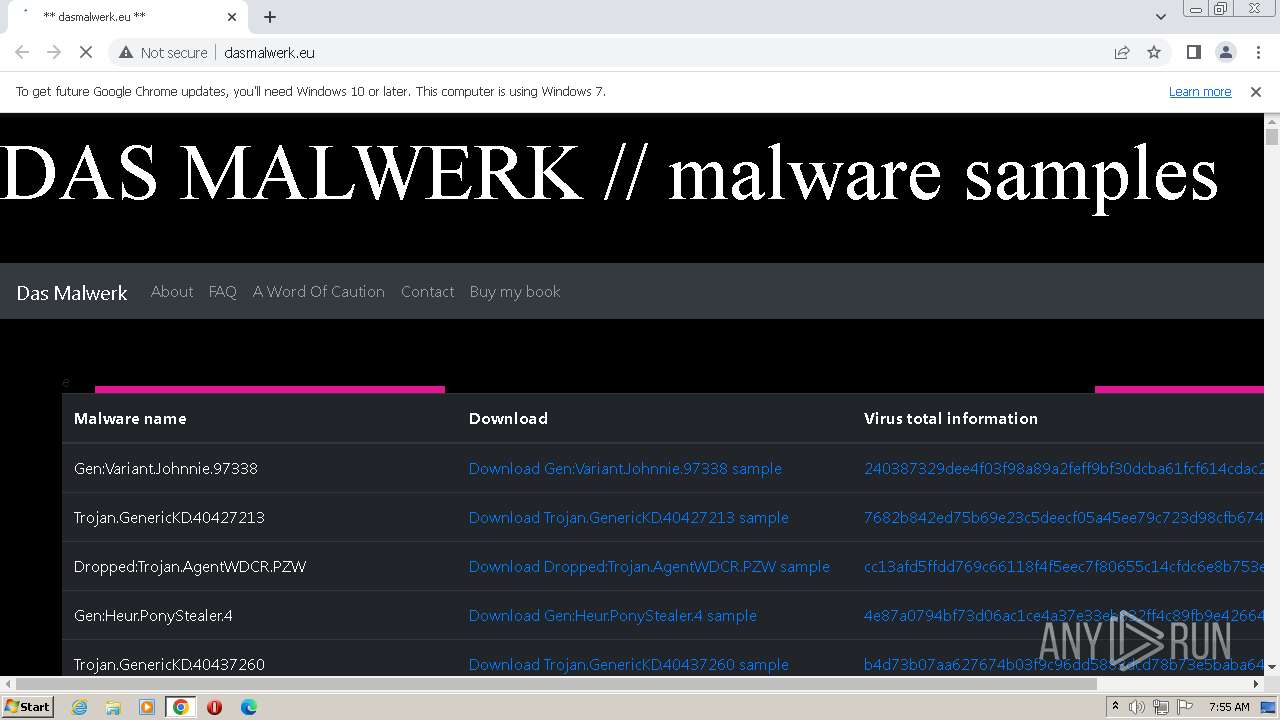
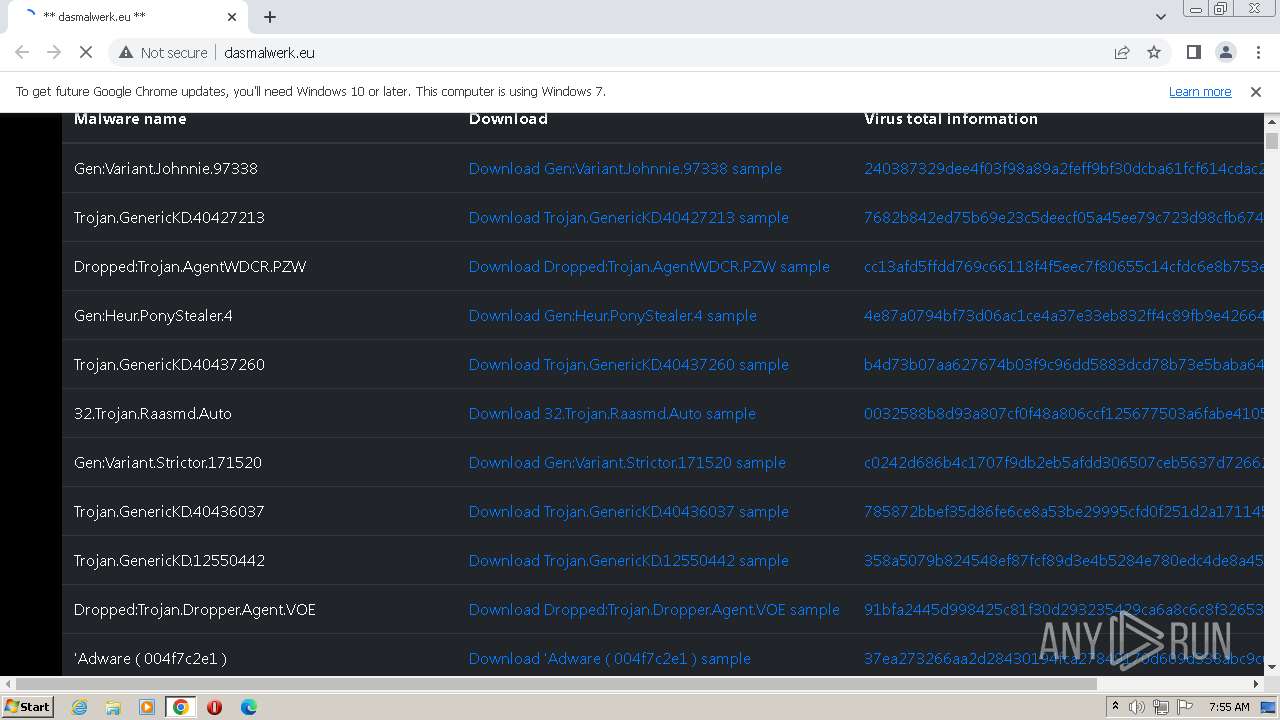
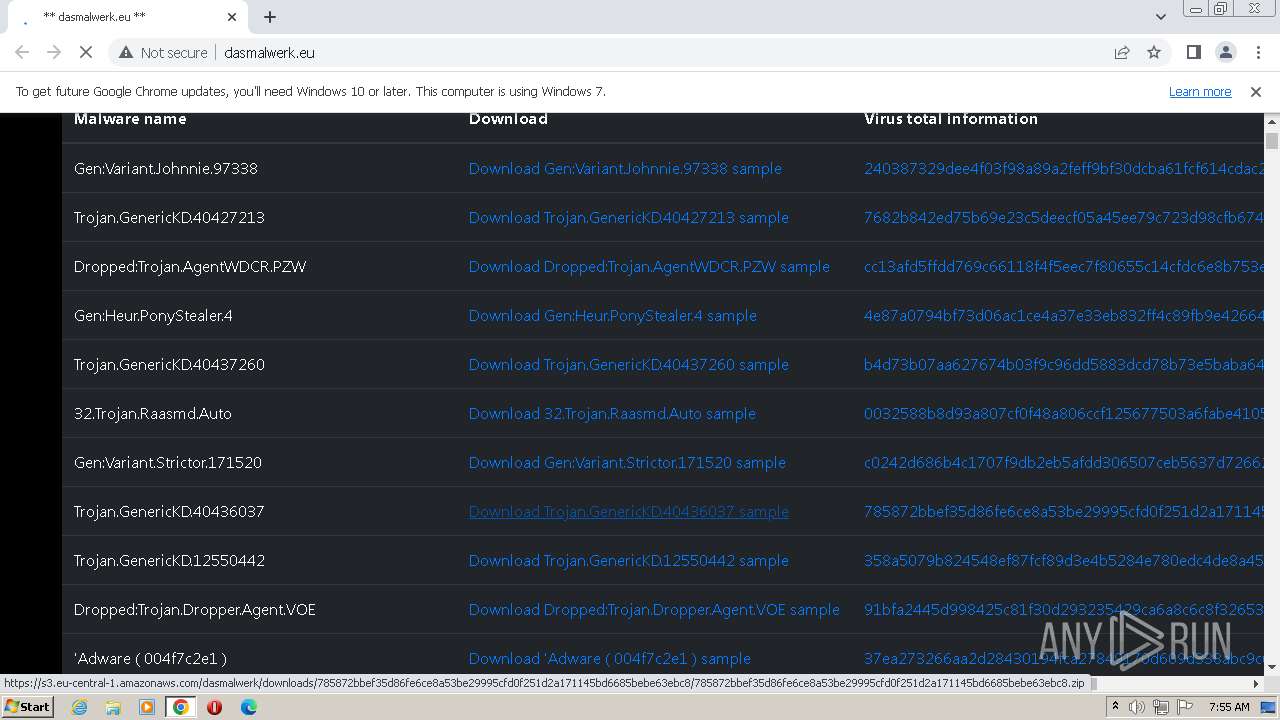
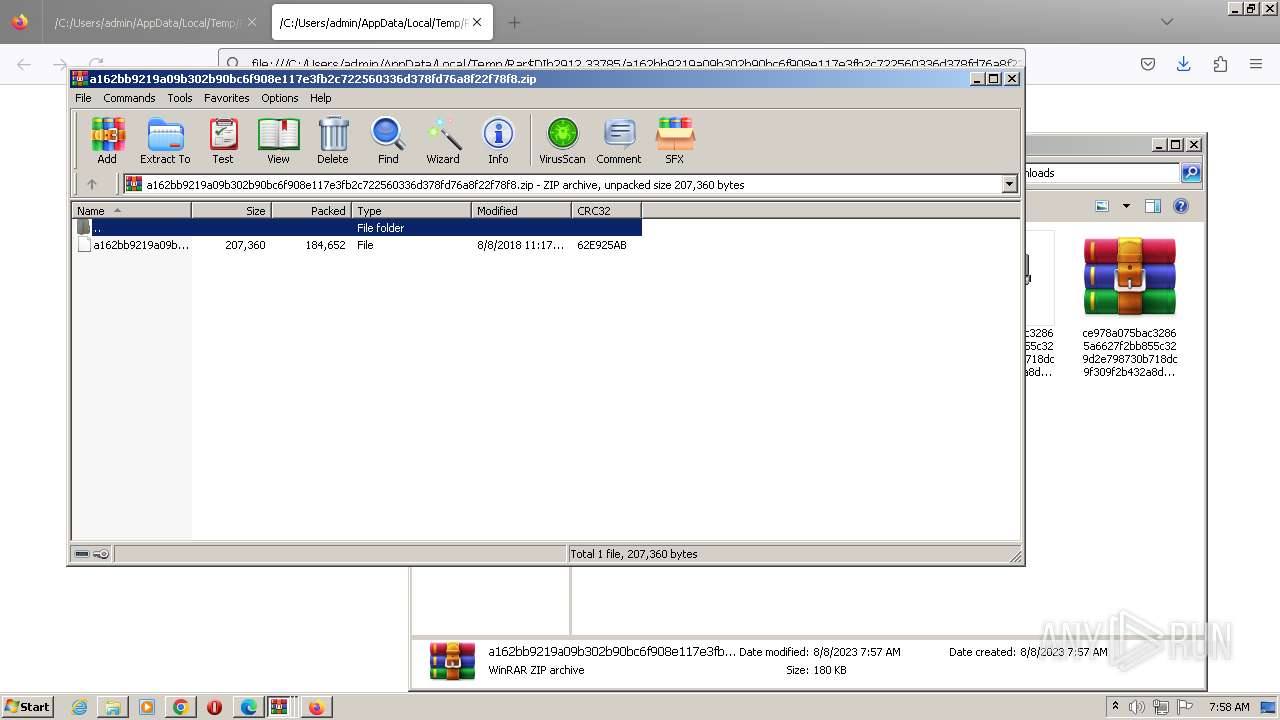
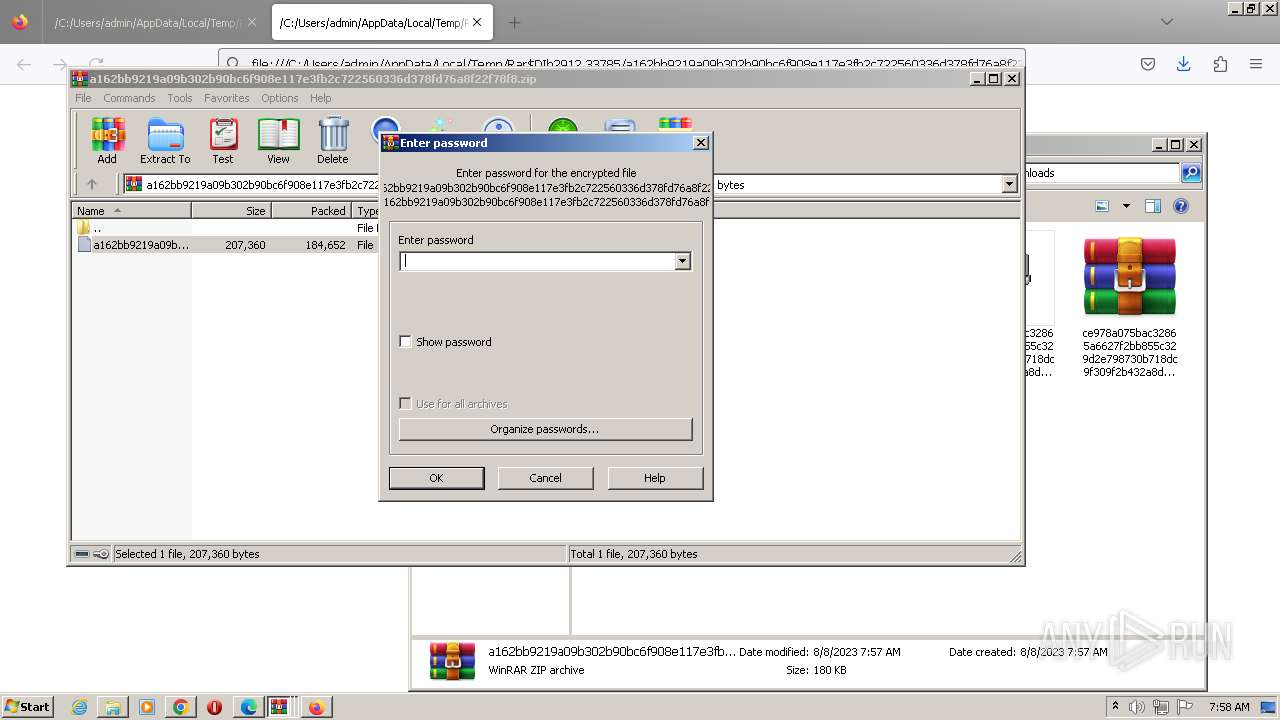
| URL: | http://dasmalwerk.eu/ |
| Full analysis: | https://app.any.run/tasks/a113a111-83b2-4403-a22a-2b63f4c45254 |
| Verdict: | Malicious activity |
| Analysis date: | August 08, 2023, 06:54:40 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | BFEFE9C6EB5288165D2522ED489FFE4A |
| SHA1: | 1239B2F9266826F5B1808C0485E5822D4B336E62 |
| SHA256: | 5DB25CBA94050D458B70691903AB25FF7F5304A0669764BD06BB78945DCD2238 |
| SSDEEP: | 3:N1KaEWIEJK0f:Ca/INk |
MALICIOUS
Application was dropped or rewritten from another process
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 2324)
- DjvuApp.exe (PID: 1204)
- DjvuApp.exe (PID: 3020)
- DjvuApp.exe (PID: 3300)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 284)
- DjvuApp.exe (PID: 620)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 1388)
- DjvuApp.exe (PID: 1276)
- DjvuApp.exe (PID: 2228)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 1968)
- DjvuApp.exe (PID: 2948)
- DjvuApp.exe (PID: 284)
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 5436)
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 5916)
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 5132)
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 4232)
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 4088)
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 6064)
Loads dropped or rewritten executable
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 2324)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 284)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 1388)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 1968)
Changes the autorun value in the registry
- DjvuApp.exe (PID: 3300)
- DjvuApp.exe (PID: 1276)
- DjvuApp.exe (PID: 2948)
SUSPICIOUS
Uses RUNDLL32.EXE to load library
- WinRAR.exe (PID: 1636)
- WinRAR.exe (PID: 2912)
- WinRAR.exe (PID: 1808)
Reads the Internet Settings
- rundll32.exe (PID: 896)
- rundll32.exe (PID: 2588)
- DjvuApp.exe (PID: 1276)
- rundll32.exe (PID: 4964)
Executable content was dropped or overwritten
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 2324)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 284)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 1388)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 1968)
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 5436)
Creates a software uninstall entry
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 284)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 1388)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 1968)
Checks for external IP
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 5916)
Starts itself from another location
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 5436)
The process executes via Task Scheduler
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 4232)
INFO
The process uses the downloaded file
- chrome.exe (PID: 3900)
- chrome.exe (PID: 2552)
- chrome.exe (PID: 2968)
- WinRAR.exe (PID: 1636)
- chrome.exe (PID: 2596)
- WinRAR.exe (PID: 2912)
- chrome.exe (PID: 2672)
- WinRAR.exe (PID: 1808)
Reads the computer name
- wmpnscfg.exe (PID: 3772)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 2324)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 284)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 1388)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 1968)
- DjvuApp.exe (PID: 1276)
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 5436)
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 5916)
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 5132)
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 4232)
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 4088)
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 6064)
Checks supported languages
- wmpnscfg.exe (PID: 3772)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 2324)
- DjvuApp.exe (PID: 1204)
- DjvuApp.exe (PID: 3020)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 284)
- DjvuApp.exe (PID: 620)
- DjvuApp.exe (PID: 3300)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 1388)
- DjvuApp.exe (PID: 2228)
- DjvuApp.exe (PID: 1276)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 1968)
- DjvuApp.exe (PID: 284)
- DjvuApp.exe (PID: 2948)
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 5916)
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 5436)
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 4232)
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 5132)
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 4088)
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 6064)
Manual execution by a user
- wmpnscfg.exe (PID: 3772)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 2324)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 284)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 1388)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 1968)
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 5436)
- msedge.exe (PID: 3800)
- WinRAR.exe (PID: 1808)
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 5132)
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 4088)
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 6064)
Reads the machine GUID from the registry
- wmpnscfg.exe (PID: 3772)
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 5916)
The process checks LSA protection
- wmpnscfg.exe (PID: 3772)
- rundll32.exe (PID: 896)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 2324)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 284)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 1388)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 1968)
- rundll32.exe (PID: 2588)
- DjvuApp.exe (PID: 1276)
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 5916)
- rundll32.exe (PID: 4964)
Application launched itself
- firefox.exe (PID: 2588)
- firefox.exe (PID: 2776)
- chrome.exe (PID: 2880)
- firefox.exe (PID: 3128)
- msedge.exe (PID: 2924)
- msedge.exe (PID: 3800)
- firefox.exe (PID: 5568)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1636)
- firefox.exe (PID: 2776)
- WinRAR.exe (PID: 2912)
- WinRAR.exe (PID: 1808)
Create files in a temporary directory
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 2324)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 284)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 1388)
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 1968)
Creates files or folders in the user directory
- ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe (PID: 2324)
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 5436)
- a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe (PID: 5916)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
140
Monitored processes
90
Malicious processes
8
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 188 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=3804 --field-trial-handle=1124,i,14363421786305986881,13176703260167491289,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 280 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=1864 --field-trial-handle=1124,i,14363421786305986881,13176703260167491289,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
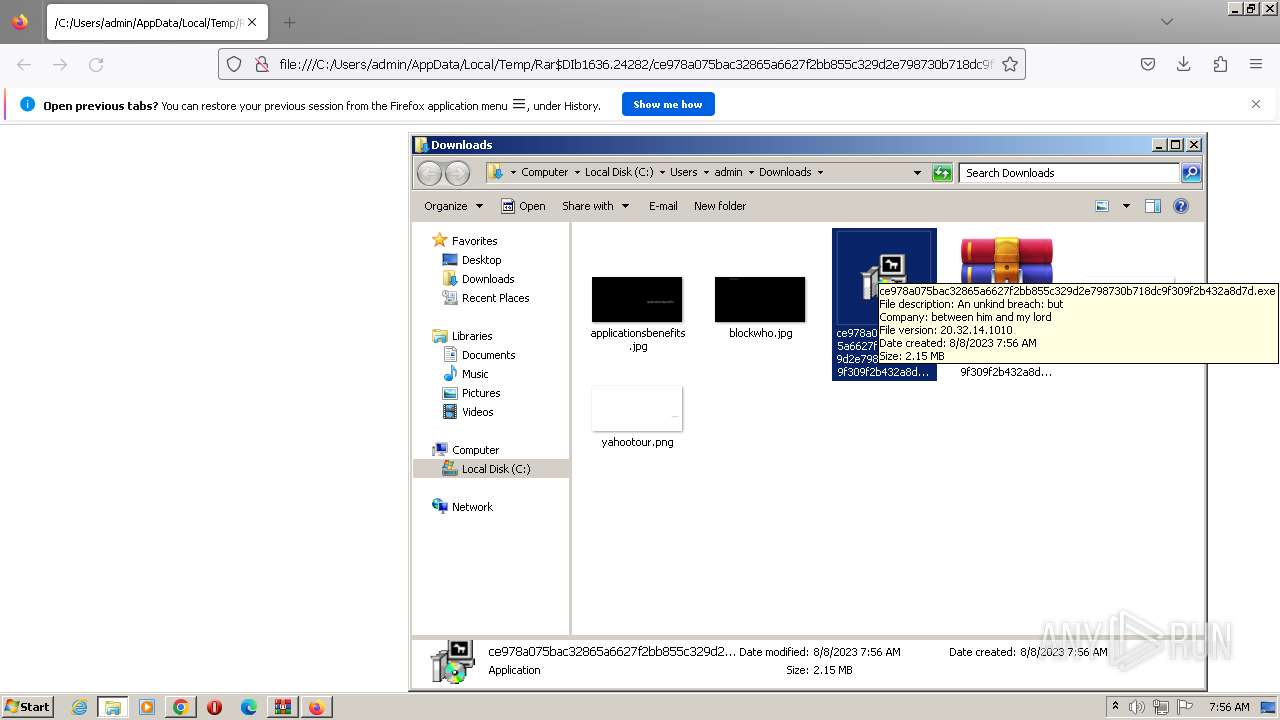
| 284 | "C:\Users\admin\Downloads\ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe" | C:\Users\admin\Downloads\ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe | explorer.exe | ||||||||||||
User: admin Company: between him and my lord Integrity Level: MEDIUM Description: An unkind breach: but Exit code: 0 Version: 20.32.14.1010 Modules
| |||||||||||||||
| 284 | "C:\Users\admin\AppData\Roaming\DjvuApp\DjvuApp.exe" "write_patch_str_to_reg" "C:\Users\admin\Downloads\ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe" "HKCU" "Software\DjvuApp" "intesq" | C:\Users\admin\AppData\Roaming\DjvuApp\DjvuApp.exe | — | ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe | |||||||||||
User: admin Company: Ialkiyxli Zeuvfifqyu Integrity Level: MEDIUM Description: dpaveoh rimpeypse Exit code: 0 Version: 9.19.201.12821 Modules
| |||||||||||||||
| 448 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=2960 --field-trial-handle=1124,i,14363421786305986881,13176703260167491289,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 488 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2008 --field-trial-handle=1124,i,14363421786305986881,13176703260167491289,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 620 | "C:\Users\admin\AppData\Roaming\DjvuApp\DjvuApp.exe" "write_patch_str_to_reg" "C:\Users\admin\Downloads\ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe" "HKCU" "Software\DjvuApp" "intesq" | C:\Users\admin\AppData\Roaming\DjvuApp\DjvuApp.exe | — | ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe | |||||||||||
User: admin Company: Ialkiyxli Zeuvfifqyu Integrity Level: MEDIUM Description: dpaveoh rimpeypse Exit code: 0 Version: 9.19.201.12821 Modules
| |||||||||||||||
| 668 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=1420 --field-trial-handle=1124,i,14363421786305986881,13176703260167491289,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
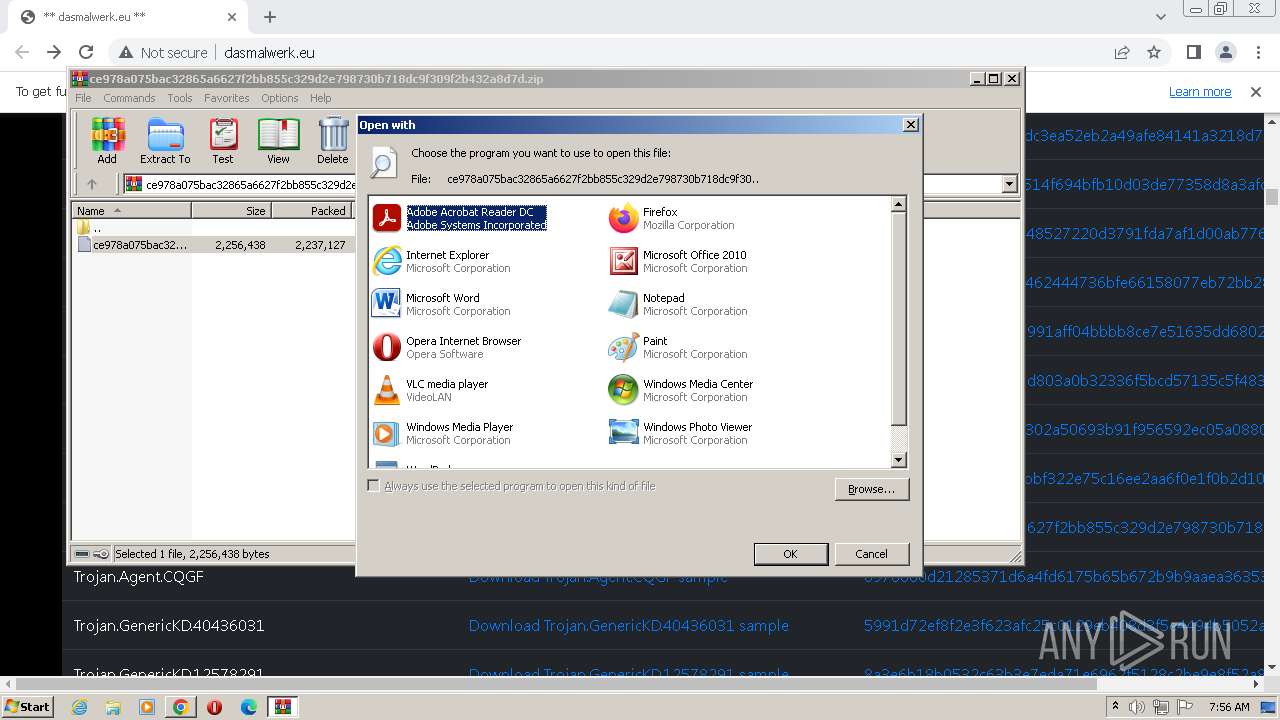
| 896 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Rar$DIb1636.24282\ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d | C:\Windows\System32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1204 | "C:\Users\admin\AppData\Roaming\DjvuApp\DjvuApp.exe" "first_run" "C:\Users\admin\Downloads\ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe" | C:\Users\admin\AppData\Roaming\DjvuApp\DjvuApp.exe | — | ce978a075bac32865a6627f2bb855c329d2e798730b718dc9f309f2b432a8d7d.exe | |||||||||||
User: admin Company: Ialkiyxli Zeuvfifqyu Integrity Level: MEDIUM Description: dpaveoh rimpeypse Exit code: 0 Version: 9.19.201.12821 Modules
| |||||||||||||||
Total events
33 576
Read events
33 034
Write events
538
Delete events
4
Modification events
| (PID) Process: | (2880) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2880) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2880) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (2880) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2880) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2880) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 1 | |||
| (PID) Process: | (2880) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2880) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (2880) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_installdate |
Value: 0 | |||
| (PID) Process: | (2880) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid_enableddate |
Value: 0 | |||
Executable files
20
Suspicious files
396
Text files
182
Unknown types
19
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF4672ab.TMP | — | |
MD5:— | SHA256:— | |||
| 2880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:9C016064A1F864C8140915D77CF3389A | SHA256:0E7265D4A8C16223538EDD8CD620B8820611C74538E420A88E333BE7F62AC787 | |||
| 2880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF4684ac.TMP | — | |
MD5:— | SHA256:— | |||
| 2880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\metadata\LOG.old | text | |
MD5:8268A4D53A6A9432A8266584CBD7D624 | SHA256:F785C42945CFE320C52C763837CD41541A8CAAB3E5FD567999EED5343CF0FD7A | |||
| 2880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:E91E138A25FD7E5BCA5E60111F39C91A | SHA256:B1F7E3537A31A4B847F862858E5D2581993CC9372F19ABF19EA2A9185FE42A4F | |||
| 2880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:9F941EA08DBDCA2EB3CFA1DBBBA6F5DC | SHA256:127F71DF0D2AD895D4F293E62284D85971AE047CA15F90B87BF6335898B0B655 | |||
| 2880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\d4e9c701-ab92-4ed3-b494-b086d95f4f53.tmp | binary | |
MD5:5058F1AF8388633F609CADB75A75DC9D | SHA256:— | |||
| 2880 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\shared_proto_db\metadata\LOG.old~RF467402.TMP | text | |
MD5:7C1C23F006788D107F8A01B852CC6701 | SHA256:9FA4E627077EDCBEC8AAA1ED2DD5538E630790893F88F02F1E9CC863E6A27848 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
54
DNS requests
34
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
860 | svchost.exe | HEAD | — | 209.197.3.8:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/ec243c2e-e29f-46d6-92ef-c60f8cfa76e0?P1=1692046558&P2=404&P3=2&P4=XGMGGgwZivtdSkKoNDtiovgjyTGrBS9ffdZsuwgp0iKAWFVyirkWbHj2wztvVWjKxvXi3Lz80moYhZ8WDm4C%2fA%3d%3d | US | — | — | whitelisted |
860 | svchost.exe | HEAD | — | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | US | — | — | whitelisted |
3384 | chrome.exe | GET | 404 | 3.33.152.147:80 | http://dasmalwerk.eu/favicon.ico | US | html | 125 b | whitelisted |
5916 | a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe | GET | 200 | 34.160.111.145:80 | http://myexternalip.com/raw | US | text | 12 b | shared |
860 | svchost.exe | GET | 206 | 209.197.3.8:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/ec243c2e-e29f-46d6-92ef-c60f8cfa76e0?P1=1692046558&P2=404&P3=2&P4=XGMGGgwZivtdSkKoNDtiovgjyTGrBS9ffdZsuwgp0iKAWFVyirkWbHj2wztvVWjKxvXi3Lz80moYhZ8WDm4C%2fA%3d%3d | US | binary | 732 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/j2hxfei2occ5siitujtlwgp6xi_3/ojhpjlocmbogdgmfpkhlaaeamibhnphh_3_all_gplutbkdljxxbjolk3siq7kive.crx3 | US | binary | 1.10 Mb | whitelisted |
860 | svchost.exe | GET | 206 | 209.197.3.8:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/ec243c2e-e29f-46d6-92ef-c60f8cfa76e0?P1=1692046558&P2=404&P3=2&P4=XGMGGgwZivtdSkKoNDtiovgjyTGrBS9ffdZsuwgp0iKAWFVyirkWbHj2wztvVWjKxvXi3Lz80moYhZ8WDm4C%2fA%3d%3d | US | binary | 44.8 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 209.197.3.8:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/ec243c2e-e29f-46d6-92ef-c60f8cfa76e0?P1=1692046558&P2=404&P3=2&P4=XGMGGgwZivtdSkKoNDtiovgjyTGrBS9ffdZsuwgp0iKAWFVyirkWbHj2wztvVWjKxvXi3Lz80moYhZ8WDm4C%2fA%3d%3d | US | binary | 10.1 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 209.197.3.8:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/ec243c2e-e29f-46d6-92ef-c60f8cfa76e0?P1=1692046558&P2=404&P3=2&P4=XGMGGgwZivtdSkKoNDtiovgjyTGrBS9ffdZsuwgp0iKAWFVyirkWbHj2wztvVWjKxvXi3Lz80moYhZ8WDm4C%2fA%3d%3d | US | binary | 21.6 Kb | whitelisted |
860 | svchost.exe | GET | 206 | 209.197.3.8:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/ec243c2e-e29f-46d6-92ef-c60f8cfa76e0?P1=1692046558&P2=404&P3=2&P4=XGMGGgwZivtdSkKoNDtiovgjyTGrBS9ffdZsuwgp0iKAWFVyirkWbHj2wztvVWjKxvXi3Lz80moYhZ8WDm4C%2fA%3d%3d | US | binary | 10.2 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3384 | chrome.exe | 54.228.42.199:443 | das-malwerk.herokuapp.com | AMAZON-02 | IE | suspicious |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2640 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2880 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
3384 | chrome.exe | 142.250.186.141:443 | accounts.google.com | GOOGLE | US | whitelisted |
3384 | chrome.exe | 3.33.152.147:80 | dasmalwerk.eu | AMAZON-02 | US | malicious |
3384 | chrome.exe | 54.78.134.111:443 | das-malwerk.herokuapp.com | AMAZON-02 | IE | suspicious |
3384 | chrome.exe | 216.58.206.36:443 | www.google.com | GOOGLE | US | whitelisted |
3384 | chrome.exe | 104.18.11.207:443 | maxcdn.bootstrapcdn.com | CLOUDFLARENET | — | suspicious |
3384 | chrome.exe | 69.16.175.42:443 | code.jquery.com | STACKPATH-CDN | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dasmalwerk.eu |
| whitelisted |
accounts.google.com |
| shared |
das-malwerk.herokuapp.com |
| unknown |
www.google.com |
| malicious |
maxcdn.bootstrapcdn.com |
| whitelisted |
code.jquery.com |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | A Network Trojan was detected | ET MALWARE User-Agent (Xmaker) |
5916 | a162bb9219a09b302b90bc6f908e117e3fb2c722560336d378fd76a8f22f78f8.exe | Device Retrieving External IP Address Detected | ET POLICY External IP Check myexternalip.com |
1 ETPRO signatures available at the full report