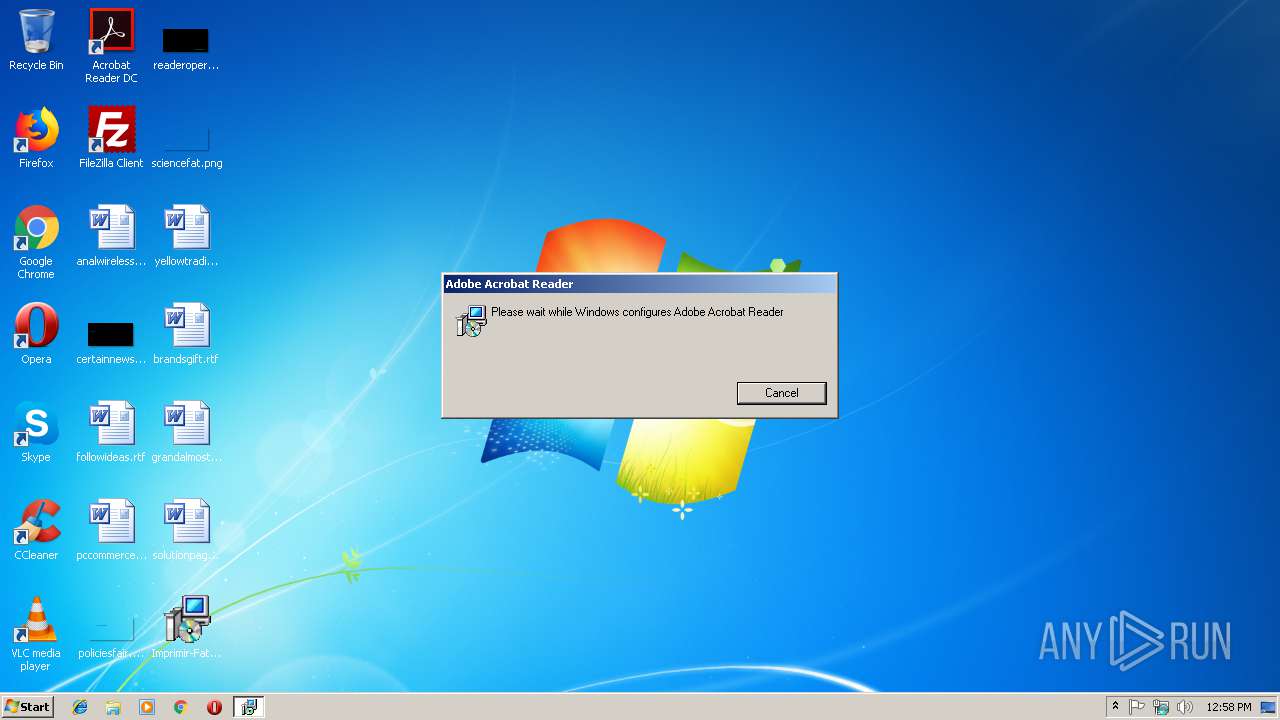
| File name: | Imprimir-Fatura-19-02-2019.msi |
| Full analysis: | https://app.any.run/tasks/2ebbdcf4-8a76-4fcd-b348-a95449eb9d8c |
| Verdict: | Malicious activity |
| Analysis date: | February 19, 2019, 12:58:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.3, MSI Installer, Last Printed: Wed Nov 21 14:59:58 2007, Create Time/Date: Wed Nov 21 14:59:58 2007, Last Saved Time/Date: Wed Nov 21 15:17:57 2007, Code page: 1252, Revision Number: {DBE20CDB-2E4C-4274-8B8D-8078B0735B02}, Number of Words: 10, Subject: Adobe Acrobat Reader, Author: Adobe Acrobat Reader, Name of Creating Application: Advanced Installer 12.2.1 build 64247, Template: ;1033, Comments: This installer database contains the logic and data required to install Adobe Acrobat Reader., Title: Installation Database, Keywords: Installer, MSI, Database, Security: 0, Number of Pages: 200 |
| MD5: | 4B1D9230B374EFFDDA67AFE2F57E2585 |
| SHA1: | F7D78F46D1C913414C385461F95E74FA962EECFD |
| SHA256: | 5D111482EA0B0B5065E00600D1618ACE2E9DDD5F1D75CF0BCDE4EF98E7D0F913 |
| SSDEEP: | 3072:zry4hdOmkr/wgz88ereWn/7w05g059xt7I3D7YQA6McB3RUN46ILJ9+ZB5yOanI:zrZdObO8er1nzTHC3D7YQAprp |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 300)
Changes the autorun value in the registry
- reg.exe (PID: 2944)
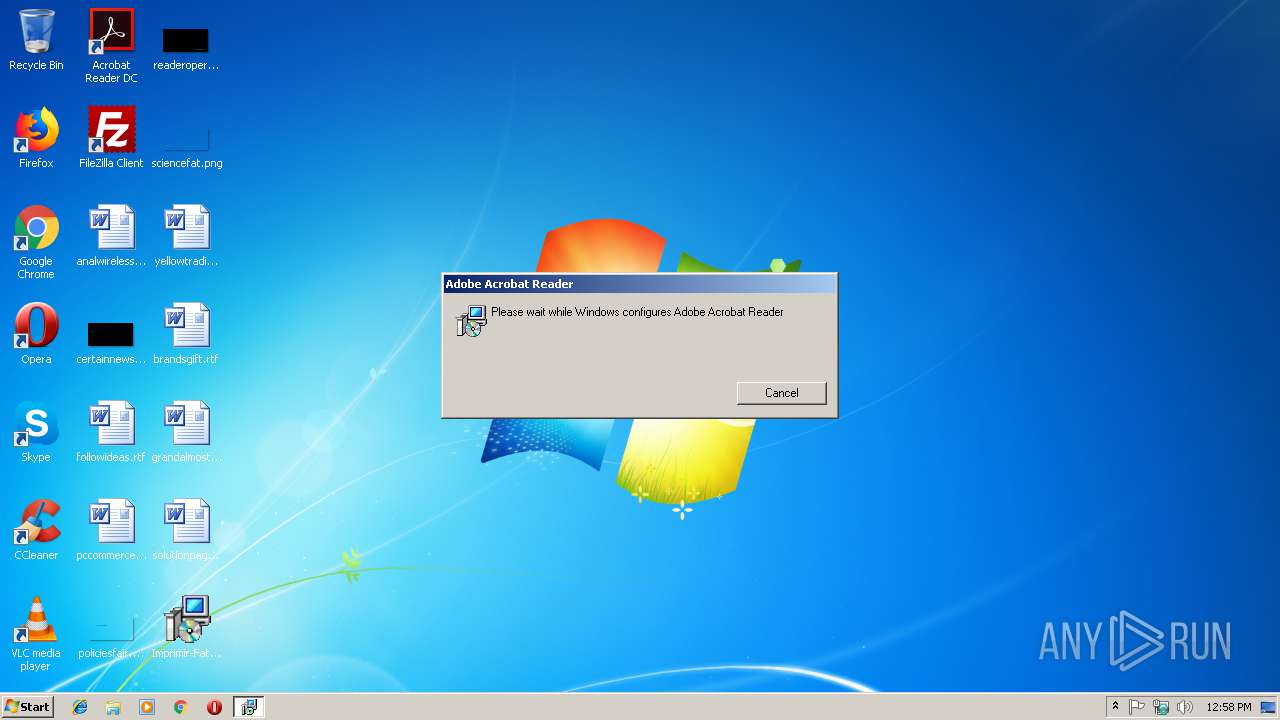
Application was dropped or rewritten from another process
- lc103B.tmp (PID: 2900)
SUSPICIOUS
Creates files in the user directory
- cmd.exe (PID: 3464)
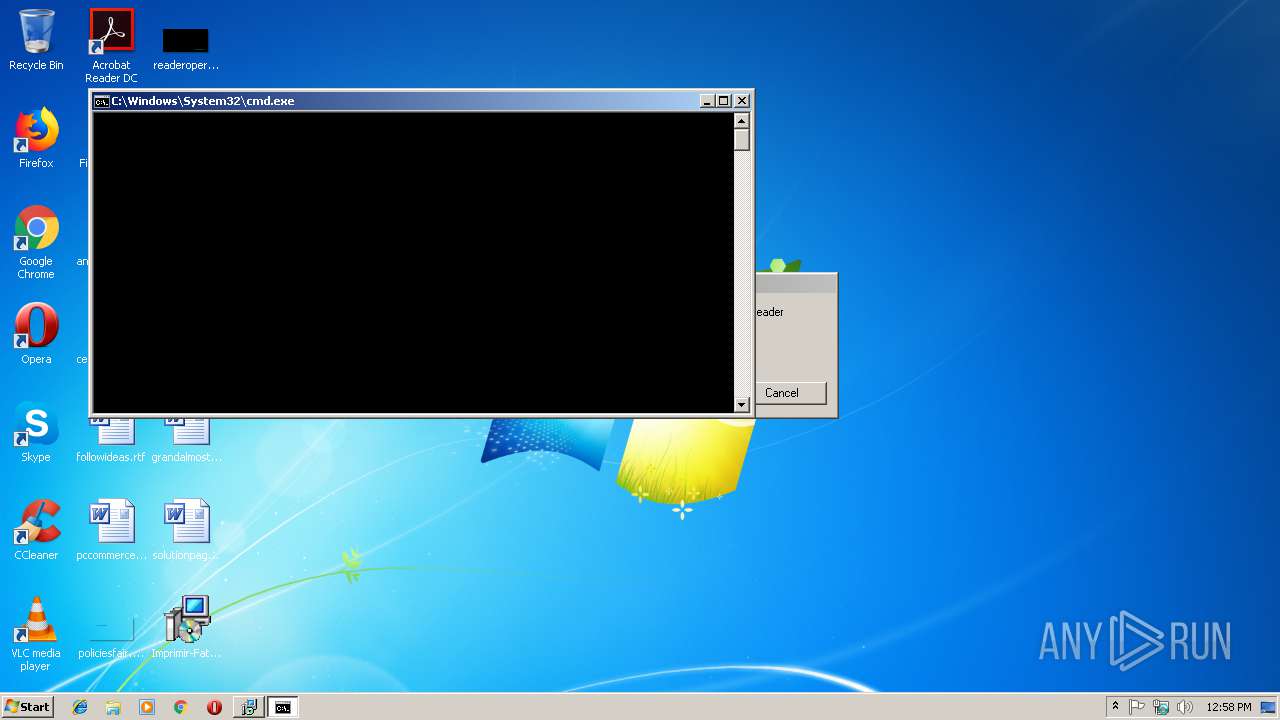
Starts CMD.EXE for commands execution
- MsiExec.exe (PID: 2344)
Starts Internet Explorer
- cmd.exe (PID: 3464)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2592)
- MsiExec.exe (PID: 2344)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 3048)
Reads Internet Cache Settings
- MsiExec.exe (PID: 2344)
INFO
Changes internet zones settings
- iexplore.exe (PID: 2856)
Application launched itself
- msiexec.exe (PID: 2592)
Reads Internet Cache Settings
- iexplore.exe (PID: 3400)
- iexplore.exe (PID: 2856)
Creates files in the user directory
- iexplore.exe (PID: 3400)
Reads internet explorer settings
- iexplore.exe (PID: 3400)
Reads settings of System Certificates
- iexplore.exe (PID: 2856)
Starts application with an unusual extension
- MsiExec.exe (PID: 2344)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (88.6) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (10) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| LastPrinted: | 2007:11:21 14:59:58 |
|---|---|
| CreateDate: | 2007:11:21 14:59:58 |
| ModifyDate: | 2007:11:21 15:17:57 |
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {DBE20CDB-2E4C-4274-8B8D-8078B0735B02} |
| Words: | 10 |
| Subject: | Adobe Acrobat Reader |
| Author: | Adobe Acrobat Reader |
| LastModifiedBy: | - |
| Software: | Advanced Installer 12.2.1 build 64247 |
| Template: | ;1033 |
| Comments: | This installer database contains the logic and data required to install Adobe Acrobat Reader. |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| Security: | None |
| Pages: | 200 |
Total processes
51
Monitored processes
14
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe6_ Global\UsGthrCtrlFltPipeMssGthrPipe6 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2344 | C:\Windows\system32\MsiExec.exe -Embedding 15F131178115DCA1864E4291A7A4516E | C:\Windows\system32\MsiExec.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 1073807364 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2592 | C:\Windows\system32\msiexec.exe /V | C:\Windows\system32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2856 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1073807364 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2900 | "C:\Users\admin\AppData\Local\Temp\lc103B.tmp" | C:\Users\admin\AppData\Local\Temp\lc103B.tmp | — | MsiExec.exe | |||||||||||
User: admin Company: Caphyon LTD Integrity Level: MEDIUM Description: Executable that detects if running in a virtual machine Exit code: 1073807364 Version: 12.2.1.0 Modules
| |||||||||||||||
| 2944 | reg add HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run /v CzSZSr /t reg_sz /d "C:\Users\admin\Links\CzSZSr\CzSZSr.exe" | C:\Windows\system32\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3048 | "C:\Windows\System32\cmd.exe" /C start /MIN reg add HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run /v CzSZSr /t reg_sz /d "C:\Users\admin\Links\CzSZSr\CzSZSr.exe" | C:\Windows\System32\cmd.exe | — | MsiExec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3104 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\Desktop\Imprimir-Fatura-19-02-2019.msi" | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3204 | "C:\Windows\System32\cmd.exe" /C shutdown -r -f -t 0 | C:\Windows\System32\cmd.exe | — | MsiExec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3400 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2856 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 468
Read events
1 371
Write events
94
Delete events
3
Modification events
| (PID) Process: | (300) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\System32\msimsg.dll,-34 |
Value: Windows Installer Package | |||
| (PID) Process: | (2592) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 200A0000F074B7CE52C8D401 | |||
| (PID) Process: | (2592) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 846094D676564989E1D0A4B3F33A147E6A3D6F17F6666E133A09AAE41BE0B351 | |||
| (PID) Process: | (2592) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (2344) MsiExec.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2344) MsiExec.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2856) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (300) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (300) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\5F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\notepad.exe,-469 |
Value: Text Document | |||
| (PID) Process: | (2856) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
10
Suspicious files
5
Text files
17
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2592 | msiexec.exe | C:\Windows\Installer\20ebdb.msi | executable | |
MD5:— | SHA256:— | |||
| 3400 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\U2ZG9DE0\index[1].js | text | |
MD5:— | SHA256:— | |||
| 3400 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@adobe[1].txt | text | |
MD5:— | SHA256:— | |||
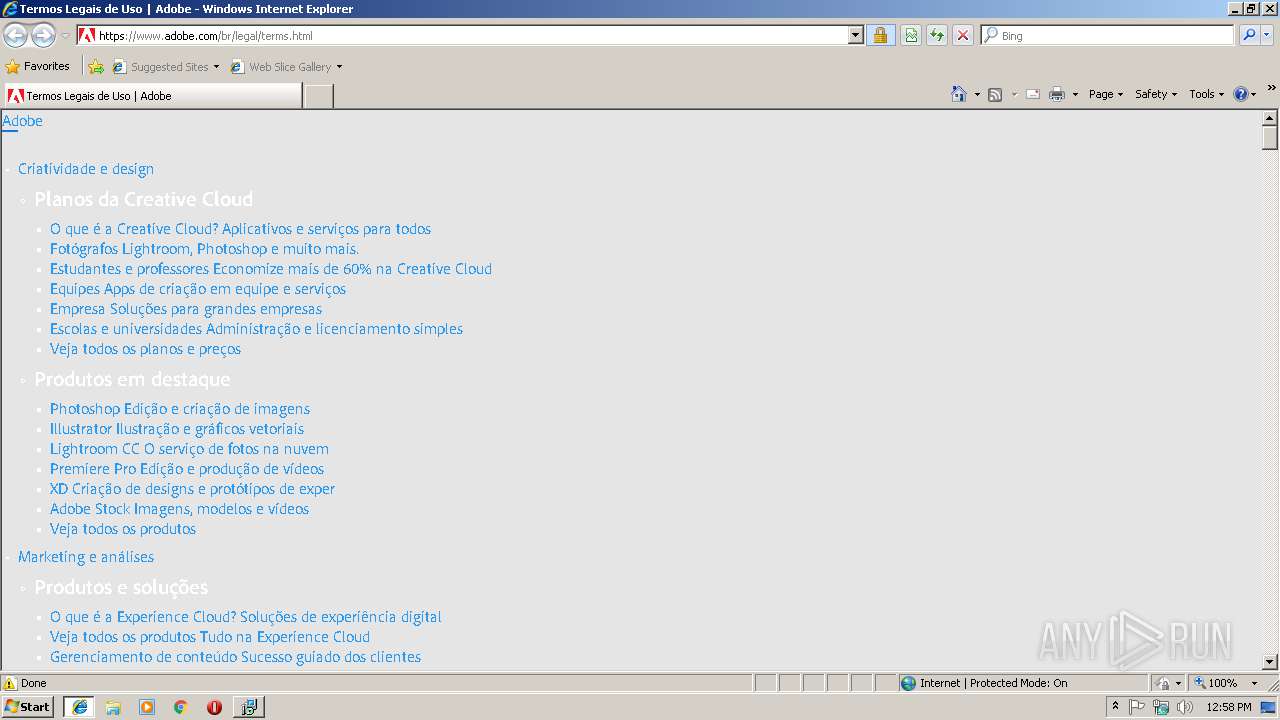
| 3400 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\terms[1].html | html | |
MD5:— | SHA256:— | |||
| 3400 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\adobe.min.fp-9f089e57989ec2e6fb36add7a91cbd7b[1].css | text | |
MD5:— | SHA256:— | |||
| 3400 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\U2ZG9DE0\liveperson.min.fp-0232b34deadc0421a8b6a57415f16562[1].css | text | |
MD5:— | SHA256:— | |||
| 3400 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\PP6KS563\main.min[1].js | text | |
MD5:— | SHA256:— | |||
| 3400 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\adobe-head.min.fp-49c976728c560175ef3915d2bbcaa219[1].js | text | |
MD5:— | SHA256:— | |||
| 3400 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\OCDM6JB6\customized.min.fp-98a146bdf24a2f72b562417b9c873c42[1].css | text | |
MD5:— | SHA256:— | |||
| 3400 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\BWPPCY0O\adobe.min.fp-5126a3a9012a80969defc0f9e08668e7[1].js | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
18
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2856 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2856 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3400 | iexplore.exe | 67.199.248.13:443 | adobe.ly | Bitly Inc | US | shared |
2344 | MsiExec.exe | 52.218.24.163:443 | s3-eu-west-1.amazonaws.com | Amazon.com, Inc. | IE | unknown |
2344 | MsiExec.exe | 172.217.21.228:80 | www.google.com | Google Inc. | US | whitelisted |
2856 | iexplore.exe | 92.123.235.227:443 | www.adobe.com | Akamai International B.V. | — | whitelisted |
3400 | iexplore.exe | 92.123.235.227:443 | www.adobe.com | Akamai International B.V. | — | whitelisted |
3400 | iexplore.exe | 23.38.53.224:443 | use.typekit.com | Akamai International B.V. | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
s3-eu-west-1.amazonaws.com |
| shared |
www.bing.com |
| whitelisted |
adobe.ly |
| suspicious |
www.adobe.com |
| whitelisted |
use.typekit.com |
| whitelisted |
p.typekit.net |
| shared |
www.google.com |
| malicious |