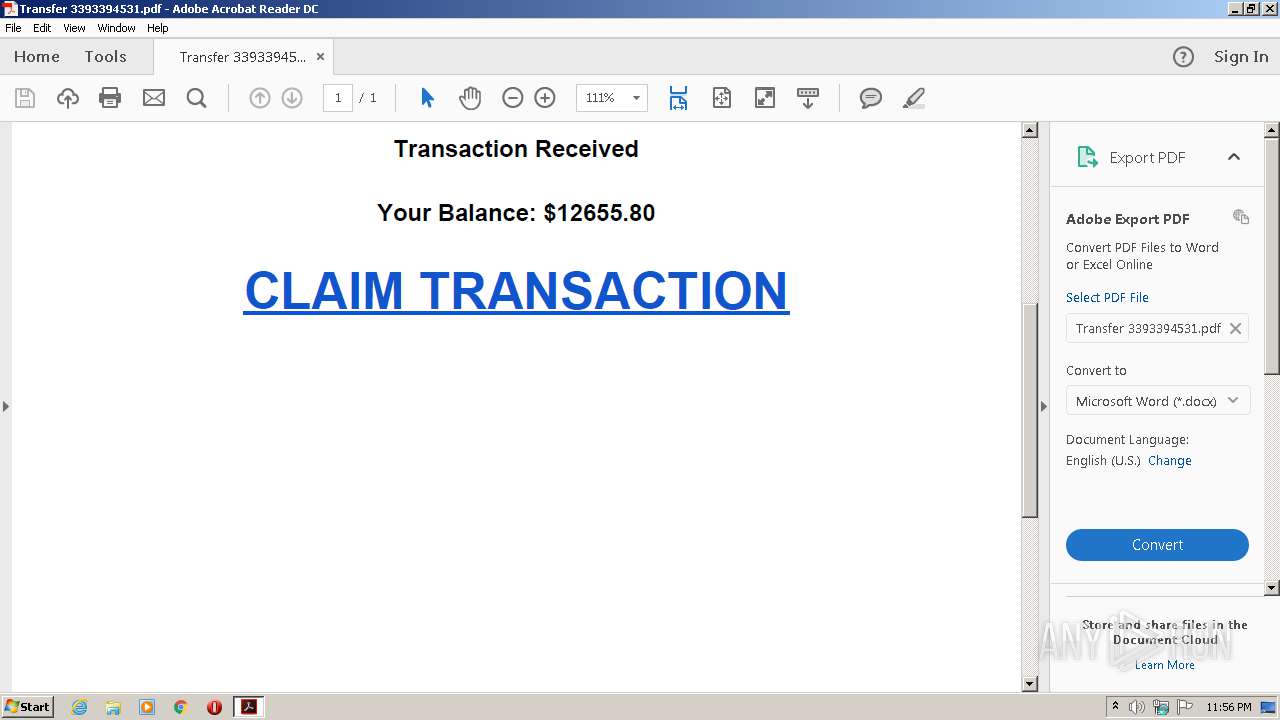
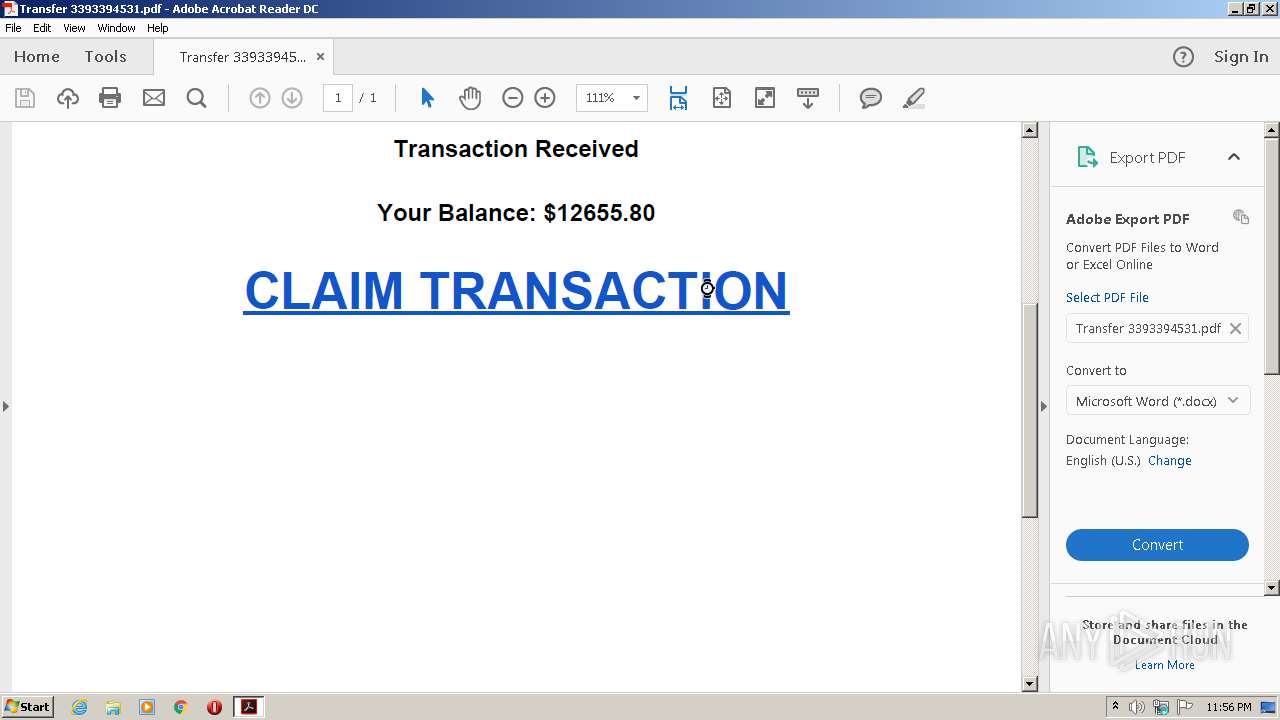
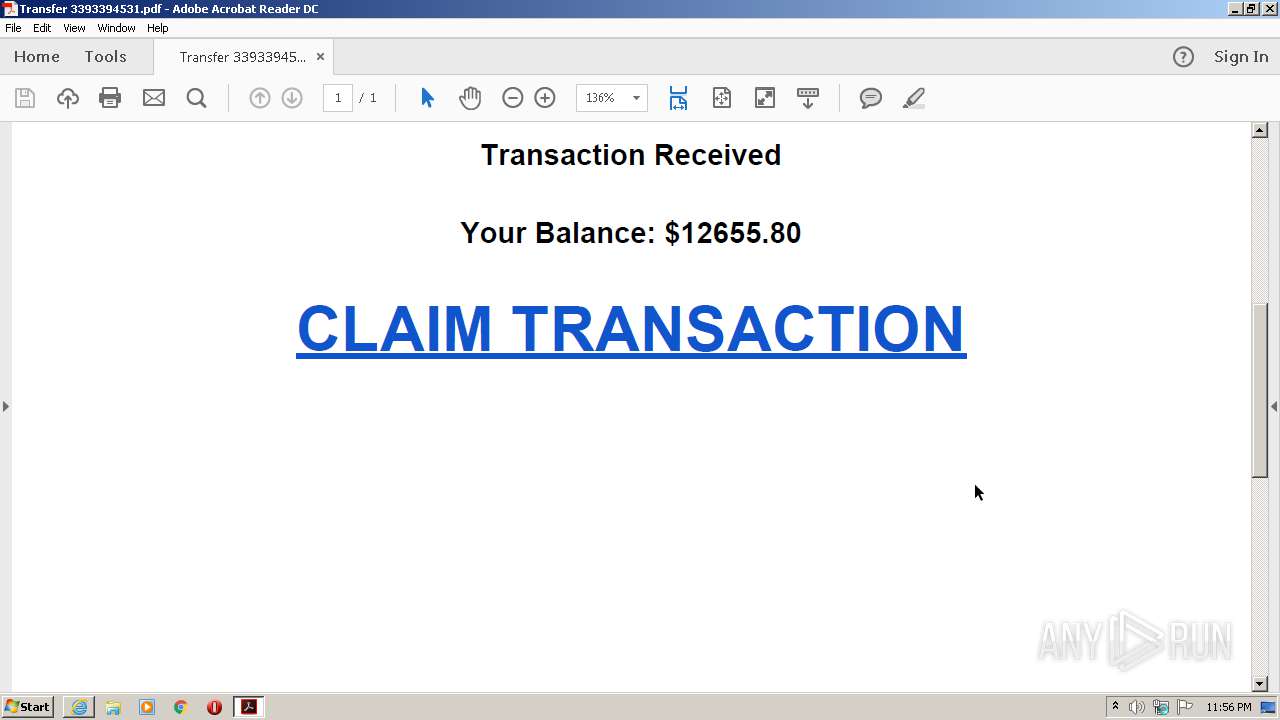
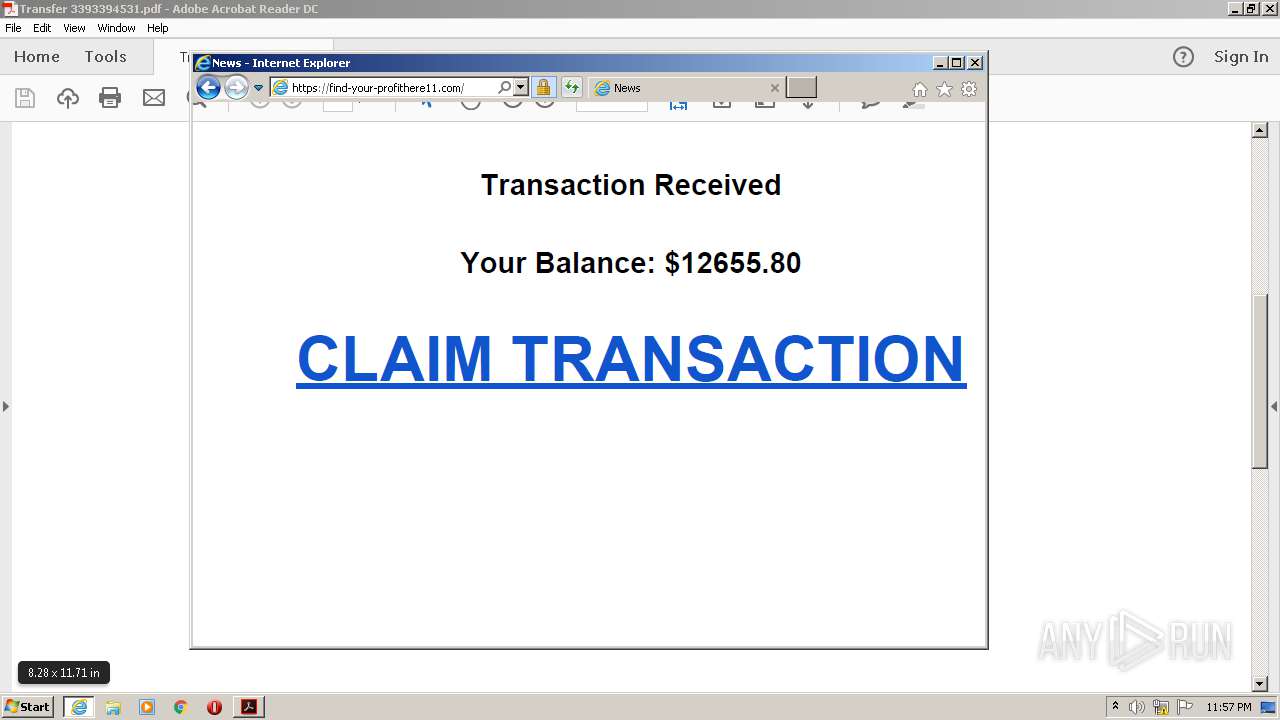
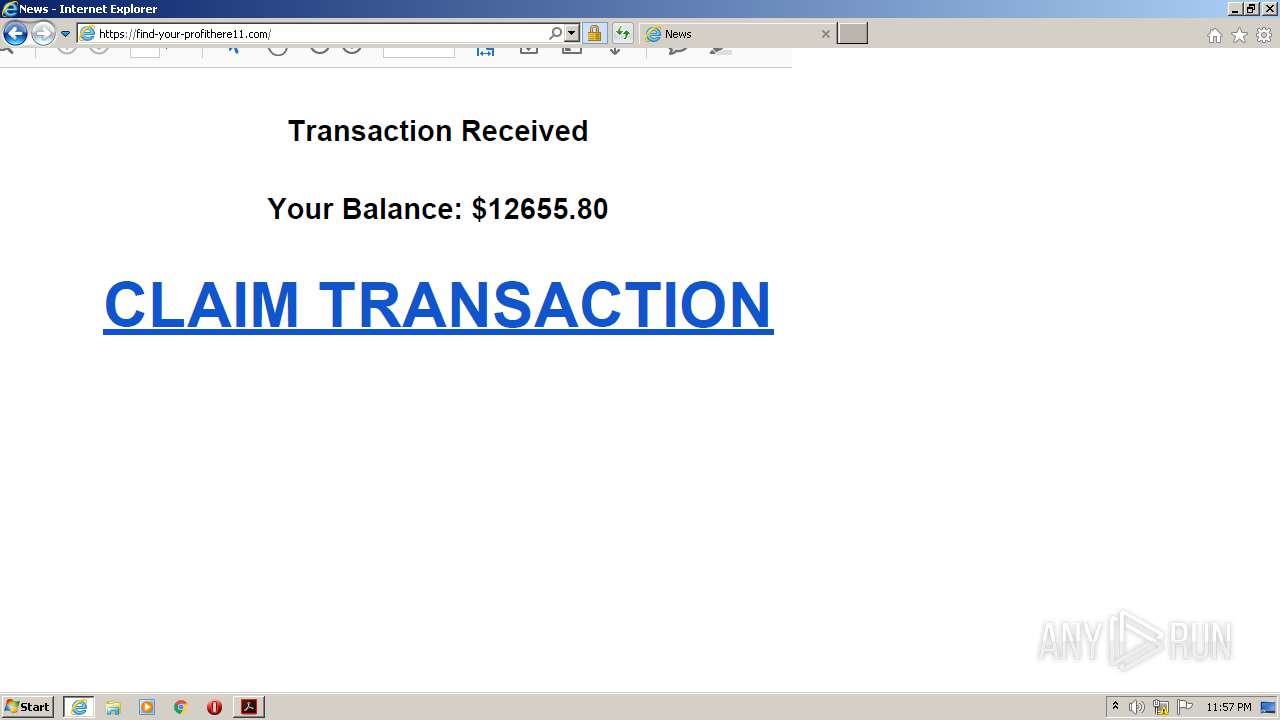
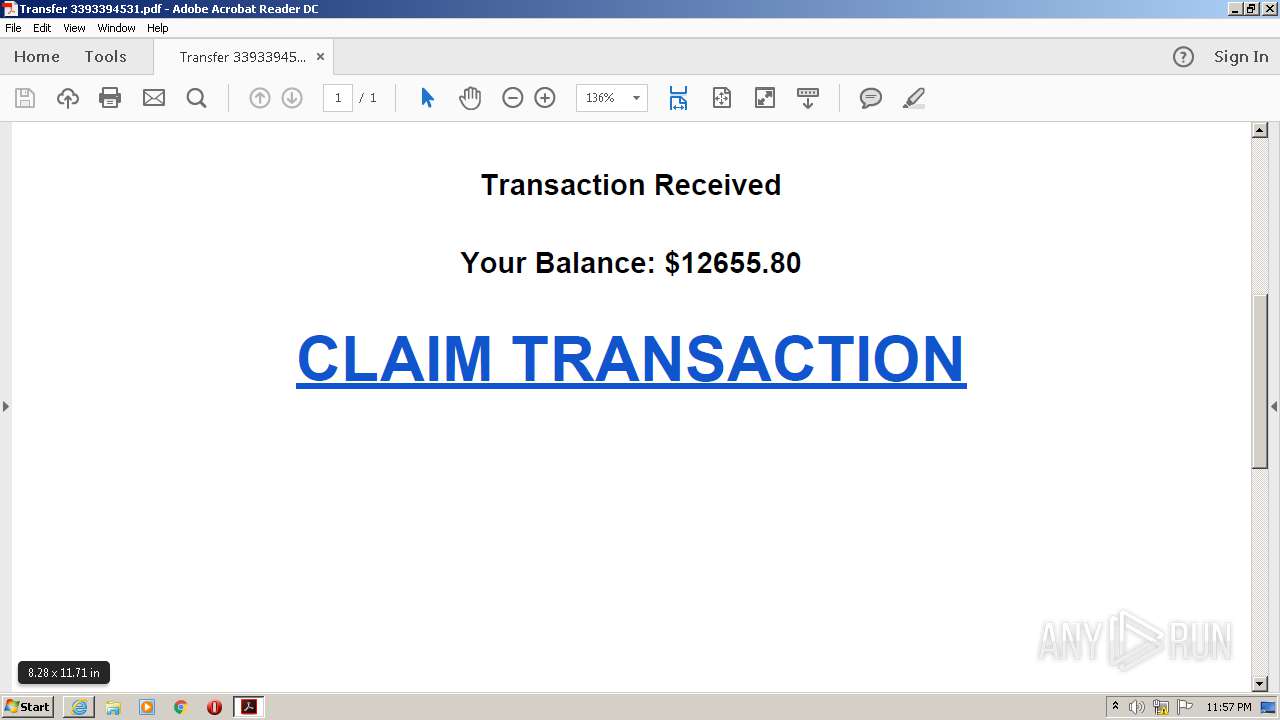
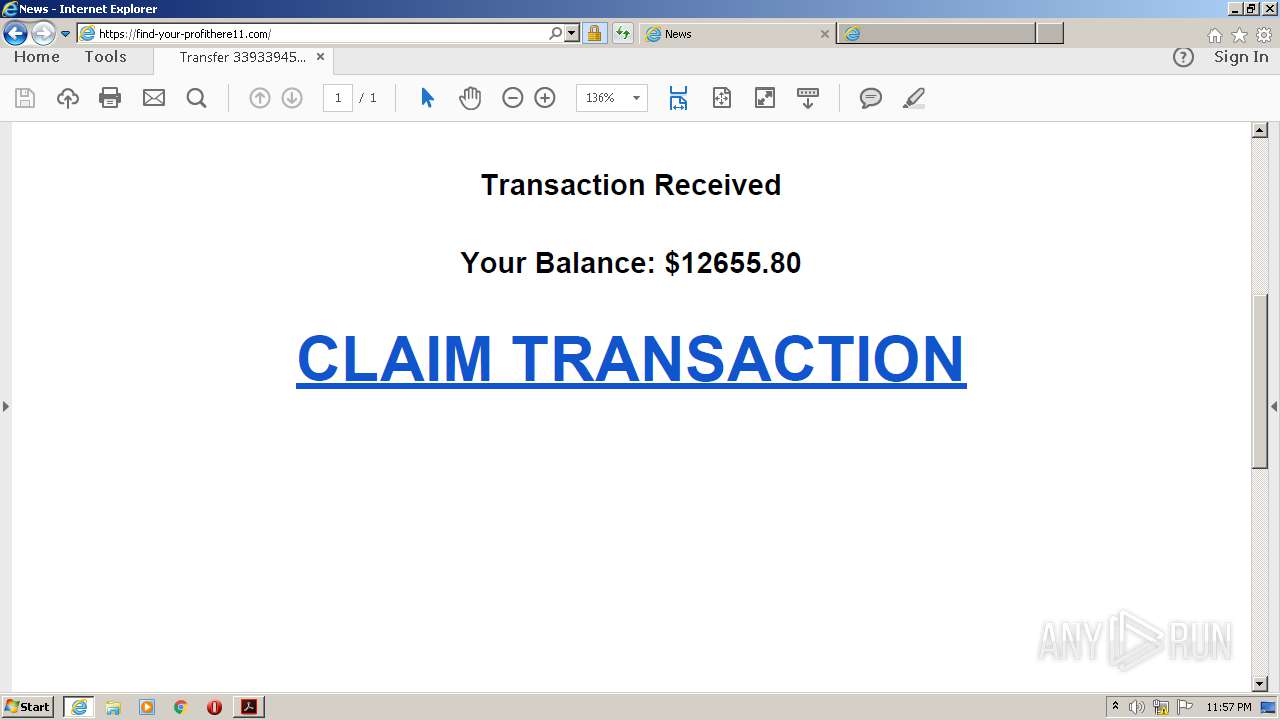
| File name: | Transfer 3393394531.pdf |
| Full analysis: | https://app.any.run/tasks/2fa313e1-d231-4c09-9ca9-3c7346fc0819 |
| Verdict: | Malicious activity |
| Analysis date: | September 29, 2020, 22:55:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/pdf |
| File info: | PDF document, version 1.5 |
| MD5: | 3192160D9181C3E344B0F2E9F9BE8F2A |
| SHA1: | 13C3BA3A10EB48EBAC6452409657D8678578ACA3 |
| SHA256: | 5DA299718E470C869B749890D8C0681F583966D5565495AAA8BAE428C86A1837 |
| SSDEEP: | 1536:cdlwH9Hg1QgEyWgQaoTJshjJPZWYVppJB:Glux9yWgMKJP4YnB |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts Internet Explorer
- AcroRd32.exe (PID: 968)
Changes IE settings (feature browser emulation)
- AcroRd32.exe (PID: 968)
Creates files in the program directory
- AdobeARM.exe (PID: 2536)
INFO
Application launched itself
- AcroRd32.exe (PID: 968)
- RdrCEF.exe (PID: 540)
- iexplore.exe (PID: 2100)
Reads Internet Cache Settings
- iexplore.exe (PID: 2100)
- AcroRd32.exe (PID: 968)
- AcroRd32.exe (PID: 2164)
- iexplore.exe (PID: 2408)
- iexplore.exe (PID: 2352)
Reads the hosts file
- RdrCEF.exe (PID: 540)
Changes internet zones settings
- iexplore.exe (PID: 2100)
Reads settings of System Certificates
- AcroRd32.exe (PID: 968)
- iexplore.exe (PID: 2408)
- iexplore.exe (PID: 2100)
Reads internet explorer settings
- iexplore.exe (PID: 2408)
- iexplore.exe (PID: 2352)
Creates files in the user directory
- iexplore.exe (PID: 2408)
- iexplore.exe (PID: 2100)
- iexplore.exe (PID: 2352)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2100)
Changes settings of System certificates
- iexplore.exe (PID: 2100)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| | | Adobe Portable Document Format (100) |
EXIF
| PDFVersion: | 1.5 |
|---|---|
| Linearized: | Yes |
| Producer: | Skia/PDF m87 |
| PageCount: | 1 |
Total processes
44
Monitored processes
10
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 540 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16448250 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 860 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\Reader_sl.exe | — | AdobeARM.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat SpeedLauncher Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 968 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" "C:\Users\admin\AppData\Local\Temp\Transfer 3393394531.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | explorer.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 0 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 2100 | "C:\Program Files\Internet Explorer\iexplore.exe" http://leaheby.acatfimyrt.work/33382c | C:\Program Files\Internet Explorer\iexplore.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2164 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\AppData\Local\Temp\Transfer 3393394531.pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 0 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 2352 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2100 CREDAT:857361 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2408 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2100 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2536 | "C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe" /PRODUCT:Reader /VERSION:15.0 /MODE:3 | C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Reader and Acrobat Manager Exit code: 0 Version: 1.824.27.2646 Modules
| |||||||||||||||
| 3244 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="540.0.377609693\58934184" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 3288 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --disable-3d-apis --disable-databases --disable-direct-npapi-requests --disable-file-system --disable-notifications --disable-shared-workers --disable-direct-write --lang=en-US --lang=en-US --log-severity=disable --product-version="ReaderServices/15.23.20053 Chrome/45.0.2454.85" --device-scale-factor=1 --enable-delegated-renderer --num-raster-threads=2 --gpu-rasterization-msaa-sample-count=8 --content-image-texture-target=3553 --video-image-texture-target=3553 --disable-accelerated-video-decode --disable-webrtc-hw-encoding --disable-gpu-compositing --channel="540.1.1926989663\512061302" --allow-no-sandbox-job /prefetch:673131151 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
Total events
1 018
Read events
862
Write events
153
Delete events
3
Modification events
| (PID) Process: | (2164) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (2164) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | bExpandRHPInViewer |
Value: 1 | |||
| (PID) Process: | (2164) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\NoTimeOut |
| Operation: | write | Name: | smailto |
Value: 5900 | |||
| (PID) Process: | (968) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_BROWSER_EMULATION |
| Operation: | write | Name: | AcroRd32.exe |
Value: 10001 | |||
| (PID) Process: | (968) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (968) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A5000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (968) AcroRd32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\13B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2100) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 3594402030 | |||
| (PID) Process: | (2100) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30840499 | |||
| (PID) Process: | (2100) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
0
Suspicious files
32
Text files
73
Unknown types
34
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2164 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages-journal | — | |
MD5:— | SHA256:— | |||
| 2164 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9Rskggch_xa6r7q_1o4.tmp | — | |
MD5:— | SHA256:— | |||
| 2164 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9Reoov7o_xa6r7p_1o4.tmp | — | |
MD5:— | SHA256:— | |||
| 2164 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9Rmnnkfl_xa6r7s_1o4.tmp | — | |
MD5:— | SHA256:— | |||
| 2164 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9Rwzk51d_xa6r7r_1o4.tmp | — | |
MD5:— | SHA256:— | |||
| 968 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\CabAF07.tmp | — | |
MD5:— | SHA256:— | |||
| 968 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\TarAF08.tmp | — | |
MD5:— | SHA256:— | |||
| 2408 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\CabC01E.tmp | — | |
MD5:— | SHA256:— | |||
| 2408 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\TarC01F.tmp | — | |
MD5:— | SHA256:— | |||
| 2164 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages | sqlite | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
88
DNS requests
17
Threats
7
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
968 | AcroRd32.exe | GET | 304 | 2.16.107.49:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/277_15_23_20070.zip | unknown | — | — | whitelisted |
968 | AcroRd32.exe | GET | 304 | 2.16.107.49:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/280_15_23_20070.zip | unknown | — | — | whitelisted |
968 | AcroRd32.exe | GET | 304 | 2.16.107.49:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/278_15_23_20070.zip | unknown | — | — | whitelisted |
968 | AcroRd32.exe | GET | 304 | 2.16.107.49:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/281_15_23_20070.zip | unknown | — | — | whitelisted |
2408 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQS14tALDViBvqCf47YkiQRtKz1BAQUpc436uuwdQ6UZ4i0RfrZJBCHlh8CEA2lgvq%2FySgvaMoz%2FAIGEA4%3D | US | der | 280 b | whitelisted |
968 | AcroRd32.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
2408 | iexplore.exe | GET | 200 | 2.16.186.35:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | unknown | der | 1.37 Kb | whitelisted |
2408 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQS14tALDViBvqCf47YkiQRtKz1BAQUpc436uuwdQ6UZ4i0RfrZJBCHlh8CEA2lgvq%2FySgvaMoz%2FAIGEA4%3D | US | der | 280 b | whitelisted |
2408 | iexplore.exe | GET | 200 | 2.16.186.27:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgNucfuynlus1eFhqCQyCXkvag%3D%3D | unknown | der | 527 b | whitelisted |
2408 | iexplore.exe | GET | 200 | 2.16.186.27:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgOtkhJ2M%2BN%2FHoWcvTvRL%2Bhzyw%3D%3D | unknown | der | 527 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
968 | AcroRd32.exe | 2.18.233.74:443 | armmf.adobe.com | Akamai International B.V. | — | whitelisted |
968 | AcroRd32.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2408 | iexplore.exe | 104.24.123.127:443 | stumfuncrosa.work | Cloudflare Inc | US | shared |
2408 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2408 | iexplore.exe | 95.181.172.95:80 | leaheby.acatfimyrt.work | QWARTA LLC | RU | suspicious |
2100 | iexplore.exe | 95.181.172.95:80 | leaheby.acatfimyrt.work | QWARTA LLC | RU | suspicious |
2408 | iexplore.exe | 193.35.51.12:443 | find-your-profithere11.com | Irida Telekom Ltd. | RU | suspicious |
2408 | iexplore.exe | 2.16.186.35:80 | isrg.trustid.ocsp.identrust.com | Akamai International B.V. | — | whitelisted |
2408 | iexplore.exe | 2.16.186.27:80 | ocsp.int-x3.letsencrypt.org | Akamai International B.V. | — | whitelisted |
2100 | iexplore.exe | 193.35.51.12:443 | find-your-profithere11.com | Irida Telekom Ltd. | RU | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
acroipm2.adobe.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
leaheby.acatfimyrt.work |
| suspicious |
stumfuncrosa.work |
| suspicious |
find-your-profithere11.com |
| suspicious |
isrg.trustid.ocsp.identrust.com |
| whitelisted |
ocsp.int-x3.letsencrypt.org |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .work TLD |
2408 | iexplore.exe | Potentially Bad Traffic | ET INFO HTTP Request to Suspicious *.work Domain |
1052 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .work TLD |
2100 | iexplore.exe | Potentially Bad Traffic | ET INFO HTTP Request to Suspicious *.work Domain |
2408 | iexplore.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 28 |
2352 | iexplore.exe | Potentially Bad Traffic | ET INFO HTTP Request to Suspicious *.work Domain |
2100 | iexplore.exe | Potentially Bad Traffic | ET INFO HTTP Request to Suspicious *.work Domain |