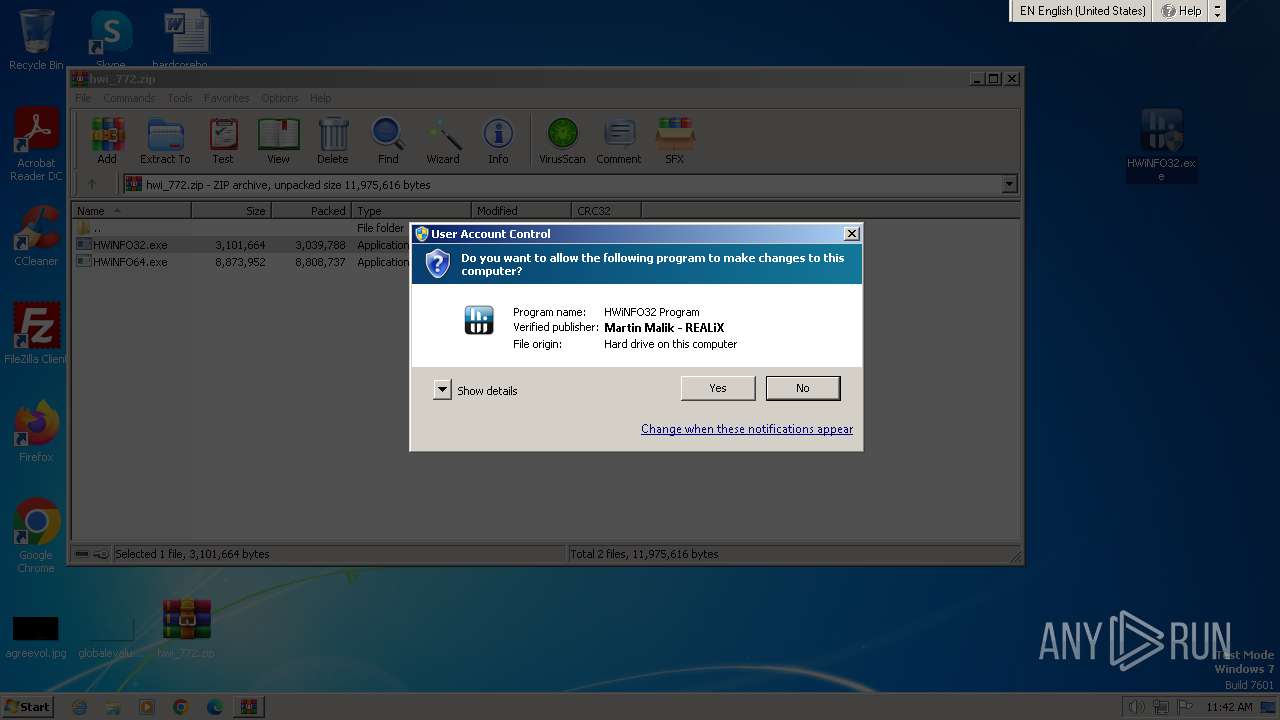
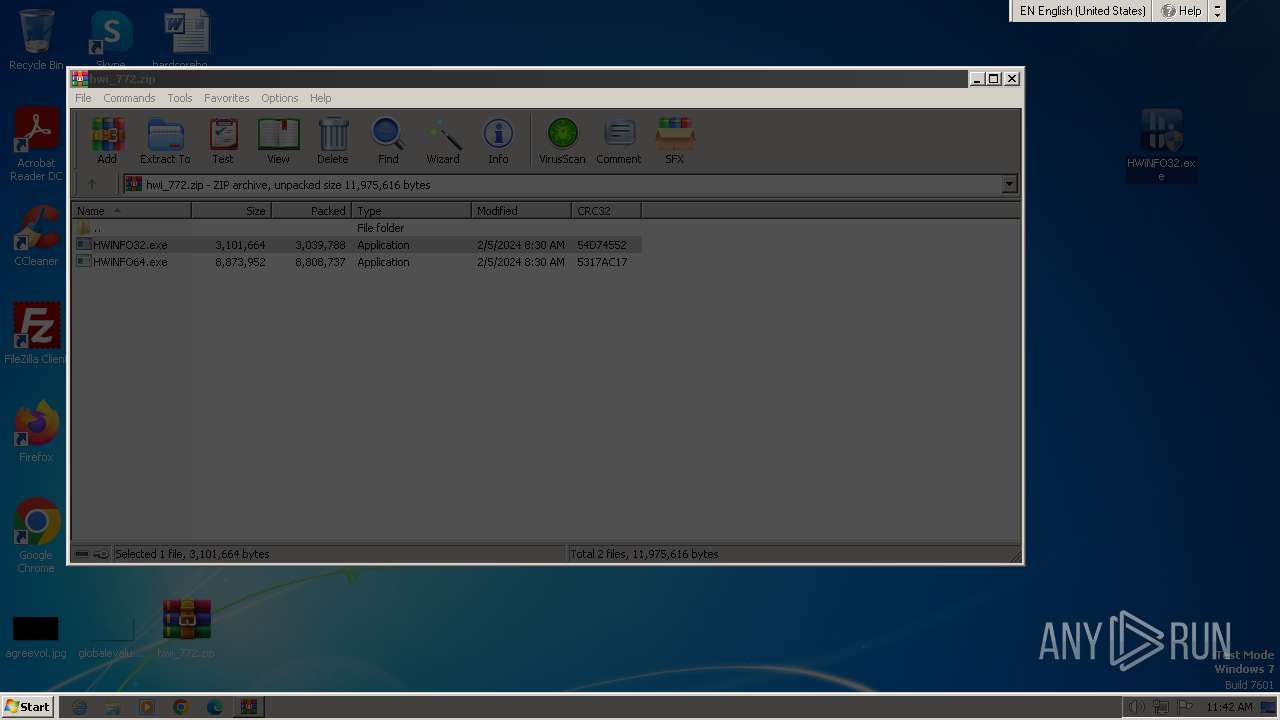
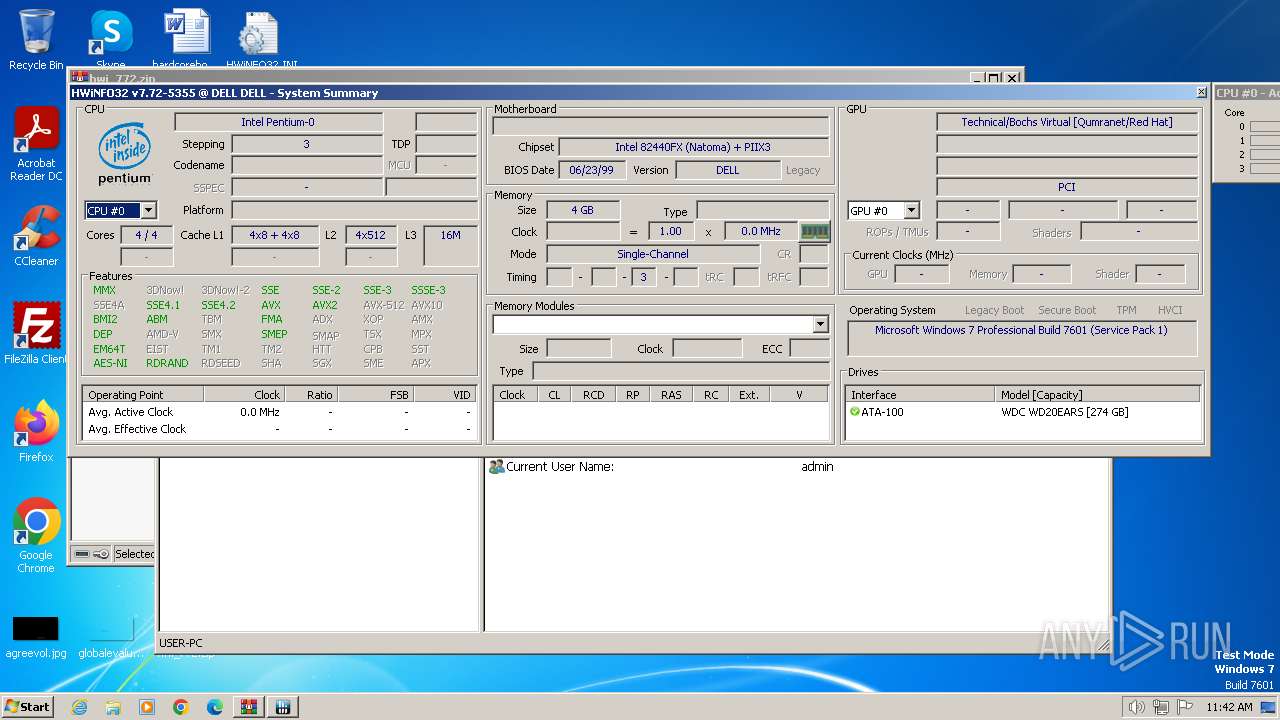
| File name: | hwi_772.zip |
| Full analysis: | https://app.any.run/tasks/0e0a2d33-6ebe-4f2d-aeb7-476a3917981e |
| Verdict: | Malicious activity |
| Analysis date: | March 08, 2024, 11:42:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | DA51113A7BE83E97B601D359D74F7B79 |
| SHA1: | 35BDCFEFBB3FBFBCCA362228C65CB258C32845A6 |
| SHA256: | 5DB2364E372FA2B9A1D81A66A9FB4B4298F74915EDA7EEA7F9BB0F6F8E1DE6CD |
| SSDEEP: | 98304:l/ktAAvgIKJKRZMPeYc4ASeg0y+tbDNDXV5yA3Zq3JcXcwiv8OGj5pI980zWJ4q4:iXPOmOJ/Hjq9tf3Ka/aQGXpi4/ |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3972)
- HWiNFO32.exe (PID: 116)
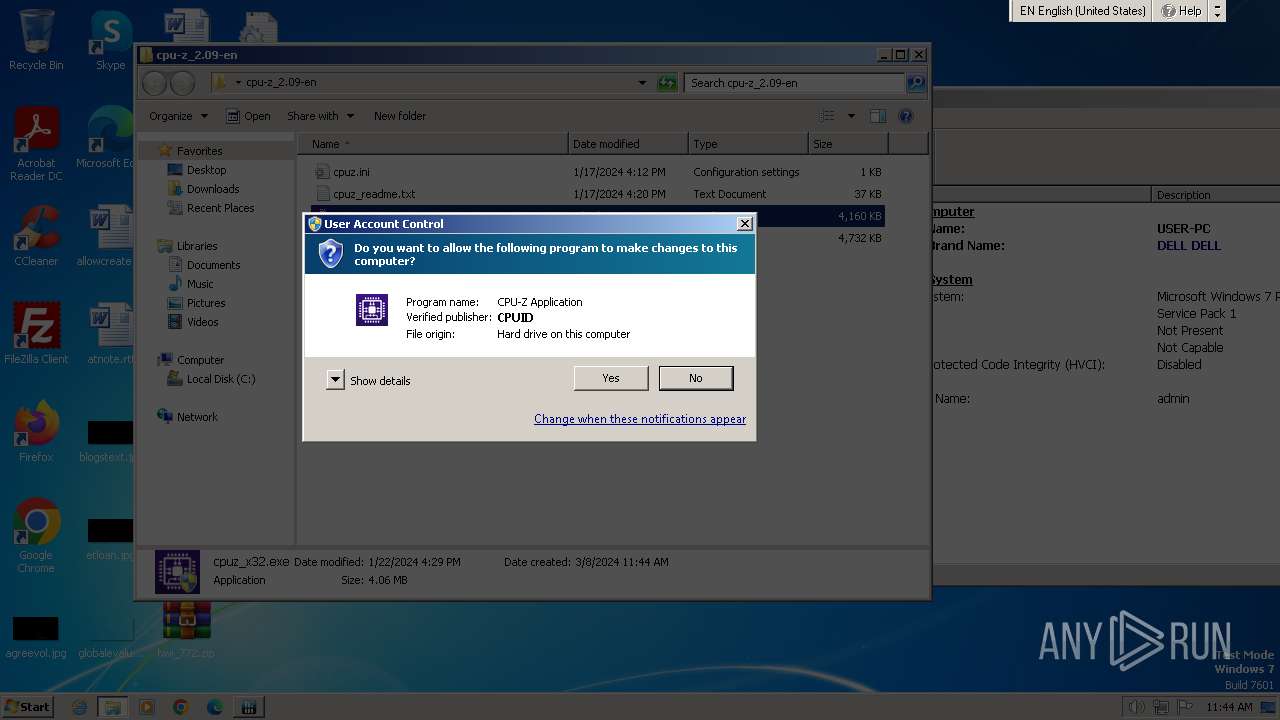
- cpuz_x32.exe (PID: 1020)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- HWiNFO32.exe (PID: 116)
- cpuz_x32.exe (PID: 1020)
Executable content was dropped or overwritten
- HWiNFO32.exe (PID: 116)
- cpuz_x32.exe (PID: 1020)
Reads settings of System Certificates
- HWiNFO32.exe (PID: 116)
- cpuz_x32.exe (PID: 1020)
Reads security settings of Internet Explorer
- HWiNFO32.exe (PID: 116)
- cpuz_x32.exe (PID: 1020)
Checks Windows Trust Settings
- HWiNFO32.exe (PID: 116)
- cpuz_x32.exe (PID: 1020)
Reads the BIOS version
- HWiNFO32.exe (PID: 116)
Reads the Internet Settings
- HWiNFO32.exe (PID: 116)
- cpuz_x32.exe (PID: 1020)
Adds/modifies Windows certificates
- cpuz_x32.exe (PID: 1020)
INFO
Reads the computer name
- HWiNFO32.exe (PID: 116)
- cpuz_x32.exe (PID: 1020)
- wmpnscfg.exe (PID: 392)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3972)
- WinRAR.exe (PID: 3984)
Checks supported languages
- HWiNFO32.exe (PID: 116)
- cpuz_x32.exe (PID: 1020)
- wmpnscfg.exe (PID: 392)
Create files in a temporary directory
- HWiNFO32.exe (PID: 116)
Manual execution by a user
- HWiNFO32.exe (PID: 116)
- WinRAR.exe (PID: 3984)
- cpuz_x32.exe (PID: 1020)
- wmpnscfg.exe (PID: 392)
- cpuz_x32.exe (PID: 1484)
Reads the software policy settings
- HWiNFO32.exe (PID: 116)
- cpuz_x32.exe (PID: 1020)
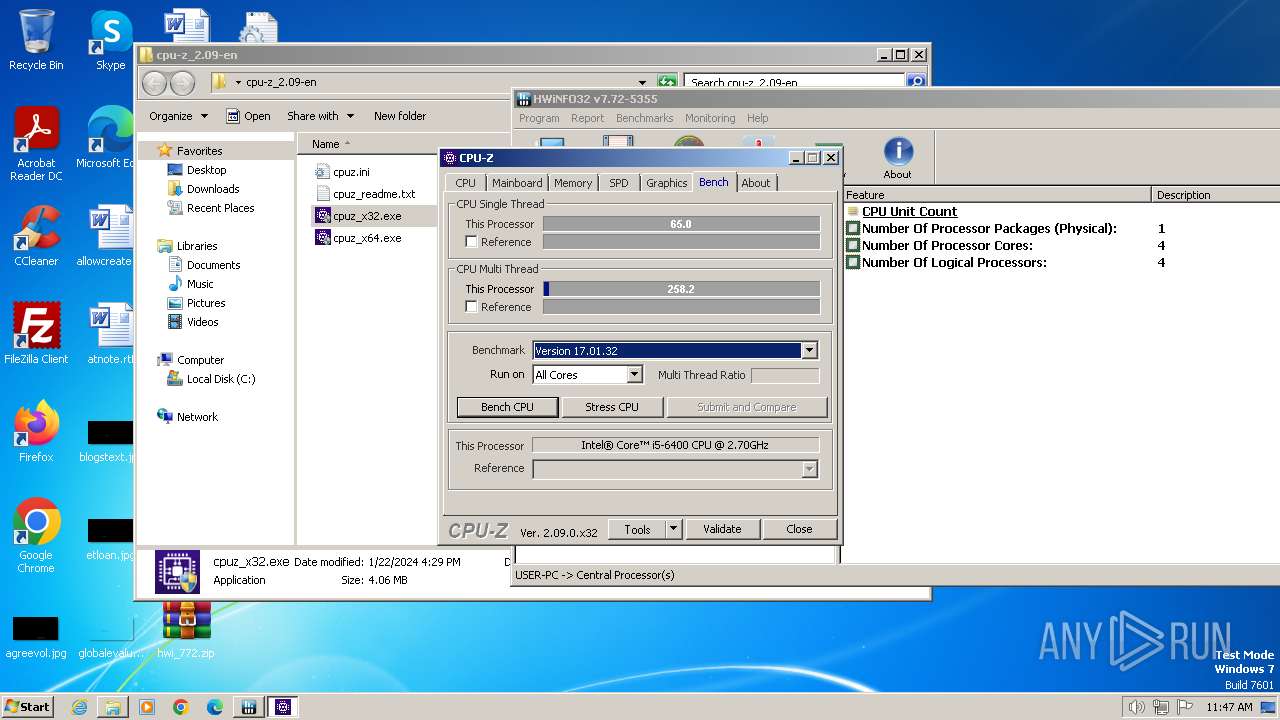
Reads CPU info
- HWiNFO32.exe (PID: 116)
Reads the machine GUID from the registry
- HWiNFO32.exe (PID: 116)
- cpuz_x32.exe (PID: 1020)
Checks proxy server information
- HWiNFO32.exe (PID: 116)
- cpuz_x32.exe (PID: 1020)
Creates files or folders in the user directory
- HWiNFO32.exe (PID: 116)
- cpuz_x32.exe (PID: 1020)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3984)
Reads Environment values
- cpuz_x32.exe (PID: 1020)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:02:05 09:30:34 |
| ZipCRC: | 0x54d74552 |
| ZipCompressedSize: | 3039788 |
| ZipUncompressedSize: | 3101664 |
| ZipFileName: | HWiNFO32.exe |
Total processes
57
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Users\admin\Desktop\HWiNFO32.exe" | C:\Users\admin\Desktop\HWiNFO32.exe | explorer.exe | ||||||||||||
User: admin Company: REALiX s.r.o. Integrity Level: HIGH Description: HWiNFO32 Exit code: 0 Version: 7.72-5355 Modules
| |||||||||||||||
| 392 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1020 | "C:\Users\admin\Desktop\cpu-z_2.09-en\cpuz_x32.exe" | C:\Users\admin\Desktop\cpu-z_2.09-en\cpuz_x32.exe | explorer.exe | ||||||||||||
User: admin Company: CPUID Integrity Level: HIGH Description: CPU-Z Application Exit code: 0 Version: 2, 0, 9, 0 Modules
| |||||||||||||||
| 1484 | "C:\Users\admin\Desktop\cpu-z_2.09-en\cpuz_x32.exe" | C:\Users\admin\Desktop\cpu-z_2.09-en\cpuz_x32.exe | — | explorer.exe | |||||||||||
User: admin Company: CPUID Integrity Level: MEDIUM Description: CPU-Z Application Exit code: 3221226540 Version: 2, 0, 9, 0 Modules
| |||||||||||||||
| 3972 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\hwi_772.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3984 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\cpu-z_2.09-en.zip" C:\Users\admin\Desktop\cpu-z_2.09-en\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
14 031
Read events
13 870
Write events
137
Delete events
24
Modification events
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\hwi_772.zip | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3972) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
5
Suspicious files
6
Text files
6
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 116 | HWiNFO32.exe | C:\Users\admin\Desktop\HWiNFO32.INI | text | |
MD5:31EA0D720B02F5BE9A0A8C843FA525B6 | SHA256:2B52116A161DB87EAD7FBA5329E113610A39EC5183D713A9D9A7222FE657C949 | |||
| 116 | HWiNFO32.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_F2DAF19C1F776537105D08FC8D978464 | binary | |
MD5:8202A1CD02E7D69597995CABBE881A12 | SHA256:58F381C3A0A0ACE6321DA22E40BD44A597BD98B9C9390AB9258426B5CF75A7A5 | |||
| 1020 | cpuz_x32.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:BED797C0F9066C5B4FBE7A26526A5DDB | SHA256:98CC963CE614A2A60A92D7538CA9A1A72F49A2C7D33D1120E256B6326B800476 | |||
| 1020 | cpuz_x32.exe | C:\Windows\temp\cpuz_driver_1020.log | text | |
MD5:5331A892B196C460F69966D30B4B56E1 | SHA256:C88717244A7B9CAD9BF4DF03B38337527AC4B4B84F048100382FCBC1FDF8FC3F | |||
| 3984 | WinRAR.exe | C:\Users\admin\Desktop\cpu-z_2.09-en\cpuz_x32.exe | executable | |
MD5:F3BF8D3AB2F151D28E3A63AC9E6E4DEE | SHA256:AF0918DB9AA303C6522FBF8423EB006E229E6BE516AA03875964702711922BBE | |||
| 3984 | WinRAR.exe | C:\Users\admin\Desktop\cpu-z_2.09-en\cpuz_readme.txt | text | |
MD5:4822336A7C15F6548D9ADF08F87EABD7 | SHA256:333939BD029A3325E4377FC6F33C57BD43647356B84D479732A493F5C1EAA8BF | |||
| 1020 | cpuz_x32.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | der | |
MD5:822467B728B7A66B081C91795373789A | SHA256:AF2343382B88335EEA72251AD84949E244FF54B6995063E24459A7216E9576B9 | |||
| 116 | HWiNFO32.exe | C:\Users\admin\AppData\Local\Temp\HWiNFO32_191.SYS | executable | |
MD5:6B8909A66EDD2AB656D15B625BA6F6DE | SHA256:FC98ADFA2B94D5ABCF11655807E7FDCA1028C7142C97B7C3B5435E0421FEBFAE | |||
| 116 | HWiNFO32.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:352649F70048A56EB54D4F4C082B7B38 | SHA256:862FE2EE2984C826D4EBCA4BAF6B57EF1CB637F05E2962FECF0C447A93B2A66F | |||
| 116 | HWiNFO32.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:B05BC8B50BA895B9A4E252213CE4D29F | SHA256:9B397A2D279B08835B5A8B723D8B722BF25F509C780FFD9C1764CAC702B7EA2F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
11
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
116 | HWiNFO32.exe | GET | 304 | 23.53.42.59:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?53c50ebd11a047c3 | unknown | — | — | unknown |
116 | HWiNFO32.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | binary | 1.41 Kb | unknown |
116 | HWiNFO32.exe | GET | 200 | 142.250.185.195:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFCjJ1PwkYAi7fE%3D | unknown | binary | 724 b | unknown |
1080 | svchost.exe | GET | 200 | 23.53.41.243:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?89bca2e7018c82c0 | unknown | compressed | 67.5 Kb | unknown |
1020 | cpuz_x32.exe | GET | 200 | 195.138.255.18:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgQy%2BbCaB9oPhwT%2BuDTXjawRlg%3D%3D | unknown | binary | 503 b | unknown |
1020 | cpuz_x32.exe | GET | 200 | 2.19.217.103:80 | http://x1.c.lencr.org/ | unknown | binary | 717 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
116 | HWiNFO32.exe | 172.67.205.235:443 | www.hwinfo.com | CLOUDFLARENET | US | unknown |
116 | HWiNFO32.exe | 23.53.42.59:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
116 | HWiNFO32.exe | 142.250.185.195:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
1080 | svchost.exe | 23.53.41.243:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1020 | cpuz_x32.exe | 195.154.81.43:443 | download.cpuid.com | Online S.a.s. | FR | unknown |
1020 | cpuz_x32.exe | 2.19.217.103:80 | x1.c.lencr.org | Akamai International B.V. | NL | unknown |
1020 | cpuz_x32.exe | 195.138.255.18:80 | r3.o.lencr.org | AS33891 Netzbetrieb GmbH | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.hwinfo.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
download.cpuid.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |