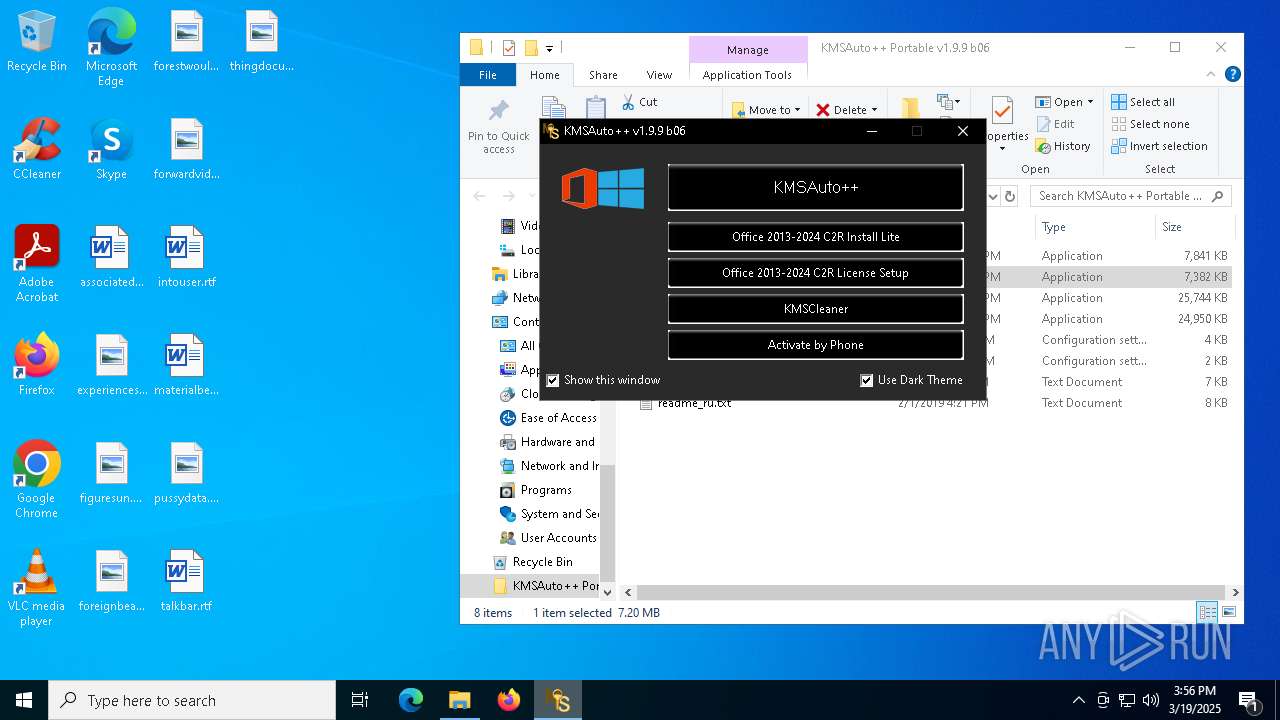
| File name: | KMSAuto++ Portable v1.9.9 b06.7z |
| Full analysis: | https://app.any.run/tasks/9315a6a8-902c-40df-a8f3-918d750a8b9c |
| Verdict: | Malicious activity |
| Analysis date: | March 19, 2025, 15:52:52 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 423EFB73A631241EC0CBA8190AFD7D3E |
| SHA1: | 579FF2365A9499E0C8EEF4FA1EBCD8BA9E228A08 |
| SHA256: | 5DEC7CD4F7ED331AA36D40CC6BEEDD9606F382334CB39CAE6B4E33E87BC81021 |
| SSDEEP: | 98304:7me5cfyoCMtTUwmyMAYVQyLCp3d9JAH9ul/HmZ7s0XWQHVAHTPUsGXz4CJYGzSjr:C8T06rzVdmIuiuD1xLh |
MALICIOUS
Accesses name of the domain to which a computer belongs via WMI (SCRIPT)
- cscript.exe (PID: 7012)
Uses WMIC.EXE to add exclusions to the Windows Defender
- cmd.exe (PID: 6700)
- cmd.exe (PID: 1228)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 6456)
SUSPICIOUS
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7848)
- cmd.exe (PID: 6040)
- cmd.exe (PID: 5956)
- cmd.exe (PID: 5376)
- OInstallLite.exe (PID: 7560)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- cscript.exe (PID: 7680)
- cscript.exe (PID: 5936)
- cscript.exe (PID: 8176)
- cscript.exe (PID: 7012)
Gets full path of the running script (SCRIPT)
- cscript.exe (PID: 7680)
- cscript.exe (PID: 5936)
- cscript.exe (PID: 7012)
- cscript.exe (PID: 8176)
- cscript.exe (PID: 5212)
The process executes VB scripts
- cmd.exe (PID: 1072)
- cmd.exe (PID: 968)
- cmd.exe (PID: 7696)
- cmd.exe (PID: 6068)
- cmd.exe (PID: 6256)
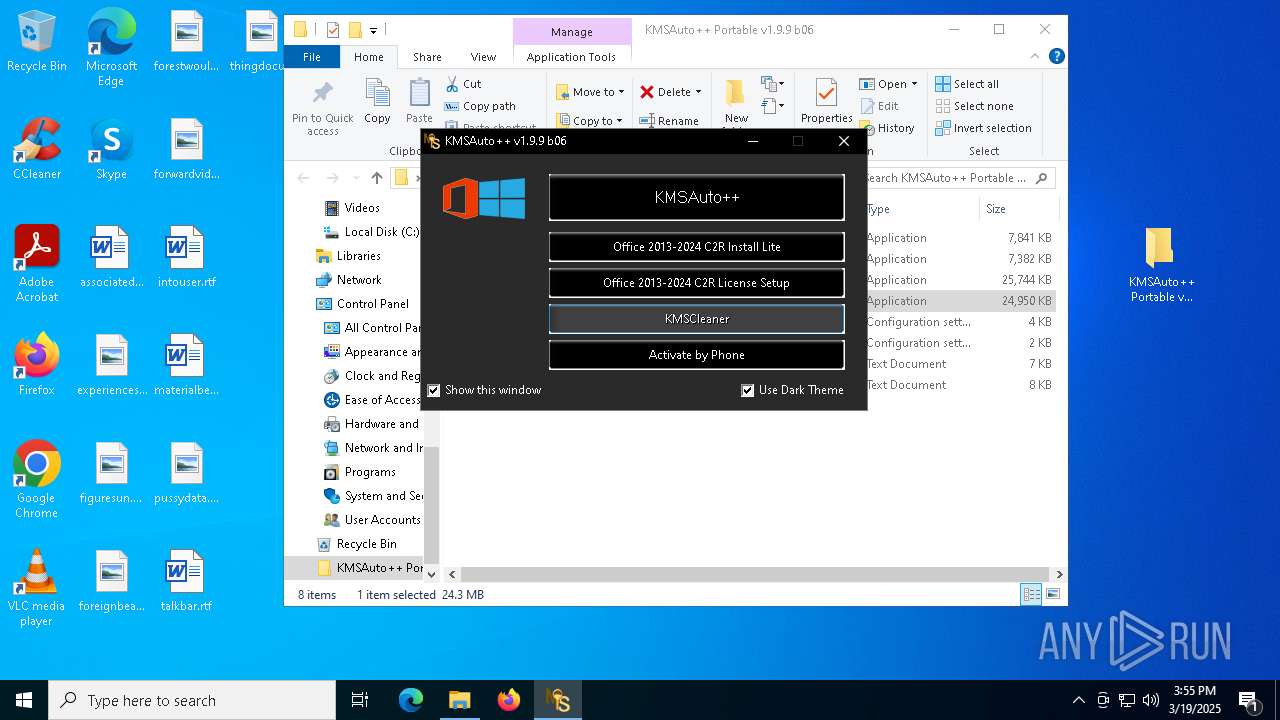
Starts SC.EXE for service management
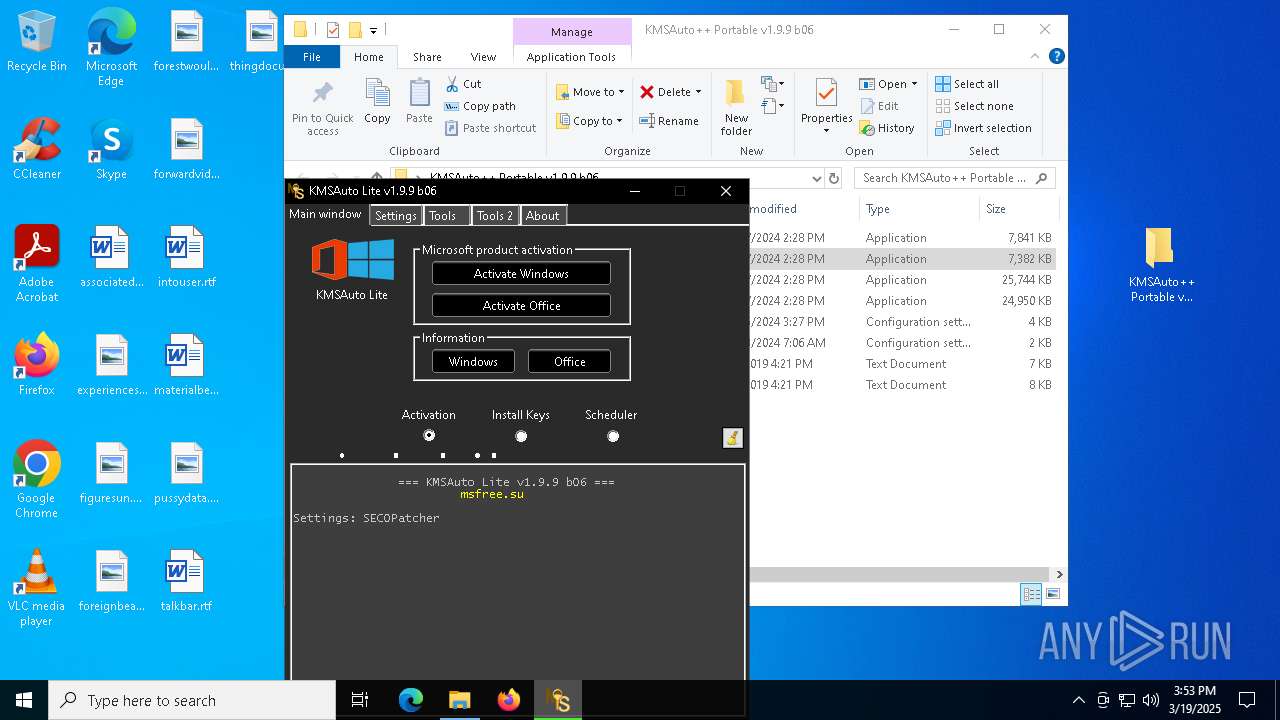
- KMSAuto.exe (PID: 7304)
- KMSAuto++.exe (PID: 5112)
- KMSAuto.exe (PID: 7756)
Windows service management via SC.EXE
- sc.exe (PID: 4040)
- sc.exe (PID: 8176)
- sc.exe (PID: 4108)
- sc.exe (PID: 4380)
- sc.exe (PID: 7576)
- sc.exe (PID: 3828)
- sc.exe (PID: 5364)
- sc.exe (PID: 7960)
Starts CMD.EXE for commands execution
- KMSAuto.exe (PID: 7304)
- KMSAuto++.exe (PID: 5112)
- OInstallLite.exe (PID: 7560)
- KMSAuto.exe (PID: 7756)
- O15-19LicSetup.exe (PID: 5508)
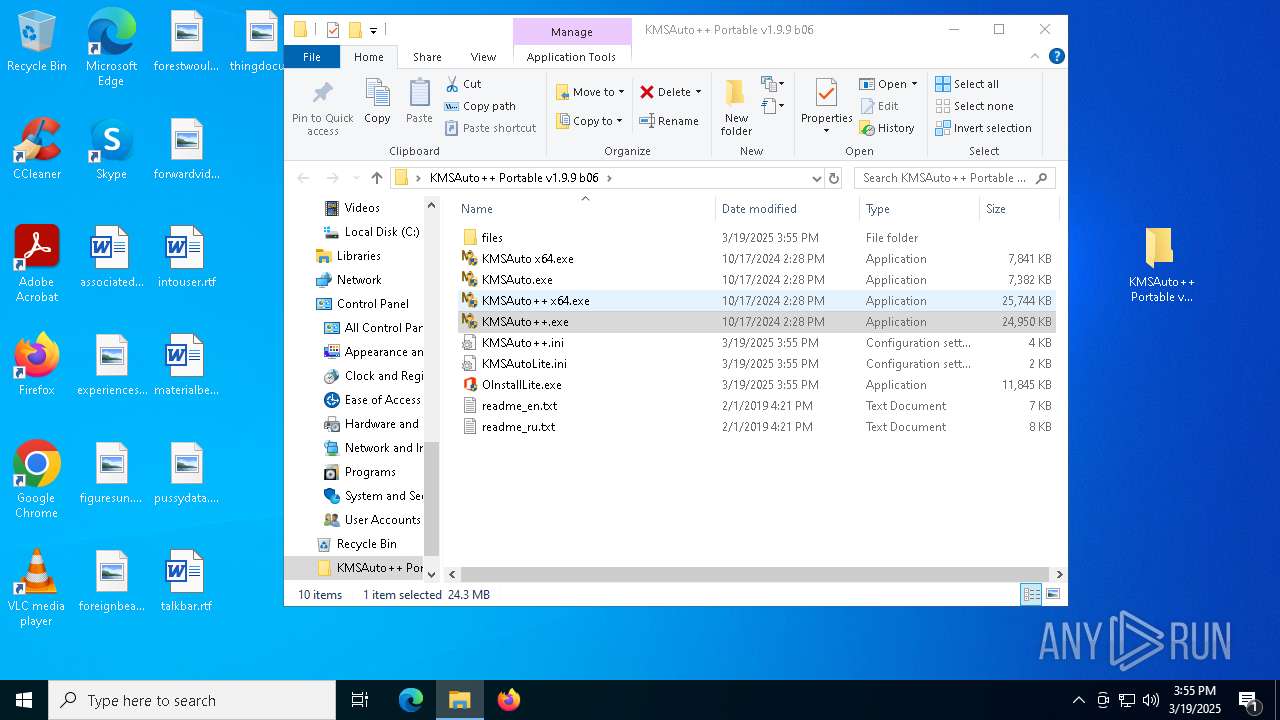
Executable content was dropped or overwritten
- KMSAuto++.exe (PID: 5112)
- OInstallLite.exe (PID: 7560)
- files.dat (PID: 6036)
- O15-19LicSetup.exe (PID: 5508)
- files.dat (PID: 3180)
Found strings related to reading or modifying Windows Defender settings
- OInstallLite.exe (PID: 7560)
Drops 7-zip archiver for unpacking
- OInstallLite.exe (PID: 7560)
- O15-19LicSetup.exe (PID: 5508)
Starts application with an unusual extension
- cmd.exe (PID: 1128)
- cmd.exe (PID: 1116)
- cmd.exe (PID: 5864)
Process drops legitimate windows executable
- files.dat (PID: 6036)
- files.dat (PID: 3180)
The process drops C-runtime libraries
- files.dat (PID: 6036)
- files.dat (PID: 3180)
Probably download files using WebClient
- OInstallLite.exe (PID: 7560)
Starts POWERSHELL.EXE for commands execution
- OInstallLite.exe (PID: 7560)
Executes script without checking the security policy
- powershell.exe (PID: 6456)
The process bypasses the loading of PowerShell profile settings
- OInstallLite.exe (PID: 7560)
Accesses computer name via WMI (SCRIPT)
- cscript.exe (PID: 5212)
Creates FileSystem object to access computer's file system (SCRIPT)
- cscript.exe (PID: 5212)
Gets the drive type (SCRIPT)
- cscript.exe (PID: 5212)
Gets a collection of all available drive names (SCRIPT)
- cscript.exe (PID: 5212)
Accesses WMI object, sets custom ImpersonationLevel (SCRIPT)
- cscript.exe (PID: 5212)
Sets XML DOM element text (SCRIPT)
- cscript.exe (PID: 5212)
INFO
Checks proxy server information
- BackgroundTransferHost.exe (PID: 3180)
- powershell.exe (PID: 6456)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7476)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 7276)
- BackgroundTransferHost.exe (PID: 1180)
- BackgroundTransferHost.exe (PID: 3180)
- BackgroundTransferHost.exe (PID: 8004)
- BackgroundTransferHost.exe (PID: 7868)
- cscript.exe (PID: 7680)
- cscript.exe (PID: 5936)
- WMIC.exe (PID: 4932)
- cscript.exe (PID: 5212)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 3180)
- cscript.exe (PID: 5212)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 3180)
Manual execution by a user
- KMSAuto.exe (PID: 4200)
- KMSAuto.exe (PID: 7304)
- KMSAuto++.exe (PID: 5048)
- KMSAuto++.exe (PID: 5112)
- KMSAuto.exe (PID: 7756)
- KMSAuto.exe (PID: 7268)
Checks supported languages
- KMSAuto.exe (PID: 7304)
- OInstallLite.exe (PID: 7560)
- KMSAuto.exe (PID: 7756)
Reads Environment values
- KMSAuto.exe (PID: 7304)
- KMSAuto++.exe (PID: 5112)
Reads product name
- KMSAuto.exe (PID: 7304)
- KMSAuto++.exe (PID: 5112)
Reads the computer name
- KMSAuto.exe (PID: 7304)
- KMSAuto++.exe (PID: 5112)
- O15-19LicSetup.exe (PID: 5508)
Create files in a temporary directory
- KMSAuto.exe (PID: 7304)
- KMSAuto.exe (PID: 7756)
- files.dat (PID: 3180)
- files.dat (PID: 6980)
- O15-19LicSetup.exe (PID: 5508)
Reads Microsoft Office registry keys
- OInstallLite.exe (PID: 7560)
The sample compiled with english language support
- OInstallLite.exe (PID: 7560)
- files.dat (PID: 6036)
- O15-19LicSetup.exe (PID: 5508)
- files.dat (PID: 3180)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|
Total processes
258
Monitored processes
110
Malicious processes
7
Suspicious processes
11
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | "C:\WINDOWS\Sysnative\reg.exe" query "HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Defender" /v DisableAntiSpyware | C:\Windows\System32\reg.exe | — | KMSAuto.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 232 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 616 | "C:\WINDOWS\Sysnative\reg.exe" add "HKLM\SOFTWARE\Microsoft\Windows Script Host\Settings" /v Enabled /t REG_DWORD /d 1 /f | C:\Windows\System32\reg.exe | — | OInstallLite.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 736 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 864 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 920 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 968 | "C:\WINDOWS\Sysnative\cmd.exe" /c cscript //nologo "C:\Users\admin\AppData\Local\Temp\slmgr.vbs" /dlv | C:\Windows\System32\cmd.exe | — | KMSAuto.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 976 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1012 | "C:\WINDOWS\Sysnative\reg.exe" query "HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender" /v DisableAntiSpyware | C:\Windows\System32\reg.exe | — | KMSAuto.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1072 | "C:\WINDOWS\Sysnative\cmd.exe" /c cscript //nologo "C:\Users\admin\AppData\Local\Temp\slmgr.vbs" /dlv all | C:\Windows\System32\cmd.exe | — | KMSAuto.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
17 265
Read events
17 207
Write events
58
Delete events
0
Modification events
| (PID) Process: | (7476) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (7476) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7476) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7476) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7476) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\KMSAuto++ Portable v1.9.9 b06.7z | |||
| (PID) Process: | (7476) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7476) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7476) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7476) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7276) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
18
Suspicious files
10
Text files
2 380
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3180 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\23dc5a3b-1ac4-41ce-a091-bdb327c339d8.down_data | — | |
MD5:— | SHA256:— | |||
| 5112 | KMSAuto++.exe | C:\Users\admin\Desktop\KMSAuto++ Portable v1.9.9 b06\OInstallLite.exe | executable | |
MD5:96EAD49880812C394EAF658EA2362070 | SHA256:8869707B8F91F32261B208F6F07FC8D2E0C790EBB3657C092F0F623DB6D989B6 | |||
| 3180 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\12264c31-5e7a-40ca-9e9b-69eb6361fa6d.up_meta_secure | binary | |
MD5:EE9E42226DB119A21F3912BCB3C82BA9 | SHA256:DDF1C2486FFEE21B9368E18AA7F68ED69D3B890DFF51872747C96CCC971DA7F9 | |||
| 3180 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:159D0E367104B2A46B5B22572DB377FB | SHA256:DD50D2816D2D72E950EFFEE5876F952C133A068AB081A7D4D502948EFB2E5330 | |||
| 6036 | files.dat | C:\Users\admin\Desktop\KMSAuto++ Portable v1.9.9 b06\files\x64\msvcr100.dll | executable | |
MD5:DF3CA8D16BDED6A54977B30E66864D33 | SHA256:1D1A1AE540BA132F998D60D3622F0297B6E86AE399332C3B47462D7C0F560A36 | |||
| 3180 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\12264c31-5e7a-40ca-9e9b-69eb6361fa6d.395b237c-057b-4a8d-9beb-a97430f20948.down_meta | binary | |
MD5:66ECDB5C6748DF31F401CF621AB71B04 | SHA256:685CA9031B760F36D82A849E2A369DB72603B124686163DFFB6D3483883BEDE8 | |||
| 3180 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\23dc5a3b-1ac4-41ce-a091-bdb327c339d8.395b237c-057b-4a8d-9beb-a97430f20948.down_meta | binary | |
MD5:66ECDB5C6748DF31F401CF621AB71B04 | SHA256:685CA9031B760F36D82A849E2A369DB72603B124686163DFFB6D3483883BEDE8 | |||
| 3180 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:C8AF25AA60A073D8DCEA106CD46D1073 | SHA256:ECE1E0D365A6A4F49DD6700870A17DC3225812E0260FECB63169CC23F7960612 | |||
| 7476 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb7476.40384\KMSAuto++ Portable v1.9.9 b06\readme_en.txt | text | |
MD5:7A4FB804AF171AD041C65E3E46FD00B2 | SHA256:C7A2D7FA7DCF9A08A5179720F81B947221F0E94BC797878352ECAE52D923C939 | |||
| 7476 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb7476.40384\KMSAuto++ Portable v1.9.9 b06\KMSAuto++.exe | executable | |
MD5:324C898621297AF29E77076909BF52F9 | SHA256:6785EC0D7D578777E46016DDB03894B344E30A5025F4A1B9E7A4642CBA14131F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
28
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7616 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7900 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7900 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3180 | BackgroundTransferHost.exe | GET | 200 | 23.54.109.203:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5212 | cscript.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicCodSigPCA_2010-07-06.crl | unknown | — | — | whitelisted |
5212 | cscript.exe | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
3216 | svchost.exe | 20.197.71.89:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | SG | whitelisted |
6544 | svchost.exe | 20.190.159.71:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7616 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7616 | backgroundTaskHost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3180 | BackgroundTransferHost.exe | 104.126.37.171:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |