| File name: | STR.BYPASS.exe |
| Full analysis: | https://app.any.run/tasks/b1ece310-4976-4858-99cf-105b18c08ce2 |
| Verdict: | Malicious activity |
| Analysis date: | June 19, 2025, 15:10:02 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 6 sections |
| MD5: | 9900848B9A79D1FBBD029C1011B61497 |
| SHA1: | B8CF6312D1864C8C616F92B464BAB5C80172CCE0 |
| SHA256: | 5DD5D7D7982CCCB1A7FF2B1BE04C5B414F60791AAD8EF2D8F849EC498CBF82D2 |
| SSDEEP: | 98304:i1svXJG6gIS6AMG6PY3nOV2oQcONGxYODZ0ZZnEIfWwd+PmSu6Zlyk2gxfNqoGE+:ruRyBDDSR3qyCFMyXK |
MALICIOUS
Changes the autorun value in the registry
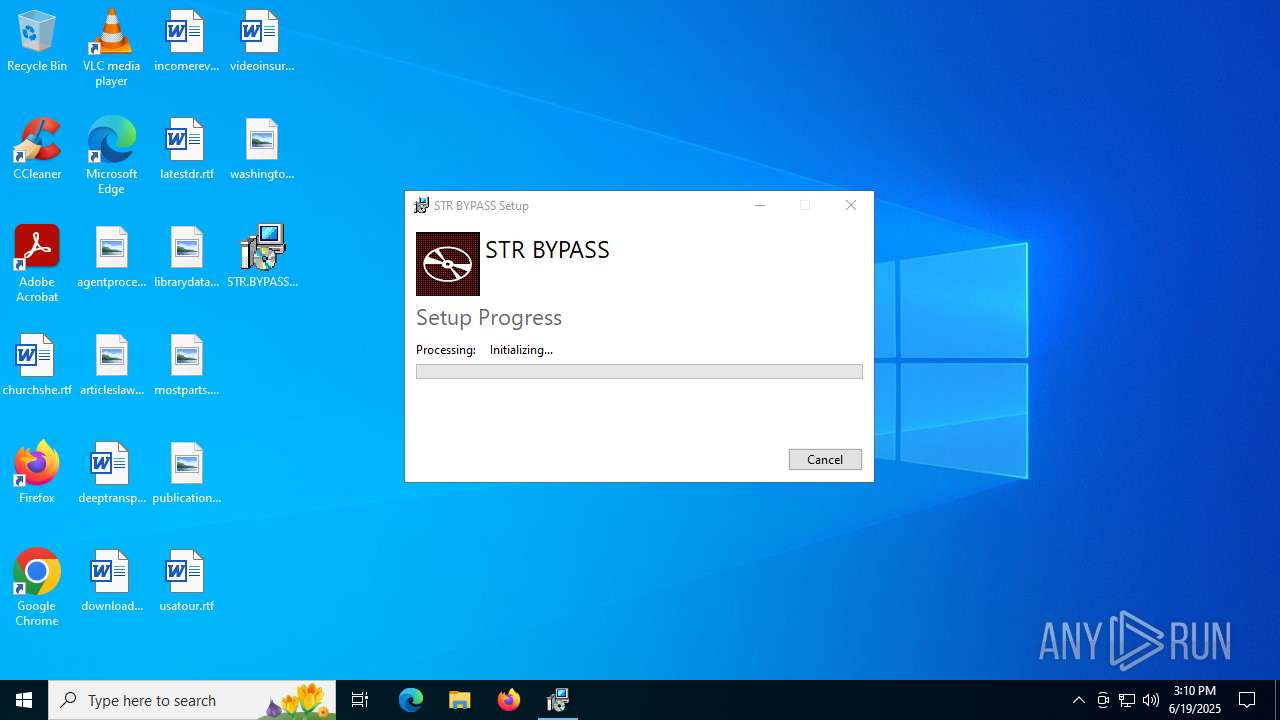
- strbypass-setup-1.0.2.exe (PID: 1480)
SUSPICIOUS
Executable content was dropped or overwritten
- STR.BYPASS.exe (PID: 3540)
- STR.BYPASS.exe (PID: 1520)
- strbypass-setup-1.0.2.exe (PID: 1480)
- strbypass-setup-1.0.2.exe (PID: 5764)
Searches for installed software
- STR.BYPASS.exe (PID: 1520)
- dllhost.exe (PID: 3888)
- strbypass-setup-1.0.2.exe (PID: 6264)
- strbypass-setup-1.0.2.exe (PID: 5764)
Starts itself from another location
- STR.BYPASS.exe (PID: 3540)
- STR.BYPASS.exe (PID: 1520)
Reads security settings of Internet Explorer
- STR.BYPASS.exe (PID: 1520)
- strbypass.exe (PID: 2428)
- strbypass.exe (PID: 2764)
Executes as Windows Service
- VSSVC.exe (PID: 5232)
- strbypass.exe (PID: 6796)
Creates a software uninstall entry
- strbypass-setup-1.0.2.exe (PID: 1480)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 620)
Application launched itself
- msiexec.exe (PID: 620)
- strbypass.exe (PID: 2428)
- strbypass.exe (PID: 6796)
- strbypass-setup-1.0.2.exe (PID: 6264)
- strbypass-setup-1.0.2.exe (PID: 4752)
Reads the date of Windows installation
- strbypass.exe (PID: 2428)
There is functionality for taking screenshot (YARA)
- strbypass.exe (PID: 6796)
INFO
Checks supported languages
- STR.BYPASS.exe (PID: 3540)
- STR.BYPASS.exe (PID: 1520)
- strbypass-setup-1.0.2.exe (PID: 1480)
- msiexec.exe (PID: 620)
- msiexec.exe (PID: 4868)
- msiexec.exe (PID: 3608)
- strbypass.exe (PID: 2428)
- strbypass.exe (PID: 2596)
- strbypass.exe (PID: 6796)
- strbypass.exe (PID: 2764)
- strbypass-setup-1.0.2.exe (PID: 4752)
- strbypass-setup-1.0.2.exe (PID: 5764)
- strbypass-setup-1.0.2.exe (PID: 6264)
The sample compiled with english language support
- STR.BYPASS.exe (PID: 3540)
- STR.BYPASS.exe (PID: 1520)
- strbypass-setup-1.0.2.exe (PID: 1480)
- msiexec.exe (PID: 620)
- strbypass-setup-1.0.2.exe (PID: 5764)
Create files in a temporary directory
- STR.BYPASS.exe (PID: 3540)
- STR.BYPASS.exe (PID: 1520)
- strbypass-setup-1.0.2.exe (PID: 1480)
- strbypass-setup-1.0.2.exe (PID: 5764)
Process checks computer location settings
- STR.BYPASS.exe (PID: 1520)
- strbypass.exe (PID: 2428)
Reads the computer name
- STR.BYPASS.exe (PID: 1520)
- strbypass-setup-1.0.2.exe (PID: 1480)
- msiexec.exe (PID: 620)
- msiexec.exe (PID: 4868)
- msiexec.exe (PID: 3608)
- strbypass.exe (PID: 2428)
- strbypass.exe (PID: 6796)
- strbypass.exe (PID: 2596)
- strbypass.exe (PID: 2764)
- strbypass-setup-1.0.2.exe (PID: 5764)
Manages system restore points
- SrTasks.exe (PID: 2356)
Creates files in the program directory
- strbypass-setup-1.0.2.exe (PID: 1480)
Launching a file from a Registry key
- strbypass-setup-1.0.2.exe (PID: 1480)
The sample compiled with chinese language support
- strbypass-setup-1.0.2.exe (PID: 1480)
- STR.BYPASS.exe (PID: 1520)
- msiexec.exe (PID: 620)
Reads the machine GUID from the registry
- strbypass-setup-1.0.2.exe (PID: 1480)
Executable content was dropped or overwritten
- msiexec.exe (PID: 620)
Creates a software uninstall entry
- msiexec.exe (PID: 620)
Manual execution by a user
- strbypass-setup-1.0.2.exe (PID: 6264)
Detects GO elliptic curve encryption (YARA)
- strbypass.exe (PID: 6796)
Reads the software policy settings
- slui.exe (PID: 5244)
Application based on Golang
- strbypass.exe (PID: 6796)
Checks proxy server information
- slui.exe (PID: 5244)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:03:22 22:14:43+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit, Removable run from swap, Net run from swap |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 314368 |
| InitializedDataSize: | 164352 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x302e5 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.2.0 |
| ProductVersionNumber: | 1.0.2.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| CompanyName: | Strugov97 |
| FileDescription: | STR BYPASS |
| FileVersion: | 1.0.2 |
| InternalName: | setup |
| LegalCopyright: | Copyright (c) Strugov97. All rights reserved. |
| OriginalFileName: | strbypass-setup-1.0.2.exe |
| ProductName: | STR BYPASS |
| ProductVersion: | 1.0.2 |
Total processes
156
Monitored processes
18
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 620 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1480 | "C:\Users\admin\AppData\Local\Temp\{9B2CCCB1-B621-4F71-A085-B942AABD3DD1}\.be\strbypass-setup-1.0.2.exe" -q -burn.elevated BurnPipe.{A41E3236-141B-4FE6-B0BD-36710652816E} {4CF379FD-3914-43B7-8E61-6C5BF39C954A} 1520 | C:\Users\admin\AppData\Local\Temp\{9B2CCCB1-B621-4F71-A085-B942AABD3DD1}\.be\strbypass-setup-1.0.2.exe | STR.BYPASS.exe | ||||||||||||
User: admin Company: Strugov97 Integrity Level: HIGH Description: STR BYPASS Exit code: 0 Version: 1.0.2 Modules
| |||||||||||||||
| 1520 | "C:\Users\admin\AppData\Local\Temp\{6269F4B1-15C5-4972-B5A9-81E0AADA3E54}\.cr\STR.BYPASS.exe" -burn.clean.room="C:\Users\admin\Desktop\STR.BYPASS.exe" -burn.filehandle.attached=696 -burn.filehandle.self=704 | C:\Users\admin\AppData\Local\Temp\{6269F4B1-15C5-4972-B5A9-81E0AADA3E54}\.cr\STR.BYPASS.exe | STR.BYPASS.exe | ||||||||||||
User: admin Company: Strugov97 Integrity Level: MEDIUM Description: STR BYPASS Exit code: 0 Version: 1.0.2 Modules
| |||||||||||||||
| 2356 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
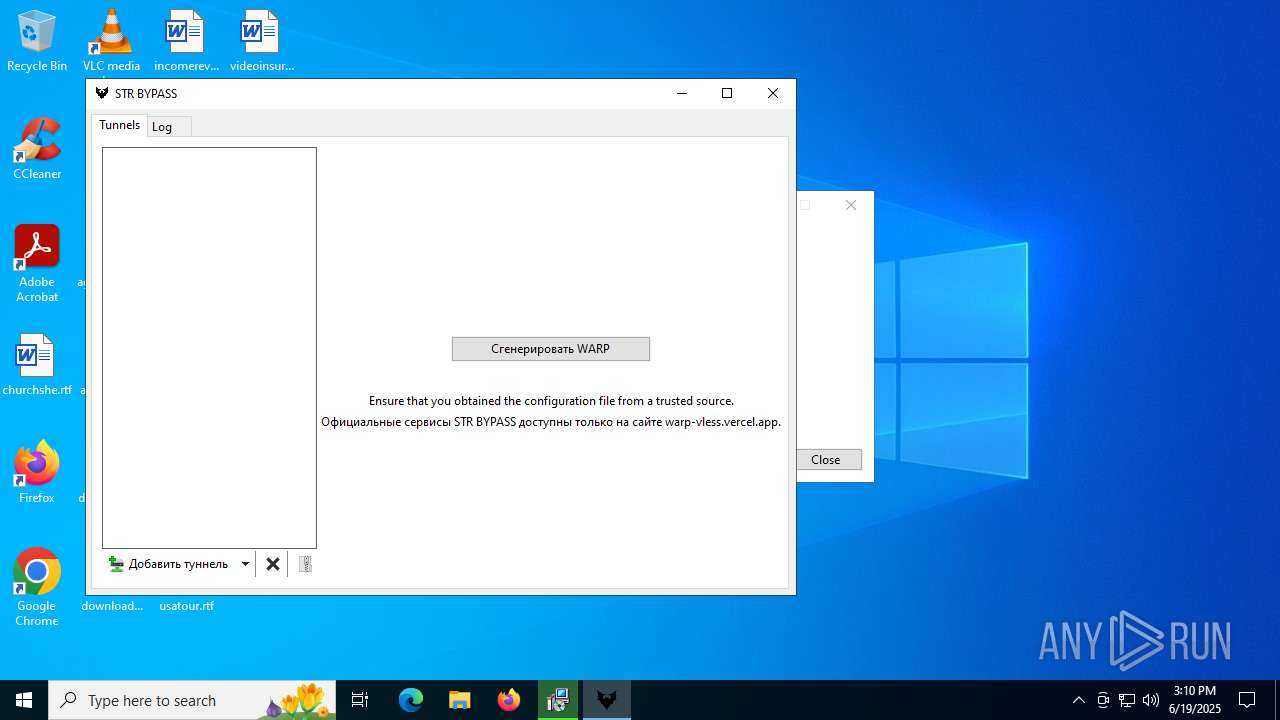
| 2428 | "C:\Program Files\STR BYPASS\strbypass.exe" | C:\Program Files\STR BYPASS\strbypass.exe | — | msiexec.exe | |||||||||||
User: admin Company: Amnezia Integrity Level: HIGH Description: STR BYPASS Exit code: 0 Version: 1.0.2 Modules
| |||||||||||||||
| 2596 | "C:\Program Files\STR BYPASS\strbypass.exe" /installmanagerservice | C:\Program Files\STR BYPASS\strbypass.exe | strbypass.exe | ||||||||||||
User: SYSTEM Company: Amnezia Integrity Level: SYSTEM Description: STR BYPASS Exit code: 0 Version: 1.0.2 Modules
| |||||||||||||||
| 2764 | "C:\Program Files\STR BYPASS\strbypass.exe" /ui 840 836 848 856 | C:\Program Files\STR BYPASS\strbypass.exe | — | strbypass.exe | |||||||||||
User: admin Company: Amnezia Integrity Level: HIGH Description: STR BYPASS Version: 1.0.2 Modules
| |||||||||||||||
| 3540 | "C:\Users\admin\Desktop\STR.BYPASS.exe" | C:\Users\admin\Desktop\STR.BYPASS.exe | explorer.exe | ||||||||||||
User: admin Company: Strugov97 Integrity Level: MEDIUM Description: STR BYPASS Exit code: 0 Version: 1.0.2 Modules
| |||||||||||||||
| 3576 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3608 | C:\Windows\System32\MsiExec.exe -Embedding 16BB6E93093BDB667A1F126C8E0D4D8A E Global\MSI0000 | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
17 359
Read events
16 672
Write events
644
Delete events
43
Modification events
| (PID) Process: | (3888) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 48000000000000009EAEAC452CE1DB01300F0000AC0E0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1480) strbypass-setup-1.0.2.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 40000000000000009EAEAC452CE1DB01C8050000C80A0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3888) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 4800000000000000392FD5452CE1DB01300F0000AC0E0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3888) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000392FD5452CE1DB01300F0000AC0E0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3888) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000392FD5452CE1DB01300F0000AC0E0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3888) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000F4C1DE452CE1DB01300F0000AC0E0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3888) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (3888) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 480000000000000077C21C462CE1DB01300F0000AC0E0000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3888) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000078C21462CE1DB01300F0000F8140000E8030000010000000000000000000000B9E683E52A85D5418F4785990E700C7400000000000000000000000000000000 | |||
| (PID) Process: | (5232) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000EECF2F462CE1DB017014000058030000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
19
Suspicious files
14
Text files
13
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3888 | dllhost.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3540 | STR.BYPASS.exe | C:\Users\admin\AppData\Local\Temp\{6269F4B1-15C5-4972-B5A9-81E0AADA3E54}\.cr\STR.BYPASS.exe | executable | |
MD5:D47F798CAB3CB744F959FC3FF7E8C3A2 | SHA256:BDDE9890FB1F081FADDBA1698729FECCC5F230D2B21FE10F23C8D24F04DAA4FC | |||
| 1520 | STR.BYPASS.exe | C:\Users\admin\AppData\Local\Temp\{9B2CCCB1-B621-4F71-A085-B942AABD3DD1}\.ba\thm.wxl | xml | |
MD5:FC0DB4142556D3F38B0744A12F5F9D3D | SHA256:8FBEB7F0B546D394D99B49D678D516402E8F54E5DEA590CC91733F502F288019 | |||
| 1520 | STR.BYPASS.exe | C:\Users\admin\AppData\Local\Temp\{9B2CCCB1-B621-4F71-A085-B942AABD3DD1}\.ba\wixstdba.dll | executable | |
MD5:87C8A7EA44E8EE0D9358E25B7DCD397D | SHA256:B7DE0A0CA3A94738747ABD708E30BA1F9638A8C8B7D8173C76D4F39FAE3D9346 | |||
| 1520 | STR.BYPASS.exe | C:\Users\admin\AppData\Local\Temp\{9B2CCCB1-B621-4F71-A085-B942AABD3DD1}\.ba\thm.xml | xml | |
MD5:C29A69F34FF31FF63C3EC6B2D4F903E5 | SHA256:8D67851408A62B0F04DBAADDC588CD98499CF3630EC5DF9F7C0699F0D367F79C | |||
| 1480 | strbypass-setup-1.0.2.exe | C:\ProgramData\Package Cache\.unverified\strbypass_amd64_1.0.2.msi | executable | |
MD5:74E48C508E200F0F1776E5F697ED6928 | SHA256:0593BA87FBC82496A7267BF7598F2FC7F9E87EBFCA104327322C96E5D7842AD9 | |||
| 1520 | STR.BYPASS.exe | C:\Users\admin\AppData\Local\Temp\{9B2CCCB1-B621-4F71-A085-B942AABD3DD1}\strbypass_amd64_1.0.2.msi | executable | |
MD5:74E48C508E200F0F1776E5F697ED6928 | SHA256:0593BA87FBC82496A7267BF7598F2FC7F9E87EBFCA104327322C96E5D7842AD9 | |||
| 3888 | dllhost.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:21A7D1116E5DB8DA5454B0312EB3A0A9 | SHA256:5AF2C53813B366C1B4307DD3113F73926C272D628E98CD6A064ADF3F43C05C6D | |||
| 3888 | dllhost.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{e583e6b9-852a-41d5-8f47-85990e700c74}_OnDiskSnapshotProp | binary | |
MD5:21A7D1116E5DB8DA5454B0312EB3A0A9 | SHA256:5AF2C53813B366C1B4307DD3113F73926C272D628E98CD6A064ADF3F43C05C6D | |||
| 1480 | strbypass-setup-1.0.2.exe | C:\ProgramData\Package Cache\{B028CCDB-4A87-4BE9-A729-D25FDE658D33}v1.0.2\strbypass-amd64-1.0.2.msi | executable | |
MD5:74E48C508E200F0F1776E5F697ED6928 | SHA256:0593BA87FBC82496A7267BF7598F2FC7F9E87EBFCA104327322C96E5D7842AD9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
47
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 200 | 20.190.159.23:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
— | — | POST | 200 | 20.190.159.129:443 | https://login.live.com/RST2.srf | unknown | xml | 11.0 Kb | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.159.23:443 | https://login.live.com/RST2.srf | unknown | xml | 10.3 Kb | whitelisted |
4868 | RUXIMICS.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4868 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.159.130:443 | https://login.live.com/RST2.srf | unknown | xml | 10.3 Kb | whitelisted |
— | — | POST | 403 | 95.101.149.131:443 | https://go.microsoft.com/fwlink/?LinkID=2257403&clcid=0x409 | unknown | html | 386 b | whitelisted |
— | — | POST | 403 | 95.101.149.131:443 | https://go.microsoft.com/fwlink/?LinkID=2257403&clcid=0x409 | unknown | html | 386 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4868 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2336 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2288 | svchost.exe | 20.190.160.17:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4868 | RUXIMICS.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |