| File name: | DETAILS_AMOUNT.zip |
| Full analysis: | https://app.any.run/tasks/8db9320d-fab6-4eed-9d43-8d7eacd4b318 |
| Verdict: | Malicious activity |
| Analysis date: | July 12, 2020, 19:09:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | D9F0712D0773BC77DBAB90928BB57F13 |
| SHA1: | 6C34B1ACCB5B73B6FB38ADB9BD99BAA36E02F408 |
| SHA256: | 5D5AE2C33251E011015ACC714D026727FD244DB0E3C1338AAAFA5833AC7A6A1A |
| SSDEEP: | 6144:X9KwSWRFAZJQ6HYOX3MQqVLTRU3UOIgs38efusFpx3N3HcXqHSM05LYgH+1:X8gS7sLLCUOEMe2s13dHwqt05z+1 |
MALICIOUS
Application was dropped or rewritten from another process
- DETAILS AMOUNT.exe (PID: 3328)
- DETAILS AMOUNT.exe (PID: 2128)
- DETAILS AMOUNT.exe (PID: 2396)
- DETAILS AMOUNT.exe (PID: 3176)
- DETAILS AMOUNT.exe (PID: 2008)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 1848)
Uses Task Scheduler to run other applications
- DETAILS AMOUNT.exe (PID: 3176)
Actions looks like stealing of personal data
- DETAILS AMOUNT.exe (PID: 2396)
- DETAILS AMOUNT.exe (PID: 2008)
SUSPICIOUS
Reads the BIOS version
- DETAILS AMOUNT.exe (PID: 3176)
Creates files in the user directory
- DETAILS AMOUNT.exe (PID: 3176)
Executable content was dropped or overwritten
- DETAILS AMOUNT.exe (PID: 3176)
- WinRAR.exe (PID: 3208)
Reads Environment values
- DETAILS AMOUNT.exe (PID: 2396)
- DETAILS AMOUNT.exe (PID: 2008)
Application launched itself
- DETAILS AMOUNT.exe (PID: 3176)
- DETAILS AMOUNT.exe (PID: 2128)
Uses RUNDLL32.EXE to load library
- WinRAR.exe (PID: 3208)
Starts Internet Explorer
- rundll32.exe (PID: 1752)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 1088)
- iexplore.exe (PID: 2172)
Creates files in the user directory
- iexplore.exe (PID: 2172)
- iexplore.exe (PID: 1088)
Changes internet zones settings
- iexplore.exe (PID: 1088)
Reads internet explorer settings
- iexplore.exe (PID: 2172)
Dropped object may contain Bitcoin addresses
- iexplore.exe (PID: 2172)
Reads settings of System Certificates
- iexplore.exe (PID: 2172)
- iexplore.exe (PID: 1088)
Changes settings of System certificates
- iexplore.exe (PID: 1088)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1088)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2020:07:10 08:16:29 |
| ZipCRC: | 0x87d6ef61 |
| ZipCompressedSize: | 416403 |
| ZipUncompressedSize: | 455168 |
| ZipFileName: | DETAILS AMOUNT.exe |
Total processes
47
Monitored processes
11
Malicious processes
5
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
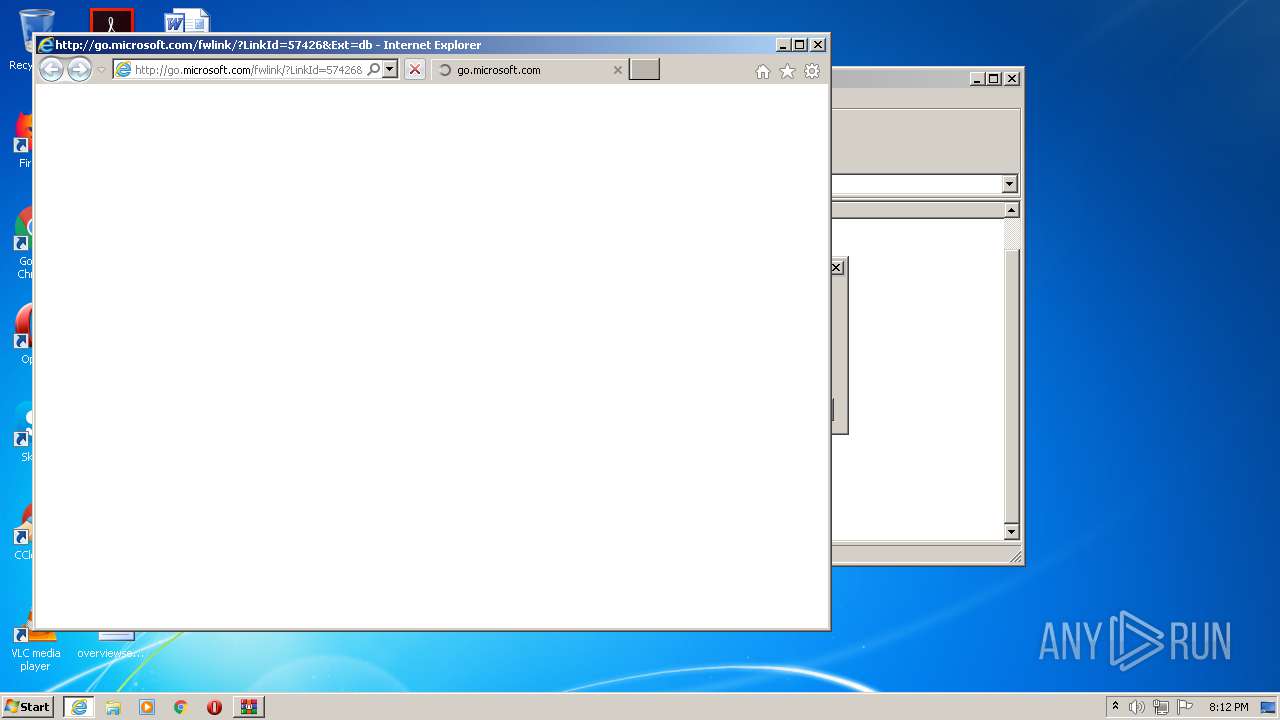
| 1088 | "C:\Program Files\Internet Explorer\iexplore.exe" http://go.microsoft.com/fwlink/?LinkId=57426&Ext=db | C:\Program Files\Internet Explorer\iexplore.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1752 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\IconCache.db | C:\Windows\system32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1848 | "C:\Windows\System32\schtasks.exe" /Create /TN "Updates\GYORCOiROgtEyc" /XML "C:\Users\admin\AppData\Local\Temp\tmp5116.tmp" | C:\Windows\System32\schtasks.exe | — | DETAILS AMOUNT.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Manages scheduled tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2008 | "{path}" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3208.45460\DETAILS AMOUNT.exe | DETAILS AMOUNT.exe | ||||||||||||
User: admin Company: Fandango ltd Integrity Level: MEDIUM Description: Rotten Tomatoes Exit code: 0 Version: 19.8.8.0 Modules
| |||||||||||||||
| 2128 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3208.45460\DETAILS AMOUNT.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3208.45460\DETAILS AMOUNT.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Fandango ltd Integrity Level: MEDIUM Description: Rotten Tomatoes Exit code: 0 Version: 19.8.8.0 Modules
| |||||||||||||||
| 2172 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1088 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2396 | "{path}" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3208.36756\DETAILS AMOUNT.exe | DETAILS AMOUNT.exe | ||||||||||||
User: admin Company: Fandango ltd Integrity Level: MEDIUM Description: Rotten Tomatoes Exit code: 4294967295 Version: 19.8.8.0 Modules
| |||||||||||||||
| 2672 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\IconCache.db | C:\Windows\system32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3176 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3208.36756\DETAILS AMOUNT.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3208.36756\DETAILS AMOUNT.exe | WinRAR.exe | ||||||||||||
User: admin Company: Fandango ltd Integrity Level: MEDIUM Description: Rotten Tomatoes Exit code: 4294967295 Version: 19.8.8.0 Modules
| |||||||||||||||
| 3208 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\DETAILS_AMOUNT.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
Total events
7 516
Read events
2 271
Write events
3 529
Delete events
1 716
Modification events
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\DETAILS_AMOUNT.zip | |||
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3208) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
Executable files
4
Suspicious files
8
Text files
10
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2172 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab7478.tmp | — | |
MD5:— | SHA256:— | |||
| 2172 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar7479.tmp | — | |
MD5:— | SHA256:— | |||
| 2172 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\OAZDC1DR.txt | — | |
MD5:— | SHA256:— | |||
| 2172 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\YVUSF6M4.txt | — | |
MD5:— | SHA256:— | |||
| 2172 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\VJ741KE2.txt | — | |
MD5:— | SHA256:— | |||
| 2172 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\FBAN9VUG.txt | — | |
MD5:— | SHA256:— | |||
| 1088 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 1088 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\CabC47D.tmp | — | |
MD5:— | SHA256:— | |||
| 1088 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\CabC47C.tmp | — | |
MD5:— | SHA256:— | |||
| 1088 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\TarC47F.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
19
DNS requests
10
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2172 | iexplore.exe | GET | 302 | 104.108.60.47:80 | http://go.microsoft.com/fwlink/?LinkId=57426&Ext=db | NL | — | — | whitelisted |
2172 | iexplore.exe | GET | 301 | 2.16.186.27:80 | http://shell.windows.com/fileassoc/fileassoc.asp?Ext=db | unknown | — | — | whitelisted |
2172 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2172 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
1088 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2172 | iexplore.exe | 104.108.60.47:80 | go.microsoft.com | Akamai Technologies, Inc. | NL | malicious |
2172 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
1088 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2008 | DETAILS AMOUNT.exe | 108.167.183.29:587 | mail.elfengineeringintl.com | CyrusOne LLC | US | malicious |
1088 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2172 | iexplore.exe | 2.16.186.27:80 | shell.windows.com | Akamai International B.V. | — | whitelisted |
1088 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2172 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2396 | DETAILS AMOUNT.exe | 108.167.183.29:587 | mail.elfengineeringintl.com | CyrusOne LLC | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
mail.elfengineeringintl.com |
| malicious |
go.microsoft.com |
| whitelisted |
shell.windows.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.bing.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
ieonline.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2396 | DETAILS AMOUNT.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
2396 | DETAILS AMOUNT.exe | Generic Protocol Command Decode | SURICATA SMTP invalid reply |
2008 | DETAILS AMOUNT.exe | Generic Protocol Command Decode | SURICATA Applayer Detect protocol only one direction |
2008 | DETAILS AMOUNT.exe | Generic Protocol Command Decode | SURICATA SMTP invalid reply |