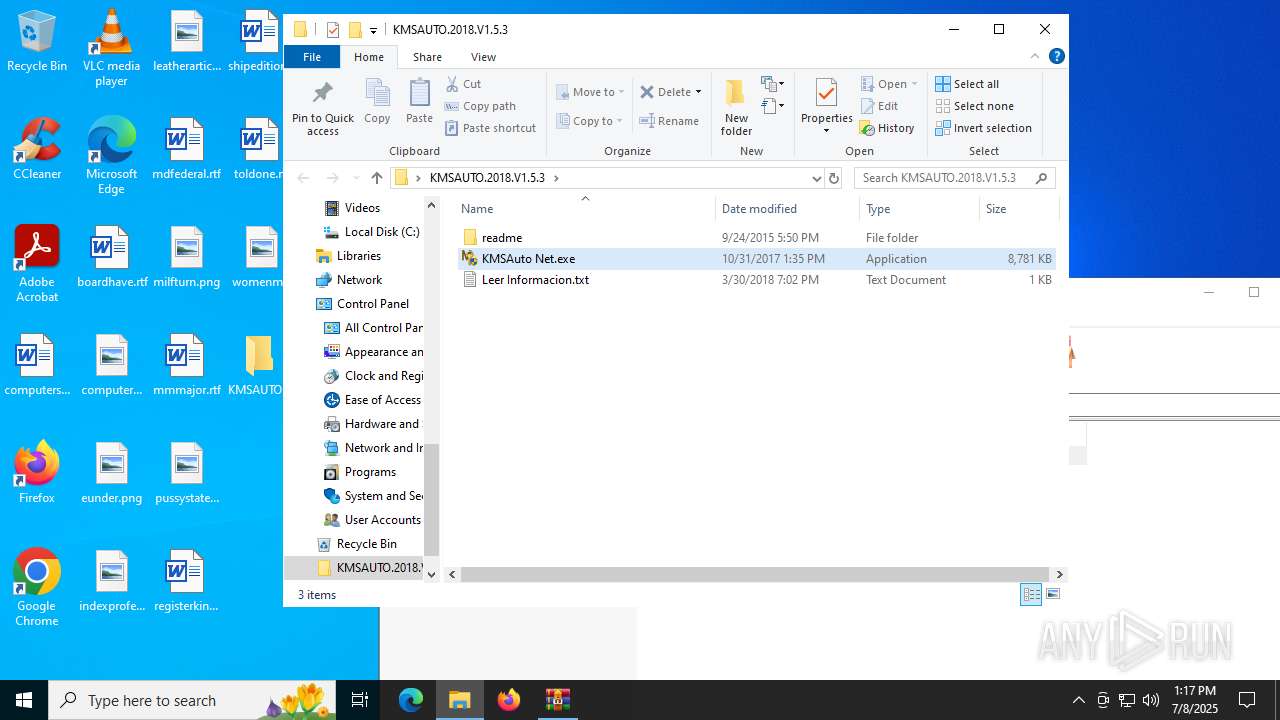
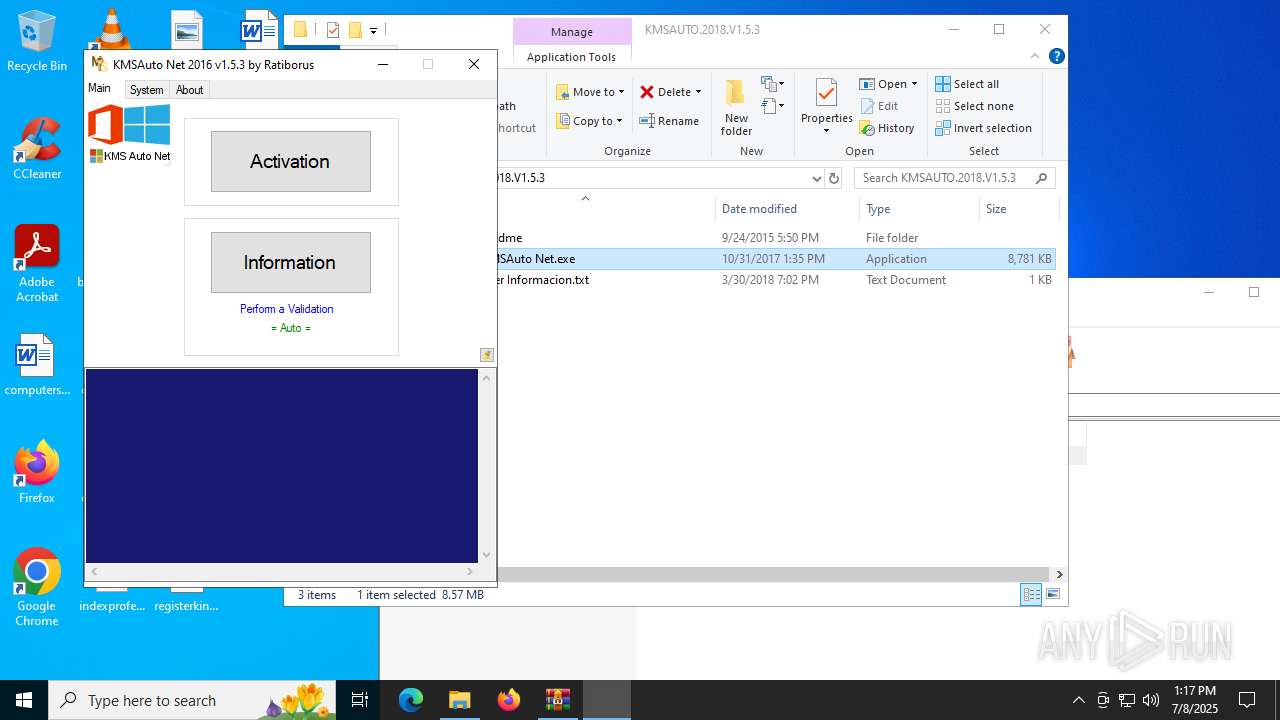
| File name: | KMSAUTO.2018.V1.5.3.rar |
| Full analysis: | https://app.any.run/tasks/ab6399a1-f353-41d8-85ae-0502cdac07be |
| Verdict: | Malicious activity |
| Analysis date: | July 08, 2025, 13:16:24 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | A85EAC002928ACE6BBDD9C38DCCC0489 |
| SHA1: | 962CF3CBC987284708F85DDBC5E2270C4D60E8CA |
| SHA256: | 5DD424D55D332A96C59AFE4D4F30C52CBBC06E766BF82F5632E67BD171923053 |
| SSDEEP: | 49152:A9wrICJf9rFz/mKRIkID17mx5idipAla+OGXmtkQ+eQ52a/YVwkjm9d3KreTu2y9:31xz5R+1sidngtkFpF0e9oeTu27kd |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2080)
Executing a file with an untrusted certificate
- KMSAuto Net.exe (PID: 3620)
- KMSAuto Net.exe (PID: 1632)
- certmgr.exe (PID: 3636)
- certmgr.exe (PID: 2696)
- KMSSS.exe (PID: 4684)
- FakeClient.exe (PID: 3704)
SUSPICIOUS
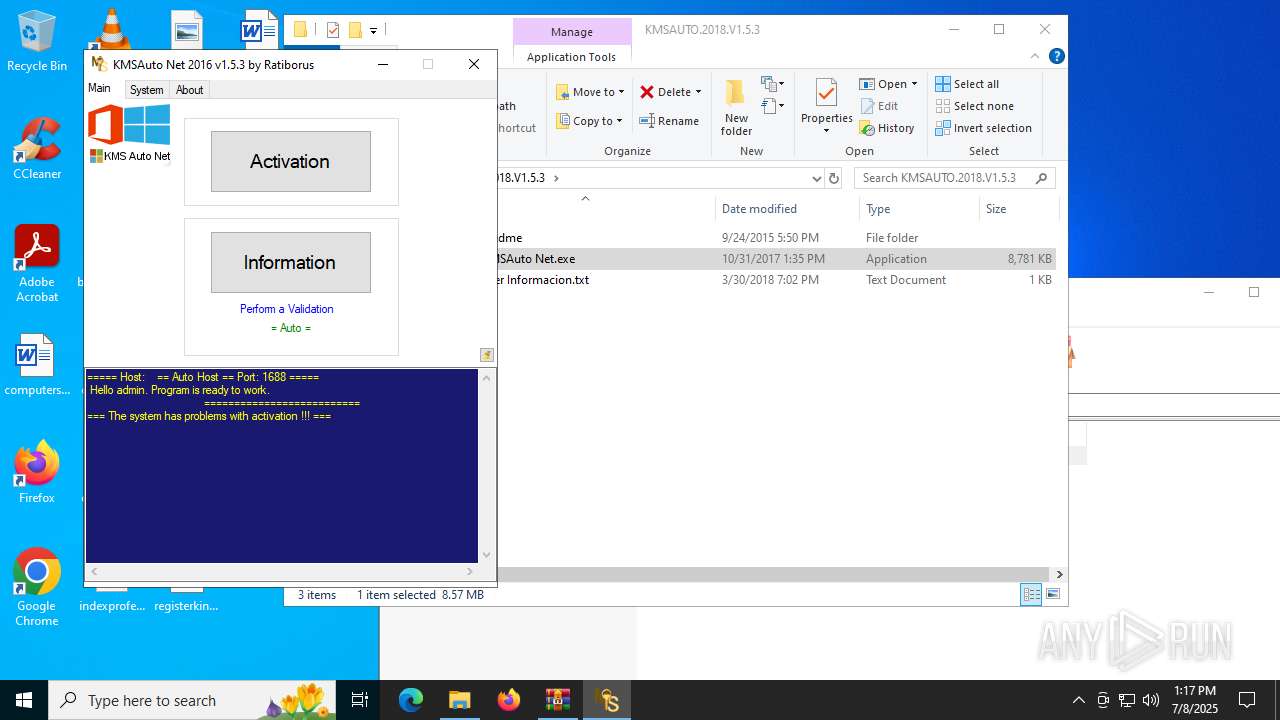
KMS tool has been detected
- KMSAuto Net.exe (PID: 1632)
- KMSAuto Net.exe (PID: 3620)
- KMSAuto Net.exe (PID: 1632)
Reads Internet Explorer settings
- KMSAuto Net.exe (PID: 1632)
Starts CMD.EXE for commands execution
- KMSAuto Net.exe (PID: 1632)
- cmd.exe (PID: 6260)
There is functionality for taking screenshot (YARA)
- KMSAuto Net.exe (PID: 1632)
Executable content was dropped or overwritten
- wzt.dat (PID: 5352)
- KMSAuto Net.exe (PID: 1632)
- AESDecoder.exe (PID: 5724)
- bin_x64.dat (PID: 5744)
- bin.dat (PID: 6896)
- bin_x64.dat (PID: 6164)
Drops 7-zip archiver for unpacking
- KMSAuto Net.exe (PID: 1632)
Starts application with an unusual extension
- cmd.exe (PID: 4512)
- cmd.exe (PID: 864)
- cmd.exe (PID: 3760)
- cmd.exe (PID: 5824)
Process drops legitimate windows executable
- wzt.dat (PID: 5352)
- bin_x64.dat (PID: 5744)
- bin_x64.dat (PID: 6164)
Adds/modifies Windows certificates
- certmgr.exe (PID: 3636)
- certmgr.exe (PID: 2696)
Drops a system driver (possible attempt to evade defenses)
- bin_x64.dat (PID: 5744)
- bin_x64.dat (PID: 6164)
Application launched itself
- cmd.exe (PID: 6260)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- KMSAuto Net.exe (PID: 1632)
Creates or modifies Windows services
- KMSAuto Net.exe (PID: 1632)
Windows service management via SC.EXE
- sc.exe (PID: 3556)
Executes as Windows Service
- KMSSS.exe (PID: 4684)
Uses ROUTE.EXE to modify routing table
- cmd.exe (PID: 5716)
Uses NETSH.EXE to add a firewall rule or allowed programs
- KMSAuto Net.exe (PID: 1632)
Creates a new Windows service
- sc.exe (PID: 2292)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2080)
Manual execution by a user
- KMSAuto Net.exe (PID: 3620)
- KMSAuto Net.exe (PID: 1632)
Checks supported languages
- KMSAuto Net.exe (PID: 1632)
- wzt.dat (PID: 5352)
- certmgr.exe (PID: 3636)
- certmgr.exe (PID: 2696)
- AESDecoder.exe (PID: 5724)
- bin_x64.dat (PID: 5744)
- bin.dat (PID: 6896)
- KMSSS.exe (PID: 4684)
- bin_x64.dat (PID: 6164)
- FakeClient.exe (PID: 3704)
Reads the computer name
- KMSAuto Net.exe (PID: 1632)
- KMSSS.exe (PID: 4684)
- FakeClient.exe (PID: 3704)
Reads the machine GUID from the registry
- KMSAuto Net.exe (PID: 1632)
- KMSSS.exe (PID: 4684)
Creates a new folder
- cmd.exe (PID: 4960)
- cmd.exe (PID: 6412)
Creates files or folders in the user directory
- KMSAuto Net.exe (PID: 1632)
Reads product name
- KMSAuto Net.exe (PID: 1632)
Reads Environment values
- KMSAuto Net.exe (PID: 1632)
Creates files in the program directory
- cmd.exe (PID: 6412)
- wzt.dat (PID: 5352)
- KMSAuto Net.exe (PID: 1632)
- AESDecoder.exe (PID: 5724)
- bin_x64.dat (PID: 5744)
- bin.dat (PID: 6896)
- KMSSS.exe (PID: 4684)
- bin_x64.dat (PID: 6164)
The sample compiled with english language support
- wzt.dat (PID: 5352)
- KMSAuto Net.exe (PID: 1632)
- bin_x64.dat (PID: 5744)
- bin_x64.dat (PID: 6164)
Adds a route via ROUTE.EXE
- ROUTE.EXE (PID: 3588)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| FileVersion: | RAR v4 |
|---|---|
| CompressedSize: | 3494384 |
| UncompressedSize: | 8991592 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2017:10:31 13:35:34 |
| PackingMethod: | Normal |
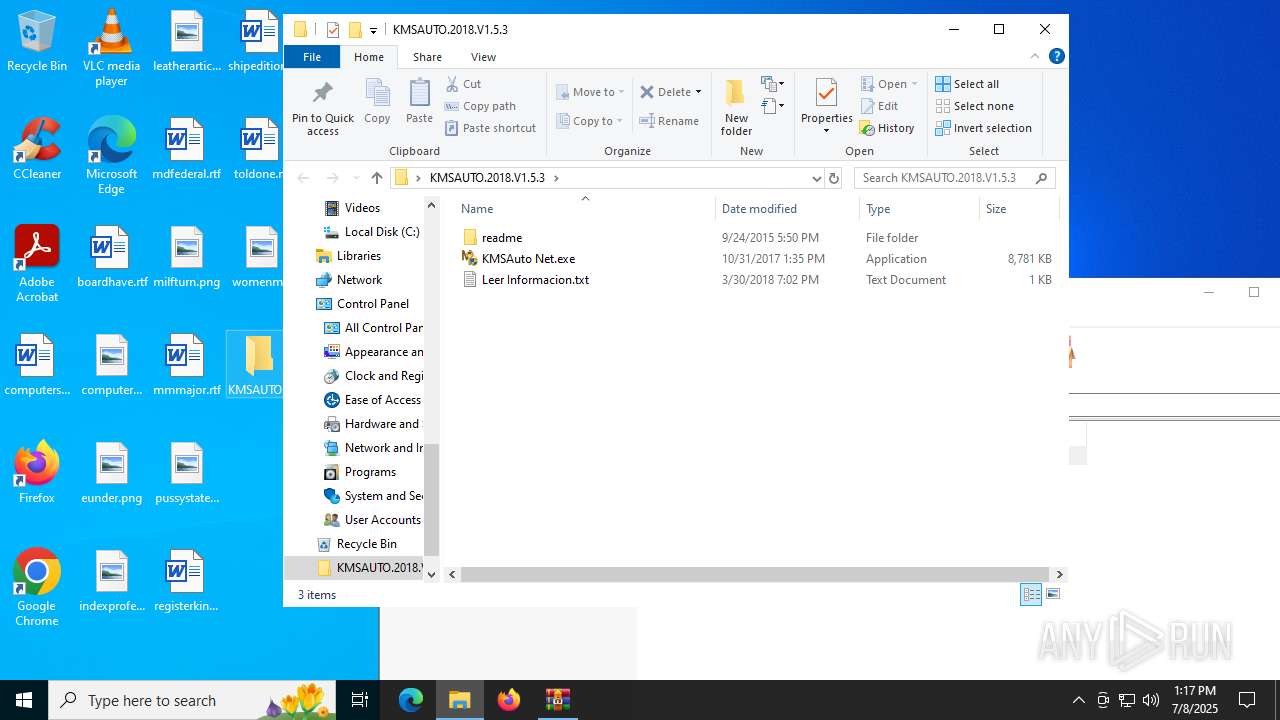
| ArchivedFileName: | KMSAUTO.2018.V1.5.3\KMSAuto Net.exe |
Total processes
201
Monitored processes
66
Malicious processes
5
Suspicious processes
5
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 620 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | C:\WINDOWS\Sysnative\cmd.exe /c echo test>>"C:\Users\admin\Desktop\KMSAUTO.2018.V1.5.3\test.test" | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 864 | C:\WINDOWS\Sysnative\cmd.exe /D /c bin.dat -y -pkmsauto | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1044 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1200 | C:\WINDOWS\Sysnative\cmd.exe /D /c del /F /Q "bin.dat" | C:\Windows\System32\cmd.exe | — | KMSAuto Net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1204 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1336 | find ":1688 " | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (grep) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1612 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1612 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 760
Read events
5 728
Write events
17
Delete events
15
Modification events
| (PID) Process: | (2080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\KMSAUTO.2018.V1.5.3.rar | |||
| (PID) Process: | (2080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 4 |
Value: | |||
| (PID) Process: | (2080) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 3 |
Value: | |||
Executable files
26
Suspicious files
6
Text files
16
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2080 | WinRAR.exe | C:\Users\admin\Desktop\KMSAUTO.2018.V1.5.3\Leer Informacion.txt | text | |
MD5:325D5B655C582A93892CD4B87A751CDC | SHA256:8972F7BF9AFAB204BB81BC426875464170E49091538157B5D21269E3C4447777 | |||
| 2080 | WinRAR.exe | C:\Users\admin\Desktop\KMSAUTO.2018.V1.5.3\readme\readme_bg.txt | text | |
MD5:C55477D53DC34F0C75E62E9657C6A443 | SHA256:99D0EDB27FB925CED9CC874B9DFEE992922C793CB3DC2FF316C27FC5C2F95CB8 | |||
| 2080 | WinRAR.exe | C:\Users\admin\Desktop\KMSAUTO.2018.V1.5.3\readme\readme_cn.txt | text | |
MD5:331ABF76B15C262AB1062B2A4133EF1D | SHA256:563DF1A8135D7A95B83732402E5E7B9758ED087BE77713BE3FB3F16368A0E626 | |||
| 2080 | WinRAR.exe | C:\Users\admin\Desktop\KMSAUTO.2018.V1.5.3\KMSAuto Net.exe | executable | |
MD5:FD743B55D530E0468805DE0E83758FE9 | SHA256:161937ED1502C491748D055287898DD37AF96405AEFF48C2500B834F6739E72D | |||
| 1632 | KMSAuto Net.exe | C:\ProgramData\KMSAuto\bin.dat | executable | |
MD5:4C3E59E7EE273173E9413531647C3881 | SHA256:29D3EEF47A628754C99C65C789FC42331FA18AADF49E4D4AB4EDD0D0C76163BA | |||
| 6896 | bin.dat | C:\ProgramData\KMSAuto\bin\KMSSS.exe.aes | binary | |
MD5:6B9E3C521D83336489DA3D7B57101F01 | SHA256:1EE3257EA009B2E1DE167FA1E28BF4238E3C3F073D36356F6A65023E3C976145 | |||
| 728 | cmd.exe | C:\Users\admin\Desktop\KMSAUTO.2018.V1.5.3\test.test | text | |
MD5:9F06243ABCB89C70E0C331C61D871FA7 | SHA256:837CCB607E312B170FAC7383D7CCFD61FA5072793F19A25E75FBACB56539B86B | |||
| 1632 | KMSAuto Net.exe | C:\ProgramData\KMSAuto\wzt.dat | executable | |
MD5:822DA2319294F2B768BFE9ED4EEBAC15 | SHA256:17B74D4EA905FAC0BA6857F78F47EE1E940675AF1BC27DED69FE2941318106EF | |||
| 6896 | bin.dat | C:\ProgramData\KMSAuto\bin\AESDecoder.exe | executable | |
MD5:B90ED3E4DBB23A464723706F12C86065 | SHA256:8391D5B724D235BA52531D9A6D85E466382CE15CBD6BA97C4AD1278ED1F03BD7 | |||
| 5352 | wzt.dat | C:\ProgramData\KMSAuto\wzt\wzteam.cer | der | |
MD5:76B56D90E6F1DA030A8B85E64579F25A | SHA256:FD2D7DF0220DD65EE23D0090299DFCC356F6F8F7167BAE9ADF7D08CEFAF39D02 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
21
DNS requests
16
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 2.16.168.114:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
436 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2272 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
2272 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5060 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 52.137.106.217:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
1268 | svchost.exe | 2.16.168.114:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
1268 | svchost.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
436 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
436 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Unknown Traffic | ET USER_AGENTS Microsoft Dr Watson User-Agent (MSDW) |
Process | Message |
|---|---|
FakeClient.exe | WdfCoInstaller: [07/08/2025 13:17.29.192] ReadComponents: WdfSection for Driver Service windivert using KMDF lib version Major 0x1, minor 0x9
|
FakeClient.exe | WdfCoInstaller: [07/08/2025 13:17.29.192] BootApplication: could not open service windivert, error error(1060) The specified service does not exist as an installed service.
|
FakeClient.exe | WdfCoInstaller: [07/08/2025 13:17.29.192] BootApplication: GetStartType error error(87) The parameter is incorrect.
Driver Service name windivert
|