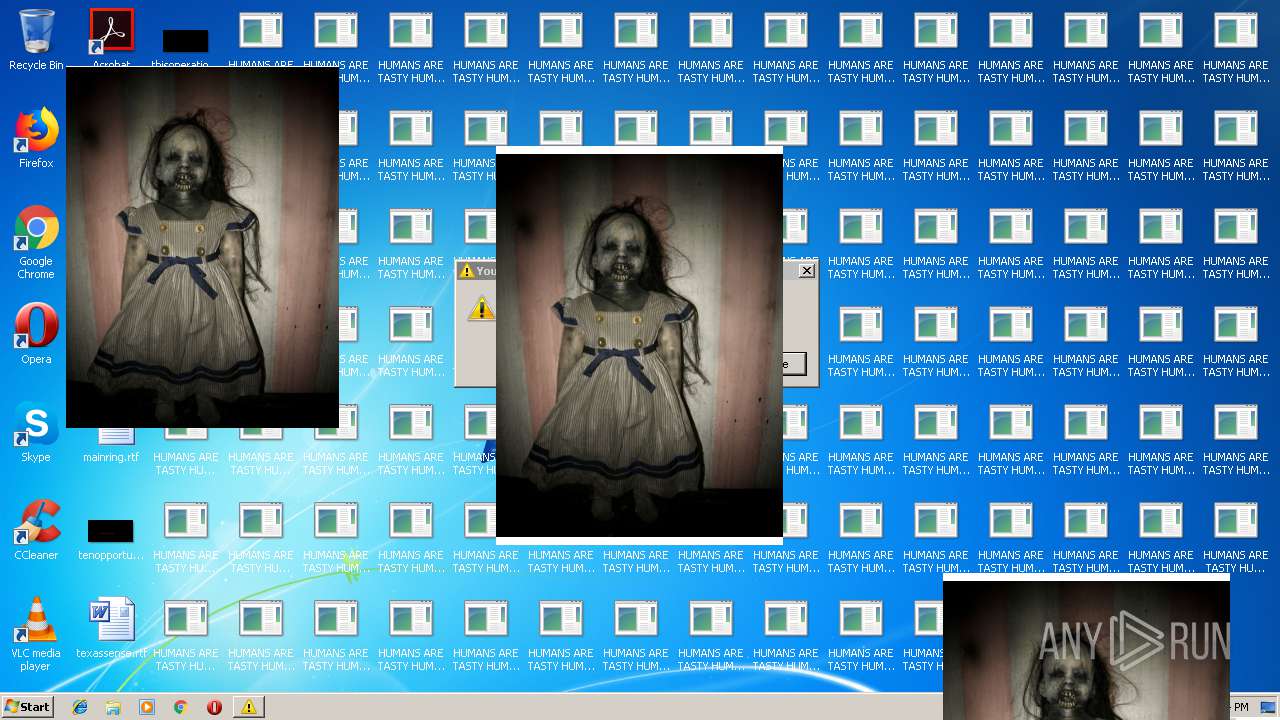
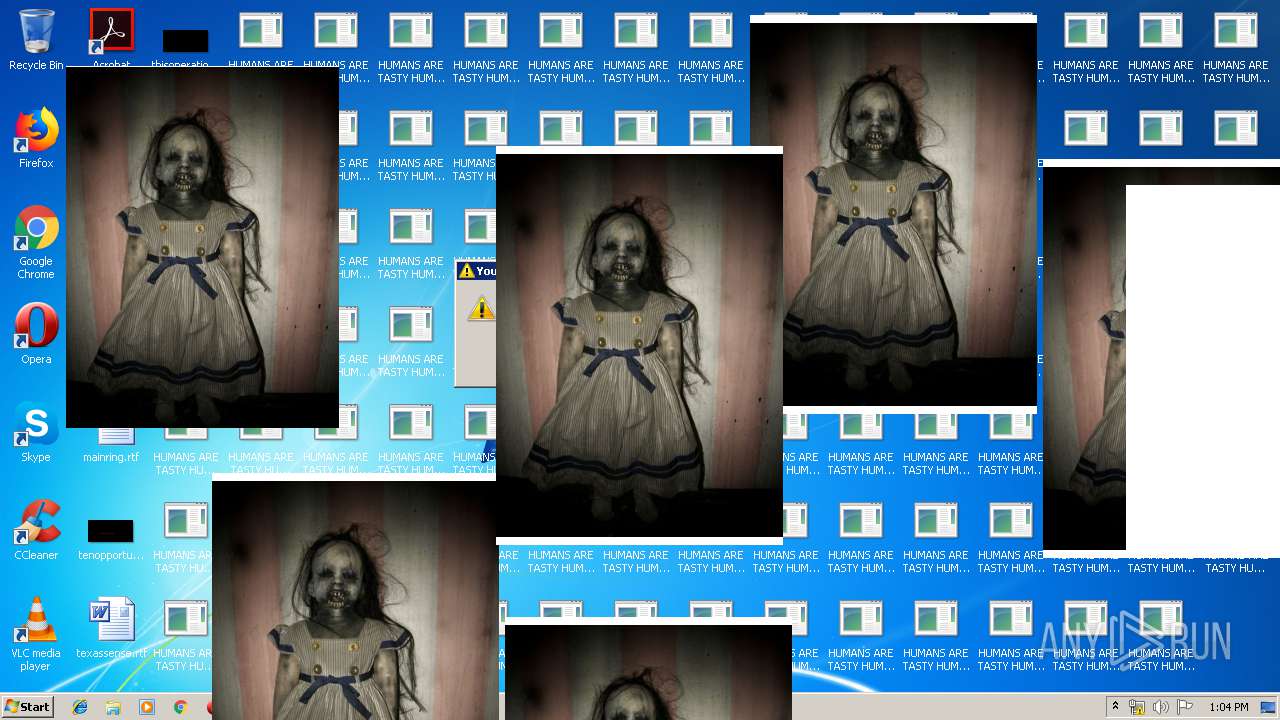
| File name: | MrsMajor2.0.exe |
| Full analysis: | https://app.any.run/tasks/d8e22f33-1fae-479e-ba02-f65cb006c80a |
| Verdict: | Malicious activity |
| Analysis date: | April 06, 2019, 12:03:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 247A35851FDEE53A1696715D67BD0905 |
| SHA1: | D2E86020E1D48E527E81E550F06C651328BD58A4 |
| SHA256: | 5DD4EA169CABF9226F54BB53E63EA6A1B5880A0D1222242AEE378EFB6255B57D |
| SSDEEP: | 786432:7VQ4fX8siQIZwastE9oGH5UcnaAVBmn163+L2:7ywXwdwRQo2O1L2 |
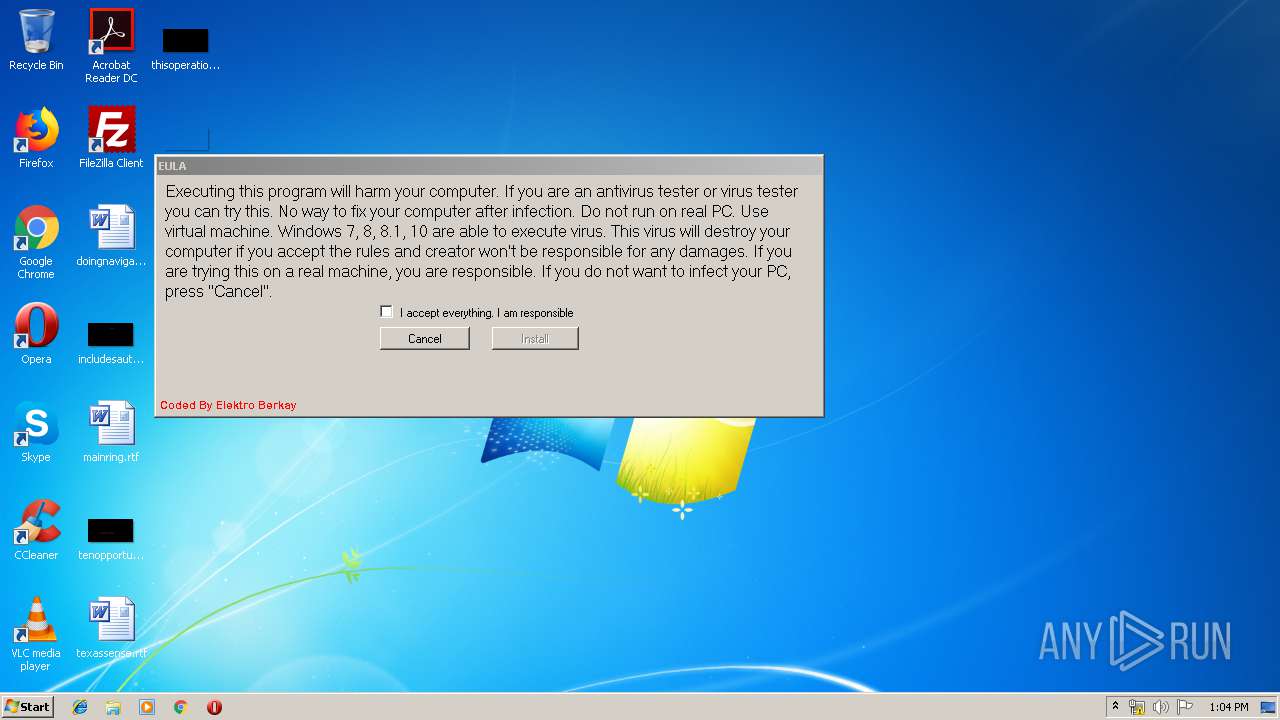
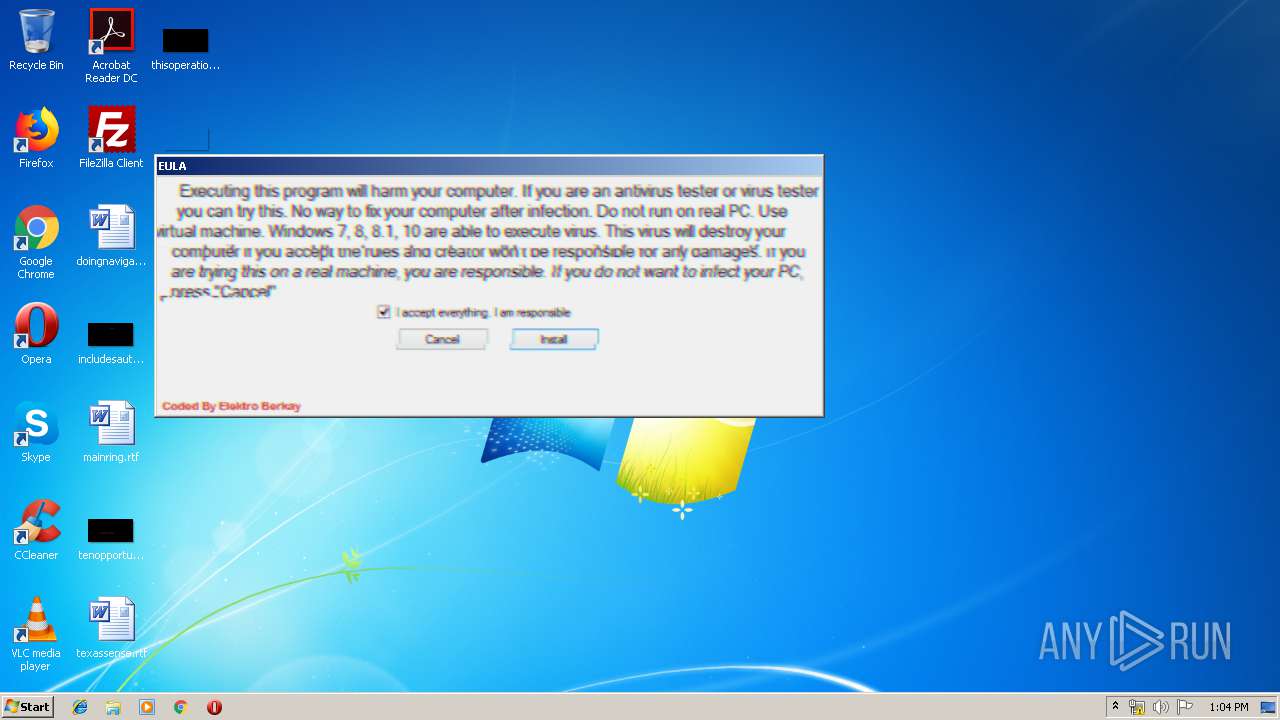
MALICIOUS
Application was dropped or rewritten from another process
- eula32.exe (PID: 3116)
- GetReady.exe (PID: 3644)
- notmuch.exe (PID: 1008)
Changes the autorun value in the registry
- wscript.exe (PID: 2352)
Changes the login/logoff helper path in the registry
- wscript.exe (PID: 2352)
Disables registry editing tools (regedit)
- wscript.exe (PID: 2352)
SUSPICIOUS
Executes scripts
- MrsMajor2.0.exe (PID: 580)
Executable content was dropped or overwritten
- MrsMajor2.0.exe (PID: 580)
- wscript.exe (PID: 2352)
- cmd.exe (PID: 2520)
Starts CMD.EXE for commands execution
- wscript.exe (PID: 2352)
- GetReady.exe (PID: 3644)
Creates files in the program directory
- wscript.exe (PID: 2352)
Uses ICACLS.EXE to modify access control list
- cmd.exe (PID: 2520)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (35.8) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (31.7) |
| .scr | | | Windows screen saver (15) |
| .dll | | | Win32 Dynamic Link Library (generic) (7.5) |
| .exe | | | Win32 Executable (generic) (5.1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2016:05:04 09:30:05+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 2.5 |
| CodeSize: | 49152 |
| InitializedDataSize: | 26840064 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 1.0.0.0 |
| ProductVersionNumber: | 1.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug, Pre-release, Private build |
| FileOS: | Windows 16-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Windows, Latin1 |
| FileDescription: | Cling Clang.. |
| FileVersion: | 1,0,0,0 |
| ProductName: | MrsMajor 2.0 |
| InternalName: | majordared.exe |
| ProductVersion: | 1.0.0.0 |
| LegalCopyright: | Elektro Berkay |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 04-May-2016 07:30:05 |
| Detected languages: |
|
| FileDescription: | Cling Clang.. |
| FileVersion: | 1,0,0,0 |
| ProductName: | MrsMajor 2.0 |
| InternalName: | majordared.exe |
| ProductVersion: | 1.0.0.0 |
| LegalCopyright: | Elektro Berkay |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 04-May-2016 07:30:05 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.code | 0x00001000 | 0x000020C7 | 0x00002200 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.43644 |
.text | 0x00004000 | 0x00009C1A | 0x00009E00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.5668 |
.rdata | 0x0000E000 | 0x0000097E | 0x00000A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.60937 |
.data | 0x0000F000 | 0x00001784 | 0x00001400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 4.79557 |
.rsrc | 0x00011000 | 0x01996D74 | 0x01996E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.7581 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.09999 | 668 | Latin 1 / Western European | UNKNOWN | RT_MANIFEST |
B | 5.38576 | 3046 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
D | 3.46772 | 14 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
F | 7.75753 | 26786395 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
I | 4.82225 | 1874 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
N | 2.86596 | 20 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
O | 0.650022 | 6 | Latin 1 / Western European | UNKNOWN | RT_RCDATA |
Imports
COMCTL32.DLL |
GDI32.DLL |
KERNEL32.dll |
MSVCRT.dll |
OLE32.DLL |
SHELL32.DLL |
SHLWAPI.DLL |
USER32.DLL |
WINMM.DLL |
Total processes
54
Monitored processes
13
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 296 | icacls taskmgr.exe /granted "admin":F | C:\Windows\System32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 580 | "C:\Users\admin\Desktop\MrsMajor2.0.exe" | C:\Users\admin\Desktop\MrsMajor2.0.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 864 | takeown /f taskmgr.exe | C:\Windows\System32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1000 | takeown /f sethc.exe | C:\Windows\System32\takeown.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Takes ownership of a file Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1008 | "C:\Program Files\MicrosoftWindowsServicesEtc\notmuch.exe" | C:\Program Files\MicrosoftWindowsServicesEtc\notmuch.exe | — | wscript.exe | |||||||||||
User: admin Integrity Level: HIGH Description: NotMuch Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 1476 | "C:\Users\admin\Desktop\MrsMajor2.0.exe" | C:\Users\admin\Desktop\MrsMajor2.0.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
| 1564 | "C:\Windows\System32\cmd.exe" /c cd\&cd "C:\Users\admin\AppData\Local\Temp" & eula32.exe | C:\Windows\System32\cmd.exe | — | wscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2136 | icacls sethc.exe /granted "admin":F | C:\Windows\System32\icacls.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2352 | "C:\Windows\system32\wscript.exe" C:\Users\admin\AppData\Local\Temp\9B9F.tmp\9BA0.vbs | C:\Windows\system32\wscript.exe | MrsMajor2.0.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2520 | "C:\Windows\system32\cmd.exe" /c "C:\Users\admin\AppData\Local\Temp\1\D637.bat "C:\Program Files\MicrosoftWindowsServicesEtc\GetReady.exe"" | C:\Windows\system32\cmd.exe | GetReady.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
222
Read events
192
Write events
30
Delete events
0
Modification events
| (PID) Process: | (580) MrsMajor2.0.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (580) MrsMajor2.0.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2352) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2352) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2352) wscript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System |
| Operation: | write | Name: | ConsentPromptBehaviorAdmin |
Value: 0 | |||
| (PID) Process: | (2352) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MajorX |
Value: wscript.exe "C:\Users\admin\AppData\Local\Temp\xRun.vbs" | |||
| (PID) Process: | (2352) wscript.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon |
| Operation: | write | Name: | Shell |
Value: explorer.exe, wscript.exe "C:\Program Files\MicrosoftWindowsServicesEtc\xRunReg.vbs" | |||
| (PID) Process: | (2352) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\system |
| Operation: | write | Name: | wallpaper |
Value: C:\Users\admin\AppData\Local\Temp\theTruth.jpg | |||
| (PID) Process: | (2352) wscript.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\ActiveDesktop |
| Operation: | write | Name: | NoChangingWallPaper |
Value: 1 | |||
| (PID) Process: | (2352) wscript.exe | Key: | HKEY_CURRENT_USER\Control Panel\Cursors |
| Operation: | write | Name: | Arrow |
Value: C:\Program Files\MicrosoftWindowsServicesEtc\data\excursor.ani | |||
Executable files
30
Suspicious files
0
Text files
46
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 580 | MrsMajor2.0.exe | C:\Users\admin\AppData\Local\Temp\9B9F.tmp\MicrosoftWindowsServicesEtc\clingclang.wav | — | |
MD5:— | SHA256:— | |||
| 580 | MrsMajor2.0.exe | C:\Users\admin\AppData\Local\Temp\9B9F.tmp\MicrosoftWindowsServicesEtc\breakrule.exe | executable | |
MD5:BCB0AC4822DE8AEB86EA8A83CD74D7CA | SHA256:5EAFEBD52FBF6D0E8ABD0CC9BF42D36E5B6E4D85B8EBE59F61C9F2D6DCCC65E4 | |||
| 580 | MrsMajor2.0.exe | C:\Users\admin\AppData\Local\Temp\9B9F.tmp\MicrosoftWindowsServicesEtc\CallFunc.vbs | text | |
MD5:5F9737F03289963A6D7A71EFAB0813C4 | SHA256:A767894A68EBC490CB5AB2B7B04DD12B7465553CE7BA7E41E1EA45F1EAEF5275 | |||
| 580 | MrsMajor2.0.exe | C:\Users\admin\AppData\Local\Temp\9B9F.tmp\MicrosoftWindowsServicesEtc\bsod.exe | executable | |
MD5:8F6A3B2B1AF3A4AACD8DF1734D250CFE | SHA256:6581EEAB9FD116662B4CA73F6EF00FB96E0505D01CFB446EE4B32BBDEEFE1361 | |||
| 580 | MrsMajor2.0.exe | C:\Users\admin\AppData\Local\Temp\9B9F.tmp\MicrosoftWindowsServicesEtc\checker.bat | text | |
MD5:F59801D5C49713770BDB2F14EFF34E2F | SHA256:3382484B5A6A04D05500E7622DA37C1FFAEF3A1343395942BC7802BF2A19B53F | |||
| 580 | MrsMajor2.0.exe | C:\Users\admin\AppData\Local\Temp\9B9F.tmp\9BA0.vbs | text | |
MD5:FD76266C8088A4DCA45414C36C7E9523 | SHA256:F853DDDB0F9F1B74B72BCCDB5191C28E18D466B5DBC205F7741A24391375CD6F | |||
| 580 | MrsMajor2.0.exe | C:\Users\admin\AppData\Local\Temp\9B9F.tmp\MicrosoftWindowsServicesEtc\example.txt | text | |
MD5:8837818893CE61B6730DD8A83D625890 | SHA256:CC6D0F847FDE710096B01ABF905C037594FF4AFAE6E68A8B6AF0CC59543E29BB | |||
| 580 | MrsMajor2.0.exe | C:\Users\admin\AppData\Local\Temp\9B9F.tmp\MicrosoftWindowsServicesEtc\Major.exe | executable | |
MD5:D604C29940864C64B4752D31E2DEB465 | SHA256:DA0233F5E5E9A34E8DD4F6911444CA1F3E29BB9CBD958A9F4508AC7D72CCD55D | |||
| 580 | MrsMajor2.0.exe | C:\Users\admin\AppData\Local\Temp\9B9F.tmp\MicrosoftWindowsServicesEtc\GetReady.exe | executable | |
MD5:57F3795953DAFA8B5E2B24BA5BFAD87F | SHA256:5319958EFC38EA81F61854EB9F6C8AEE32394D4389E52FE5C1F7F7EF6B261725 | |||
| 580 | MrsMajor2.0.exe | C:\Users\admin\AppData\Local\Temp\9B9F.tmp\MicrosoftWindowsServicesEtc\majordared.exe | executable | |
MD5:570D35AABEE1887F7F6AB3F0A1E76984 | SHA256:FA24BC7BC366F2AD579D57A691FB0D10D868E501221DF0C32A98E705D2D61E43 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report