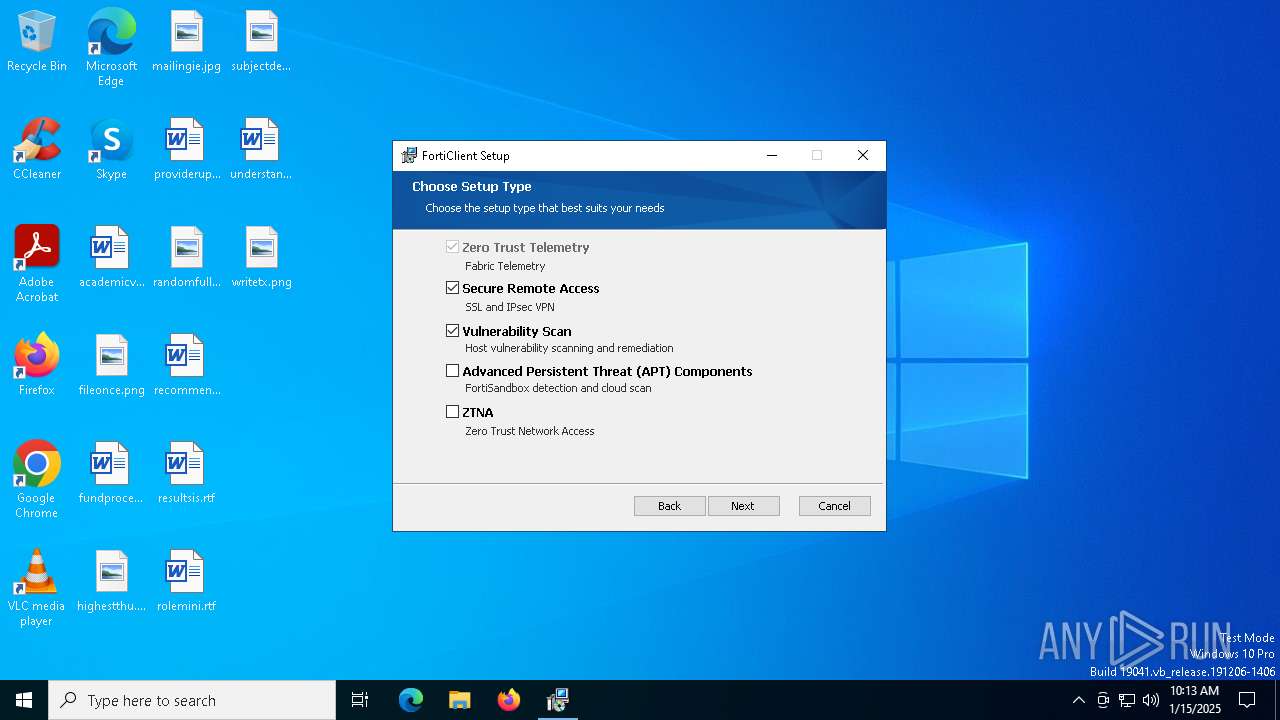
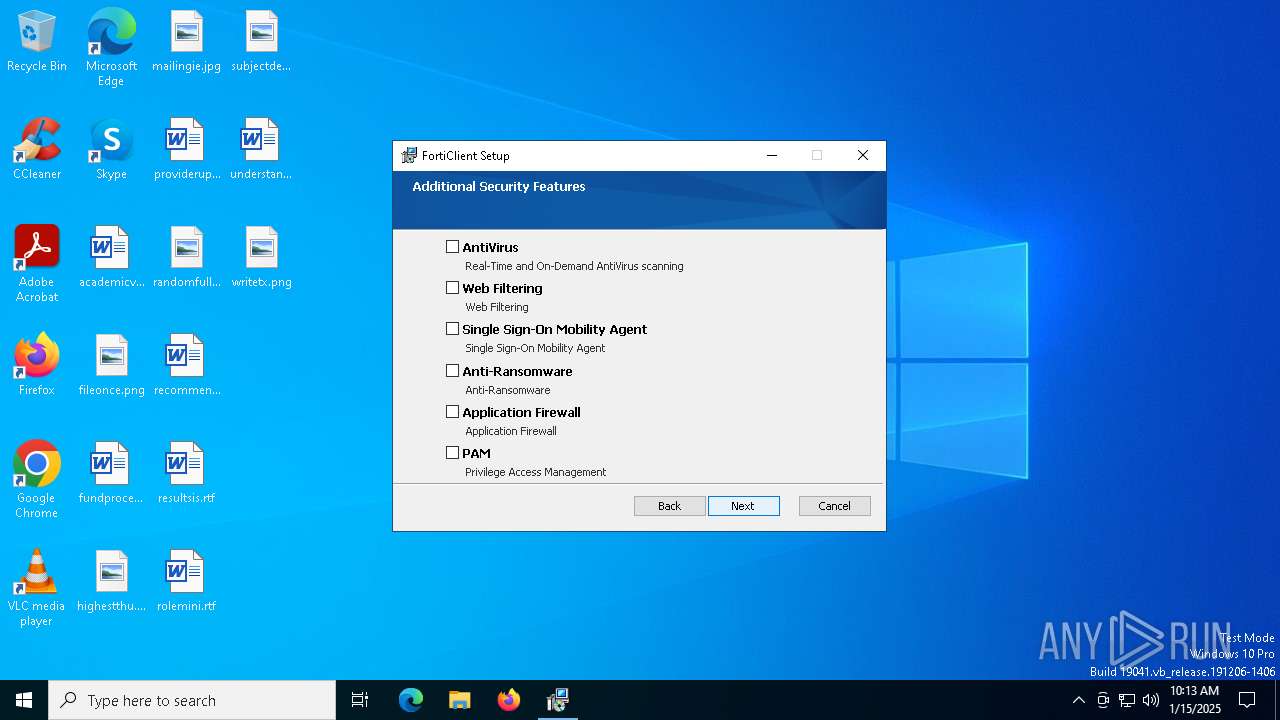
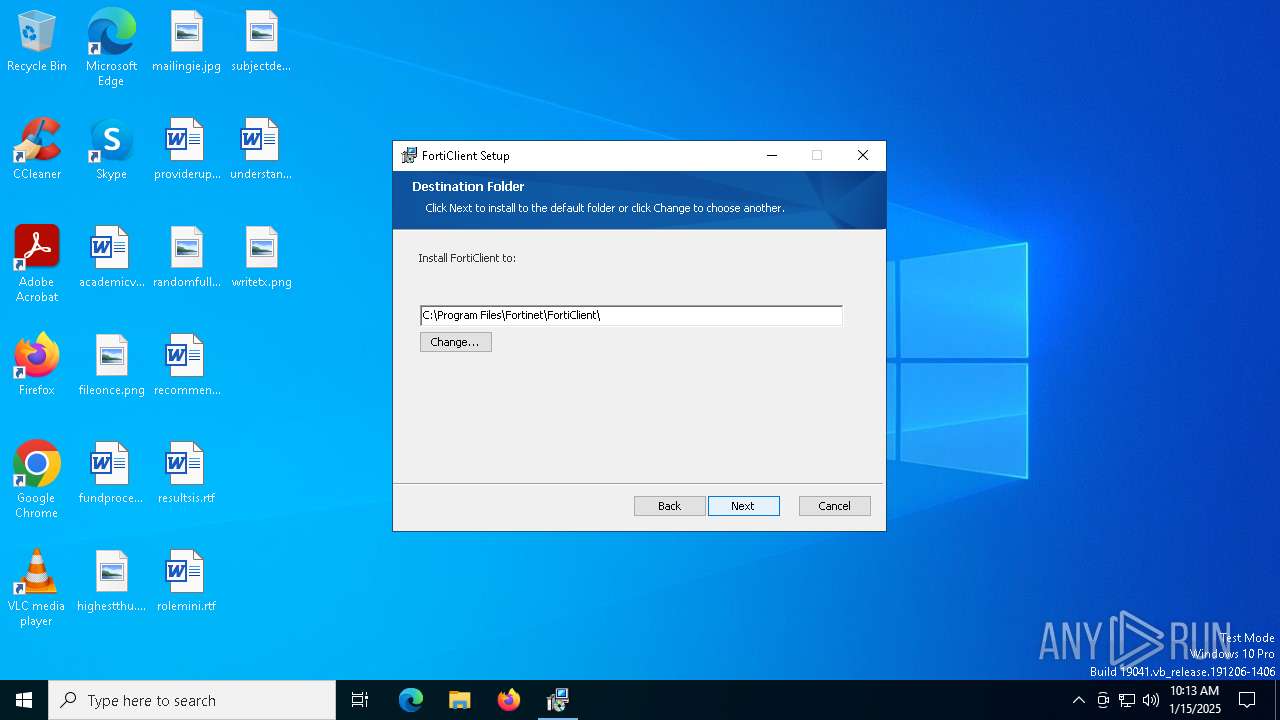
| URL: | https://links.fortinet.com/forticlient/win64/fabricagent |
| Full analysis: | https://app.any.run/tasks/3cf43fc2-8292-46be-9977-96be44e8ab28 |
| Verdict: | Malicious activity |
| Analysis date: | January 15, 2025, 10:11:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | C44243994241DA6951C05987A82B74B4 |
| SHA1: | 11357A6844BD889A4B7C2E78D9A28F3D57645138 |
| SHA256: | 5D46D3A7BA73116DEE4AD76142881CC278E47A510DA960C57D1B2816DB9475A6 |
| SSDEEP: | 3:N8MLO/I9lVDuy:2MaA97 |
MALICIOUS
Changes the autorun value in the registry
- VC_redist.x64.exe (PID: 3488)
- VC_redist.x86.exe (PID: 3680)
Registers / Runs the DLL via REGSVR32.EXE
- scheduler.exe (PID: 2220)
Starts NET.EXE for service management
- net.exe (PID: 6656)
- FortiSSLVPNdaemon.exe (PID: 6936)
SUSPICIOUS
Executable content was dropped or overwritten
- FortiClientOnlineInstaller.exe (PID: 6188)
- FortiClientOnlineInstaller.exe (PID: 3560)
- drvinst.exe (PID: 6032)
- drvinst.exe (PID: 1304)
- drvinst.exe (PID: 5912)
- drvinst.exe (PID: 4724)
- drvinst.exe (PID: 5872)
- VC_redist.x64.exe (PID: 3952)
- VC_redist.x64.exe (PID: 6880)
- VC_redist.x64.exe (PID: 3488)
- VC_redist.x86.exe (PID: 6200)
- VC_redist.x64.exe (PID: 7040)
- VC_redist.x64.exe (PID: 1540)
- VC_redist.x86.exe (PID: 3824)
- VC_redist.x86.exe (PID: 3680)
- VC_redist.x86.exe (PID: 4504)
- VC_redist.x86.exe (PID: 5008)
- update_task.exe (PID: 7968)
Reads security settings of Internet Explorer
- FortiClientOnlineInstaller.exe (PID: 6188)
- FortiClientOnlineInstaller.exe (PID: 3560)
- VC_redist.x64.exe (PID: 1540)
- VC_redist.x86.exe (PID: 4504)
Starts itself from another location
- FortiClientOnlineInstaller.exe (PID: 6188)
- VC_redist.x64.exe (PID: 6880)
- VC_redist.x86.exe (PID: 3824)
Creates/Modifies COM task schedule object
- FortiClientOnlineInstaller.exe (PID: 3560)
- msiexec.exe (PID: 7004)
Connects to the server without a host name
- FortiClientOnlineInstaller.exe (PID: 3560)
Checks Windows Trust Settings
- FortiClientOnlineInstaller.exe (PID: 3560)
- drvinst.exe (PID: 6032)
- drvinst.exe (PID: 5872)
- scheduler.exe (PID: 2220)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 7004)
Drops a system driver (possible attempt to evade defenses)
- drvinst.exe (PID: 6032)
- drvinst.exe (PID: 5872)
- msiexec.exe (PID: 7004)
- drvinst.exe (PID: 4724)
Process drops legitimate windows executable
- msiexec.exe (PID: 7004)
- msiexec.exe (PID: 2216)
- VC_redist.x64.exe (PID: 6880)
- VC_redist.x64.exe (PID: 3488)
- VC_redist.x64.exe (PID: 3952)
- VC_redist.x86.exe (PID: 6200)
- VC_redist.x64.exe (PID: 7040)
- VC_redist.x86.exe (PID: 3680)
- VC_redist.x86.exe (PID: 3824)
- VC_redist.x86.exe (PID: 5008)
- update_task.exe (PID: 7968)
Creates files in the driver directory
- msiexec.exe (PID: 7004)
- drvinst.exe (PID: 1304)
- drvinst.exe (PID: 5872)
- drvinst.exe (PID: 6032)
- drvinst.exe (PID: 4724)
- msiexec.exe (PID: 2216)
The process drops C-runtime libraries
- msiexec.exe (PID: 2216)
- msiexec.exe (PID: 7004)
Executes as Windows Service
- scheduler.exe (PID: 2220)
- VSSVC.exe (PID: 7136)
Adds/modifies Windows certificates
- scheduler.exe (PID: 2220)
Starts a Microsoft application from unusual location
- VC_redist.x64.exe (PID: 3488)
- VC_redist.x64.exe (PID: 6880)
- VC_redist.x86.exe (PID: 3824)
- VC_redist.x86.exe (PID: 3680)
Searches for installed software
- dllhost.exe (PID: 4548)
- VC_redist.x64.exe (PID: 1540)
- VC_redist.x86.exe (PID: 3824)
Creates a software uninstall entry
- VC_redist.x64.exe (PID: 3488)
- VC_redist.x86.exe (PID: 3680)
Application launched itself
- VC_redist.x64.exe (PID: 1540)
- VC_redist.x64.exe (PID: 2800)
- VC_redist.x86.exe (PID: 6192)
- FortiClient.exe (PID: 7264)
- VC_redist.x86.exe (PID: 4504)
Checks for external IP
- FortiESNAC.exe (PID: 6812)
INFO
Executable content was dropped or overwritten
- chrome.exe (PID: 6296)
- msiexec.exe (PID: 7004)
- msiexec.exe (PID: 2216)
The process uses the downloaded file
- chrome.exe (PID: 6296)
- chrome.exe (PID: 3288)
- FortiClientOnlineInstaller.exe (PID: 6188)
Application launched itself
- chrome.exe (PID: 6296)
- msiexec.exe (PID: 7004)
The sample compiled with english language support
- chrome.exe (PID: 6296)
- FortiClientOnlineInstaller.exe (PID: 6188)
- msiexec.exe (PID: 7004)
- FortiClientOnlineInstaller.exe (PID: 3560)
- msiexec.exe (PID: 2216)
- VC_redist.x64.exe (PID: 6880)
- VC_redist.x64.exe (PID: 3488)
- VC_redist.x64.exe (PID: 3952)
- VC_redist.x86.exe (PID: 6200)
- VC_redist.x64.exe (PID: 7040)
- VC_redist.x64.exe (PID: 1540)
- VC_redist.x86.exe (PID: 3680)
- VC_redist.x86.exe (PID: 4504)
- VC_redist.x86.exe (PID: 3824)
- VC_redist.x86.exe (PID: 5008)
- update_task.exe (PID: 7968)
Process checks whether UAC notifications are on
- FortiClientOnlineInstaller.exe (PID: 6188)
Checks supported languages
- FortiClientOnlineInstaller.exe (PID: 6188)
- FortiClientOnlineInstaller.exe (PID: 3560)
- msiexec.exe (PID: 5244)
- msiexec.exe (PID: 6772)
- msiexec.exe (PID: 7004)
- msiexec.exe (PID: 2216)
- drvinst.exe (PID: 5872)
- drvinst.exe (PID: 6032)
- drvinst.exe (PID: 4724)
- VC_redist.x86.exe (PID: 6200)
- VC_redist.x86.exe (PID: 6192)
- VC_redist.x86.exe (PID: 4504)
- VC_redist.x86.exe (PID: 5008)
- FCCOMInt.exe (PID: 1828)
- FCDBLog.exe (PID: 1220)
- FortiClient.exe (PID: 7460)
- FortiClient.exe (PID: 7824)
- FortiClient.exe (PID: 7560)
Reads the computer name
- FortiClientOnlineInstaller.exe (PID: 6188)
- FortiClientOnlineInstaller.exe (PID: 3560)
- msiexec.exe (PID: 7004)
- msiexec.exe (PID: 6772)
- msiexec.exe (PID: 5244)
- msiexec.exe (PID: 2216)
- drvinst.exe (PID: 4724)
- drvinst.exe (PID: 6032)
- drvinst.exe (PID: 5912)
- drvinst.exe (PID: 5872)
- VC_redist.x64.exe (PID: 6880)
- VC_redist.x86.exe (PID: 4504)
- FortiVPN.exe (PID: 6184)
Create files in a temporary directory
- FortiClientOnlineInstaller.exe (PID: 6188)
- FortiClientOnlineInstaller.exe (PID: 3560)
- msiexec.exe (PID: 5244)
Process checks computer location settings
- FortiClientOnlineInstaller.exe (PID: 6188)
- FCDBLog.exe (PID: 1220)
Creates files in the program directory
- FortiClientOnlineInstaller.exe (PID: 3560)
Reads the software policy settings
- FortiClientOnlineInstaller.exe (PID: 3560)
- drvinst.exe (PID: 5872)
- msiexec.exe (PID: 2216)
- scheduler.exe (PID: 2220)
Reads the machine GUID from the registry
- FortiClientOnlineInstaller.exe (PID: 3560)
- drvinst.exe (PID: 6032)
- drvinst.exe (PID: 5872)
- msiexec.exe (PID: 2216)
- scheduler.exe (PID: 2220)
- VC_redist.x64.exe (PID: 3488)
Reads Environment values
- msiexec.exe (PID: 5244)
- FCDBLog.exe (PID: 1220)
- FortiTray.exe (PID: 6748)
- FortiVPN.exe (PID: 6184)
- FortiClient.exe (PID: 7264)
- update_task.exe (PID: 7968)
Creates a software uninstall entry
- msiexec.exe (PID: 2216)
- msiexec.exe (PID: 7004)
Manages system restore points
- SrTasks.exe (PID: 6188)
Sends debugging messages
- msiexec.exe (PID: 7004)
Reads product name
- FortiClient.exe (PID: 7264)
Manual execution by a user
- FortiClient.exe (PID: 7264)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
202
Monitored processes
65
Malicious processes
19
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 720 | FortiSettings.exe -s FC_{73EFB30F-1CAD-4a7a-AE2E-150282B6CE25}_000024 | C:\Program Files\Fortinet\FortiClient\FortiSettings.exe | — | scheduler.exe | |||||||||||
User: SYSTEM Company: Fortinet Inc. Integrity Level: SYSTEM Description: FortiClient Settings Service Version: 7.4.2.1737 | |||||||||||||||
| 1220 | FCDBLog.exe -s FC_{73EFB30F-1CAD-4a7a-AE2E-150282B6CE25}_000011 | C:\Program Files\Fortinet\FortiClient\FCDBLog.exe | — | scheduler.exe | |||||||||||
User: SYSTEM Company: Fortinet Inc. Integrity Level: SYSTEM Description: FortiClient Logging daemon Version: 7.4.2.1737 | |||||||||||||||
| 1304 | DrvInst.exe "2" "211" "ROOT\NET\0001" "C:\WINDOWS\INF\oem6.inf" "oem6.inf:3205552cbf00c145:ftsvnic.ndi:14.0.4.122:root\ftsvnic," "4219b83e7" "00000000000001E4" | C:\Windows\System32\drvinst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1540 | "C:\ProgramData\Package Cache\{8bdfe669-9705-4184-9368-db9ce581e0e7}\VC_redist.x64.exe" -burn.clean.room="C:\ProgramData\Package Cache\{8bdfe669-9705-4184-9368-db9ce581e0e7}\VC_redist.x64.exe" -burn.filehandle.attached=540 -burn.filehandle.self=568 -uninstall -quiet -burn.related.upgrade -burn.ancestors={5af95fd8-a22e-458f-acee-c61bd787178e} -burn.filehandle.self=1072 -burn.embedded BurnPipe.{04A654D4-06B2-4F0B-8F6C-39562D0BBBBB} {BF543971-C794-4327-9486-DF0F39CC7CF1} 3488 | C:\ProgramData\Package Cache\{8bdfe669-9705-4184-9368-db9ce581e0e7}\VC_redist.x64.exe | VC_redist.x64.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Visual C++ 2015-2022 Redistributable (x64) - 14.36.32532 Exit code: 0 Version: 14.36.32532.0 Modules
| |||||||||||||||
| 1828 | "C:\Program Files\Fortinet\FortiClient\fccomint.exe" /regserver | C:\Program Files\Fortinet\FortiClient\FCCOMInt.exe | — | scheduler.exe | |||||||||||
User: SYSTEM Company: Fortinet Inc. Integrity Level: SYSTEM Description: FortiClient COM Interface (Executable) Exit code: 0 Version: 7.4.2.1737 | |||||||||||||||
| 2216 | C:\Windows\System32\MsiExec.exe -Embedding C141E72DE0611ACF7A8B7FFC82C46181 E Global\MSI0000 | C:\Windows\System32\msiexec.exe | msiexec.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2220 | "C:\Program Files\Fortinet\FortiClient\scheduler.exe" | C:\Program Files\Fortinet\FortiClient\scheduler.exe | services.exe | ||||||||||||
User: SYSTEM Company: Fortinet Inc. Integrity Level: SYSTEM Description: FortiClient Scheduler Version: 7.4.2.1737 Modules
| |||||||||||||||
| 2800 | "C:\ProgramData\Package Cache\{8bdfe669-9705-4184-9368-db9ce581e0e7}\VC_redist.x64.exe" -uninstall -quiet -burn.related.upgrade -burn.ancestors={5af95fd8-a22e-458f-acee-c61bd787178e} -burn.filehandle.self=1072 -burn.embedded BurnPipe.{04A654D4-06B2-4F0B-8F6C-39562D0BBBBB} {BF543971-C794-4327-9486-DF0F39CC7CF1} 3488 | C:\ProgramData\Package Cache\{8bdfe669-9705-4184-9368-db9ce581e0e7}\VC_redist.x64.exe | — | VC_redist.x64.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Visual C++ 2015-2022 Redistributable (x64) - 14.36.32532 Exit code: 0 Version: 14.36.32532.0 Modules
| |||||||||||||||
| 3092 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.ProcessorMetrics --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5228 --field-trial-handle=1916,i,13470436927276504224,12073434989859204714,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 3288 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5160 --field-trial-handle=1916,i,13470436927276504224,12073434989859204714,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
59 614
Read events
56 508
Write events
2 374
Delete events
732
Modification events
| (PID) Process: | (6296) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (6296) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (6296) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (6296) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (6296) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (3288) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 01000000000000007EFF8ED63567DB01 | |||
| (PID) Process: | (3560) FortiClientOnlineInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{8052F904-874D-4d28-9380-AA9BDBF13AFD}\InProcServer32 |
| Operation: | write | Name: | ThreadingModel |
Value: diskcopy.dll | |||
| (PID) Process: | (3560) FortiClientOnlineInstaller.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{8052F904-874D-4d28-9380-AA9BDBF13AFD}\InProcServer32 |
| Operation: | write | Name: | AppID |
Value: {38EF4C74-0B57-45C1-923C-5F475EAC60F9} | |||
| (PID) Process: | (6296) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 1 | |||
| (PID) Process: | (6296) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | delete value | Name: | GoogleChromeAutoLaunch_A822CA3D40D4B8944864CFEA751D8D57 |
Value: | |||
Executable files
329
Suspicious files
337
Text files
185
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1367b6.TMP | — | |
MD5:— | SHA256:— | |||
| 6296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old~RF1367c6.TMP | — | |
MD5:— | SHA256:— | |||
| 6296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old~RF1367c6.TMP | — | |
MD5:— | SHA256:— | |||
| 6296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old~RF1367c6.TMP | — | |
MD5:— | SHA256:— | |||
| 6296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 6296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF1367d5.TMP | — | |
MD5:— | SHA256:— | |||
| 6296 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old~RF1367d5.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
51
DNS requests
29
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6296 | chrome.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEA6bGI750C3n79tQ4ghAGFo%3D | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6296 | chrome.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfIs%2BLjDtGwQ09XEB1Yeq%2BtX%2BBgQQU7NfjgtJxXWRM3y5nP%2Be6mK4cD08CEAitQLJg0pxMn17Nqb2Trtk%3D | unknown | — | — | whitelisted |
6296 | chrome.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEA8ZK8C1K2FOF0Q2W4wIAOc%3D | unknown | — | — | whitelisted |
3560 | FortiClientOnlineInstaller.exe | POST | 200 | 173.243.138.76:80 | http://173.243.138.76/fdsupdate | unknown | — | — | unknown |
3560 | FortiClientOnlineInstaller.exe | POST | — | 209.40.106.66:80 | http://209.40.106.66/fdsupdate | unknown | — | — | unknown |
3560 | FortiClientOnlineInstaller.exe | POST | 200 | 209.40.106.66:80 | http://209.40.106.66/fdsupdate | unknown | — | — | unknown |
4308 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4308 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5464 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1176 | svchost.exe | 184.30.131.245:80 | — | AKAMAI-AS | US | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1488 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1076 | svchost.exe | 69.192.162.125:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
6612 | chrome.exe | 173.194.79.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
6296 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6612 | chrome.exe | 154.52.2.213:443 | links.fortinet.com | FORTINET | US | malicious |
6612 | chrome.exe | 154.52.2.214:443 | filestore.fortinet.com | FORTINET | US | malicious |
6612 | chrome.exe | 142.250.185.78:443 | sb-ssl.google.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
go.microsoft.com |
| whitelisted |
links.fortinet.com |
| malicious |
accounts.google.com |
| whitelisted |
filestore.fortinet.com |
| malicious |
sb-ssl.google.com |
| whitelisted |
www.google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
forticlient.fortinet.net |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Misc activity | ET INFO External IP Lookup Domain (ipify .org) in DNS Lookup |
6812 | FortiESNAC.exe | Misc activity | ET INFO External IP Address Lookup Domain (ipify .org) in TLS SNI |
Process | Message |
|---|---|
msiexec.exe | Failed to release Service
|