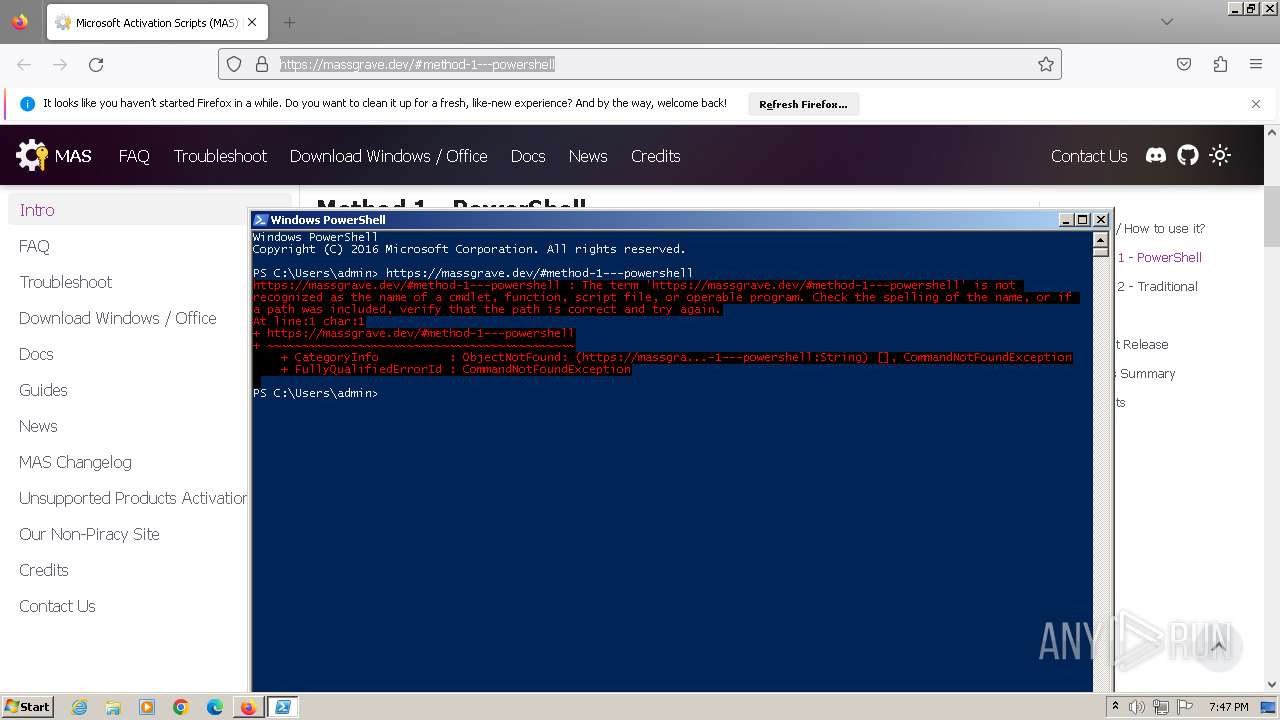
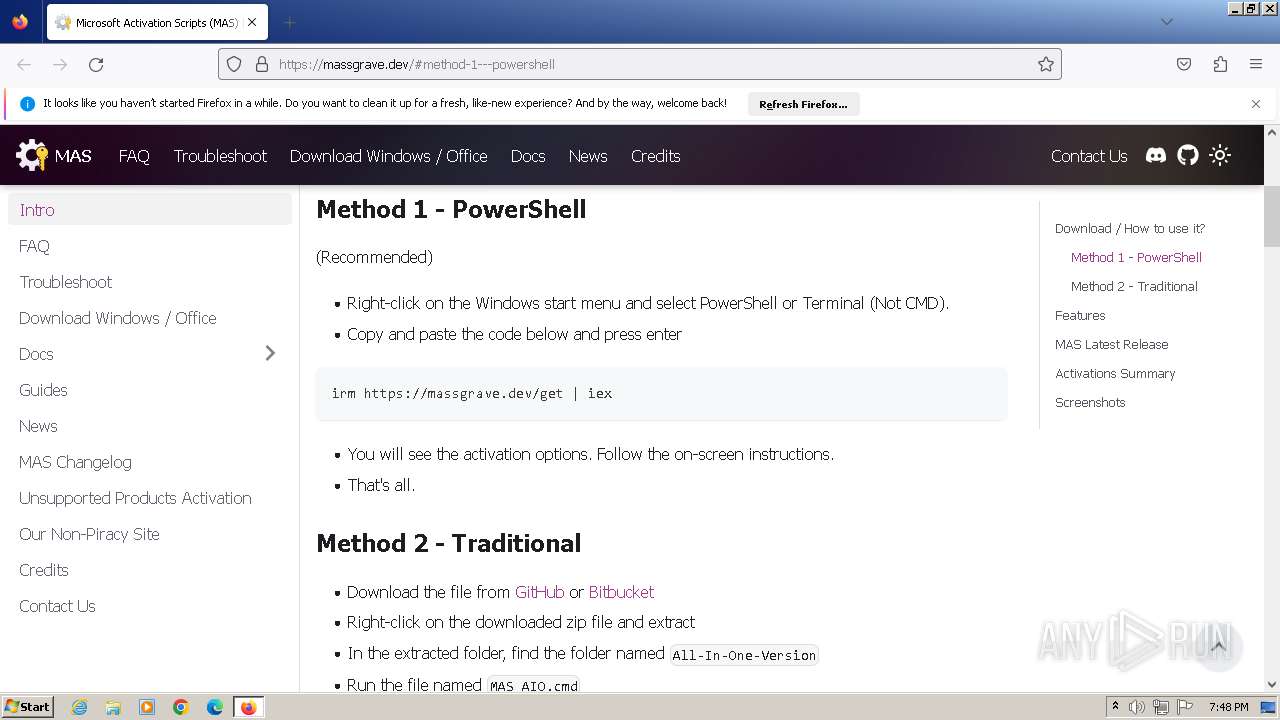
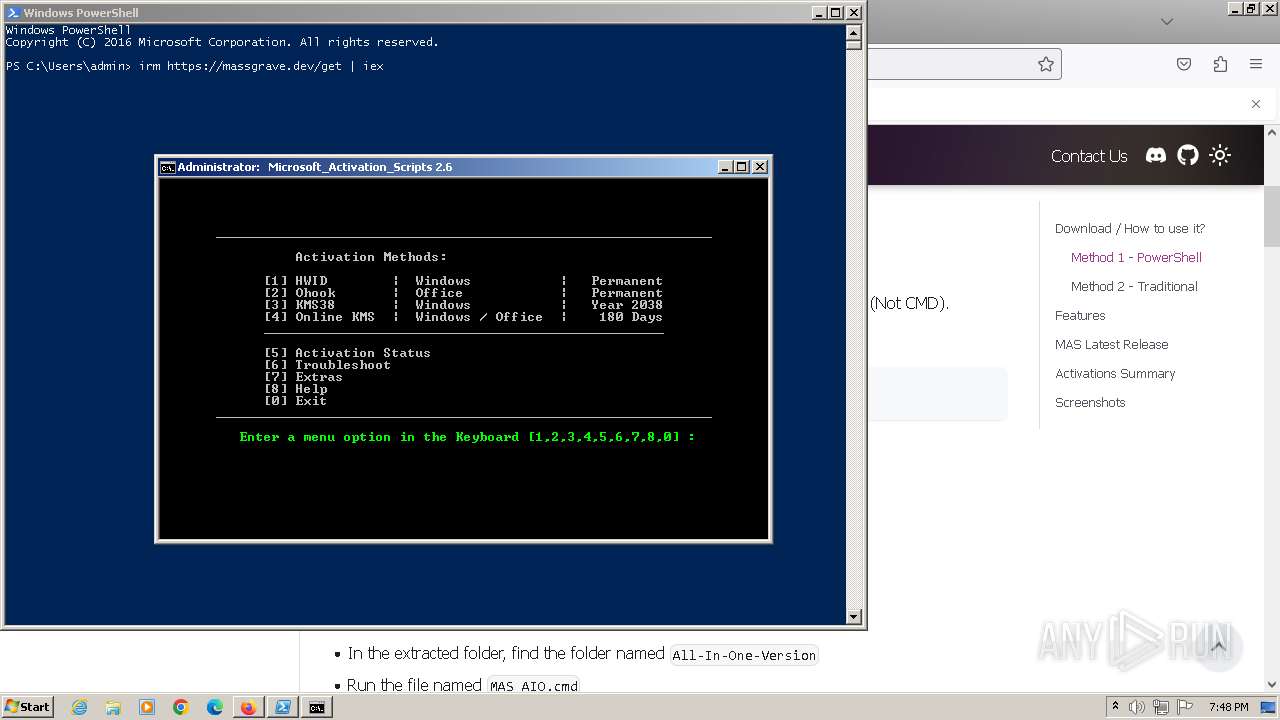
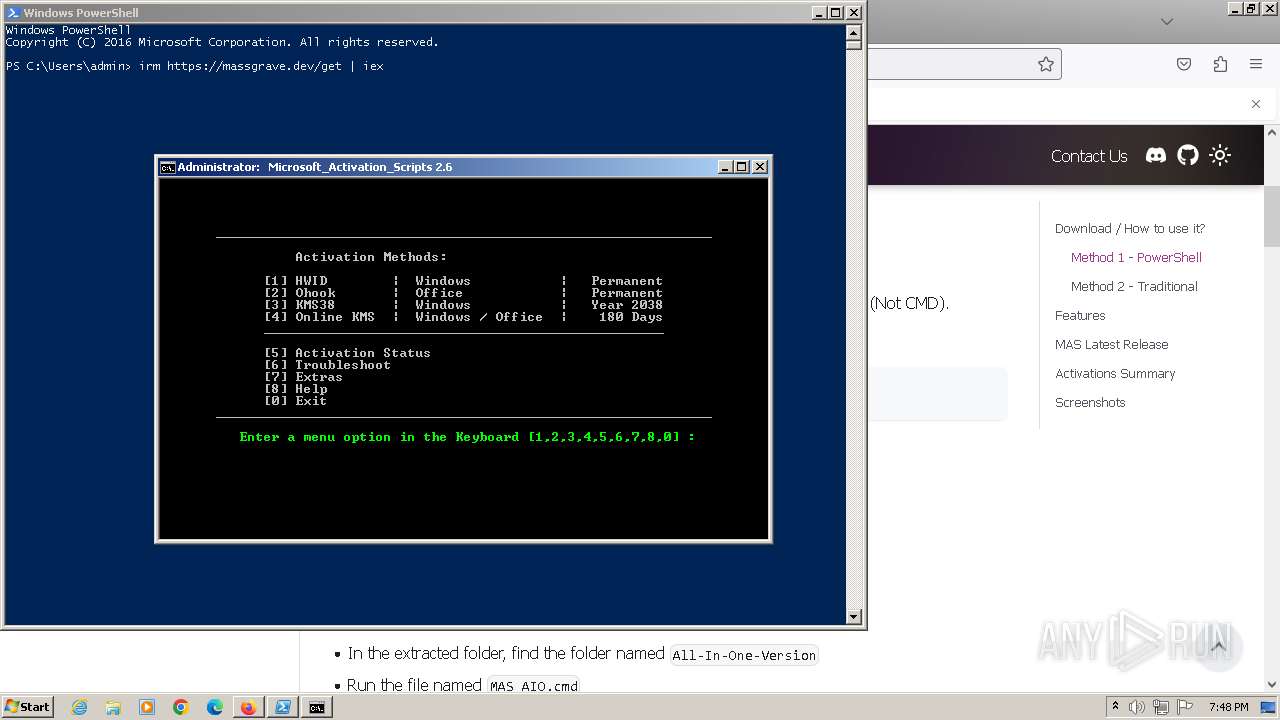
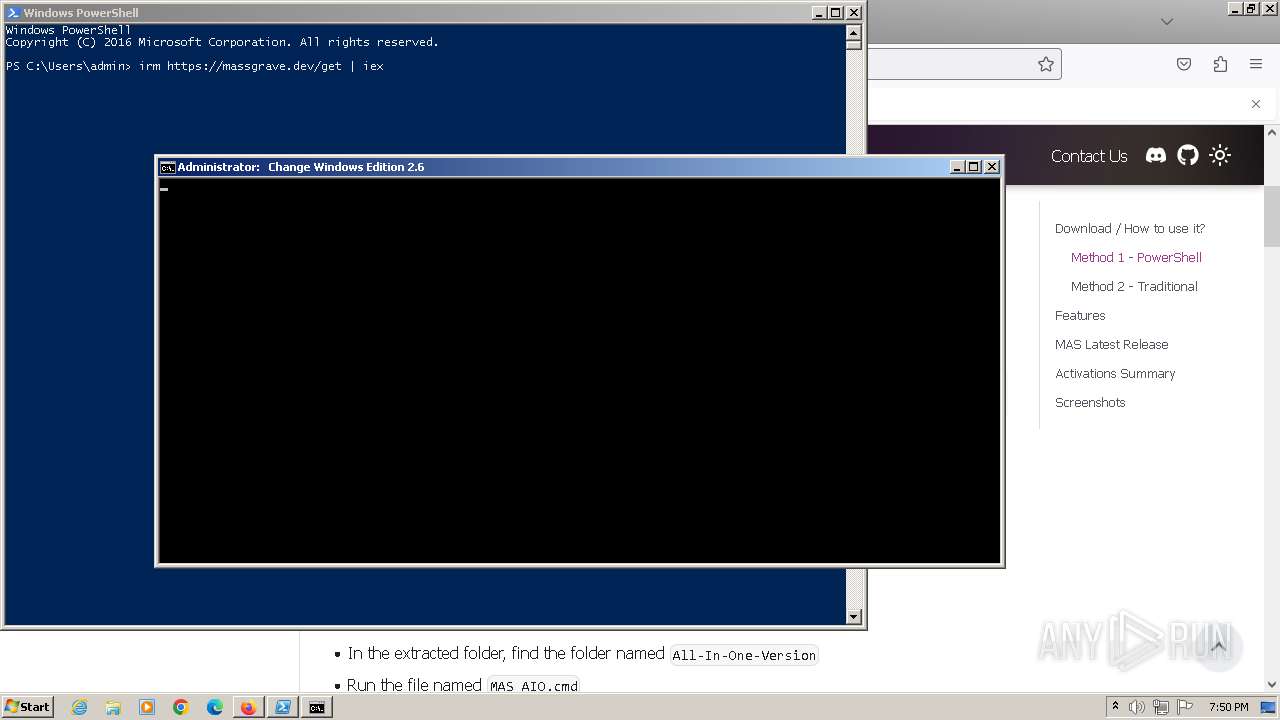
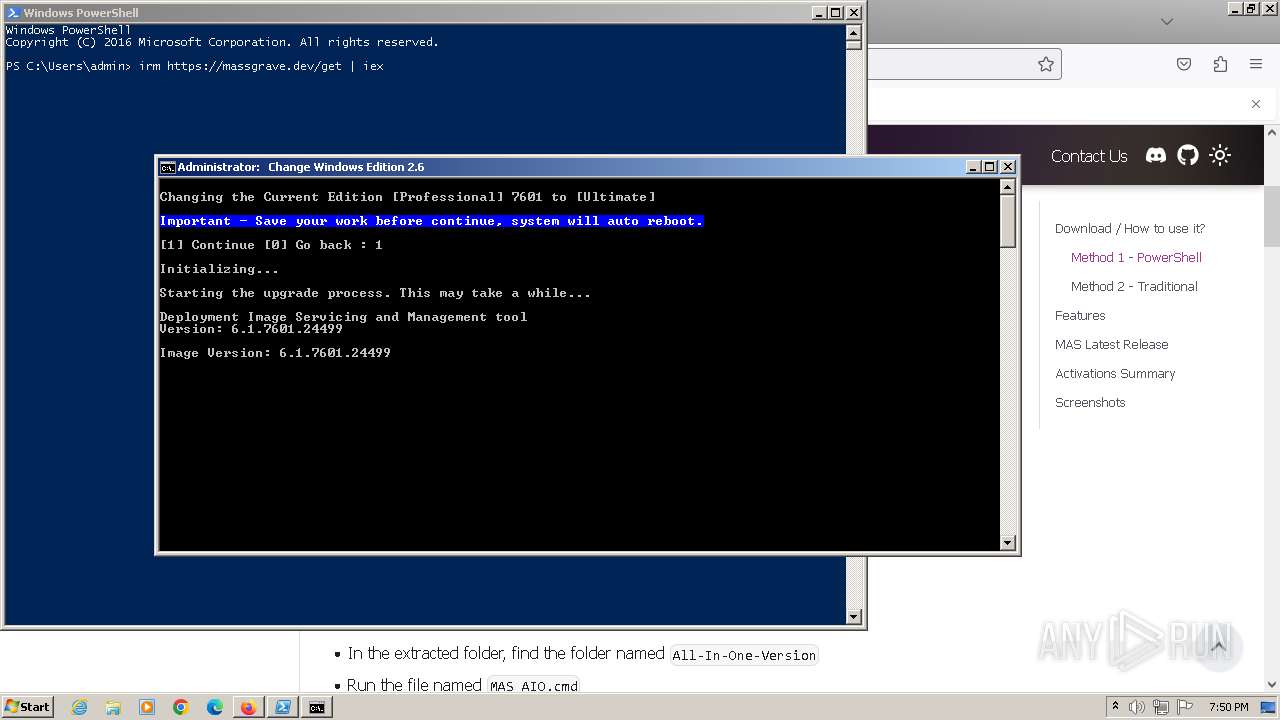
| URL: | https://massgrave.dev/#method-1---powershell |
| Full analysis: | https://app.any.run/tasks/07422a83-ffe2-4552-8658-50f0e80780a1 |
| Verdict: | Malicious activity |
| Analysis date: | May 07, 2024, 18:47:13 |
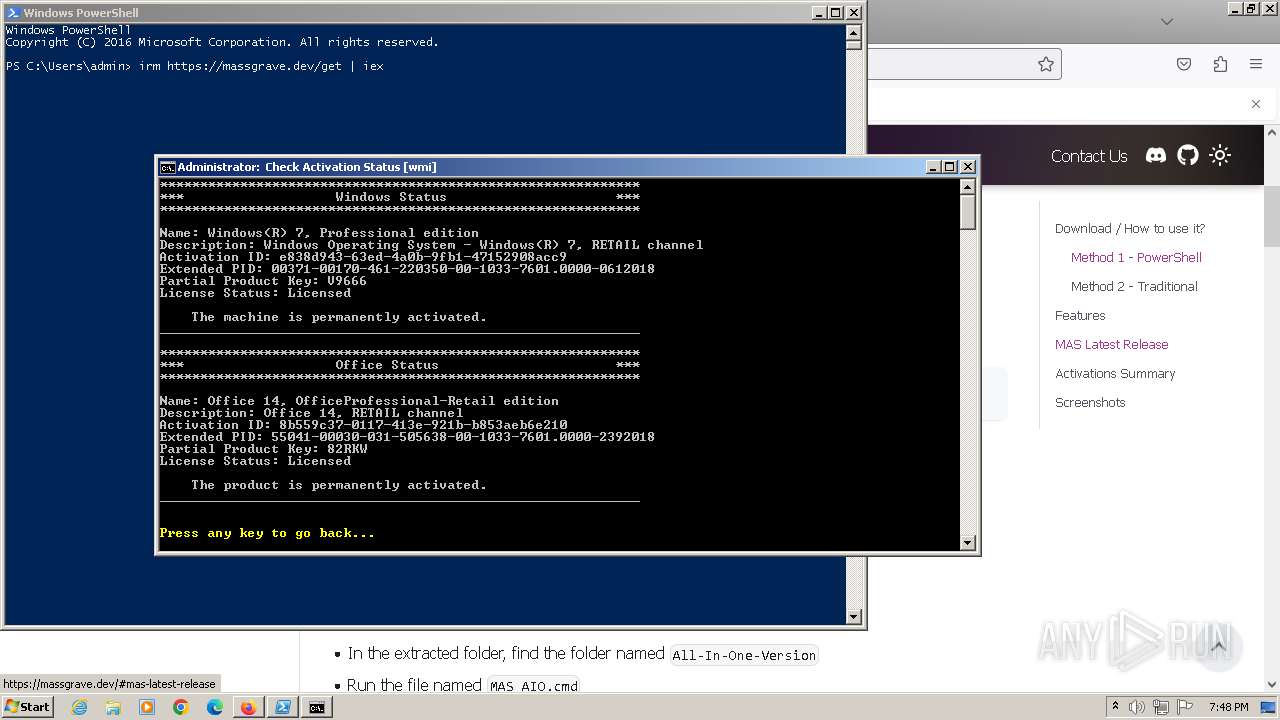
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 21405AA47403190658342834AF40AFC6 |
| SHA1: | 6C4B9539184D12A75AC0807A223C34EB9D11F359 |
| SHA256: | 5DAD82375F383CB3106B57AF1D75BC902EB673B54BAFF7FCE8E492939B3574B8 |
| SSDEEP: | 3:N8a0Kf0apJJJn:2a0oHJ |
MALICIOUS
Starts NET.EXE for service management
- net.exe (PID: 3784)
- cmd.exe (PID: 1568)
- net.exe (PID: 2844)
SUSPICIOUS
Reads the Internet Settings
- powershell.exe (PID: 3256)
- powershell.exe (PID: 3916)
- WMIC.exe (PID: 3524)
- WMIC.exe (PID: 3816)
- WMIC.exe (PID: 3012)
- WMIC.exe (PID: 2868)
- WMIC.exe (PID: 3056)
- WMIC.exe (PID: 3100)
- WMIC.exe (PID: 3756)
- WMIC.exe (PID: 1856)
- WMIC.exe (PID: 664)
- WMIC.exe (PID: 1396)
- WMIC.exe (PID: 3848)
Starts CMD.EXE for commands execution
- powershell.exe (PID: 3256)
- cmd.exe (PID: 3632)
- powershell.exe (PID: 3916)
- cmd.exe (PID: 1568)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 3256)
Executing commands from ".cmd" file
- powershell.exe (PID: 3256)
- cmd.exe (PID: 3632)
- powershell.exe (PID: 3916)
- cmd.exe (PID: 1568)
Starts SC.EXE for service management
- cmd.exe (PID: 3632)
- cmd.exe (PID: 1568)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 3632)
- cmd.exe (PID: 1568)
- cmd.exe (PID: 3080)
- cmd.exe (PID: 2124)
- cmd.exe (PID: 2780)
Application launched itself
- cmd.exe (PID: 3632)
- cmd.exe (PID: 1568)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 3632)
- cmd.exe (PID: 1568)
- cmd.exe (PID: 3296)
- cmd.exe (PID: 3476)
- cmd.exe (PID: 2780)
Unusual connection from system programs
- powershell.exe (PID: 3256)
The Powershell connects to the Internet
- powershell.exe (PID: 3256)
Uses WMIC.EXE to obtain computer system information
- cmd.exe (PID: 1568)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 1568)
- cmd.exe (PID: 3076)
- cmd.exe (PID: 3752)
- cmd.exe (PID: 2124)
- cmd.exe (PID: 3080)
- cmd.exe (PID: 1932)
Hides command output
- cmd.exe (PID: 328)
- cmd.exe (PID: 2788)
- cmd.exe (PID: 2872)
- cmd.exe (PID: 3304)
- cmd.exe (PID: 1932)
- cmd.exe (PID: 3124)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 2788)
Process drops legitimate windows executable
- Dism.exe (PID: 2016)
- Dism.exe (PID: 3320)
- Dism.exe (PID: 2800)
The process creates files with name similar to system file names
- Dism.exe (PID: 2016)
- Dism.exe (PID: 3320)
- Dism.exe (PID: 2800)
Executable content was dropped or overwritten
- Dism.exe (PID: 2016)
- Dism.exe (PID: 3320)
- Dism.exe (PID: 2800)
Starts a Microsoft application from unusual location
- DismHost.exe (PID: 3372)
- DismHost.exe (PID: 3608)
- DismHost.exe (PID: 3700)
Uses base64 encoding (POWERSHELL)
- powershell.exe (PID: 552)
- powershell.exe (PID: 3612)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 2780)
- cmd.exe (PID: 1568)
Gets content of a file (POWERSHELL)
- powershell.exe (PID: 552)
- powershell.exe (PID: 3612)
Executes as Windows Service
- VSSVC.exe (PID: 328)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 2856)
- powershell.exe (PID: 3256)
- powershell.exe (PID: 2800)
Application launched itself
- firefox.exe (PID: 3996)
- firefox.exe (PID: 3980)
Reads the computer name
- wmpnscfg.exe (PID: 2856)
- DismHost.exe (PID: 3372)
- DismHost.exe (PID: 3608)
- DismHost.exe (PID: 3700)
Checks supported languages
- wmpnscfg.exe (PID: 2856)
- mode.com (PID: 3252)
- mode.com (PID: 3072)
- mode.com (PID: 3668)
- mode.com (PID: 3356)
- mode.com (PID: 3696)
- DismHost.exe (PID: 3372)
- mode.com (PID: 3696)
- mode.com (PID: 3044)
- DismHost.exe (PID: 3608)
- DismHost.exe (PID: 3700)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 2800)
Checks current location (POWERSHELL)
- powershell.exe (PID: 2800)
- powershell.exe (PID: 3256)
Checks operating system version
- cmd.exe (PID: 3632)
- cmd.exe (PID: 1568)
Executable content was dropped or overwritten
- firefox.exe (PID: 3996)
Drops the executable file immediately after the start
- firefox.exe (PID: 3996)
- Dism.exe (PID: 2016)
- Dism.exe (PID: 3320)
- Dism.exe (PID: 2800)
Create files in a temporary directory
- Dism.exe (PID: 2016)
- Dism.exe (PID: 3320)
- Dism.exe (PID: 2800)
Reads Environment values
- DismHost.exe (PID: 3372)
Converts byte array into ASCII string (POWERSHELL)
- powershell.exe (PID: 552)
- powershell.exe (PID: 3612)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 552)
- powershell.exe (PID: 3612)
Reads the machine GUID from the registry
- DismHost.exe (PID: 3372)
- DismHost.exe (PID: 3608)
- DismHost.exe (PID: 3700)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
233
Monitored processes
149
Malicious processes
9
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 112 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3996.1.954624971\609688035" -parentBuildID 20230710165010 -prefsHandle 1432 -prefMapHandle 1428 -prefsLen 28600 -prefMapSize 244195 -appDir "C:\Program Files\Mozilla Firefox\browser" - {b78ba75f-5a9f-491c-a361-27cc59bb2d02} 3996 "\\.\pipe\gecko-crash-server-pipe.3996" 1444 1651d390 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 316 | findstr /i /c:"Target Edition : " | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 328 | findstr /a:0A /f:`.txt "." | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 328 | C:\Windows\system32\cmd.exe /c reg query "HKLM\SYSTEM\CurrentControlSet\Control\ProductOptions" /v OSProductPfn 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 328 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 524 | C:\Windows\system32\cmd.exe /c ping -4 -n 1 updatecheck.massgrave.dev | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
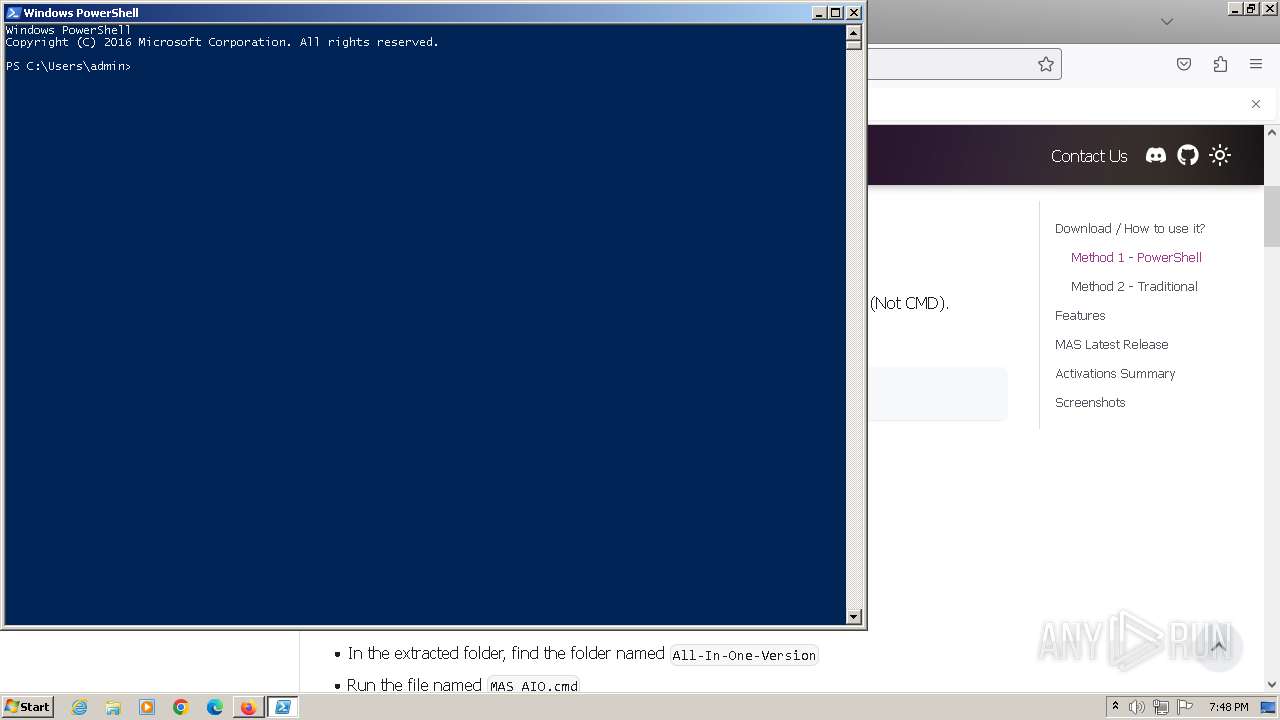
| 552 | powershell.exe "$f=[io.file]::ReadAllText('C:\Users\admin\AppData\Local\Temp\MAS_26169452.cmd') -split ':cbsxml\:.*';& ([ScriptBlock]::Create($f[1])) -GetTargetEditions;" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 588 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="3996.2.1308676865\972166805" -childID 1 -isForBrowser -prefsHandle 2072 -prefMapHandle 2068 -prefsLen 24491 -prefMapSize 244195 -jsInitHandle 888 -jsInitLen 240908 -parentBuildID 20230710165010 -appDir "C:\Program Files\Mozilla Firefox\browser" - {a82456ff-cac6-4f7e-b1aa-d9fca06343a4} 3996 "\\.\pipe\gecko-crash-server-pipe.3996" 2084 1b695e00 tab | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 115.0.2 Modules
| |||||||||||||||
| 664 | wmic path SoftwareLicensingProduct where (ApplicationID='55c92734-d682-4d71-983e-d6ec3f16059f') get ID /VALUE | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 916 | findstr /i ID | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
50 497
Read events
50 171
Write events
321
Delete events
5
Modification events
| (PID) Process: | (3980) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: 7E66E4E200000000 | |||
| (PID) Process: | (3996) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 4928E6E200000000 | |||
| (PID) Process: | (3996) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Installer\308046B0AF4A39CB |
| Operation: | delete value | Name: | installer.taskbarpin.win10.enabled |
Value: | |||
| (PID) Process: | (3996) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 0 | |||
| (PID) Process: | (3996) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (3996) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Theme |
Value: 1 | |||
| (PID) Process: | (3996) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Enabled |
Value: 1 | |||
| (PID) Process: | (3996) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 1 | |||
| (PID) Process: | (3996) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableDefaultBrowserAgent |
Value: 0 | |||
| (PID) Process: | (3996) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|SetDefaultBrowserUserChoice |
Value: 1 | |||
Executable files
97
Suspicious files
202
Text files
42
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3996 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 3996 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\activity-stream.discovery_stream.json | — | |
MD5:— | SHA256:— | |||
| 3996 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 3996 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3996 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cert9.db-journal | binary | |
MD5:FDE7D8E7B8A0EAA19928A5765739BA36 | SHA256:E806B484954C4469A401F7D872475D43F0640BDF13D7949F7AAA99E4AFCDB94C | |||
| 3996 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3996 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3561288849sdhlie.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3996 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 3996 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 3996 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:04BADC0A17F546BBD91CC2404D2776D9 | SHA256:54CD83D3031D15EA1F5B1C5D73416C0B2F9151F93E130DD525DDA488A8EB9110 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
62
DNS requests
124
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3996 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | unknown |
3996 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | unknown |
3996 | firefox.exe | POST | 200 | 95.100.146.66:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
3996 | firefox.exe | POST | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gts1c3 | unknown | — | — | unknown |
3996 | firefox.exe | POST | 200 | 95.100.146.66:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
3996 | firefox.exe | POST | 200 | 95.100.146.66:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
3996 | firefox.exe | POST | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gts1c3 | unknown | — | — | unknown |
3996 | firefox.exe | POST | 200 | 95.100.146.66:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
3996 | firefox.exe | POST | 200 | 95.100.146.66:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
3996 | firefox.exe | POST | 200 | 95.100.146.66:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
3996 | firefox.exe | 104.21.22.3:443 | massgrave.dev | CLOUDFLARENET | — | unknown |
3996 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | GOOGLE | US | whitelisted |
3996 | firefox.exe | 34.117.188.166:443 | contile.services.mozilla.com | GOOGLE-CLOUD-PLATFORM | US | unknown |
3996 | firefox.exe | 34.149.100.209:443 | firefox.settings.services.mozilla.com | GOOGLE | US | unknown |
3996 | firefox.exe | 95.100.146.66:80 | r3.o.lencr.org | Akamai International B.V. | CZ | unknown |
3996 | firefox.exe | 142.250.185.234:443 | safebrowsing.googleapis.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
massgrave.dev |
| unknown |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
spocs.getpocket.com |
| shared |
prod.ads.prod.webservices.mozgcp.net |
| unknown |
r3.o.lencr.org |
| shared |
firefox.settings.services.mozilla.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Dism.exe | PID=2016 Attempting to initialize the logger from the Image Session. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=2016 Initializing a provider store for the LOCAL session type. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=2016 Provider has not previously been encountered. Attempting to initialize the provider. - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=2016 Instantiating the Provider Store. - CDISMImageSession::get_ProviderStore |
Dism.exe | PID=2016 Loading Provider from location C:\Windows\System32\Dism\LogProvider.dll - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=2016 Failed to get an OSServices provider. Must be running in local store. Falling back to checking alongside the log provider for wdscore.dll. - CDISMLogger::FindWdsCore(hr:0x80004005) |
Dism.exe | PID=2016 Getting Provider OSServices - CDISMProviderStore::GetProvider |
Dism.exe | PID=2016 The requested provider was not found in the Provider Store. - CDISMProviderStore::Internal_GetProvider(hr:0x80004005) |
Dism.exe | PID=2016 Connecting to the provider located at C:\Windows\System32\Dism\LogProvider.dll. - CDISMProviderStore::Internal_LoadProvider |
DismHost.exe | PID=3372 Encountered a loaded provider DISMLogger. - CDISMProviderStore::Internal_DisconnectProvider |