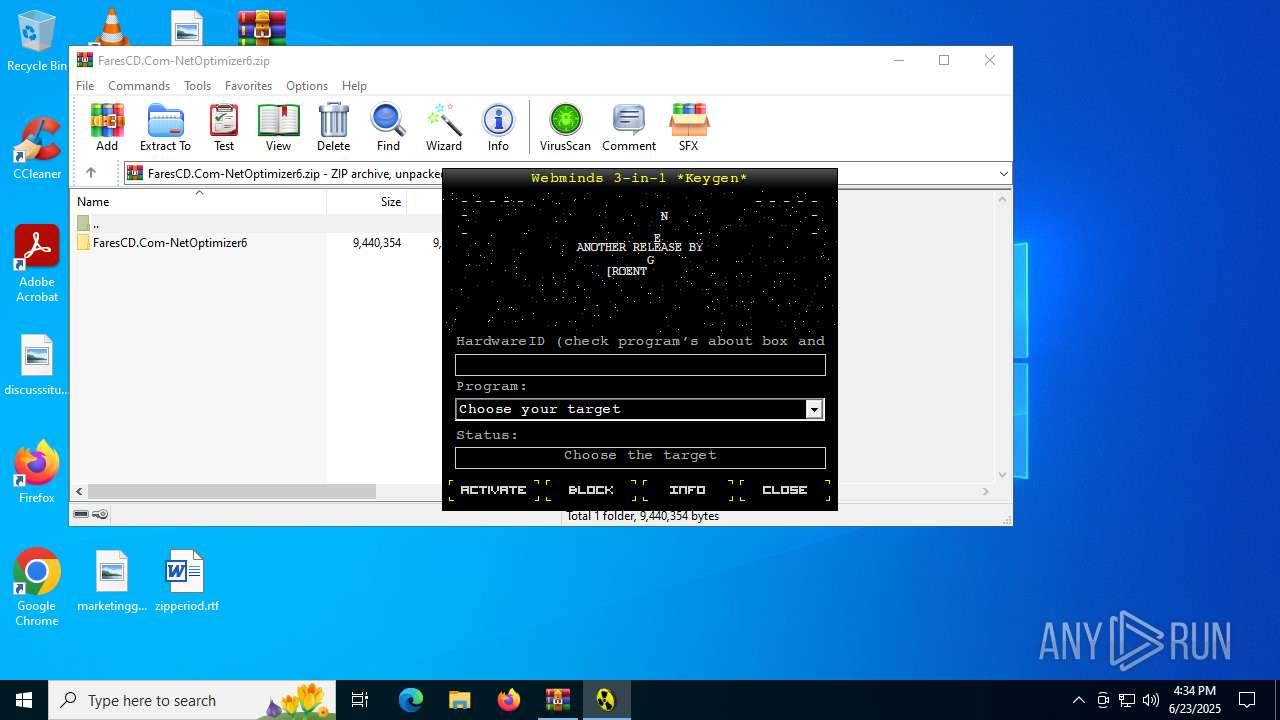
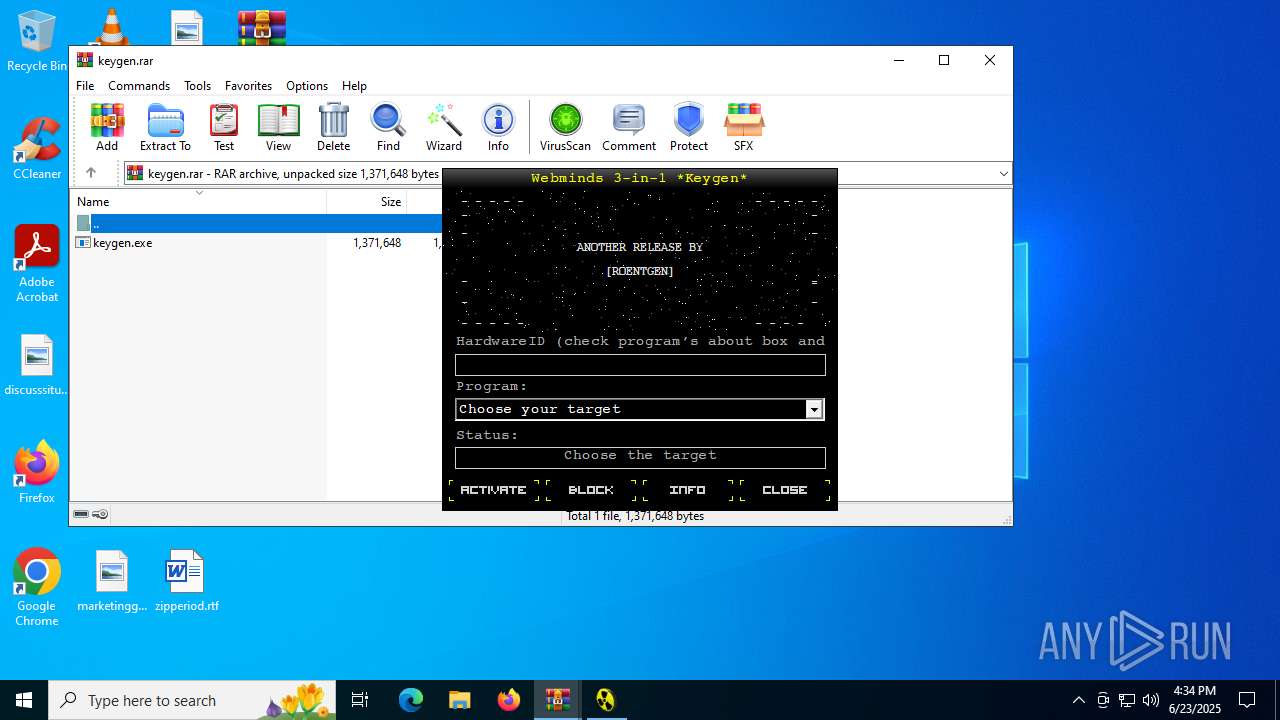
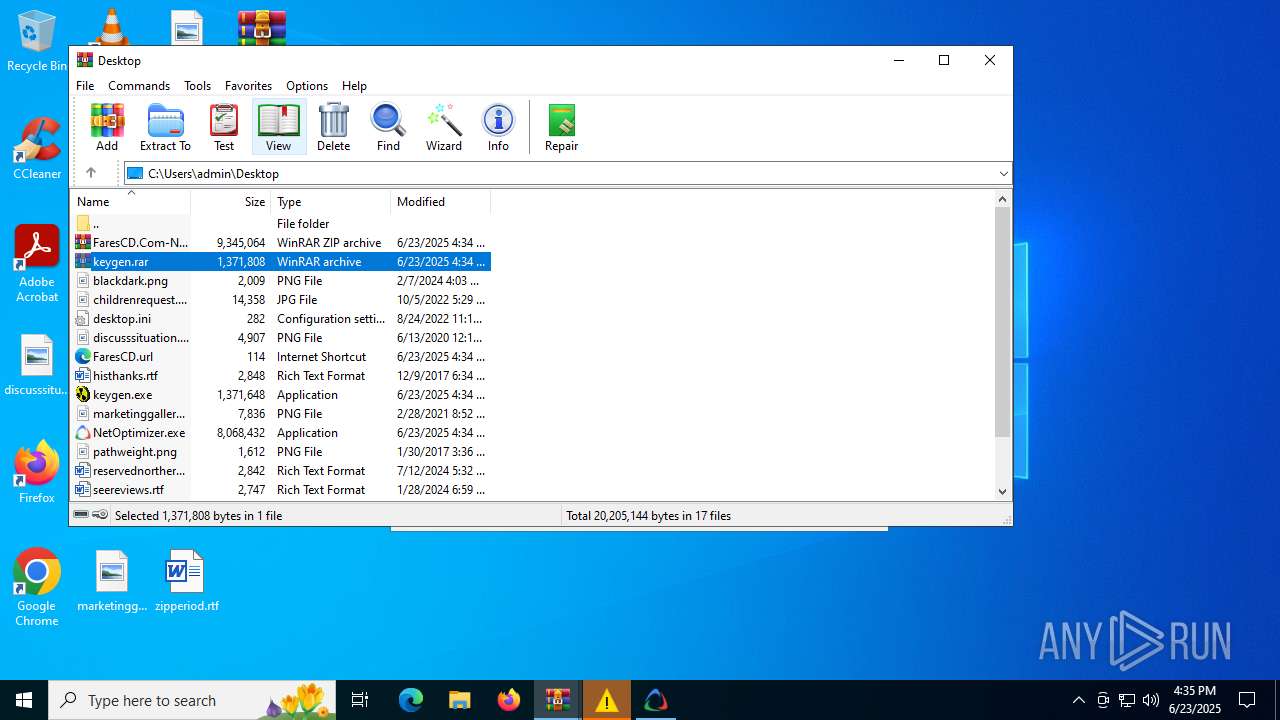
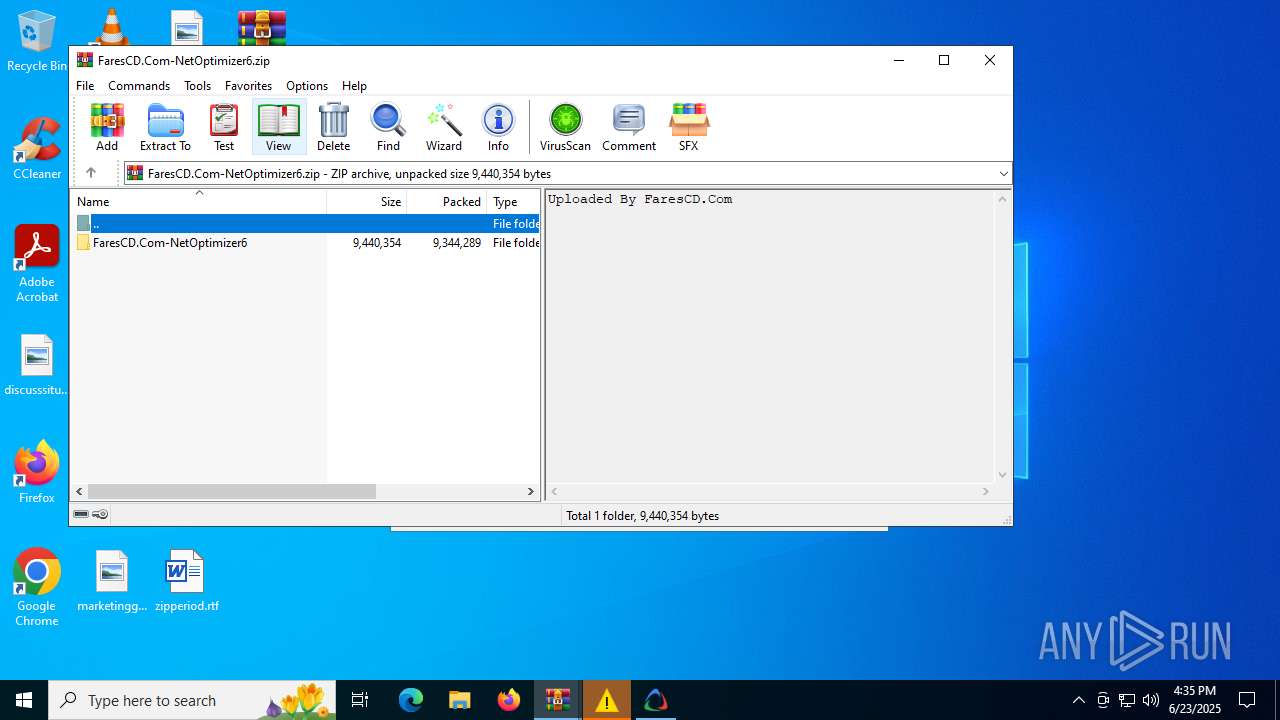
| File name: | FaresCD.Com-NetOptimizer6.zip |
| Full analysis: | https://app.any.run/tasks/aa552aa8-c761-48e6-8423-f9099bf68246 |
| Verdict: | Malicious activity |
| Analysis date: | June 23, 2025, 16:34:31 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v1.0 to extract, compression method=store |
| MD5: | 0EEA708AA7578151BB77001FE98C7E4E |
| SHA1: | 39B45E31BDA9813D63A019BDA7C2E42933F2B751 |
| SHA256: | 5D5E198EEE97878AED46292529650F3411E4E0FE2FC82D3B712AB7FAB43302E4 |
| SSDEEP: | 98304:DPcgTVZYSfLf12SORbrvUleHYdct5vPG/CBVC4DIVelo6Hp34hImSMFEezMVKV3V:40rO7yMyeuZkF+xxYK |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 4224)
SUSPICIOUS
Reads the Windows owner or organization settings
- NetOptimizer.tmp (PID: 1512)
Executable content was dropped or overwritten
- NetOptimizer.tmp (PID: 1512)
- NetOptimizer.exe (PID: 5628)
- NetOptimizer.exe (PID: 3480)
Reads security settings of Internet Explorer
- NetOptimizer.tmp (PID: 2512)
- WinRAR.exe (PID: 1128)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 1128)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 1128)
INFO
Manual execution by a user
- keygen.exe (PID: 5400)
- rundll32.exe (PID: 5780)
- WinRAR.exe (PID: 1128)
- NetOptimizer.exe (PID: 3480)
Reads the computer name
- keygen.exe (PID: 5400)
- NetOptimizer.tmp (PID: 2512)
- NetOptimizer.tmp (PID: 1512)
- MpCmdRun.exe (PID: 436)
Checks supported languages
- keygen.exe (PID: 5400)
- NetOptimizer.exe (PID: 3480)
- NetOptimizer.tmp (PID: 2512)
- NetOptimizer.exe (PID: 5628)
- NetOptimizer.tmp (PID: 1512)
- MpCmdRun.exe (PID: 436)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 5780)
Create files in a temporary directory
- NetOptimizer.exe (PID: 3480)
- NetOptimizer.tmp (PID: 1512)
- NetOptimizer.exe (PID: 5628)
- MpCmdRun.exe (PID: 436)
Detects InnoSetup installer (YARA)
- NetOptimizer.exe (PID: 3480)
- NetOptimizer.tmp (PID: 2512)
- NetOptimizer.exe (PID: 5628)
- NetOptimizer.tmp (PID: 1512)
Process checks computer location settings
- NetOptimizer.tmp (PID: 2512)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1128)
Compiled with Borland Delphi (YARA)
- NetOptimizer.tmp (PID: 2512)
- NetOptimizer.exe (PID: 3480)
- NetOptimizer.exe (PID: 5628)
- NetOptimizer.tmp (PID: 1512)
Checks proxy server information
- slui.exe (PID: 6492)
Reads the software policy settings
- slui.exe (PID: 6492)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 10 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2024:10:22 05:19:44 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | FaresCD.Com-NetOptimizer6/ |
Total processes
145
Monitored processes
12
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
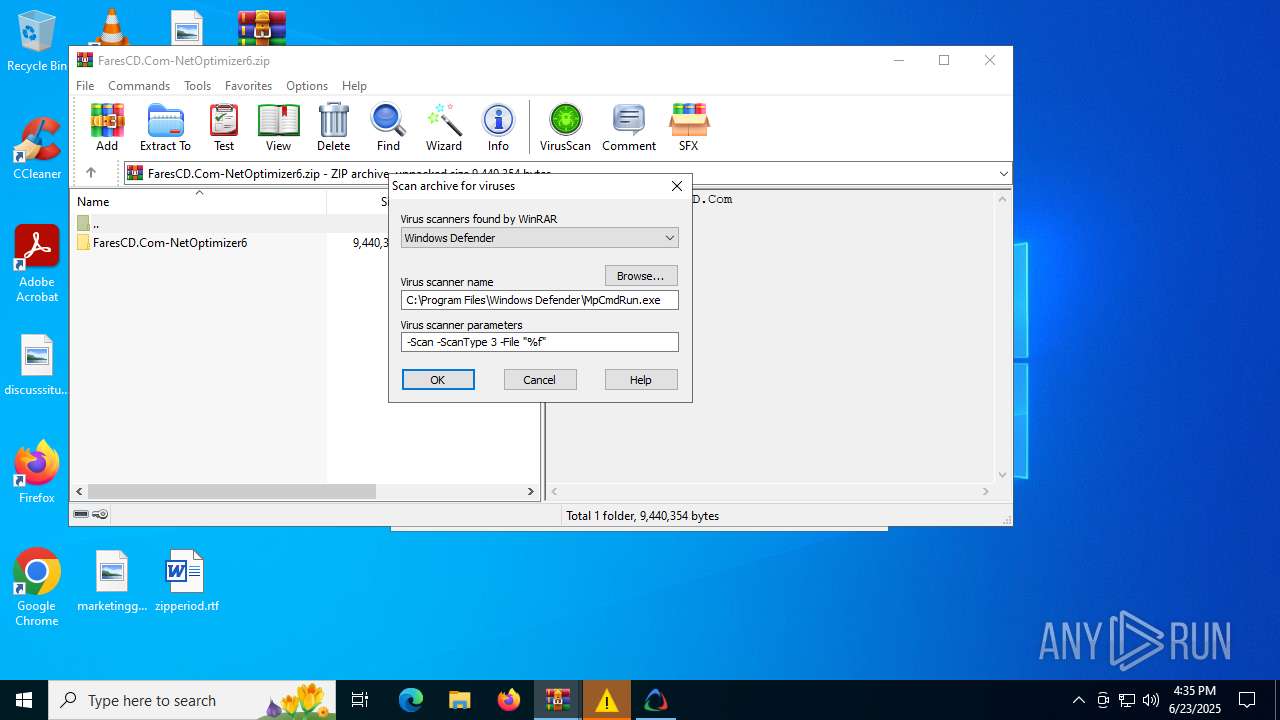
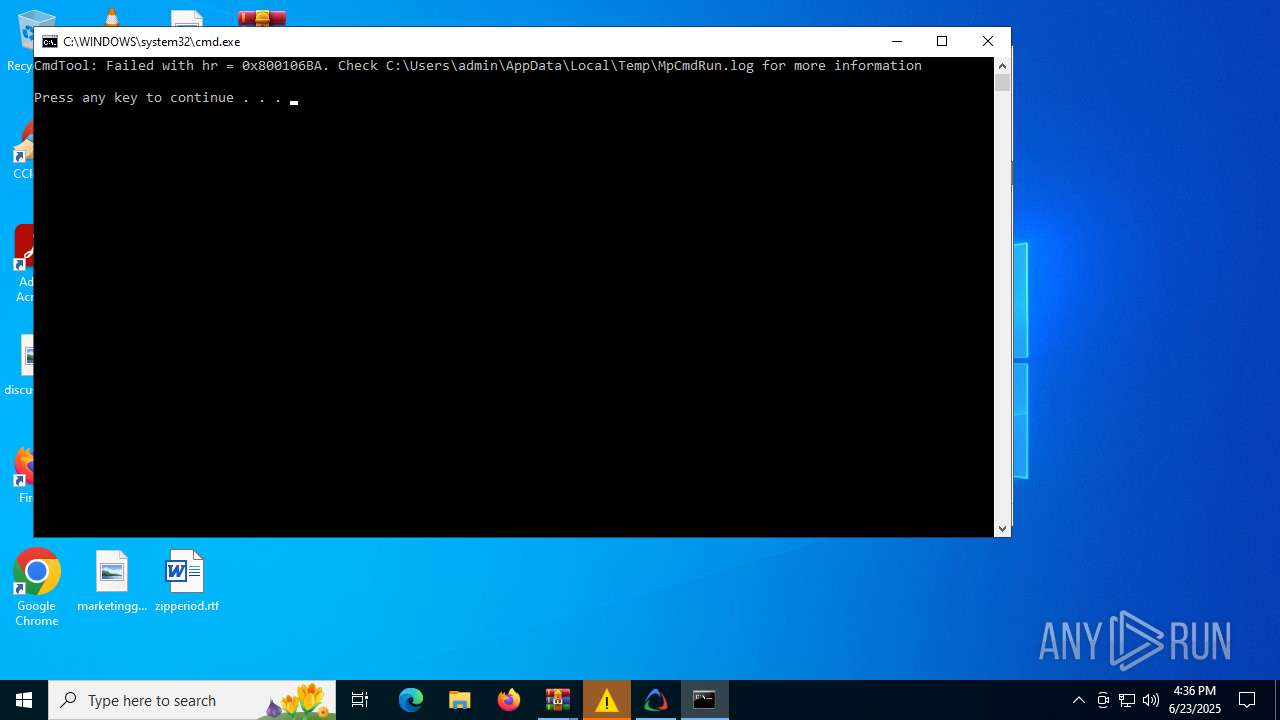
| 436 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR1128.39161" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1128 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\keygen.rar | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 1512 | "C:\Users\admin\AppData\Local\Temp\is-6VNLJ.tmp\NetOptimizer.tmp" /SL5="$80236,7624895,151552,C:\Users\admin\Desktop\NetOptimizer.exe" /SPAWNWND=$20372 /NOTIFYWND=$80360 | C:\Users\admin\AppData\Local\Temp\is-6VNLJ.tmp\NetOptimizer.tmp | NetOptimizer.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Setup/Uninstall Version: 51.1052.0.0 Modules
| |||||||||||||||
| 2468 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2512 | "C:\Users\admin\AppData\Local\Temp\is-9OKCF.tmp\NetOptimizer.tmp" /SL5="$80360,7624895,151552,C:\Users\admin\Desktop\NetOptimizer.exe" | C:\Users\admin\AppData\Local\Temp\is-9OKCF.tmp\NetOptimizer.tmp | — | NetOptimizer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Setup/Uninstall Version: 51.1052.0.0 Modules
| |||||||||||||||
| 3480 | "C:\Users\admin\Desktop\NetOptimizer.exe" | C:\Users\admin\Desktop\NetOptimizer.exe | explorer.exe | ||||||||||||
User: admin Company: Webminds, Inc. Integrity Level: MEDIUM Description: NetOptimizer™ Setup Version: 6.6.24.1020 Modules
| |||||||||||||||
| 4224 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\FaresCD.Com-NetOptimizer6.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4680 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\AppData\Local\Temp\Rar$VR1128.39161\Rar$Scan93647.bat" " | C:\Windows\System32\cmd.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
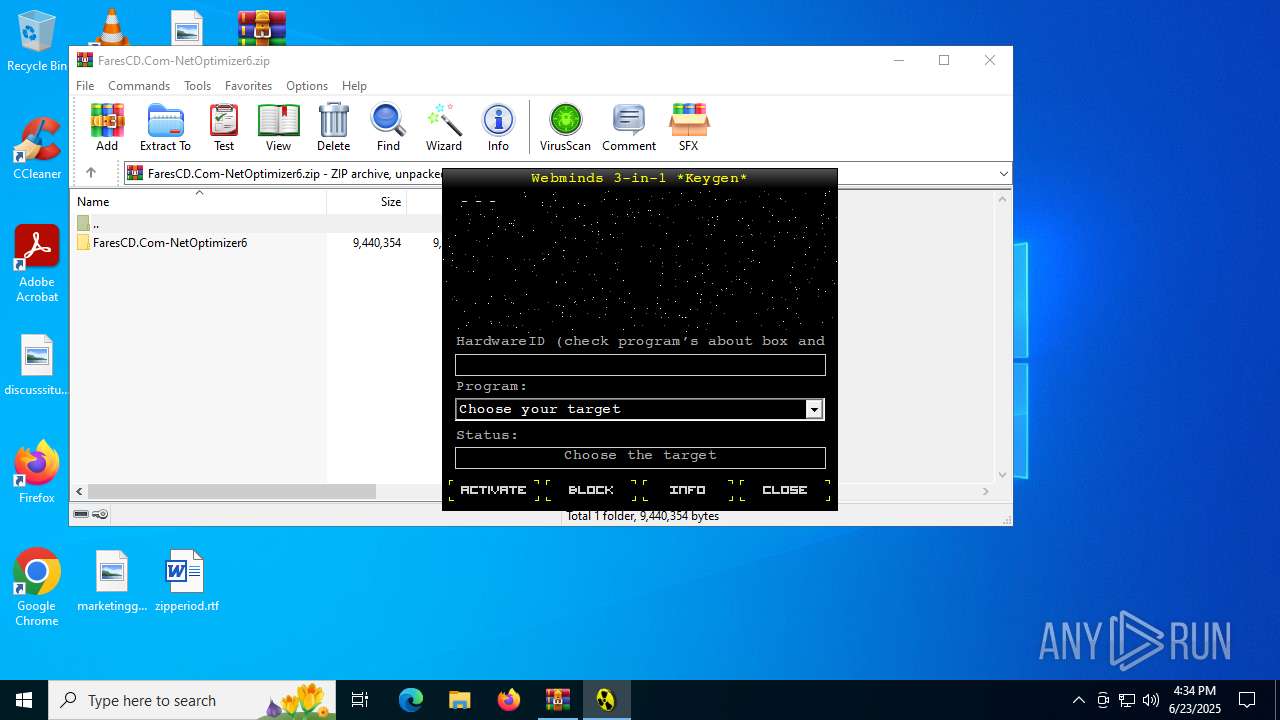
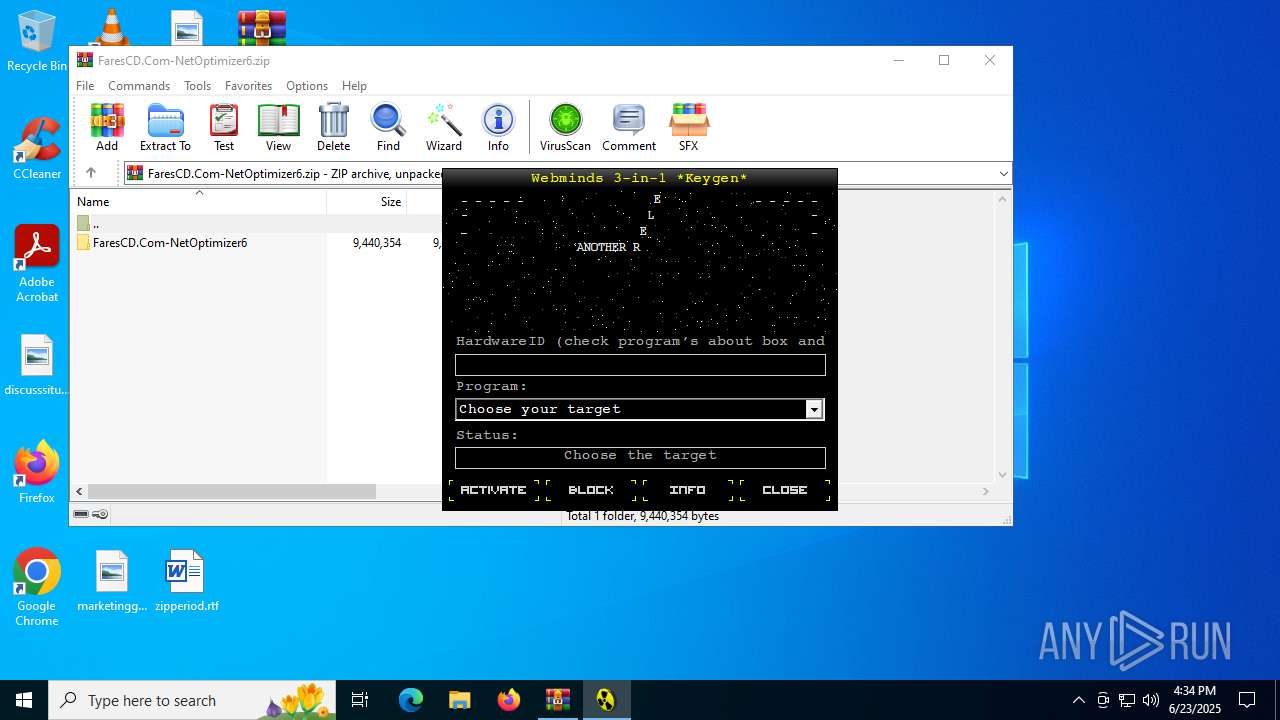
| 5400 | "C:\Users\admin\Desktop\keygen.exe" | C:\Users\admin\Desktop\keygen.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 5628 | "C:\Users\admin\Desktop\NetOptimizer.exe" /SPAWNWND=$20372 /NOTIFYWND=$80360 | C:\Users\admin\Desktop\NetOptimizer.exe | NetOptimizer.tmp | ||||||||||||
User: admin Company: Webminds, Inc. Integrity Level: HIGH Description: NetOptimizer™ Setup Version: 6.6.24.1020 Modules
| |||||||||||||||
Total events
7 470
Read events
7 435
Write events
35
Delete events
0
Modification events
| (PID) Process: | (4224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\FaresCD.Com-NetOptimizer6.zip | |||
| (PID) Process: | (4224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4224) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (1128) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
Executable files
4
Suspicious files
1
Text files
2
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1512 | NetOptimizer.tmp | C:\Users\admin\AppData\Local\Temp\is-90HVJ.tmp\_isetup\_setup64.tmp | executable | |
MD5:E4211D6D009757C078A9FAC7FF4F03D4 | SHA256:388A796580234EFC95F3B1C70AD4CB44BFDDC7BA0F9203BF4902B9929B136F95 | |||
| 3480 | NetOptimizer.exe | C:\Users\admin\AppData\Local\Temp\is-9OKCF.tmp\NetOptimizer.tmp | executable | |
MD5:CE3498F6E2871D1E5D128597E890A37E | SHA256:E5BD267099F63B076CB680A6C239B68791BADF53E4F5126707033B48860608E3 | |||
| 1128 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1128.39161\FaresCD.Com-NetOptimizer6.zip\FaresCD.Com-NetOptimizer6\FaresCD.url | url | |
MD5:B5CDCB1B1DF1C7CB0EC2935F03F5B612 | SHA256:070EB8D88896595F257D84EDC13A6DF78A3B670116D1DEFA674F2BE393522C87 | |||
| 1128 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1128.39161\FaresCD.Com-NetOptimizer6.zip\FaresCD.Com-NetOptimizer6\NetOptimizer.exe | executable | |
MD5:D2E6FCBDD6EB0E78FC56A0D3C56B6387 | SHA256:CBEBF11A2DBCC855CBD2914916B7E587C5C9FC0DA7296E6A892101B889506823 | |||
| 1128 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1128.39161\Rar$Scan93647.bat | text | |
MD5:32C36A67956B6472A887CFA3DD4485D1 | SHA256:CDFB48E256F4AEA7CEBDECF9A82BD5AEC93B919C09A125C31A4B6480D90EAF6F | |||
| 436 | MpCmdRun.exe | C:\Users\admin\AppData\Local\Temp\MpCmdRun.log | text | |
MD5:904DA011F040D7E908D99A7000F9AF98 | SHA256:C810B4CF23966F3C3CF5F51CAB74B9FCC5F9AF979A4F79FCCEADCE7768189465 | |||
| 1128 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR1128.39161\FaresCD.Com-NetOptimizer6.zip\FaresCD.Com-NetOptimizer6\keygen.rar | compressed | |
MD5:48B7AA58F3ED08FF971C77DB79A54D30 | SHA256:5F4CCED02F408D167BA5ADB069FD8A29EBAEF20E59DFB261B9E61FD91408342A | |||
| 5628 | NetOptimizer.exe | C:\Users\admin\AppData\Local\Temp\is-6VNLJ.tmp\NetOptimizer.tmp | executable | |
MD5:CE3498F6E2871D1E5D128597E890A37E | SHA256:E5BD267099F63B076CB680A6C239B68791BADF53E4F5126707033B48860608E3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
29
TCP/UDP connections
44
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2028 | RUXIMICS.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.53.40.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2028 | RUXIMICS.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 200 | 20.190.159.23:443 | https://login.live.com/RST2.srf | unknown | xml | 1.24 Kb | whitelisted |
— | — | POST | 200 | 20.190.159.129:443 | https://login.live.com/ppsecure/deviceaddcredential.srf | unknown | text | 16.7 Kb | whitelisted |
— | — | POST | 200 | 40.126.31.129:443 | https://login.live.com/RST2.srf | unknown | xml | 11.0 Kb | whitelisted |
— | — | POST | 200 | 20.190.159.129:443 | https://login.live.com/RST2.srf | unknown | xml | 11.1 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2028 | RUXIMICS.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2028 | RUXIMICS.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.53.40.176:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5944 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2028 | RUXIMICS.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |